Chapter 3: Alarm correlation
|
|
|
- Rosalyn Parsons
- 5 years ago
- Views:
Transcription
1 Chapter 3: Alarm correlation Algorithmic Methods of Data Mining, Fall 2005, Chapter 3: Alarm correlation 1 Part II. Episodes in sequences Chapter 3: Alarm correlation Chapter 4: Frequent episodes Chapter 5: Minimal occurrences of episodes Chapter 6: Episode discovery process
2 3. Alarm correlation: networks and alarms network elements: switches, base stations, transmission equipment, etc elements in a network an alarm: a message generated by a network element 1234 EL1 BTS A1 Channel missing hundreds of different alarm types alarms a day each contains only local information Algorithmic Methods of Data Mining, Fall 2005, Chapter 3: Alarm correlation 3 Characteristics of the alarm flow a variety of situations bursts of alarms hardware and software change fast
3 Alarm correlation correlating alarms: combining the fragmented information contained in the alarm sequence and interpreting the whole flow of alarms removing redundant alarms filtering out low-priority alarms replacing alarms by something else systems exist knowledge base (correlation rules) constructed manually look at the alarms occurring in a given time window apply actions given in the matching correlation rules Algorithmic Methods of Data Mining, Fall 2005, Chapter 3: Alarm correlation 5 Problem how to obtain the information needed for the preparation of an alarm correlation system more generally: how to obtain insight into the behavior of the network (alarms)
4 Solutions how to analyze a flow of alarms? lots of possibilities: hazard models, neural networks, rule-based representations comprehensibility of the discovered knowledge simple rule-based representations if certain alarms occur within a time window, then a certain alarm will also occur Algorithmic Methods of Data Mining, Fall 2005, Chapter 3: Alarm correlation 7 Episodes E F A B A B C α β γ Figure 3.2: Episodes
5 Basic solution look for repeated occurrences of episodes in the alarm flow sequences occurrence: alarms of the specified type occur in the specified order why this form? comprehensible standard for correlation systems represent simple causal relationships insensitive to inaccurate clocks allows analysis of merged, unrelated sequences Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 2 Chapter 4: Episodes
6 4. Frequent episodes The framework Algorithms Experiments Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 10 Example sequence E D F A B C E F C D B A D C E F C B E A E C F A D time Figure 3.1: A sequence of alarms Observations: whenever E occurs, F occurs soon whenever A and B occur (in either order), C occurs soon
7 Data a set R of event types an event is a pair (A,t) A R is an event type t is an integer, the (occurrence) time of the event event sequence s on R: a triple (s,t s,t e ) T s < T e are integer (starting and ending time) s = (A 1,t 1 ),(A 2,t 2 ),...,(A n,t n ) A i R and T s t i < T e for all i = 1,...,n t i t i+1 for all i = 1,...,n 1 Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 12 Example E D F A B C E F C D B A D C E F C B E A E C F A D : The example event sequence s and two windows of width 5. Figure
8 Windows event sequence s = (s,t s,t e ) a window on it: w = (w,t s,t e ) t s < T e,t e > T s w consists of those pairs (A,t) from s where t s t < t e width(w) = t e t s : the width of the window w W(s, win): all windows w on s such that width(w) = win first and last windows! Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 14 Episodes an episode α is a triple (V,,g) V is a set of nodes is a partial order on V g : V R is a mapping associating each node with an event type intuition: the events in g(v ) have to occur in the order described by size of α, denoted α, is V parallel episode: the partial order is trivial serial episode: is a total order injective: no event type occurs twice in the episode
9 Example E F α the set V, the mapping g Figure 4.2: An episode Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 16 Example, subepisode A B A B C β γ Figure 4.3: A subepisode and episode
10 Subepisodes β = (V,,g ) is a subepisode of α = (V,,g), β α, if: there exists an injective mapping f : V V such that g (v) = g(f(v)) for all v V for all v,w V with v w also f(v) f(w) An episode α is a superepisode of β if and only if β α β α if β α and α β In the example: β γ Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 18 Occurrences of episodes α = (V,,g) occurs in an event sequence s = ( (A 1,t 1 ),(A 2,t 2 ),...,(A n,t n ),T s,t e ), if there exists an injective mapping h : V {1,..., n} from nodes to events, such that g(x) = A h(x) for all x V for all x,y V with x y and x y we have t h(x) < t h(y) (or h(x) < h(y)) (w,35,40) on the example sequence: events of types A, B, C, and E both β and γ occur
11 Frequency of occurrence the frequency of an episode α in s is fr(α,s,win) = {w W(s,win) α occurs in w}, W(s, win) i.e., the fraction of windows on s in which α occurs. a frequency threshold min fr α is frequent if fr(α, s, win) min fr F(s,win,min fr): collection of frequent episodes in s with respect to win and min fr size = l: F l (s,win,min fr). Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 20 Pattern discovery task given an event sequence s, a set E of episodes, a window width win, and a frequency threshold min fr, find F(s,win,min fr)
12 Algorithms Algorithm 4.13 Input: A set R of event types, an event sequence s over R, a set E of episodes, a window width win, and a frequency threshold min fr. Output: The collection F(s, win, min fr) of frequent episodes. Method: 1. compute C 1 := {α E α = 1;} 2. l := 1; 3. while C l do 4. // Database pass (Algorithms 4.19 and 4.21): 5. compute F l (s, win, min fr) := {α C l fr(α,s, win) min fr}; 6. l := l + 1; 7. // Candidate generation (Algorithm 4.14): 8. compute C l := {α E α = l, and β F β (s, win, min fr) for all β E such that β α and β < l}; 9. for all l do output F l (s, win, min fr); Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 22 Basic lemma, once again Lemma 4.12 If an episode α is frequent in an event sequence s, then all subepisodes β α are frequent.
13 Parallel, serial, injective episodes parallel episode: the partial order is trivial (= frequent sets) serial episode: is a total order (= frequent subsequence) injective: no event type occurs twice in the episode (= proper sets, not multi sets) useful cases: (serial or parallel) [injective] episodes reduce redundancy in generated episodes keep episodes comprehensible simpler to implement Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 24 Generation of candidate episodes parallel episodes, serial episodes (injective or non-injective) same idea as for association rules a candidate episode has to be a combination of two episodes of smaller size very small variations to the candidate generation procedure
14 Recognizing episodes in sequences first problem: given a sequence and an episode, find out whether the episode occurs in the sequence finding the number of windows containing an occurrence of the episode can be reduced to this successive windows have a lot in common how to use this? an incremental algorithm Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 26 Parallel episodes for each candidate α maintain a counter α.event count: how many events of α are present in the window When α.event count becomes equal to α, indicating that α is entirely included in the window save the starting time of the window in α.inwindow when α.event count decreases again, increase the field α.freq count by the number of windows where α remained entirely in the window
15 Algorithm Input: A collection C of parallel episodes, an event sequence s = (s, T s, T e ), a window width win, and a frequency threshold min fr. Output: The episodes of C that are frequent in s with respect to win and min fr. Method: 1. // Initialization: 2. for each α in C do 3. for each A in α do 4. A.count := 0 ; 5. for i := 1 to α do contains(a, i) := ; 6. for each α in C do 7. for each A in α do 8. a := number of events of type A in α ; 9. contains(a, a) := contains(a, a) {α}; 10. α.event count := 0 ; 11. α.freq count := 0 ; Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 28 Algorithm Method: 1. // Recognition: 2. for start := T s win + 1 to T e do 3. // Bring in new events to the window: 4. for all events (A, t) in s such that t = start + win 1 do 5. A.count := A.count + 1 ; 6. for each α contains( A, A.count) do 7. α.event count := α.event count + A.count; 8. if α.event count = α then α.inwindow := start; 9. // Drop out old events from the window: 10. for all events (A, t) in s such that t = start 1 do 11. for each α contains( A, A.count) do 12. if α.event count = α then 13. α.freq count := α.freq count α.inwindow + start; 14. α.event count := α.event count A.count; 15. A.count := A.count 1 ; 16. // Output: 17. for all episodes α in C do 18. if α.freq count/(t e T s + win 1) min fr then output α;
16 Theorem 1 Algorithm 102 works correctly. Proof We consider the following two invariants. (1) For each event type A that occurs in any episode, the variable A.count correctly contains the number of events of type A in the current window. (2) For each episode α, the counter α.event count equals α exactly when α occurs in the current window. Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 30 Complexity Assume that exactly one event takes place every time unit. Assume candidate episodes are all of size l, and let n be the length of the sequence. Theorem 2 The time complexity of Algorithm 102 is O((n + l 2 ) C ). Proof Initialization takes time O( C l 2 ). How many accesses to α.event count on lines 7 and 14. In the recognition phase there are O(n) shifts of the window. In each shift, one new event comes into the window, and one old event leaves the window. Thus, for any episode α, α.event count is accessed at most twice during one shift. The cost of the recognition phase is thus O(n C ).
17 Serial episodes use state automata that accept the candidate episodes example: episode A B A B General episodes different alternatives Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 32 Injective Window Serial episodes parallel episodes width (s) Count Time (s) Count Time (s) Table 4.1: Results of experiments with s 1 using a fixed frequency threshold of and a varying window width
18 Injective Frequency Serial episodes parallel episodes threshold Count Time (s) Count Time (s) Table 4.2: Results of experiments with s 1 using a fixed window width of 60 s and a varying frequency threshold Algorithmic Methods of Data Mining, Fall 2005, Chapter 4: Episodes 34 Episode Number of Number of Number of size episodes candidate frequent Match episodes episodes % % % % % % % % % % Table 4.3: Number of candidate and frequent serial episodes in s 1 with frequency threshold and averaged over window widths 10, 20, 40, 60, 80, 100, and 120 s
19 Experiences in alarm correlation Useful in finding long-term, rather frequently occurring dependencies, creating an overview of a short-term alarm sequence, and evaluating the consistency and correctness of alarm databases discovered rules have been applied in alarm correlation lots of rules are trivial Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes3 Chapter 5: Minimal occurrences of episodes
20 5. Minimal occurrences of episodes an alternative approach to discovery of episodes no windows for each potentially interesting episode, find out the exact occurrences of the episode advantages: easy to modify time limits, several time limits for one rule ( if A and B occur within 15 seconds, then C follows within 30 seconds ) disadvantages: uses lots of space Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes 37 Definitions an episode α and an event sequence s interval [t s,t e ) is a minimal occurrence of α in s, if α occurs in the window w = (w,t s,t e ) on s α does not occur in any proper subwindow on w set of (intervals of) minimal occurrences of an episode α: mo(α) = { [t s,t e ) [t s,t e ) is a minimal occurrence of α}.
21 Example E F A B A B C α β Figure 1: Episodes. γ E D F A B C E F C D B A D C E F C B E A E C F A D Figure 2: The example event sequence s. Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes 39 β consisting of event types A and B has four minimal occurrences in s: mo(β) = {[35,38),[46,48),[47,58),[57,60)}. The partially ordered episode γ has the following three minimal occurrences: [35, 39),[46, 51),[57, 62).
22 Episodes rules, new version episode rule: β [win 1 ] α [win 2 ], β and α are episodes such that β α win 1 and win 2 are integers if episode β has a minimal occurrence at interval [t s,t e ) with t e t s win 1, then episode α occurs at interval [t s,t e) for some t e such that t e t s win 2 Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes 41 formally: mo win1 (β) = {[t s,t e ) mo(β) t e t s win 1 } given α and an interval [u s,u e ), define occ(α,[u s,u e )) = true if and only if there exists a minimal occurrence [u s,u e) mo(α) such that u s u s and u e u e The confidence of an episode rule β [win 1 ] α [win 2 ] is now {[t s,t e ) mo win1 (β) occ(α,[t s,t s + win 2 ))}. mo win1 (β)
23 Example, cont. β [3] γ [4] three minimal occurrences [35,38),[46,48),[57,60) of β of width at most 3 in the denominator Only [35,38), has an occurrence of α within width 4, so the confidence is 1/3. rule β [3] γ [5] the confidence is 1. Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes 43 Rule forms temporal relationships can be complex
24 Frequency and support previously: frequency = fraction of windows containing the episode no fixed window size several minimal occurrences within a window support of an episode: the number of minimal occurrences of an episode, mo(α) Algorithmic Methods of Data Mining, Fall 2005, Chapter 5: Minimal occurrences of episodes 45 Rule discovery task an event sequence s a class E of episodes a set W of time bounds find all frequent episode rules of the form β [win 1 ] α [win 2 ] β,α E and win 1,win 2 W.
A Fast Algorithm For Finding Frequent Episodes In Event Streams
 A Fast Algorithm For Finding Frequent Episodes In Event Streams Srivatsan Laxman Microsoft Research Labs India Bangalore slaxman@microsoft.com P. S. Sastry Indian Institute of Science Bangalore sastry@ee.iisc.ernet.in
A Fast Algorithm For Finding Frequent Episodes In Event Streams Srivatsan Laxman Microsoft Research Labs India Bangalore slaxman@microsoft.com P. S. Sastry Indian Institute of Science Bangalore sastry@ee.iisc.ernet.in
Computer Log Anomaly Detection Using Frequent Episodes
 Computer Log Anomaly Detection Using Frequent Episodes Perttu Halonen, Markus Miettinen, and Kimmo Hätönen Abstract In this paper, we propose a set of algorithms to automate the detection of anomalous
Computer Log Anomaly Detection Using Frequent Episodes Perttu Halonen, Markus Miettinen, and Kimmo Hätönen Abstract In this paper, we propose a set of algorithms to automate the detection of anomalous
Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011
 Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011 Lecture 9 In which we introduce the maximum flow problem. 1 Flows in Networks Today we start talking about the Maximum Flow
Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011 Lecture 9 In which we introduce the maximum flow problem. 1 Flows in Networks Today we start talking about the Maximum Flow
Similarly, the point marked in red below is a local minimum for the function, since there are no points nearby that are lower than it:
 Extreme Values of Multivariate Functions Our next task is to develop a method for determining local extremes of multivariate functions, as well as absolute extremes of multivariate functions on closed
Extreme Values of Multivariate Functions Our next task is to develop a method for determining local extremes of multivariate functions, as well as absolute extremes of multivariate functions on closed
Communication Theory II
 Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Information Theory and Communication Optimal Codes
 Information Theory and Communication Optimal Codes Ritwik Banerjee rbanerjee@cs.stonybrook.edu c Ritwik Banerjee Information Theory and Communication 1/1 Roadmap Examples and Types of Codes Kraft Inequality
Information Theory and Communication Optimal Codes Ritwik Banerjee rbanerjee@cs.stonybrook.edu c Ritwik Banerjee Information Theory and Communication 1/1 Roadmap Examples and Types of Codes Kraft Inequality
SOLITAIRE CLOBBER AS AN OPTIMIZATION PROBLEM ON WORDS
 INTEGERS: ELECTRONIC JOURNAL OF COMBINATORIAL NUMBER THEORY 8 (2008), #G04 SOLITAIRE CLOBBER AS AN OPTIMIZATION PROBLEM ON WORDS Vincent D. Blondel Department of Mathematical Engineering, Université catholique
INTEGERS: ELECTRONIC JOURNAL OF COMBINATORIAL NUMBER THEORY 8 (2008), #G04 SOLITAIRE CLOBBER AS AN OPTIMIZATION PROBLEM ON WORDS Vincent D. Blondel Department of Mathematical Engineering, Université catholique
The Capability of Error Correction for Burst-noise Channels Using Error Estimating Code
 The Capability of Error Correction for Burst-noise Channels Using Error Estimating Code Yaoyu Wang Nanjing University yaoyu.wang.nju@gmail.com June 10, 2016 Yaoyu Wang (NJU) Error correction with EEC June
The Capability of Error Correction for Burst-noise Channels Using Error Estimating Code Yaoyu Wang Nanjing University yaoyu.wang.nju@gmail.com June 10, 2016 Yaoyu Wang (NJU) Error correction with EEC June
CCO Commun. Comb. Optim.
 Communications in Combinatorics and Optimization Vol. 2 No. 2, 2017 pp.149-159 DOI: 10.22049/CCO.2017.25918.1055 CCO Commun. Comb. Optim. Graceful labelings of the generalized Petersen graphs Zehui Shao
Communications in Combinatorics and Optimization Vol. 2 No. 2, 2017 pp.149-159 DOI: 10.22049/CCO.2017.25918.1055 CCO Commun. Comb. Optim. Graceful labelings of the generalized Petersen graphs Zehui Shao
Sensors, Signals and Noise
 Sensors, Signals and Noise COURSE OUTLINE Introduction Signals and Noise Filtering Noise Sensors and associated electronics Sergio Cova SENSORS SIGNALS AND NOISE SSN04b FILTERING NOISE rv 2017/01/25 1
Sensors, Signals and Noise COURSE OUTLINE Introduction Signals and Noise Filtering Noise Sensors and associated electronics Sergio Cova SENSORS SIGNALS AND NOISE SSN04b FILTERING NOISE rv 2017/01/25 1
Near-Optimal Radio Use For Wireless Network Synch. Synchronization
 Near-Optimal Radio Use For Wireless Network Synchronization LANL, UCLA 10th of July, 2009 Motivation Consider sensor network: tiny, inexpensive embedded computers run complex software sense environmental
Near-Optimal Radio Use For Wireless Network Synchronization LANL, UCLA 10th of July, 2009 Motivation Consider sensor network: tiny, inexpensive embedded computers run complex software sense environmental
Graphs and Network Flows IE411. Lecture 14. Dr. Ted Ralphs
 Graphs and Network Flows IE411 Lecture 14 Dr. Ted Ralphs IE411 Lecture 14 1 Review: Labeling Algorithm Pros Guaranteed to solve any max flow problem with integral arc capacities Provides constructive tool
Graphs and Network Flows IE411 Lecture 14 Dr. Ted Ralphs IE411 Lecture 14 1 Review: Labeling Algorithm Pros Guaranteed to solve any max flow problem with integral arc capacities Provides constructive tool
1. Functions and set sizes 2. Infinite set sizes. ! Let X,Y be finite sets, f:x!y a function. ! Theorem: If f is injective then X Y.
 2 Today s Topics: CSE 20: Discrete Mathematics for Computer Science Prof. Miles Jones 1. Functions and set sizes 2. 3 4 1. Functions and set sizes! Theorem: If f is injective then Y.! Try and prove yourself
2 Today s Topics: CSE 20: Discrete Mathematics for Computer Science Prof. Miles Jones 1. Functions and set sizes 2. 3 4 1. Functions and set sizes! Theorem: If f is injective then Y.! Try and prove yourself
Association Rule Mining. Entscheidungsunterstützungssysteme SS 18
 Association Rule Mining Entscheidungsunterstützungssysteme SS 18 Frequent Pattern Analysis Frequent pattern: a pattern (a set of items, subsequences, substructures, etc.) that occurs frequently in a data
Association Rule Mining Entscheidungsunterstützungssysteme SS 18 Frequent Pattern Analysis Frequent pattern: a pattern (a set of items, subsequences, substructures, etc.) that occurs frequently in a data
Bit Reversal Broadcast Scheduling for Ad Hoc Systems
 Bit Reversal Broadcast Scheduling for Ad Hoc Systems Marcin Kik, Maciej Gebala, Mirosław Wrocław University of Technology, Poland IDCS 2013, Hangzhou How to broadcast efficiently? Broadcasting ad hoc systems
Bit Reversal Broadcast Scheduling for Ad Hoc Systems Marcin Kik, Maciej Gebala, Mirosław Wrocław University of Technology, Poland IDCS 2013, Hangzhou How to broadcast efficiently? Broadcasting ad hoc systems
Sets. Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, Outline Sets Equality Subset Empty Set Cardinality Power Set
 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, 2012 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) Gazihan Alankuş (Based on original slides by Brahim Hnich
Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, 2012 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) Gazihan Alankuş (Based on original slides by Brahim Hnich
By Scott Fallstrom and Brent Pickett The How and Whys Guys
 Math Fundamentals for Statistics I (Math 52) Unit 2:Number Line and Ordering By Scott Fallstrom and Brent Pickett The How and Whys Guys This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike
Math Fundamentals for Statistics I (Math 52) Unit 2:Number Line and Ordering By Scott Fallstrom and Brent Pickett The How and Whys Guys This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike
Avoiding consecutive patterns in permutations
 Avoiding consecutive patterns in permutations R. E. L. Aldred M. D. Atkinson D. J. McCaughan January 3, 2009 Abstract The number of permutations that do not contain, as a factor (subword), a given set
Avoiding consecutive patterns in permutations R. E. L. Aldred M. D. Atkinson D. J. McCaughan January 3, 2009 Abstract The number of permutations that do not contain, as a factor (subword), a given set
Weighted Polya Theorem. Solitaire
 Weighted Polya Theorem. Solitaire Sasha Patotski Cornell University ap744@cornell.edu December 15, 2015 Sasha Patotski (Cornell University) Weighted Polya Theorem. Solitaire December 15, 2015 1 / 15 Cosets
Weighted Polya Theorem. Solitaire Sasha Patotski Cornell University ap744@cornell.edu December 15, 2015 Sasha Patotski (Cornell University) Weighted Polya Theorem. Solitaire December 15, 2015 1 / 15 Cosets
Broadcast in Radio Networks in the presence of Byzantine Adversaries
 Broadcast in Radio Networks in the presence of Byzantine Adversaries Vinod Vaikuntanathan Abstract In PODC 0, Koo [] presented a protocol that achieves broadcast in a radio network tolerating (roughly)
Broadcast in Radio Networks in the presence of Byzantine Adversaries Vinod Vaikuntanathan Abstract In PODC 0, Koo [] presented a protocol that achieves broadcast in a radio network tolerating (roughly)
Some results on Su Doku
 Some results on Su Doku Sourendu Gupta March 2, 2006 1 Proofs of widely known facts Definition 1. A Su Doku grid contains M M cells laid out in a square with M cells to each side. Definition 2. For every
Some results on Su Doku Sourendu Gupta March 2, 2006 1 Proofs of widely known facts Definition 1. A Su Doku grid contains M M cells laid out in a square with M cells to each side. Definition 2. For every
Game Theory and Algorithms Lecture 19: Nim & Impartial Combinatorial Games
 Game Theory and Algorithms Lecture 19: Nim & Impartial Combinatorial Games May 17, 2011 Summary: We give a winning strategy for the counter-taking game called Nim; surprisingly, it involves computations
Game Theory and Algorithms Lecture 19: Nim & Impartial Combinatorial Games May 17, 2011 Summary: We give a winning strategy for the counter-taking game called Nim; surprisingly, it involves computations
Algorithms and Data Structures CS 372. The Sorting Problem. Insertion Sort - Summary. Merge Sort. Input: Output:
 Algorithms and Data Structures CS Merge Sort (Based on slides by M. Nicolescu) The Sorting Problem Input: A sequence of n numbers a, a,..., a n Output: A permutation (reordering) a, a,..., a n of the input
Algorithms and Data Structures CS Merge Sort (Based on slides by M. Nicolescu) The Sorting Problem Input: A sequence of n numbers a, a,..., a n Output: A permutation (reordering) a, a,..., a n of the input
NON-OVERLAPPING PERMUTATION PATTERNS. To Doron Zeilberger, for his Sixtieth Birthday
 NON-OVERLAPPING PERMUTATION PATTERNS MIKLÓS BÓNA Abstract. We show a way to compute, to a high level of precision, the probability that a randomly selected permutation of length n is nonoverlapping. As
NON-OVERLAPPING PERMUTATION PATTERNS MIKLÓS BÓNA Abstract. We show a way to compute, to a high level of precision, the probability that a randomly selected permutation of length n is nonoverlapping. As
Comm. 502: Communication Theory. Lecture 6. - Introduction to Source Coding
 Comm. 50: Communication Theory Lecture 6 - Introduction to Source Coding Digital Communication Systems Source of Information User of Information Source Encoder Source Decoder Channel Encoder Channel Decoder
Comm. 50: Communication Theory Lecture 6 - Introduction to Source Coding Digital Communication Systems Source of Information User of Information Source Encoder Source Decoder Channel Encoder Channel Decoder
Notes for Recitation 3
 6.042/18.062J Mathematics for Computer Science September 17, 2010 Tom Leighton, Marten van Dijk Notes for Recitation 3 1 State Machines Recall from Lecture 3 (9/16) that an invariant is a property of a
6.042/18.062J Mathematics for Computer Science September 17, 2010 Tom Leighton, Marten van Dijk Notes for Recitation 3 1 State Machines Recall from Lecture 3 (9/16) that an invariant is a property of a
UMLEmb: UML for Embedded Systems. II. Modeling in SysML. Eurecom
 UMLEmb: UML for Embedded Systems II. Modeling in SysML Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Eurecom, office 470 http://soc.eurecom.fr/umlemb/ @UMLEmb Eurecom Goals Learning objective
UMLEmb: UML for Embedded Systems II. Modeling in SysML Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Eurecom, office 470 http://soc.eurecom.fr/umlemb/ @UMLEmb Eurecom Goals Learning objective
Cardinality and Bijections
 Countable and Cardinality and Bijections Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 13, 2012 Countable and Countable and Countable and How to count elements in a set? How
Countable and Cardinality and Bijections Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 13, 2012 Countable and Countable and Countable and How to count elements in a set? How
Reinforcement Learning in Games Autonomous Learning Systems Seminar
 Reinforcement Learning in Games Autonomous Learning Systems Seminar Matthias Zöllner Intelligent Autonomous Systems TU-Darmstadt zoellner@rbg.informatik.tu-darmstadt.de Betreuer: Gerhard Neumann Abstract
Reinforcement Learning in Games Autonomous Learning Systems Seminar Matthias Zöllner Intelligent Autonomous Systems TU-Darmstadt zoellner@rbg.informatik.tu-darmstadt.de Betreuer: Gerhard Neumann Abstract
Today. Nondeterministic games: backgammon. Algorithm for nondeterministic games. Nondeterministic games in general. See Russell and Norvig, chapter 6
 Today See Russell and Norvig, chapter Game playing Nondeterministic games Games with imperfect information Nondeterministic games: backgammon 5 8 9 5 9 8 5 Nondeterministic games in general In nondeterministic
Today See Russell and Norvig, chapter Game playing Nondeterministic games Games with imperfect information Nondeterministic games: backgammon 5 8 9 5 9 8 5 Nondeterministic games in general In nondeterministic
Improving Automatic Confluence Analysis of Rewrite Systems by Redundant Rules
 Improving Automatic Confluence Analysis of Rewrite Systems by Redundant Rules Julian Nagele Bertram Felgenhauer Aart Middeldorp University of Innsbruck, Austria 26th RTA 1 July 2015 Outline Motivation
Improving Automatic Confluence Analysis of Rewrite Systems by Redundant Rules Julian Nagele Bertram Felgenhauer Aart Middeldorp University of Innsbruck, Austria 26th RTA 1 July 2015 Outline Motivation
Math Fundamentals for Statistics (Math 52) Unit 2:Number Line and Ordering. By Scott Fallstrom and Brent Pickett The How and Whys Guys.
 Math Fundamentals for Statistics (Math 52) Unit 2:Number Line and Ordering By Scott Fallstrom and Brent Pickett The How and Whys Guys Unit 2 Page 1 2.1: Place Values We just looked at graphing ordered
Math Fundamentals for Statistics (Math 52) Unit 2:Number Line and Ordering By Scott Fallstrom and Brent Pickett The How and Whys Guys Unit 2 Page 1 2.1: Place Values We just looked at graphing ordered
Two-Player Tower of Hanoi
 Two-Player Tower of Hanoi Jonathan Chappelon, Urban Larsson, Akihiro Matsuura To cite this version: Jonathan Chappelon, Urban Larsson, Akihiro Matsuura. Two-Player Tower of Hanoi. 16 pages, 6 figures,
Two-Player Tower of Hanoi Jonathan Chappelon, Urban Larsson, Akihiro Matsuura To cite this version: Jonathan Chappelon, Urban Larsson, Akihiro Matsuura. Two-Player Tower of Hanoi. 16 pages, 6 figures,
Mental rehearsal to enhance navigation learning.
 Mental rehearsal to enhance navigation learning. K.Verschuren July 12, 2010 Student name Koen Verschuren Telephone 0612214854 Studentnumber 0504289 E-mail adress Supervisors K.Verschuren@student.ru.nl
Mental rehearsal to enhance navigation learning. K.Verschuren July 12, 2010 Student name Koen Verschuren Telephone 0612214854 Studentnumber 0504289 E-mail adress Supervisors K.Verschuren@student.ru.nl
Secondary Transmission Profile for a Single-band Cognitive Interference Channel
 Secondary Transmission rofile for a Single-band Cognitive Interference Channel Debashis Dash and Ashutosh Sabharwal Department of Electrical and Computer Engineering, Rice University Email:{ddash,ashu}@rice.edu
Secondary Transmission rofile for a Single-band Cognitive Interference Channel Debashis Dash and Ashutosh Sabharwal Department of Electrical and Computer Engineering, Rice University Email:{ddash,ashu}@rice.edu
Computational aspects of two-player zero-sum games Course notes for Computational Game Theory Section 3 Fall 2010
 Computational aspects of two-player zero-sum games Course notes for Computational Game Theory Section 3 Fall 21 Peter Bro Miltersen November 1, 21 Version 1.3 3 Extensive form games (Game Trees, Kuhn Trees)
Computational aspects of two-player zero-sum games Course notes for Computational Game Theory Section 3 Fall 21 Peter Bro Miltersen November 1, 21 Version 1.3 3 Extensive form games (Game Trees, Kuhn Trees)
Handling Search Inconsistencies in MTD(f)
 Handling Search Inconsistencies in MTD(f) Jan-Jaap van Horssen 1 February 2018 Abstract Search inconsistencies (or search instability) caused by the use of a transposition table (TT) constitute a well-known
Handling Search Inconsistencies in MTD(f) Jan-Jaap van Horssen 1 February 2018 Abstract Search inconsistencies (or search instability) caused by the use of a transposition table (TT) constitute a well-known
AN ALTERNATIVE METHOD FOR ASSOCIATION RULES
 AN ALTERNATIVE METHOD FOR ASSOCIATION RULES RECAP Mining Frequent Itemsets Itemset A collection of one or more items Example: {Milk, Bread, Diaper} k-itemset An itemset that contains k items Support (
AN ALTERNATIVE METHOD FOR ASSOCIATION RULES RECAP Mining Frequent Itemsets Itemset A collection of one or more items Example: {Milk, Bread, Diaper} k-itemset An itemset that contains k items Support (
Exploiting the disjoint cycle decomposition in genome rearrangements
 Exploiting the disjoint cycle decomposition in genome rearrangements Jean-Paul Doignon Anthony Labarre 1 doignon@ulb.ac.be alabarre@ulb.ac.be Université Libre de Bruxelles June 7th, 2007 Ordinal and Symbolic
Exploiting the disjoint cycle decomposition in genome rearrangements Jean-Paul Doignon Anthony Labarre 1 doignon@ulb.ac.be alabarre@ulb.ac.be Université Libre de Bruxelles June 7th, 2007 Ordinal and Symbolic
14.2 Limits and Continuity
 14 Partial Derivatives 14.2 Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Let s compare the behavior of the functions Tables 1 2 show values of f(x,
14 Partial Derivatives 14.2 Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Let s compare the behavior of the functions Tables 1 2 show values of f(x,
Ma/CS 6a Class 16: Permutations
 Ma/CS 6a Class 6: Permutations By Adam Sheffer The 5 Puzzle Problem. Start with the configuration on the left and move the tiles to obtain the configuration on the right. The 5 Puzzle (cont.) The game
Ma/CS 6a Class 6: Permutations By Adam Sheffer The 5 Puzzle Problem. Start with the configuration on the left and move the tiles to obtain the configuration on the right. The 5 Puzzle (cont.) The game
What is a Sorting Function?
 Department of Computer Science University of Copenhagen Email: henglein@diku.dk WG 2.8 2008, Park City, June 15-22, 2008 Outline 1 Sorting algorithms Literature definitions What is a sorting criterion?
Department of Computer Science University of Copenhagen Email: henglein@diku.dk WG 2.8 2008, Park City, June 15-22, 2008 Outline 1 Sorting algorithms Literature definitions What is a sorting criterion?
Yale University Department of Computer Science
 LUX ETVERITAS Yale University Department of Computer Science Secret Bit Transmission Using a Random Deal of Cards Michael J. Fischer Michael S. Paterson Charles Rackoff YALEU/DCS/TR-792 May 1990 This work
LUX ETVERITAS Yale University Department of Computer Science Secret Bit Transmission Using a Random Deal of Cards Michael J. Fischer Michael S. Paterson Charles Rackoff YALEU/DCS/TR-792 May 1990 This work
Game-Playing & Adversarial Search
 Game-Playing & Adversarial Search This lecture topic: Game-Playing & Adversarial Search (two lectures) Chapter 5.1-5.5 Next lecture topic: Constraint Satisfaction Problems (two lectures) Chapter 6.1-6.4,
Game-Playing & Adversarial Search This lecture topic: Game-Playing & Adversarial Search (two lectures) Chapter 5.1-5.5 Next lecture topic: Constraint Satisfaction Problems (two lectures) Chapter 6.1-6.4,
The Math Behind Futurama: The Prisoner of Benda
 of Benda May 7, 2013 The problem (informally) Professor Farnsworth has created a mind-switching machine that switches two bodies, but the switching can t be reversed using just those two bodies. Using
of Benda May 7, 2013 The problem (informally) Professor Farnsworth has created a mind-switching machine that switches two bodies, but the switching can t be reversed using just those two bodies. Using
1 This work was partially supported by NSF Grant No. CCR , and by the URI International Engineering Program.
 Combined Error Correcting and Compressing Codes Extended Summary Thomas Wenisch Peter F. Swaszek Augustus K. Uht 1 University of Rhode Island, Kingston RI Submitted to International Symposium on Information
Combined Error Correcting and Compressing Codes Extended Summary Thomas Wenisch Peter F. Swaszek Augustus K. Uht 1 University of Rhode Island, Kingston RI Submitted to International Symposium on Information
Monitoring Churn in Wireless Networks
 Monitoring Churn in Wireless Networks Stephan Holzer 1 Yvonne-Anne Pignolet 2 Jasmin Smula 1 Roger Wattenhofer 1 {stholzer, smulaj, wattenhofer}@tik.ee.ethz.ch, yvonne-anne.pignolet@ch.abb.com 1 Computer
Monitoring Churn in Wireless Networks Stephan Holzer 1 Yvonne-Anne Pignolet 2 Jasmin Smula 1 Roger Wattenhofer 1 {stholzer, smulaj, wattenhofer}@tik.ee.ethz.ch, yvonne-anne.pignolet@ch.abb.com 1 Computer
An Enhanced Fast Multi-Radio Rendezvous Algorithm in Heterogeneous Cognitive Radio Networks
 1 An Enhanced Fast Multi-Radio Rendezvous Algorithm in Heterogeneous Cognitive Radio Networks Yeh-Cheng Chang, Cheng-Shang Chang and Jang-Ping Sheu Department of Computer Science and Institute of Communications
1 An Enhanced Fast Multi-Radio Rendezvous Algorithm in Heterogeneous Cognitive Radio Networks Yeh-Cheng Chang, Cheng-Shang Chang and Jang-Ping Sheu Department of Computer Science and Institute of Communications
Enumeration of Two Particular Sets of Minimal Permutations
 3 47 6 3 Journal of Integer Sequences, Vol. 8 (05), Article 5.0. Enumeration of Two Particular Sets of Minimal Permutations Stefano Bilotta, Elisabetta Grazzini, and Elisa Pergola Dipartimento di Matematica
3 47 6 3 Journal of Integer Sequences, Vol. 8 (05), Article 5.0. Enumeration of Two Particular Sets of Minimal Permutations Stefano Bilotta, Elisabetta Grazzini, and Elisa Pergola Dipartimento di Matematica
Libyan Licenses Plate Recognition Using Template Matching Method
 Journal of Computer and Communications, 2016, 4, 62-71 Published Online May 2016 in SciRes. http://www.scirp.org/journal/jcc http://dx.doi.org/10.4236/jcc.2016.47009 Libyan Licenses Plate Recognition Using
Journal of Computer and Communications, 2016, 4, 62-71 Published Online May 2016 in SciRes. http://www.scirp.org/journal/jcc http://dx.doi.org/10.4236/jcc.2016.47009 Libyan Licenses Plate Recognition Using
LECTURE 19 - LAGRANGE MULTIPLIERS
 LECTURE 9 - LAGRANGE MULTIPLIERS CHRIS JOHNSON Abstract. In this lecture we ll describe a way of solving certain optimization problems subject to constraints. This method, known as Lagrange multipliers,
LECTURE 9 - LAGRANGE MULTIPLIERS CHRIS JOHNSON Abstract. In this lecture we ll describe a way of solving certain optimization problems subject to constraints. This method, known as Lagrange multipliers,
Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility
 Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility theorem (consistent decisions under uncertainty should
Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility theorem (consistent decisions under uncertainty should
Powerline Communication Link and below Layers
 Powerline Communication Link and below Layers Notes by Rui Wang June 11, 2008 Introduction 2 Introduction.................................................................. 3 Introduction..................................................................
Powerline Communication Link and below Layers Notes by Rui Wang June 11, 2008 Introduction 2 Introduction.................................................................. 3 Introduction..................................................................
A Problem in Real-Time Data Compression: Sunil Ashtaputre. Jo Perry. and. Carla Savage. Center for Communications and Signal Processing
 A Problem in Real-Time Data Compression: How to Keep the Data Flowing at a Regular Rate by Sunil Ashtaputre Jo Perry and Carla Savage Center for Communications and Signal Processing Department of Computer
A Problem in Real-Time Data Compression: How to Keep the Data Flowing at a Regular Rate by Sunil Ashtaputre Jo Perry and Carla Savage Center for Communications and Signal Processing Department of Computer
EEE 309 Communication Theory
 EEE 309 Communication Theory Semester: January 2016 Dr. Md. Farhad Hossain Associate Professor Department of EEE, BUET Email: mfarhadhossain@eee.buet.ac.bd Office: ECE 331, ECE Building Part 05 Pulse Code
EEE 309 Communication Theory Semester: January 2016 Dr. Md. Farhad Hossain Associate Professor Department of EEE, BUET Email: mfarhadhossain@eee.buet.ac.bd Office: ECE 331, ECE Building Part 05 Pulse Code
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Algorithmic Game Theory Date: 12/6/18
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Algorithmic Game Theory Date: 12/6/18 24.1 Introduction Today we re going to spend some time discussing game theory and algorithms.
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Algorithmic Game Theory Date: 12/6/18 24.1 Introduction Today we re going to spend some time discussing game theory and algorithms.
5.4 Imperfect, Real-Time Decisions
 5.4 Imperfect, Real-Time Decisions Searching through the whole (pruned) game tree is too inefficient for any realistic game Moves must be made in a reasonable amount of time One has to cut off the generation
5.4 Imperfect, Real-Time Decisions Searching through the whole (pruned) game tree is too inefficient for any realistic game Moves must be made in a reasonable amount of time One has to cut off the generation
Scheduling. Radek Mařík. April 28, 2015 FEE CTU, K Radek Mařík Scheduling April 28, / 48
 Scheduling Radek Mařík FEE CTU, K13132 April 28, 2015 Radek Mařík (marikr@fel.cvut.cz) Scheduling April 28, 2015 1 / 48 Outline 1 Introduction to Scheduling Methodology Overview 2 Classification of Scheduling
Scheduling Radek Mařík FEE CTU, K13132 April 28, 2015 Radek Mařík (marikr@fel.cvut.cz) Scheduling April 28, 2015 1 / 48 Outline 1 Introduction to Scheduling Methodology Overview 2 Classification of Scheduling
Analog to Digital Conversion
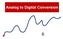 Analog to Digital Conversion 02534567998 6 4 2 3 4 5 6 ANALOG to DIGITAL CONVERSION Analog variation (Continuous, smooth variation) Digitized Variation (Discrete set of points) N2 N1 Digitization applied
Analog to Digital Conversion 02534567998 6 4 2 3 4 5 6 ANALOG to DIGITAL CONVERSION Analog variation (Continuous, smooth variation) Digitized Variation (Discrete set of points) N2 N1 Digitization applied
TD-Leaf(λ) Giraffe: Using Deep Reinforcement Learning to Play Chess. Stefan Lüttgen
 TD-Leaf(λ) Giraffe: Using Deep Reinforcement Learning to Play Chess Stefan Lüttgen Motivation Learn to play chess Computer approach different than human one Humans search more selective: Kasparov (3-5
TD-Leaf(λ) Giraffe: Using Deep Reinforcement Learning to Play Chess Stefan Lüttgen Motivation Learn to play chess Computer approach different than human one Humans search more selective: Kasparov (3-5
Information flow over wireless networks: a deterministic approach
 Information flow over wireless networks: a deterministic approach alman Avestimehr In collaboration with uhas iggavi (EPFL) and avid Tse (UC Berkeley) Overview Point-to-point channel Information theory
Information flow over wireless networks: a deterministic approach alman Avestimehr In collaboration with uhas iggavi (EPFL) and avid Tse (UC Berkeley) Overview Point-to-point channel Information theory
Compositional Analysis Framework using EDP Resource Models
 University of Pennsylvania ScholarlyCommons Departmental Papers (CIS) Department of Computer & Information Science December 2007 Compositional Analysis Framework using EDP Resource Models Arvind Easwaran
University of Pennsylvania ScholarlyCommons Departmental Papers (CIS) Department of Computer & Information Science December 2007 Compositional Analysis Framework using EDP Resource Models Arvind Easwaran
Huffman Coding - A Greedy Algorithm. Slides based on Kevin Wayne / Pearson-Addison Wesley
 - A Greedy Algorithm Slides based on Kevin Wayne / Pearson-Addison Wesley Greedy Algorithms Greedy Algorithms Build up solutions in small steps Make local decisions Previous decisions are never reconsidered
- A Greedy Algorithm Slides based on Kevin Wayne / Pearson-Addison Wesley Greedy Algorithms Greedy Algorithms Build up solutions in small steps Make local decisions Previous decisions are never reconsidered
Alert: An Adaptive Low-Latency Event-Driven MAC Protocol for Wireless Sensor Networks
 Alert: An Adaptive Low-Latency Event-Driven MAC Protocol for Wireless Sensor Networks Vinod Namboodiri Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA vnambood@ecs.umass.edu
Alert: An Adaptive Low-Latency Event-Driven MAC Protocol for Wireless Sensor Networks Vinod Namboodiri Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA vnambood@ecs.umass.edu
Transport Capacity and Spectral Efficiency of Large Wireless CDMA Ad Hoc Networks
 Transport Capacity and Spectral Efficiency of Large Wireless CDMA Ad Hoc Networks Yi Sun Department of Electrical Engineering The City College of City University of New York Acknowledgement: supported
Transport Capacity and Spectral Efficiency of Large Wireless CDMA Ad Hoc Networks Yi Sun Department of Electrical Engineering The City College of City University of New York Acknowledgement: supported
Circular Nim Games. S. Heubach 1 M. Dufour 2. May 7, 2010 Math Colloquium, Cal Poly San Luis Obispo
 Circular Nim Games S. Heubach 1 M. Dufour 2 1 Dept. of Mathematics, California State University Los Angeles 2 Dept. of Mathematics, University of Quebeq, Montreal May 7, 2010 Math Colloquium, Cal Poly
Circular Nim Games S. Heubach 1 M. Dufour 2 1 Dept. of Mathematics, California State University Los Angeles 2 Dept. of Mathematics, University of Quebeq, Montreal May 7, 2010 Math Colloquium, Cal Poly
THE use of balanced codes is crucial for some information
 A Construction for Balancing Non-Binary Sequences Based on Gray Code Prefixes Elie N. Mambou and Theo G. Swart, Senior Member, IEEE arxiv:70.008v [cs.it] Jun 07 Abstract We introduce a new construction
A Construction for Balancing Non-Binary Sequences Based on Gray Code Prefixes Elie N. Mambou and Theo G. Swart, Senior Member, IEEE arxiv:70.008v [cs.it] Jun 07 Abstract We introduce a new construction
6. FUNDAMENTALS OF CHANNEL CODER
 82 6. FUNDAMENTALS OF CHANNEL CODER 6.1 INTRODUCTION The digital information can be transmitted over the channel using different signaling schemes. The type of the signal scheme chosen mainly depends on
82 6. FUNDAMENTALS OF CHANNEL CODER 6.1 INTRODUCTION The digital information can be transmitted over the channel using different signaling schemes. The type of the signal scheme chosen mainly depends on
Pattern Avoidance in Poset Permutations
 Pattern Avoidance in Poset Permutations Sam Hopkins and Morgan Weiler Massachusetts Institute of Technology and University of California, Berkeley Permutation Patterns, Paris; July 5th, 2013 1 Definitions
Pattern Avoidance in Poset Permutations Sam Hopkins and Morgan Weiler Massachusetts Institute of Technology and University of California, Berkeley Permutation Patterns, Paris; July 5th, 2013 1 Definitions
A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks
 MIC2005: The Sixth Metaheuristics International Conference??-1 A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks Clayton Commander Carlos A.S. Oliveira Panos M. Pardalos Mauricio
MIC2005: The Sixth Metaheuristics International Conference??-1 A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks Clayton Commander Carlos A.S. Oliveira Panos M. Pardalos Mauricio
Narrow misère Dots-and-Boxes
 Games of No Chance 4 MSRI Publications Volume 63, 05 Narrow misère Dots-and-Boxes SÉBASTIEN COLLETTE, ERIK D. DEMAINE, MARTIN L. DEMAINE AND STEFAN LANGERMAN We study misère Dots-and-Boxes, where the goal
Games of No Chance 4 MSRI Publications Volume 63, 05 Narrow misère Dots-and-Boxes SÉBASTIEN COLLETTE, ERIK D. DEMAINE, MARTIN L. DEMAINE AND STEFAN LANGERMAN We study misère Dots-and-Boxes, where the goal
Non-overlapping permutation patterns
 PU. M. A. Vol. 22 (2011), No.2, pp. 99 105 Non-overlapping permutation patterns Miklós Bóna Department of Mathematics University of Florida 358 Little Hall, PO Box 118105 Gainesville, FL 326118105 (USA)
PU. M. A. Vol. 22 (2011), No.2, pp. 99 105 Non-overlapping permutation patterns Miklós Bóna Department of Mathematics University of Florida 358 Little Hall, PO Box 118105 Gainesville, FL 326118105 (USA)
Game Theory and Randomized Algorithms
 Game Theory and Randomized Algorithms Guy Aridor Game theory is a set of tools that allow us to understand how decisionmakers interact with each other. It has practical applications in economics, international
Game Theory and Randomized Algorithms Guy Aridor Game theory is a set of tools that allow us to understand how decisionmakers interact with each other. It has practical applications in economics, international
VLSI Design Verification and Test Delay Faults II CMPE 646
 Path Counting The number of paths can be an exponential function of the # of gates. Parallel multipliers are notorious for having huge numbers of paths. It is possible to efficiently count paths in spite
Path Counting The number of paths can be an exponential function of the # of gates. Parallel multipliers are notorious for having huge numbers of paths. It is possible to efficiently count paths in spite
Eric Duchêne (Univ. Claude Bernard Lyon 1) Michel Rigo (University of Liège)
 INVARIANT GAMES Eric Duchêne (Univ. Claude Bernard Lyon 1) Michel Rigo (University of Liège) http://www.discmath.ulg.ac.be/ Words 2009, Univ. of Salerno, 14th September 2009 COMBINATORIAL GAME THEORY FOR
INVARIANT GAMES Eric Duchêne (Univ. Claude Bernard Lyon 1) Michel Rigo (University of Liège) http://www.discmath.ulg.ac.be/ Words 2009, Univ. of Salerno, 14th September 2009 COMBINATORIAL GAME THEORY FOR
CONTINUOUS DIGITAL CALIBRATION OF PIPELINED A/D CONVERTERS
 CONTINUOUS DIGITAL CALIBRATION OF PIPELINED A/D CONVERTERS By Alma Delić-Ibukić B.S. University of Maine, 2002 A THESIS Submitted in Partial Fulfillment of the Requirements for the Degree of Master of
CONTINUOUS DIGITAL CALIBRATION OF PIPELINED A/D CONVERTERS By Alma Delić-Ibukić B.S. University of Maine, 2002 A THESIS Submitted in Partial Fulfillment of the Requirements for the Degree of Master of
Error Detection and Correction
 . Error Detection and Companies, 27 CHAPTER Error Detection and Networks must be able to transfer data from one device to another with acceptable accuracy. For most applications, a system must guarantee
. Error Detection and Companies, 27 CHAPTER Error Detection and Networks must be able to transfer data from one device to another with acceptable accuracy. For most applications, a system must guarantee
Spatial-Temporal Data Mining in Traffic Incident Detection
 Spatial-Temporal Data Mining in Traffic Incident Detection Ying Jin, Jing Dai, Chang-Tien Lu Department of Computer Science, Virginia Polytechnic Institute and State University {jiny, daij, ctlu}@vt.edu
Spatial-Temporal Data Mining in Traffic Incident Detection Ying Jin, Jing Dai, Chang-Tien Lu Department of Computer Science, Virginia Polytechnic Institute and State University {jiny, daij, ctlu}@vt.edu
Color of Interference and Joint Encoding and Medium Access in Large Wireless Networks
 Color of Interference and Joint Encoding and Medium Access in Large Wireless Networks Nithin Sugavanam, C. Emre Koksal, Atilla Eryilmaz Department of Electrical and Computer Engineering The Ohio State
Color of Interference and Joint Encoding and Medium Access in Large Wireless Networks Nithin Sugavanam, C. Emre Koksal, Atilla Eryilmaz Department of Electrical and Computer Engineering The Ohio State
Parsimony II Search Algorithms
 Parsimony II Search Algorithms Genome 373 Genomic Informatics Elhanan Borenstein Raw distance correction As two DNA sequences diverge, it is easy to see that their maximum raw distance is ~0.75 (assuming
Parsimony II Search Algorithms Genome 373 Genomic Informatics Elhanan Borenstein Raw distance correction As two DNA sequences diverge, it is easy to see that their maximum raw distance is ~0.75 (assuming
Outline for this presentation. Introduction I -- background. Introduction I Background
 Mining Spectrum Usage Data: A Large-Scale Spectrum Measurement Study Sixing Yin, Dawei Chen, Qian Zhang, Mingyan Liu, Shufang Li Outline for this presentation! Introduction! Methodology! Statistic and
Mining Spectrum Usage Data: A Large-Scale Spectrum Measurement Study Sixing Yin, Dawei Chen, Qian Zhang, Mingyan Liu, Shufang Li Outline for this presentation! Introduction! Methodology! Statistic and
CS440/ECE448 Lecture 9: Minimax Search. Slides by Svetlana Lazebnik 9/2016 Modified by Mark Hasegawa-Johnson 9/2017
 CS440/ECE448 Lecture 9: Minimax Search Slides by Svetlana Lazebnik 9/2016 Modified by Mark Hasegawa-Johnson 9/2017 Why study games? Games are a traditional hallmark of intelligence Games are easy to formalize
CS440/ECE448 Lecture 9: Minimax Search Slides by Svetlana Lazebnik 9/2016 Modified by Mark Hasegawa-Johnson 9/2017 Why study games? Games are a traditional hallmark of intelligence Games are easy to formalize
Lecture 15. Global extrema and Lagrange multipliers. Dan Nichols MATH 233, Spring 2018 University of Massachusetts
 Lecture 15 Global extrema and Lagrange multipliers Dan Nichols nichols@math.umass.edu MATH 233, Spring 2018 University of Massachusetts March 22, 2018 (2) Global extrema of a multivariable function Definition
Lecture 15 Global extrema and Lagrange multipliers Dan Nichols nichols@math.umass.edu MATH 233, Spring 2018 University of Massachusetts March 22, 2018 (2) Global extrema of a multivariable function Definition
Achieving Network Consistency. Octav Chipara
 Achieving Network Consistency Octav Chipara Reminders Homework is postponed until next class if you already turned in your homework, you may resubmit Please send me your peer evaluations 2 Next few lectures
Achieving Network Consistency Octav Chipara Reminders Homework is postponed until next class if you already turned in your homework, you may resubmit Please send me your peer evaluations 2 Next few lectures
Quasi-Optimal Resource Allocation in Multi-Spot MFTDMA Satellite Networks
 COMBINATORIAL OPTIMIZATION IN COMMUNICATION NETWORKS Maggie Cheng, Yingshu Li and Ding-Zhu Du (Eds.) pp. 1-41 c 2005 Kluwer Academic Publishers Quasi-Optimal Resource Allocation in Multi-Spot MFTDMA Satellite
COMBINATORIAL OPTIMIZATION IN COMMUNICATION NETWORKS Maggie Cheng, Yingshu Li and Ding-Zhu Du (Eds.) pp. 1-41 c 2005 Kluwer Academic Publishers Quasi-Optimal Resource Allocation in Multi-Spot MFTDMA Satellite
Table of Contents. Table of Contents 1
 Table of Contents 1) The Factor Game a) Investigation b) Rules c) Game Boards d) Game Table- Possible First Moves 2) Toying with Tiles a) Introduction b) Tiles 1-10 c) Tiles 11-16 d) Tiles 17-20 e) Tiles
Table of Contents 1) The Factor Game a) Investigation b) Rules c) Game Boards d) Game Table- Possible First Moves 2) Toying with Tiles a) Introduction b) Tiles 1-10 c) Tiles 11-16 d) Tiles 17-20 e) Tiles
Combinatorial Games. Jeffrey Kwan. October 2, 2017
 Combinatorial Games Jeffrey Kwan October 2, 2017 Don t worry, it s just a game... 1 A Brief Introduction Almost all of the games that we will discuss will involve two players with a fixed set of rules
Combinatorial Games Jeffrey Kwan October 2, 2017 Don t worry, it s just a game... 1 A Brief Introduction Almost all of the games that we will discuss will involve two players with a fixed set of rules
Error-Correcting Codes
 Error-Correcting Codes Information is stored and exchanged in the form of streams of characters from some alphabet. An alphabet is a finite set of symbols, such as the lower-case Roman alphabet {a,b,c,,z}.
Error-Correcting Codes Information is stored and exchanged in the form of streams of characters from some alphabet. An alphabet is a finite set of symbols, such as the lower-case Roman alphabet {a,b,c,,z}.
Cooperative Multi-Agent Learning and Coordination for Cognitive Radio Networks
 1 Cooperative Multi-Agent Learning and Coordination for Cognitive Radio Networks William Zame, Jie Xu, and Mihaela van der Schaar Abstract The radio spectrum is a scarce resource. Cognitive radio stretches
1 Cooperative Multi-Agent Learning and Coordination for Cognitive Radio Networks William Zame, Jie Xu, and Mihaela van der Schaar Abstract The radio spectrum is a scarce resource. Cognitive radio stretches
Solution: Alice tosses a coin and conveys the result to Bob. Problem: Alice can choose any result.
 Example - Coin Toss Coin Toss: Alice and Bob want to toss a coin. Easy to do when they are in the same room. How can they toss a coin over the phone? Mutual Commitments Solution: Alice tosses a coin and
Example - Coin Toss Coin Toss: Alice and Bob want to toss a coin. Easy to do when they are in the same room. How can they toss a coin over the phone? Mutual Commitments Solution: Alice tosses a coin and
6.2 Modular Arithmetic
 6.2 Modular Arithmetic Every reader is familiar with arithmetic from the time they are three or four years old. It is the study of numbers and various ways in which we can combine them, such as through
6.2 Modular Arithmetic Every reader is familiar with arithmetic from the time they are three or four years old. It is the study of numbers and various ways in which we can combine them, such as through
Efficiency and detectability of random reactive jamming in wireless networks
 Efficiency and detectability of random reactive jamming in wireless networks Ni An, Steven Weber Modeling & Analysis of Networks Laboratory Drexel University Department of Electrical and Computer Engineering
Efficiency and detectability of random reactive jamming in wireless networks Ni An, Steven Weber Modeling & Analysis of Networks Laboratory Drexel University Department of Electrical and Computer Engineering
Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks
 Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks Mariam Kaynia and Nihar Jindal Dept. of Electrical and Computer Engineering, University of Minnesota Dept. of Electronics and Telecommunications,
Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks Mariam Kaynia and Nihar Jindal Dept. of Electrical and Computer Engineering, University of Minnesota Dept. of Electronics and Telecommunications,
Pin-Permutations and Structure in Permutation Classes
 and Structure in Permutation Classes Frédérique Bassino Dominique Rossin Journées de Combinatoire de Bordeaux, feb. 2009 liafa Main result of the talk Conjecture[Brignall, Ruškuc, Vatter]: The pin-permutation
and Structure in Permutation Classes Frédérique Bassino Dominique Rossin Journées de Combinatoire de Bordeaux, feb. 2009 liafa Main result of the talk Conjecture[Brignall, Ruškuc, Vatter]: The pin-permutation
SOURCES OF ERROR IN UNBALANCE MEASUREMENTS. V.J. Gosbell, H.M.S.C. Herath, B.S.P. Perera, D.A. Robinson
 SOURCES OF ERROR IN UNBALANCE MEASUREMENTS V.J. Gosbell, H.M.S.C. Herath, B.S.P. Perera, D.A. Robinson Integral Energy Power Quality Centre School of Electrical, Computer and Telecommunications Engineering
SOURCES OF ERROR IN UNBALANCE MEASUREMENTS V.J. Gosbell, H.M.S.C. Herath, B.S.P. Perera, D.A. Robinson Integral Energy Power Quality Centre School of Electrical, Computer and Telecommunications Engineering
Contents. MA 327/ECO 327 Introduction to Game Theory Fall 2017 Notes. 1 Wednesday, August Friday, August Monday, August 28 6
 MA 327/ECO 327 Introduction to Game Theory Fall 2017 Notes Contents 1 Wednesday, August 23 4 2 Friday, August 25 5 3 Monday, August 28 6 4 Wednesday, August 30 8 5 Friday, September 1 9 6 Wednesday, September
MA 327/ECO 327 Introduction to Game Theory Fall 2017 Notes Contents 1 Wednesday, August 23 4 2 Friday, August 25 5 3 Monday, August 28 6 4 Wednesday, August 30 8 5 Friday, September 1 9 6 Wednesday, September
Edge-disjoint tree representation of three tree degree sequences
 Edge-disjoint tree representation of three tree degree sequences Ian Min Gyu Seong Carleton College seongi@carleton.edu October 2, 208 Ian Min Gyu Seong (Carleton College) Trees October 2, 208 / 65 Trees
Edge-disjoint tree representation of three tree degree sequences Ian Min Gyu Seong Carleton College seongi@carleton.edu October 2, 208 Ian Min Gyu Seong (Carleton College) Trees October 2, 208 / 65 Trees
II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing
 Class Subject Code Subject II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing 1.CONTENT LIST: Introduction to Unit I - Signals and Systems 2. SKILLS ADDRESSED: Listening 3. OBJECTIVE
Class Subject Code Subject II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing 1.CONTENT LIST: Introduction to Unit I - Signals and Systems 2. SKILLS ADDRESSED: Listening 3. OBJECTIVE
Utilization-Aware Adaptive Back-Pressure Traffic Signal Control
 Utilization-Aware Adaptive Back-Pressure Traffic Signal Control Wanli Chang, Samarjit Chakraborty and Anuradha Annaswamy Abstract Back-pressure control of traffic signal, which computes the control phase
Utilization-Aware Adaptive Back-Pressure Traffic Signal Control Wanli Chang, Samarjit Chakraborty and Anuradha Annaswamy Abstract Back-pressure control of traffic signal, which computes the control phase
14.7 Maximum and Minimum Values
 CHAPTER 14. PARTIAL DERIVATIVES 115 14.7 Maximum and Minimum Values Definition. Let f(x, y) be a function. f has a local max at (a, b) iff(a, b) (a, b). f(x, y) for all (x, y) near f has a local min at
CHAPTER 14. PARTIAL DERIVATIVES 115 14.7 Maximum and Minimum Values Definition. Let f(x, y) be a function. f has a local max at (a, b) iff(a, b) (a, b). f(x, y) for all (x, y) near f has a local min at
