Basic Communication Operations (cont.) Alexandre David B2-206
|
|
|
- Albert Burke
- 5 years ago
- Views:
Transcription
1 Basic Communication Oerations (cont.) Alexandre David B-06
2 Today Scatter and Gather (4.4). All-to-All Personalized Communication (4.5). Circular Shift (4.6). Imroving the Seed of Some Communication Oerations (4.7) Alexandre David, MVP'06
3 Scatter and Gather Scatter: A node sends a unique message to every other node unique er node. Gather: Dual oeration but the target node does not combine the messages into one. M Scatter M M Gather 0 M 0 M 0 0 M Alexandre David, MVP'06 3
4 Alexandre David, MVP'06 4
5 Alexandre David, MVP'06 5 Cost Analysis Number of stes: log. Size transferred: m/, m/4,,m. Geometric sum Cost T=t s log+t w m(-). ) ( ) ( ) ( log n n n n n = = = = = =
6 All-to-All Personalized Communication Each node sends a distinct message to every other node. M 0, M 0, M, M, M,0 M, M, M, M,0 M, M, M, M 0,0 M,0 M,0 M 0,0 M 0, M 0, Alexandre David, MVP'06 6
7 Examle: Transose Alexandre David, MVP'06 7
8 Total Exchange on a Ring Alexandre David, MVP'06 8
9 Total Exchange on a Ring Alexandre David, MVP'06 9
10 Cost Analysis Number of stes: -. Size transmitted: m(-),m(-),m. T = t ( ) + s i= it w m = ( t s + t w m / )( ) Otimal Alexandre David, MVP'06 0
11 Total Exchange on a Mesh Alexandre David, MVP'06
12 Total Exchange on a Mesh Alexandre David, MVP'06
13 Total Exchange on a Mesh Alexandre David, MVP'06 3
14 Cost Analysis Substitute by (number of nodes er dimension). Substitute message size m by m. Cost is the same for each dimension. T=(t s +t w m)( -) Alexandre David, MVP'06 4
15 Total Exchange on a Hyercube Generalize the mesh algorithm to log stes = number of dimensions, with nodes er dimension. Same rocedure as all-to-all broadcast Alexandre David, MVP'06 5
16 Total Exchange on a Hyercube Alexandre David, MVP'06 6
17 Total Exchange on a Hyercube Alexandre David, MVP'06 7
18 Total Exchange on a Hyercube Alexandre David, MVP'06 8
19 Total Exchange on a Hyercube Alexandre David, MVP'06 9
20 Cost Analysis Number of stes: log. Size transmitted er ste: m/. Cost: T=(t s +t w m/) log. Otimal? NO Each node sends and receives m(-) words. Average distance = ( log)/. Total traffic = *m(-)* log/. Number of links = log/. Time lower bound = t w m(-) Alexandre David, MVP'06 0
21 An Otimal Algorithm Have every air of nodes communicate directly with each other - communication stes but without congestion. At j th ste node i communicates with node (i xor j) with E-cube routing Alexandre David, MVP'06
22 Total Exchange on a Hyercube Alexandre David, MVP'06
23 Total Exchange on a Hyercube Alexandre David, MVP'06 3
24 Total Exchange on a Hyercube Alexandre David, MVP'06 4
25 Total Exchange on a Hyercube Alexandre David, MVP'06 5
26 Total Exchange on a Hyercube Alexandre David, MVP'06 6
27 Total Exchange on a Hyercube Etc Alexandre David, MVP'06 7
28 Cost Analysis Remark: Transmit less, only what is needed, but more stes. Number of stes: -. Transmission: size m er ste. Cost: T=(t s +t w m)(-). Comared witht=(t s +t w m/) log. Previous algorithm better for small messages Alexandre David, MVP'06 8
29 Circular Shift It s a articular ermutation. Circular q-shift: Node i sends data to node (i+q) mod (in a set of nodes). Useful in some matrix oerations and attern matching. Ring: intuitive algorithm in min{q,-q} neighbor to neighbor communication stes. Why? Alexandre David, MVP'06 9
30 Circular 5-shift on a mesh. q mod on rows comensate q / on colums Alexandre David, MVP'06 30
31 Circular Shift on a Hyercube Ma a linear array with d nodes onto a hyercube of dimension d. Exand q shift as a sum of owers of (e.g. 5-shift = 0 + ). Perform the decomosed shifts. Use bi-directional links for forward (shift itself) and backward (rotation art) log stes Alexandre David, MVP'06 3
32 Or better: Direct E-cube routing. q-shifts on a 8-node hyercube Alexandre David, MVP'06 3
33 Imroving Performance So far messages of size m were not slit. If we slit them into arts: One-to-all broadcast = scatter + all-to-all broadcast of messages of size m/. All-to-one reduction = all-to-all reduce + scatter of messages of size m/. All-reduce = all-to-all reduction + all-to-all broadcast of messages of size m/ Alexandre David, MVP'06 33
Design of Parallel Algorithms. Communication Algorithms
 + Design of Parallel Algorithms Communication Algorithms + Topic Overview n One-to-All Broadcast and All-to-One Reduction n All-to-All Broadcast and Reduction n All-Reduce and Prefix-Sum Operations n Scatter
+ Design of Parallel Algorithms Communication Algorithms + Topic Overview n One-to-All Broadcast and All-to-One Reduction n All-to-All Broadcast and Reduction n All-Reduce and Prefix-Sum Operations n Scatter
CS256 Applied Theory of Computation
 CS256 Applied Theory of Computation Parallel Computation III John E Savage Overview Mapping normal algorithms to meshes Shuffle operations on linear arrays Shuffle operations on two-dimensional arrays
CS256 Applied Theory of Computation Parallel Computation III John E Savage Overview Mapping normal algorithms to meshes Shuffle operations on linear arrays Shuffle operations on two-dimensional arrays
SQUARING THE MAGIC SQUARES OF ORDER 4
 Journal of lgebra Number Theory: dvances and lications Volume 7 Number Pages -6 SQURING THE MGIC SQURES OF ORDER STEFNO BRBERO UMBERTO CERRUTI and NDIR MURRU Deartment of Mathematics University of Turin
Journal of lgebra Number Theory: dvances and lications Volume 7 Number Pages -6 SQURING THE MGIC SQURES OF ORDER STEFNO BRBERO UMBERTO CERRUTI and NDIR MURRU Deartment of Mathematics University of Turin
Introduction to Number Theory 2. c Eli Biham - November 5, Introduction to Number Theory 2 (12)
 Introduction to Number Theory c Eli Biham - November 5, 006 345 Introduction to Number Theory (1) Quadratic Residues Definition: The numbers 0, 1,,...,(n 1) mod n, are called uadratic residues modulo n.
Introduction to Number Theory c Eli Biham - November 5, 006 345 Introduction to Number Theory (1) Quadratic Residues Definition: The numbers 0, 1,,...,(n 1) mod n, are called uadratic residues modulo n.
Snow College Mathematics Contest
 Snow College Mathematics Contest Aril, 08 Senior Division: Grades 0- Form: T Bubble in the single best choice for each question you choose to answer.. If log 0 5=0.699 what is log 0 500?.699 5.699 6.99
Snow College Mathematics Contest Aril, 08 Senior Division: Grades 0- Form: T Bubble in the single best choice for each question you choose to answer.. If log 0 5=0.699 what is log 0 500?.699 5.699 6.99
Summary of Basic Concepts
 Transmission Summary of Basic Concepts Sender Channel Receiver Dr. Christian Rohner Encoding Modulation Demodulation Decoding Bits Symbols Noise Terminology Communications Research Group Bandwidth [Hz]
Transmission Summary of Basic Concepts Sender Channel Receiver Dr. Christian Rohner Encoding Modulation Demodulation Decoding Bits Symbols Noise Terminology Communications Research Group Bandwidth [Hz]
The Message Passing Interface (MPI)
 The Message Passing Interface (MPI) MPI is a message passing library standard which can be used in conjunction with conventional programming languages such as C, C++ or Fortran. MPI is based on the point-to-point
The Message Passing Interface (MPI) MPI is a message passing library standard which can be used in conjunction with conventional programming languages such as C, C++ or Fortran. MPI is based on the point-to-point
Link and Link Impedance 2018/02/13. VECTOR DATA ANALYSIS Network Analysis TYPES OF OPERATIONS
 VECTOR DATA ANALYSIS Network Analysis A network is a system of linear features that has the appropriate attributes for the flow of objects. A network is typically topology-based: lines (arcs) meet at intersections
VECTOR DATA ANALYSIS Network Analysis A network is a system of linear features that has the appropriate attributes for the flow of objects. A network is typically topology-based: lines (arcs) meet at intersections
Entropy Coding. Outline. Entropy. Definitions. log. A = {a, b, c, d, e}
 Outline efinition of ntroy Three ntroy coding techniques: Huffman coding rithmetic coding Lemel-Ziv coding ntroy oding (taken from the Technion) ntroy ntroy of a set of elements e,,e n with robabilities,
Outline efinition of ntroy Three ntroy coding techniques: Huffman coding rithmetic coding Lemel-Ziv coding ntroy oding (taken from the Technion) ntroy ntroy of a set of elements e,,e n with robabilities,
Hypercube Networks-III
 6.895 Theory of Parallel Systems Lecture 18 ypercube Networks-III Lecturer: harles Leiserson Scribe: Sriram Saroop and Wang Junqing Lecture Summary 1. Review of the previous lecture This section highlights
6.895 Theory of Parallel Systems Lecture 18 ypercube Networks-III Lecturer: harles Leiserson Scribe: Sriram Saroop and Wang Junqing Lecture Summary 1. Review of the previous lecture This section highlights
An Overview of PAPR Reduction Optimization Algorithm for MC-CDMA System
 RESEARCH ARTICLE OPEN ACCESS An Overview of PAPR Reduction Otimization Algorithm for MC-CDMA System Kanchan Singla*, Rajbir Kaur**, Gagandee Kaur*** *(Deartment of Electronics and Communication, Punjabi
RESEARCH ARTICLE OPEN ACCESS An Overview of PAPR Reduction Otimization Algorithm for MC-CDMA System Kanchan Singla*, Rajbir Kaur**, Gagandee Kaur*** *(Deartment of Electronics and Communication, Punjabi
Overview: Routing and Communication Costs
 Overview: Routing and Communication Costs Optimizing communications is non-trivial! (Introduction to Parallel Computing, Grama et al) routing mechanisms and communication costs routing strategies: store-and-forward,
Overview: Routing and Communication Costs Optimizing communications is non-trivial! (Introduction to Parallel Computing, Grama et al) routing mechanisms and communication costs routing strategies: store-and-forward,
Link State Routing. Brad Karp UCL Computer Science. CS 3035/GZ01 3 rd December 2013
 Link State Routing Brad Karp UCL Computer Science CS 33/GZ 3 rd December 3 Outline Link State Approach to Routing Finding Links: Hello Protocol Building a Map: Flooding Protocol Healing after Partitions:
Link State Routing Brad Karp UCL Computer Science CS 33/GZ 3 rd December 3 Outline Link State Approach to Routing Finding Links: Hello Protocol Building a Map: Flooding Protocol Healing after Partitions:
Overview: Routing and Communication Costs Store-and-Forward Routing Mechanisms and Communication Costs (Static) Cut-Through Routing/Wormhole Routing
 Overview: Routing and Communication Costs Store-and-Forward Optimizing communications is non-trivial! (Introduction to arallel Computing, Grama et al) routing mechanisms and communication costs routing
Overview: Routing and Communication Costs Store-and-Forward Optimizing communications is non-trivial! (Introduction to arallel Computing, Grama et al) routing mechanisms and communication costs routing
Is 1 a Square Modulo p? Is 2?
 Chater 21 Is 1 a Square Modulo? Is 2? In the revious chater we took various rimes and looked at the a s that were quadratic residues and the a s that were nonresidues. For examle, we made a table of squares
Chater 21 Is 1 a Square Modulo? Is 2? In the revious chater we took various rimes and looked at the a s that were quadratic residues and the a s that were nonresidues. For examle, we made a table of squares
Performance Analysis of MIMO System using Space Division Multiplexing Algorithms
 Performance Analysis of MIMO System using Sace Division Multilexing Algorithms Dr.C.Poongodi 1, Dr D Deea, M. Renuga Devi 3 and N Sasireka 3 1, Professor, Deartment of ECE 3 Assistant Professor, Deartment
Performance Analysis of MIMO System using Sace Division Multilexing Algorithms Dr.C.Poongodi 1, Dr D Deea, M. Renuga Devi 3 and N Sasireka 3 1, Professor, Deartment of ECE 3 Assistant Professor, Deartment
Link State Routing. Stefano Vissicchio UCL Computer Science CS 3035/GZ01
 Link State Routing Stefano Vissicchio UCL Computer Science CS 335/GZ Reminder: Intra-domain Routing Problem Shortest paths problem: What path between two vertices offers minimal sum of edge weights? Classic
Link State Routing Stefano Vissicchio UCL Computer Science CS 335/GZ Reminder: Intra-domain Routing Problem Shortest paths problem: What path between two vertices offers minimal sum of edge weights? Classic
CS601 Data Communication Solved Objective For Midterm Exam Preparation
 CS601 Data Communication Solved Objective For Midterm Exam Preparation Question No: 1 Effective network mean that the network has fast delivery, timeliness and high bandwidth duplex transmission accurate
CS601 Data Communication Solved Objective For Midterm Exam Preparation Question No: 1 Effective network mean that the network has fast delivery, timeliness and high bandwidth duplex transmission accurate
Efficient Importance Sampling for Monte Carlo Simulation of Multicast Networks
 Efficient Imortance Samling for Monte Carlo Simulation of Multicast Networks P. Lassila, J. Karvo and J. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P.O.Box 3000,
Efficient Imortance Samling for Monte Carlo Simulation of Multicast Networks P. Lassila, J. Karvo and J. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P.O.Box 3000,
TWO-WAY communication between two nodes was first
 6060 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 61, NO. 11, NOVEMBER 2015 On the Capacity Regions of Two-Way Diamond Channels Mehdi Ashraphijuo, Vaneet Aggarwal, Member, IEEE, and Xiaodong Wang, Fellow,
6060 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 61, NO. 11, NOVEMBER 2015 On the Capacity Regions of Two-Way Diamond Channels Mehdi Ashraphijuo, Vaneet Aggarwal, Member, IEEE, and Xiaodong Wang, Fellow,
Color each numeral card. Count the objects in each group. Then color the group of objects the same color as the numeral card that it matches.
 Lesson 7 Problem Set Color each numeral card. Count the objects in each group. Then color the group of objects the same color as the numeral card that it matches. 1 2 3 4 5 Black Blue Brown Red Yellow
Lesson 7 Problem Set Color each numeral card. Count the objects in each group. Then color the group of objects the same color as the numeral card that it matches. 1 2 3 4 5 Black Blue Brown Red Yellow
Privacy at the communication layer
 Privacy at the communication layer The Dining Cryptographers Problem: Unconditional Sender and Recipient Untraceability David Chaum 1988 CS-721 Carmela Troncoso http://carmelatroncoso.com/ (borrowed slides
Privacy at the communication layer The Dining Cryptographers Problem: Unconditional Sender and Recipient Untraceability David Chaum 1988 CS-721 Carmela Troncoso http://carmelatroncoso.com/ (borrowed slides
CS601-Data Communication Latest Solved Mcqs from Midterm Papers
 CS601-Data Communication Latest Solved Mcqs from Midterm Papers May 07,2011 Lectures 1-22 Moaaz Siddiq Latest Mcqs MIDTERM EXAMINATION Spring 2010 Question No: 1 ( Marks: 1 ) - Please choose one Effective
CS601-Data Communication Latest Solved Mcqs from Midterm Papers May 07,2011 Lectures 1-22 Moaaz Siddiq Latest Mcqs MIDTERM EXAMINATION Spring 2010 Question No: 1 ( Marks: 1 ) - Please choose one Effective
)454 1 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU
 INTERNATIONAL TELECOMMUNICATION UNION )454 1 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU 30%#)&)#!4)/.3 /& 3)'.!,,).' 3934%- 2 ).4%22%')34%2 3)'.!,,).' 3)'.!,,).' #/$% )454 Recommendation 1 (Extract
INTERNATIONAL TELECOMMUNICATION UNION )454 1 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU 30%#)&)#!4)/.3 /& 3)'.!,,).' 3934%- 2 ).4%22%')34%2 3)'.!,,).' 3)'.!,,).' #/$% )454 Recommendation 1 (Extract
Chapter 3 Chip Planning
 Chapter 3 Chip Planning 3.1 Introduction to Floorplanning 3. Optimization Goals in Floorplanning 3.3 Terminology 3.4 Floorplan Representations 3.4.1 Floorplan to a Constraint-Graph Pair 3.4. Floorplan
Chapter 3 Chip Planning 3.1 Introduction to Floorplanning 3. Optimization Goals in Floorplanning 3.3 Terminology 3.4 Floorplan Representations 3.4.1 Floorplan to a Constraint-Graph Pair 3.4. Floorplan
ELG 5372 Error Control Coding. Lecture 10: Performance Measures: BER after decoding
 ELG 532 Error Control Coding Lecture 10: Performance Measures: BER after decoding Error Correction Performance Review The robability of incorrectly decoding a received word is the robability that the error
ELG 532 Error Control Coding Lecture 10: Performance Measures: BER after decoding Error Correction Performance Review The robability of incorrectly decoding a received word is the robability that the error
Solution Algorithm to the Sam Loyd (n 2 1) Puzzle
 Solution Algorithm to the Sam Loyd (n 2 1) Puzzle Kyle A. Bishop Dustin L. Madsen December 15, 2009 Introduction The Sam Loyd puzzle was a 4 4 grid invented in the 1870 s with numbers 0 through 15 on each
Solution Algorithm to the Sam Loyd (n 2 1) Puzzle Kyle A. Bishop Dustin L. Madsen December 15, 2009 Introduction The Sam Loyd puzzle was a 4 4 grid invented in the 1870 s with numbers 0 through 15 on each
Math 124 Homework 5 Solutions
 Math 12 Homework 5 Solutions by Luke Gustafson Fall 2003 1. 163 1 2 (mod 2 gives = 2 the smallest rime. 2a. First, consider = 2. We know 2 is not a uadratic residue if and only if 3, 5 (mod 8. By Dirichlet
Math 12 Homework 5 Solutions by Luke Gustafson Fall 2003 1. 163 1 2 (mod 2 gives = 2 the smallest rime. 2a. First, consider = 2. We know 2 is not a uadratic residue if and only if 3, 5 (mod 8. By Dirichlet
for Vehicular Ad Hoc Networks
 Distributed Fair Transmit Power Adjustment for Vehicular Ad Hoc Networks Third Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON 06) Reston, VA,
Distributed Fair Transmit Power Adjustment for Vehicular Ad Hoc Networks Third Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON 06) Reston, VA,
Distance-Vector Routing
 Distance-Vector Routing Antonio Carzaniga Faculty of Informatics University of Lugano June 8, 2007 c 2005 2007 Antonio Carzaniga 1 Recap on link-state routing Distance-vector routing Bellman-Ford equation
Distance-Vector Routing Antonio Carzaniga Faculty of Informatics University of Lugano June 8, 2007 c 2005 2007 Antonio Carzaniga 1 Recap on link-state routing Distance-vector routing Bellman-Ford equation
Digital Image Processing. Digital Image Fundamentals II 12 th June, 2017
 Digital Image Processing Digital Image Fundamentals II 12 th June, 2017 Image Enhancement Image Enhancement Types of Image Enhancement Operations Neighborhood Operations on Images Spatial Filtering Filtering
Digital Image Processing Digital Image Fundamentals II 12 th June, 2017 Image Enhancement Image Enhancement Types of Image Enhancement Operations Neighborhood Operations on Images Spatial Filtering Filtering
An Optimal (d 1)-Fault-Tolerant All-to-All Broadcasting Scheme for d-dimensional Hypercubes
 An Optimal (d 1)-Fault-Tolerant All-to-All Broadcasting Scheme for d-dimensional Hypercubes Siu-Cheung Chau Dept. of Physics and Computing, Wilfrid Laurier University, Waterloo, Ontario, Canada, N2L 3C5
An Optimal (d 1)-Fault-Tolerant All-to-All Broadcasting Scheme for d-dimensional Hypercubes Siu-Cheung Chau Dept. of Physics and Computing, Wilfrid Laurier University, Waterloo, Ontario, Canada, N2L 3C5
High resolution radar signal detection based on feature analysis
 Available online www.jocr.com Journal of Chemical and Pharmaceutical Research, 4, 6(6):73-77 Research Article ISSN : 975-7384 CODEN(USA) : JCPRC5 High resolution radar signal detection based on feature
Available online www.jocr.com Journal of Chemical and Pharmaceutical Research, 4, 6(6):73-77 Research Article ISSN : 975-7384 CODEN(USA) : JCPRC5 High resolution radar signal detection based on feature
Information flow over wireless networks: a deterministic approach
 Information flow over wireless networks: a deterministic approach alman Avestimehr In collaboration with uhas iggavi (EPFL) and avid Tse (UC Berkeley) Overview Point-to-point channel Information theory
Information flow over wireless networks: a deterministic approach alman Avestimehr In collaboration with uhas iggavi (EPFL) and avid Tse (UC Berkeley) Overview Point-to-point channel Information theory
Principles of Ad Hoc Networking
 Principles of Ad Hoc Networking Michel Barbeau and Evangelos Kranakis November 12, 2007 Wireless security challenges Network type Wireless Mobility Ad hoc Sensor Challenge Open medium Handover implies
Principles of Ad Hoc Networking Michel Barbeau and Evangelos Kranakis November 12, 2007 Wireless security challenges Network type Wireless Mobility Ad hoc Sensor Challenge Open medium Handover implies
Selective Families, Superimposed Codes and Broadcasting on Unknown Radio Networks. Andrea E.F. Clementi Angelo Monti Riccardo Silvestri
 Selective Families, Superimposed Codes and Broadcasting on Unknown Radio Networks Andrea E.F. Clementi Angelo Monti Riccardo Silvestri Introduction A radio network is a set of radio stations that are able
Selective Families, Superimposed Codes and Broadcasting on Unknown Radio Networks Andrea E.F. Clementi Angelo Monti Riccardo Silvestri Introduction A radio network is a set of radio stations that are able
MIMO II: Physical Channel Modeling, Spatial Multiplexing. COS 463: Wireless Networks Lecture 17 Kyle Jamieson
 MIMO II: Physical Channel Modeling, Spatial Multiplexing COS 463: Wireless Networks Lecture 17 Kyle Jamieson Today 1. Graphical intuition in the I-Q plane 2. Physical modeling of the SIMO channel 3. Physical
MIMO II: Physical Channel Modeling, Spatial Multiplexing COS 463: Wireless Networks Lecture 17 Kyle Jamieson Today 1. Graphical intuition in the I-Q plane 2. Physical modeling of the SIMO channel 3. Physical
Earth fault hazard voltages and their limitation
 Earth fault hazard voltages and their limitation The effect of electricity on human body - combustion - chemical changes in blood - heart fibrillation Currents corresonding to 10% and 1% robabilities of
Earth fault hazard voltages and their limitation The effect of electricity on human body - combustion - chemical changes in blood - heart fibrillation Currents corresonding to 10% and 1% robabilities of
Introduction to DSP ECE-S352 Fall Quarter 2000 Matlab Project 1
 Objective: Introduction to DSP ECE-S352 Fall Quarter 2000 Matlab Project 1 This Matlab Project is an extension of the basic correlation theory presented in the course. It shows a practical application
Objective: Introduction to DSP ECE-S352 Fall Quarter 2000 Matlab Project 1 This Matlab Project is an extension of the basic correlation theory presented in the course. It shows a practical application
The Optimization Model and Algorithm for Train Connection at Transfer Stations in Urban Rail Transit Network
 Send Orders for Rerints to rerints@benthamscienceae 690 The Oen Cybernetics & Systemics Journal, 05, 9, 690-698 Oen Access The Otimization Model and Algorithm for Train Connection at Transfer Stations
Send Orders for Rerints to rerints@benthamscienceae 690 The Oen Cybernetics & Systemics Journal, 05, 9, 690-698 Oen Access The Otimization Model and Algorithm for Train Connection at Transfer Stations
Modeling of power autotransformer
 Modeling of ower autotransformer VLADMÍR VOLČKO, ŽAETA ELEHOVÁ, ATO BELÁŇ, PETER JAGA, DOMK VGLAŠ, MROLAVA MTKOVÁ Deartment of Electrical Power Engineering lovak niversity of Technology in Bratislava lkovičova,
Modeling of ower autotransformer VLADMÍR VOLČKO, ŽAETA ELEHOVÁ, ATO BELÁŇ, PETER JAGA, DOMK VGLAŠ, MROLAVA MTKOVÁ Deartment of Electrical Power Engineering lovak niversity of Technology in Bratislava lkovičova,
ODMA Opportunity Driven Multiple Access
 ODMA Opportunity Driven Multiple Access by Keith Mayes & James Larsen Opportunity Driven Multiple Access is a mechanism for maximizing the potential for effective communication. This is achieved by distributing
ODMA Opportunity Driven Multiple Access by Keith Mayes & James Larsen Opportunity Driven Multiple Access is a mechanism for maximizing the potential for effective communication. This is achieved by distributing
Lectures: Feb 27 + Mar 1 + Mar 3, 2017
 CS420+500: Advanced Algorithm Design and Analysis Lectures: Feb 27 + Mar 1 + Mar 3, 2017 Prof. Will Evans Scribe: Adrian She In this lecture we: Summarized how linear programs can be used to model zero-sum
CS420+500: Advanced Algorithm Design and Analysis Lectures: Feb 27 + Mar 1 + Mar 3, 2017 Prof. Will Evans Scribe: Adrian She In this lecture we: Summarized how linear programs can be used to model zero-sum
CS 621 Mobile Computing
 Lecture 11 CS 621 Mobile Computing Location Management for Mobile Cellular Systems Zubin Bhuyan, Department of CSE, Tezpur University http://www.tezu.ernet.in/~zubin Several slides and images in this presentation
Lecture 11 CS 621 Mobile Computing Location Management for Mobile Cellular Systems Zubin Bhuyan, Department of CSE, Tezpur University http://www.tezu.ernet.in/~zubin Several slides and images in this presentation
CH 4. Air Interface of the IS-95A CDMA System
 CH 4. Air Interface of the IS-95A CDMA System 1 Contents Summary of IS-95A Physical Layer Parameters Forward Link Structure Pilot, Sync, Paging, and Traffic Channels Channel Coding, Interleaving, Data
CH 4. Air Interface of the IS-95A CDMA System 1 Contents Summary of IS-95A Physical Layer Parameters Forward Link Structure Pilot, Sync, Paging, and Traffic Channels Channel Coding, Interleaving, Data
Iterative Joint Source/Channel Decoding for JPEG2000
 Iterative Joint Source/Channel Decoding for JPEG Lingling Pu, Zhenyu Wu, Ali Bilgin, Michael W. Marcellin, and Bane Vasic Dept. of Electrical and Computer Engineering The University of Arizona, Tucson,
Iterative Joint Source/Channel Decoding for JPEG Lingling Pu, Zhenyu Wu, Ali Bilgin, Michael W. Marcellin, and Bane Vasic Dept. of Electrical and Computer Engineering The University of Arizona, Tucson,
An Efficient VLSI Architecture Parallel Prefix Counting With Domino Logic Λ
 An Efficient VLSI Architecture Parallel Prefix Counting With Domino Logic Λ Rong Lin y Koji Nakano z Stehan Olariu x Albert Y. Zomaya Abstract We roose an efficient reconfigurable arallel refix counting
An Efficient VLSI Architecture Parallel Prefix Counting With Domino Logic Λ Rong Lin y Koji Nakano z Stehan Olariu x Albert Y. Zomaya Abstract We roose an efficient reconfigurable arallel refix counting
Switching threshold. Switch delay model. Input pattern effects on delay
 Switching threshold Low Power VLSI System Design Lecture 8 & 9: Transistor Sizing and Low Power Memory Design Prof. R. Iris ahar October & 4, 017 Define V M to be the oint where V in = V out (both PMOS
Switching threshold Low Power VLSI System Design Lecture 8 & 9: Transistor Sizing and Low Power Memory Design Prof. R. Iris ahar October & 4, 017 Define V M to be the oint where V in = V out (both PMOS
Energy-Efficient Communication Protocol for Wireless Microsensor Networks
 Energy-Efficient Communication Protocol for Wireless Microsensor Networks Wendi Rabiner Heinzelman Anatha Chandrasakan Hari Balakrishnan Massachusetts Institute of Technology Presented by Rick Skowyra
Energy-Efficient Communication Protocol for Wireless Microsensor Networks Wendi Rabiner Heinzelman Anatha Chandrasakan Hari Balakrishnan Massachusetts Institute of Technology Presented by Rick Skowyra
Wireless ad hoc networks. Acknowledgement: Slides borrowed from Richard Y. Yale
 Wireless ad hoc networks Acknowledgement: Slides borrowed from Richard Y. Yang @ Yale Infrastructure-based v.s. ad hoc Infrastructure-based networks Cellular network 802.11, access points Ad hoc networks
Wireless ad hoc networks Acknowledgement: Slides borrowed from Richard Y. Yang @ Yale Infrastructure-based v.s. ad hoc Infrastructure-based networks Cellular network 802.11, access points Ad hoc networks
RF Considerations for Wireless Systems Design. Frank Jimenez Manager, Technical Support & Service
 RF Considerations for Wireless Systems Design Frank Jimenez Manager, Technical Support & Service 1 The Presentation Objective We will cover.. The available wireless spectrum 802.11 technology and the wireless
RF Considerations for Wireless Systems Design Frank Jimenez Manager, Technical Support & Service 1 The Presentation Objective We will cover.. The available wireless spectrum 802.11 technology and the wireless
On the Capacity Regions of Two-Way Diamond. Channels
 On the Capacity Regions of Two-Way Diamond 1 Channels Mehdi Ashraphijuo, Vaneet Aggarwal and Xiaodong Wang arxiv:1410.5085v1 [cs.it] 19 Oct 2014 Abstract In this paper, we study the capacity regions of
On the Capacity Regions of Two-Way Diamond 1 Channels Mehdi Ashraphijuo, Vaneet Aggarwal and Xiaodong Wang arxiv:1410.5085v1 [cs.it] 19 Oct 2014 Abstract In this paper, we study the capacity regions of
Chapter 12. Cross-Layer Optimization for Multi- Hop Cognitive Radio Networks
 Chapter 12 Cross-Layer Optimization for Multi- Hop Cognitive Radio Networks 1 Outline CR network (CRN) properties Mathematical models at multiple layers Case study 2 Traditional Radio vs CR Traditional
Chapter 12 Cross-Layer Optimization for Multi- Hop Cognitive Radio Networks 1 Outline CR network (CRN) properties Mathematical models at multiple layers Case study 2 Traditional Radio vs CR Traditional
Optimum use of a 4-element Yagi-Uda Antenna for the Reception of Several UHF TV Channels
 ENGNEE - Vol, No 3, [67-7], 7 The nstitution of Engineers, Sri anka htt://doiorg/438/engineerv5i3766 Otimum use of a 4-element Yagi-Uda Antenna for e ecetion of Several UHF TV Channels CJSAH Perera Abstract:
ENGNEE - Vol, No 3, [67-7], 7 The nstitution of Engineers, Sri anka htt://doiorg/438/engineerv5i3766 Otimum use of a 4-element Yagi-Uda Antenna for e ecetion of Several UHF TV Channels CJSAH Perera Abstract:
Design of PID Controller Based on an Expert System
 International Journal of Comuter, Consumer and Control (IJ3C), Vol. 3, No.1 (014) 31 Design of PID Controller Based on an Exert System Wei Li Abstract For the instability of traditional control systems,
International Journal of Comuter, Consumer and Control (IJ3C), Vol. 3, No.1 (014) 31 Design of PID Controller Based on an Exert System Wei Li Abstract For the instability of traditional control systems,
MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012
 Location Management for Mobile Cellular Systems MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Cellular System
Location Management for Mobile Cellular Systems MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Cellular System
Ultra-Low Duty Cycle MAC with Scheduled Channel Polling
 Ultra-Low Duty Cycle MAC with Scheduled Channel Polling Wei Ye and John Heidemann CS577 Brett Levasseur 12/3/2013 Outline Introduction Scheduled Channel Polling (SCP-MAC) Energy Performance Analysis Implementation
Ultra-Low Duty Cycle MAC with Scheduled Channel Polling Wei Ye and John Heidemann CS577 Brett Levasseur 12/3/2013 Outline Introduction Scheduled Channel Polling (SCP-MAC) Energy Performance Analysis Implementation
Collaborative transmission in wireless sensor networks
 Collaborative transmission in wireless sensor networks Cooperative transmission schemes Stephan Sigg Distributed and Ubiquitous Systems Technische Universität Braunschweig November 22, 2010 Stephan Sigg
Collaborative transmission in wireless sensor networks Cooperative transmission schemes Stephan Sigg Distributed and Ubiquitous Systems Technische Universität Braunschweig November 22, 2010 Stephan Sigg
Multi-period Channel Assignment
 Multi-eriod Channel Assignment Hakim Mabed, Alexandre Caminada and Jin-Kao Hao 2 France Télécom R&D, 6 Avenue des Usines, BP 382, 97 Belfort, France {hakim.mabed,alexandre.caminada}@francetelecm.com Tel:
Multi-eriod Channel Assignment Hakim Mabed, Alexandre Caminada and Jin-Kao Hao 2 France Télécom R&D, 6 Avenue des Usines, BP 382, 97 Belfort, France {hakim.mabed,alexandre.caminada}@francetelecm.com Tel:
n Based on the decision rule Po- Ning Chapter Po- Ning Chapter
 n Soft decision decoding (can be analyzed via an equivalent binary-input additive white Gaussian noise channel) o The error rate of Ungerboeck codes (particularly at high SNR) is dominated by the two codewords
n Soft decision decoding (can be analyzed via an equivalent binary-input additive white Gaussian noise channel) o The error rate of Ungerboeck codes (particularly at high SNR) is dominated by the two codewords
Reduced Overhead Distributed Consensus-Based Estimation Algorithm
 Reduced Overhead Distributed Consensus-Based Estimation Algorithm Ban-Sok Shin, Henning Paul, Dirk Wübben and Armin Dekorsy Department of Communications Engineering University of Bremen Bremen, Germany
Reduced Overhead Distributed Consensus-Based Estimation Algorithm Ban-Sok Shin, Henning Paul, Dirk Wübben and Armin Dekorsy Department of Communications Engineering University of Bremen Bremen, Germany
Mobility Tolerant Broadcast in Mobile Ad Hoc Networks
 Mobility Tolerant Broadcast in Mobile Ad Hoc Networks Pradip K Srimani 1 and Bhabani P Sinha 2 1 Department of Computer Science, Clemson University, Clemson, SC 29634 0974 2 Electronics Unit, Indian Statistical
Mobility Tolerant Broadcast in Mobile Ad Hoc Networks Pradip K Srimani 1 and Bhabani P Sinha 2 1 Department of Computer Science, Clemson University, Clemson, SC 29634 0974 2 Electronics Unit, Indian Statistical
State-of-the-Art Verification of the Hard Driven GTO Inverter Development for a 100 MVA Intertie
 State-of-the-Art Verification of the Hard Driven GTO Inverter Develoment for a 100 MVA Intertie P. K. Steimer, H. Grüning, J. Werninger R&D Drives and Power Electronics ABB Industrie AG CH-5300 Turgi,
State-of-the-Art Verification of the Hard Driven GTO Inverter Develoment for a 100 MVA Intertie P. K. Steimer, H. Grüning, J. Werninger R&D Drives and Power Electronics ABB Industrie AG CH-5300 Turgi,
Integrated Strategy for Generating Permutation
 Int J Contemp Math Sciences, Vol 6, 011, no 4, 1167-1174 Integrated Strategy for Generating Permutation Sharmila Karim 1, Zurni Omar and Haslinda Ibrahim Quantitative Sciences Building College of Arts
Int J Contemp Math Sciences, Vol 6, 011, no 4, 1167-1174 Integrated Strategy for Generating Permutation Sharmila Karim 1, Zurni Omar and Haslinda Ibrahim Quantitative Sciences Building College of Arts
Scalable Routing Protocols for Mobile Ad Hoc Networks
 Helsinki University of Technology T-79.300 Postgraduate Course in Theoretical Computer Science Scalable Routing Protocols for Mobile Ad Hoc Networks Hafeth Hourani hafeth.hourani@nokia.com Contents Overview
Helsinki University of Technology T-79.300 Postgraduate Course in Theoretical Computer Science Scalable Routing Protocols for Mobile Ad Hoc Networks Hafeth Hourani hafeth.hourani@nokia.com Contents Overview
Encoding and Framing
 Encoding and Framing EECS 489 Computer Networks http://www.eecs.umich.edu/~zmao/eecs489 Z. Morley Mao Tuesday Nov 2, 2004 Acknowledgement: Some slides taken from Kurose&Ross and Katz&Stoica 1 Questions
Encoding and Framing EECS 489 Computer Networks http://www.eecs.umich.edu/~zmao/eecs489 Z. Morley Mao Tuesday Nov 2, 2004 Acknowledgement: Some slides taken from Kurose&Ross and Katz&Stoica 1 Questions
Communication Theory II
 Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Smart Antenna Techniques and Their Application to Wireless Ad Hoc Networks. Plenary Talk at: Jack H. Winters. September 13, 2005
 Smart Antenna Techniques and Their Application to Wireless Ad Hoc Networks Plenary Talk at: Jack H. Winters September 13, 2005 jwinters@motia.com 12/05/03 Slide 1 1 Outline Service Limitations Smart Antennas
Smart Antenna Techniques and Their Application to Wireless Ad Hoc Networks Plenary Talk at: Jack H. Winters September 13, 2005 jwinters@motia.com 12/05/03 Slide 1 1 Outline Service Limitations Smart Antennas
Encoding and Framing. Questions. Signals: Analog vs. Digital. Signals: Periodic vs. Aperiodic. Attenuation. Data vs. Signal
 Questions Encoding and Framing Why are some links faster than others? What limits the amount of information we can send on a link? How can we increase the capacity of a link? EECS 489 Computer Networks
Questions Encoding and Framing Why are some links faster than others? What limits the amount of information we can send on a link? How can we increase the capacity of a link? EECS 489 Computer Networks
CH 5. Air Interface of the IS-95A CDMA System
 CH 5. Air Interface of the IS-95A CDMA System 1 Contents Summary of IS-95A Physical Layer Parameters Forward Link Structure Pilot, Sync, Paging, and Traffic Channels Channel Coding, Interleaving, Data
CH 5. Air Interface of the IS-95A CDMA System 1 Contents Summary of IS-95A Physical Layer Parameters Forward Link Structure Pilot, Sync, Paging, and Traffic Channels Channel Coding, Interleaving, Data
Uplink Scheduling in Wireless Networks with Successive Interference Cancellation
 1 Ulink Scheduling in Wireless Networks with Successive Interference Cancellation Majid Ghaderi, Member, IEEE, and Mohsen Mollanoori, Student Member, IEEE, Abstract In this aer, we study the roblem of
1 Ulink Scheduling in Wireless Networks with Successive Interference Cancellation Majid Ghaderi, Member, IEEE, and Mohsen Mollanoori, Student Member, IEEE, Abstract In this aer, we study the roblem of
Opportunistic Routing in Wireless Mesh Networks
 Opportunistic Routing in Wireless Mesh Networks Amir arehshoorzadeh amir@ac.upc.edu Llorenç Cerdá-Alabern llorenc@ac.upc.edu Vicent Pla vpla@dcom.upv.es August 31, 2012 Opportunistic Routing in Wireless
Opportunistic Routing in Wireless Mesh Networks Amir arehshoorzadeh amir@ac.upc.edu Llorenç Cerdá-Alabern llorenc@ac.upc.edu Vicent Pla vpla@dcom.upv.es August 31, 2012 Opportunistic Routing in Wireless
Introduction. Introduction ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS. Smart Wireless Sensor Systems 1
 ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS Xiang Ji and Hongyuan Zha Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley,
ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS Xiang Ji and Hongyuan Zha Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley,
T. Yoo, E. Setton, X. Zhu, Pr. Goldsmith and Pr. Girod Department of Electrical Engineering Stanford University
 Cross-layer design for video streaming over wireless ad hoc networks T. Yoo, E. Setton, X. Zhu, Pr. Goldsmith and Pr. Girod Department of Electrical Engineering Stanford University Outline Cross-layer
Cross-layer design for video streaming over wireless ad hoc networks T. Yoo, E. Setton, X. Zhu, Pr. Goldsmith and Pr. Girod Department of Electrical Engineering Stanford University Outline Cross-layer
Exercises to Chapter 2 solutions
 Exercises to Chapter 2 solutions 1 Exercises to Chapter 2 solutions E2.1 The Manchester code was first used in Manchester Mark 1 computer at the University of Manchester in 1949 and is still used in low-speed
Exercises to Chapter 2 solutions 1 Exercises to Chapter 2 solutions E2.1 The Manchester code was first used in Manchester Mark 1 computer at the University of Manchester in 1949 and is still used in low-speed
High-Throughput VLSI Implementations of Iterative Decoders and Related Code Construction Problems
 High-Throughput VLSI Implementations of Iterative Decoders and Related Code Construction Problems Vijay Nagarajan, Stefan Laendner, Nikhil Jayakumar, Olgica Milenkovic, and Sunil P. Khatri University of
High-Throughput VLSI Implementations of Iterative Decoders and Related Code Construction Problems Vijay Nagarajan, Stefan Laendner, Nikhil Jayakumar, Olgica Milenkovic, and Sunil P. Khatri University of
4 + 3 = 7 10= Starting at the bigger number and counting on. Progression in Calculations
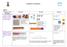 Progression in Calculations Addition Objective and Strategies Combining two parts to make a whole: partwhole model Concrete Pictorial Abstract Use cubes to add two numbers together as a group or in a bar.
Progression in Calculations Addition Objective and Strategies Combining two parts to make a whole: partwhole model Concrete Pictorial Abstract Use cubes to add two numbers together as a group or in a bar.
Evolutionary Circuit Design: Information Theory Perspective on Signal Propagation
 Evolutionary Circuit Design: Theory Persective on Signal Proagation Denis Poel Deartment of Comuter Science, Baker University, P.O. 65, Baldwin City, KS 66006, E-mail: oel@ieee.org Nawar Hakeem Deartment
Evolutionary Circuit Design: Theory Persective on Signal Proagation Denis Poel Deartment of Comuter Science, Baker University, P.O. 65, Baldwin City, KS 66006, E-mail: oel@ieee.org Nawar Hakeem Deartment
OPTICAL NETWORKS. Building Blocks. A. Gençata İTÜ, Dept. Computer Engineering 2005
 OPTICAL NETWORKS Building Blocks A. Gençata İTÜ, Dept. Computer Engineering 2005 Introduction An introduction to WDM devices. optical fiber optical couplers optical receivers optical filters optical amplifiers
OPTICAL NETWORKS Building Blocks A. Gençata İTÜ, Dept. Computer Engineering 2005 Introduction An introduction to WDM devices. optical fiber optical couplers optical receivers optical filters optical amplifiers
THE field of personal wireless communications is expanding
 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 5, NO. 6, DECEMBER 1997 907 Distributed Channel Allocation for PCN with Variable Rate Traffic Partha P. Bhattacharya, Leonidas Georgiadis, Senior Member, IEEE,
IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 5, NO. 6, DECEMBER 1997 907 Distributed Channel Allocation for PCN with Variable Rate Traffic Partha P. Bhattacharya, Leonidas Georgiadis, Senior Member, IEEE,
Anomalies in Optimal Rate-control and Scheduling Protocols for Cognitive Radio Networks
 Anomalies in Optimal Rate-control and Scheduling Protocols for Cognitive Radio Networks Vinay Kolar 1 V. Munishwar 2 N. Abu-Ghazaleh 1,2 1 Department of Computer Science Carnegie Mellon University, Qatar
Anomalies in Optimal Rate-control and Scheduling Protocols for Cognitive Radio Networks Vinay Kolar 1 V. Munishwar 2 N. Abu-Ghazaleh 1,2 1 Department of Computer Science Carnegie Mellon University, Qatar
Bottleneck Zone Analysis in WSN Using Low Duty Cycle in Wireless Micro Sensor Network
 Bottleneck Zone Analysis in WSN Using Low Duty Cycle in Wireless Micro Sensor Network 16 1 Punam Dhawad, 2 Hemlata Dakhore 1 Department of Computer Science and Engineering, G.H. Raisoni Institute of Engineering
Bottleneck Zone Analysis in WSN Using Low Duty Cycle in Wireless Micro Sensor Network 16 1 Punam Dhawad, 2 Hemlata Dakhore 1 Department of Computer Science and Engineering, G.H. Raisoni Institute of Engineering
Safeguarding Wireless Service Access
 Safeguarding Wireless Service Access Panos Papadimitratos Electrical and Computer Engineering Virginia Tech Wireless Service Access Service Access Points Users Wireless Service Access (cont d) Ad Hoc Networking
Safeguarding Wireless Service Access Panos Papadimitratos Electrical and Computer Engineering Virginia Tech Wireless Service Access Service Access Points Users Wireless Service Access (cont d) Ad Hoc Networking
THE USE OF INSULATED WIRES MILLIKEN CONDUCTORS IN HIGH VOLTAGE POWER TRANSMISSION UNDERGROUND AC LINES. x y s ABSTRACT
 THE USE OF INSULATED WIRES MILLIKEN CONDUCTORS IN HIGH VOLTAGE POWER TRANSMISSION UNDERGROUND AC LINES David DUBOIS, NEXANS, (France), david.dubois@nexans.com Pierre MIREBEAU, NEXANS, (France), ierre.mirebeau@nexans.com
THE USE OF INSULATED WIRES MILLIKEN CONDUCTORS IN HIGH VOLTAGE POWER TRANSMISSION UNDERGROUND AC LINES David DUBOIS, NEXANS, (France), david.dubois@nexans.com Pierre MIREBEAU, NEXANS, (France), ierre.mirebeau@nexans.com
Routing Messages in a Network
 Routing Messages in a Network Reference : J. Leung, T. Tam and G. Young, 'On-Line Routing of Real-Time Messages,' Journal of Parallel and Distributed Computing, 34, pp. 211-217, 1996. J. Leung, T. Tam,
Routing Messages in a Network Reference : J. Leung, T. Tam and G. Young, 'On-Line Routing of Real-Time Messages,' Journal of Parallel and Distributed Computing, 34, pp. 211-217, 1996. J. Leung, T. Tam,
RClamp2574N. High Power TVS for Ethernet Interfaces. PROTECTION PRODUCTS - RailClamp Description. Features. Mechanical Characteristics.
 - RailClam Descrition RailClam TS diodes are secifically designed to rotect sensitive comonents which are connected to high-seed data and transmission lines from overvoltage caused by ESD (electrostatic
- RailClam Descrition RailClam TS diodes are secifically designed to rotect sensitive comonents which are connected to high-seed data and transmission lines from overvoltage caused by ESD (electrostatic
Coding aware routing in wireless networks with bandwidth guarantees. IEEEVTS Vehicular Technology Conference Proceedings. Copyright IEEE.
 Title Coding aware routing in wireless networks with bandwidth guarantees Author(s) Hou, R; Lui, KS; Li, J Citation The IEEE 73rd Vehicular Technology Conference (VTC Spring 2011), Budapest, Hungary, 15-18
Title Coding aware routing in wireless networks with bandwidth guarantees Author(s) Hou, R; Lui, KS; Li, J Citation The IEEE 73rd Vehicular Technology Conference (VTC Spring 2011), Budapest, Hungary, 15-18
SPACE-FREQUENCY CODED OFDM FOR UNDERWATER ACOUSTIC COMMUNICATIONS
 SPACE-FREQUENCY CODED OFDM FOR UNDERWATER ACOUSTIC COMMUNICATIONS E. V. Zorita and M. Stojanovic MITSG 12-35 Sea Grant College Program Massachusetts Institute of Technology Cambridge, Massachusetts 02139
SPACE-FREQUENCY CODED OFDM FOR UNDERWATER ACOUSTIC COMMUNICATIONS E. V. Zorita and M. Stojanovic MITSG 12-35 Sea Grant College Program Massachusetts Institute of Technology Cambridge, Massachusetts 02139
Series PID Pitch Controller of Large Wind Turbines Generator
 SERBIAN JOURNAL OF ELECRICAL ENGINEERING Vol. 1, No., June 015, 183-196 UDC: 61.311.4:681.5 DOI: 10.98/SJEE150183M Series PID Pitch Controller of Large Wind urbines Generator Aleksandar D. Micić 1, Miroslav
SERBIAN JOURNAL OF ELECRICAL ENGINEERING Vol. 1, No., June 015, 183-196 UDC: 61.311.4:681.5 DOI: 10.98/SJEE150183M Series PID Pitch Controller of Large Wind urbines Generator Aleksandar D. Micić 1, Miroslav
Reliable Videos Broadcast with Network Coding and Coordinated Multiple Access Points
 Reliable Videos Broadcast with Network Coding and Coordinated Multiple Access Points Pouya Ostovari and Jie Wu Computer & Information Sciences Temple University Center for Networked Computing http://www.cnc.temple.edu
Reliable Videos Broadcast with Network Coding and Coordinated Multiple Access Points Pouya Ostovari and Jie Wu Computer & Information Sciences Temple University Center for Networked Computing http://www.cnc.temple.edu
VP3: Using Vertex Path and Power Proximity for Energy Efficient Key Distribution
 VP3: Using Vertex Path and Power Proximity for Energy Efficient Key Distribution Loukas Lazos, Javier Salido and Radha Poovendran Network Security Lab, Dept. of EE, University of Washington, Seattle, WA
VP3: Using Vertex Path and Power Proximity for Energy Efficient Key Distribution Loukas Lazos, Javier Salido and Radha Poovendran Network Security Lab, Dept. of EE, University of Washington, Seattle, WA
Radio channel measurement based evaluation method of mobile terminal diversity antennas
 HELSINKI UNIVERSITY OF TECHNOLOGY Radio laboratory SMARAD Centre of Excellence Radio channel measurement based evaluation method of mobile terminal diversity antennas S-72.333, Postgraduate Course in Radio
HELSINKI UNIVERSITY OF TECHNOLOGY Radio laboratory SMARAD Centre of Excellence Radio channel measurement based evaluation method of mobile terminal diversity antennas S-72.333, Postgraduate Course in Radio
DIGITAL INTELLIGENT POWER FACTOR REGULATOR
 An ISO 9001:2008 Comany DIGITAL INTELLIGENT POWER FACTOR REGULATOR Model - KM-PFR-9-06 / KM-PFR-9-12 The ioneers & leaders in high quality ower factor controllers & maximum demand controllers, now introduce
An ISO 9001:2008 Comany DIGITAL INTELLIGENT POWER FACTOR REGULATOR Model - KM-PFR-9-06 / KM-PFR-9-12 The ioneers & leaders in high quality ower factor controllers & maximum demand controllers, now introduce
Count the objects after you draw 1 more. Write the number in the box. Use the code to color when you are finished. Draw 1 more face. How many?
 Lesson 17 Problem Set Count the objects after you draw 1 more. Write the number in the box. Use the code to color when you are finished. 3 blue 4 red 5 yellow 6 green Draw 1 more cloud. Draw 1 more face.
Lesson 17 Problem Set Count the objects after you draw 1 more. Write the number in the box. Use the code to color when you are finished. 3 blue 4 red 5 yellow 6 green Draw 1 more cloud. Draw 1 more face.
Routing versus Network Coding in Erasure Networks with Broadcast and Interference Constraints
 Routing versus Network Coding in Erasure Networks with Broadcast and Interference Constraints Brian Smith Department of ECE University of Texas at Austin Austin, TX 7872 bsmith@ece.utexas.edu Piyush Gupta
Routing versus Network Coding in Erasure Networks with Broadcast and Interference Constraints Brian Smith Department of ECE University of Texas at Austin Austin, TX 7872 bsmith@ece.utexas.edu Piyush Gupta
LDPC Decoding: VLSI Architectures and Implementations
 LDPC Decoding: VLSI Architectures and Implementations Module : LDPC Decoding Ned Varnica varnica@gmail.com Marvell Semiconductor Inc Overview Error Correction Codes (ECC) Intro to Low-density parity-check
LDPC Decoding: VLSI Architectures and Implementations Module : LDPC Decoding Ned Varnica varnica@gmail.com Marvell Semiconductor Inc Overview Error Correction Codes (ECC) Intro to Low-density parity-check
FOUNTAIN codes [1], [2] have been introduced to achieve
![FOUNTAIN codes [1], [2] have been introduced to achieve FOUNTAIN codes [1], [2] have been introduced to achieve](/thumbs/90/103462743.jpg) Controlled Flooding of Fountain Codes Waqas bin Abbas, Paolo Casari, Senior Member, IEEE, Michele Zorzi, Fellow, IEEE Abstract We consider a multiho network where a source node must reliably deliver a
Controlled Flooding of Fountain Codes Waqas bin Abbas, Paolo Casari, Senior Member, IEEE, Michele Zorzi, Fellow, IEEE Abstract We consider a multiho network where a source node must reliably deliver a
Cellular Network Planning and Optimization Part VI: WCDMA Basics. Jyri Hämäläinen, Communications and Networking Department, TKK, 24.1.
 Cellular Network Planning and Optimization Part VI: WCDMA Basics Jyri Hämäläinen, Communications and Networking Department, TKK, 24.1.2008 Outline Network elements Physical layer Radio resource management
Cellular Network Planning and Optimization Part VI: WCDMA Basics Jyri Hämäläinen, Communications and Networking Department, TKK, 24.1.2008 Outline Network elements Physical layer Radio resource management
Basic Solution Concepts and Computational Issues
 CHAPTER asic Solution Concepts and Computational Issues Éva Tardos and Vijay V. Vazirani Abstract We consider some classical games and show how they can arise in the context of the Internet. We also introduce
CHAPTER asic Solution Concepts and Computational Issues Éva Tardos and Vijay V. Vazirani Abstract We consider some classical games and show how they can arise in the context of the Internet. We also introduce
The Gini Coefficient: An Application to Greece
 International Journal of Economics and Finance; Vol. 10, No. 3; 2018 ISSN 1916-971X E-ISSN 1916-9728 Published by Canadian Center of Science and Education The Gini Coefficient: An Alication to Greece Augustine
International Journal of Economics and Finance; Vol. 10, No. 3; 2018 ISSN 1916-971X E-ISSN 1916-9728 Published by Canadian Center of Science and Education The Gini Coefficient: An Alication to Greece Augustine
