Securing the IT Supply Chain in the Age of Globalization. An Interim Report
|
|
|
- Lester Lester
- 5 years ago
- Views:
Transcription
1 Carnegie Mellon Securing the IT Supply Chain in the Age of Globalization An Interim Report James C. Hoe (representing CyLab and CSSI) Carnegie Mellon University November 28, 2007
2 Motivations for This Study Outsourcing of design and manufacturing of IT systems and components Potentials for deliberate tampering to degrade security or reliability What are the implications for the US government s IT infrastructure? What measures has the IT industry taken to mitigate the downsides? What more should the IT industry do in the future? Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 2
3 To put it concretely Does it make a difference to the US government that the same ThinkPads were badged as IBM one day and Lenovo the next? Does it make a difference (security wise) to the US government that an IT product is US or foreign made? Does it make a difference to the US government if all IT manufacturing capabilities were overseas? Doesn t the rest of the world have the same concerns about their reliance on US IT products? Doesn t the average consumer also want assurances in security and reliability? (see answers at the end) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 3
4 CyLab/ISA Industry Study Input (from Industry and Government) workshops of industry, government and academicians (2 IS Alliance Workshops, 1 NSF Workshop) industry questionnaires and interviews regular phone conferences with ISA steering committee Output (from CMU) cataloging of current and anticipated threats in design and manufacturing tampering cataloging of current industry best practices in safe guarding against tampering recommendations for further actions (policies, practices and research) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 4
5 Outline Introduction Review of the 1st IS Alliance workshop My current thinking on this topic Wrap up Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 5
6 1 st ISA Workshop Agenda The government s perspective Annabelle Lee, DHS Director of Security Standards and Best Practices and cochair of the US Government Inter Agency Task Force on Securing the IT Supply Chain The industry s perspective Industry Panel (A. Szakal, IBM; J. Carlisle, Lenovo and D. Doughty, Intel) An economist s perspective Scott Borg, Chief Economist US Cyber Consequences Unit A software engineer s perspective Bill Scherlis, CMU A hardware designer s perspective James C. Hoe, CMU Where research is needed Academic Panel Breakout groups Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 6
7 Government s perspectives Annabelle Lee, DHS An issue for all parts of the system no matter where the companies are located or where the products are developed increase adversary s cost reduce the US government s risk of exposure decrease the payoff of a successful attack Defense in breadth protect all phases of the lifecycle (design spec decommission) many phases are owned/controlled by the private sector Inter Agency Supply Chain Risk Management Working Groups Acquisition Process; Education and Training; IT Assurance; and Standards, Guidelines and Best Practices Cyber security impacts physical security (power grid, air traffic...) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 7
8 David Doughty, Intel Industry s Perspective there is no perfect security; what is enough security to deter attempts (cost vs. effectiveness) more than the CPUs are susceptible (from chipsets to the network) Andras Szakal, IBM greater threats on the software side current practices are good (100% assurance not the goal) need practicable framework for establishing trust between supplier and consumer (and still test some more for yourself) Jeff Carlisle, Lenovo global supply chain is a reality facing every company industry as a whole needs to proactively head off any problems (real or perceived) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 8
9 Economist s Perspective Scott Borg, US Cyber Consequences Unit Analyze supply chain attacks as specific combinations of attackers: { criminal gangs, disgrunttled (ex)employees, rogue corporations, ideological militants, nation states } attacks: { interrupt, corrupt, discredit, control } an operation motives: { gain financially, divert value, manipulate financial instruments, make credible a coercive threat, advertise a cause, stop an opposing activity, reduce the opposer s ability to attack/defend } Almost all attack scenarios are unlikely due to lowerhanging fruit alternatives, except... Most probable threat (by cost effectiveness analysis) nation states x {*} x reduce the ability to attack/defend malicious firmware Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 9
10 Software Engineer s Perspective Bill Scherlis, CMU Provenance and trust are important when we lack the technology to analyze the artifact itself (e.g., source code) More than processes, we need tools, analysis and techniques to improve observability in order to make acceptance evaluation possible Trust the tools to do more formal methods and verification have come a long way Don t lump defect types different attributes need different technologies Security, dependability and quality issues go hand in hand Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 10
11 Hardware Designer s Perspective James C. Hoe, CMU High end ICs (CPUs) are relatively safe from tampering cost, technology and man power involved are very high too many low hanging fruits (insider, software/firmware attacks) for comparable ends Low end ICs carry much greater threats creatable by a small entity with no accountability a $2 NIC or disk controller has as much access as the CPU low margin market leaves little headroom for care Tampering testing is not a part of the established HW flow need to extend/adapt design for test (DFT) to tamper detection very hard to find dormant behaviors with specific triggers R&D needed to catch up essentially from scratch Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 11
12 Breakout Groups 1 and 2 Where are the most likely points of attack? SW and firmware are much more vulnerable than HW behaviors that can remain dormant until specifically triggered insider attacks will always remain a great concern What are existing best practices and certifications? How to do risk analysis? no consensus on the cost effectiveness of the lifecycle model? does quality assurance suffice as security assurance? can we develop run time protection against anomalies? BTW, both groups found these two questions impossible to answer except for fixed contexts (no one size fits all) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 12
13 Breakout Group 3 What are the risk calculations from the government s perspective? how can we trust the supply chain when we know the source countries are spying on us? is there a difference between US and foreign corporations anymore? Can we fashion an educational agenda for decision makers industry needs to be prepared to respond by educating the correct issues solving the correct issues advocating the correct issues Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 13
14 To put this study in context... Carnegie Mellon
15 Seagate/Maxtor News November 12, Reuters China virus found in Seagate drives in Taiwan: external disc drives sold in Taiwan had been infected with a virus which reportedly sent users' information to China Investigation Bureau officials said their investigation suggested infection may have occurred when the devices were in the hands of Chinese sub contractors during the manufacturing process xdny.q24lc92i2d1qidzdaf Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 15
16 The sky is falling? From Seagate s website ( en us / support/downloads/personal_storage/ps3200 sw) Seagate has traced this issue to a small number of units produced by a Maxtor sub contract manufacturer located in China. According to Kaspersky the virus is the Virus.Win32.AutoRun.ah, a molar virus that searches for passwords to online games and sends them to a server located in China. All of the known games affected are Chinese with the exception of World of Warcraft. My prognosis: accidental, operator error lesson: don t web surf on the manufacturing floor computer this is not unique: ipods had a similar episode in 2006 Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 16
17 The sky is falling? But, before we get too comfortable, this could also be a test the water precursor to something much more sinister? Unlikely in this case, since it is just too crude of an attempt to be useful even as an experiment Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 17
18 The sky is falling? The incident does prove, deliberate or not, it is possible for an artifact of tampering to get through quality assurance With humans in the loop, you don t need high tech If it is an operator error, it can happen anywhere in the world Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 18
19 The sky is falling? No serious IT department would fall for this CMU/ECE IT reformats each new PC and reinstalls from an inhouse disk image presumably this is also standard practice with government agencies and major corporations But does anyone reload firmware? Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 19
20 What about the consumers? The sky is falling? Are you vigilant/paranoid enough to reinstall your next brand new home PC after you unpack it? How about your iphone? Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 20
21 To Wrap up The need to secure the IT supply chain is real, and it is not just a government problem The problem is encompassing and amorphous policies and best practices are only road blocks to anticipated problems The overall framework of solutions cannot be rigid attackers are creative and fluid operator errors simply defy imagination The solutions have to be practicable from both supply side and demand side One cannot have perfect security, but there is no substitute for due diligence. Raise the lowest hanging fruit. Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 21
22 Some Answers Does it make a difference to the US government that ThinkPads were badged as IBM one day and Lenovo the next? No difference, provided there is an objective way to prove that the ThinkPads from Lenovo really is the same as IBM s. Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 22
23 Some Answers Does it make a difference (security wise) to the US government that an IT product is US or foreign made? No difference. A good security assessment should rely very little on assumptions based on the country of origin. Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 23
24 Some Answers Does it make a difference to the US government if all IT manufacturing capabilities were overseas? Yes. There are definite supply risks if this became a reality, and Moore s Law voids an IT equivalent of the Strategic Petroleum Reserve Need to ensure a diverse source of supplies Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 24
25 Some Answers Doesn t the rest of the world have the same concerns about their reliance on US IT products? Yes. For example, the Chinese Academy of Sciences has developed a commercially viable home grown CPU (Loongson, ST Micro Part Number STLS2E02) Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 25
26 Some Answers Doesn t the average consumer also want assurances in security and reliability? Yes. I do. Secure Manufacturing in the Age of Globalization Workshop, 2007 J. C. Hoe 26
Policy Perspective: The Current and Proposed Security Framework
 Policy Perspective: The Current and Proposed Security Framework Ms. Kristen Baldwin, DASD(SE) August 16, 2016 05/10/16 Page-1 Outline Design as critical method to addressing trust/assurance We have a new
Policy Perspective: The Current and Proposed Security Framework Ms. Kristen Baldwin, DASD(SE) August 16, 2016 05/10/16 Page-1 Outline Design as critical method to addressing trust/assurance We have a new
TRUSTED STATE-OF-THE-ART FOUNDRY ACCESS
 TRUSTED STATE-OF-THE-ART FOUNDRY ACCESS Impact Analysis, Assessment, and Strategy Report OCTOBER 2018 B POTOMAC INSTITUTE FOR POLICY STUDIES G POTOMAC INSTITUTE FOR POLICY STUDIES Trusted State-of-the-Art
TRUSTED STATE-OF-THE-ART FOUNDRY ACCESS Impact Analysis, Assessment, and Strategy Report OCTOBER 2018 B POTOMAC INSTITUTE FOR POLICY STUDIES G POTOMAC INSTITUTE FOR POLICY STUDIES Trusted State-of-the-Art
DARPA TRUST in IC s Effort. Dr. Dean Collins Deputy Director, MTO 7 March 2007
 DARPA TRUST in IC s Effort Dr. Dean Collins Deputy Director, MTO 7 March 27 Report Documentation Page Form Approved OMB No. 74-88 Public reporting burden for the collection of information is estimated
DARPA TRUST in IC s Effort Dr. Dean Collins Deputy Director, MTO 7 March 27 Report Documentation Page Form Approved OMB No. 74-88 Public reporting burden for the collection of information is estimated
SPICE: IS A CAPABILITY MATURITY MODEL APPLICABLE IN THE CONSTRUCTION INDUSTRY? Spice: A mature model
 SPICE: IS A CAPABILITY MATURITY MODEL APPLICABLE IN THE CONSTRUCTION INDUSTRY? Spice: A mature model M. SARSHAR, M. FINNEMORE, R.HAIGH, J.GOULDING Department of Surveying, University of Salford, Salford,
SPICE: IS A CAPABILITY MATURITY MODEL APPLICABLE IN THE CONSTRUCTION INDUSTRY? Spice: A mature model M. SARSHAR, M. FINNEMORE, R.HAIGH, J.GOULDING Department of Surveying, University of Salford, Salford,
Violent Intent Modeling System
 for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
Software-Intensive Systems Producibility
 Pittsburgh, PA 15213-3890 Software-Intensive Systems Producibility Grady Campbell Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University SSTC 2006. - page 1 Producibility
Pittsburgh, PA 15213-3890 Software-Intensive Systems Producibility Grady Campbell Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University SSTC 2006. - page 1 Producibility
Solutions to selected exercises
 1 Software Engineering 8 th edition Solutions to selected exercises These solutions are made available for instructional purposes only. They may only be distributed to students and it is a condition of
1 Software Engineering 8 th edition Solutions to selected exercises These solutions are made available for instructional purposes only. They may only be distributed to students and it is a condition of
Trusted Microelectronic Investment Strategy
 Trusted Microelectronic Investment Strategy Dr. Jeremy Muldavin, DASD(SE) August 16, 2016 08/16/16 Page-1 Outline State of advanced microelectronics for DoD applications Strategy to assure access for the
Trusted Microelectronic Investment Strategy Dr. Jeremy Muldavin, DASD(SE) August 16, 2016 08/16/16 Page-1 Outline State of advanced microelectronics for DoD applications Strategy to assure access for the
CHINA STRONG PROMOTION OF SEMICONDUCTOR INDUSTRY PROACTIVE APPROACH WITH POWER DEVICES
 1 CHINA STRONG PROMOTION OF SEMICONDUCTOR INDUSTRY PROACTIVE APPROACH WITH POWER DEVICES Technology Studies Dept. II, Mitsui Global Strategic Studies Institute Noriyasu Ninagawa INTRODUCTION PROMOTING
1 CHINA STRONG PROMOTION OF SEMICONDUCTOR INDUSTRY PROACTIVE APPROACH WITH POWER DEVICES Technology Studies Dept. II, Mitsui Global Strategic Studies Institute Noriyasu Ninagawa INTRODUCTION PROMOTING
Science and Technology for Naval Warfare,
 Science and Technology for Naval Warfare, 2015--2020 Mark Lister Chairman, NRAC NDIA Disruptive Technologies Conference September 4, 2007 Excerpted from the Final Briefing Outline Terms of Reference Panel
Science and Technology for Naval Warfare, 2015--2020 Mark Lister Chairman, NRAC NDIA Disruptive Technologies Conference September 4, 2007 Excerpted from the Final Briefing Outline Terms of Reference Panel
Statement of Work (SOW) inemi Environmentally Sustainable Electronics TIG Value Recovery from End-of-Life Electronics
 Version # 1.0 Date: February 18, 2016 Statement of Work (SOW) inemi Environmentally Sustainable Electronics TIG Value Recovery from End-of-Life Electronics Project Co-Chair: Wayne Rifer Green Electronics
Version # 1.0 Date: February 18, 2016 Statement of Work (SOW) inemi Environmentally Sustainable Electronics TIG Value Recovery from End-of-Life Electronics Project Co-Chair: Wayne Rifer Green Electronics
Challenges and Opportunities in the Changing Science & Technology Landscape
 Challenges and Opportunities in the Changing Science & Technology Landscape (Capability Gap Changing Surprises Avoidance and Exploitation) Dr. Don Wyma Director for Scientific & Technical Intelligence
Challenges and Opportunities in the Changing Science & Technology Landscape (Capability Gap Changing Surprises Avoidance and Exploitation) Dr. Don Wyma Director for Scientific & Technical Intelligence
ROI of Dependability Activities
 ROI of Dependability Activities Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 June 29, 2008 (Contractors) Don t understand dependability They don t understand how to evaluate
ROI of Dependability Activities Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 June 29, 2008 (Contractors) Don t understand dependability They don t understand how to evaluate
Long-Term Strategy for DoD Trusted and Assured Microelectronics Needs
 Long-Term Strategy for DoD Trusted and Assured Microelectronics Needs Jeremy Muldavin Office of the Deputy Assistant Secretary of Defense for Systems Engineering 19th Annual NDIA Systems Engineering Conference
Long-Term Strategy for DoD Trusted and Assured Microelectronics Needs Jeremy Muldavin Office of the Deputy Assistant Secretary of Defense for Systems Engineering 19th Annual NDIA Systems Engineering Conference
Digital Engineering Support to Mission Engineering
 21 st Annual National Defense Industrial Association Systems and Mission Engineering Conference Digital Engineering Support to Mission Engineering Philomena Zimmerman Dr. Judith Dahmann Office of the Under
21 st Annual National Defense Industrial Association Systems and Mission Engineering Conference Digital Engineering Support to Mission Engineering Philomena Zimmerman Dr. Judith Dahmann Office of the Under
The Blockchain Ethical Design Framework
 The Blockchain Ethical Design Framework September 19, 2018 Dr. Cara LaPointe Senior Fellow Georgetown University Beeck Center for Social Impact + Innovation The Blockchain Ethical Design Framework Driving
The Blockchain Ethical Design Framework September 19, 2018 Dr. Cara LaPointe Senior Fellow Georgetown University Beeck Center for Social Impact + Innovation The Blockchain Ethical Design Framework Driving
Nuclear Safety and Security Culture Roles and Responsibilities of Individuals. Middle East Scientific Institute for Security (MESIS)
 Nuclear Safety and Security Culture Roles and Responsibilities of Individuals 8 th Annual RMCC Workshop Middle East Scientific Institute for Security (MESIS) Amman, Jordan June 17-19, 2013 Dr. J. David
Nuclear Safety and Security Culture Roles and Responsibilities of Individuals 8 th Annual RMCC Workshop Middle East Scientific Institute for Security (MESIS) Amman, Jordan June 17-19, 2013 Dr. J. David
Four Conference Breakout Sessions
 Four Conference Breakout Sessions Day 1 Wednesday, September 7 th : 1. Standards, Metrics, Models for SwA - Crystal 2 Led by Mr. Ken Hong Fong, OUSD (AT&L) 2. Industry Best Practices for SwA Crystal 3
Four Conference Breakout Sessions Day 1 Wednesday, September 7 th : 1. Standards, Metrics, Models for SwA - Crystal 2 Led by Mr. Ken Hong Fong, OUSD (AT&L) 2. Industry Best Practices for SwA Crystal 3
Toward Objective Global Privacy Standards. Ari Schwartz Senior Internet Policy Advisor
 Toward Objective Global Privacy Standards Ari Schwartz Senior Internet Policy Advisor Summary Technical standards offer a new ability to support the important public policy goal of better protecting privacy.
Toward Objective Global Privacy Standards Ari Schwartz Senior Internet Policy Advisor Summary Technical standards offer a new ability to support the important public policy goal of better protecting privacy.
Advances in AI and Security between 2016 and What You Need to Know
 Advances in AI and Security between 2016 and 2019---What You Need to Know Course Description July 31, 2017 100 MARYLAND AVENUE, NE SUITE 510 WASHINGTON, DC 20002 2 Executive Short Course Overview The Institute
Advances in AI and Security between 2016 and 2019---What You Need to Know Course Description July 31, 2017 100 MARYLAND AVENUE, NE SUITE 510 WASHINGTON, DC 20002 2 Executive Short Course Overview The Institute
Assessing and Integrating Emerging Technologies
 Assessing and Integrating Emerging Technologies TENICA s 2018 Enterprise Innovation Symposium Georgia Tech Global Learning Center Wednesday, May 2, 2018 Richard Domikis Chief Engineer Intelligence & Cyber
Assessing and Integrating Emerging Technologies TENICA s 2018 Enterprise Innovation Symposium Georgia Tech Global Learning Center Wednesday, May 2, 2018 Richard Domikis Chief Engineer Intelligence & Cyber
System of Systems Software Assurance
 System of Systems Software Assurance Introduction Under DoD sponsorship, the Software Engineering Institute has initiated a research project on system of systems (SoS) software assurance. The project s
System of Systems Software Assurance Introduction Under DoD sponsorship, the Software Engineering Institute has initiated a research project on system of systems (SoS) software assurance. The project s
ibeacon Spoofing Security and Privacy Implications of ibeacon Technology Karan Singhal
 ibeacon Spoofing Security and Privacy Implications of ibeacon Technology Karan Singhal ABSTRACT Apple introduced ibeacons with ios 7, revolutionizing the way our phones interact with real- life places
ibeacon Spoofing Security and Privacy Implications of ibeacon Technology Karan Singhal ABSTRACT Apple introduced ibeacons with ios 7, revolutionizing the way our phones interact with real- life places
Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the
 Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the U. S. Senate Committee on Commerce, Science, and Transportation Subcommittee
Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the U. S. Senate Committee on Commerce, Science, and Transportation Subcommittee
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT. 15 May :00-21:00
 DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
A Hybrid Risk Management Process for Interconnected Infrastructures
 A Hybrid Management Process for Interconnected Infrastructures Stefan Schauer Workshop on Novel Approaches in and Security Management for Critical Infrastructures Vienna, 19.09.2017 Contents Motivation
A Hybrid Management Process for Interconnected Infrastructures Stefan Schauer Workshop on Novel Approaches in and Security Management for Critical Infrastructures Vienna, 19.09.2017 Contents Motivation
Applied Safety Science and Engineering Techniques (ASSET TM )
 Applied Safety Science and Engineering Techniques (ASSET TM ) The Evolution of Hazard Based Safety Engineering into the Framework of a Safety Management Process Applied Safety Science and Engineering Techniques
Applied Safety Science and Engineering Techniques (ASSET TM ) The Evolution of Hazard Based Safety Engineering into the Framework of a Safety Management Process Applied Safety Science and Engineering Techniques
Stanford Center for AI Safety
 Stanford Center for AI Safety Clark Barrett, David L. Dill, Mykel J. Kochenderfer, Dorsa Sadigh 1 Introduction Software-based systems play important roles in many areas of modern life, including manufacturing,
Stanford Center for AI Safety Clark Barrett, David L. Dill, Mykel J. Kochenderfer, Dorsa Sadigh 1 Introduction Software-based systems play important roles in many areas of modern life, including manufacturing,
ULS Systems Research Roadmap
 ULS Systems Research Roadmap Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 2008 Carnegie Mellon University Roadmap Intent Help evaluate the ULS systems relevance of existing
ULS Systems Research Roadmap Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 2008 Carnegie Mellon University Roadmap Intent Help evaluate the ULS systems relevance of existing
The Role of Public Procurement in Low-carbon Innovation in Infrastructure
 ROUND TABLE ON SUSTAINABLE DEVELOPMENT The Role of Public Procurement in Low-carbon Innovation in Infrastructure Summary of the Round Table on Sustainable Development 1 held at OECD Headquarters, Paris,
ROUND TABLE ON SUSTAINABLE DEVELOPMENT The Role of Public Procurement in Low-carbon Innovation in Infrastructure Summary of the Round Table on Sustainable Development 1 held at OECD Headquarters, Paris,
Domestic Robots. a case study on security in ubiquitous computing. Thomas Knell Ubiquitous Computing Seminar
 Domestic Robots a case study on security in ubiquitous computing Thomas Knell Ubiquitous Computing Seminar 15.4.2014 Defining Robot There exists no universally accepted definition of a robot! Any automatically
Domestic Robots a case study on security in ubiquitous computing Thomas Knell Ubiquitous Computing Seminar 15.4.2014 Defining Robot There exists no universally accepted definition of a robot! Any automatically
DEFENSE ACQUISITION UNIVERSITY EMPLOYEE SELF-ASSESSMENT. Outcomes and Enablers
 Outcomes and Enablers 1 From an engineering leadership perspective, the student will describe elements of DoD systems engineering policy and process across the Defense acquisition life-cycle in accordance
Outcomes and Enablers 1 From an engineering leadership perspective, the student will describe elements of DoD systems engineering policy and process across the Defense acquisition life-cycle in accordance
TRUST in Integrated Circuits Program
 TRUST in Integrated Circuits Program Briefing to Industry Mr. Brian Sharkey i_sw Corp 26 March 2007 Agenda 0800-0815 0815 Introductions and Agenda 0815-0900 0900 Technical Objectives of the TRUST Program
TRUST in Integrated Circuits Program Briefing to Industry Mr. Brian Sharkey i_sw Corp 26 March 2007 Agenda 0800-0815 0815 Introductions and Agenda 0815-0900 0900 Technical Objectives of the TRUST Program
DoD Engineering and Better Buying Power 3.0
 DoD Engineering and Better Buying Power 3.0 Mr. Stephen P. Welby Deputy Assistant Secretary of Defense for Systems Engineering NDIA Systems Engineering Division Annual Strategic Planning Meeting December
DoD Engineering and Better Buying Power 3.0 Mr. Stephen P. Welby Deputy Assistant Secretary of Defense for Systems Engineering NDIA Systems Engineering Division Annual Strategic Planning Meeting December
DHS-DOD Software Assurance Forum, McLean VA 6 Oct 2008 Very loosely based on Daniel s 2007 briefing
 DHS-DOD Software Assurance Forum, McLean VA 6 Oct 2008 Very loosely based on Daniel s 2007 briefing Software For Dependable Systems: Sufficient Evidence? John Rushby Computer Science Laboratory SRI International
DHS-DOD Software Assurance Forum, McLean VA 6 Oct 2008 Very loosely based on Daniel s 2007 briefing Software For Dependable Systems: Sufficient Evidence? John Rushby Computer Science Laboratory SRI International
ADDENDUM 1. Changes Related to the Bachelor of Science in Intelligence Degree:
 ADDENDUM 1 CE UNIVERSITY 2017 2018 CATALOG ADDENDUM 1 National Intelligence University (NIU) produced this Catalog Addendum to supplement the NIU Catalog and Defense Intelligence Agency publications. You
ADDENDUM 1 CE UNIVERSITY 2017 2018 CATALOG ADDENDUM 1 National Intelligence University (NIU) produced this Catalog Addendum to supplement the NIU Catalog and Defense Intelligence Agency publications. You
Science Impact Enhancing the Use of USGS Science
 United States Geological Survey. 2002. "Science Impact Enhancing the Use of USGS Science." Unpublished paper, 4 April. Posted to the Science, Environment, and Development Group web site, 19 March 2004
United States Geological Survey. 2002. "Science Impact Enhancing the Use of USGS Science." Unpublished paper, 4 April. Posted to the Science, Environment, and Development Group web site, 19 March 2004
Academic Year
 2017-2018 Academic Year Note: The research questions and topics listed below are offered for consideration by faculty and students. If you have other ideas for possible research, the Academic Alliance
2017-2018 Academic Year Note: The research questions and topics listed below are offered for consideration by faculty and students. If you have other ideas for possible research, the Academic Alliance
ROGUEWOLF. SmartCities: Anticipating Agents of Change. Adam Amos-Binks Colleen Stacy Lucia Titus Kathleen Vogel Lori Wachter.
 ROGUEWOLF SmartCities: Anticipating Agents of Change Adam Amos-Binks Colleen Stacy Lucia Titus Kathleen Vogel Lori Wachter November 2, 2016 Outline Motivation: SmartCities + Anticipatory thinking Approach
ROGUEWOLF SmartCities: Anticipating Agents of Change Adam Amos-Binks Colleen Stacy Lucia Titus Kathleen Vogel Lori Wachter November 2, 2016 Outline Motivation: SmartCities + Anticipatory thinking Approach
Communication and participation:
 Communication and participation: Why, how, when, and with whom in a SNF/HLW transportation system to address social and economic impacts By Seth Tuler This presentation was supported by a grant from the
Communication and participation: Why, how, when, and with whom in a SNF/HLW transportation system to address social and economic impacts By Seth Tuler This presentation was supported by a grant from the
TRL Corollaries for Practice-Based Technologies
 Pittsburgh, PA 15213-3890 TRL Corollaries for Practice-Based Technologies Caroline Graettinger SuZ Garcia Jack Ferguson Sponsored by the U.S. Department of Defense 2003 by Carnegie Mellon University Version
Pittsburgh, PA 15213-3890 TRL Corollaries for Practice-Based Technologies Caroline Graettinger SuZ Garcia Jack Ferguson Sponsored by the U.S. Department of Defense 2003 by Carnegie Mellon University Version
Wombat Security s Beyond the Phish. Report. security technologies. #BeyondthePhish
 Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
A Knowledge-Centric Approach for Complex Systems. Chris R. Powell 1/29/2015
 A Knowledge-Centric Approach for Complex Systems Chris R. Powell 1/29/2015 Dr. Chris R. Powell, MBA 31 years experience in systems, hardware, and software engineering 17 years in commercial development
A Knowledge-Centric Approach for Complex Systems Chris R. Powell 1/29/2015 Dr. Chris R. Powell, MBA 31 years experience in systems, hardware, and software engineering 17 years in commercial development
Autonomy Test & Evaluation Verification & Validation (ATEVV) Challenge Area
 Autonomy Test & Evaluation Verification & Validation (ATEVV) Challenge Area Stuart Young, ARL ATEVV Tri-Chair i NDIA National Test & Evaluation Conference 3 March 2016 Outline ATEVV Perspective on Autonomy
Autonomy Test & Evaluation Verification & Validation (ATEVV) Challenge Area Stuart Young, ARL ATEVV Tri-Chair i NDIA National Test & Evaluation Conference 3 March 2016 Outline ATEVV Perspective on Autonomy
Evaluation of Competing Threat Modeling Methodologies
 Evaluation of Competing Threat Modeling Methodologies Dr. Forrest Shull Team: Nancy Mead, Kelwyn Pender, & Sam Weber (SEI) Jane Cleland-Huang, Janine Spears, & Stefan Hiebl (DePaul) Tadayoshi Kohno (University
Evaluation of Competing Threat Modeling Methodologies Dr. Forrest Shull Team: Nancy Mead, Kelwyn Pender, & Sam Weber (SEI) Jane Cleland-Huang, Janine Spears, & Stefan Hiebl (DePaul) Tadayoshi Kohno (University
Introduction. CELIA ROMM University of Wollongong. FAY SUDWEEKS University of Sydney
 CHAPTER 1 Introduction CELIA ROMM University of Wollongong FAY SUDWEEKS University of Sydney The emergence of electronic commerce as a distinct area in business is seen by many researchers and executives
CHAPTER 1 Introduction CELIA ROMM University of Wollongong FAY SUDWEEKS University of Sydney The emergence of electronic commerce as a distinct area in business is seen by many researchers and executives
Event Summary: Merit-Based and Competitive Awarding of Federal IT Services: Public Policy and Department of Defense Cloud Computing
 Hudson Institute Event Summary: Merit-Based and Competitive Awarding of Federal IT Services: Public Policy and Department of Defense Cloud Computing Participants: William Schneider, moderator, Senior Fellow,
Hudson Institute Event Summary: Merit-Based and Competitive Awarding of Federal IT Services: Public Policy and Department of Defense Cloud Computing Participants: William Schneider, moderator, Senior Fellow,
UNCLASSIFIED. R-1 ITEM NOMENCLATURE PE S: Microelectronics Technology Development and Support (DMEA) FY 2013 OCO
 Exhibit R-2, RDT&E Budget Item Justification: PB 2013 Defense Logistics Agency DATE: February 2012 COST ($ in Millions) FY 2011 FY 2012 Base OCO Total FY 2014 FY 2015 FY 2016 FY 2017 Defense Logistics
Exhibit R-2, RDT&E Budget Item Justification: PB 2013 Defense Logistics Agency DATE: February 2012 COST ($ in Millions) FY 2011 FY 2012 Base OCO Total FY 2014 FY 2015 FY 2016 FY 2017 Defense Logistics
DoD Electronics Priorities
 DoD Electronics Priorities Kristen Baldwin Acting Deputy Assistant Secretary of Defense for Systems Engineering Kickoff Meeting Arlington, VA January 18, 2018 Jan 18, 2018 Page-1 Elements of a Strategy
DoD Electronics Priorities Kristen Baldwin Acting Deputy Assistant Secretary of Defense for Systems Engineering Kickoff Meeting Arlington, VA January 18, 2018 Jan 18, 2018 Page-1 Elements of a Strategy
Engineering Autonomy
 Engineering Autonomy Mr. Robert Gold Director, Engineering Enterprise Office of the Deputy Assistant Secretary of Defense for Systems Engineering 20th Annual NDIA Systems Engineering Conference Springfield,
Engineering Autonomy Mr. Robert Gold Director, Engineering Enterprise Office of the Deputy Assistant Secretary of Defense for Systems Engineering 20th Annual NDIA Systems Engineering Conference Springfield,
Buenos Aires Action Plan
 STUDY GROUP 2 QUESTION 4/2 Assistance to developing countries 1 for implementing conformance and interoperability programmes and combating counterfeit information and communication technology equipment
STUDY GROUP 2 QUESTION 4/2 Assistance to developing countries 1 for implementing conformance and interoperability programmes and combating counterfeit information and communication technology equipment
Scenario Development Process
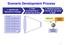 Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Digital Transformation in Thailand: Policy and Institutional Reform
 Digital Transformation in Thailand: Policy and Institutional Reform Kasititorn Pooparadai, Ph.D. presented at Development Implications of Digital Economies (DIODE): Policy and Practice Workshop Oxford
Digital Transformation in Thailand: Policy and Institutional Reform Kasititorn Pooparadai, Ph.D. presented at Development Implications of Digital Economies (DIODE): Policy and Practice Workshop Oxford
A Semiconductor Manufacturers Perspective on Obsolescence and Counterfeiting
 A Semiconductor Manufacturers Perspective on Obsolescence and Counterfeiting Peter Marston Business Development and Technical Consultant IIOM Conference June 2015 Topics Semiconductor Manufacturing - Historical
A Semiconductor Manufacturers Perspective on Obsolescence and Counterfeiting Peter Marston Business Development and Technical Consultant IIOM Conference June 2015 Topics Semiconductor Manufacturing - Historical
Judith A. O'Brien Director, Keystone Energy Program and Strategic Partnerships
 Judith A. O'Brien Director, Keystone Energy Program and Strategic Partnerships 1730 Rhode Island Ave, NW Ste 509 Washington, DC, 20036 202.452.1592 jobrien@keystone.org Judy has been a facilitator and
Judith A. O'Brien Director, Keystone Energy Program and Strategic Partnerships 1730 Rhode Island Ave, NW Ste 509 Washington, DC, 20036 202.452.1592 jobrien@keystone.org Judy has been a facilitator and
Frequently Asked Questions for the Pathway to Chartership
 Frequently Asked Questions for the Pathway to Chartership Index Answers for everyone... 2 What is the pathway?... 2 How does the pathway work?... 2 How do I register... 3 What is a Mentor... 3 Does my
Frequently Asked Questions for the Pathway to Chartership Index Answers for everyone... 2 What is the pathway?... 2 How does the pathway work?... 2 How do I register... 3 What is a Mentor... 3 Does my
How do you teach AI the value of trust?
 How do you teach AI the value of trust? AI is different from traditional IT systems and brings with it a new set of opportunities and risks. To build trust in AI organizations will need to go beyond monitoring
How do you teach AI the value of trust? AI is different from traditional IT systems and brings with it a new set of opportunities and risks. To build trust in AI organizations will need to go beyond monitoring
Training that is standardized and supports the effective operations of NIIMS.
 HISTORY OF THE INCIDENT COMMAND SYSTEM In the early 1970's, Southern California experienced several devastating wildland fires. The overall cost and loss associated with these fires totaled $18 million
HISTORY OF THE INCIDENT COMMAND SYSTEM In the early 1970's, Southern California experienced several devastating wildland fires. The overall cost and loss associated with these fires totaled $18 million
The Future is Now: Are you ready? Brian David
 The Future is Now: Are you ready? Brian David Johnson @BDJFuturist Age 13 Who am I? Age 13 Who am I? Who am I? Nerd! Age 13 In the next 10 years 2020 and Beyond Desktops Laptops Large Tablets Smartphone
The Future is Now: Are you ready? Brian David Johnson @BDJFuturist Age 13 Who am I? Age 13 Who am I? Who am I? Nerd! Age 13 In the next 10 years 2020 and Beyond Desktops Laptops Large Tablets Smartphone
Graffiti Management Strategy Update
 Page 1 of 5 Background On November 22, 2017, Council approved Graffiti Management Strategy (PW17078/ PED17198). Staff brought forward six recommendations; two additional recommendations were added by committee.
Page 1 of 5 Background On November 22, 2017, Council approved Graffiti Management Strategy (PW17078/ PED17198). Staff brought forward six recommendations; two additional recommendations were added by committee.
Making Identity Use Predictable. UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016
 Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Defining Makers Making: Emergent Practice and Emergent Meanings
 Paper ID #6852 Defining Makers Making: Emergent Practice and Emergent Meanings Dr. Micah Lande, Arizona State University Dr. Micah Lande is an assistant professor in the Department of Engineering in the
Paper ID #6852 Defining Makers Making: Emergent Practice and Emergent Meanings Dr. Micah Lande, Arizona State University Dr. Micah Lande is an assistant professor in the Department of Engineering in the
DEPUIS project: Design of Environmentallyfriendly Products Using Information Standards
 DEPUIS project: Design of Environmentallyfriendly Products Using Information Standards Anna Amato 1, Anna Moreno 2 and Norman Swindells 3 1 ENEA, Italy, anna.amato@casaccia.enea.it 2 ENEA, Italy, anna.moreno@casaccia.enea.it
DEPUIS project: Design of Environmentallyfriendly Products Using Information Standards Anna Amato 1, Anna Moreno 2 and Norman Swindells 3 1 ENEA, Italy, anna.amato@casaccia.enea.it 2 ENEA, Italy, anna.moreno@casaccia.enea.it
Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain
 This fiche is part of the wider roadmap for cross-cutting KETs activities Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain Cross-cutting
This fiche is part of the wider roadmap for cross-cutting KETs activities Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain Cross-cutting
The Strategy of Promoting Born - Global and High- Growth SMEs
 2014/SMEWG39/011 Agenda Item: 11.1.3 The Strategy of Promoting Born - Global and High- Growth SMEs Purpose: Information Submitted by: Chinese Taipei 39 th Small and Medium Enterprises Working Group Meeting
2014/SMEWG39/011 Agenda Item: 11.1.3 The Strategy of Promoting Born - Global and High- Growth SMEs Purpose: Information Submitted by: Chinese Taipei 39 th Small and Medium Enterprises Working Group Meeting
Your degree program, institution and (expected) graduation date: PhD in Public Policy, Harvard University, June 2009 (awarded)
 Final Progress Report Sustainability Science Program September 1, 2008 August 31, 2009 Name: Kira Matus Date: July 15, 2009 Field(s): Public Policy Your degree program, institution and (expected) graduation
Final Progress Report Sustainability Science Program September 1, 2008 August 31, 2009 Name: Kira Matus Date: July 15, 2009 Field(s): Public Policy Your degree program, institution and (expected) graduation
China s High-tech Exports: Myth and Reality
 GRIPS Discussion Paper 11-05 China s High-tech Exports: Myth and Reality By Yuqing Xing June 2011 National Graduate Institute for Policy Studies 7-22-1 Roppongi, Minato-ku, Tokyo, Japan 106-8677 China
GRIPS Discussion Paper 11-05 China s High-tech Exports: Myth and Reality By Yuqing Xing June 2011 National Graduate Institute for Policy Studies 7-22-1 Roppongi, Minato-ku, Tokyo, Japan 106-8677 China
Expression Of Interest
 Expression Of Interest Modelling Complex Warfighting Strategic Research Investment Joint & Operations Analysis Division, DST Points of Contact: Management and Administration: Annette McLeod and Ansonne
Expression Of Interest Modelling Complex Warfighting Strategic Research Investment Joint & Operations Analysis Division, DST Points of Contact: Management and Administration: Annette McLeod and Ansonne
POLICY BRIEF. Defense innovation requires strong leadership coupled with a framework of
 STUDY OF INNOVATION AND TECHNOLOGY IN CHINA POLICY BRIEF 2014-2 January 2014 Assessing High-Risk, High-Benefit Research Organizations: The DARPA Effect Maggie MARCUM Defense innovation requires strong
STUDY OF INNOVATION AND TECHNOLOGY IN CHINA POLICY BRIEF 2014-2 January 2014 Assessing High-Risk, High-Benefit Research Organizations: The DARPA Effect Maggie MARCUM Defense innovation requires strong
APSEC President s Report
 2015/EWG49/008 Agenda Item: 5a APSEC President s Report Purpose: Information Submitted by: APSEC 49 th Energy Working Group Meeting Gyeongju, Korea 22 26 June 2015 Report on APEC Sustainable Energy Center
2015/EWG49/008 Agenda Item: 5a APSEC President s Report Purpose: Information Submitted by: APSEC 49 th Energy Working Group Meeting Gyeongju, Korea 22 26 June 2015 Report on APEC Sustainable Energy Center
Sypris Solutions, Inc. Conflict Minerals Report For the Period Ending December 31, 2013
 Sypris Solutions, Inc. Conflict Minerals Report For the Period Ending December 31, 2013 Introduction This Conflict Minerals Report (Report) of Sypris Solutions, Inc. (Sypris, Company or we) for the year
Sypris Solutions, Inc. Conflict Minerals Report For the Period Ending December 31, 2013 Introduction This Conflict Minerals Report (Report) of Sypris Solutions, Inc. (Sypris, Company or we) for the year
Standards and privacy engineering ISO, OASIS, PRIPARE and Other Important Developments
 Standards and privacy engineering ISO, OASIS, PRIPARE and Other Important Developments Antonio Kung, CTO 25 rue du Général Foy, 75008 Paris www.trialog.com 9 May 2017 1 Introduction Speaker Engineering
Standards and privacy engineering ISO, OASIS, PRIPARE and Other Important Developments Antonio Kung, CTO 25 rue du Général Foy, 75008 Paris www.trialog.com 9 May 2017 1 Introduction Speaker Engineering
Dr. Cynthia Dion-Schwartz Acting Associate Director, SW and Embedded Systems, Defense Research and Engineering (DDR&E)
 Software-Intensive Systems Producibility Initiative Dr. Cynthia Dion-Schwartz Acting Associate Director, SW and Embedded Systems, Defense Research and Engineering (DDR&E) Dr. Richard Turner Stevens Institute
Software-Intensive Systems Producibility Initiative Dr. Cynthia Dion-Schwartz Acting Associate Director, SW and Embedded Systems, Defense Research and Engineering (DDR&E) Dr. Richard Turner Stevens Institute
A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE
 A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE Expert 1A Dan GROSU Executive Agency for Higher Education and Research Funding Abstract The paper presents issues related to a systemic
A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE Expert 1A Dan GROSU Executive Agency for Higher Education and Research Funding Abstract The paper presents issues related to a systemic
This version has been archived. Find the current version at on the Current Documents page. Scientific Working Groups on.
 Scientific Working Groups on Digital Evidence and Imaging Technology SWGDE/SWGIT Guidelines & Recommendations for Training in Digital & Multimedia Evidence Disclaimer: As a condition to the use of this
Scientific Working Groups on Digital Evidence and Imaging Technology SWGDE/SWGIT Guidelines & Recommendations for Training in Digital & Multimedia Evidence Disclaimer: As a condition to the use of this
Interoperable systems that are trusted and secure
 Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Integrated Reporting WG
 Integrated Reporting WG Merran Kelsall, IAASB Member and Integrated Reporting Working Group Chair IAASB Meeting March 16, 2016 Page 1 Public Interest Keep the International Standards fit for purpose in
Integrated Reporting WG Merran Kelsall, IAASB Member and Integrated Reporting Working Group Chair IAASB Meeting March 16, 2016 Page 1 Public Interest Keep the International Standards fit for purpose in
Autonomous Robotic (Cyber) Weapons?
 Autonomous Robotic (Cyber) Weapons? Giovanni Sartor EUI - European University Institute of Florence CIRSFID - Faculty of law, University of Bologna Rome, November 24, 2013 G. Sartor (EUI-CIRSFID) Autonomous
Autonomous Robotic (Cyber) Weapons? Giovanni Sartor EUI - European University Institute of Florence CIRSFID - Faculty of law, University of Bologna Rome, November 24, 2013 G. Sartor (EUI-CIRSFID) Autonomous
Frameworks for Assessing IT Systems Engineering Acquisition Issues and Proposed Approaches in Support of Public Law 111
 Frameworks for Assessing IT Systems Engineering Acquisition Issues and Proposed Approaches in Support of Public Law 111 15 th Annual Systems Engineering Conference Net Centric Operations/Interoperability
Frameworks for Assessing IT Systems Engineering Acquisition Issues and Proposed Approaches in Support of Public Law 111 15 th Annual Systems Engineering Conference Net Centric Operations/Interoperability
2017 Report from St. Vincent & the Grenadines. Cultural Diversity 2005 Convention
 1 2017 Report from St. Vincent & the Grenadines Cultural Diversity 2005 Convention Prepared by Anthony Theobalds Chief Cultural Officer -SVG February 2017 2 EXECUTIVE SUMMARY This report is an outcome
1 2017 Report from St. Vincent & the Grenadines Cultural Diversity 2005 Convention Prepared by Anthony Theobalds Chief Cultural Officer -SVG February 2017 2 EXECUTIVE SUMMARY This report is an outcome
TECHNICAL TRAINING ON ENERGY PLANNING LONG-RANGE ENERGY ALTERNATIVES PLANNING SYSTEM (LEAP) AND OTHER CONTEMPORARY PLANNING APPROACHES
 TECHNICAL TRAINING ON ENERGY PLANNING LONG-RANGE ENERGY ALTERNATIVES PLANNING SYSTEM (LEAP) AND OTHER CONTEMPORARY PLANNING APPROACHES September 29 - October 3, 2014 Kigali, Rwanda 8:00-9:30 Participant
TECHNICAL TRAINING ON ENERGY PLANNING LONG-RANGE ENERGY ALTERNATIVES PLANNING SYSTEM (LEAP) AND OTHER CONTEMPORARY PLANNING APPROACHES September 29 - October 3, 2014 Kigali, Rwanda 8:00-9:30 Participant
July 12, Subject: DFARS Case 2012-D055 Definitions. Dear Ms. Murphy:
 July 12, 2013 Defense Acquisition Regulations System Attn: Ms. Meredith Murphy OUSD (AT&L) DPAP/DARS Room 3B855 3060 Defense Pentagon Washington, DC 20301 3060 Subject: DFARS Case 2012-D055 Definitions
July 12, 2013 Defense Acquisition Regulations System Attn: Ms. Meredith Murphy OUSD (AT&L) DPAP/DARS Room 3B855 3060 Defense Pentagon Washington, DC 20301 3060 Subject: DFARS Case 2012-D055 Definitions
Interagency Working Group on Import Safety. Executive Order July 18, 2007
 Executive Order 13439 July 18, 2007 Establish an Interagency Working Group on Import Safety We need to continually improve our import safeguards to meet the changing demands of a global economy. We must
Executive Order 13439 July 18, 2007 Establish an Interagency Working Group on Import Safety We need to continually improve our import safeguards to meet the changing demands of a global economy. We must
Embracing the human and social dimension of technology and innovation
 Embracing the human and social dimension of technology and innovation - Dealing with complexity through interaction CHASS Inaugural National Forum September 26, 2012 Lars Klüver; director The Danish Board
Embracing the human and social dimension of technology and innovation - Dealing with complexity through interaction CHASS Inaugural National Forum September 26, 2012 Lars Klüver; director The Danish Board
Handling Digital Photographs for Use in Criminal Trials V2, March 2008
 Handling Digital Photographs for Use in Criminal Trials V2, March 2008 This is a DRAFT guide that may, once fully developed, be used by law enforcement to help ensure that digital photographs are admissible
Handling Digital Photographs for Use in Criminal Trials V2, March 2008 This is a DRAFT guide that may, once fully developed, be used by law enforcement to help ensure that digital photographs are admissible
Program Automotive Security and Privacy
 FFI BOARD FUNDED PROGRAM Program Automotive Security and Privacy 2015-11-03 Innehållsförteckning 1 Abstract... 3 2 Background... 4 3 Program objectives... 5 4 Program description... 5 5 Program scope...
FFI BOARD FUNDED PROGRAM Program Automotive Security and Privacy 2015-11-03 Innehållsförteckning 1 Abstract... 3 2 Background... 4 3 Program objectives... 5 4 Program description... 5 5 Program scope...
Cyber-Physical Systems, Power Grid, and Engineering Education NSF Perspective
 Cyber-Physical Systems, Power Grid, and Engineering Education NSF Perspective Pramod Khargonekar Assistant Director for Engineering National Science Foundation Workshop on Cyber-Physical Systems Education
Cyber-Physical Systems, Power Grid, and Engineering Education NSF Perspective Pramod Khargonekar Assistant Director for Engineering National Science Foundation Workshop on Cyber-Physical Systems Education
Summary Remarks By David A. Olive. WITSA Public Policy Chairman. November 3, 2009
 Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
Committee on the Internal Market and Consumer Protection. of the Committee on the Internal Market and Consumer Protection
 European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
5 TH MANAGEMENT SEMINARS FOR HEADS OF NATIONAL STATISTICAL OFFICES (NSO) IN ASIA AND THE PACIFIC SEPTEMBER 2006, DAEJEON, REPUBLIC OF KOREA
 Malaysia 5 TH MANAGEMENT SEMINARS FOR HEADS OF NATIONAL STATISTICAL OFFICES (NSO) IN ASIA AND THE PACIFIC. 18 20 SEPTEMBER 2006, DAEJEON, REPUBLIC OF KOREA 1. Overview of the Population and Housing Census
Malaysia 5 TH MANAGEMENT SEMINARS FOR HEADS OF NATIONAL STATISTICAL OFFICES (NSO) IN ASIA AND THE PACIFIC. 18 20 SEPTEMBER 2006, DAEJEON, REPUBLIC OF KOREA 1. Overview of the Population and Housing Census
Domain Understanding and Requirements Elicitation
 and Requirements Elicitation CS/SE 3RA3 Ryszard Janicki Department of Computing and Software, McMaster University, Hamilton, Ontario, Canada Ryszard Janicki 1/24 Previous Lecture: The requirement engineering
and Requirements Elicitation CS/SE 3RA3 Ryszard Janicki Department of Computing and Software, McMaster University, Hamilton, Ontario, Canada Ryszard Janicki 1/24 Previous Lecture: The requirement engineering
Social Network Behaviours to Explain the Spread of Online Game
 Social Network Behaviours to Explain the Spread of Online Game 91 Marilou O. Espina orcid.org/0000-0002-4727-6798 ms0940067@yahoo.com Bukidnon State University Jovelin M. Lapates orcid.org/0000-0002-4233-4143
Social Network Behaviours to Explain the Spread of Online Game 91 Marilou O. Espina orcid.org/0000-0002-4727-6798 ms0940067@yahoo.com Bukidnon State University Jovelin M. Lapates orcid.org/0000-0002-4233-4143
Prototyping: Accelerating the Adoption of Transformative Capabilities
 Prototyping: Accelerating the Adoption of Transformative Capabilities Mr. Elmer Roman Director, Joint Capability Technology Demonstration (JCTD) DASD, Emerging Capability & Prototyping (EC&P) 10/27/2016
Prototyping: Accelerating the Adoption of Transformative Capabilities Mr. Elmer Roman Director, Joint Capability Technology Demonstration (JCTD) DASD, Emerging Capability & Prototyping (EC&P) 10/27/2016
Executive Summary. Chapter 1. Overview of Control
 Chapter 1 Executive Summary Rapid advances in computing, communications, and sensing technology offer unprecedented opportunities for the field of control to expand its contributions to the economic and
Chapter 1 Executive Summary Rapid advances in computing, communications, and sensing technology offer unprecedented opportunities for the field of control to expand its contributions to the economic and
Description of the methodology
 Description of the methodology The prevailing standard for the electronics industry as being used in this overview is based by SOMO on the sustainability -policy, -standard and -practice that is currently
Description of the methodology The prevailing standard for the electronics industry as being used in this overview is based by SOMO on the sustainability -policy, -standard and -practice that is currently
UN-GGIM Future Trends in Geospatial Information Management 1
 UNITED NATIONS SECRETARIAT ESA/STAT/AC.279/P5 Department of Economic and Social Affairs October 2013 Statistics Division English only United Nations Expert Group on the Integration of Statistical and Geospatial
UNITED NATIONS SECRETARIAT ESA/STAT/AC.279/P5 Department of Economic and Social Affairs October 2013 Statistics Division English only United Nations Expert Group on the Integration of Statistical and Geospatial
SUSTAINABILITY MATERIALITY OVERVIEW
 SUSTAINABILITY MATERIALITY OVERVIEW EMC undertakes materiality assessments to identify and prioritize sustainability factors for the purposes of deciding where to focus our resources, setting goals, and
SUSTAINABILITY MATERIALITY OVERVIEW EMC undertakes materiality assessments to identify and prioritize sustainability factors for the purposes of deciding where to focus our resources, setting goals, and
Mr. Alain Schoenenberger
 TRADE AND DEVELOPMENT BOARD COMMISSION ON ENTERPRISE, BUSINESS FACILITATION AND DEVELOPMENT EXPERT MEETING ON BEST PRACTICES AND POLICY OPTIONS IN THE PROMOTION OF SME-TNC LINKAGES GENEVA, 6-8 NOVEMBER
TRADE AND DEVELOPMENT BOARD COMMISSION ON ENTERPRISE, BUSINESS FACILITATION AND DEVELOPMENT EXPERT MEETING ON BEST PRACTICES AND POLICY OPTIONS IN THE PROMOTION OF SME-TNC LINKAGES GENEVA, 6-8 NOVEMBER
CyPhers Project: Main Results
 CyPhers Project: Main Results Saddek Bensalem / shortened Presentation by Sebastian Engell (CPSoS) SoS Open Workshop, Florence May 28, 2015 fortiss (Munich) KTH (Stockholm) U. Joseph Fourier (Grenoble)
CyPhers Project: Main Results Saddek Bensalem / shortened Presentation by Sebastian Engell (CPSoS) SoS Open Workshop, Florence May 28, 2015 fortiss (Munich) KTH (Stockholm) U. Joseph Fourier (Grenoble)
Perspectives of Scientists on technology and the SDGs 61 scientists 3 tasks 20 countries 45 disciplines. 97 scientists 58 briefs
 Perspectives of Scientists on technology and the SDGs 61 scientists 3 tasks 20 countries 45 disciplines 97 scientists 58 briefs Technology-related SDG targets (48 of 169 targets) Proposals for leveraging
Perspectives of Scientists on technology and the SDGs 61 scientists 3 tasks 20 countries 45 disciplines 97 scientists 58 briefs Technology-related SDG targets (48 of 169 targets) Proposals for leveraging
