Workshop 19 on Security and Governance of Identity on the Internet. Presented by BCS the chartered institute for IT, UK and OpenNet, Korea.
|
|
|
- Claud Pitts
- 5 years ago
- Views:
Transcription
1 Workshop 19 on Security and Governance of Identity on the Internet. Presented by BCS the chartered institute for IT, UK and OpenNet, Korea. The workshop went very well and had a good attendance. The discussions were split in two. The first covered identity attributes and identity being used to fund the Internet, the second covered the balance between privacy, security and anonymity. In the first part Dr. Louise Bennett from the BCS who was chairing the session introduced the session and the BCS. She introduced the other panel members: Andy Smith BCS Prof. Keechang Kim OpenNet Korea Sarah Whynne-Williams Facebook Prof. Hong Xoe, Normal University Beijing We also had Ian Fish as the remote moderator onsite. Unfortunately we did not have very good remote participation as due to the early time of the session it was 02:00 in Europe where most publicizing of the session had taken place. Louise introduced the workshop by describing the work the BCS had undertaken over the last 3 years including at IGF 6 and 7 and the reports that had been written following these. Louise then covered the use of identity as currency on the Internet she covered various aspects including how identity attributes are used to pay for services and how use of attributes for targeted marketing etc. She pointed out that identity is critical to the digital economy with everything from know your customer regulations to simple financial transactions all reliant on some form of assured identity. These may not be totally online but even a pseudonym used on the Internet can normally be traced back to a credit card or bank account and from there to a real person. She covered the need to develop valid incentive models that would make the various stakeholders exist or want to participate in an online identity governance framework and the need to understand how this might work across very different jurisdictions because the Internet is global. She noted that one business model that is contentious is the monetization of personal data attributes on the Internet to
2 subsidize free or cheap products and services. In return, you are often targeted with advertising or offered pay versions of the free software. This is really step 1 in monetization of your identity. She gave cautionary note that some people believe if you are using a free service, you are not a customer; you are a product. This could be viewed another way as the aggregation of personal data is the productization of people. Identity becomes currency. Most of us give this attribute data information away when we interact on the Internet without even realizing it. Companies are storing that data and monetizing it to give us superficially free services. Be they access to social networks or search company algorithms or money. By and large we want these apparently free or subsidized services and are prepared to put up with sometimes invasive advertising that might be associated with them. The Internet, though, is not a free resource. It costs money to build and maintain it. The question is: Are you happy to help fund the Internet with your identity attributes? You need to realize you are doing so and accept that if that's what you want. Andy Then took over and gave a brief summary on protecting the naïve from themselves. He started with a question - How many people have put personal information up on the Internet then regretted having done so? Also find out that having put the information up on the Internet, it is virtually impossible to remove it again. He noted that data aggregation is becoming more of a problem with huge amounts of personal data (BigData) or the aggregation of multiple data sets can be data mined to find out unexpected or unintended results - that is the problem. He noted there are now really good, freely available search algorithms, but you have now got a lot of publicly available information you can get someone's address details and that from 192.com, their career information from monster.com and you can start bringing this all together and aggregating it and mining it. He noted It's quite amazing how much you can find out about individuals. He then covered identity theft and the fact People just don't realize they put themselves at risk. You still get people who
3 are going to a cybercafé and using an untrusted machine to fill in forms online and give away all of their personal information. People don't understand what the risks are and don't understand how the risks come about, this is why we're all about protecting the naive from themselves. It's people who want to use the Internet, want to take advantage of all the benefits on the Internet but are not tech-savvy. We need to find a way of helping these people to understand the risks we want to make sure they are using the Internet securely. The final point he covered was frauds and scams and how easily people are taken in by these currently, include spam and fake websites. Michael Nelson asked the question 15 years ago I was convinced that we should have the online identity problem tackled in four or five years. Do the panelists have any idea on why that hasn't happened? This prompted an interesting discussion on why online identity systems work but they usually only work in very specific circumstances and there is still no sign of a global solution. However the question was not directly answered until a further discussion after the session. It seems to come down to the risk reward model and the fact that people still operate in communities even online, thus no one organisation will ever be accepted as the ultimate arbitrator of online identity. Andy pointed out that any such system would also have to deal with the whole population, every age, every language, every ethnicity, every creed, every religion. He also noted that static credentials such as passwords just don't work when you are dealing with organised crime, but these are still the only simple and prevalent method for access control. Keechang noted that identity is also context specific and driven by a value base. The problem is that there is no simple solution and the preconceived notion of one size fits all is flawed. Michael then asked another question about the Indian approach. The resultant discussion was on biometrics and the use of biometrics to provide convenient and security identity, both with biometrics being used as the user ID and as a credential. What was noted from the Indian example is its not perfect, but
4 importantly its not expected to be perfect, its expected to be much better than the solutions it replaced. It unlikely that any system will be perfect and any that claims to be will fail the first time it is circumvented. Keechang noted that state-managed identity being used on the Internet should be regarded with caution as they often have the best intentions but do not implement the systems very well. He noted that if your password is used to identify you, and your password is somehow leaked, you can simply reset your password. But biometric data, when it is leaked and it is in the bad hands, it's going to be very difficult to reset it! He noted people tend to have overconfidence about biometric being very secure. Andy noted that if you can have electronic identity in some form of token using PKI that is properly implemented, you can have secure online identity and you can only reveal the personal information necessary to do a particular transaction. I think that's the way we need to go is actually having some form of secure online identity that does not use static credentials. Sarah commented that we are seeing this in services like Facebook and work needs to be done on how you merge the technologies with biometric data and safeguards that need to go on top of use of biometric data. The Chair of the web payments group at the W3C asked a question - How do we get more stakeholders such as Government involved with the technology companies that are actually building these solutions and developing standards? Louise agreed with him that it was a problem and even IGF has not got a full balance of stakeholders yet. However she noted her view is that there's never going to be some big universal solution. We're going to have appropriate solutions for different classes of transactions and people will have different identities, different levels of security that they need for doing different things. Louise then moved on to the second set of discussion topics which were introduced by Keechang and Sarah and covered the balance between Security, Privacy and anonymity. Keechang introduced one of the problems he had been dealing with. South Korea has had an experience of enforcing state-
5 managed offline identity regime on online. In 2007 the South Korean government introduced legislation which required Internet users to identify themselves if they want to put a posting on the certain websites. They chose to use the Citizens registration number. So that's a very cautious attempt to use and enforce identity in the Internet that created a huge problem. He explained some of the dangers in introducing such an identity regime without thinking it through properly and looking at how it can be misused. He also asked if a national identity regime in the Internet really makes sense in the first place. The point is that the way it was implemented isolated those websites to non-koreans. They effectively implemented censorship without meaning to. The other issue is misuse of tokens as they can be copied and used for identity theft or even just pretending to be someone else when performing nefarious activities. This means that currently enforcement is flawed as the wrong person is found guilty. There are many stakeholders and players like governments, service providers and users and I think you need to have far more careful approach. He used the example of Age verification would be very important issue but very difficult issue. Because for services like Facebook or any service which aims at global market can they rely on one particular government's authoritative statement about a user's age? But then how are you going to come up with this age verification? Idenity can be a very diverse, fluid concept and depending on whether you talk about prevention of crime, prevention of online fraud, whether you talk about protection of a minor from adultoriented material, the goals are different and the level of assurance is bound to be different and the context of use is also going to be different. Sarah then gave a brief introduction to anonymity and its use online. She pointed out that organisations such as Facebook obviously made a value judgment around whether anonymity is desired and one thing that we think is fundamental to Facebook having over a billion members is our real-name culture and part of that is that there seems to be a desire that wasn't there for people to interact as their authentic selves on the Internet.
6 When we look at Facebook as a community, this real-name policy is actually essential to creating an environment where people feel comfortable and secure because they know who they are interacting with. She noted that there are challenges when you operate under a real name policy. Part of that is when you create a real-name culture, when you are not operating anonymously, there is a layer of accountability that is not there when you are anonymous. Hong then gave a short talk on the real name system in China, since we talk about identity on the Internet. She pointed out that the real name system in China is very much legitimate and expanding its implementation. This is defined by law, and enacted in 2000 by state Council. Still the most fundamental law on all information services offered an on the Internet. If you want to offer any public information services on the Internet in China you have to provide your real name information that is absolute. The logic behind this is that you are making information available to the public; you should make yourself available to the government and very much viable. This is one perspective. There are other circumstances that have become interesting. How to handle Internet content providers. For example, the blogging and microblogging in China, as Internet is really the paradise of information flow. Very hard to filter, control, censor, so these services are very much developing in China, though the more popular international ones are still blocked. You could use a pseudo-name, but it must be very viable so the issue for the content service provider, they must verify the real identity of all their users. This is their legal obligation. She noted in Europe, the recent court decision from the court that anonymous posting should be allowed so these people won't be in fear of the crime of defamation and this could be seen as positive for information flow and free expression. So we put a question mark of this real name system and look at it in the whole international perspective. Keechang added a point on anonymity because both previous speakers recognize the need for anonymity, but at the same time, they emphasize the benefits of real identity. He noted there is
7 a certain amount of ambiguity about the notion of anonymity itself and in many cases, the very notion of anonymity is deceptive and misleading because technically it is very difficult to achieve. So what is really important is to educate people that they are really not anonymous! You cannot be truly anonymous. You are being watched and especially by government and also by industry. But then at the same time we should not give up the notion of privacy because privacy is something which is entirely compatible with the situation where your identity is known. You don't need anonymity to have privacy. A comment was made on anonymity not being possible with the person stating they completely agree that from a governmental perspective, you are not anonymous online because so much data can be found out about you but from the perspective of young people, using services like Twitter which don't require your real name, it's not always possible to find out who the person is you are receiving anonymous postings from. A question was raised to the panel - Do you think there's a risk that although using online services like Facebook which require real name do you think there's a risk it limits our freedom of expression because we are scared of the accountability? Sarah replied I think it comes back to having a choice of platform and that identity is being used in different ways depending on the context. Keechang reiterated that Technically Internet is not anonymous. But by having a civilized governance framework and rules to operate by anonymity can be retained in the most part unless the authorities have a need for law enforcement or national security purposes to investigate who someone is. A question was raised about the process and strength of process to required to register that credential in the first place. Andy responded that he things this will remain one of the big problems as today most online identities are still based on a real world identity normally itself based on a government-issued identity or identity document. He noted it's incredibly difficult to do remote verification and registration of identity. A lot of people have tried it. There
8 have been various schemes on the Internet but unless you've got some way of verifying the attributes someone claims and corroborating the evidence they give you, it is really difficult to have any assurance in the identity and that identity belonging to the person that is claiming it. Keechang noted that the Korean government tried doing this with a PKI. They experimented and actually enforced a nationwide, mandatory PKI system where every user who intends to do financial transaction, online, online banking and shopping, must have. Its based on a government-endorsed PKI certificate. The government thought that would provide a very secure, very reliable identity verification for critically important transactions, online transactions. However the certificate and public keys can be extracted from peoples PCs as they are not properly protected which undermines the whole concept. A remote participant asked about the point on being tracked online as he didn t think it would be a view the whole panel held. Sarah replied it was an incredibly dynamic area and they were trying to make the US government be more transparent about the actions it takes. She noted we should make sure we're talking about what our expectations are and communicating those expectations and I actually hope that's part of the IGF more broadly. Hong commented you could presume you are anonymous but you are highly traceable by the governments or the other technical capable people. But her real concern is that once our identity has been identified on the Internet we enter into a scary world. Can we leave the system? Stop being identified? Can I erase my identity apart from the facial identity? If it can't be forgotten, can I be forgiven? Keechang reiterated his view I think government, if they narrow down their focus on certain individuals basically there is no way you can hide. That is why in my view it is important to educate people and propagate this technical effect you cannot hide. Andy commented I think the truth is that governments do monitor the Internet. They monitor all usage on the Internet and they will continue to do that. There are very, very good reasons, law enforcement, national security, for doing that.
9 But Governments may be monitoring and recording lots of information but they look at it reactively. They only look at it when there is a problem or something they need to investigate. They don't have the time, resources, or the inclination to look at every thing and track people. It is just not viable. Louise then make closing comments and all the panelists summed up. Conclusions There is still work to be done on the different balances. The balance is between anonymity and privacy/security not between privacy and security. Anonymity on the Internet is very hard to achieve, metadata can often be used to trace people. Normally this is a good thing as it is used to track criminals and is only done reactively however it can also be misused. Big data, aggregation and data mining are becoming more of a problem and both industry and online organisations are making more use of big data to more effectively target product advertising and services. Privacy online is possible but most people are naive in how they use the Internet and reveal more personal data than they should. This is more of an issue as nothing is ever deleted once it's on the Internet. Without people agreeing to subsidised services by 'paying' with their identity the Internet would be much more expensive and some services may not even exist. Some governments have tried to use regulations and enforce real name identity and even though this could be a good thing they have not normally implemented them properly which results in risk and misuse especially for the identity owner. Real-name identity systems have many benefits in a civilized online world and should be used. It is doubtful that anonymity is technically really possible and though there are sometimes good motives for wanting it, anonymity is often abused for nefarious actions. If Government are going to implement identity systems they
10 should do them properly and ensure that the failure modes are understood, that the identity system does not censor the network or services or limited them to a small community and that they are properly tested and secured before being implemented. Identity systems should be compatible and frameworks such as identity assertion based on commercial contractual models similar to those used in the global finance industry should be investigated for online identity.
Building DIGITAL TRUST People s Plan for Digital: A discussion paper
 Building DIGITAL TRUST People s Plan for Digital: A discussion paper We want Britain to be the world s most advanced digital society. But that won t happen unless the digital world is a world of trust.
Building DIGITAL TRUST People s Plan for Digital: A discussion paper We want Britain to be the world s most advanced digital society. But that won t happen unless the digital world is a world of trust.
Australian Census 2016 and Privacy Impact Assessment (PIA)
 http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
Making Identity Use Predictable. UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016
 Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Global Standards Symposium. Security, privacy and trust in standardisation. ICDPPC Chair John Edwards. 24 October 2016
 Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
Identity Management and its impact on the Digital Economy
 Identity Management and its impact on the Digital Economy Alejandro Barros 1, Alejandro Pareja 2 October 2016 Contents Introduction... 2 Identity Management... 3 Enrolment in the National Identity System...
Identity Management and its impact on the Digital Economy Alejandro Barros 1, Alejandro Pareja 2 October 2016 Contents Introduction... 2 Identity Management... 3 Enrolment in the National Identity System...
KEY FOCUS. Mobile Solutions for. Securing the Entire Identity Trust Chain. Border Management. Solving the Challenges of Breeder Documents
 I n f o r ma t i o nb r o c h u r e ABOUT THE 5TH BMIC The 5th and Identity Conference on Technical Cooperation & Capacity Building (5th BMIC) is organised by the International Organization for Migration
I n f o r ma t i o nb r o c h u r e ABOUT THE 5TH BMIC The 5th and Identity Conference on Technical Cooperation & Capacity Building (5th BMIC) is organised by the International Organization for Migration
Pan-Canadian Trust Framework Overview
 Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
IAB Europe Guidance THE DEFINITION OF PERSONAL DATA. IAB Europe GDPR Implementation Working Group WHITE PAPER
 IAB Europe Guidance WHITE PAPER THE DEFINITION OF PERSONAL DATA Five Practical Steps to help companies comply with the E-Privacy Working Directive Paper 02/2017 IAB Europe GDPR Implementation Working Group
IAB Europe Guidance WHITE PAPER THE DEFINITION OF PERSONAL DATA Five Practical Steps to help companies comply with the E-Privacy Working Directive Paper 02/2017 IAB Europe GDPR Implementation Working Group
Secrets of Social Media on Purpose
 The Ultimate Social Media Playbook for Soulful Storytellers How to supercharge your social media efforts and skyrocket your blog traffic for increased impact and income. Secrets of Social Media on Purpose
The Ultimate Social Media Playbook for Soulful Storytellers How to supercharge your social media efforts and skyrocket your blog traffic for increased impact and income. Secrets of Social Media on Purpose
"It's an extreme sport, Running and Fundraising!"
 "Never think you need to apologize for asking someone to give to a worthy objective, it is the same as you are giving an opportunity to participate in high-grade investment. The duty of giving is equal
"Never think you need to apologize for asking someone to give to a worthy objective, it is the same as you are giving an opportunity to participate in high-grade investment. The duty of giving is equal
Everything You Wanted to Know About Contracts (But Were Afraid to Ask) Professor Monestier
 Everything You Wanted to Know About Contracts (But Were Afraid to Ask) Professor Monestier Welcome to Law School! You re probably pretty nervous/excited/stressed out right now, with a million questions
Everything You Wanted to Know About Contracts (But Were Afraid to Ask) Professor Monestier Welcome to Law School! You re probably pretty nervous/excited/stressed out right now, with a million questions
Klixx instructions. Hello here is your instruction manual for your Klixx box INDEX
 1 Klixx instructions Hello here is your instruction manual for your Klixx box Inside this little device is a whole new world of television with over 70,000 links. Dont be worried though, with this guide
1 Klixx instructions Hello here is your instruction manual for your Klixx box Inside this little device is a whole new world of television with over 70,000 links. Dont be worried though, with this guide
Why Affiliate Marketing Doesn t Work for You
 1 Why do people fail? Why Affiliate Marketing Doesn t Work for You Lots of people read certain books thinking they'll get that one big secret. We're always looking for it, but we fail to look behind the
1 Why do people fail? Why Affiliate Marketing Doesn t Work for You Lots of people read certain books thinking they'll get that one big secret. We're always looking for it, but we fail to look behind the
LEARN HOW TO MAKE EASY MONEY
 LEARN HOW TO MAKE EASY MONEY How To Make Money Easy And Fast No Hard Work Do You Need Money? Find Out How!!?!! As You Seen On Oprah And 20/20 Oprah Winfrey and ABC's ***** investigation team 20/20 also
LEARN HOW TO MAKE EASY MONEY How To Make Money Easy And Fast No Hard Work Do You Need Money? Find Out How!!?!! As You Seen On Oprah And 20/20 Oprah Winfrey and ABC's ***** investigation team 20/20 also
TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV
 Tech EUROPE TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV Brussels, 14 January 2014 TechAmerica Europe represents
Tech EUROPE TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV Brussels, 14 January 2014 TechAmerica Europe represents
Does it happen that you're in the middle of the call and the flow of conversation doesn't follow the script that you've posted on your wall?
 Does it happen that you're in the middle of the call and the flow of conversation doesn't follow the script that you've posted on your wall? Then Suddenly you found yourself lost for words and wasn't sure
Does it happen that you're in the middle of the call and the flow of conversation doesn't follow the script that you've posted on your wall? Then Suddenly you found yourself lost for words and wasn't sure
Legal Aspects of Identity Management and Trust Services
 Legal Aspects of Identity Management and Trust Services Anna Joubin-Bret Secretary What is Identity Management (IdM)? Fundamental issue for the use of electronic means Answers the basic questions: Who
Legal Aspects of Identity Management and Trust Services Anna Joubin-Bret Secretary What is Identity Management (IdM)? Fundamental issue for the use of electronic means Answers the basic questions: Who
Author: Iris Carter-Collins
 Reputation Management Vol. 1 Title: Learn How To Manage Your Reputation Author: Iris Carter-Collins Table Of Contents Learn How To Manage Your Reputation 1 To maintain a good reputation, you must learn
Reputation Management Vol. 1 Title: Learn How To Manage Your Reputation Author: Iris Carter-Collins Table Of Contents Learn How To Manage Your Reputation 1 To maintain a good reputation, you must learn
Ethical and social aspects of management information systems
 Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
ISSUANCE AND CIVIL REGISTRATION
 IDENTITY VERIFICATION IN PASSPORT ISSUANCE AND CIVIL REGISTRATION THE IMPORTANCE OF CONTEXT AND CONTINUITY OF IDENTITY Ross Greenwood Identity Matters Consulting Australia PURPOSE To invite a claim to
IDENTITY VERIFICATION IN PASSPORT ISSUANCE AND CIVIL REGISTRATION THE IMPORTANCE OF CONTEXT AND CONTINUITY OF IDENTITY Ross Greenwood Identity Matters Consulting Australia PURPOSE To invite a claim to
Our position. ICDPPC declaration on ethics and data protection in artificial intelligence
 ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
I want a website but I don't know where to start.
 I want a website but I don't know where to start. The free and simple guide for people that know absolutely nothing about websites. Written by Rob Swan Edited by Gareth Penhallurick Copyright 2010 Rob
I want a website but I don't know where to start. The free and simple guide for people that know absolutely nothing about websites. Written by Rob Swan Edited by Gareth Penhallurick Copyright 2010 Rob
Terms and Conditions
 Terms and Conditions LEGAL NOTICE The Publisher has strived to be as accurate and complete as possible in the creation of this report, notwithstanding the fact that he does not warrant or represent at
Terms and Conditions LEGAL NOTICE The Publisher has strived to be as accurate and complete as possible in the creation of this report, notwithstanding the fact that he does not warrant or represent at
Anarchy Arcade. Frequently Asked Questions
 Anarchy Arcade Frequently Asked Questions by Elijah Newman-Gomez Table of Contents 1. What is Anarchy Arcade?...2 2. What is SMAR CADE: Anarchy Edition?...2 3. Why distribute a free version now?...2 4.
Anarchy Arcade Frequently Asked Questions by Elijah Newman-Gomez Table of Contents 1. What is Anarchy Arcade?...2 2. What is SMAR CADE: Anarchy Edition?...2 3. Why distribute a free version now?...2 4.
Robert Bond Partner, Commercial/IP/IT
 Using Privacy Impact Assessments Effectively robert.bond@bristows.com Robert Bond Partner, Commercial/IP/IT BA (Hons) Law, Wolverhampton University Qualified as a Solicitor 1979 Qualified as a Notary Public
Using Privacy Impact Assessments Effectively robert.bond@bristows.com Robert Bond Partner, Commercial/IP/IT BA (Hons) Law, Wolverhampton University Qualified as a Solicitor 1979 Qualified as a Notary Public
Interview with Brian Hamilton '90, Co-founder and CEO of Sageworks
 Interview with Brian Hamilton '90, Co-founder and CEO of Sageworks Interview by Howie Rhee '04 You went to Sacred Heart University for your undergraduate degree. What did you study and were you involved
Interview with Brian Hamilton '90, Co-founder and CEO of Sageworks Interview by Howie Rhee '04 You went to Sacred Heart University for your undergraduate degree. What did you study and were you involved
Using Google Analytics to Make Better Decisions
 Using Google Analytics to Make Better Decisions This transcript was lightly edited for clarity. Hello everybody, I'm back at ACPLS 20 17, and now I'm talking with Jon Meck from LunaMetrics. Jon, welcome
Using Google Analytics to Make Better Decisions This transcript was lightly edited for clarity. Hello everybody, I'm back at ACPLS 20 17, and now I'm talking with Jon Meck from LunaMetrics. Jon, welcome
17 Maximum Conversion Rate Tips
 17 Maximum Conversion Rate Tips Discover how to increase your sales copy conversions by making minimum changes that deliver maximum impact! Special Report by Brian Terry Brought to you by: http://bigsellingwebsitedesign.com
17 Maximum Conversion Rate Tips Discover how to increase your sales copy conversions by making minimum changes that deliver maximum impact! Special Report by Brian Terry Brought to you by: http://bigsellingwebsitedesign.com
Enabling Trust in e-business: Research in Enterprise Privacy Technologies
 Enabling Trust in e-business: Research in Enterprise Privacy Technologies Dr. Michael Waidner IBM Zurich Research Lab http://www.zurich.ibm.com / wmi@zurich.ibm.com Outline Motivation Privacy-enhancing
Enabling Trust in e-business: Research in Enterprise Privacy Technologies Dr. Michael Waidner IBM Zurich Research Lab http://www.zurich.ibm.com / wmi@zurich.ibm.com Outline Motivation Privacy-enhancing
Klixx instructions. Hello here is your instruction manual for your Klixx box. low quality or not working, just choose a different one INDEX
 1 Klixx instructions Hello here is your instruction manual for your Klixx box. Inside this little device is a whole new world of television with over 70,000 links. Dont be worried though, with this guide
1 Klixx instructions Hello here is your instruction manual for your Klixx box. Inside this little device is a whole new world of television with over 70,000 links. Dont be worried though, with this guide
Participant Information Sheet
 Participant Information Sheet Project Title: Harlie Human and Robot Language Interaction Experiment Principal Investigator: Dr Christina Knuepffer, Postdoctoral Research Fellow, School of Information Technology
Participant Information Sheet Project Title: Harlie Human and Robot Language Interaction Experiment Principal Investigator: Dr Christina Knuepffer, Postdoctoral Research Fellow, School of Information Technology
Legal Notice: The Author and Publisher assume no responsibility or liability whatsoever on the behalf of any Purchaser or Reader of these materials.
 BACK DOOR SUPPLIERS Legal Notice: While all attempts have been made to verify information provided in this publication,neither the Author nor the Publisher assumes any responsibility for errors, omissions,
BACK DOOR SUPPLIERS Legal Notice: While all attempts have been made to verify information provided in this publication,neither the Author nor the Publisher assumes any responsibility for errors, omissions,
The Clixsense Report. WARNING!!!
 The Clixsense Report. WARNING!!! The Information Contained In This Report Can Result In An Explosion Of Daily Income, And No Matter How Much You Earn... You Will Get Paid In Full Guaranteed! Stop Wasting
The Clixsense Report. WARNING!!! The Information Contained In This Report Can Result In An Explosion Of Daily Income, And No Matter How Much You Earn... You Will Get Paid In Full Guaranteed! Stop Wasting
We encourage you to print this booklet for easy reading. Blogging for Beginners 1
 We have strived to be as accurate and complete as possible in this report. Due to the rapidly changing nature of the Internet the contents are not warranted to be accurate. While all attempts have been
We have strived to be as accurate and complete as possible in this report. Due to the rapidly changing nature of the Internet the contents are not warranted to be accurate. While all attempts have been
The little BIG book of badness
 The little BIG book of badness (how to stay safe on the Internet - a guidebook for students and parents) You re safer in our world Use this book to find out how you and your computer can stay away from
The little BIG book of badness (how to stay safe on the Internet - a guidebook for students and parents) You re safer in our world Use this book to find out how you and your computer can stay away from
ARE TRUST & IDENTITY HOLDING BACK FURTHER GROWTH OF THE SHARING ECONOMY?
 ARE TRUST & IDENTITY HOLDING BACK FURTHER GROWTH OF THE SHARING ECONOMY?.5 charts to analyse and grow participation in the sharing economy TRUST AND IDENTITY A consumer requirement or a willing risk? In
ARE TRUST & IDENTITY HOLDING BACK FURTHER GROWTH OF THE SHARING ECONOMY?.5 charts to analyse and grow participation in the sharing economy TRUST AND IDENTITY A consumer requirement or a willing risk? In
5 Fatal Internet Marketing Mistakes That Can KILL The Sales and Profits In Your Business
 5 Fatal Internet Marketing Mistakes That Can KILL The Sales and Profits In Your Business Local Biz Consultant Over the last decade we've experienced a radical shift in the way we seek out information and
5 Fatal Internet Marketing Mistakes That Can KILL The Sales and Profits In Your Business Local Biz Consultant Over the last decade we've experienced a radical shift in the way we seek out information and
AIMICT.ORG AIMICT Newsletter
 SEPTEMBER 2018 AIMICT.ORG 1 IN THIS ISSUE AIMICT Conducts ISO 9001 Lead Auditor Course AIMICT Conducts ILM s Training of Trainers Program in Irbid AIMICT Organizes Professional Quality Manager Program
SEPTEMBER 2018 AIMICT.ORG 1 IN THIS ISSUE AIMICT Conducts ISO 9001 Lead Auditor Course AIMICT Conducts ILM s Training of Trainers Program in Irbid AIMICT Organizes Professional Quality Manager Program
LEGAL TECH NEWSLETTER FEBRUARY 2015
 LEGAL TECH NEWSLETTER FEBRUARY 2015 Can Computers Practice Law? By Nina Cunningham Can computers practice law? Many are inclined to say yes when using them affects us in so many ways. When scanning the
LEGAL TECH NEWSLETTER FEBRUARY 2015 Can Computers Practice Law? By Nina Cunningham Can computers practice law? Many are inclined to say yes when using them affects us in so many ways. When scanning the
Suggest holding off until next time you visit, so you can ask your parents first.
 Quiz This Safer Internet Day the UK Safer Internet entre is focussing on how consent works in an online context. It will explore how young people ask for, give and receive consent online. This could be
Quiz This Safer Internet Day the UK Safer Internet entre is focussing on how consent works in an online context. It will explore how young people ask for, give and receive consent online. This could be
LAB3-R04 A Hard Privacy Impact Assessment. Post conference summary
 LAB3-R04 A Hard Privacy Impact Assessment Post conference summary John Elliott Joanne Furtsch @withoutfire @PrivacyGeek Table of Contents THANK YOU... 3 WHAT IS PRIVACY?... 3 The European Perspective...
LAB3-R04 A Hard Privacy Impact Assessment Post conference summary John Elliott Joanne Furtsch @withoutfire @PrivacyGeek Table of Contents THANK YOU... 3 WHAT IS PRIVACY?... 3 The European Perspective...
Paid Surveys Secret. The Most Guarded Secret Top Survey Takers Cash In and Will Never Tell You! Top Secret Report. Published by Surveys & Friends
 Paid Surveys Secret The Most Guarded Secret Top Survey Takers Cash In and Will Never Tell You! Top Secret Report Published by Surveys & Friends http://www.surveysandfriends.com All Rights Reserved This
Paid Surveys Secret The Most Guarded Secret Top Survey Takers Cash In and Will Never Tell You! Top Secret Report Published by Surveys & Friends http://www.surveysandfriends.com All Rights Reserved This
Level 1 VRQ Qualifications in Photo Imaging (7512) Assessment pack
 Level 1 VRQ Qualifications in Photo Imaging (7512) Assessment pack www.cityandguilds.com May 2012 Version 1.1 About City & Guilds City & Guilds is the UK s leading provider of vocational qualifications,
Level 1 VRQ Qualifications in Photo Imaging (7512) Assessment pack www.cityandguilds.com May 2012 Version 1.1 About City & Guilds City & Guilds is the UK s leading provider of vocational qualifications,
Is Transparency a useful Paradigm for Privacy?
 Is Transparency a useful Paradigm for Privacy? Shonan Seminar, August 6 th, 2013 Japan Prof. Dr. Dr. h.c. Günter Müller Institute of Computer Science and Social Studies Department of Telematics Outline
Is Transparency a useful Paradigm for Privacy? Shonan Seminar, August 6 th, 2013 Japan Prof. Dr. Dr. h.c. Günter Müller Institute of Computer Science and Social Studies Department of Telematics Outline
This policy sets out how Legacy Foresight and its Associates will seek to ensure compliance with the legislation.
 Privacy Notice August 2018 Introduction The General Data Protection Regulation (GDPR) is European wide data protection legislation that requires organisations working with individuals based in the European
Privacy Notice August 2018 Introduction The General Data Protection Regulation (GDPR) is European wide data protection legislation that requires organisations working with individuals based in the European
Circle Link 1 Online Rules of the Road
 4 th Grade Scavenger Hunt Links Content Circle Link 1 http://www.commonsensemedia.org/get-cybersmart-phineas-and-ferb Online Rules of the Road 1. Guard your privacy. What people know about you is up to
4 th Grade Scavenger Hunt Links Content Circle Link 1 http://www.commonsensemedia.org/get-cybersmart-phineas-and-ferb Online Rules of the Road 1. Guard your privacy. What people know about you is up to
This is simply, customers looking for businesses that service their local area. Businesses like yours.
 Websites for Small Business The internet has become an integral part of doing business in Australia and around the world and one of the fastest growing areas of the World Wide Web is Local Search. This
Websites for Small Business The internet has become an integral part of doing business in Australia and around the world and one of the fastest growing areas of the World Wide Web is Local Search. This
2013, All Rights Reserved
 Money Making Mama Mini Presents: Mystery Shopping Basics By Rayven Perkins Permission is granted to distribute this publication to your friends or associates as you see fit as long as you do not change
Money Making Mama Mini Presents: Mystery Shopping Basics By Rayven Perkins Permission is granted to distribute this publication to your friends or associates as you see fit as long as you do not change
Bank $21,000 a month with CPA
 2010 Bank $21,000 a month with CPA Andrew Gotti I will show you the best group of people to target with your offers. Firstly, I would like to thank all of you for purchasing my short guide. I will show
2010 Bank $21,000 a month with CPA Andrew Gotti I will show you the best group of people to target with your offers. Firstly, I would like to thank all of you for purchasing my short guide. I will show
Ep #181: Proactivation
 Full Episode Transcript With Your Host Brooke Castillo Welcome to The Life Coach School Podcast, where it s all about real clients, real problems, and real coaching. And now your host, Master Coach Instructor,
Full Episode Transcript With Your Host Brooke Castillo Welcome to The Life Coach School Podcast, where it s all about real clients, real problems, and real coaching. And now your host, Master Coach Instructor,
Personal Data Protection Competency Framework for School Students. Intended to help Educators
 Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
MANIFESTATION REVEALED - THE LAWS OF MIND SYSTEM
 MANIFESTATION REVEALED - THE LAWS OF MIND SYSTEM In this short worksheet, we're going to talk about some basics of the Laws Of Mind System. We're also going to talk about how it's different from the law
MANIFESTATION REVEALED - THE LAWS OF MIND SYSTEM In this short worksheet, we're going to talk about some basics of the Laws Of Mind System. We're also going to talk about how it's different from the law
Exactly, exactly. Well, I have a presentation here that I think I can very nicely
 The following is an actual transcript of the ChiroSecure Live Event with Dr. Stu Hoffman and Dr. Sam Collins. We do our best to make sure the transcript is as accurate as possible; however, it may contain
The following is an actual transcript of the ChiroSecure Live Event with Dr. Stu Hoffman and Dr. Sam Collins. We do our best to make sure the transcript is as accurate as possible; however, it may contain
The State of Food Blogging March 2012 Part I: The Bloggers. How would you classify yourself as a Food Blogger?
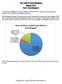 The State of Food Blogging March 2012 Part I: The Bloggers The State of Food Blogging Survey was conducted in February of 2012 by Foodista and Zephyr Adventures, organizers of the International Food Blogger
The State of Food Blogging March 2012 Part I: The Bloggers The State of Food Blogging Survey was conducted in February of 2012 by Foodista and Zephyr Adventures, organizers of the International Food Blogger
Hey, Janice. Thank you so much for talking with me today. Ed, thanks so much. I'm delighted to be here to talk to you.
 Case Study: How The 2X Project Helped Janice Hughes Strengthen Her Market Positioning, Land More Lucrative Clients and Increase the Quality and Quantity of Client Leads Hey, Janice. Thank you so much for
Case Study: How The 2X Project Helped Janice Hughes Strengthen Her Market Positioning, Land More Lucrative Clients and Increase the Quality and Quantity of Client Leads Hey, Janice. Thank you so much for
Decentralized Protocol for Self-Sovereign Identities with Embedded Compliance
 Decentralized Protocol for Self-Sovereign Identities with Embedded Compliance A self-sovereign identity portal for regulated industries and the Internet of Everything guy.davies@blockpass.org www.blockpass.org
Decentralized Protocol for Self-Sovereign Identities with Embedded Compliance A self-sovereign identity portal for regulated industries and the Internet of Everything guy.davies@blockpass.org www.blockpass.org
This Is A Free Report! You Do NOT Have The Right To Copy This Report In ANY Way, Shape, Or Form!
 This Is A Free Report! You Do NOT Have The Right To Copy This Report In ANY Way, Shape, Or Form! You can enjoy it and then pass it to someone else. Feel free to distribute the report as is to your friends,
This Is A Free Report! You Do NOT Have The Right To Copy This Report In ANY Way, Shape, Or Form! You can enjoy it and then pass it to someone else. Feel free to distribute the report as is to your friends,
Artificial intelligence and judicial systems: The so-called predictive justice
 Artificial intelligence and judicial systems: The so-called predictive justice 09 May 2018 1 Context The use of so-called artificial intelligence received renewed interest over the past years.. Computers
Artificial intelligence and judicial systems: The so-called predictive justice 09 May 2018 1 Context The use of so-called artificial intelligence received renewed interest over the past years.. Computers
Frequently Asked Questions
 Frequently Asked Questions Index Frequently Asked Questions... 1 Being a Mystery Shopper... 3 What is a mystery shopper?... 3 How can I become a mystery shopper?... 3 What are you looking for in a mystery
Frequently Asked Questions Index Frequently Asked Questions... 1 Being a Mystery Shopper... 3 What is a mystery shopper?... 3 How can I become a mystery shopper?... 3 What are you looking for in a mystery
Warning a client of risks 1/2
 Legal English Warning a client of risks 1/2 Let me caution you that in this jurisdiction the fines can be very high for this sort of activity. I must warn you that individuals directly involved in serious
Legal English Warning a client of risks 1/2 Let me caution you that in this jurisdiction the fines can be very high for this sort of activity. I must warn you that individuals directly involved in serious
UNIVERSAL SERVICE PRINCIPLES IN E-COMMUNICATIONS
 UNIVERSAL SERVICE PRINCIPLES IN E-COMMUNICATIONS BEUC paper EC register for interest representatives: identification number 9505781573-45 100% broadband coverage by 2013 ICT services have become central
UNIVERSAL SERVICE PRINCIPLES IN E-COMMUNICATIONS BEUC paper EC register for interest representatives: identification number 9505781573-45 100% broadband coverage by 2013 ICT services have become central
Interest Balancing Test Assessment on the processing of the copies of data subjects driving licences for the MOL Limo service
 1 Legitimate interest of the controller or a third party: General description of the processing environment Users can commence the registration required for using the MOL LIMO service in the Mobile Application
1 Legitimate interest of the controller or a third party: General description of the processing environment Users can commence the registration required for using the MOL LIMO service in the Mobile Application
Before we start, I want to share with you how this challenge came to be.
 Hey! Thank you for signing up for my Next Level Instagram Challenge! This 7 day challenge will grow your account but not without some work. What kind of work? In this challenge, you will be engaging (following,
Hey! Thank you for signing up for my Next Level Instagram Challenge! This 7 day challenge will grow your account but not without some work. What kind of work? In this challenge, you will be engaging (following,
Privacy Policy SOP-031
 SOP-031 Version: 2.0 Effective Date: 18-Nov-2013 Table of Contents 1. DOCUMENT HISTORY...3 2. APPROVAL STATEMENT...3 3. PURPOSE...4 4. SCOPE...4 5. ABBREVIATIONS...5 6. PROCEDURES...5 6.1 COLLECTION OF
SOP-031 Version: 2.0 Effective Date: 18-Nov-2013 Table of Contents 1. DOCUMENT HISTORY...3 2. APPROVAL STATEMENT...3 3. PURPOSE...4 4. SCOPE...4 5. ABBREVIATIONS...5 6. PROCEDURES...5 6.1 COLLECTION OF
NOTICE: THIS REPORT IS COPYRIGHT OF ANGELA WILLS & MARKETERS MOJO
 NOTICE: THIS REPORT IS COPYRIGHT OF ANGELA WILLS & MARKETERS MOJO That's right! You MAY NOT can give it away, share it with friends, print it out and present the information or even sell it. **However,
NOTICE: THIS REPORT IS COPYRIGHT OF ANGELA WILLS & MARKETERS MOJO That's right! You MAY NOT can give it away, share it with friends, print it out and present the information or even sell it. **However,
AN APPROACH TO ONLINE ANONYMOUS ELECTRONIC CASH. Li Ying. A thesis submitted in partial fulfillment of the requirements for the degree of
 AN APPROACH TO ONLINE ANONYMOUS ELECTRONIC CASH by Li Ying A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Software Engineering Faculty of Science and
AN APPROACH TO ONLINE ANONYMOUS ELECTRONIC CASH by Li Ying A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Software Engineering Faculty of Science and
019 My Wife Caught Me Looking at Porn, Now What?!?!
 019 My Wife Caught Me Looking at Porn, Now What?!?! Welcome to Pornfree Radio. I'm Matt Dobschuetz. This is the podcast for people who want to live 100% porn free. Today's episode is called, My Wife Caught
019 My Wife Caught Me Looking at Porn, Now What?!?! Welcome to Pornfree Radio. I'm Matt Dobschuetz. This is the podcast for people who want to live 100% porn free. Today's episode is called, My Wife Caught
2. Why did you apply to the Bristol Home Energy Upgrade project? Please rank in order of importance with 1 being the most important.
 Introduction To make sure Bristol is best placed to secure funding for projects like this in the future we are undertaking some in depth evaluation of the Bristol Home Energy Upgrade project. We would
Introduction To make sure Bristol is best placed to secure funding for projects like this in the future we are undertaking some in depth evaluation of the Bristol Home Energy Upgrade project. We would
Become a Motivational Speaker
 Get paid to speak! FabJob Guide to Become a Motivational Speaker Tag Goulet and Clayton Warholm Visit www.fabjob.com Contents About the Authors...9 Acknowledgements...10 1. Introduction...11 1.1 What Is
Get paid to speak! FabJob Guide to Become a Motivational Speaker Tag Goulet and Clayton Warholm Visit www.fabjob.com Contents About the Authors...9 Acknowledgements...10 1. Introduction...11 1.1 What Is
The Witness Charter - Looking after Witnesses
 The Witness Charter - Looking after Witnesses The support you can get and how you should be treated when telling the police about a crime right up to when it is heard in court and afterwards. An EasyRead
The Witness Charter - Looking after Witnesses The support you can get and how you should be treated when telling the police about a crime right up to when it is heard in court and afterwards. An EasyRead
InternetMarketingWithBarb.com
 How to Outsource Like A Pro Unless you have unlimited funds, chances are you won't be able to hire many full-time employees to handle the various essential functions when you first start your business.
How to Outsource Like A Pro Unless you have unlimited funds, chances are you won't be able to hire many full-time employees to handle the various essential functions when you first start your business.
Contact with the media
 Contact with the media Support for survivors of sexual offences How we can help and about this guidance We are the Independent Press Standards Organisation (IPSO), the independent regulator of most of
Contact with the media Support for survivors of sexual offences How we can help and about this guidance We are the Independent Press Standards Organisation (IPSO), the independent regulator of most of
COLD CALLING SCRIPTS
 COLD CALLING SCRIPTS Portlandrocks Hello and welcome to this portion of the WSO where we look at a few cold calling scripts to use. If you want to learn more about the entire process of cold calling then
COLD CALLING SCRIPTS Portlandrocks Hello and welcome to this portion of the WSO where we look at a few cold calling scripts to use. If you want to learn more about the entire process of cold calling then
Do You Want To Be Your Own Boss?
 Do You Want To Be Your Own Boss? Your Online Money Making Search Ends Here Get answers for the Questions, why you need to be your own boss? Why online? and How to make money by blogging? St Paul Severe
Do You Want To Be Your Own Boss? Your Online Money Making Search Ends Here Get answers for the Questions, why you need to be your own boss? Why online? and How to make money by blogging? St Paul Severe
You may provide the following information either as a running paragraph or under headings as shown below. [Informed Consent Form for ]
![You may provide the following information either as a running paragraph or under headings as shown below. [Informed Consent Form for ] You may provide the following information either as a running paragraph or under headings as shown below. [Informed Consent Form for ]](/thumbs/72/66522199.jpg) [Informed Consent Form for ] Name the group of individuals for whom this consent is written. Because research for a single project is often carried out with a number of different groups of individuals
[Informed Consent Form for ] Name the group of individuals for whom this consent is written. Because research for a single project is often carried out with a number of different groups of individuals
This Privacy Policy describes the types of personal information SF Express Co., Ltd. and
 Effective Date: 2017/05/10 Updated date: 2017/05/25 This Privacy Policy describes the types of personal information SF Express Co., Ltd. and its affiliates (collectively as "SF") collect about consumers
Effective Date: 2017/05/10 Updated date: 2017/05/25 This Privacy Policy describes the types of personal information SF Express Co., Ltd. and its affiliates (collectively as "SF") collect about consumers
The University of Sheffield Research Ethics Policy Note no. 14 RESEARCH INVOLVING SOCIAL MEDIA DATA 1. BACKGROUND
 The University of Sheffield Research Ethics Policy te no. 14 RESEARCH INVOLVING SOCIAL MEDIA DATA 1. BACKGROUND Social media are communication tools that allow users to share information and communicate
The University of Sheffield Research Ethics Policy te no. 14 RESEARCH INVOLVING SOCIAL MEDIA DATA 1. BACKGROUND Social media are communication tools that allow users to share information and communicate
clarification to bring legal certainty to these issues have been voiced in various position papers and statements.
 ESR Statement on the European Commission s proposal for a Regulation on the protection of individuals with regard to the processing of personal data on the free movement of such data (General Data Protection
ESR Statement on the European Commission s proposal for a Regulation on the protection of individuals with regard to the processing of personal data on the free movement of such data (General Data Protection
ISO/IEC INTERNATIONAL STANDARD. Information technology Security techniques Privacy framework
 INTERNATIONAL STANDARD ISO/IEC 29100 First edition 2011-12-15 Information technology Security techniques Privacy framework Technologies de l'information Techniques de sécurité Cadre privé Reference number
INTERNATIONAL STANDARD ISO/IEC 29100 First edition 2011-12-15 Information technology Security techniques Privacy framework Technologies de l'information Techniques de sécurité Cadre privé Reference number
B) Issues to be Prioritised within the Proposed Global Strategy and Plan of Action:
 INTERGOVERNMENTAL WORKING GROUP ON PUBLIC HEALTH, INNOVATION AND INTELLECTUAL PROPERTY EGA Submission to Section 1 Draft Global Strategy and Plan of Action The European Generic Medicines Association is
INTERGOVERNMENTAL WORKING GROUP ON PUBLIC HEALTH, INNOVATION AND INTELLECTUAL PROPERTY EGA Submission to Section 1 Draft Global Strategy and Plan of Action The European Generic Medicines Association is
Preparing for Your Interview
 ADVICE Preparing for Your Interview By Rob Jenkins JANUARY 13, 2011 Brian Taylor If you were fortunate enough to score an interview at a community college in the coming months, you're no doubt looking
ADVICE Preparing for Your Interview By Rob Jenkins JANUARY 13, 2011 Brian Taylor If you were fortunate enough to score an interview at a community college in the coming months, you're no doubt looking
Public consultation on Europeana
 Contribution ID: 941f02ae-8804-42f5-824a-fe9fbe6521fc Date: 08/11/2017 08:35:00 Public consultation on Europeana Fields marked with * are mandatory. Introduction Welcome to the consultation on Europeana.
Contribution ID: 941f02ae-8804-42f5-824a-fe9fbe6521fc Date: 08/11/2017 08:35:00 Public consultation on Europeana Fields marked with * are mandatory. Introduction Welcome to the consultation on Europeana.
Appointment Setter Training
 Appointment Setter Training Setting appointments on the phone is a numbers game. Numbers never lie and as long you follow our script and personalize it to you, you will have success. Consistency is the
Appointment Setter Training Setting appointments on the phone is a numbers game. Numbers never lie and as long you follow our script and personalize it to you, you will have success. Consistency is the
PARTICIPATORY ACCUSATION
 PARTICIPATORY ACCUSATION A. Introduction B. Ask Subject to Describe in Detail How He/She Handles Transactions, i.e., Check, Cash, Credit Card, or Other Incident to Lock in Details OR Slide into Continue
PARTICIPATORY ACCUSATION A. Introduction B. Ask Subject to Describe in Detail How He/She Handles Transactions, i.e., Check, Cash, Credit Card, or Other Incident to Lock in Details OR Slide into Continue
International Seminar on Personal Data Protection and Privacy Câmara Dos Deputados-BRAZIL
 International Seminar on Personal Data Protection and Privacy Câmara Dos Deputados-BRAZIL Panel: Data protection in Finance, Health Services and Telecommunications Carlos López Blanco Telefónica S.A. 10.05.2017
International Seminar on Personal Data Protection and Privacy Câmara Dos Deputados-BRAZIL Panel: Data protection in Finance, Health Services and Telecommunications Carlos López Blanco Telefónica S.A. 10.05.2017
"The Lottery Shotgun Method:
 "The Lottery Shotgun Method: Winning More Without Breaking The Bank" By Lottery Guy Copyright 2012 Lottery-Guy.com. ALL RIGHTS RESERVED. This report is copyright. It may not be copied, reproduced or distributed
"The Lottery Shotgun Method: Winning More Without Breaking The Bank" By Lottery Guy Copyright 2012 Lottery-Guy.com. ALL RIGHTS RESERVED. This report is copyright. It may not be copied, reproduced or distributed
First Components Ltd, Savigny Oddie Ltd, & Datum Engineering Ltd. is pleased to provide the following
 Privacy Notice Introduction This document refers to personal data, which is defined as information concerning any living person (a natural person who hereafter will be called the Data Subject) that is
Privacy Notice Introduction This document refers to personal data, which is defined as information concerning any living person (a natural person who hereafter will be called the Data Subject) that is
UK Internet Policy Forum Open Internet and the Digital Economy - Wednesday 2 April 2014.
 UK Internet Policy Forum Open Internet and the Digital Economy - Wednesday 2 April 2014. The digital economy, innovation, and consumers have benefited greatly from the open internet. The nature of the
UK Internet Policy Forum Open Internet and the Digital Economy - Wednesday 2 April 2014. The digital economy, innovation, and consumers have benefited greatly from the open internet. The nature of the
Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology
 Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology Edited by Mireille Hildebrandt and Katja de Vries New York, New York, Routledge, 2013, ISBN 978-0-415-64481-5
Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology Edited by Mireille Hildebrandt and Katja de Vries New York, New York, Routledge, 2013, ISBN 978-0-415-64481-5
Terms and conditions APPROVED DOCUMENT. Clear design Simple language
 Terms and conditions APPROVED DOCUMENT Clear design Simple language Terms and conditions 1. Welcome to Marcus by Goldman Sachs 2 2. How to contact us 2 3. How your Marcus account works 3 4. When we might
Terms and conditions APPROVED DOCUMENT Clear design Simple language Terms and conditions 1. Welcome to Marcus by Goldman Sachs 2 2. How to contact us 2 3. How your Marcus account works 3 4. When we might
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase. Term Paper Sample Topics
 A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
What most people do when they're thinking building an online business is they're just thinking a website.
 How to Build an Online Business What most people do when they're thinking building an online business is they're just thinking a website. You can't just think website anymore, it's more than that. But
How to Build an Online Business What most people do when they're thinking building an online business is they're just thinking a website. You can't just think website anymore, it's more than that. But
LISA: WE ARE BACK AND I'M LISA SCHAFFNER YOU ARE WATCHING HOW TO BUY A HOME THE RIGHT WAY
 LISA: WE ARE BACK AND I'M LISA SCHAFFNER YOU ARE WATCHING HOW TO BUY A HOME THE RIGHT WAY IN THIS PARTICULAR SEGMENT WE'RE GONNA TAKE A LOOK AT WHAT YOU SHOULD KNOW ABOUT WORKING WITH A LENDER AS WELL
LISA: WE ARE BACK AND I'M LISA SCHAFFNER YOU ARE WATCHING HOW TO BUY A HOME THE RIGHT WAY IN THIS PARTICULAR SEGMENT WE'RE GONNA TAKE A LOOK AT WHAT YOU SHOULD KNOW ABOUT WORKING WITH A LENDER AS WELL
3 SPEAKER: Maybe just your thoughts on finally. 5 TOMMY ARMOUR III: It's both, you look forward. 6 to it and don't look forward to it.
 1 1 FEBRUARY 10, 2010 2 INTERVIEW WITH TOMMY ARMOUR, III. 3 SPEAKER: Maybe just your thoughts on finally 4 playing on the Champions Tour. 5 TOMMY ARMOUR III: It's both, you look forward 6 to it and don't
1 1 FEBRUARY 10, 2010 2 INTERVIEW WITH TOMMY ARMOUR, III. 3 SPEAKER: Maybe just your thoughts on finally 4 playing on the Champions Tour. 5 TOMMY ARMOUR III: It's both, you look forward 6 to it and don't
Social Media, information and communication technologies: Part 3
 Social Media, information and communication technologies: Part 3 Providing social work services online/remotely This guideline will focus on the ethical considerations for social workers when using technology
Social Media, information and communication technologies: Part 3 Providing social work services online/remotely This guideline will focus on the ethical considerations for social workers when using technology
~ 1 ~ WELCOME TO:
 ~ 1 ~ WELCOME TO: Hi, and thank you for subscribing to my newsletter and downloading this e-book. First, I want to congratulate you for reading this because by doing so, you're way up ahead than all the
~ 1 ~ WELCOME TO: Hi, and thank you for subscribing to my newsletter and downloading this e-book. First, I want to congratulate you for reading this because by doing so, you're way up ahead than all the
Tough Questions and Answers
 Ready Reference G-5 Tough Questions and Answers In reviewing these responses, remember that these are sample answers. Please do not rehearse them verbatim or adopt them as your own. They are meant to get
Ready Reference G-5 Tough Questions and Answers In reviewing these responses, remember that these are sample answers. Please do not rehearse them verbatim or adopt them as your own. They are meant to get
Table of Contents. Introduction 3. How it Works 4. Who Can Benefit From GPT Sites 5. Getting Started 6
 Table of Contents Introduction 3 How it Works 4 Who Can Benefit From GPT Sites 5 Getting Started 6 Tips to Help You Maximize Your Profits Through Trial Offers 7 Site Registration 9 Completing Your First
Table of Contents Introduction 3 How it Works 4 Who Can Benefit From GPT Sites 5 Getting Started 6 Tips to Help You Maximize Your Profits Through Trial Offers 7 Site Registration 9 Completing Your First
"Of course you always lose your voice," she said "Your technique is wrong." And from that moment on, my life would never be the same.
 raesent Tempor Introduction "Of course you always lose your voice," she said "Your technique is wrong." And from that moment on, my life would never be the same. Yes, this is a story about one of my hobbies:
raesent Tempor Introduction "Of course you always lose your voice," she said "Your technique is wrong." And from that moment on, my life would never be the same. Yes, this is a story about one of my hobbies:
ICC POSITION ON LEGITIMATE INTERESTS
 ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
