Technology Evolutionary Games in Complex Transportation Systems in the Face of Adaptive Adversaries
|
|
|
- Sheila Powers
- 5 years ago
- Views:
Transcription
1 CREATE Research Archive Non-published Research Reports 2011 Technology Evolutionary Games in Complex Transportation Systems in the Face of Adaptive Adversaries Jun Zhuang University of Buffalo, The State University of New York, Elizabeth A. Newell University of Buffalo, The State University of New York Follow this and additional works at: Recommended Citation Zhuang, Jun and Newell, Elizabeth A., "Technology Evolutionary Games in Complex Transportation Systems in the Face of Adaptive Adversaries" (2011). Non-published Research Reports. Paper This Article is brought to you for free and open access by CREATE Research Archive. It has been accepted for inclusion in Non-published Research Reports by an authorized administrator of CREATE Research Archive. For more information, please contact
2 Technology Evolutionary Games in Complex Transportation Systems in the Face of Adaptive Adversaries May 5, 2011 Jun Zhuang Center for Risk and Economic Analysis of Terrorism Events (CREATE) Department of Industrial and Systems Engineering, University at Buffalo, SUNY Assistant Professor 403 Bell Hall, Buffalo, NY Elizabeth Newell Department of Industrial and Systems Engineering, University at Buffalo, SUNY Undergraduate Researcher 438 Bell Hall, Buffalo, NY This project was funded through the CREATE Center of Excellence by a grant from the United States Department of Homeland Security, Science and Technology Directorate, Office of University Programs.
3 Technology Evolutionary Games 2 Abstract There exists an evolutionary game between transportation systems and adaptive adversaries. The strategic interactions have high impacts on complex transportation systems, not only to security infrastructure, technologies, and costs, but also to the general public s travel pattern and welfare. In this research, we utilize evolutionary game theory to model the interactions between adaptive adversaries (such as terrorists) and transportation systems (including transportation authorities, companies, and the general public). All players adapt their strategies to the other players previous choices. By this, players maximize their own payoffs or welfare according to their preferences, and are subject to their own budget constraints. This research provides a general theoretical framework for decision-making in complex transportation systems in the face of adaptive adversaries, and provides managerial insights on when and where to adopt what technology in order to maximize the (long-run) social welfare of transportation systems. Keywords: Adaptive adversaries; Decision making; Evolutionary games; Security games; Technology Adoption Transportation systems
4 Technology Evolutionary Games 3 Technology Evolutionary Games in Complex Transportation Systems in the Face of Adaptive Adversaries Introduction There exists an evolutionary game between transportation systems and adaptive adversaries. For example, airport security can be modeled as an evolutionary game between transportation authorities and adaptive adversaries (e.g., terrorists) (Transportation Security Administration 2011). This evolutionary game started when three Romanian terrorists killed an aircrew member on board a Romanian Airline flight on July 25, On January 6, 1960, following the mid-air explosion by a suicide bomber who killed all thirty-four passengers on board a National Airline plane, transportation authorities started using baggage inspection devices. The United States government began using armed guards on commercial planes in response to the American airline flight being diverted to Cuba in May As well, U.S. President John F. Kennedy also signed legislation that made air piracy punishable by imprisonment or even death in 1961, in response to the Cuban flight diversion. The Federal Aviation Administration (FAA) developed profiling and metal detectors in screening passengers in response to eight airlines that were hijacked to Cuba early in Following the August 1969 hijacking of a United States aircraft flying outside the Western Hemisphere to Israel and being diverted to Syria, U.S. President Richard Nixon established an enforcement program known as the Customs Air Security Officers Program, or better known as the Sky Marshal Program, that attempts to stop hijacking. In March 1972, a Los Angeles bound flight from the John F. Kennedy International Airport was notified that they had a bomb on board. Minutes before it was set to detonate, a bomb-sniffing dog discovered a bomb, and thus, the FAA Explosives Detection Canine Team Program was created. But up until this point, immense loss
5 Technology Evolutionary Games 4 of human life due to adaptive adversaries had not occurred; planes were used as political messages, not as weapons. Following the September 11, 2001 terrorist attacks, this changed. Four planes were hijacked on that day; two flown into the Manhattan World Trade Centers, one flown into the Pentagon, and another, fortunately, crashed in Pennsylvania due to courageous passengers and crewmembers. About three thousand people were killed due to the attack. After, stricter security measures were put into effect. All passenger airplanes flying to the United States were required to have reinforced cockpit doors. The Transportation Security Administration (TSA) was created. Following these developments and other terrorist attacks since September 11, 2001, evolving terrorism methods have included box cutters, knives, shoe bombers, liquid-based explosives, and underwear bombers. The correspondingly evolving security measures following these methods include prohibiting knives, nail clippers, lighters, liquids and gels, and the recently adopted advanced imaging technology, full body scanners, and pat downs. Such strategic interactions and evolutionary measures have high impacts on the complex transportation systems, not only to the security infrastructure, technologies, and costs, but also to the general public s travel pattern and welfare. It is critical to understand the evolutionary dynamics from a system perspective, and understand when and where to adopt what technology in order to maximize the long-run social welfare of transportation systems. In this research, we provide a basic framework for technology evolutionary games in complex transportation systems in the face of adaptive adversaries.
6 Technology Evolutionary Games 5 Discussion In this section, we provide the problem statement, potential solution, and research methodology. We also include in this section results and challenges, who would benefit from this research, and a brief conclusion of our research. Statement of the Problem We propose to utilize evolutionary game theory (Sandholm 2002, 2010) to model the interactions between adaptive adversaries (such as terrorists) and transportation systems (including transportation authorities and the general public). Evolutionary game theory is a branch of game theory that applies to the evolving interactions between strategically dependent players. It began as a mathematical way to model complex changes in biological systems in 1930 (Fisher, 1930), and evolved to applications in economics, sociology, anthropology and philosophy and other social sciences. Its applications have been used to model social norms and beliefs, and how they have evolved over time depending on the moves and interactions of different players in the system. When viewing the changing technology as an evolutionary game, we are able to better study the changes that occur between the transportation systems and the adaptive adversary. To the best of our knowledge, there is no previous work utilizing evolutionary games to study the strategic interactions between terrorists and transportation systems. Statement of the Potential Solution and the Research Methodology First, we model the evolutionary game by specifying the following four critical factors: 1) Players: a. Transportation Authorities (Defenders): Such as the U.S. Transportation Security Administration (TSA), and other federal and local authorities.
7 Technology Evolutionary Games 6 b. Transportation Users (Private Citizens): Such as private citizens, commercial/business users, and government employees. c. Adaptive Adversaries (Attackers): Including terrorist organizations who would be interested in attacking transportation systems. 2) Objectives/payoffs for each player, including measures of, and preferences for, defense costs and potential casualties and economic losses (for the transportation authorities), and psychological, economic, political, religious, and financial costs and benefits (for adaptive adversaries). Multi-attribute utility theory will be used to model these objectives (Keeney and Raiffa 1976; Keeney 2007). (3) Options for each player, including the transportation authorities decision on when, what technology/security measures to adopt (such as metal detectors, full body scanners, and patdowns) and where to adopt (urban areas such as New York City, Washington, DC, Los Angeles, Miami, Chicago, Philadelphia, Buffalo, Tampa); the transportation users travel choices (such as air flights, subways, trains, buses, ferries and personal cars); and adaptive adversaries options of when and where to use what methods of attack, including the scenarios of attacking a mass transit system in a major United States city, attacking a major transportation infrastructure component such as a large suspension bridge, and using transportation as an attack vector such as to spread contagious diseases or dissemination of other chemical, biological, nuclear, radiological or explosive agents. (4) Information and uncertainties: human-terrain data, previous observed and unobserved actions, and possible information disclosure strategies (such as secrecy, truthful and deceptive disclosure, as studied previously by the author; see Zhuang and Bier 2010, and Zhuang et al. 2010). Those previous works show that when the first mover possesses some private
8 Technology Evolutionary Games 7 information, he/she may prefer to use secrecy or deception to mislead the second mover. We will assume that the players have uncertainties about other players attributes using subjective probability distributions, and update their beliefs in a Bayesian manner during the duration of the game. Consider a discrete-time horizon, where. There are N types of methods of defense and M types of methods of attack on K targets. In the beginning of period t, the defense level is D n,k,t-1 for each of the defense methods n=1,,n on each target k=1,, K, where D n,k,0 is the original defense level for method type n on target k. The attacker observes those defense levels and finds certain weaknesses in the system D k,t-1 ={D n,k,t-1 ; n=1,,n} and chooses the attack method for target k=1,,k, where A k,t =0 implies no attack. The defender observes the attack levels A k,t that it created through its preparation and mitigation stages, and responds by defense levels D t (A t, D t-1 ), where A t ={A k,t ; k=1,,k} and D t ={A k,t ; k=1,,k}; following the adaptive adversaries attack, the defender will recover, and choose whether and how to retaliate. Finally, the private citizens (travelers) observe the attack and defense levels and methods on each target, and select their travel pattern P t based off their assumptions in safety and in transportation hassle. Then the game evolves to the next period t+1. The sequence of move is illustrated in Image 1.
9 Technology Evolutionary Games 8 IMAGE 1: Sequence of Actions for the T-period Evolutionary Game The discount factors are denoted as,, and for the attacker, the defender, and private citizens, respectively. When the discount factors equal zero, the players are fully myopic and only care about the payoffs for the current periods. When the discount factors equal one, the players are fully farsighted and equally value the payoffs for the current and the future periods. As a starting point, we assume each player is fully strategic, and we want to maximize the longrun discounted payoffs by choosing the optimal choices at each period. That is, for the attacker, we have the total discounted payoffs equal to: T t"1 $ U A = #! A & t=1 % K # k=1 ' u A,k (A k,t, D k,t"1 )) ( where u A,k is the attacker s payoff obtained from target k, as a function of the previous-period defense and current-period attack. The payoff function includes the costs of the attack effort, and the (expected) benefits from a successful attack. We have u A,k (A k,t, D k,t-1 ) decreases in D k,t-1 and may increase or decrease in A k,t, depending on the costs of the attack effort. By modeling the
10 Technology Evolutionary Games 9 costs of attacks, we implicitly model or at least approximate the budget constraints for the attacker. For the defender, we have the total discounted payoffs equal to: T t"1 $ U D = #! D & t=1 % K # k=1 ' u D,k (D k,t, P t (A t, D t ) A k,t, D k,t"1 )) ( where u D,k is the defender s payoff obtained from target k, as a function of the current-period defense and potential private citizens response P t (A t, D t ), given previous period defense and current-period attack efforts. The payoff function includes the cost of operating the current technology level, and researching and developing new technology, as well as retaliating for the attack costs. We have u D,k decreases in A k,t. By modeling the costs of defense, we implicitly model or at least approximate the budget constraints for the defender. For the private citizens, we have the total discounted payoffs equal to: where u P is the private citizens payoff as a function of the reaction P t given attack and defense levels. The payoff function could include costs and inconveniences/congestion (Wang and Zhuang 2011) due to the changes of travel patterns. We define the subgame perfect Nash equilibrium such that at each decision point, each player chooses the options that maximize the total discounted future payoffs. Statement of the End Users/Customers/ Who Would Benefit Following the above work that is introduced in this white paper, the Department of Homeland Security/Transportation Security Administration (DHS/TSA) would benefit. In particular, this research will provide a general theoretical framework for decision making in such complex transportation systems in the face of adaptive adversaries. This model could be verified
11 Technology Evolutionary Games 10 and evaluated using historical data. Using simulation, this research will provide some novel insights on possible future evolutionary paths; e.g., when and where to adopt what technology, in order to maximize the long-run social welfare of transportation systems. Statement of the Challenges in Attaining the Solution and Results There are multiple challenges in modeling the evolutionary games and attaining the solution and results. First, even the current model has already specified when (the time period) and where (the target) to use what technology (defense method), and there are many more important factors that need to be considered. This includes incomplete information, risk attitudes, possible secrecy and deception, multiple types of players and players possible non-strategic behavior (Hao et al. 2009) and errors (Zhuang, 2010). Second, the sets of potential attack/defense methods, potential targets, and time periods could be uncertain by themselves, further complicating the modeling of incomplete information. Third, it may be difficult to get data for estimating the parameters in the models. Finally, it could be computationally intractable in attaining the solution and results, especially at real-world scale. Conclusion In this work, we provide a basic framework for technology evolutionary games in complex transportation systems in the face of adaptive adversaries. In the future, we would like to mathematically solve the game, verify, and evaluate the models using historical and simulated data. Through this work, we expect to provide insights to the following question: what is the cost-benefit analysis of adopting particular technologies, considering the adaptive traveler and adversary behavior. For example, we expect to find the following results: (a) the defender may not always want to adopt the most advanced technology to fix the most vulnerable parts of the system, especially when the attacker has an alternative attacking method or targets at relatively
12 Technology Evolutionary Games 11 low costs, or when the private citizen would change travel patterns in a unfavorable manner responding to such adoption; (b) the defender may not want to invest in technology on certain targets, if the technology/target is not the most vulnerable (or most attractive to the terrorist) component of the system; and (c) the defender may want to strategically delay the adoption of technology, if doing so would prevent the adaptive adversary behavior from evolving to a more detrimental path.
13 Technology Evolutionary Games 12 References Fisher, R. A. (1930) The Genetic Theory of Natural Selection. Clarendon Press. Oxford, UK. Hao, M., S. Jin and J. Zhuang. (2009) Robustness of Optimal Defensive Resource Allocations in the Face of Less than Fully Rational Attackers, Proceedings of the 2009 Industrial Engineering Research Conference, p.p Keeney, R.L. Modeling values for anti-terrorism analysis, Risk Analysis, 27(3): , Keeney, R.L. and H. Raiffa. Decisions with Multiple Objectives: Preferences and Value Tradeoffs. Wiley, New York, NY, Sandholm, W. H. (2002). Evolutionary Implementation and Congestion Pricing. Review of Economic Studies, 69, Sandholm, W. H. (2010). Population Games and Evolutionary Dynamics. MIT Press. Cambridge, MA. Transportation Security Administration. (2011). Checkpoint Evolution. URL: Accessed April 25, Wang, X. and J. Zhuang. (2011). Balancing Congestion and Security in the Presence of Strategic Applicants with Private Information. European Journal of Operational Research, 212(1): , Zhuang, J. (2010). Impacts of Subsidized Security on Stability and Total Social Costs of Equilibrium Solutions in an N-Player Game with Errors. The Engineering Economist, 55(2), Zhuang, J. and V.M. Bier. (2010). Reasons for Secrecy and Deception in Homeland-Security Resource Allocation. Risk Analysis, 30(12),
14 Technology Evolutionary Games 13 Zhuang, J., V.M. Bier, and O. Alagoz. (2010). Modeling Secrecy and Deception in a Multipleperiod Attacker-Defender Signaling Game. European Journal of Operational Research, 203(2),
Stochastic Game Models for Homeland Security
 CREATE Research Archive Research Project Summaries 2008 Stochastic Game Models for Homeland Security Erim Kardes University of Southern California, kardes@usc.edu Follow this and additional works at: http://research.create.usc.edu/project_summaries
CREATE Research Archive Research Project Summaries 2008 Stochastic Game Models for Homeland Security Erim Kardes University of Southern California, kardes@usc.edu Follow this and additional works at: http://research.create.usc.edu/project_summaries
Game Theory for Safety and Security. Arunesh Sinha
 Game Theory for Safety and Security Arunesh Sinha Motivation: Real World Security Issues 2 Central Problem Allocating limited security resources against an adaptive, intelligent adversary 3 Prior Work
Game Theory for Safety and Security Arunesh Sinha Motivation: Real World Security Issues 2 Central Problem Allocating limited security resources against an adaptive, intelligent adversary 3 Prior Work
Modeling Security Decisions as Games
 Modeling Security Decisions as Games Chris Kiekintveld University of Texas at El Paso.. and MANY Collaborators Decision Making and Games Research agenda: improve and justify decisions Automated intelligent
Modeling Security Decisions as Games Chris Kiekintveld University of Texas at El Paso.. and MANY Collaborators Decision Making and Games Research agenda: improve and justify decisions Automated intelligent
Design of intelligent surveillance systems: a game theoretic case. Nicola Basilico Department of Computer Science University of Milan
 Design of intelligent surveillance systems: a game theoretic case Nicola Basilico Department of Computer Science University of Milan Introduction Intelligent security for physical infrastructures Our objective:
Design of intelligent surveillance systems: a game theoretic case Nicola Basilico Department of Computer Science University of Milan Introduction Intelligent security for physical infrastructures Our objective:
A short introduction to Security Games
 Game Theoretic Foundations of Multiagent Systems: Algorithms and Applications A case study: Playing Games for Security A short introduction to Security Games Nicola Basilico Department of Computer Science
Game Theoretic Foundations of Multiagent Systems: Algorithms and Applications A case study: Playing Games for Security A short introduction to Security Games Nicola Basilico Department of Computer Science
Innovations in Risk and Economic Modeling of Counterterrorism
 CREATE Research Archive Research Project Summaries 2011 Innovations in Risk and Economic Modeling of Counterterrorism Vicki M. Bier University of Wisconsin Madison, bier@engr.wisc.edu Follow this and additional
CREATE Research Archive Research Project Summaries 2011 Innovations in Risk and Economic Modeling of Counterterrorism Vicki M. Bier University of Wisconsin Madison, bier@engr.wisc.edu Follow this and additional
Sequential Multi-Channel Access Game in Distributed Cognitive Radio Networks
 Sequential Multi-Channel Access Game in Distributed Cognitive Radio Networks Chunxiao Jiang, Yan Chen, and K. J. Ray Liu Department of Electrical and Computer Engineering, University of Maryland, College
Sequential Multi-Channel Access Game in Distributed Cognitive Radio Networks Chunxiao Jiang, Yan Chen, and K. J. Ray Liu Department of Electrical and Computer Engineering, University of Maryland, College
Heuristics, Optimization, and Equilibrium Analysis for Automated Wargames
 CREATE Research Archive Non-published Research Reports 2012 Heuristics, Optimization, and Equilibrium Analysis for Automated Wargames Jun Zhuang University of Buffalo, The State University of New York,
CREATE Research Archive Non-published Research Reports 2012 Heuristics, Optimization, and Equilibrium Analysis for Automated Wargames Jun Zhuang University of Buffalo, The State University of New York,
Research Statement Arunesh Sinha aruneshs/
 Research Statement Arunesh Sinha aruneshs@usc.edu http://www-bcf.usc.edu/ aruneshs/ Research Theme My research lies at the intersection of Artificial Intelligence and Security 1 and Privacy. Security and
Research Statement Arunesh Sinha aruneshs@usc.edu http://www-bcf.usc.edu/ aruneshs/ Research Theme My research lies at the intersection of Artificial Intelligence and Security 1 and Privacy. Security and
S&T Stakeholders Conference
 S&T Stakeholders Conference May 21-24, 2007 Future Attribute Screening Technology Mobile Module (FAST M 2 ) Innovation/HSARPA HIP Bob Burns Program Manager Office of Innovation/Human Factors Division Science
S&T Stakeholders Conference May 21-24, 2007 Future Attribute Screening Technology Mobile Module (FAST M 2 ) Innovation/HSARPA HIP Bob Burns Program Manager Office of Innovation/Human Factors Division Science
Homemade Explosives (HME) Program Overview. Doug Bauer, PhD Explosives Division Science and Technology Directorate
 Homemade Explosives (HME) Program Overview Doug Bauer, PhD Explosives Division Science and Technology Directorate 1 The HME Threat and DHS S&T Numerous attempted and executed terrorist attacks involving
Homemade Explosives (HME) Program Overview Doug Bauer, PhD Explosives Division Science and Technology Directorate 1 The HME Threat and DHS S&T Numerous attempted and executed terrorist attacks involving
Game Theory. Department of Electronics EL-766 Spring Hasan Mahmood
 Game Theory Department of Electronics EL-766 Spring 2011 Hasan Mahmood Email: hasannj@yahoo.com Course Information Part I: Introduction to Game Theory Introduction to game theory, games with perfect information,
Game Theory Department of Electronics EL-766 Spring 2011 Hasan Mahmood Email: hasannj@yahoo.com Course Information Part I: Introduction to Game Theory Introduction to game theory, games with perfect information,
Two Modeling Cultures. Marco Janssen School of Sustainability Center for Behavior, Institutions and the Environment Arizona State University
 Two Modeling Cultures Marco Janssen School of Sustainability Center for Behavior, Institutions and the Environment Arizona State University Outline Background Brief history of integrated global models
Two Modeling Cultures Marco Janssen School of Sustainability Center for Behavior, Institutions and the Environment Arizona State University Outline Background Brief history of integrated global models
Asynchronous Best-Reply Dynamics
 Asynchronous Best-Reply Dynamics Noam Nisan 1, Michael Schapira 2, and Aviv Zohar 2 1 Google Tel-Aviv and The School of Computer Science and Engineering, The Hebrew University of Jerusalem, Israel. 2 The
Asynchronous Best-Reply Dynamics Noam Nisan 1, Michael Schapira 2, and Aviv Zohar 2 1 Google Tel-Aviv and The School of Computer Science and Engineering, The Hebrew University of Jerusalem, Israel. 2 The
Appendix A A Primer in Game Theory
 Appendix A A Primer in Game Theory This presentation of the main ideas and concepts of game theory required to understand the discussion in this book is intended for readers without previous exposure to
Appendix A A Primer in Game Theory This presentation of the main ideas and concepts of game theory required to understand the discussion in this book is intended for readers without previous exposure to
Chemical-Biological Defense S&T For Homeland Security
 DHS SCIENCE AND TECHNOLOGY Chemical-Biological Defense S&T For Homeland Security August 2017 Dr. John W. Fischer Director, Chemical Biological Defense Division Homeland Security Advanced Research Projects
DHS SCIENCE AND TECHNOLOGY Chemical-Biological Defense S&T For Homeland Security August 2017 Dr. John W. Fischer Director, Chemical Biological Defense Division Homeland Security Advanced Research Projects
Executive Summary: Understanding Risk Communication Best Practices and Theory
 Executive Summary: Understanding Risk Communication Best Practices and Theory Report to the Human Factors/Behavioral Sciences Division, Science and Technology Directorate, U.S. Department of Homeland Security
Executive Summary: Understanding Risk Communication Best Practices and Theory Report to the Human Factors/Behavioral Sciences Division, Science and Technology Directorate, U.S. Department of Homeland Security
Mehrdad Amirghasemi a* Reza Zamani a
 The roles of evolutionary computation, fitness landscape, constructive methods and local searches in the development of adaptive systems for infrastructure planning Mehrdad Amirghasemi a* Reza Zamani a
The roles of evolutionary computation, fitness landscape, constructive methods and local searches in the development of adaptive systems for infrastructure planning Mehrdad Amirghasemi a* Reza Zamani a
Copyright 2008, Yan Chen
 Unless otherwise noted, the content of this course material is licensed under a Creative Commons Attribution Non-Commercial 3.0 License. http://creativecommons.org/licenses/by-nc/3.0/ Copyright 2008, Yan
Unless otherwise noted, the content of this course material is licensed under a Creative Commons Attribution Non-Commercial 3.0 License. http://creativecommons.org/licenses/by-nc/3.0/ Copyright 2008, Yan
THEORY: NASH EQUILIBRIUM
 THEORY: NASH EQUILIBRIUM 1 The Story Prisoner s Dilemma Two prisoners held in separate rooms. Authorities offer a reduced sentence to each prisoner if he rats out his friend. If a prisoner is ratted out
THEORY: NASH EQUILIBRIUM 1 The Story Prisoner s Dilemma Two prisoners held in separate rooms. Authorities offer a reduced sentence to each prisoner if he rats out his friend. If a prisoner is ratted out
April 10, Develop and demonstrate technologies needed to remotely detect the early stages of a proliferant nation=s nuclear weapons program.
 Statement of Robert E. Waldron Assistant Deputy Administrator for Nonproliferation Research and Engineering National Nuclear Security Administration U. S. Department of Energy Before the Subcommittee on
Statement of Robert E. Waldron Assistant Deputy Administrator for Nonproliferation Research and Engineering National Nuclear Security Administration U. S. Department of Energy Before the Subcommittee on
Repeated Games. Economics Microeconomic Theory II: Strategic Behavior. Shih En Lu. Simon Fraser University (with thanks to Anke Kessler)
 Repeated Games Economics 302 - Microeconomic Theory II: Strategic Behavior Shih En Lu Simon Fraser University (with thanks to Anke Kessler) ECON 302 (SFU) Repeated Games 1 / 25 Topics 1 Information Sets
Repeated Games Economics 302 - Microeconomic Theory II: Strategic Behavior Shih En Lu Simon Fraser University (with thanks to Anke Kessler) ECON 302 (SFU) Repeated Games 1 / 25 Topics 1 Information Sets
CHAPTER LEARNING OUTCOMES. By the end of this section, students will be able to:
 CHAPTER 4 4.1 LEARNING OUTCOMES By the end of this section, students will be able to: Understand what is meant by a Bayesian Nash Equilibrium (BNE) Calculate the BNE in a Cournot game with incomplete information
CHAPTER 4 4.1 LEARNING OUTCOMES By the end of this section, students will be able to: Understand what is meant by a Bayesian Nash Equilibrium (BNE) Calculate the BNE in a Cournot game with incomplete information
Dynamics and Coevolution in Multi Level Strategic interaction Games. (CoNGas)
 Dynamics and Coevolution in Multi Level Strategic interaction Games (CoNGas) Francesco De Pellegrini CREATE-NET Obj. ICT-2011 9.7 DyM-CS 15/06/2012 Abstract Many real world systems possess a rich multi-level
Dynamics and Coevolution in Multi Level Strategic interaction Games (CoNGas) Francesco De Pellegrini CREATE-NET Obj. ICT-2011 9.7 DyM-CS 15/06/2012 Abstract Many real world systems possess a rich multi-level
Chapter 13. Game Theory
 Chapter 13 Game Theory A camper awakens to the growl of a hungry bear and sees his friend putting on a pair of running shoes. You can t outrun a bear, scoffs the camper. His friend coolly replies, I don
Chapter 13 Game Theory A camper awakens to the growl of a hungry bear and sees his friend putting on a pair of running shoes. You can t outrun a bear, scoffs the camper. His friend coolly replies, I don
ECON 312: Games and Strategy 1. Industrial Organization Games and Strategy
 ECON 312: Games and Strategy 1 Industrial Organization Games and Strategy A Game is a stylized model that depicts situation of strategic behavior, where the payoff for one agent depends on its own actions
ECON 312: Games and Strategy 1 Industrial Organization Games and Strategy A Game is a stylized model that depicts situation of strategic behavior, where the payoff for one agent depends on its own actions
3 Game Theory II: Sequential-Move and Repeated Games
 3 Game Theory II: Sequential-Move and Repeated Games Recognizing that the contributions you make to a shared computer cluster today will be known to other participants tomorrow, you wonder how that affects
3 Game Theory II: Sequential-Move and Repeated Games Recognizing that the contributions you make to a shared computer cluster today will be known to other participants tomorrow, you wonder how that affects
Sequential Games When there is a sufficient lag between strategy choices our previous assumption of simultaneous moves may not be realistic. In these
 When there is a sufficient lag between strategy choices our previous assumption of simultaneous moves may not be realistic. In these settings, the assumption of sequential decision making is more realistic.
When there is a sufficient lag between strategy choices our previous assumption of simultaneous moves may not be realistic. In these settings, the assumption of sequential decision making is more realistic.
UNCLASSIFIED. UNCLASSIFIED R-1 Line Item #13 Page 1 of 11
 Exhibit R-2, PB 2010 Air Force RDT&E Budget Item Justification DATE: May 2009 Applied Research COST ($ in Millions) FY 2008 Actual FY 2009 FY 2010 FY 2011 FY 2012 FY 2013 FY 2014 FY 2015 Cost To Complete
Exhibit R-2, PB 2010 Air Force RDT&E Budget Item Justification DATE: May 2009 Applied Research COST ($ in Millions) FY 2008 Actual FY 2009 FY 2010 FY 2011 FY 2012 FY 2013 FY 2014 FY 2015 Cost To Complete
Game Theory: The Basics. Theory of Games and Economics Behavior John Von Neumann and Oskar Morgenstern (1943)
 Game Theory: The Basics The following is based on Games of Strategy, Dixit and Skeath, 1999. Topic 8 Game Theory Page 1 Theory of Games and Economics Behavior John Von Neumann and Oskar Morgenstern (1943)
Game Theory: The Basics The following is based on Games of Strategy, Dixit and Skeath, 1999. Topic 8 Game Theory Page 1 Theory of Games and Economics Behavior John Von Neumann and Oskar Morgenstern (1943)
Introduction: What is Game Theory?
 Microeconomics I: Game Theory Introduction: What is Game Theory? (see Osborne, 2009, Sect 1.1) Dr. Michael Trost Department of Applied Microeconomics October 25, 2013 Dr. Michael Trost Microeconomics I:
Microeconomics I: Game Theory Introduction: What is Game Theory? (see Osborne, 2009, Sect 1.1) Dr. Michael Trost Department of Applied Microeconomics October 25, 2013 Dr. Michael Trost Microeconomics I:
Economic Systems as Constructively Rational Games: Oh, the Places We Could Go!
 Economics Presentations, Posters and Proceedings Economics 2016 Economic Systems as Constructively Rational Games: Oh, the Places We Could Go! Leigh Tesfatsion Iowa State University, tesfatsi@iastate.edu
Economics Presentations, Posters and Proceedings Economics 2016 Economic Systems as Constructively Rational Games: Oh, the Places We Could Go! Leigh Tesfatsion Iowa State University, tesfatsi@iastate.edu
Anavilhanas Natural Reserve (about 4000 Km 2 )
 Anavilhanas Natural Reserve (about 4000 Km 2 ) A control room receives this alarm signal: what to do? adversarial patrolling with spatially uncertain alarm signals Nicola Basilico, Giuseppe De Nittis,
Anavilhanas Natural Reserve (about 4000 Km 2 ) A control room receives this alarm signal: what to do? adversarial patrolling with spatially uncertain alarm signals Nicola Basilico, Giuseppe De Nittis,
CSCI 699: Topics in Learning and Game Theory Fall 2017 Lecture 3: Intro to Game Theory. Instructor: Shaddin Dughmi
 CSCI 699: Topics in Learning and Game Theory Fall 217 Lecture 3: Intro to Game Theory Instructor: Shaddin Dughmi Outline 1 Introduction 2 Games of Complete Information 3 Games of Incomplete Information
CSCI 699: Topics in Learning and Game Theory Fall 217 Lecture 3: Intro to Game Theory Instructor: Shaddin Dughmi Outline 1 Introduction 2 Games of Complete Information 3 Games of Incomplete Information
Optimal Bandwidth Allocation with Dynamic Service Selection in Heterogeneous Wireless Networks
 Optimal Bandwidth Allocation Dynamic Service Selection in Heterogeneous Wireless Networs Kun Zhu, Dusit Niyato, and Ping Wang School of Computer Engineering, Nanyang Technological University NTU), Singapore
Optimal Bandwidth Allocation Dynamic Service Selection in Heterogeneous Wireless Networs Kun Zhu, Dusit Niyato, and Ping Wang School of Computer Engineering, Nanyang Technological University NTU), Singapore
TRB Workshop on the Future of Road Vehicle Automation
 TRB Workshop on the Future of Road Vehicle Automation Steven E. Shladover University of California PATH Program ITFVHA Meeting, Vienna October 21, 2012 1 Outline TRB background Workshop organization Automation
TRB Workshop on the Future of Road Vehicle Automation Steven E. Shladover University of California PATH Program ITFVHA Meeting, Vienna October 21, 2012 1 Outline TRB background Workshop organization Automation
Computational Methods for Non-Cooperative Game Theory
 Computational Methods for Non-Cooperative Game Theory What is a game? Introduction A game is a decision problem in which there a multiple decision makers, each with pay-off interdependence Each decisions
Computational Methods for Non-Cooperative Game Theory What is a game? Introduction A game is a decision problem in which there a multiple decision makers, each with pay-off interdependence Each decisions
February 11, 2015 :1 +0 (1 ) = :2 + 1 (1 ) =3 1. is preferred to R iff
 February 11, 2015 Example 60 Here s a problem that was on the 2014 midterm: Determine all weak perfect Bayesian-Nash equilibria of the following game. Let denote the probability that I assigns to being
February 11, 2015 Example 60 Here s a problem that was on the 2014 midterm: Determine all weak perfect Bayesian-Nash equilibria of the following game. Let denote the probability that I assigns to being
Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility
 Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility theorem (consistent decisions under uncertainty should
Summary Overview of Topics in Econ 30200b: Decision theory: strong and weak domination by randomized strategies, domination theorem, expected utility theorem (consistent decisions under uncertainty should
Academic Year
 2017-2018 Academic Year Note: The research questions and topics listed below are offered for consideration by faculty and students. If you have other ideas for possible research, the Academic Alliance
2017-2018 Academic Year Note: The research questions and topics listed below are offered for consideration by faculty and students. If you have other ideas for possible research, the Academic Alliance
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks
 Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
One Step Behind. The catch up mind-set that permeates the security industry.
 One Step Behind. The catch up mind-set that permeates the security industry. A white paper discussing the divergence between the efficacy of current fixed point, single use security equipment and the increasing
One Step Behind. The catch up mind-set that permeates the security industry. A white paper discussing the divergence between the efficacy of current fixed point, single use security equipment and the increasing
Power Napping with Loud Neighbors: Optimal Energy-Constrained Jamming and Anti-Jamming
 Power Napping with Loud Neighbors: Optimal Energy-Constrained Jamming and Anti-Jamming Bruce DeBruhl, Christian Kroer, Anupam Datta, Tuomas Sandholm, and Patrick Tague Carnegie Mellon University {debruhl@,
Power Napping with Loud Neighbors: Optimal Energy-Constrained Jamming and Anti-Jamming Bruce DeBruhl, Christian Kroer, Anupam Datta, Tuomas Sandholm, and Patrick Tague Carnegie Mellon University {debruhl@,
Guidetti Translates Thesis Into Profession
 Calhoun: The NPS Institutional Archive News Center News Articles Collection 2009-11 Guidetti Translates Thesis Into Profession Center for Homeland Defense and Security Naval Postgraduate School, Monterey,
Calhoun: The NPS Institutional Archive News Center News Articles Collection 2009-11 Guidetti Translates Thesis Into Profession Center for Homeland Defense and Security Naval Postgraduate School, Monterey,
Using Proof-of-Work to Coordinate
 Using Proof-of-Work to Coordinate Adam Brandenburger* and Kai Steverson * J.P. Valles Professor, NYU Stern School of Business Distinguished Professor, NYU Tandon School of Engineering Faculty Director,
Using Proof-of-Work to Coordinate Adam Brandenburger* and Kai Steverson * J.P. Valles Professor, NYU Stern School of Business Distinguished Professor, NYU Tandon School of Engineering Faculty Director,
Information and Communications Technology and Environmental Regulation: Critical Perspectives
 Image: European Space Agency Information and Communications Technology and Environmental Regulation: Critical Perspectives Rónán Kennedy School of Law, National University of Ireland Galway ronan.m.kennedy@nuigalway.ie
Image: European Space Agency Information and Communications Technology and Environmental Regulation: Critical Perspectives Rónán Kennedy School of Law, National University of Ireland Galway ronan.m.kennedy@nuigalway.ie
Quantifying Flexibility in the Operationally Responsive Space Paradigm
 Executive Summary of Master s Thesis MIT Systems Engineering Advancement Research Initiative Quantifying Flexibility in the Operationally Responsive Space Paradigm Lauren Viscito Advisors: D. H. Rhodes
Executive Summary of Master s Thesis MIT Systems Engineering Advancement Research Initiative Quantifying Flexibility in the Operationally Responsive Space Paradigm Lauren Viscito Advisors: D. H. Rhodes
HOMELAND SECURITY & EMERGENCY MANAGEMENT (HSEM)
 Homeland Security & Emergency Management (HSEM) 1 HOMELAND SECURITY & EMERGENCY MANAGEMENT (HSEM) HSEM 501 CRITICAL ISSUES IN This course reintroduces the homeland security professional to the wicked problems
Homeland Security & Emergency Management (HSEM) 1 HOMELAND SECURITY & EMERGENCY MANAGEMENT (HSEM) HSEM 501 CRITICAL ISSUES IN This course reintroduces the homeland security professional to the wicked problems
Experimental Economics A EXPLORATIONS IN ECONOMIC HISTORY A FINANCE AND STOCHASTICS A FINANCIAL MANAGEMENT (el.
 A+ Journals ACADEMY OF MANAGEMENT JOURNAL 0001-4273 A+ ACADEMY OF MANAGEMENT REVIEW 0363-7425 A+ ACCOUNTING ORGANIZATIONS AND SOCIETY 0361-3682 A+ ACCOUNTING REVIEW 0001-4826 A+ ADMINISTRATIVE SCIENCE
A+ Journals ACADEMY OF MANAGEMENT JOURNAL 0001-4273 A+ ACADEMY OF MANAGEMENT REVIEW 0363-7425 A+ ACCOUNTING ORGANIZATIONS AND SOCIETY 0361-3682 A+ ACCOUNTING REVIEW 0001-4826 A+ ADMINISTRATIVE SCIENCE
Nuclear Safety and Security Culture Roles and Responsibilities of Individuals. Middle East Scientific Institute for Security (MESIS)
 Nuclear Safety and Security Culture Roles and Responsibilities of Individuals 8 th Annual RMCC Workshop Middle East Scientific Institute for Security (MESIS) Amman, Jordan June 17-19, 2013 Dr. J. David
Nuclear Safety and Security Culture Roles and Responsibilities of Individuals 8 th Annual RMCC Workshop Middle East Scientific Institute for Security (MESIS) Amman, Jordan June 17-19, 2013 Dr. J. David
Reading Robert Gibbons, A Primer in Game Theory, Harvester Wheatsheaf 1992.
 Reading Robert Gibbons, A Primer in Game Theory, Harvester Wheatsheaf 1992. Additional readings could be assigned from time to time. They are an integral part of the class and you are expected to read
Reading Robert Gibbons, A Primer in Game Theory, Harvester Wheatsheaf 1992. Additional readings could be assigned from time to time. They are an integral part of the class and you are expected to read
A Modified Perspective of Decision Support in C 2
 SAND2005-2938C A Modified Perspective of Decision Support in C 2 June 14, 2005 Michael Senglaub, PhD Dave Harris Sandia National Labs Sandia is a multiprogram laboratory operated by Sandia Corporation,
SAND2005-2938C A Modified Perspective of Decision Support in C 2 June 14, 2005 Michael Senglaub, PhD Dave Harris Sandia National Labs Sandia is a multiprogram laboratory operated by Sandia Corporation,
Finite games: finite number of players, finite number of possible actions, finite number of moves. Canusegametreetodepicttheextensiveform.
 A game is a formal representation of a situation in which individuals interact in a setting of strategic interdependence. Strategic interdependence each individual s utility depends not only on his own
A game is a formal representation of a situation in which individuals interact in a setting of strategic interdependence. Strategic interdependence each individual s utility depends not only on his own
Fundamental Research in Systems Engineering: Asking Why? rather than How?
 Fundamental Research in Systems Engineering: Asking Why? rather than How? Chris Paredis Program Director NSF ENG/CMMI Engineering & Systems Design, Systems Science cparedis@nsf.gov (703) 292-2241 1 Disclaimer
Fundamental Research in Systems Engineering: Asking Why? rather than How? Chris Paredis Program Director NSF ENG/CMMI Engineering & Systems Design, Systems Science cparedis@nsf.gov (703) 292-2241 1 Disclaimer
An Integrated Expert User with End User in Technology Acceptance Model for Actual Evaluation
 Computer and Information Science; Vol. 9, No. 1; 2016 ISSN 1913-8989 E-ISSN 1913-8997 Published by Canadian Center of Science and Education An Integrated Expert User with End User in Technology Acceptance
Computer and Information Science; Vol. 9, No. 1; 2016 ISSN 1913-8989 E-ISSN 1913-8997 Published by Canadian Center of Science and Education An Integrated Expert User with End User in Technology Acceptance
/13/$ IEEE
 A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
Chapter 1: Introduction to Neuro-Fuzzy (NF) and Soft Computing (SC)
 Chapter 1: Introduction to Neuro-Fuzzy (NF) and Soft Computing (SC) Introduction (1.1) SC Constituants and Conventional Artificial Intelligence (AI) (1.2) NF and SC Characteristics (1.3) Jyh-Shing Roger
Chapter 1: Introduction to Neuro-Fuzzy (NF) and Soft Computing (SC) Introduction (1.1) SC Constituants and Conventional Artificial Intelligence (AI) (1.2) NF and SC Characteristics (1.3) Jyh-Shing Roger
Advanced Microeconomics: Game Theory
 Advanced Microeconomics: Game Theory P. v. Mouche Wageningen University 2018 Outline 1 Motivation 2 Games in strategic form 3 Games in extensive form What is game theory? Traditional game theory deals
Advanced Microeconomics: Game Theory P. v. Mouche Wageningen University 2018 Outline 1 Motivation 2 Games in strategic form 3 Games in extensive form What is game theory? Traditional game theory deals
Emerging Security Challenges Division NATO
 NATO Science for Peace and Security (SPS) Programme Workshop on CBRN Defence 22-24 October 2013 Brussels Emerging Security Challenges Division NATO 1 NATO Science for Peace and Security (SPS) Programme
NATO Science for Peace and Security (SPS) Programme Workshop on CBRN Defence 22-24 October 2013 Brussels Emerging Security Challenges Division NATO 1 NATO Science for Peace and Security (SPS) Programme
Game Theoretic Analysis of Security and Sustainability
 Game Theoretic Analysis of Security and Sustainability Bo An boan@ntu.edu.sg School of Computer Science and Engineering Nanyang Technological University August 22, 2017@IJCAI 17, Early Career Spotlight
Game Theoretic Analysis of Security and Sustainability Bo An boan@ntu.edu.sg School of Computer Science and Engineering Nanyang Technological University August 22, 2017@IJCAI 17, Early Career Spotlight
The Underwear Bomber
 The Underwear Bomber A Case Study of Inside-Out Risk Management KIP HAWLEY CENTER FOR HOMELAND DEFENSE AND SECURITY DEPT. OF NATIONAL SECURITY AFFAIRS NAVAL POSTGRADUATE SCHOOL Slide 1 Opening Credits
The Underwear Bomber A Case Study of Inside-Out Risk Management KIP HAWLEY CENTER FOR HOMELAND DEFENSE AND SECURITY DEPT. OF NATIONAL SECURITY AFFAIRS NAVAL POSTGRADUATE SCHOOL Slide 1 Opening Credits
AN ENABLING FOUNDATION FOR NASA S EARTH AND SPACE SCIENCE MISSIONS
 AN ENABLING FOUNDATION FOR NASA S EARTH AND SPACE SCIENCE MISSIONS Committee on the Role and Scope of Mission-enabling Activities in NASA s Space and Earth Science Missions Space Studies Board National
AN ENABLING FOUNDATION FOR NASA S EARTH AND SPACE SCIENCE MISSIONS Committee on the Role and Scope of Mission-enabling Activities in NASA s Space and Earth Science Missions Space Studies Board National
Neuro-Fuzzy and Soft Computing: Fuzzy Sets. Chapter 1 of Neuro-Fuzzy and Soft Computing by Jang, Sun and Mizutani
 Chapter 1 of Neuro-Fuzzy and Soft Computing by Jang, Sun and Mizutani Outline Introduction Soft Computing (SC) vs. Conventional Artificial Intelligence (AI) Neuro-Fuzzy (NF) and SC Characteristics 2 Introduction
Chapter 1 of Neuro-Fuzzy and Soft Computing by Jang, Sun and Mizutani Outline Introduction Soft Computing (SC) vs. Conventional Artificial Intelligence (AI) Neuro-Fuzzy (NF) and SC Characteristics 2 Introduction
Autonomous weapons systems as WMD vectors a new threat and a potential for terrorism?
 ISADARCO Winter Course 2016, Andalo, Italy, 8-15 January 2016 Advanced and cyber weapons systems: Technology and Arms control Autonomous weapons systems as WMD vectors a new threat and a potential for
ISADARCO Winter Course 2016, Andalo, Italy, 8-15 January 2016 Advanced and cyber weapons systems: Technology and Arms control Autonomous weapons systems as WMD vectors a new threat and a potential for
Port infrastructures, infrastmcture system, innovation, system attributes, uncertainty
 The Netherlands Research School for Transport, Infrastructure and Logistics TRAIL 11'"TRAIL Congress November 2010 INNOVATION IN PORT INFRASTRUCTURE DESIGN p. Taneja (CITG, TU Delft), W. Zwakhals (Port
The Netherlands Research School for Transport, Infrastructure and Logistics TRAIL 11'"TRAIL Congress November 2010 INNOVATION IN PORT INFRASTRUCTURE DESIGN p. Taneja (CITG, TU Delft), W. Zwakhals (Port
RAHS: A Systematic Process of Foresight
 RAHS: A Systematic Process of Foresight Chew Lock Pin Director Risk Assessment and Horizon Scanning (RAHS) Programme Office National Security Coordination Secretariat Prime Minister s Office Singapore
RAHS: A Systematic Process of Foresight Chew Lock Pin Director Risk Assessment and Horizon Scanning (RAHS) Programme Office National Security Coordination Secretariat Prime Minister s Office Singapore
Game Playing Beyond Minimax. Game Playing Summary So Far. Game Playing Improving Efficiency. Game Playing Minimax using DFS.
 Game Playing Summary So Far Game tree describes the possible sequences of play is a graph if we merge together identical states Minimax: utility values assigned to the leaves Values backed up the tree
Game Playing Summary So Far Game tree describes the possible sequences of play is a graph if we merge together identical states Minimax: utility values assigned to the leaves Values backed up the tree
Interagency Working Group on Import Safety. Executive Order July 18, 2007
 Executive Order 13439 July 18, 2007 Establish an Interagency Working Group on Import Safety We need to continually improve our import safeguards to meet the changing demands of a global economy. We must
Executive Order 13439 July 18, 2007 Establish an Interagency Working Group on Import Safety We need to continually improve our import safeguards to meet the changing demands of a global economy. We must
Introduction Economic Models Game Theory Models Games Summary. Syllabus
 Syllabus Contact: kalk00@vse.cz home.cerge-ei.cz/kalovcova/teaching.html Office hours: Wed 7.30pm 8.00pm, NB339 or by email appointment Osborne, M. J. An Introduction to Game Theory Gibbons, R. A Primer
Syllabus Contact: kalk00@vse.cz home.cerge-ei.cz/kalovcova/teaching.html Office hours: Wed 7.30pm 8.00pm, NB339 or by email appointment Osborne, M. J. An Introduction to Game Theory Gibbons, R. A Primer
ECON 301: Game Theory 1. Intermediate Microeconomics II, ECON 301. Game Theory: An Introduction & Some Applications
 ECON 301: Game Theory 1 Intermediate Microeconomics II, ECON 301 Game Theory: An Introduction & Some Applications You have been introduced briefly regarding how firms within an Oligopoly interacts strategically
ECON 301: Game Theory 1 Intermediate Microeconomics II, ECON 301 Game Theory: An Introduction & Some Applications You have been introduced briefly regarding how firms within an Oligopoly interacts strategically
Game Theory. 4: Nash equilibrium in different games and mixed strategies
 Game Theory 4: Nash equilibrium in different games and mixed strategies Review of lecture three A game with no dominated strategy: The battle of the sexes The concept of Nash equilibrium The formal definition
Game Theory 4: Nash equilibrium in different games and mixed strategies Review of lecture three A game with no dominated strategy: The battle of the sexes The concept of Nash equilibrium The formal definition
Blast effects and protective structures: an interdisciplinary course for military engineers
 Safety and Security Engineering III 293 Blast effects and protective structures: an interdisciplinary course for military engineers M. Z. Zineddin Department of Civil and Environmental Engineering, HQ
Safety and Security Engineering III 293 Blast effects and protective structures: an interdisciplinary course for military engineers M. Z. Zineddin Department of Civil and Environmental Engineering, HQ
ECO 199 B GAMES OF STRATEGY Spring Term 2004 B February 24 SEQUENTIAL AND SIMULTANEOUS GAMES. Representation Tree Matrix Equilibrium concept
 CLASSIFICATION ECO 199 B GAMES OF STRATEGY Spring Term 2004 B February 24 SEQUENTIAL AND SIMULTANEOUS GAMES Sequential Games Simultaneous Representation Tree Matrix Equilibrium concept Rollback (subgame
CLASSIFICATION ECO 199 B GAMES OF STRATEGY Spring Term 2004 B February 24 SEQUENTIAL AND SIMULTANEOUS GAMES Sequential Games Simultaneous Representation Tree Matrix Equilibrium concept Rollback (subgame
First Prev Next Last Go Back Full Screen Close Quit. Game Theory. Giorgio Fagiolo
 Game Theory Giorgio Fagiolo giorgio.fagiolo@univr.it https://mail.sssup.it/ fagiolo/welcome.html Academic Year 2005-2006 University of Verona Web Resources My homepage: https://mail.sssup.it/~fagiolo/welcome.html
Game Theory Giorgio Fagiolo giorgio.fagiolo@univr.it https://mail.sssup.it/ fagiolo/welcome.html Academic Year 2005-2006 University of Verona Web Resources My homepage: https://mail.sssup.it/~fagiolo/welcome.html
Integrated Safety Envelopes
 Integrated Safety Envelopes Built-in Restrictions of Navigable Airspace Edward A. Lee Professor, EECS, UC Berkeley NSF / OSTP Workshop on Information Technology Research for Critical Infrastructure Protection
Integrated Safety Envelopes Built-in Restrictions of Navigable Airspace Edward A. Lee Professor, EECS, UC Berkeley NSF / OSTP Workshop on Information Technology Research for Critical Infrastructure Protection
Basics of Game Theory
 Basics of Game Theory Giacomo Bacci and Luca Sanguinetti Department of Information Engineering isa University {giacomo.bacci,luca.sanguinetti}@iet.unipi.it April - May, 2010 G. Bacci and L. Sanguinetti
Basics of Game Theory Giacomo Bacci and Luca Sanguinetti Department of Information Engineering isa University {giacomo.bacci,luca.sanguinetti}@iet.unipi.it April - May, 2010 G. Bacci and L. Sanguinetti
Dynamic Programming. Objective
 Dynamic Programming Richard de Neufville Professor of Engineering Systems and of Civil and Environmental Engineering MIT Massachusetts Institute of Technology Dynamic Programming Slide 1 of 43 Objective
Dynamic Programming Richard de Neufville Professor of Engineering Systems and of Civil and Environmental Engineering MIT Massachusetts Institute of Technology Dynamic Programming Slide 1 of 43 Objective
Ignatius A. Grande, Esq. Hughes Hubbard & Reed LLP One Battery Park Plaza New York, NY (212)
 Ignatius A. Grande, Esq. Hughes Hubbard & Reed LLP One Battery Park Plaza New York, NY 10004 (212) 837-6120 grande@hugheshubbard.com Ignatius Grande is Senior Discovery Attorney at Hughes Hubbard & Reed
Ignatius A. Grande, Esq. Hughes Hubbard & Reed LLP One Battery Park Plaza New York, NY 10004 (212) 837-6120 grande@hugheshubbard.com Ignatius Grande is Senior Discovery Attorney at Hughes Hubbard & Reed
for Analy zing Terrorism
 Game Th e or y as a To ol for Analy zing Terrorism Vito FRAGNELLI Università del Piemonte Orientale Dipartimento di Scienze e Tecnologie Avanzate Via V.Bellini 25/G 15100 Alessandria, Italy vito.frag n
Game Th e or y as a To ol for Analy zing Terrorism Vito FRAGNELLI Università del Piemonte Orientale Dipartimento di Scienze e Tecnologie Avanzate Via V.Bellini 25/G 15100 Alessandria, Italy vito.frag n
Chapter: Science, Technology, and Society
 Table of Contents Chapter: Science, Technology, and Society Section 1: Science and Technology Section 2: Forces that Shape Technology Section 3: Developing Technology 1 Science and Technology Scientific
Table of Contents Chapter: Science, Technology, and Society Section 1: Science and Technology Section 2: Forces that Shape Technology Section 3: Developing Technology 1 Science and Technology Scientific
Secure Societies. Pauli Stigell, Pekka Rantala
 Secure Societies Pauli Stigell, Pekka Rantala Security Union Security research is on the rise in conventional and cyber fields. Finns have a relatively good record in this programme and the programme s
Secure Societies Pauli Stigell, Pekka Rantala Security Union Security research is on the rise in conventional and cyber fields. Finns have a relatively good record in this programme and the programme s
MODELING COMPLEX SOCIO-TECHNICAL ENTERPRISES. William B. Rouse November 13, 2013
 MODELING COMPLEX SOCIO-TECHNICAL ENTERPRISES William B. Rouse November 13, 2013 Overview Complex Socio-Technical Systems Overall Methodology Thinking in Terms of Phenomena Abstraction, Aggregation & Representation
MODELING COMPLEX SOCIO-TECHNICAL ENTERPRISES William B. Rouse November 13, 2013 Overview Complex Socio-Technical Systems Overall Methodology Thinking in Terms of Phenomena Abstraction, Aggregation & Representation
Computational Implementation of location problem models for medical services
 2012 SPRING ISEN 601 PROJECT Computational Implementation of location problem models for medical services Facility location problem for large-scale emergencies Yeong In Kim, SooIn Choi 5/1/2012 1. Intro
2012 SPRING ISEN 601 PROJECT Computational Implementation of location problem models for medical services Facility location problem for large-scale emergencies Yeong In Kim, SooIn Choi 5/1/2012 1. Intro
Scenario Development Process
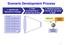 Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Uncertainty Feature Optimization for the Airline Scheduling Problem
 1 Uncertainty Feature Optimization for the Airline Scheduling Problem Niklaus Eggenberg Dr. Matteo Salani Funded by Swiss National Science Foundation (SNSF) 2 Outline Uncertainty Feature Optimization (UFO)
1 Uncertainty Feature Optimization for the Airline Scheduling Problem Niklaus Eggenberg Dr. Matteo Salani Funded by Swiss National Science Foundation (SNSF) 2 Outline Uncertainty Feature Optimization (UFO)
Virtual Model Validation for Economics
 Virtual Model Validation for Economics David K. Levine, www.dklevine.com, September 12, 2010 White Paper prepared for the National Science Foundation, Released under a Creative Commons Attribution Non-Commercial
Virtual Model Validation for Economics David K. Levine, www.dklevine.com, September 12, 2010 White Paper prepared for the National Science Foundation, Released under a Creative Commons Attribution Non-Commercial
7th Grade US History Standard # Do Now Day #15 DO NOW
 Name Course: US History/Ms. Brown Homeroom: 7th Grade US History Standard # Do Now Day #15 Aims: SWBAT define social science SWBAT identify a perspective of a social scientist DO NOW Directions: Answer
Name Course: US History/Ms. Brown Homeroom: 7th Grade US History Standard # Do Now Day #15 Aims: SWBAT define social science SWBAT identify a perspective of a social scientist DO NOW Directions: Answer
Fictitious Play applied on a simplified poker game
 Fictitious Play applied on a simplified poker game Ioannis Papadopoulos June 26, 2015 Abstract This paper investigates the application of fictitious play on a simplified 2-player poker game with the goal
Fictitious Play applied on a simplified poker game Ioannis Papadopoulos June 26, 2015 Abstract This paper investigates the application of fictitious play on a simplified 2-player poker game with the goal
LECTURE 26: GAME THEORY 1
 15-382 COLLECTIVE INTELLIGENCE S18 LECTURE 26: GAME THEORY 1 INSTRUCTOR: GIANNI A. DI CARO ICE-CREAM WARS http://youtu.be/jilgxenbk_8 2 GAME THEORY Game theory is the formal study of conflict and cooperation
15-382 COLLECTIVE INTELLIGENCE S18 LECTURE 26: GAME THEORY 1 INSTRUCTOR: GIANNI A. DI CARO ICE-CREAM WARS http://youtu.be/jilgxenbk_8 2 GAME THEORY Game theory is the formal study of conflict and cooperation
Ch 26-2 Atomic Anxiety
 Ch 26-2 Atomic Anxiety The Main Idea The growing power of, and military reliance on, nuclear weapons helped create significant anxiety in the American public in the 1950s. Content Statements 23. Use of
Ch 26-2 Atomic Anxiety The Main Idea The growing power of, and military reliance on, nuclear weapons helped create significant anxiety in the American public in the 1950s. Content Statements 23. Use of
Identifying Materials using Radio Frequency
 Identifying Materials using Radio Frequency Group Members: Cuong Trinh/ trinhcuonglouis@yahoo.com Chi Huynh/ chihuynh2005@yahoo.com Khanh Truong/ khtruong89@yahoo.com Advisor: Ray Kwok Date: December 07,
Identifying Materials using Radio Frequency Group Members: Cuong Trinh/ trinhcuonglouis@yahoo.com Chi Huynh/ chihuynh2005@yahoo.com Khanh Truong/ khtruong89@yahoo.com Advisor: Ray Kwok Date: December 07,
final examination on May 31 Topics from the latter part of the course (covered in homework assignments 4-7) include:
 The final examination on May 31 may test topics from any part of the course, but the emphasis will be on topic after the first three homework assignments, which were covered in the midterm. Topics from
The final examination on May 31 may test topics from any part of the course, but the emphasis will be on topic after the first three homework assignments, which were covered in the midterm. Topics from
Artificial Intelligence and Asymmetric Information Theory. Tshilidzi Marwala and Evan Hurwitz. University of Johannesburg.
 Artificial Intelligence and Asymmetric Information Theory Tshilidzi Marwala and Evan Hurwitz University of Johannesburg Abstract When human agents come together to make decisions it is often the case that
Artificial Intelligence and Asymmetric Information Theory Tshilidzi Marwala and Evan Hurwitz University of Johannesburg Abstract When human agents come together to make decisions it is often the case that
Smart specialisation. Dominique Foray An Industrial Renaissance in Europe Federation of Austrian Industries Vienna, June 6th 2014
 Smart specialisation Dominique Foray An Industrial Renaissance in Europe Federation of Austrian Industries Vienna, June 6th 2014 Why not doing industrial policy? Government failures, risks, inefficiencies
Smart specialisation Dominique Foray An Industrial Renaissance in Europe Federation of Austrian Industries Vienna, June 6th 2014 Why not doing industrial policy? Government failures, risks, inefficiencies
CPS 570: Artificial Intelligence Game Theory
 CPS 570: Artificial Intelligence Game Theory Instructor: Vincent Conitzer What is game theory? Game theory studies settings where multiple parties (agents) each have different preferences (utility functions),
CPS 570: Artificial Intelligence Game Theory Instructor: Vincent Conitzer What is game theory? Game theory studies settings where multiple parties (agents) each have different preferences (utility functions),
Advisor: Professor Frank Y.S. Lin Present by Tim Q.T. Chen
 Advisor: Professor Frank Y.S. Lin Present by Tim Q.T. Chen 1 Introduction Game Theory Attack Graph A Game Theoretic Method for Decision and Analysis of the Optimal Active Defense Strategy Optimal Network
Advisor: Professor Frank Y.S. Lin Present by Tim Q.T. Chen 1 Introduction Game Theory Attack Graph A Game Theoretic Method for Decision and Analysis of the Optimal Active Defense Strategy Optimal Network
GAME THEORY: ANALYSIS OF STRATEGIC THINKING Exercises on Multistage Games with Chance Moves, Randomized Strategies and Asymmetric Information
 GAME THEORY: ANALYSIS OF STRATEGIC THINKING Exercises on Multistage Games with Chance Moves, Randomized Strategies and Asymmetric Information Pierpaolo Battigalli Bocconi University A.Y. 2006-2007 Abstract
GAME THEORY: ANALYSIS OF STRATEGIC THINKING Exercises on Multistage Games with Chance Moves, Randomized Strategies and Asymmetric Information Pierpaolo Battigalli Bocconi University A.Y. 2006-2007 Abstract
An Introduction to Agent-based
 An Introduction to Agent-based Modeling and Simulation i Dr. Emiliano Casalicchio casalicchio@ing.uniroma2.it Download @ www.emilianocasalicchio.eu (talks & seminars section) Outline Part1: An introduction
An Introduction to Agent-based Modeling and Simulation i Dr. Emiliano Casalicchio casalicchio@ing.uniroma2.it Download @ www.emilianocasalicchio.eu (talks & seminars section) Outline Part1: An introduction
An Introduction to Computable General Equilibrium Modeling
 An Introduction to Computable General Equilibrium Modeling Selim Raihan Professor Department of Economics, University of Dhaka And, Executive Director, SANEM Presented at the ARTNeT-GIZ Capacity Building
An Introduction to Computable General Equilibrium Modeling Selim Raihan Professor Department of Economics, University of Dhaka And, Executive Director, SANEM Presented at the ARTNeT-GIZ Capacity Building
 an author's https://oatao.univ-toulouse.fr/20074 https://doi.org/10.1109/syscon.2018.8369615 Smirnova, Ksenia and Golkar, Alessandro and Vingerhoeds, Rob A. A game-theoretic framework for concurrent technology
an author's https://oatao.univ-toulouse.fr/20074 https://doi.org/10.1109/syscon.2018.8369615 Smirnova, Ksenia and Golkar, Alessandro and Vingerhoeds, Rob A. A game-theoretic framework for concurrent technology
