The New Economy: Transatlantic Policy Comparison Data Privacy By Abe Newman
|
|
|
- Veronica Davidson
- 6 years ago
- Views:
Transcription
1 The New Economy: Transatlantic Policy Comparison Data Privacy By Abe Newman A central concern of privacy is the ability of an individual to control the access to and use of personal information. New technologies, which radically enhance data production and processing, challenge privacy expectations. Societies around the world wrestle with the question over where the new lines of privacy should be drawn. On the one hand, numerous private and public sectors of the economy employ personal data as vital economic capital. Direct marketing, insurance, telecommunications, health care and welfare administration rely on data management to enhance efficiency and reduce costs. On the other hand, individuals and privacy advocates resist and protest the eclipse of privacy for the sake of economic efficiency. As uses of personal information clash with concerns over information autonomy, regulation mediates the debate. Much like welfare systems, which emerged in the wake of the industrial revolution, the regulation of personal data use will have far reaching implications for the development of industrial economies in the 21 st century. In the late 1960s and early 1970s, concerns arose over government proposals to centralize public data collection. Meant to assist social policy management and expansion, national government databases led to successful coalitions across industrialized countries for data protection regulation. This first wave of data protection policy concentrated on the formulation of basic principles that were intended to guide future data protection efforts. These principles have come to be known as the Fair Information Practice Principals (FIPP) and rest on the following concepts: Notice data users should openly notify data subjects of privacy policies; Consent data should not be disclosed or used for purposes without data subject consent; Security stored data must be secure from theft or corruption; Access - data subjects should have access to stored data in order to verify validity; Accountability a procedure must exist to enforce and punish breaches of the principles. At the fore of the movement to enshrine basic privacy principles, the German State of Hessen passed the first comprehensive data privacy law in 1970, followed by the Swedish Privacy Act in 1973 and the German federal regulation in Europe has continued this leadership in privacy protection through the passage of the EU Data Privacy Directive in The U.S., in contrast, has rejected comprehensive government regulation, opting for limited sectoral policies and industry led initiatives. How do these systems differ across and within regions? How well suited are they to meet the challenges posed by new data collection technologies? What will the differences mean for the use of information in both the public and private sector? Do regulations vary in their relative efficacy concerning data privacy protection? How do existing protection systems forge new political interest and coalitions around future privacy concerns? 1
2 Propositions for Discussion Proposition 1. Digital Challenges Ignite Privacy Debate: With the codification of the FIPP in international agreements like OECD guidelines on information use and the European Union Privacy Directive, the basic principles of data protection are internationally recognized. This general consensus, however, does not guide specific responses to new data collection technologies. The development of technologies like chip-cards, genetic testing, e-medical records, and location monitoring redefine personal information collection possibilities. The power of these technologies to monitor individual behavior raises new calls for regulation. The next round of battles is not about whether data protection should occur or over the basic policy principles of data privacy. Battles will instead concern the implementation of FIPP to specific applications of digital technologies. Disputes over the appropriate use of certain data collection technologies pits economic interests against individual information autonomy. The opt-in consent requirements for healthcare as opposed to opt-out for finance in the U.S. exemplifies this trend. Differences in industry and government interests like those of doctor associations, financial service providers, insurance companies, direct marketers, and advertising agencies will produce variation in acceptable personal data use across national economies. New coalitions emerge that pit those benefiting from information monitoring against those that loose decision-making freedom. Proposition 2. Regulatory Variation Persists: Enforcement of the FIPP and specific responses to new technologies differ across countries. Although the EU Directive succeeded in preventing escalating trade tensions among member states, the character of the directive allows for considerable variation in national implementation. Instead of unifying on one common mechanism of enforcement, multiple distinct institutional designs continue to exist within the EU. The centralized French monitoring organization concentrates on databank licensing while the decentralized network of German regulators work to advise legislators and private sector actors. The French system s focus on licensing becomes increasingly taxing as the number of organizations with databases rises. This focus drains resources, hampering the organizations ability to respond to consumer complaints and enforce audits. The federal structure of the German system spreads out regulators. The layers of privacy authorities provide advice and support for private sector actors wishing to comply with data protection legislation or create selfregulatory solutions. Outside of Europe a variety of responses exist. In Japan, MITI coordinates seal programs. The United States relies on publicity and pressure from NGOs and enforcement by the FTC to protect privacy interests. Are some data protection institutions better equipped to confront digital challenges? Do different data protection systems provide certain states an institutional comparative advantage in data privacy protection? Proposition 2. Effective Data Protection is a Thing of the Future: Data protection relies on three basic implementation mechanisms: government, business, and technology. The first wave of privacy policies focused on the potential government abuse of 2
3 databanks and relied on government regulation as the central means of control. As the primary threat to data privacy shifts from the government to businesses what mix of the three strategies might produce adequate protection at a minimal cost? Technological responses will no doubt play an integral role in the new architecture of control. Microprocessors are embedded in more and more products and linked to expanding numbers of communications networks, increasing data collection points and linkages between data users. As physical choke points for regulation disappear, governments and businesses will rely on technological controls to reduce unwanted privacy abuses. This does not mean, however that technology alone resolves privacy dilemmas. Legislation will be used to enforce computer code just as computer code will be used to reinforce legislation. Political interests and institutions will influence national decisions regarding technological controls. The role of governments and business will differ crossnationally. European governments encourage standardization around common technological solutions like the Platform for Privacy Preferences (P3P) while different groups like TRUSTe, Zero-Knowledge and Zoom compete in a North American market for technological responses. How does variation in data protection regulation affect the adoption rate and character of privacy enhancing technologies (PETs)? Does the centralized European system hamper flexible solutions? or does the U.S. system lack the capacity to monitor industry brokered deals? Background for Discussion In the mid1960s, government agencies were some of the few organizations capable of purchasing supercomputers powerful enough to sort and analyze large quantities of data. As states expanded social programs and services, governments looked to use the technical capacity of centralized data processing to augment bureaucratic control. These efficiency gains, though, aroused equally powerful surveillance paranoia. Coalitions formed to support legislation intended to check government abuse of new data processing technologies. This first wave of regulation focused on the creation of general principles and implementation mechanisms. These laws date back to the Swedish Data Privacy Act of 1973 or the U.S. Privacy Act of 1974 and were internationally codified by the OECD in the 1981 Guidelines Governing the Protection of Privacy and Transborder Flows of Personal Data. These principles have become known as the Fair Information Practice 3
4 Principles (FIPP). 1 The European Union Data Privacy Directive adopted in 1995 completes this wave of comprehensive regulation. The Directive requires member states to adopt comprehensive data protection legislation following the Fair Information Practice Principles (FIPP) and establish an independent national data protection commission. Information technology innovations raise additional privacy concerns and potentially strain the capabilities of these first regulatory efforts. Aside from debates concerning the response to the September 2001 terrorist attacks, the primary agent of privacy intrusion has shifted from government actors to the private sector. Initial privacy laws passed during the 1970s focused their attention on public sector threats. The Orwellian vision of Big Brother depicted in 1984 was long heralded as the ultimate justification for privacy protection. But information technology empowers private actors as much as public officials. Distributed networks and personal computers provide average businesses with data processing capacities previously reserved to the largest corporations and public agencies. Additionally, deregulation and fiscal constraints increasingly force public bureaucracies to rely on private sector information sources. The threat of personal information abuse transforms from a government based surveillance society into something better described by an AOLianworld where consumer monitoring expands at rapid speeds. Additionally, new data collection technologies augment monitoring capacities. First, the quantity of information that one can accumulate and analyze is increasing 1 The principles include: Notice data users should openly notify data subjects of privacy policies; Consent data should not be disclosed or used for purposes without data subject consent; Security stored data must be secure from theft or corruption; Access - data subjects should have access to stored data in order to verify validity; Accountability a procedure must exist to enforce and punish breaches of the principles. 4
5 exponentially. Web trails, credit card records, and club cards generate growing amounts of personal data. With the rise of data banks and data processing programs, staggering amounts of information can be stored and dissected into refined profiles of individual behavior. Second, the rise in information gathering changes the quality of collected information. As the capacity of data monitoring improves, new areas of human behavior fall under public scrutiny. This rise in the quantity and the quality of personal information collection and use alters the character of privacy expectations. The U.S. as well as many European nations base privacy protection on the assumption of a reasonable expectation of privacy. It is not the data itself that is protected but the use of the data in a particular context. For example, an individual might want a doctor to know that they have a disease but not want an employer to have the same information. Privacy rights protect a particular use of information and not the information itself. As information technology challenges preexisting public and private boundries, conflicts emerge over appropriate levels of privacy for specific digital technologies. Digital Challenges Ignite Privacy Debate: Public concern over private sector collection, storage, and analysis of commercially produced information grew over the last two decades, threatening the future commercialization and spread of information driven innovations like e-commerce. The most recent wave of privacy legislation is addressing difficult questions centering on the acceptability of certain new monitoring and data collection technologies, for example the appropriate use of video technologies, location monitoring, e-medical records, and chip-cards. 5
6 These technologies have the capacity to redefine the current borders of the private sphere. If location monitoring became an accepted practice, marketing firms could track daily movements and then target individuals with certain products at specific locations. Similarly, the broad exceptance of video surveillance in the workplace and other public settings radically alters how individuals conceive of autonomous space. As the push for specific sector or technology regulation emerges, political battles intensify and new coalitions for and against privacy emerge. As more and more industries use personal information to provide their services, information becomes valuable capital. Therefore, attempts to regulate specific personal data use or collection engenders the type of interest group conflict previously associated with traditional industrial lobbies. Coalitions emerge that pit those benefiting from information monitoring against those that loose decision-making freedom. The 1997 EU Telecommunication Directive, 1999 Gramm-Leach-Bliley financial privacy rules, and the 2001 Medical Privacy Rules all typify the next round of data protection legislation. They are characteristic of the transition from broad legislation and sweeping principles to specific implementation procedures. Broad political consensus around the FIPP fades as concrete interests are threatened. The difference between opt-in and out requirements in the Medical Privacy Rules versus the financial privacy regulation serve as a case in point. Medical rules were developed and debated by the department of Health and Human Services after Congress delegated rule making authority in 1996 while the financial services rules were a byproduct of Congressional financial modernization legislation. Different policy-making processes permit different interest groups varying amounts of access in this new round of data privacy regulation. 6
7 Regional variation in interest group alignments influences the texture of the debates on either side of the Atlantic. The lack of data privacy protection for the Internet in the U.S. stems in part from the inherent tension between data protection and freedom of information. Interestingly, a set of electronic privacy advocates emerged in the early 1990s including groups like the Electronic Privacy Information Center (EPIC) and the Electronic Frontier Foundation (E.F.F.). These digital freedom advocates receive minimal support from traditional civil liberty organizations like the ACLU. The ACLU sees data protection as a threat to free speech and therefore limits its involvement in data privacy issues. Although this tension plays a lesser role in Europe owing to less encompassing free speech rights, a different conflict exists. Consumer protection groups press for detailed accounts of consumer transactions and data protection officials call for data frugality. These and other differential interest group configurations will overlay emerging regulatory conversations concerning gene-testing, e-medical records, location monitoring, and direct marketing. Regulatory Variation Persists: Despite convergence around the FIPP and the EU Privacy Directive, national regulatory variation continues to persist both within Europe and across major industrialized economies. Legacies from earlier data privacy efforts influence government responses. Looking at the three largest economic regions in the world, a diversity of regulatory patterns emerges. Europe has comprehensive legal regulation of data privacy but there is diversity in the enforcement mechanisms adopted by different member states. The European Union Privacy directive required national enabling legislation which permits this variation. 7
8 European countries with existing data protection agencies relied on their specific strengths when adapting the directive to national settings. For example, the French monitoring agency, the CNIL, is a centralized agency that focuses its efforts on database licensing. Lacking the resources to audit large segments of the public sector, the agency is more involved in data use by large corporations or public sector initiatives. The German authority, in contrast, functions in a decentralized manner with layers of data protection agencies at the various tiers of government. Local data protection officials coordinate with regional businesses to develop data privacy policies. As a result, German agencies are better positioned to facilitate private sector solutions although they have fewer formal powers than the CNIL. Lacking a centralized data protection authority from the first wave, a patchwork of regulators and NGOs respond to data privacy concerns in the U.S. Data privacy protection is organized around sectoral lines. Certain industries like health care and video rentals have clearly defined laws while other industries like data marketing face no specific regulation. At the center of the U.S. systems sits the FTC which reviews breaches of FIPPs. The U.S. regulatory system responds when companies break promises concerning data protection. NGOs monitor and draw attention to private sector missteps. This system of enforcement encourages companies to adopt preventative measures to reduce bad publicity. Firms also have an incentive to avoid sweeping privacy commitments that might open them up to suits based on unfair trade practices. Japanese initiatives, unlike those in the U.S. and Europe, are not influenced by previous waves of data protection. Emerging as a response to the European Union Privacy Directive, Japanese data protection is coordinated by MITI and a number of 8
9 industry associations. Viewed primarily as a trade issue, as opposed to a domestic policy concern, MITI has taken the lead role in developing data protection standards. Mirroring U.S. responses, government policies encourage business efforts like seal programs and self-regulation. A recent agreement between TRUSTe and the Japanese Engineers Trade Association, gives TRUSTe jurisdiction to offer its seal program and dispute settlement mechanism to Japanese web sites. Effective Data Protection is a Thing of the Future: The decentralization of information exchanges through networked technologies challenges the appropriateness of purely government mandated standards. Many command and control regulatory strategies seem almost farcical as data collection technology is embedded into more and more machines and then connected to an ever-increasing number of networked systems. As more and more entities have the capacity and resources to develop sophisticated data collection and processing systems, regulatory agencies find their resources strained. This problem is typified by the French, Swedish, and British agencies, all of which continue to view database registration as a primary data protection tool. They devote so much effort to registration that lose their ability to audit or follow up on consumer complaints. The current regulatory difficulties do not imply, however, that digital networks will remain the free flowing, decentralized Internet of the mid 1990s. Public and private sector organizations have an incentive to impose some structure on data networks: Firms seek to increase knowledge extraction and governments hope to reclaim authority. In addition to government regulation, industry self-regulation and technology offer potential regulatory solutions. 9
10 Technology will no doubt play an integral role in the emerging system of regulation. Government mandates will be supplemented by and may encourage technological interventions that limit or channel data transmissions. Like one-way streets directing the flow of traffic, digital architectures may be imposed through computer code that serve to promote data protection legislation. The reverse will undoubtedly also occur. Legislation will enforce computer code as happened with the Digital Millenium Copyright Act. Government data protection regimes influence the character of emerging technological solutions. For example, central data authorities in Europe coordinated their initial efforts at promoting privacy enhancing technology (PETs) for the Internet around the Platform for Privacy Preferences (P3P). Using European Union research monies and the bully pulpit of data protection authorities, the European Union has attempted to coordinate a standardized response to data protection concerns on the Web. The U.S., in contrast, lacks a centralized data protection authority to mediate such efforts. Instead, the threat of Federal Trade Commission investigation or negative press rallied by NGOs encourages companies to adopt a variety of PETs. A diverse group of firms like TRUSTe, Zero-Knowledge, Webwasher and Zoom compete in the North American market for technological responses to concerns over Internet privacy. Conclusion: The combination of new privacy coalitions, government institutions, and technological controls shape the borders of privacy in a digital age. Variation in the three elements across countries will produce different political bargains over appropriate protection. The character of these solutions will affect individual autonomy as well as 10
11 economic opportunity. As industrial counties rely increasingly on information as economic capital, the regulation of personal information takes on new importance. Politically ineffective data privacy policies threaten to spur a privacy revolt, hampering the diffusion of information technologies like e-medical records or responsible data marketing. Affective protection may allay individual concerns while limiting the use of personal information in a range of economic activities. Much like welfare systems, which emerged in the wake of the industrial revolution, the regulation of personal data use will have far reaching implications for the development of industrial economies in the 21 st century. 11
BASED ECONOMIES. Nicholas S. Vonortas
 KNOWLEDGE- BASED ECONOMIES Nicholas S. Vonortas Center for International Science and Technology Policy & Department of Economics The George Washington University CLAI June 9, 2008 Setting the Stage The
KNOWLEDGE- BASED ECONOMIES Nicholas S. Vonortas Center for International Science and Technology Policy & Department of Economics The George Washington University CLAI June 9, 2008 Setting the Stage The
Internet 2020: The Next Billion Users
 Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Ethical and social aspects of management information systems
 Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
Pan-Canadian Trust Framework Overview
 Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
The Fourth Industrial Revolution in Major Countries and Its Implications of Korea: U.S., Germany and Japan Cases
 Vol. 8 No. 20 ISSN -2233-9140 The Fourth Industrial Revolution in Major Countries and Its Implications of Korea: U.S., Germany and Japan Cases KIM Gyu-Pan Director General of Advanced Economies Department
Vol. 8 No. 20 ISSN -2233-9140 The Fourth Industrial Revolution in Major Countries and Its Implications of Korea: U.S., Germany and Japan Cases KIM Gyu-Pan Director General of Advanced Economies Department
EXPLORATION DEVELOPMENT OPERATION CLOSURE
 i ABOUT THE INFOGRAPHIC THE MINERAL DEVELOPMENT CYCLE This is an interactive infographic that highlights key findings regarding risks and opportunities for building public confidence through the mineral
i ABOUT THE INFOGRAPHIC THE MINERAL DEVELOPMENT CYCLE This is an interactive infographic that highlights key findings regarding risks and opportunities for building public confidence through the mineral
Dynamics of National Systems of Innovation in Developing Countries and Transition Economies. Jean-Luc Bernard UNIDO Representative in Iran
 Dynamics of National Systems of Innovation in Developing Countries and Transition Economies Jean-Luc Bernard UNIDO Representative in Iran NSI Definition Innovation can be defined as. the network of institutions
Dynamics of National Systems of Innovation in Developing Countries and Transition Economies Jean-Luc Bernard UNIDO Representative in Iran NSI Definition Innovation can be defined as. the network of institutions
Personal Data Protection Competency Framework for School Students. Intended to help Educators
 Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy?
 Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Enforcement of Intellectual Property Rights Frequently Asked Questions
 EUROPEAN COMMISSION MEMO Brussels/Strasbourg, 1 July 2014 Enforcement of Intellectual Property Rights Frequently Asked Questions See also IP/14/760 I. EU Action Plan on enforcement of Intellectual Property
EUROPEAN COMMISSION MEMO Brussels/Strasbourg, 1 July 2014 Enforcement of Intellectual Property Rights Frequently Asked Questions See also IP/14/760 I. EU Action Plan on enforcement of Intellectual Property
ITI Comment Submission to USTR Negotiating Objectives for a U.S.-Japan Trade Agreement
 ITI Comment Submission to USTR-2018-0034 Negotiating Objectives for a U.S.-Japan Trade Agreement DECEMBER 3, 2018 Introduction The Information Technology Industry Council (ITI) welcomes the opportunity
ITI Comment Submission to USTR-2018-0034 Negotiating Objectives for a U.S.-Japan Trade Agreement DECEMBER 3, 2018 Introduction The Information Technology Industry Council (ITI) welcomes the opportunity
Chapter 4. L&L 12ed Global Ed ETHICAL AND SOCIAL ISSUES IN INFORMATION SYSTEMS. Information systems and ethics
 MANAGING THE DIGITAL FIRM, 12 TH EDITION, GLOBAL EDITION Chapter 4 ETHICAL AND SOCIAL ISSUES IN Learning Objectives What ethical, social, and political issues are raised by information systems? What specific
MANAGING THE DIGITAL FIRM, 12 TH EDITION, GLOBAL EDITION Chapter 4 ETHICAL AND SOCIAL ISSUES IN Learning Objectives What ethical, social, and political issues are raised by information systems? What specific
Management Information Systems MANAGING THE DIGITAL FIRM, 12 TH EDITION. Chapter 4 ETHICAL AND SOCIAL ISSUES IN INFORMATION SYSTEMS
 MANAGING THE DIGITAL FIRM, 12 TH EDITION Chapter 4 ETHICAL AND SOCIAL ISSUES IN Learning Objectives What ethical, social, and political issues are raised by information systems? What specific principles
MANAGING THE DIGITAL FIRM, 12 TH EDITION Chapter 4 ETHICAL AND SOCIAL ISSUES IN Learning Objectives What ethical, social, and political issues are raised by information systems? What specific principles
March 27, The Information Technology Industry Council (ITI) appreciates this opportunity
 Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Our position. ICDPPC declaration on ethics and data protection in artificial intelligence
 ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
The 45 Adopted Recommendations under the WIPO Development Agenda
 The 45 Adopted Recommendations under the WIPO Development Agenda * Recommendations with an asterisk were identified by the 2007 General Assembly for immediate implementation Cluster A: Technical Assistance
The 45 Adopted Recommendations under the WIPO Development Agenda * Recommendations with an asterisk were identified by the 2007 General Assembly for immediate implementation Cluster A: Technical Assistance
Analysis of Privacy and Data Protection Laws and Directives Around the World
 Analysis of Privacy and Data Protection Laws and Directives Around the World Michael Willett (Seagate) ISTPA Board and Framework Chair Track IIB: Global Privacy Policy The Privacy Symposium: Boston, 23
Analysis of Privacy and Data Protection Laws and Directives Around the World Michael Willett (Seagate) ISTPA Board and Framework Chair Track IIB: Global Privacy Policy The Privacy Symposium: Boston, 23
WIPO Development Agenda
 WIPO Development Agenda 2 The WIPO Development Agenda aims to ensure that development considerations form an integral part of WIPO s work. As such, it is a cross-cutting issue which touches upon all sectors
WIPO Development Agenda 2 The WIPO Development Agenda aims to ensure that development considerations form an integral part of WIPO s work. As such, it is a cross-cutting issue which touches upon all sectors
B) Issues to be Prioritised within the Proposed Global Strategy and Plan of Action:
 INTERGOVERNMENTAL WORKING GROUP ON PUBLIC HEALTH, INNOVATION AND INTELLECTUAL PROPERTY EGA Submission to Section 1 Draft Global Strategy and Plan of Action The European Generic Medicines Association is
INTERGOVERNMENTAL WORKING GROUP ON PUBLIC HEALTH, INNOVATION AND INTELLECTUAL PROPERTY EGA Submission to Section 1 Draft Global Strategy and Plan of Action The European Generic Medicines Association is
Summary Remarks By David A. Olive. WITSA Public Policy Chairman. November 3, 2009
 Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID
 garfinkel.book Page 275 Thursday, June 2, 2005 11:56 PM Chapter 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID Ari Schwartz 1 Paula Bruening 2 Introduction T he private sector s rollout of RFID at
garfinkel.book Page 275 Thursday, June 2, 2005 11:56 PM Chapter 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID Ari Schwartz 1 Paula Bruening 2 Introduction T he private sector s rollout of RFID at
the Companies and Intellectual Property Commission of South Africa (CIPC)
 organized by the Companies and Intellectual Property Commission of South Africa (CIPC) the World Intellectual Property Organization (WIPO) the International Criminal Police Organization (INTERPOL) the
organized by the Companies and Intellectual Property Commission of South Africa (CIPC) the World Intellectual Property Organization (WIPO) the International Criminal Police Organization (INTERPOL) the
Presentation to NAS Committee on IP Management in Standards-Setting Processes. Dan Bart President and CEO Valley View Corporation November 4, 2011
 Presentation to NAS Committee on IP Management in Standards-Setting Processes Dan Bart President and CEO Valley View Corporation November 4, 2011 Who is Dan Bart? Current Chairman of the ANSI IPR Policy
Presentation to NAS Committee on IP Management in Standards-Setting Processes Dan Bart President and CEO Valley View Corporation November 4, 2011 Who is Dan Bart? Current Chairman of the ANSI IPR Policy
Innovation and the Future of Finance
 December 4, 2017 Bank of Japan Innovation and the Future of Finance Remarks at the Paris EUROPLACE Financial Forum in Tokyo Haruhiko Kuroda Governor of the Bank of Japan I. Paris International Expositions
December 4, 2017 Bank of Japan Innovation and the Future of Finance Remarks at the Paris EUROPLACE Financial Forum in Tokyo Haruhiko Kuroda Governor of the Bank of Japan I. Paris International Expositions
THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR
 THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR THE NEXT DIRECTOR AND DEPUTY DIRECTOR OF THE U.S. PATENT AND TRADEMARK OFFICE Revised and approved, AIPLA
THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR THE NEXT DIRECTOR AND DEPUTY DIRECTOR OF THE U.S. PATENT AND TRADEMARK OFFICE Revised and approved, AIPLA
Digital Identity Innovation Canada s Opportunity to Lead the World. Digital ID and Authentication Council of Canada Pre-Budget Submission
 Digital Identity Innovation Canada s Opportunity to Lead the World Digital ID and Authentication Council of Canada Pre-Budget Submission August 4, 2017 Canadian governments, banks, telcos, healthcare providers
Digital Identity Innovation Canada s Opportunity to Lead the World Digital ID and Authentication Council of Canada Pre-Budget Submission August 4, 2017 Canadian governments, banks, telcos, healthcare providers
Counterfeit, Falsified and Substandard Medicines
 Meeting Summary Counterfeit, Falsified and Substandard Medicines Charles Clift Senior Research Consultant, Centre on Global Health Security December 2010 The views expressed in this document are the sole
Meeting Summary Counterfeit, Falsified and Substandard Medicines Charles Clift Senior Research Consultant, Centre on Global Health Security December 2010 The views expressed in this document are the sole
The Role of the Intellectual Property Office
 The Role of the Intellectual Property Office Intellectual Property Office is an operating name of the Patent Office The Hargreaves Review In 2011, Professor Ian Hargreaves published his review of intellectual
The Role of the Intellectual Property Office Intellectual Property Office is an operating name of the Patent Office The Hargreaves Review In 2011, Professor Ian Hargreaves published his review of intellectual
Energy Trade and Transportation: Conscious Parallelism
 Energy Trade and Transportation: Conscious Parallelism DRAFT Speech by Carmen Dybwad, Board Member, National Energy Board to the IAEE North American Conference Mexico City October 20, 2003 Introduction
Energy Trade and Transportation: Conscious Parallelism DRAFT Speech by Carmen Dybwad, Board Member, National Energy Board to the IAEE North American Conference Mexico City October 20, 2003 Introduction
An Essential Health and Biomedical R&D Treaty
 An Essential Health and Biomedical R&D Treaty Submission by Health Action International Global, Initiative for Health & Equity in Society, Knowledge Ecology International, Médecins Sans Frontières, Third
An Essential Health and Biomedical R&D Treaty Submission by Health Action International Global, Initiative for Health & Equity in Society, Knowledge Ecology International, Médecins Sans Frontières, Third
Comments of the AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION. Regarding
 Comments of the AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION Regarding THE ISSUES PAPER OF THE AUSTRALIAN ADVISORY COUNCIL ON INTELLECTUAL PROPERTY CONCERNING THE PATENTING OF BUSINESS SYSTEMS ISSUED
Comments of the AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION Regarding THE ISSUES PAPER OF THE AUSTRALIAN ADVISORY COUNCIL ON INTELLECTUAL PROPERTY CONCERNING THE PATENTING OF BUSINESS SYSTEMS ISSUED
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION
 28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
The ICT industry as driver for competition, investment, growth and jobs if we make the right choices
 SPEECH/06/127 Viviane Reding Member of the European Commission responsible for Information Society and Media The ICT industry as driver for competition, investment, growth and jobs if we make the right
SPEECH/06/127 Viviane Reding Member of the European Commission responsible for Information Society and Media The ICT industry as driver for competition, investment, growth and jobs if we make the right
OECD Innovation Strategy: Key Findings
 The Voice of OECD Business March 2010 OECD Innovation Strategy: Key Findings (SG/INNOV(2010)1) BIAC COMMENTS General comments BIAC has strongly supported the development of the horizontal OECD Innovation
The Voice of OECD Business March 2010 OECD Innovation Strategy: Key Findings (SG/INNOV(2010)1) BIAC COMMENTS General comments BIAC has strongly supported the development of the horizontal OECD Innovation
Thomas Jefferson High School for Science and Technology INTRODUCTION TO SCIENCE POLICY Program of Studies
 Thomas Jefferson High School for Science and Technology INTRODUCTION TO SCIENCE POLICY Program of Studies Standards Benchmarks Indicators 1. Students will demonstrate an understanding of the fundamental
Thomas Jefferson High School for Science and Technology INTRODUCTION TO SCIENCE POLICY Program of Studies Standards Benchmarks Indicators 1. Students will demonstrate an understanding of the fundamental
TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH
 PROGRAM OVERVIEW TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH 02 03 04 05 07 1 WHERE ENTREPRENEURS AND POLICY LEADERS COME TOGETHER. BUSINESS INSPIRES AND
PROGRAM OVERVIEW TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH 02 03 04 05 07 1 WHERE ENTREPRENEURS AND POLICY LEADERS COME TOGETHER. BUSINESS INSPIRES AND
Ethics Guideline for the Intelligent Information Society
 Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
COMMISSION OF THE EUROPEAN COMMUNITIES COMMISSION RECOMMENDATION
 COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 20.8.2009 C(2009) 6464 final COMMISSION RECOMMENDATION 20.8.2009 on media literacy in the digital environment for a more competitive audiovisual and content
COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 20.8.2009 C(2009) 6464 final COMMISSION RECOMMENDATION 20.8.2009 on media literacy in the digital environment for a more competitive audiovisual and content
Updating Data Protection: Part I -- Identifying the Objectives
 Maurer School of Law: Indiana University Digital Repository @ Maurer Law Articles by Maurer Faculty Faculty Scholarship 2009 Updating Data Protection: Part I -- Identifying the Objectives Fred H. Cate
Maurer School of Law: Indiana University Digital Repository @ Maurer Law Articles by Maurer Faculty Faculty Scholarship 2009 Updating Data Protection: Part I -- Identifying the Objectives Fred H. Cate
Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY
 Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY The Internet is changing the way that individuals launch businesses, established companies function, and
Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY The Internet is changing the way that individuals launch businesses, established companies function, and
Bridging the Technology Gap
 Bridging the Technology Gap Short courses for Permanent Missions in Geneva Friday 24th April 2009 Kathy Stokes Science and Technology Section Division of Technology & Logistics UNCTAD Outline Introductory
Bridging the Technology Gap Short courses for Permanent Missions in Geneva Friday 24th April 2009 Kathy Stokes Science and Technology Section Division of Technology & Logistics UNCTAD Outline Introductory
GLOBAL RISK AND INVESTIGATIONS JAPAN CAPABILITY STATEMENT
 GLOBAL RISK AND INVESTIGATIONS JAPAN CAPABILITY STATEMENT CRITICAL THINKING AT THE CRITICAL TIME ABOUT US The Global Risk and Investigations Practice (GRIP) of FTI Consulting is the leading provider of
GLOBAL RISK AND INVESTIGATIONS JAPAN CAPABILITY STATEMENT CRITICAL THINKING AT THE CRITICAL TIME ABOUT US The Global Risk and Investigations Practice (GRIP) of FTI Consulting is the leading provider of
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA Health Insurance Portability and Accountability Act (HIPAA)
 Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
MEASURES TO SUPPORT SMEs IN THE EUROPEAN UNION
 STUDIA UNIVERSITATIS BABEŞ-BOLYAI, NEGOTIA, LV, 1, 2010 MEASURES TO SUPPORT SMEs IN THE EUROPEAN UNION VALENTINA DIANA IGNĂTESCU 1 ABSTRACT. This paper aims to identify and analyze the principal measures
STUDIA UNIVERSITATIS BABEŞ-BOLYAI, NEGOTIA, LV, 1, 2010 MEASURES TO SUPPORT SMEs IN THE EUROPEAN UNION VALENTINA DIANA IGNĂTESCU 1 ABSTRACT. This paper aims to identify and analyze the principal measures
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase. Term Paper Sample Topics
 A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
What does the revision of the OECD Privacy Guidelines mean for businesses?
 m lex A B E X T R A What does the revision of the OECD Privacy Guidelines mean for businesses? The Organization for Economic Cooperation and Development ( OECD ) has long recognized the importance of privacy
m lex A B E X T R A What does the revision of the OECD Privacy Guidelines mean for businesses? The Organization for Economic Cooperation and Development ( OECD ) has long recognized the importance of privacy
"Made In China 2025 & Internet Plus: The 4th Industrial Revolution" Opportunities for Foreign Invested Enterprises in China
 China Insights - Made in China 2025 and Internet Plus - Opportunities for foreign companies in China "Made In China 2025 & Internet Plus: The 4th Industrial Revolution" Opportunities for Foreign Invested
China Insights - Made in China 2025 and Internet Plus - Opportunities for foreign companies in China "Made In China 2025 & Internet Plus: The 4th Industrial Revolution" Opportunities for Foreign Invested
Overview of Intellectual Property Policy and Law of China in 2017
 CPI s Asia Column Presents: Overview of Intellectual Property Policy and Law of China in 2017 By LIU Chuntian 1 & WANG Jiajia 2 (Renmin University of China) October 2018 As China s economic development
CPI s Asia Column Presents: Overview of Intellectual Property Policy and Law of China in 2017 By LIU Chuntian 1 & WANG Jiajia 2 (Renmin University of China) October 2018 As China s economic development
Science Impact Enhancing the Use of USGS Science
 United States Geological Survey. 2002. "Science Impact Enhancing the Use of USGS Science." Unpublished paper, 4 April. Posted to the Science, Environment, and Development Group web site, 19 March 2004
United States Geological Survey. 2002. "Science Impact Enhancing the Use of USGS Science." Unpublished paper, 4 April. Posted to the Science, Environment, and Development Group web site, 19 March 2004
15890/14 MVG/cb 1 DG G 3 C
 Council of the European Union Brussels, 4 December 2014 (OR. en) 15890/14 OUTCOME OF PROCEEDINGS From: To: No. prev. doc.: Subject: Council Delegations IND 354 COMPET 640 MI 930 RECH 452 ECOFIN 1069 ENV
Council of the European Union Brussels, 4 December 2014 (OR. en) 15890/14 OUTCOME OF PROCEEDINGS From: To: No. prev. doc.: Subject: Council Delegations IND 354 COMPET 640 MI 930 RECH 452 ECOFIN 1069 ENV
Global Standards Symposium. Security, privacy and trust in standardisation. ICDPPC Chair John Edwards. 24 October 2016
 Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
Innovation and Technology Law Curriculum
 Innovation and Technology Law Curriculum Core Courses FOUNDATIONS OF PRIVACY LAW (FALL 2016) This course explores the principles of privacy law in relation to the affairs of government, non-government
Innovation and Technology Law Curriculum Core Courses FOUNDATIONS OF PRIVACY LAW (FALL 2016) This course explores the principles of privacy law in relation to the affairs of government, non-government
Author: Paul-Jasper Dittrich
 Digitalisation What can be done to make Europe competitive? Report of the Expert Group Digitalisation, taking place at the International Expert Conference Europe on the Move? Towards a progressive future!
Digitalisation What can be done to make Europe competitive? Report of the Expert Group Digitalisation, taking place at the International Expert Conference Europe on the Move? Towards a progressive future!
Guidelines to Promote National Integrated Circuit Industry Development : Unofficial Translation
 Guidelines to Promote National Integrated Circuit Industry Development : Unofficial Translation Ministry of Industry and Information Technology National Development and Reform Commission Ministry of Finance
Guidelines to Promote National Integrated Circuit Industry Development : Unofficial Translation Ministry of Industry and Information Technology National Development and Reform Commission Ministry of Finance
Before the NATIONAL HIGHWAY TRAFFIC SAFETY ADMINISTRATION Washington, D.C Docket No. NHTSA
 Before the NATIONAL HIGHWAY TRAFFIC SAFETY ADMINISTRATION Washington, D.C. 20590 Docket No. NHTSA-2002-13546 COMMENTS OF THE ELECTRONIC PRIVACY INFORMATION CENTER February 28, 2003 The Electronic Privacy
Before the NATIONAL HIGHWAY TRAFFIC SAFETY ADMINISTRATION Washington, D.C. 20590 Docket No. NHTSA-2002-13546 COMMENTS OF THE ELECTRONIC PRIVACY INFORMATION CENTER February 28, 2003 The Electronic Privacy
Session 1, Part 2: Emerging issues in e-commerce Australian experiences of privacy and consumer protection regulation
 2013/ SOM3/CTI/WKSP1/007 Australian Experiences of Privacy and Consumer Protection Regulation Submitted by: Australia Workshop on Building and Enhancing FTA Negotiation Skills on e-commerce Medan, Indonesia
2013/ SOM3/CTI/WKSP1/007 Australian Experiences of Privacy and Consumer Protection Regulation Submitted by: Australia Workshop on Building and Enhancing FTA Negotiation Skills on e-commerce Medan, Indonesia
Protection of Privacy Policy
 Protection of Privacy Policy Policy No. CIMS 006 Version No. 1.0 City Clerk's Office An Information Management Policy Subject: Protection of Privacy Policy Keywords: Information management, privacy, breach,
Protection of Privacy Policy Policy No. CIMS 006 Version No. 1.0 City Clerk's Office An Information Management Policy Subject: Protection of Privacy Policy Keywords: Information management, privacy, breach,
#Renew2030. Boulevard A Reyers 80 B1030 Brussels Belgium
 #Renew2030 Boulevard A Reyers 80 B1030 Brussels Belgium secretariat@orgalim.eu +32 2 206 68 83 @Orgalim_EU www.orgalim.eu SHAPING A FUTURE THAT S GOOD. Orgalim is registered under the European Union Transparency
#Renew2030 Boulevard A Reyers 80 B1030 Brussels Belgium secretariat@orgalim.eu +32 2 206 68 83 @Orgalim_EU www.orgalim.eu SHAPING A FUTURE THAT S GOOD. Orgalim is registered under the European Union Transparency
Ethics, privacy and legal issues concerning GIS. This is lecture 12
 Ethics, privacy and legal issues concerning GIS This is lecture 12 New technologies; new laws Any new technology brings with it a set of previously unencountered ethical problems. E.g. printing press;
Ethics, privacy and legal issues concerning GIS This is lecture 12 New technologies; new laws Any new technology brings with it a set of previously unencountered ethical problems. E.g. printing press;
Digital Industrialisation in Developing Countries - A Review of the Business and Policy Landscape
 1 Digital Industrialisation in Developing Countries - A Review of the Business and Policy Landscape Executive Summary (As accompanying the full paper at https://tinyurl.com/digi-dev-countries ) Parminder
1 Digital Industrialisation in Developing Countries - A Review of the Business and Policy Landscape Executive Summary (As accompanying the full paper at https://tinyurl.com/digi-dev-countries ) Parminder
BUREAU OF LAND MANAGEMENT INFORMATION QUALITY GUIDELINES
 BUREAU OF LAND MANAGEMENT INFORMATION QUALITY GUIDELINES Draft Guidelines for Ensuring and Maximizing the Quality, Objectivity, Utility, and Integrity of Information Disseminated by the Bureau of Land
BUREAU OF LAND MANAGEMENT INFORMATION QUALITY GUIDELINES Draft Guidelines for Ensuring and Maximizing the Quality, Objectivity, Utility, and Integrity of Information Disseminated by the Bureau of Land
RBI Working Group report on FinTech: Key themes
 www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
Globalisation increasingly affects how companies in OECD countries
 ISBN 978-92-64-04767-9 Open Innovation in Global Networks OECD 2008 Executive Summary Globalisation increasingly affects how companies in OECD countries operate, compete and innovate, both at home and
ISBN 978-92-64-04767-9 Open Innovation in Global Networks OECD 2008 Executive Summary Globalisation increasingly affects how companies in OECD countries operate, compete and innovate, both at home and
ICO submission to the inquiry of the House of Lords Select Committee on Communications - The Internet : To Regulate or not to Regulate?
 Information Commissioner s Office ICO submission to the inquiry of the House of Lords Select Committee on Communications - The Internet : To Regulate or not to Regulate? 16 May 2018 V. 1.0 Final 1 Contents
Information Commissioner s Office ICO submission to the inquiry of the House of Lords Select Committee on Communications - The Internet : To Regulate or not to Regulate? 16 May 2018 V. 1.0 Final 1 Contents
Interoperable systems that are trusted and secure
 Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Environmental Protection Agency
 Good Laboratory Management: Means compliance with the correct regulations for each individual study.. Environmental Protection Agency Established 1970 To enforce environmental protection standards Clean
Good Laboratory Management: Means compliance with the correct regulations for each individual study.. Environmental Protection Agency Established 1970 To enforce environmental protection standards Clean
Mining, Minerals and Sustainable Development Project PROJECT BULLETIN. Special Issue
 Mining, Minerals and Sustainable Development Project email: mmsd@iied.org www.iied.org/mmsd PROJECT BULLETIN Bulletin No. 11 02/03/01 Special Issue MMSD considers it important to provide its bulletin readers
Mining, Minerals and Sustainable Development Project email: mmsd@iied.org www.iied.org/mmsd PROJECT BULLETIN Bulletin No. 11 02/03/01 Special Issue MMSD considers it important to provide its bulletin readers
Globalizing IPR Protection: How Important Might RTAs Be?
 Globalizing IPR Protection: How Important Might RTAs Be? Keith Maskus, University of Colorado Boulder (keith.maskus@colorado.edu) NAS Innovation Policy Forum National and International IP Policies and
Globalizing IPR Protection: How Important Might RTAs Be? Keith Maskus, University of Colorado Boulder (keith.maskus@colorado.edu) NAS Innovation Policy Forum National and International IP Policies and
INTERNET CONNECTIVITY
 FULFILLING THE PROMISE OF INTERNET CONNECTIVITY The reach of Internet connectivity is both breathtaking and a cause for concern. In assessing its progress, the principal aspects to consider are access,
FULFILLING THE PROMISE OF INTERNET CONNECTIVITY The reach of Internet connectivity is both breathtaking and a cause for concern. In assessing its progress, the principal aspects to consider are access,
Position Paper: Ethical, Legal and Socio-economic Issues in Robotics
 Position Paper: Ethical, Legal and Socio-economic Issues in Robotics eurobotics topics group on ethical, legal and socioeconomic issues (ELS) http://www.pt-ai.org/tg-els/ 23.03.2017 (vs. 1: 20.03.17) Version
Position Paper: Ethical, Legal and Socio-economic Issues in Robotics eurobotics topics group on ethical, legal and socioeconomic issues (ELS) http://www.pt-ai.org/tg-els/ 23.03.2017 (vs. 1: 20.03.17) Version
Whatever Happened to the. Fair Information Practices?
 Whatever Happened to the Fair Information Practices? Beth Givens Director Privacy Rights Clearinghouse Privacy Symposium August 22, 2007 Cambridge, MA Topics Definition and origins of FIPs Overview of
Whatever Happened to the Fair Information Practices? Beth Givens Director Privacy Rights Clearinghouse Privacy Symposium August 22, 2007 Cambridge, MA Topics Definition and origins of FIPs Overview of
The BGF-G7 Summit Report The AIWS 7-Layer Model to Build Next Generation Democracy
 The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
Introduction to the SMEs Division of WIPO
 Introduction to the SMEs Division of WIPO Guriqbal Singh Jaiya Director Small and Medium-Sized Enterprises Division World Intellectual Property Organization 1 National Needs and Concerns Sustainable Economic
Introduction to the SMEs Division of WIPO Guriqbal Singh Jaiya Director Small and Medium-Sized Enterprises Division World Intellectual Property Organization 1 National Needs and Concerns Sustainable Economic
The 26 th APEC Economic Leaders Meeting
 The 26 th APEC Economic Leaders Meeting PORT MORESBY, PAPUA NEW GUINEA 18 November 2018 The Chair s Era Kone Statement Harnessing Inclusive Opportunities, Embracing the Digital Future 1. The Statement
The 26 th APEC Economic Leaders Meeting PORT MORESBY, PAPUA NEW GUINEA 18 November 2018 The Chair s Era Kone Statement Harnessing Inclusive Opportunities, Embracing the Digital Future 1. The Statement
Self regulation applied to interactive games : success and challenges
 SPEECH/07/429 Viviane Reding Member of the European Commission responsible for Information Society and Media Self regulation applied to interactive games : success and challenges ISFE Expert Conference
SPEECH/07/429 Viviane Reding Member of the European Commission responsible for Information Society and Media Self regulation applied to interactive games : success and challenges ISFE Expert Conference
Committee on the Internal Market and Consumer Protection. of the Committee on the Internal Market and Consumer Protection
 European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
Denmark as a digital frontrunner
 Denmark as a digital frontrunner Recommendations for the government from the Digital Growth Panel May 2017 Digital Growth Panel Summary Vision: Denmark as a digital frontrunner Denmark and the rest of
Denmark as a digital frontrunner Recommendations for the government from the Digital Growth Panel May 2017 Digital Growth Panel Summary Vision: Denmark as a digital frontrunner Denmark and the rest of
Children s rights in the digital environment: Challenges, tensions and opportunities
 Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Guidelines on Standardization and Patent Pool Arrangements
 Guidelines on Standardization and Patent Pool Arrangements Part 1 Introduction In industries experiencing innovation and technical change, such as the information technology sector, it is important to
Guidelines on Standardization and Patent Pool Arrangements Part 1 Introduction In industries experiencing innovation and technical change, such as the information technology sector, it is important to
28 March Report of the Working Group on Pharmaceuticals and Public Health of the High Level Committee on Health.
 PHARMACEUTICALS AND PUBLIC HEALTH IN THE EU: PROPOSALS TO THE HIGH LEVEL COMMITTEE ON HEALTH FOR POLICIES AND ACTIONS IN THE FRAMEWORK OF THE TREATY OF AMSTERDAM a) 28 March 2000 a) Report of the Working
PHARMACEUTICALS AND PUBLIC HEALTH IN THE EU: PROPOSALS TO THE HIGH LEVEL COMMITTEE ON HEALTH FOR POLICIES AND ACTIONS IN THE FRAMEWORK OF THE TREATY OF AMSTERDAM a) 28 March 2000 a) Report of the Working
IP KEY SOUTH EAST ASIA ANNUAL WORK PLAN FOR 2018
 ANNUAL WORK PLAN FOR 2018 IP KEY SOUTH EAST ASIA ANNUAL WORK PLAN FOR 2018 IP Key South East Asia is an EU Project designed to support the Free Trade Agreement (FTA) talks and Intellectual Property Dialogues
ANNUAL WORK PLAN FOR 2018 IP KEY SOUTH EAST ASIA ANNUAL WORK PLAN FOR 2018 IP Key South East Asia is an EU Project designed to support the Free Trade Agreement (FTA) talks and Intellectual Property Dialogues
24 May Committee Secretariat Justice Committee Parliament Buildings Wellington. Dear Justice Select Committee member,
 24 May 2018 Committee Secretariat Justice Committee Parliament Buildings Wellington Dear Justice Select Committee member, Submission to the Justice Committee Review Privacy Bill Thank you for the opportunity
24 May 2018 Committee Secretariat Justice Committee Parliament Buildings Wellington Dear Justice Select Committee member, Submission to the Justice Committee Review Privacy Bill Thank you for the opportunity
Chapter 4 INFORMATION SYSTEMS
 Chapter 4 MANAGING THE DIGITAL FIRM, 12 TH EDITION ETHICAL AND SOCIAL ISSUES IN VIDEO CASES Case 1: Big Brother is Copying Everything on the Internet Case 2: Delete: The Virtue of Forgetting in a Digital
Chapter 4 MANAGING THE DIGITAL FIRM, 12 TH EDITION ETHICAL AND SOCIAL ISSUES IN VIDEO CASES Case 1: Big Brother is Copying Everything on the Internet Case 2: Delete: The Virtue of Forgetting in a Digital
PROMOTING QUALITY AND STANDARDS
 PROMOTING QUALITY AND STANDARDS 1 PROMOTING QUALITY AND STANDARDS Strengthen capacities of national and regional quality systems (i.e. metrology, standardization and accreditation) Build conformity assessment
PROMOTING QUALITY AND STANDARDS 1 PROMOTING QUALITY AND STANDARDS Strengthen capacities of national and regional quality systems (i.e. metrology, standardization and accreditation) Build conformity assessment
Transparency in Negotiations Involving Norms for Knowledge Goods. What Should USTR Do? 21 Specific Recommendations
 What Should USTR Do? 21 Specific Recommendations July 22, 2009 To: United States Trade Representative From: Electronic Frontier Foundation (EFF) Essential Action Knowledge Ecology International (KEI) Public
What Should USTR Do? 21 Specific Recommendations July 22, 2009 To: United States Trade Representative From: Electronic Frontier Foundation (EFF) Essential Action Knowledge Ecology International (KEI) Public
Expert Group Meeting on
 Aide memoire Expert Group Meeting on Governing science, technology and innovation to achieve the targets of the Sustainable Development Goals and the aspirations of the African Union s Agenda 2063 2 and
Aide memoire Expert Group Meeting on Governing science, technology and innovation to achieve the targets of the Sustainable Development Goals and the aspirations of the African Union s Agenda 2063 2 and
The global leader in trusted identities for an increasingly digital world. Press kit September, 28 th 2017
 The global leader in trusted identities for an increasingly digital world Press kit September, 28 th 2017 2 FOREWORD Foreword by Didier Lamouche, Chief Executive Officer I am pleased and proud to present
The global leader in trusted identities for an increasingly digital world Press kit September, 28 th 2017 2 FOREWORD Foreword by Didier Lamouche, Chief Executive Officer I am pleased and proud to present
Scenario Development Process
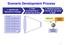 Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Ten Principles for a Revised US Privacy Framework
 Ten Principles for a Revised US Privacy Framework Our economies and societies are in the midst of the 4 th industrial revolution, with digitalization and datafication transforming the way we live, work
Ten Principles for a Revised US Privacy Framework Our economies and societies are in the midst of the 4 th industrial revolution, with digitalization and datafication transforming the way we live, work
CRS Report for Congress
 95-150 SPR Updated November 17, 1998 CRS Report for Congress Received through the CRS Web Cooperative Research and Development Agreements (CRADAs) Wendy H. Schacht Specialist in Science and Technology
95-150 SPR Updated November 17, 1998 CRS Report for Congress Received through the CRS Web Cooperative Research and Development Agreements (CRADAs) Wendy H. Schacht Specialist in Science and Technology
clarification to bring legal certainty to these issues have been voiced in various position papers and statements.
 ESR Statement on the European Commission s proposal for a Regulation on the protection of individuals with regard to the processing of personal data on the free movement of such data (General Data Protection
ESR Statement on the European Commission s proposal for a Regulation on the protection of individuals with regard to the processing of personal data on the free movement of such data (General Data Protection
The Policy Content and Process in an SDG Context: Objectives, Instruments, Capabilities and Stages
 The Policy Content and Process in an SDG Context: Objectives, Instruments, Capabilities and Stages Ludovico Alcorta UNU-MERIT alcorta@merit.unu.edu www.merit.unu.edu Agenda Formulating STI policy STI policy/instrument
The Policy Content and Process in an SDG Context: Objectives, Instruments, Capabilities and Stages Ludovico Alcorta UNU-MERIT alcorta@merit.unu.edu www.merit.unu.edu Agenda Formulating STI policy STI policy/instrument
ONR Strategy 2015 to 2020
 Title of publication ONR Strategy 2015 to 2020 Office for Nuclear Regulation Page 1 of 5 Introduction Nick Baldwin, Chair The Energy Act 2013 provided for the creation of ONR as an independent, statutory
Title of publication ONR Strategy 2015 to 2020 Office for Nuclear Regulation Page 1 of 5 Introduction Nick Baldwin, Chair The Energy Act 2013 provided for the creation of ONR as an independent, statutory
Report to Congress regarding the Terrorism Information Awareness Program
 Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
DIMACS/PORTIA Workshop on Privacy Preserving
 DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
Section 1: Internet Governance Principles
 Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
Responsible AI & National AI Strategies
 Responsible AI & National AI Strategies European Union Commission Dr. Anand S. Rao Global Artificial Intelligence Lead Today s discussion 01 02 Opportunities in Artificial Intelligence Risks of Artificial
Responsible AI & National AI Strategies European Union Commission Dr. Anand S. Rao Global Artificial Intelligence Lead Today s discussion 01 02 Opportunities in Artificial Intelligence Risks of Artificial
Recommendation Regarding a National Strategy for Intellectual Property. Background. 6 June 2013
 6 June 2013 Recommendation Regarding a National Strategy for Intellectual Property Background All forms of intellectual property (IP) rights are pillars of a new, knowledgebased economy. The potential
6 June 2013 Recommendation Regarding a National Strategy for Intellectual Property Background All forms of intellectual property (IP) rights are pillars of a new, knowledgebased economy. The potential
Executive Summary Industry s Responsibility in Promoting Responsible Development and Use:
 Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
Methodology for Agent-Oriented Software
 ب.ظ 03:55 1 of 7 2006/10/27 Next: About this document... Methodology for Agent-Oriented Software Design Principal Investigator dr. Frank S. de Boer (frankb@cs.uu.nl) Summary The main research goal of this
ب.ظ 03:55 1 of 7 2006/10/27 Next: About this document... Methodology for Agent-Oriented Software Design Principal Investigator dr. Frank S. de Boer (frankb@cs.uu.nl) Summary The main research goal of this
