Domestic Robots. a case study on security in ubiquitous computing. Thomas Knell Ubiquitous Computing Seminar
|
|
|
- Jeffery Owens
- 6 years ago
- Views:
Transcription
1 Domestic Robots a case study on security in ubiquitous computing Thomas Knell Ubiquitous Computing Seminar
2 Defining Robot There exists no universally accepted definition of a robot! Any automatically operated machine that replaces human effort, though it may not resemble human beings in appearance or perform functions in a humanlike manner. Encyclopaedia Britannica! A robot is a cyber-physical system with sensors, actuators and mobility. A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al.! I can't define a robot, but I know one when I see one. Joseph Engelberger (pioneer in industrial robotics) 2
3 Example 1: Cleaning Robots Roomba MyWindoro 3
4 Example 2: PR2 PR2 is a robotics research and development platform that lets you innovate right out of the box. No more building hardware and software from scratch. 4
5 Example 3: Atlas Atlas is a high mobility, humanoid robot designed to operate outdoors, even on extremely rough terrain. 5
6 Perception of Robots! Survey from 2007! 240 Participants 6 What do people expect from robots?, C. Ray et al.
7 Stakeholder expectations! New appliance: The household robot! Users may have: Incorrect preconceptions No point of reference to understand the robot! Designers will have to either: Create very intuitive products, or Integrate training course A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al. 7
8 What is Security?! Security: Systems behave as intended even in the presence of an adversary! Safety: Systems behave as intended even in the presence of accidental failures 8
9 Network Security Goals! Confidentiality Encryption! Integrity MAC, Digital Signature! Availability Redundancy, more Bandwidth And More:! Authentication! Accountability! Non-repudiation! Privacy 9 Network Security, Bernhard Plattner
10 Secure Communication Channel! Confidential channel No eavesdropping possible on information sent! Authentic channel Sender is the one he claims to be and Content is original! Secure channel Authentic and confidential channel 10 Network Security, Bernhard Plattner
11 Attack Classification Passive attacks Active attacks Confidentiality Availability Integrity and Authenticity Compromise of content Traffic analysis Denial of service Modification Fabrication Replay 11 Classification due to Steve Kent, BBN Technologies
12 Timeline: Computers 1951 UNIVAC 1946 ENIAC 1944 Colossus 12 The Future of Household Robots, T. Denning
13 Timeline: Computers 1984 Apple Macintosh 1982 Commodore IBM PC 1977 Apple II 1974 Altair The Future of Household Robots, T. Denning
14 Timeline: Computers 14 The Future of Household Robots, T. Denning
15 Timeline: Computer Security Attacks Phone Phreaking 15 The Future of Household Robots, T. Denning
16 Timeline: Computer Security Attacks 1980s The 414s break into 60 Computer systems 16 The Future of Household Robots, T. Denning
17 Timeline: Computer Security Attacks 1986 The Brain Virus 17 The Future of Household Robots, T. Denning
18 Timeline: Computer Security Attacks 1988 Morris Worm 18 The Future of Household Robots, T. Denning
19 Timeline: Computer Security Attacks 2000s DDoS Attacks 19 The Future of Household Robots, T. Denning
20 Timeline: Computer Security Attacks! Rootkits! Trojan Horses! Botnets! Phishing! Keyloggers! Cross-Site Scripting! etc. 20 The Future of Household Robots, T. Denning
21 Timeline: Computer Security Attacks Observations:! The attack rate increases! The attacks lag behind the technology 21 The Future of Household Robots, T. Denning
22 Timeline: Robots 1979 Robotics Institute founded at Carnegie Mellon University 22 The Future of Household Robots, T. Denning
23 Timeline: Robots 1982 WABOT-2 accompanies people on a keyboard instrument 23 The Future of Household Robots, T. Denning
24 Timeline: Robots 1986 Honda founds Humanoid Robot Division 24 The Future of Household Robots, T. Denning
25 Timeline: Robots 1999 AIBO 25 The Future of Household Robots, T. Denning
26 Timeline: Robots 2000 ASIMO 26 The Future of Household Robots, T. Denning
27 Timeline: Robots 2001 Paro therapeutic seal 27 The Future of Household Robots, T. Denning
28 Timeline: Robots 2002 Roomba 28 The Future of Household Robots, T. Denning
29 Timeline: Robots 2005 Actroid Android 29 The Future of Household Robots, T. Denning
30 Timeline: Robots 2008 Okonomiyaki Robot 30 The Future of Household Robots, T. Denning
31 Timeline: Robots Observations:! No large-scale attacks on robot security yet Recall (computer security):! The attack rate increases! The attacks lag behind the technology 31 The Future of Household Robots, T. Denning
32 A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons 32
33 Rovio! For adults! Telepresence! Home surveillance! Check up on relatives! Follows pre-programmed IR beacons! Controlled via web interface 33
34 Spykee! Toy for children! Assembled and configured by children! Telepresence: Parent can tuck in kids when out of town! Spy robot! Controlled via program 34
35 Discovered Vulnerabilities 35
36 Remote Discovery A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al. 36
37 Eavesdropping Neighbor or Hacker in a car A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al. 37
38 Intercepting Credentials (MITM) Can intercept login credentials A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al. 38
39 Physical Takeover! With credentials: Drive the robot anywhere! Access the AV stream at any time 39
40 Possible Attacks! Robot vandalism Damage fragile object Knock object off of a table Damaging the robot itself (robot suicide)! Manipulate Objects Use mobility to locate (physical) key Take image of a key Pick up and hide key! Eldercare Robot used to trip an elder Play noises and speech to confuse elder A Spotlight on Security and Privacy Risks with Future Household Robots: Attacks and Lessons, T. Denning et al. 40
41 Mechatronic Security and Robot Authentication 41
42 Robot as Living Individuals! Born at some point Has non-clonable DNA Gets a birth certificate! Starts usual transactions with its environment Learning, developing its knowledge and capabilities! Gets old Has to be repaired, or dies 42 Mechatronic Security and Robot Authentication, W. Adi
43 Bio-Inspired Robot Identity! Biological mutation Permanent irremovable change! Electronic mutation! e-dna Simulated change Generate e-dna chain from e-mutation 43 Mechatronic Security and Robot Authentication, W. Adi
44 Detecting Cloning Attack! Cloning almost impossible Crack mutated identity Copy all robot transactions history! Detect Cloning Attack Two G units with same properties Each unit G generates new trace G' and G'' most likely different Both systems claim to be G Identification process will fail 44 Mechatronic Security and Robot Authentication, W. Adi
45 Mechatronic Security Goals! Robot is provable witness of event! Robot can prove having performed action! Robot cannot falsly claim to have performed action 45
46 Risks of Tomorrow 46
47 Risks of Tomorrow! Robots for elders Exoskeleton for mobility Lifting robot 47
48 Risks of Tomorrow! Robots for elders Exoskeleton for mobility Lifting robot! Robots for children As companions or as therapy for unique emotional needs 48
49 Risks of Tomorrow! Robots for elders Exoskeleton for mobility Lifting robot! Robots for children As companions or as therapy for unique emotional needs! Robots that use tools 49
50 Risks of Tomorrow! Robots for elders Exoskeleton for mobility Lifting robot! Robots for children As companions or as therapy for unique emotional needs! Robots that use tools! Robots with sophisticated A.I. 50
51 Are the Risks real? Potential types of attackers! Terrorists! Competitor! Acquaintance! ID Thief! Prankster! Governments 51
52 Conclusion! Spykee and Rovio robots are only toys Security not first priority Vulnerabilities not specific to robots Can be easily fixed! Future robots more complex Even developers don't understand reasons for behavior Difficult to detect an enemy's attack How to prevent the robot from leaking information?! Young area of research Lack of detailed studies Difficult to predict technology 52
53 Questions? 53
Quo vadis EU? Giorgio Mosca Director Strategy & Technologies. Bruxelles, 6 th December Company General Use
 Quo vadis EU? Giorgio Mosca Director Strategy & Technologies Bruxelles, 6 th December 2018 Leonardo is a global high-tech company and one of the key actors in Aerospace, Defence and Security worldwide
Quo vadis EU? Giorgio Mosca Director Strategy & Technologies Bruxelles, 6 th December 2018 Leonardo is a global high-tech company and one of the key actors in Aerospace, Defence and Security worldwide
Robots: Tools or Toys? Some Answers from Biorobotics, Developmental and Entertainment Robotics. AI and Robots. A History of Robots in AI
 Robots: Tools or Toys? Some Answers from Biorobotics, Developmental and Entertainment Robotics AI and Robots Outline: Verena V. Hafner May 24, 2005 Seminar Series on Artificial Intelligence, Luxembourg
Robots: Tools or Toys? Some Answers from Biorobotics, Developmental and Entertainment Robotics AI and Robots Outline: Verena V. Hafner May 24, 2005 Seminar Series on Artificial Intelligence, Luxembourg
Ethics and technology
 Professional accountants the future: Ethics and technology International Ethics Standards Board for Accountants (IESBA) 19 June 2018 Agenda ACCA Professional Insights (PI) and technology Technology impact
Professional accountants the future: Ethics and technology International Ethics Standards Board for Accountants (IESBA) 19 June 2018 Agenda ACCA Professional Insights (PI) and technology Technology impact
Dipartimento di Elettronica Informazione e Bioingegneria Robotics
 Dipartimento di Elettronica Informazione e Bioingegneria Robotics Behavioral robotics @ 2014 Behaviorism behave is what organisms do Behaviorism is built on this assumption, and its goal is to promote
Dipartimento di Elettronica Informazione e Bioingegneria Robotics Behavioral robotics @ 2014 Behaviorism behave is what organisms do Behaviorism is built on this assumption, and its goal is to promote
Revised and extended. Accompanies this course pages heavier Perception treated more thoroughly. 1 - Introduction
 Topics to be Covered Coordinate frames and representations. Use of homogeneous transformations in robotics. Specification of position and orientation Manipulator forward and inverse kinematics Mobile Robots:
Topics to be Covered Coordinate frames and representations. Use of homogeneous transformations in robotics. Specification of position and orientation Manipulator forward and inverse kinematics Mobile Robots:
Robotic Systems ECE 401RB Fall 2007
 The following notes are from: Robotic Systems ECE 401RB Fall 2007 Lecture 14: Cooperation among Multiple Robots Part 2 Chapter 12, George A. Bekey, Autonomous Robots: From Biological Inspiration to Implementation
The following notes are from: Robotic Systems ECE 401RB Fall 2007 Lecture 14: Cooperation among Multiple Robots Part 2 Chapter 12, George A. Bekey, Autonomous Robots: From Biological Inspiration to Implementation
Discussion Topics. How do we imagine will society change? What will be the drivers of change? What do we think will be the future needs of society?
 Looking Beyond 2010 Jack Smith National Research Council of Canada and the Telfer School of Management, University of Ottawa jesmith@telfer.uottawa.ca; Discussion Topics How do we imagine will society
Looking Beyond 2010 Jack Smith National Research Council of Canada and the Telfer School of Management, University of Ottawa jesmith@telfer.uottawa.ca; Discussion Topics How do we imagine will society
Artificial Intelligence: Definition
 Lecture Notes Artificial Intelligence: Definition Dae-Won Kim School of Computer Science & Engineering Chung-Ang University What are AI Systems? Deep Blue defeated the world chess champion Garry Kasparov
Lecture Notes Artificial Intelligence: Definition Dae-Won Kim School of Computer Science & Engineering Chung-Ang University What are AI Systems? Deep Blue defeated the world chess champion Garry Kasparov
An interdisciplinary collaboration of Theatre Arts and Social Robotics: The creation of empathy and embodiment in social robotics
 An interdisciplinary collaboration of Theatre Arts and Social Robotics: The creation of empathy and embodiment in social robotics Empathy: the ability to understand and share the feelings of another. Embodiment:
An interdisciplinary collaboration of Theatre Arts and Social Robotics: The creation of empathy and embodiment in social robotics Empathy: the ability to understand and share the feelings of another. Embodiment:
Advanced Manufacturing and Disruptive Technologies: Implications for Strategic Competitiveness
 Advanced Manufacturing and Disruptive Technologies: Implications for Strategic Competitiveness Dr. George Poste Chief Scientist, Complex Adaptive Systems Initiative and Del E. Webb Chair in Health Innovation
Advanced Manufacturing and Disruptive Technologies: Implications for Strategic Competitiveness Dr. George Poste Chief Scientist, Complex Adaptive Systems Initiative and Del E. Webb Chair in Health Innovation
Wombat Security s Beyond the Phish. Report. security technologies. #BeyondthePhish
 Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
Why (Special Agent) Johnny (Still) Can t Encrypt: A Security Analysis of the APCO Project 25 Two-Way Radio System
 Why (Special Agent) Johnny (Still) Can t Encrypt: A Security Analysis of the APCO Project 25 Two-Way Radio System Sandy Clark Travis Goodspeed Perry Metzger Zachary Wasserman Kevin Xu Matt Blaze Usenix
Why (Special Agent) Johnny (Still) Can t Encrypt: A Security Analysis of the APCO Project 25 Two-Way Radio System Sandy Clark Travis Goodspeed Perry Metzger Zachary Wasserman Kevin Xu Matt Blaze Usenix
Modern cartography often crosscuts issues of law and ethics, including:
 Legal and Ethical Issues Modern cartography often crosscuts issues of law and ethics, including: 1. Issues of legal liability 2. Accountability in government: The Freedom of Information Act and Open Records
Legal and Ethical Issues Modern cartography often crosscuts issues of law and ethics, including: 1. Issues of legal liability 2. Accountability in government: The Freedom of Information Act and Open Records
THE AI REVOLUTION. How Artificial Intelligence is Redefining Marketing Automation
 THE AI REVOLUTION How Artificial Intelligence is Redefining Marketing Automation The implications of Artificial Intelligence for modern day marketers The shift from Marketing Automation to Intelligent
THE AI REVOLUTION How Artificial Intelligence is Redefining Marketing Automation The implications of Artificial Intelligence for modern day marketers The shift from Marketing Automation to Intelligent
CYBER SECURITY GUIDELINES FOR COMPUTER BASED GAMING APPLICATIONS
 CYBER SECURITY GUIDELINES FOR COMPUTER BASED GAMING APPLICATIONS Document Control Version: 1.0 Author: CS Policies and Standards Section - MOTC Classification: Public Date of Issue: November 2016 Contents
CYBER SECURITY GUIDELINES FOR COMPUTER BASED GAMING APPLICATIONS Document Control Version: 1.0 Author: CS Policies and Standards Section - MOTC Classification: Public Date of Issue: November 2016 Contents
ENME 489L: Biologically Inspired Robotics
 ENME 489L: Biologically Inspired Robotics Satyandra K. Gupta and Arvind Ananthanarayanan Department of Mechanical Engineering and Institute for Systems Research University of Maryland Course Introduction
ENME 489L: Biologically Inspired Robotics Satyandra K. Gupta and Arvind Ananthanarayanan Department of Mechanical Engineering and Institute for Systems Research University of Maryland Course Introduction
Introduction. Major Malfunction. Security professional by day. White Hat hacker since the '70s. DEFCON Goon since DC5
 Introduction Major Malfunction Security professional by day White Hat hacker since the '70s DEFCON Goon since DC5 Co-founder of InterFACE internet pirate radio station Introduction Why Infra Red? Ubiquitous
Introduction Major Malfunction Security professional by day White Hat hacker since the '70s DEFCON Goon since DC5 Co-founder of InterFACE internet pirate radio station Introduction Why Infra Red? Ubiquitous
Authenticated Document Management System
 Authenticated Document Management System P. Anup Krishna Research Scholar at Bharathiar University, Coimbatore, Tamilnadu Dr. Sudheer Marar Head of Department, Faculty of Computer Applications, Nehru College
Authenticated Document Management System P. Anup Krishna Research Scholar at Bharathiar University, Coimbatore, Tamilnadu Dr. Sudheer Marar Head of Department, Faculty of Computer Applications, Nehru College
By Marek Perkowski ECE Seminar, Friday January 26, 2001
 By Marek Perkowski ECE Seminar, Friday January 26, 2001 Why people build Humanoid Robots? Challenge - it is difficult Money - Hollywood, Brooks Fame -?? Everybody? To build future gods - De Garis Forthcoming
By Marek Perkowski ECE Seminar, Friday January 26, 2001 Why people build Humanoid Robots? Challenge - it is difficult Money - Hollywood, Brooks Fame -?? Everybody? To build future gods - De Garis Forthcoming
Impacts and Risks Caused by AI Networking, and Future Challenges
 Impacts and Risks Caused by AI Networking, and Future Challenges (From Studies on AI Networking in Japan) November 17, 2016 Tatsuya KUROSAKA Project Assistant Professor at Keio University Graduate School
Impacts and Risks Caused by AI Networking, and Future Challenges (From Studies on AI Networking in Japan) November 17, 2016 Tatsuya KUROSAKA Project Assistant Professor at Keio University Graduate School
Chapter 10 Mobile Communication Systems
 Chapter 10 Mobile Communication Systems Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Cellular System Infrastructure Registration Handoff Parameters and Underlying
Chapter 10 Mobile Communication Systems Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Cellular System Infrastructure Registration Handoff Parameters and Underlying
Partner for Success Secure & Smart Future Home
 Partner for Success Secure & Smart Future Home Jiang Yanbing Director of Strategy and Market Development Dept. Infineon Technologies China Table of contents 1 About Infineon 2 Make Future Home Smart and
Partner for Success Secure & Smart Future Home Jiang Yanbing Director of Strategy and Market Development Dept. Infineon Technologies China Table of contents 1 About Infineon 2 Make Future Home Smart and
2013 IT Risk/Reward Barometer: Asia-Pacific Results. October Unless otherwise noted, n = 343
 2013 IT Risk/Reward Barometer: Asia-Pacific Results October 2013 www.isaca.org/risk-reward-barometer Unless otherwise noted, n = 343 Respondents are business and IT professionals from the Asia-Pacific
2013 IT Risk/Reward Barometer: Asia-Pacific Results October 2013 www.isaca.org/risk-reward-barometer Unless otherwise noted, n = 343 Respondents are business and IT professionals from the Asia-Pacific
Introduction. Major Malfunction. Security professional by day. White Hat hacker since the '70s. DEFCON Goon since DC5
 Introduction Major Malfunction Security professional by day White Hat hacker since the '70s DEFCON Goon since DC5 Co-founder of InterFACE internet pirate radio station Introduction Why Infra Red? Ubiquitous
Introduction Major Malfunction Security professional by day White Hat hacker since the '70s DEFCON Goon since DC5 Co-founder of InterFACE internet pirate radio station Introduction Why Infra Red? Ubiquitous
Ensuring the Safety of an Autonomous Robot in Interaction with Children
 Machine Learning in Robot Assisted Therapy Ensuring the Safety of an Autonomous Robot in Interaction with Children Challenges and Considerations Stefan Walke stefan.walke@tum.de SS 2018 Overview Physical
Machine Learning in Robot Assisted Therapy Ensuring the Safety of an Autonomous Robot in Interaction with Children Challenges and Considerations Stefan Walke stefan.walke@tum.de SS 2018 Overview Physical
Robotics Intelligent connection of the perception to action. Applications
 Robotics Intelligent connection of the perception to action Applications Applications Automotive industry Assembly Medical laboratories Medecine Nuclear energy Agriculture Spatial exploration Underwater
Robotics Intelligent connection of the perception to action Applications Applications Automotive industry Assembly Medical laboratories Medecine Nuclear energy Agriculture Spatial exploration Underwater
Essay on A Survey of Socially Interactive Robots Authors: Terrence Fong, Illah Nourbakhsh, Kerstin Dautenhahn Summarized by: Mehwish Alam
 1 Introduction Essay on A Survey of Socially Interactive Robots Authors: Terrence Fong, Illah Nourbakhsh, Kerstin Dautenhahn Summarized by: Mehwish Alam 1.1 Social Robots: Definition: Social robots are
1 Introduction Essay on A Survey of Socially Interactive Robots Authors: Terrence Fong, Illah Nourbakhsh, Kerstin Dautenhahn Summarized by: Mehwish Alam 1.1 Social Robots: Definition: Social robots are
Robust Key Establishment in Sensor Networks
 Robust Key Establishment in Sensor Networks Yongge Wang Abstract Secure communication guaranteeing reliability, authenticity, and privacy in sensor networks with active adversaries is a challenging research
Robust Key Establishment in Sensor Networks Yongge Wang Abstract Secure communication guaranteeing reliability, authenticity, and privacy in sensor networks with active adversaries is a challenging research
Visually Guided Errand Service for Home Robot
 ICRA 2007 Dec. 18, 2006 Visually Guided Errand Service for Home Robot Sukhan Lee Professor and Director Where I am from Current Status and Future Prospect on Service Robotics Operational industrial robots
ICRA 2007 Dec. 18, 2006 Visually Guided Errand Service for Home Robot Sukhan Lee Professor and Director Where I am from Current Status and Future Prospect on Service Robotics Operational industrial robots
U ROBOT March 12, 2008 Kyung Chul Shin Yujin Robot Co.
 U ROBOT March 12, 2008 Kyung Chul Shin Yujin Robot Co. Is the era of the robot around the corner? It is coming slowly albeit steadily hundred million 1600 1400 1200 1000 Public Service Educational Service
U ROBOT March 12, 2008 Kyung Chul Shin Yujin Robot Co. Is the era of the robot around the corner? It is coming slowly albeit steadily hundred million 1600 1400 1200 1000 Public Service Educational Service
Principles of Ad Hoc Networking
 Principles of Ad Hoc Networking Michel Barbeau and Evangelos Kranakis November 12, 2007 Wireless security challenges Network type Wireless Mobility Ad hoc Sensor Challenge Open medium Handover implies
Principles of Ad Hoc Networking Michel Barbeau and Evangelos Kranakis November 12, 2007 Wireless security challenges Network type Wireless Mobility Ad hoc Sensor Challenge Open medium Handover implies
Robo$cs Introduc$on. ROS Workshop. Faculty of Informa$on Technology, Brno University of Technology Bozetechova 2, Brno
 Robo$cs Introduc$on ROS Workshop Faculty of Informa$on Technology, Brno University of Technology Bozetechova 2, 612 66 Brno name@fit.vutbr.cz What is a Robot? a programmable, mul.func.on manipulator USA
Robo$cs Introduc$on ROS Workshop Faculty of Informa$on Technology, Brno University of Technology Bozetechova 2, 612 66 Brno name@fit.vutbr.cz What is a Robot? a programmable, mul.func.on manipulator USA
CAPACITIES FOR TECHNOLOGY TRANSFER
 CAPACITIES FOR TECHNOLOGY TRANSFER The Institut de Robòtica i Informàtica Industrial (IRI) is a Joint University Research Institute of the Spanish Council for Scientific Research (CSIC) and the Technical
CAPACITIES FOR TECHNOLOGY TRANSFER The Institut de Robòtica i Informàtica Industrial (IRI) is a Joint University Research Institute of the Spanish Council for Scientific Research (CSIC) and the Technical
Challenges to human dignity from developments in AI
 Challenges to human dignity from developments in AI Thomas G. Dietterich Distinguished Professor (Emeritus) Oregon State University Corvallis, OR USA Outline What is Artificial Intelligence? Near-Term
Challenges to human dignity from developments in AI Thomas G. Dietterich Distinguished Professor (Emeritus) Oregon State University Corvallis, OR USA Outline What is Artificial Intelligence? Near-Term
Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses
 Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses A CSE 713 Presentation Harish Shankar, Ranjan Mohan. Heads Up! Through this presentation, there will be
Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses A CSE 713 Presentation Harish Shankar, Ranjan Mohan. Heads Up! Through this presentation, there will be
ME7752: Mechanics and Control of Robots Lecture 1
 ME7752: Mechanics and Control of Robots Lecture 1 Instructor: Manoj Srinivasan Office: E340 Scott Laboratory Email: srinivasan.88@osu.edu ( PDF posted. In the PDF, if there are no links to videos, do a
ME7752: Mechanics and Control of Robots Lecture 1 Instructor: Manoj Srinivasan Office: E340 Scott Laboratory Email: srinivasan.88@osu.edu ( PDF posted. In the PDF, if there are no links to videos, do a
Robot: icub This humanoid helps us study the brain
 ProfileArticle Robot: icub This humanoid helps us study the brain For the complete profile with media resources, visit: http://education.nationalgeographic.org/news/robot-icub/ Program By Robohub Tuesday,
ProfileArticle Robot: icub This humanoid helps us study the brain For the complete profile with media resources, visit: http://education.nationalgeographic.org/news/robot-icub/ Program By Robohub Tuesday,
EE631 Cooperating Autonomous Mobile Robots. Lecture 1: Introduction. Prof. Yi Guo ECE Department
 EE631 Cooperating Autonomous Mobile Robots Lecture 1: Introduction Prof. Yi Guo ECE Department Plan Overview of Syllabus Introduction to Robotics Applications of Mobile Robots Ways of Operation Single
EE631 Cooperating Autonomous Mobile Robots Lecture 1: Introduction Prof. Yi Guo ECE Department Plan Overview of Syllabus Introduction to Robotics Applications of Mobile Robots Ways of Operation Single
Identity Management and its impact on the Digital Economy
 Identity Management and its impact on the Digital Economy Alejandro Barros 1, Alejandro Pareja 2 October 2016 Contents Introduction... 2 Identity Management... 3 Enrolment in the National Identity System...
Identity Management and its impact on the Digital Economy Alejandro Barros 1, Alejandro Pareja 2 October 2016 Contents Introduction... 2 Identity Management... 3 Enrolment in the National Identity System...
Accelerating innovations in science and technology (S&T) are having profound effects on global civilization These developments will have strategic
 World Future Society Meeting 24 July 2015 Dr. James Kadtke National Defense University and U.C. San Diego jkadtke@aol.com Accelerating innovations in science and technology (S&T) are having profound effects
World Future Society Meeting 24 July 2015 Dr. James Kadtke National Defense University and U.C. San Diego jkadtke@aol.com Accelerating innovations in science and technology (S&T) are having profound effects
What is Robotics. Robotics is the science that studies robots and the technology that builds them
 What is Robotics 02CFIC CY Robotics is the science that studies robots and the technology that builds them Robotics started its development during WWII (Manhattan project) Robots (seen as an artificial
What is Robotics 02CFIC CY Robotics is the science that studies robots and the technology that builds them Robotics started its development during WWII (Manhattan project) Robots (seen as an artificial
CSE 466 Software for Embedded Systems. What is an embedded system?
 CSE 466 Software for Embedded Systems The wrap up Recall the introduction what are embedded systems? What we covered in the course CSE 466 Wrap Up 1 What is an embedded system? Let s proceed inductively
CSE 466 Software for Embedded Systems The wrap up Recall the introduction what are embedded systems? What we covered in the course CSE 466 Wrap Up 1 What is an embedded system? Let s proceed inductively
ES 492: SCIENCE IN THE MOVIES
 UNIVERSITY OF SOUTH ALABAMA ES 492: SCIENCE IN THE MOVIES LECTURE 5: ROBOTICS AND AI PRESENTER: HANNAH BECTON TODAY'S AGENDA 1. Robotics and Real-Time Systems 2. Reacting to the environment around them
UNIVERSITY OF SOUTH ALABAMA ES 492: SCIENCE IN THE MOVIES LECTURE 5: ROBOTICS AND AI PRESENTER: HANNAH BECTON TODAY'S AGENDA 1. Robotics and Real-Time Systems 2. Reacting to the environment around them
Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration
 Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration Research Supervisor: Minoru Etoh (Professor, Open and Transdisciplinary Research Initiatives, Osaka University)
Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration Research Supervisor: Minoru Etoh (Professor, Open and Transdisciplinary Research Initiatives, Osaka University)
Industrial Robotics. Claudio Melchiorri. Dipartimento di Ingegneria dell Energia Elettrica e dell Informazione (DEI) Università di Bologna
 Industrial Robotics Claudio Melchiorri Dipartimento di Ingegneria dell Energia Elettrica e dell Informazione (DEI) Università di Bologna email: claudio.melchiorri@unibo.it C. Melchiorri (DEI) Industrial
Industrial Robotics Claudio Melchiorri Dipartimento di Ingegneria dell Energia Elettrica e dell Informazione (DEI) Università di Bologna email: claudio.melchiorri@unibo.it C. Melchiorri (DEI) Industrial
T H E N E X T I N T E R N E T
 THE NEXT INTERNET TODAY S MENU Net Neutrality The big break-up AI and the future of humanity BUT FIRST Tim Cook International Conference of Data Protection and Privacy Commisioners (Brussels) Data Industrial
THE NEXT INTERNET TODAY S MENU Net Neutrality The big break-up AI and the future of humanity BUT FIRST Tim Cook International Conference of Data Protection and Privacy Commisioners (Brussels) Data Industrial
Securing the IT Supply Chain in the Age of Globalization. An Interim Report
 Carnegie Mellon Securing the IT Supply Chain in the Age of Globalization An Interim Report James C. Hoe (representing CyLab and CSSI) Carnegie Mellon University November 28, 2007 Motivations for This Study
Carnegie Mellon Securing the IT Supply Chain in the Age of Globalization An Interim Report James C. Hoe (representing CyLab and CSSI) Carnegie Mellon University November 28, 2007 Motivations for This Study
Google vs. Local Competitors in Japan
 Google vs. Local Competitors in Japan Any chance for the local competitors to win the AI market? Editorial team, Weekly Toyo Keizai According to Sano Kyuuichirou, Director, Information Economy Division,
Google vs. Local Competitors in Japan Any chance for the local competitors to win the AI market? Editorial team, Weekly Toyo Keizai According to Sano Kyuuichirou, Director, Information Economy Division,
Building Perceptive Robots with INTEL Euclid Development kit
 Building Perceptive Robots with INTEL Euclid Development kit Amit Moran Perceptual Computing Systems Innovation 2 2 3 A modern robot should Perform a task Find its way in our world and move safely Understand
Building Perceptive Robots with INTEL Euclid Development kit Amit Moran Perceptual Computing Systems Innovation 2 2 3 A modern robot should Perform a task Find its way in our world and move safely Understand
TRACING THE EVOLUTION OF DESIGN
 TRACING THE EVOLUTION OF DESIGN Product Evolution PRODUCT-ECOSYSTEM A map of variables affecting one specific product PRODUCT-ECOSYSTEM EVOLUTION A map of variables affecting a systems of products 25 Years
TRACING THE EVOLUTION OF DESIGN Product Evolution PRODUCT-ECOSYSTEM A map of variables affecting one specific product PRODUCT-ECOSYSTEM EVOLUTION A map of variables affecting a systems of products 25 Years
Android (Child android)
 Social and ethical issue Why have I developed the android? Hiroshi ISHIGURO Department of Adaptive Machine Systems, Osaka University ATR Intelligent Robotics and Communications Laboratories JST ERATO Asada
Social and ethical issue Why have I developed the android? Hiroshi ISHIGURO Department of Adaptive Machine Systems, Osaka University ATR Intelligent Robotics and Communications Laboratories JST ERATO Asada
Unit 2: THE CRIME SCENE
 Unit 2: THE CRIME SCENE Oh, how simple it would all have been had I been here before they came like a herd of buffalo and wallowed all over it. A. Conan Doyle, in The Boscombe Valley Mystery, 1892 CORPUS
Unit 2: THE CRIME SCENE Oh, how simple it would all have been had I been here before they came like a herd of buffalo and wallowed all over it. A. Conan Doyle, in The Boscombe Valley Mystery, 1892 CORPUS
Required Course Numbers. Test Content Categories. Computer Science 8 12 Curriculum Crosswalk Page 2 of 14
 TExES Computer Science 8 12 Curriculum Crosswalk Test Content Categories Domain I Technology Applications Core Competency 001: The computer science teacher knows technology terminology and concepts; the
TExES Computer Science 8 12 Curriculum Crosswalk Test Content Categories Domain I Technology Applications Core Competency 001: The computer science teacher knows technology terminology and concepts; the
Child Check In Frequently Asked Questions
 Child Check In Frequently Asked Questions Does Child Check In print to label printers (like Dymo)? Does Child Check In also print badges for the workers? How are the badges worn? How are the badges reused?
Child Check In Frequently Asked Questions Does Child Check In print to label printers (like Dymo)? Does Child Check In also print badges for the workers? How are the badges worn? How are the badges reused?
Introduction to Robotics
 Introduction to Robotics Analysis, systems, Applications Saeed B. Niku Chapter 1 Fundamentals 1. Introduction Fig. 1.1 (a) A Kuhnezug truck-mounted crane Reprinted with permission from Kuhnezug Fordertechnik
Introduction to Robotics Analysis, systems, Applications Saeed B. Niku Chapter 1 Fundamentals 1. Introduction Fig. 1.1 (a) A Kuhnezug truck-mounted crane Reprinted with permission from Kuhnezug Fordertechnik
Biometrics - A Tool in Fraud Prevention
 Biometrics - A Tool in Fraud Prevention Agenda Authentication Biometrics : Need, Available Technologies, Working, Comparison Fingerprint Technology About Enrollment, Matching and Verification Key Concepts
Biometrics - A Tool in Fraud Prevention Agenda Authentication Biometrics : Need, Available Technologies, Working, Comparison Fingerprint Technology About Enrollment, Matching and Verification Key Concepts
Dr. Ashish Dutta. Professor, Dept. of Mechanical Engineering Indian Institute of Technology Kanpur, INDIA
 Introduction: History of Robotics - past, present and future Dr. Ashish Dutta Professor, Dept. of Mechanical Engineering Indian Institute of Technology Kanpur, INDIA Origin of Automation: replacing human
Introduction: History of Robotics - past, present and future Dr. Ashish Dutta Professor, Dept. of Mechanical Engineering Indian Institute of Technology Kanpur, INDIA Origin of Automation: replacing human
Proposal # xxxxxxxxxxxx. Intercept Jammer. Date:
 Proposal # xxxxxxxxxxxx Intercept Jammer Date: Presented From: HSS Development 75 S. Broadway White Plains, NY 060 Office: 94-304-4333 www.secintel.com New York Disclaimers: All descriptions of HSS products
Proposal # xxxxxxxxxxxx Intercept Jammer Date: Presented From: HSS Development 75 S. Broadway White Plains, NY 060 Office: 94-304-4333 www.secintel.com New York Disclaimers: All descriptions of HSS products
project gnosis tech ed development centre Teaching Kids since 2013
 . project gnosis tech ed development centre Teaching Kids since 2013 Innovative solutions for intelligent integration in a Global Market driven by technology. Think Big. Think Code. Think Tech. 1 Catalogue
. project gnosis tech ed development centre Teaching Kids since 2013 Innovative solutions for intelligent integration in a Global Market driven by technology. Think Big. Think Code. Think Tech. 1 Catalogue
What is AI? AI is the reproduction of human reasoning and intelligent behavior by computational methods. an attempt of. Intelligent behavior Computer
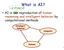 What is AI? an attempt of AI is the reproduction of human reasoning and intelligent behavior by computational methods Intelligent behavior Computer Humans 1 What is AI? (R&N) Discipline that systematizes
What is AI? an attempt of AI is the reproduction of human reasoning and intelligent behavior by computational methods Intelligent behavior Computer Humans 1 What is AI? (R&N) Discipline that systematizes
Lecture 23: Robotics. Instructor: Joelle Pineau Class web page: What is a robot?
 COMP 102: Computers and Computing Lecture 23: Robotics Instructor: (jpineau@cs.mcgill.ca) Class web page: www.cs.mcgill.ca/~jpineau/comp102 What is a robot? The word robot is popularized by the Czech playwright
COMP 102: Computers and Computing Lecture 23: Robotics Instructor: (jpineau@cs.mcgill.ca) Class web page: www.cs.mcgill.ca/~jpineau/comp102 What is a robot? The word robot is popularized by the Czech playwright
Appendix B: Example Research-Activity Description
 Appendix B: Example Research-Activity Description To qualify as a research activity, work must advance the understanding of scientific relations or technologies, address scientific or technological uncertainty,
Appendix B: Example Research-Activity Description To qualify as a research activity, work must advance the understanding of scientific relations or technologies, address scientific or technological uncertainty,
TRIESTE: A Trusted Radio Infrastructure for Enforcing SpecTrum Etiquettes
 TRIESTE: A Trusted Radio Infrastructure for Enforcing SpecTrum Etiquettes Wade Trappe Rutgers, The State University of New Jersey www.winlab.rutgers.edu 1 Talk Overview Motivation TRIESTE overview Spectrum
TRIESTE: A Trusted Radio Infrastructure for Enforcing SpecTrum Etiquettes Wade Trappe Rutgers, The State University of New Jersey www.winlab.rutgers.edu 1 Talk Overview Motivation TRIESTE overview Spectrum
2018 HSS Development
 Communications Intelligence - Mobile Collection - Situational Awareness - Tracking Identities Electronic Warfare - RF Jamming - Programmable Applications Prison Solutions - Managed Access - Denial of Service
Communications Intelligence - Mobile Collection - Situational Awareness - Tracking Identities Electronic Warfare - RF Jamming - Programmable Applications Prison Solutions - Managed Access - Denial of Service
ARTIFICIAL INTELLIGENCE - ROBOTICS
 ARTIFICIAL INTELLIGENCE - ROBOTICS http://www.tutorialspoint.com/artificial_intelligence/artificial_intelligence_robotics.htm Copyright tutorialspoint.com Robotics is a domain in artificial intelligence
ARTIFICIAL INTELLIGENCE - ROBOTICS http://www.tutorialspoint.com/artificial_intelligence/artificial_intelligence_robotics.htm Copyright tutorialspoint.com Robotics is a domain in artificial intelligence
Contents. Mental Commit Robot (Mental Calming Robot) Industrial Robots. In What Way are These Robots Intelligent. Video: Mental Commit Robots
 Human Robot Interaction for Psychological Enrichment Dr. Takanori Shibata Senior Research Scientist Intelligent Systems Institute National Institute of Advanced Industrial Science and Technology (AIST)
Human Robot Interaction for Psychological Enrichment Dr. Takanori Shibata Senior Research Scientist Intelligent Systems Institute National Institute of Advanced Industrial Science and Technology (AIST)
Human Authentication from Brain EEG Signals using Machine Learning
 Volume 118 No. 24 2018 ISSN: 1314-3395 (on-line version) url: http://www.acadpubl.eu/hub/ http://www.acadpubl.eu/hub/ Human Authentication from Brain EEG Signals using Machine Learning Urmila Kalshetti,
Volume 118 No. 24 2018 ISSN: 1314-3395 (on-line version) url: http://www.acadpubl.eu/hub/ http://www.acadpubl.eu/hub/ Human Authentication from Brain EEG Signals using Machine Learning Urmila Kalshetti,
Stanford Blockchain Protocol Analysis and Security Engineering 2018 Introduction & Overview
 Stanford Blockchain Protocol Analysis and Security Engineering 2018 Introduction & Overview Byron Gibson https://cyber.stanford.edu/bpase18 1 of 5 Contents Contents 2 I. Introduction & Overview 3 What
Stanford Blockchain Protocol Analysis and Security Engineering 2018 Introduction & Overview Byron Gibson https://cyber.stanford.edu/bpase18 1 of 5 Contents Contents 2 I. Introduction & Overview 3 What
Digital Transformation. A Game Changer. How Does the Digital Transformation Affect Informatics as a Scientific Discipline?
 Digital Transformation A Game Changer How Does the Digital Transformation Affect Informatics as a Scientific Discipline? Manfred Broy Technische Universität München Institut for Informatics ... the change
Digital Transformation A Game Changer How Does the Digital Transformation Affect Informatics as a Scientific Discipline? Manfred Broy Technische Universität München Institut for Informatics ... the change
What is a robot. Robots (seen as artificial beings) appeared in books and movies long before real applications. Basilio Bona ROBOTICS 01PEEQW
 ROBOTICS 01PEEQW An Introduction Basilio Bona DAUIN Politecnico di Torino What is a robot According to the Robot Institute of America (1979) a robot is: A reprogrammable, multifunctional manipulator designed
ROBOTICS 01PEEQW An Introduction Basilio Bona DAUIN Politecnico di Torino What is a robot According to the Robot Institute of America (1979) a robot is: A reprogrammable, multifunctional manipulator designed
This Privacy Policy describes the types of personal information SF Express Co., Ltd. and
 Effective Date: 2017/05/10 Updated date: 2017/05/25 This Privacy Policy describes the types of personal information SF Express Co., Ltd. and its affiliates (collectively as "SF") collect about consumers
Effective Date: 2017/05/10 Updated date: 2017/05/25 This Privacy Policy describes the types of personal information SF Express Co., Ltd. and its affiliates (collectively as "SF") collect about consumers
CORC 3303 Exploring Robotics. Why Teams?
 Exploring Robotics Lecture F Robot Teams Topics: 1) Teamwork and Its Challenges 2) Coordination, Communication and Control 3) RoboCup Why Teams? It takes two (or more) Such as cooperative transportation:
Exploring Robotics Lecture F Robot Teams Topics: 1) Teamwork and Its Challenges 2) Coordination, Communication and Control 3) RoboCup Why Teams? It takes two (or more) Such as cooperative transportation:
Making Identity Use Predictable. UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016
 Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
AIMICT.ORG AIMICT Newsletter
 SEPTEMBER 2018 AIMICT.ORG 1 IN THIS ISSUE AIMICT Conducts ISO 9001 Lead Auditor Course AIMICT Conducts ILM s Training of Trainers Program in Irbid AIMICT Organizes Professional Quality Manager Program
SEPTEMBER 2018 AIMICT.ORG 1 IN THIS ISSUE AIMICT Conducts ISO 9001 Lead Auditor Course AIMICT Conducts ILM s Training of Trainers Program in Irbid AIMICT Organizes Professional Quality Manager Program
An Overview of Biometrics. Dr. Charles C. Tappert Seidenberg School of CSIS, Pace University
 An Overview of Biometrics Dr. Charles C. Tappert Seidenberg School of CSIS, Pace University What are Biometrics? Biometrics refers to identification of humans by their characteristics or traits Physical
An Overview of Biometrics Dr. Charles C. Tappert Seidenberg School of CSIS, Pace University What are Biometrics? Biometrics refers to identification of humans by their characteristics or traits Physical
Software Security. Encryption. Encryption. Encryption. Encryption. Encryption. Week 5 Part 1. Masking Data from Unwelcome eyes
 Software Security Encryption Week 5 Part 1 Masking Data from Unwelcome eyes Encryption Encryption Encryption is the process of transforming data into another form Designed to make it readable only by those
Software Security Encryption Week 5 Part 1 Masking Data from Unwelcome eyes Encryption Encryption Encryption is the process of transforming data into another form Designed to make it readable only by those
Section 1 -The Pennsylvania Lottery funded Shared Ride Program for people 65 and older
 This application is for LANtaVan special transportation programs Section 1 -The Pennsylvania Lottery funded Shared Ride Program for people 65 and older Section 2 - The Pennsylvania Department of Public
This application is for LANtaVan special transportation programs Section 1 -The Pennsylvania Lottery funded Shared Ride Program for people 65 and older Section 2 - The Pennsylvania Department of Public
S&T Stakeholders Conference
 S&T Stakeholders Conference The Way Ahead: Bodies Dr. Sharla Rausch Division Director uman Factors Division Science and Technology Directorate June 2-5, 2008 PARTNERING FOR A SAFER NATION uman Factors
S&T Stakeholders Conference The Way Ahead: Bodies Dr. Sharla Rausch Division Director uman Factors Division Science and Technology Directorate June 2-5, 2008 PARTNERING FOR A SAFER NATION uman Factors
RoboCup. Presented by Shane Murphy April 24, 2003
 RoboCup Presented by Shane Murphy April 24, 2003 RoboCup: : Today and Tomorrow What we have learned Authors Minoru Asada (Osaka University, Japan), Hiroaki Kitano (Sony CS Labs, Japan), Itsuki Noda (Electrotechnical(
RoboCup Presented by Shane Murphy April 24, 2003 RoboCup: : Today and Tomorrow What we have learned Authors Minoru Asada (Osaka University, Japan), Hiroaki Kitano (Sony CS Labs, Japan), Itsuki Noda (Electrotechnical(
ROBOTICS 01PEEQW. Basilio Bona DAUIN Politecnico di Torino
 ROBOTICS 01PEEQW Basilio Bona DAUIN Politecnico di Torino What is Robotics? Robotics is the study and design of robots Robots can be used in different contexts and are classified as 1. Industrial robots
ROBOTICS 01PEEQW Basilio Bona DAUIN Politecnico di Torino What is Robotics? Robotics is the study and design of robots Robots can be used in different contexts and are classified as 1. Industrial robots
Study Guide Chapters 3 & 4 Forensic Science Name
 Chapter 3 Body of the Crime 1. Corpus Delicti means. Money 2. Top 3 reasons for committing a crime. Revenge Emotion-love,hate, anger. Body 3. 3 sources of evidence: Primary or secondary crime scene Suspects
Chapter 3 Body of the Crime 1. Corpus Delicti means. Money 2. Top 3 reasons for committing a crime. Revenge Emotion-love,hate, anger. Body 3. 3 sources of evidence: Primary or secondary crime scene Suspects
Welcome to EGN-1935: Electrical & Computer Engineering (Ad)Ventures
 : ECE (Ad)Ventures Welcome to -: Electrical & Computer Engineering (Ad)Ventures This is the first Educational Technology Class in UF s ECE Department We are Dr. Schwartz and Dr. Arroyo. University of Florida,
: ECE (Ad)Ventures Welcome to -: Electrical & Computer Engineering (Ad)Ventures This is the first Educational Technology Class in UF s ECE Department We are Dr. Schwartz and Dr. Arroyo. University of Florida,
Always stay in touch with your home!
 Always stay in touch with your home! 01 Meet Cockpit Fulfill your dream of a functional intelligent home Can you imagine life without smartphones, tablets or any other portable device that facilitate your
Always stay in touch with your home! 01 Meet Cockpit Fulfill your dream of a functional intelligent home Can you imagine life without smartphones, tablets or any other portable device that facilitate your
Simplified Electrified
 Looks right. Feels right. Works right. Simplified Electrified Simplicity is the ultimate sophistication. - Leonardo da Vinci Mechatronics Mechatronics solutions provider for design and manufacturing of
Looks right. Feels right. Works right. Simplified Electrified Simplicity is the ultimate sophistication. - Leonardo da Vinci Mechatronics Mechatronics solutions provider for design and manufacturing of
Children and Social Robots: An integrative framework
 Children and Social Robots: An integrative framework Jochen Peter Amsterdam School of Communication Research University of Amsterdam (Funded by ERC Grant 682733, CHILDROBOT) Prague, November 2016 Prague,
Children and Social Robots: An integrative framework Jochen Peter Amsterdam School of Communication Research University of Amsterdam (Funded by ERC Grant 682733, CHILDROBOT) Prague, November 2016 Prague,
Automotive Radar Sensors and Congested Radio Spectrum: An Urban Electronic Battlefield?
 Automotive Radar Sensors and Congested Radio Spectrum: An Urban Electronic Battlefield? By Sefa Tanis Share on As automotive radars become more widespread, the heavily occupied RF spectrum will resemble
Automotive Radar Sensors and Congested Radio Spectrum: An Urban Electronic Battlefield? By Sefa Tanis Share on As automotive radars become more widespread, the heavily occupied RF spectrum will resemble
New Age Vital Statistics Services: What They Do and Don t Do
 New Age Vital Statistics Services: What They Do and Don t Do Author: Guy Huntington, President, Huntington Ventures Ltd. Date: June 2018 Table of Contents Executive Summary...3 What is a New Age Digital
New Age Vital Statistics Services: What They Do and Don t Do Author: Guy Huntington, President, Huntington Ventures Ltd. Date: June 2018 Table of Contents Executive Summary...3 What is a New Age Digital
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase. Term Paper Sample Topics
 A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
Robotics in Oil and Gas. Matt Ondler President / CEO
 Robotics in Oil and Gas Matt Ondler President / CEO 1 Agenda Quick background on HMI State of robotics Sampling of robotics projects in O&G Example of a transformative robotic application Future of robotics
Robotics in Oil and Gas Matt Ondler President / CEO 1 Agenda Quick background on HMI State of robotics Sampling of robotics projects in O&G Example of a transformative robotic application Future of robotics
Slides that go with the book
 Autonomous Mobile Robots, Chapter Autonomous Mobile Robots, Chapter Autonomous Mobile Robots The three key questions in Mobile Robotics Where am I? Where am I going? How do I get there?? Slides that go
Autonomous Mobile Robots, Chapter Autonomous Mobile Robots, Chapter Autonomous Mobile Robots The three key questions in Mobile Robotics Where am I? Where am I going? How do I get there?? Slides that go
The 2 nd Annual Career Development Stakeholders Conference. The Fourth Industrial The future of work 28 June 2018
 The 2 nd Annual Career Development Stakeholders Conference The Fourth Industrial The future of work 28 June 2018 Mechanization, Steam power, weaving loom Mass production, assembly line, electrical energy
The 2 nd Annual Career Development Stakeholders Conference The Fourth Industrial The future of work 28 June 2018 Mechanization, Steam power, weaving loom Mass production, assembly line, electrical energy
ITGS Areas of Impact Revision. By Panagiotis Kafkarkou
 ITGS Areas of Impact Revision By Panagiotis Kafkarkou Areas of Impact 1. Business and Employment 2. Education 3. Health 4. Arts, Entertainment, and Leisure 5. Science and the Environment 6. Politics and
ITGS Areas of Impact Revision By Panagiotis Kafkarkou Areas of Impact 1. Business and Employment 2. Education 3. Health 4. Arts, Entertainment, and Leisure 5. Science and the Environment 6. Politics and
Teleoperated Robot Controlling Interface: an Internet of Things Based Approach
 Proc. 1 st International Conference on Machine Learning and Data Engineering (icmlde2017) 20-22 Nov 2017, Sydney, Australia ISBN: 978-0-6480147-3-7 Teleoperated Robot Controlling Interface: an Internet
Proc. 1 st International Conference on Machine Learning and Data Engineering (icmlde2017) 20-22 Nov 2017, Sydney, Australia ISBN: 978-0-6480147-3-7 Teleoperated Robot Controlling Interface: an Internet
Robot: Geminoid F This android robot looks just like a woman
 ProfileArticle Robot: Geminoid F This android robot looks just like a woman For the complete profile with media resources, visit: http://education.nationalgeographic.org/news/robot-geminoid-f/ Program
ProfileArticle Robot: Geminoid F This android robot looks just like a woman For the complete profile with media resources, visit: http://education.nationalgeographic.org/news/robot-geminoid-f/ Program
KIT to showcase self-learning humanoid robot at CEBIT
 KIT to showcase self-learning humanoid robot at CEBIT Test Center for Autonomous Driving Uncrackable Digital Wallet Cloud Service Certification Virtual Health Assistant Quantum-based Prediction of Molecular
KIT to showcase self-learning humanoid robot at CEBIT Test Center for Autonomous Driving Uncrackable Digital Wallet Cloud Service Certification Virtual Health Assistant Quantum-based Prediction of Molecular
Presented by: Michael Jackson Chairman Shaping Tomorrow. March
 1 Presented by: Michael Jackson Chairman Shaping Tomorrow March 2014 2 2 Scan Evaluate Filter Act Synthesize Strategize Forecast 3 4 Demographics Nutrition Education Personalization Networked World Globalization
1 Presented by: Michael Jackson Chairman Shaping Tomorrow March 2014 2 2 Scan Evaluate Filter Act Synthesize Strategize Forecast 3 4 Demographics Nutrition Education Personalization Networked World Globalization
AUTONOMOUS MAN-OVERBOARD DETECTION AND TRACKING
 AUTONOMOUS MAN-OVERBOARD DETECTION AND TRACKING THE SYSTEM AUTONOMOUS MAN-OVERBOARD DETECTION & TRACKING The MOBtronic man-overboard system operates autonomously, instantly detecting and classifying a
AUTONOMOUS MAN-OVERBOARD DETECTION AND TRACKING THE SYSTEM AUTONOMOUS MAN-OVERBOARD DETECTION & TRACKING The MOBtronic man-overboard system operates autonomously, instantly detecting and classifying a
Internet of Things: Hell or Paradise?
 Internet of Things: Hell or Paradise? Executive Summary of the 2016 Conference of the Nexa Center for Internet & Society Publication date: 10/01/2017 Authors: Marco Ricolfi, Antonio Vetrò, Francesco Ruggiero
Internet of Things: Hell or Paradise? Executive Summary of the 2016 Conference of the Nexa Center for Internet & Society Publication date: 10/01/2017 Authors: Marco Ricolfi, Antonio Vetrò, Francesco Ruggiero
Situational Awareness Architectural Patterns
 Situational Awareness Architectural Patterns Mike Gagliardi, Bill Wood, Len Bass SEI Manuel Beltran Boeing 11/4/2011 1 Motivation Software Patterns are the codification of common problems within a domain
Situational Awareness Architectural Patterns Mike Gagliardi, Bill Wood, Len Bass SEI Manuel Beltran Boeing 11/4/2011 1 Motivation Software Patterns are the codification of common problems within a domain
