MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID
|
|
|
- Peter Price
- 5 years ago
- Views:
Transcription
1 garfinkel.book Page 275 Thursday, June 2, :56 PM Chapter 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID Ari Schwartz 1 Paula Bruening 2 Introduction T he private sector s rollout of RFID at the item level predictably raises concerns about consumers ability to protect the privacy of their personal information. This use of RFID represents the introduction of a new method of data collection in an environment already rich with opportunities for business and government to create powerful dossiers on individuals purchases, preferences, and movement throughout the world. To the extent that RFID technologies collect information that is not specific or linked to individuals and individual identity, they tend not to sound an alarm about privacy. But as the power of the technology increases so that information collected through RFID can be associated with a specific individual, perceptions of RFID as an invasive technology raise serious concerns. In public policy discussions about the threats to privacy raised by emerging technologies, experts often make the point that technologies do not invade privacy; people use technology to engage in privacy-invading activities. But while the assertion that technologies are policy neutral has become dictum, privacy neutrality is assured only if measures are taken in law, through technology, 1. Ari Schwartz is the associate director of the Center for Democracy and Technology (CDT). 2. Paula Bruening is the staff counsel for CDT. 275
2 garfinkel.book Page 276 Thursday, June 2, :56 PM 276 CHAPTER 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID and in industry self-governance to enable consumers to exercise control over the collection of their personal information. Whether new technologies invade privacy or remain privacy neutral depends on whether privacy issues raised by the technology are examined and addressed early. Ensuring that new technologies are developed and deployed in a manner that makes it possible for consumers to exercise control over if and how much their personal information is collected and used requires a three-pronged approach. First, the design of the technology must incorporate privacy-enhancing technologies such as those that limit the collection of data, anonymize data, or offer users control over the collection of their personal information. Empowering users to consent to or deny the collection of information by a technology, or to disable a technology entirely when appropriate, gives them a critical tool for managing the collection and use of their personal information. Second, the collection, use, and retention of information with the technology must be guided by traditional principles of fair information practices incorporated in legislation. Such baseline legislation would establish consistent expectations for both consumers and businesses about their rights and responsibilities related to the data collected and would impose the force of law. Third, companies using the new technology to collect information must engage in self-regulation: self imposed, industry-wide policies that foster responsible data collection, sharing, and use. When it is enforced, self-regulation can build on the basic requirements set out in law, allowing industry to tailor its approach to privacy in a way that serves both business and consumers and allows industry to respond promptly to emerging technologies, evolving business models, and unanticipated privacy problems. The appropriate balance of these three elements technology, government action, and self-regulation depends on several factors. These include the nature of the information collection technology, the way it is used, the kind of information it collects, and the public s perception of the technology and its concern about possible privacy invasion. RFID raises unique concerns, in part because it is invisible to consumers; unless consumers are notified, they may be oblivious to its use. These concerns are heightened because of the passive way that information is collected from the RFID chips. Consumers do not engage in any active way to relinquish information or engage in data collection. And the readers are potentially ubiquitous. Current RFID readers have only short-range capabilities, but developers promise that more powerful readers will densely populate public and private spaces.
3 garfinkel.book Page 277 Thursday, June 2, :56 PM SCENARIO 1: NO ONE WINS 277 These considerations, specific to RFID technology and data collection, must guide decision making about how technology solutions, law, and self-regulation are implemented. Failure to properly account for these considerations can result in negative consequences for businesses, consumers, and the development of new technology. Public backlash against surreptitious use of technologies could slow implementation and impede its innovation for beneficial uses. As a result, neither the public nor industry would realize RFID s benefits, and government, spurred by public demand, could step in to enact legislation that would be ineffective at curbing abuses while stifling or skewing technology development. This chapter describes a series of scenarios that illustrate the best and worst results from the implementation and use of RFID for information collection. They are written from the vantage point of 2015, which is the not-too-distant future. The scenarios speculate about the decisions that might be made in the development of technology, the level of attention paid to consumer concerns and public policy about RFID, industry and government decisions on where and how to use the technology, and the possible consequences of these decisions for privacy. These scenarios are intended not to be predictive but rather to serve as the starting point for thought-provoking discussion about how best to address the privacy concerns raised by this technology. Scenario 1: No One Wins In mid-2004, industry and government increased their use of item-level RFID tagging with little thought to consumers perception about the possible invasiveness of the technology. At that time, the chips were used only in manufacturing processes and distribution chains to enhance inventory control and tracking of deliveries. However, plans were in place to implement tags more widely and to deploy more powerful tags that could transmit more sensitive information. Developers of RFID systems and organizations using the tags took no steps to consider the privacy implications of the technology and paid little attention to issues surrounding responsible tag use and the management of the information the tags collect. To fill the vacuum created by this lack of policy, by 2006, California passed a law that limited the use of RFID chips, such that the chips contained in merchandise purchased by consumers must be deactivated. Massachusetts also passed a law requiring opt-in consent by consumers for use of RFID in any way. The effect of these laws was to make it nearly impossible for companies to use RFID for even the most innocuous purposes. Companies doing business in
4 garfinkel.book Page 278 Thursday, June 2, :56 PM 278 CHAPTER 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID California had used RFID technology for inventory control, but their inability to be sure that the tags were deactivated at the customer checkout raised concerns about liability and led them to end their use entirely. Massachusetts companies found themselves unable to manage the opt-in requirement and also stopped using the tags. Unwilling to assume the costs and liability of RFID tags, companies sought other measures to monitor inventory. Initially, companies simply increased store and stockroom video surveillance to reduce theft. By 2010, facial recognition cameras had become increasingly common in stores, both on the public storeroom floor and in stockrooms. Capitalizing on the capabilities of this technology, companies soon began matching consumer purchasers with facial ID, all without customer knowledge or consent. Although the purpose of this practice initially was to reduce the incidence of shoplifting, companies eventually used it for behavior-based marketing research. Data-mining companies began buying the proprietary databases created as a result of this practice. In 2015, two companies announced that they had collected images of over 150 million Americans and tied this information to their purchasing habits. The result: unprecedented consumer concern about privacy. Scenario 2: Shangri-La While developing plans for broad implementation of RFID in retail stores, companies recognized that, as with other information collection technologies, RFID might raise consumers concerns about privacy. Moreover, companies learned from the experience they gained from implementing other information collection technologies that it is best to address privacy concerns early. To encourage consumers acceptance of the technology and to protect the trust relationship, companies decided to directly address consumers concerns about collection and storage of information through RFID technology and an associated network of databases. Working with consumer and privacy advocates, technologists, industry coalitions, and academic experts, RFID implementers developed an effective selfregulatory regime to govern information collection through RFID. Under the self-regulatory program, consumers are given clear, effective notice that RFID technology is in use, and in most instances, they have the opportunity to make decisions about the collection of information via the tag and the persistent use of the tag after the product leaves the store. Collectors and custodians of information using RFID employ strong, reliable security measures for their databases, and consumers are provided the opportunity to access information
5 garfinkel.book Page 279 Thursday, June 2, :56 PM SCENARIO 3: THE WILD WEST 279 mentioned about them. Robust enforcement, through independent oversight organizations and consumer recourse mechanisms, promote the credibility of self-regulatory measures To further enhance the effectiveness of these efforts, the business community, working with consumer advocates, initiated a far-reaching public education campaign about how RFID technology is used and how consumers can exercise their privacy rights with regard to information collected through the technology. To promote broad adoption of self-regulation, industry leaders and trade associations worked closely with companies to highlight its benefits, both to businesses and to the companies developing RFID technology. Tag manufacturers required companies using the tags to sign agreements saying they would follow the rules. Companies outside the self-regulatory structure soon found doing business much more difficult and eventually complied with the standards. While readers are available for purchase, companies consider the information about individual items proprietary and guard it closely, making it extremely difficult for sensitive information to fall into the wrong hands. Scenario 3: The Wild West In 2008, businesses and government began deploying item-level RFID tags on a broad scale. Unmoved by expressions of concern about this technology s impact on privacy, they made no effort to address the issue through technology, self-regulation, or law. Immediately after the first RFID tags were deployed in retail establishments, researchers concerned about consumer privacy and misuse of the tags and the information collected from them published papers on how to clone and destroy the tags. Privacy vigilantes, angered by the lack of protection for information collected through RFID, began to wander through stores killing existing tags and placing cloned tags in the pockets of clothing to render the RFID technology useless. Tags used by government were treated similarly. The efforts to use RFID for baggage handling and customs control were frustrated, and government agencies were forced to return to twentieth-century, pre-9/11 approaches to securing travelers and borders. Citizens and government became fearful of the ability of bad actors to thwart the tags. In place of RFID, government and law enforcement adopted more onerous and invasive search and questioning procedures for travelers.
6 garfinkel.book Page 280 Thursday, June 2, :56 PM 280 CHAPTER 17 MULTIPLE SCENARIOS FOR PRIVATE-SECTOR USE OF RFID By 2010, retailers and government began to use new, slightly more expensive tags that were harder to clone or destroy. However, two years later, information on a low-cost means to jam the new RFID readers was widely distributed. Implementers found that the large investment in the second-generation technology was completely wasted. As a third generation is developed, companies question the wisdom of investing in a continued Spy vs. Spy situation, particularly because anti-rfid activists are more organized than ever. Scenario 4: Trust but Verify In 2006, Congress passed legislation establishing baseline privacy protection for information collected about consumers. The law applied to no particular technology but rather codified in law long-established principles of fair information practices: notice, choice, security, access, and recourse to guide companies collection and management of consumer information. To comply with this general law governing information collection, companies using RFID were required to: Provide consumers with notice that RFID technology is being used and disclose the kind of information being collected by the technology Obtain the consent of the customer to share any personal information they collect using RFID for any purpose other than completing a transaction and inventory control Provide appropriate security for the information collected Provide individuals with the ability to access the information retailers maintain about them and correct inaccurate information similar to what is currently being done with credit reports The requirements of the law provided technologists and companies implementing RFID with some baseline expectations about privacy as well as the responsibilities attendant to the collection and use of information in general. Armed with this knowledge, companies using RFID were able from the outset to put in place the technological and information management controls to enhance privacy. Over and above these baseline requirements, the business community, prompted by consumer advocates, recognized that RFID raised some technology-specific questions about information collection. For example, how might a company most effectively offer notice to a consumer? The flexible environment of the Web to provide notice already tests companies ability to effectively and clearly communicate complex technical and legal
7 garfinkel.book Page 281 Thursday, June 2, :56 PM CONCLUSIONS 281 concepts with consumers. However, Web-based notice about the use of an invisible technology that collects information with no active consumer engagement presents even greater challenges. Similarly, how would companies make it possible for consumers to exercise choice about the collection and sharing of information gained with RFID technology? How could they ensure that their choice would be honored? To respond to such concerns, the business community developed privacyrespectful best practices for the use of RFID technologies. Building on the basic requirements in law, business was free to develop creative solutions to RFID-specific privacy challenges. In 2010, state attorneys general began to file lawsuits against companies found not in compliance with the requirements of the baseline privacy law. Meanwhile, business continued to develop and refine best practices in response to the developing technology and relied on self-regulatory regimes to address RFID-specific concerns. Conclusions RFID is a technology at the political crossroads. Examining scenarios for implementation of the technology and public policy is helpful to the extent that it urges policymakers in government and in industry to consider the potential harm and benefits that might result from a policy about privacy and RFID. It may also prompt them to explore the logical progression of events following the adoption of a policy and the expected and unexpected consequences that might result. Reliance on any one approach to addressing the privacy questions raised by this technology including taking no action at all is risky. The outcome could distort or impede the development of a technology that may offer significant benefits for consumers or that so severely compromises trust in the technology that public acceptance becomes impossible. The answer lies in a mix of approaches that provides a foundation of assurances for consumers in law and the flexibility of industry solutions that can respond quickly to rapidly changing technology and applications.
8 garfinkel.book Page 282 Thursday, June 2, :56 PM
Pan-Canadian Trust Framework Overview
 Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Executive Summary Industry s Responsibility in Promoting Responsible Development and Use:
 Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
ITAC RESPONSE: Modernizing Consent and Privacy in PIPEDA
 August 5, 2016 ITAC RESPONSE: Modernizing Consent and Privacy in PIPEDA The Information Technology Association of Canada (ITAC) appreciates the opportunity to participate in the Office of the Privacy Commissioner
August 5, 2016 ITAC RESPONSE: Modernizing Consent and Privacy in PIPEDA The Information Technology Association of Canada (ITAC) appreciates the opportunity to participate in the Office of the Privacy Commissioner
Should privacy impact assessments be mandatory? David Wright Trilateral Research & Consulting 17 Sept 2009
 Should privacy impact assessments be mandatory? David Wright Trilateral Research & Consulting 17 Sept 2009 1 Today s presentation Databases solving one problem & creating another What is a privacy impact
Should privacy impact assessments be mandatory? David Wright Trilateral Research & Consulting 17 Sept 2009 1 Today s presentation Databases solving one problem & creating another What is a privacy impact
Violent Intent Modeling System
 for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
Where s The Beep? Privacy, Security, & User (Mis)undestandings of RFID
 Where s The Beep? Privacy, Security, & User (Mis)undestandings of RFID Jennifer King Research Specialist Overview Quick overview of RFID Research Question Context of Inquiry Study + findings Implications
Where s The Beep? Privacy, Security, & User (Mis)undestandings of RFID Jennifer King Research Specialist Overview Quick overview of RFID Research Question Context of Inquiry Study + findings Implications
Making Identity Use Predictable. UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016
 Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
Making Identity Use Predictable UNCITRAL Colloquium on Identity Management and Trust Services 21 April, 2016 Why Am I Here CertiPath High Assurance Identity Trust Framework Supports Aerospace and Defense
This research is supported by the TechPlan program funded by the ITS Institute at the University of Minnesota
 Frank Douma, Assistant Director,! Sarah Aue, Research Assistant! State and Local Policy Program! Humphrey Institute of Public Affairs! University of Minnesota! This research is supported by the TechPlan
Frank Douma, Assistant Director,! Sarah Aue, Research Assistant! State and Local Policy Program! Humphrey Institute of Public Affairs! University of Minnesota! This research is supported by the TechPlan
EXPLORATION DEVELOPMENT OPERATION CLOSURE
 i ABOUT THE INFOGRAPHIC THE MINERAL DEVELOPMENT CYCLE This is an interactive infographic that highlights key findings regarding risks and opportunities for building public confidence through the mineral
i ABOUT THE INFOGRAPHIC THE MINERAL DEVELOPMENT CYCLE This is an interactive infographic that highlights key findings regarding risks and opportunities for building public confidence through the mineral
Presentation Outline
 Functional requirements for privacy enhancing systems Fred Carter Senior Policy & Technology Advisor Office of the Information & Privacy Commissioner / Ontario, Canada OECD Workshop on Digital Identity
Functional requirements for privacy enhancing systems Fred Carter Senior Policy & Technology Advisor Office of the Information & Privacy Commissioner / Ontario, Canada OECD Workshop on Digital Identity
FIPPs Fair Information Practice Principles
 FIPPs Fair Information Practice Principles T H E G O L D S TA N DA R D F O R P R OT EC T I N G P E R S O N A L I N F O R M AT I O N Learning Objectives Recognize the Fair Information Practice Principles
FIPPs Fair Information Practice Principles T H E G O L D S TA N DA R D F O R P R OT EC T I N G P E R S O N A L I N F O R M AT I O N Learning Objectives Recognize the Fair Information Practice Principles
March 27, The Information Technology Industry Council (ITI) appreciates this opportunity
 Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Toward Objective Global Privacy Standards. Ari Schwartz Senior Internet Policy Advisor
 Toward Objective Global Privacy Standards Ari Schwartz Senior Internet Policy Advisor Summary Technical standards offer a new ability to support the important public policy goal of better protecting privacy.
Toward Objective Global Privacy Standards Ari Schwartz Senior Internet Policy Advisor Summary Technical standards offer a new ability to support the important public policy goal of better protecting privacy.
Children s rights in the digital environment: Challenges, tensions and opportunities
 Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Australian Census 2016 and Privacy Impact Assessment (PIA)
 http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
This policy sets out how Legacy Foresight and its Associates will seek to ensure compliance with the legislation.
 Privacy Notice August 2018 Introduction The General Data Protection Regulation (GDPR) is European wide data protection legislation that requires organisations working with individuals based in the European
Privacy Notice August 2018 Introduction The General Data Protection Regulation (GDPR) is European wide data protection legislation that requires organisations working with individuals based in the European
RFID and Privacy an antagonism?
 BERLIN COMMISSIONER FOR DATA PROTECTION AND FREEDOM OF INORMATION, GERMANY RFID and Privacy an antagonism? Dr. Alexander Dix, LL.M. and Freedom of Information Member of the Art.29 Working Party Statement
BERLIN COMMISSIONER FOR DATA PROTECTION AND FREEDOM OF INORMATION, GERMANY RFID and Privacy an antagonism? Dr. Alexander Dix, LL.M. and Freedom of Information Member of the Art.29 Working Party Statement
The New Economy: Transatlantic Policy Comparison Data Privacy By Abe Newman
 The New Economy: Transatlantic Policy Comparison Data Privacy By Abe Newman A central concern of privacy is the ability of an individual to control the access to and use of personal information. New technologies,
The New Economy: Transatlantic Policy Comparison Data Privacy By Abe Newman A central concern of privacy is the ability of an individual to control the access to and use of personal information. New technologies,
Whatever Happened to the. Fair Information Practices?
 Whatever Happened to the Fair Information Practices? Beth Givens Director Privacy Rights Clearinghouse Privacy Symposium August 22, 2007 Cambridge, MA Topics Definition and origins of FIPs Overview of
Whatever Happened to the Fair Information Practices? Beth Givens Director Privacy Rights Clearinghouse Privacy Symposium August 22, 2007 Cambridge, MA Topics Definition and origins of FIPs Overview of
What does the revision of the OECD Privacy Guidelines mean for businesses?
 m lex A B E X T R A What does the revision of the OECD Privacy Guidelines mean for businesses? The Organization for Economic Cooperation and Development ( OECD ) has long recognized the importance of privacy
m lex A B E X T R A What does the revision of the OECD Privacy Guidelines mean for businesses? The Organization for Economic Cooperation and Development ( OECD ) has long recognized the importance of privacy
Privacy and the EU GDPR US and UK Privacy Professionals
 Privacy and the EU GDPR US and UK Privacy Professionals Independent research conducted by Dimensional Research on behalf of TrustArc US 888.878.7830 EU +44 (0)203.078.6495 www.trustarc.com 2017 TrustArc
Privacy and the EU GDPR US and UK Privacy Professionals Independent research conducted by Dimensional Research on behalf of TrustArc US 888.878.7830 EU +44 (0)203.078.6495 www.trustarc.com 2017 TrustArc
Section 1: Internet Governance Principles
 Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
Privacy Policy SOP-031
 SOP-031 Version: 2.0 Effective Date: 18-Nov-2013 Table of Contents 1. DOCUMENT HISTORY...3 2. APPROVAL STATEMENT...3 3. PURPOSE...4 4. SCOPE...4 5. ABBREVIATIONS...5 6. PROCEDURES...5 6.1 COLLECTION OF
SOP-031 Version: 2.0 Effective Date: 18-Nov-2013 Table of Contents 1. DOCUMENT HISTORY...3 2. APPROVAL STATEMENT...3 3. PURPOSE...4 4. SCOPE...4 5. ABBREVIATIONS...5 6. PROCEDURES...5 6.1 COLLECTION OF
CCTV Policy. Policy reviewed by Academy Transformation Trust on June This policy links to: Safeguarding Policy Data Protection Policy
 CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Located: Safeguarding Policy Data Protection Policy Review Date May 2019 Our Mission To provide the very best
CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Located: Safeguarding Policy Data Protection Policy Review Date May 2019 Our Mission To provide the very best
REPORT ON THE INTERNATIONAL CONFERENCE MEMORY OF THE WORLD IN THE DIGITAL AGE: DIGITIZATION AND PRESERVATION OUTLINE
 37th Session, Paris, 2013 inf Information document 37 C/INF.15 6 August 2013 English and French only REPORT ON THE INTERNATIONAL CONFERENCE MEMORY OF THE WORLD IN THE DIGITAL AGE: DIGITIZATION AND PRESERVATION
37th Session, Paris, 2013 inf Information document 37 C/INF.15 6 August 2013 English and French only REPORT ON THE INTERNATIONAL CONFERENCE MEMORY OF THE WORLD IN THE DIGITAL AGE: DIGITIZATION AND PRESERVATION
CONSENT IN THE TIME OF BIG DATA. Richard Austin February 1, 2017
 CONSENT IN THE TIME OF BIG DATA Richard Austin February 1, 2017 1 Agenda 1. Introduction 2. The Big Data Lifecycle 3. Privacy Protection The Existing Landscape 4. The Appropriate Response? 22 1. Introduction
CONSENT IN THE TIME OF BIG DATA Richard Austin February 1, 2017 1 Agenda 1. Introduction 2. The Big Data Lifecycle 3. Privacy Protection The Existing Landscape 4. The Appropriate Response? 22 1. Introduction
Ten Principles for a Revised US Privacy Framework
 Ten Principles for a Revised US Privacy Framework Our economies and societies are in the midst of the 4 th industrial revolution, with digitalization and datafication transforming the way we live, work
Ten Principles for a Revised US Privacy Framework Our economies and societies are in the midst of the 4 th industrial revolution, with digitalization and datafication transforming the way we live, work
Privacy engineering, privacy by design, and privacy governance
 CyLab Lorrie Faith Cranor" Engineering & Public Policy acy & Secur ity Priv e l HT TP ratory bo La 8-533 / 8-733 / 19-608 / 95-818:! Privacy Policy, Law, and Technology CyLab U sab November 17, 2015 ://
CyLab Lorrie Faith Cranor" Engineering & Public Policy acy & Secur ity Priv e l HT TP ratory bo La 8-533 / 8-733 / 19-608 / 95-818:! Privacy Policy, Law, and Technology CyLab U sab November 17, 2015 ://
Digital Identity Innovation Canada s Opportunity to Lead the World. Digital ID and Authentication Council of Canada Pre-Budget Submission
 Digital Identity Innovation Canada s Opportunity to Lead the World Digital ID and Authentication Council of Canada Pre-Budget Submission August 4, 2017 Canadian governments, banks, telcos, healthcare providers
Digital Identity Innovation Canada s Opportunity to Lead the World Digital ID and Authentication Council of Canada Pre-Budget Submission August 4, 2017 Canadian governments, banks, telcos, healthcare providers
Service Level Agreement
 Service Level Agreement Service: Firewall Administration Version: 2017.07.31 Valid: 07/01/2016-07/31/2018 Service Details: Description IET provides firewall services to help secure department networks
Service Level Agreement Service: Firewall Administration Version: 2017.07.31 Valid: 07/01/2016-07/31/2018 Service Details: Description IET provides firewall services to help secure department networks
CCTV Policy. Policy reviewed by Academy Transformation Trust on June This policy links to: T:Drive. Safeguarding Policy Data Protection Policy
 CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Safeguarding Policy Data Protection Policy Located: T:Drive Review Date May 2019 Our Mission To provide the
CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Safeguarding Policy Data Protection Policy Located: T:Drive Review Date May 2019 Our Mission To provide the
The BGF-G7 Summit Report The AIWS 7-Layer Model to Build Next Generation Democracy
 The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
ICC POSITION ON LEGITIMATE INTERESTS
 ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
What We Heard Report Inspection Modernization: The Case for Change Consultation from June 1 to July 31, 2012
 What We Heard Report Inspection Modernization: The Case for Change Consultation from June 1 to July 31, 2012 What We Heard Report: The Case for Change 1 Report of What We Heard: The Case for Change Consultation
What We Heard Report Inspection Modernization: The Case for Change Consultation from June 1 to July 31, 2012 What We Heard Report: The Case for Change 1 Report of What We Heard: The Case for Change Consultation
RFID and privacy - Some industry perspectives (ICC, EICTA)
 RFID and privacy - Some industry perspectives (ICC, EICTA) Jeroen Terstegge ICC, EICTA OECD, Paris 2005-10-05 Identification Technologies: Connecting PEOPLE to Information, Entertainment and Services.
RFID and privacy - Some industry perspectives (ICC, EICTA) Jeroen Terstegge ICC, EICTA OECD, Paris 2005-10-05 Identification Technologies: Connecting PEOPLE to Information, Entertainment and Services.
Internet 2020: The Next Billion Users
 Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Report to Congress regarding the Terrorism Information Awareness Program
 Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
THE UNIVERSITY OF AUCKLAND INTELLECTUAL PROPERTY CREATED BY STAFF AND STUDENTS POLICY Organisation & Governance
 THE UNIVERSITY OF AUCKLAND INTELLECTUAL PROPERTY CREATED BY STAFF AND STUDENTS POLICY Organisation & Governance 1. INTRODUCTION AND OBJECTIVES 1.1 This policy seeks to establish a framework for managing
THE UNIVERSITY OF AUCKLAND INTELLECTUAL PROPERTY CREATED BY STAFF AND STUDENTS POLICY Organisation & Governance 1. INTRODUCTION AND OBJECTIVES 1.1 This policy seeks to establish a framework for managing
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA Health Insurance Portability and Accountability Act (HIPAA)
 Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
About the Office of the Australian Information Commissioner
 Australian Government Office of the Australian Information Commissioner www.oaic.gov.au GPO Box 5218 Sydney NSW 2001 P +61 2 9284 9800 F +61 2 9284 9666 E enquiries@oaic.gov.au Enquiries 1300 363 992 TTY
Australian Government Office of the Australian Information Commissioner www.oaic.gov.au GPO Box 5218 Sydney NSW 2001 P +61 2 9284 9800 F +61 2 9284 9666 E enquiries@oaic.gov.au Enquiries 1300 363 992 TTY
Ethical and social aspects of management information systems
 Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
Ethical and social aspects of management Marcos Sanches Commerce Électronique The challenge Why are contemporary and the Internet a challenge for the protection of privacy and intellectual property? How
IN THE MATTER OF 2013 SPECIAL 301 REVIEW: IDENTIFICATION OF COUNTRIES UNDER SECTION 182 OF THE TRADE ACT OF Docket No.
 IN THE MATTER OF 2013 SPECIAL 301 REVIEW: IDENTIFICATION OF COUNTRIES UNDER SECTION 182 OF THE TRADE ACT OF 1974 Docket No. USTR - 2012-0022 COMMENTS OF PUBLIC KNOWLEDGE Public Knowledge (PK) appreciates
IN THE MATTER OF 2013 SPECIAL 301 REVIEW: IDENTIFICATION OF COUNTRIES UNDER SECTION 182 OF THE TRADE ACT OF 1974 Docket No. USTR - 2012-0022 COMMENTS OF PUBLIC KNOWLEDGE Public Knowledge (PK) appreciates
Establishing a Development Agenda for the World Intellectual Property Organization
 1 Establishing a Development Agenda for the World Intellectual Property Organization to be submitted by Brazil and Argentina to the 40 th Series of Meetings of the Assemblies of the Member States of WIPO
1 Establishing a Development Agenda for the World Intellectual Property Organization to be submitted by Brazil and Argentina to the 40 th Series of Meetings of the Assemblies of the Member States of WIPO
DIMACS/PORTIA Workshop on Privacy Preserving
 DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
Understanding the role governments and industry organizations play in RFID adoption. Mark Roberti, Founder & Editor, RFID Journal
 Understanding the role governments and industry organizations play in RFID adoption Mark Roberti, Founder & Editor, RFID Journal Regulations for spectrum allocation RFID standards development organizations
Understanding the role governments and industry organizations play in RFID adoption Mark Roberti, Founder & Editor, RFID Journal Regulations for spectrum allocation RFID standards development organizations
THE LABORATORY ANIMAL BREEDERS ASSOCIATION OF GREAT BRITAIN
 THE LABORATORY ANIMAL BREEDERS ASSOCIATION OF GREAT BRITAIN www.laba-uk.com Response from Laboratory Animal Breeders Association to House of Lords Inquiry into the Revision of the Directive on the Protection
THE LABORATORY ANIMAL BREEDERS ASSOCIATION OF GREAT BRITAIN www.laba-uk.com Response from Laboratory Animal Breeders Association to House of Lords Inquiry into the Revision of the Directive on the Protection
Updating Data Protection: Part I -- Identifying the Objectives
 Maurer School of Law: Indiana University Digital Repository @ Maurer Law Articles by Maurer Faculty Faculty Scholarship 2009 Updating Data Protection: Part I -- Identifying the Objectives Fred H. Cate
Maurer School of Law: Indiana University Digital Repository @ Maurer Law Articles by Maurer Faculty Faculty Scholarship 2009 Updating Data Protection: Part I -- Identifying the Objectives Fred H. Cate
Latin-American non-state actor dialogue on Article 6 of the Paris Agreement
 Latin-American non-state actor dialogue on Article 6 of the Paris Agreement Summary Report Organized by: Regional Collaboration Centre (RCC), Bogota 14 July 2016 Supported by: Background The Latin-American
Latin-American non-state actor dialogue on Article 6 of the Paris Agreement Summary Report Organized by: Regional Collaboration Centre (RCC), Bogota 14 July 2016 Supported by: Background The Latin-American
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION
 28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
#Renew2030. Boulevard A Reyers 80 B1030 Brussels Belgium
 #Renew2030 Boulevard A Reyers 80 B1030 Brussels Belgium secretariat@orgalim.eu +32 2 206 68 83 @Orgalim_EU www.orgalim.eu SHAPING A FUTURE THAT S GOOD. Orgalim is registered under the European Union Transparency
#Renew2030 Boulevard A Reyers 80 B1030 Brussels Belgium secretariat@orgalim.eu +32 2 206 68 83 @Orgalim_EU www.orgalim.eu SHAPING A FUTURE THAT S GOOD. Orgalim is registered under the European Union Transparency
The Game Changer: Privacy by Design
 WHITE PAPER Dr. Ann Cavoukian, Privacy by Design Centre of Excellence, on leading with privacy by design The Game Changer: Privacy by Design Data Security: Cost of Taking the Reactive Approach CONTENTS
WHITE PAPER Dr. Ann Cavoukian, Privacy by Design Centre of Excellence, on leading with privacy by design The Game Changer: Privacy by Design Data Security: Cost of Taking the Reactive Approach CONTENTS
Lesli K. Johnson Licensed Psychologist Licensed Independent Social Worker 17 Blue Line Drive Athens, Ohio (740)
 Lesli K. Johnson Licensed Psychologist Licensed Independent Social Worker 17 Blue Line Drive Athens, Ohio 45701 (740) 592-5689 I provide psychological services to children, adults, families and couples.
Lesli K. Johnson Licensed Psychologist Licensed Independent Social Worker 17 Blue Line Drive Athens, Ohio 45701 (740) 592-5689 I provide psychological services to children, adults, families and couples.
Interoperable systems that are trusted and secure
 Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Government managers have critical needs for models and tools to shape, manage, and evaluate 21st century services. These needs present research opportunties for both information and social scientists,
Refining foresight approaches to crisis, inertia and transition
 Refining foresight approaches to crisis, inertia and transition 25-27 April 2017 Aalto University, Espoo, Finland Jennifer Cassingena Harper, Malta Council for Science and Technology This presentation
Refining foresight approaches to crisis, inertia and transition 25-27 April 2017 Aalto University, Espoo, Finland Jennifer Cassingena Harper, Malta Council for Science and Technology This presentation
ITI Comment Submission to USTR Negotiating Objectives for a U.S.-Japan Trade Agreement
 ITI Comment Submission to USTR-2018-0034 Negotiating Objectives for a U.S.-Japan Trade Agreement DECEMBER 3, 2018 Introduction The Information Technology Industry Council (ITI) welcomes the opportunity
ITI Comment Submission to USTR-2018-0034 Negotiating Objectives for a U.S.-Japan Trade Agreement DECEMBER 3, 2018 Introduction The Information Technology Industry Council (ITI) welcomes the opportunity
Cyber Risks in Additive Manufacturing Threaten to Unravel the Digital Thread
 SPOTLIGHT / COMMENTARY / FEATURE Cyber Risks in Additive Manufacturing Threaten to Unravel the Digital Thread By Simon Goldenberg and Mark Cotteleer Wherever data and information are transmitted, used,
SPOTLIGHT / COMMENTARY / FEATURE Cyber Risks in Additive Manufacturing Threaten to Unravel the Digital Thread By Simon Goldenberg and Mark Cotteleer Wherever data and information are transmitted, used,
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy?
 Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Ensuring Adequate Policies and Resources for the 2020 Census
 Ensuring Adequate Policies and Resources for the 2020 Census Background The census is one of the most important elements of U.S. democracy. Article I, Section 2, Clause 3 of the U.S. Constitution mandates
Ensuring Adequate Policies and Resources for the 2020 Census Background The census is one of the most important elements of U.S. democracy. Article I, Section 2, Clause 3 of the U.S. Constitution mandates
Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the
 Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the U. S. Senate Committee on Commerce, Science, and Transportation Subcommittee
Testimony of Professor Lance J. Hoffman Computer Science Department The George Washington University Washington, D.C. Before the U. S. Senate Committee on Commerce, Science, and Transportation Subcommittee
Compendium Overview. By John Hagel and John Seely Brown
 Compendium Overview By John Hagel and John Seely Brown Over four years ago, we began to discern a new technology discontinuity on the horizon. At first, it came in the form of XML (extensible Markup Language)
Compendium Overview By John Hagel and John Seely Brown Over four years ago, we began to discern a new technology discontinuity on the horizon. At first, it came in the form of XML (extensible Markup Language)
Lawyers sued over advice to board
 Lawyers sued over advice to board Misrepresentation, negligence Publicly held company Number of employees Over 1,000 Approximately $2 billion A large public company misstated its revenue during three quarters
Lawyers sued over advice to board Misrepresentation, negligence Publicly held company Number of employees Over 1,000 Approximately $2 billion A large public company misstated its revenue during three quarters
Hong Kong Personal Data Protection Regulatory Framework From Compliance to Accountability
 Legal Week s Corporate Counsel Forum 2016 Renaissance Harbour View Hotel 23 June 2016 Hong Kong Personal Data Protection Regulatory Framework From Compliance to Accountability Stephen Kai-yi Wong Privacy
Legal Week s Corporate Counsel Forum 2016 Renaissance Harbour View Hotel 23 June 2016 Hong Kong Personal Data Protection Regulatory Framework From Compliance to Accountability Stephen Kai-yi Wong Privacy
Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology
 Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology Edited by Mireille Hildebrandt and Katja de Vries New York, New York, Routledge, 2013, ISBN 978-0-415-64481-5
Privacy, Due Process and the Computational Turn: The philosophy of law meets the philosophy of technology Edited by Mireille Hildebrandt and Katja de Vries New York, New York, Routledge, 2013, ISBN 978-0-415-64481-5
Enforcement of Intellectual Property Rights Frequently Asked Questions
 EUROPEAN COMMISSION MEMO Brussels/Strasbourg, 1 July 2014 Enforcement of Intellectual Property Rights Frequently Asked Questions See also IP/14/760 I. EU Action Plan on enforcement of Intellectual Property
EUROPEAN COMMISSION MEMO Brussels/Strasbourg, 1 July 2014 Enforcement of Intellectual Property Rights Frequently Asked Questions See also IP/14/760 I. EU Action Plan on enforcement of Intellectual Property
Know Your Community. Predict & Mitigate Risk. Social Unrest: Analysis, Monitoring and Developing Effective Countermeasures
 Social Unrest: Analysis, Monitoring and Developing Effective Countermeasures Knowing and Influencing Societies to Shape Security Environments ENODO Global, Inc. October 2014 Know Your Community. Predict
Social Unrest: Analysis, Monitoring and Developing Effective Countermeasures Knowing and Influencing Societies to Shape Security Environments ENODO Global, Inc. October 2014 Know Your Community. Predict
The ALA and ARL Position on Access and Digital Preservation: A Response to the Section 108 Study Group
 The ALA and ARL Position on Access and Digital Preservation: A Response to the Section 108 Study Group Introduction In response to issues raised by initiatives such as the National Digital Information
The ALA and ARL Position on Access and Digital Preservation: A Response to the Section 108 Study Group Introduction In response to issues raised by initiatives such as the National Digital Information
Dr. Binod Mishra Department of Humanities & Social Sciences Indian Institute of Technology, Roorkee. Lecture 16 Negotiation Skills
 Dr. Binod Mishra Department of Humanities & Social Sciences Indian Institute of Technology, Roorkee Lecture 16 Negotiation Skills Good morning, in the previous lectures we talked about the importance of
Dr. Binod Mishra Department of Humanities & Social Sciences Indian Institute of Technology, Roorkee Lecture 16 Negotiation Skills Good morning, in the previous lectures we talked about the importance of
LAB3-R04 A Hard Privacy Impact Assessment. Post conference summary
 LAB3-R04 A Hard Privacy Impact Assessment Post conference summary John Elliott Joanne Furtsch @withoutfire @PrivacyGeek Table of Contents THANK YOU... 3 WHAT IS PRIVACY?... 3 The European Perspective...
LAB3-R04 A Hard Privacy Impact Assessment Post conference summary John Elliott Joanne Furtsch @withoutfire @PrivacyGeek Table of Contents THANK YOU... 3 WHAT IS PRIVACY?... 3 The European Perspective...
RBI Working Group report on FinTech: Key themes
 www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
Consenting Agents: Semi-Autonomous Interactions for Ubiquitous Consent
 Consenting Agents: Semi-Autonomous Interactions for Ubiquitous Consent Richard Gomer r.gomer@soton.ac.uk m.c. schraefel mc@ecs.soton.ac.uk Enrico Gerding eg@ecs.soton.ac.uk University of Southampton SO17
Consenting Agents: Semi-Autonomous Interactions for Ubiquitous Consent Richard Gomer r.gomer@soton.ac.uk m.c. schraefel mc@ecs.soton.ac.uk Enrico Gerding eg@ecs.soton.ac.uk University of Southampton SO17
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT. 15 May :00-21:00
 DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
Growing Positive Perceptions DIFFERENTIATION. Creating Wants
 101 MARKETING MOMENTS S E C T I O N 8 DIFFERENTIATION R E L A T I O N S H I P P H A S E C L I E N T S B U Y I N G P R O C E S S Growing Positive Perceptions P R O F E S S I O N A L S S E L L I N G P R
101 MARKETING MOMENTS S E C T I O N 8 DIFFERENTIATION R E L A T I O N S H I P P H A S E C L I E N T S B U Y I N G P R O C E S S Growing Positive Perceptions P R O F E S S I O N A L S S E L L I N G P R
Global Standards Symposium. Security, privacy and trust in standardisation. ICDPPC Chair John Edwards. 24 October 2016
 Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
Global Standards Symposium Security, privacy and trust in standardisation ICDPPC Chair John Edwards 24 October 2016 CANCUN DECLARATION At the OECD Ministerial Meeting on the Digital Economy in Cancun in
the Companies and Intellectual Property Commission of South Africa (CIPC)
 organized by the Companies and Intellectual Property Commission of South Africa (CIPC) the World Intellectual Property Organization (WIPO) the International Criminal Police Organization (INTERPOL) the
organized by the Companies and Intellectual Property Commission of South Africa (CIPC) the World Intellectual Property Organization (WIPO) the International Criminal Police Organization (INTERPOL) the
Wireless Environments & Privacy
 Wireless Environments & Privacy Patricia S. Taylor Eastern Illinois University & Robert E. McGrath NCSA, University of Illinois EDRA Vancouver, BC -- May 2005 Introduction Views from a Social Scientist
Wireless Environments & Privacy Patricia S. Taylor Eastern Illinois University & Robert E. McGrath NCSA, University of Illinois EDRA Vancouver, BC -- May 2005 Introduction Views from a Social Scientist
GUIDE TO SPEAKING POINTS:
 GUIDE TO SPEAKING POINTS: The following presentation includes a set of speaking points that directly follow the text in the slide. The deck and speaking points can be used in two ways. As a learning tool
GUIDE TO SPEAKING POINTS: The following presentation includes a set of speaking points that directly follow the text in the slide. The deck and speaking points can be used in two ways. As a learning tool
Q1 Under the subject "Future of Work and the New Economy", which topics do you find important?
 Q1 Under the subject "Future of Work and the New Economy", which topics do you find important? Answered: 78 Skipped: 5 How can the Internet be... structure... Will the lack of security... How will domestic...
Q1 Under the subject "Future of Work and the New Economy", which topics do you find important? Answered: 78 Skipped: 5 How can the Internet be... structure... Will the lack of security... How will domestic...
Quality assurance in the supply chain for pharmaceuticals from the WHO perspective
 1 Quality assurance in the supply chain for pharmaceuticals from the WHO perspective Dr Sabine Kopp Quality Assurance and Safety: Medicines Medicines Policy and Standards World Health Organization Presentation
1 Quality assurance in the supply chain for pharmaceuticals from the WHO perspective Dr Sabine Kopp Quality Assurance and Safety: Medicines Medicines Policy and Standards World Health Organization Presentation
SUSTAINABILITY MATERIALITY OVERVIEW
 SUSTAINABILITY MATERIALITY OVERVIEW EMC undertakes materiality assessments to identify and prioritize sustainability factors for the purposes of deciding where to focus our resources, setting goals, and
SUSTAINABILITY MATERIALITY OVERVIEW EMC undertakes materiality assessments to identify and prioritize sustainability factors for the purposes of deciding where to focus our resources, setting goals, and
Energy Trade and Transportation: Conscious Parallelism
 Energy Trade and Transportation: Conscious Parallelism DRAFT Speech by Carmen Dybwad, Board Member, National Energy Board to the IAEE North American Conference Mexico City October 20, 2003 Introduction
Energy Trade and Transportation: Conscious Parallelism DRAFT Speech by Carmen Dybwad, Board Member, National Energy Board to the IAEE North American Conference Mexico City October 20, 2003 Introduction
TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH
 PROGRAM OVERVIEW TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH 02 03 04 05 07 1 WHERE ENTREPRENEURS AND POLICY LEADERS COME TOGETHER. BUSINESS INSPIRES AND
PROGRAM OVERVIEW TABLE OF CONTENTS OUR MISSION OUR MEMBERS OUR PLAN C_TEC S PRIORITIES WORDSMITH + BLACKSMITH 02 03 04 05 07 1 WHERE ENTREPRENEURS AND POLICY LEADERS COME TOGETHER. BUSINESS INSPIRES AND
Session 1, Part 2: Emerging issues in e-commerce Australian experiences of privacy and consumer protection regulation
 2013/ SOM3/CTI/WKSP1/007 Australian Experiences of Privacy and Consumer Protection Regulation Submitted by: Australia Workshop on Building and Enhancing FTA Negotiation Skills on e-commerce Medan, Indonesia
2013/ SOM3/CTI/WKSP1/007 Australian Experiences of Privacy and Consumer Protection Regulation Submitted by: Australia Workshop on Building and Enhancing FTA Negotiation Skills on e-commerce Medan, Indonesia
ADDENDUM D COMERICA WEB INVOICING TERMS AND CONDITIONS
 Effective 08/15/2013 ADDENDUM D COMERICA WEB INVOICING TERMS AND CONDITIONS This Addendum D is incorporated by this reference into the Comerica Web Banking Terms and Conditions ( Terms ). Capitalized terms
Effective 08/15/2013 ADDENDUM D COMERICA WEB INVOICING TERMS AND CONDITIONS This Addendum D is incorporated by this reference into the Comerica Web Banking Terms and Conditions ( Terms ). Capitalized terms
RFID: Applications, Security, and Privacy
 RFID: Applications, Security, and Privacy Simson Garfinkel, Beth Rosenberg Click here if your download doesn"t start automatically RFID: Applications, Security, and Privacy Simson Garfinkel, Beth Rosenberg
RFID: Applications, Security, and Privacy Simson Garfinkel, Beth Rosenberg Click here if your download doesn"t start automatically RFID: Applications, Security, and Privacy Simson Garfinkel, Beth Rosenberg
Regulatory Aspects of Smart Metering: United States Experience
 Regulatory Aspects of Smart Metering: United States Experience Joint Licensing/Competition Committee and Tariff/Pricing Committee Meeting Tbilisi, Georgia February 14, 2011 Presented by: Diane Ramthun
Regulatory Aspects of Smart Metering: United States Experience Joint Licensing/Competition Committee and Tariff/Pricing Committee Meeting Tbilisi, Georgia February 14, 2011 Presented by: Diane Ramthun
Robert Bond Partner, Commercial/IP/IT
 Using Privacy Impact Assessments Effectively robert.bond@bristows.com Robert Bond Partner, Commercial/IP/IT BA (Hons) Law, Wolverhampton University Qualified as a Solicitor 1979 Qualified as a Notary Public
Using Privacy Impact Assessments Effectively robert.bond@bristows.com Robert Bond Partner, Commercial/IP/IT BA (Hons) Law, Wolverhampton University Qualified as a Solicitor 1979 Qualified as a Notary Public
IMPORTANT ASPECTS OF DATA MINING & DATA PRIVACY ISSUES. K.P Jayant, Research Scholar JJT University Rajasthan
 IMPORTANT ASPECTS OF DATA MINING & DATA PRIVACY ISSUES K.P Jayant, Research Scholar JJT University Rajasthan ABSTRACT It has made the world a smaller place and has opened up previously inaccessible markets
IMPORTANT ASPECTS OF DATA MINING & DATA PRIVACY ISSUES K.P Jayant, Research Scholar JJT University Rajasthan ABSTRACT It has made the world a smaller place and has opened up previously inaccessible markets
Scenario Development Process
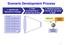 Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Privacy in a changing society
 Privacy in a changing society Concepts of privacy are evolving r a p i d ly i n t o d ay s w o r l d, a n d s o a r e t h e f a c t o r s t h at a r e emerging to threaten it. Who are we What are telling
Privacy in a changing society Concepts of privacy are evolving r a p i d ly i n t o d ay s w o r l d, a n d s o a r e t h e f a c t o r s t h at a r e emerging to threaten it. Who are we What are telling
TECHNOLOGICAL SOLUTIONS FOR A SUSTAINABLE FUTURE Building Smart Cities
 TECHNOLOGICAL SOLUTIONS FOR A SUSTAINABLE FUTURE Building Smart Cities FME in figures 21 BILLION EUROS OF ADDED VALUE 2,200 MEMBER COMPANIES 2 60 AFFILIATED TRADE ASSOCIATIONS 220,000 EMPLOYEES EXPORTS
TECHNOLOGICAL SOLUTIONS FOR A SUSTAINABLE FUTURE Building Smart Cities FME in figures 21 BILLION EUROS OF ADDED VALUE 2,200 MEMBER COMPANIES 2 60 AFFILIATED TRADE ASSOCIATIONS 220,000 EMPLOYEES EXPORTS
LEGAL TRANSFORMATION STUDY
 LEGAL TRANSFORMATION STUDY EXECUTIVE SUMMARY YOUR 2020 VISION OF THE FUTURE Legal Transformation Study 1 Fast Forward The year is 2020. Imagine where you will be and what you will be doing. Perhaps in
LEGAL TRANSFORMATION STUDY EXECUTIVE SUMMARY YOUR 2020 VISION OF THE FUTURE Legal Transformation Study 1 Fast Forward The year is 2020. Imagine where you will be and what you will be doing. Perhaps in
CSCM World Congress on CBRNe Science and Consequence Management. Remarks by Ahmet Üzümcü, Director-General OPCW. Monday 2 June 2014 Tbilisi, Georgia
 1 CSCM World Congress on CBRNe Science and Consequence Management Remarks by Ahmet Üzümcü, Director-General OPCW Monday 2 June 2014 Tbilisi, Georgia H.E. the Minister of Internal Affairs, H.E. the Minister
1 CSCM World Congress on CBRNe Science and Consequence Management Remarks by Ahmet Üzümcü, Director-General OPCW Monday 2 June 2014 Tbilisi, Georgia H.E. the Minister of Internal Affairs, H.E. the Minister
Ling/CSE 472: Introduction to Computational Linguistics. 5/25/17 Ethics & NLP 1
 Ling/CSE 472: Introduction to Computational Linguistics 5/25/17 Ethics & NLP 1 Overview Why ethics and NLP? Value Sensitive Design & Value Scenarios Envisioning Cards Reading Questions Why Ethics in NLP?
Ling/CSE 472: Introduction to Computational Linguistics 5/25/17 Ethics & NLP 1 Overview Why ethics and NLP? Value Sensitive Design & Value Scenarios Envisioning Cards Reading Questions Why Ethics in NLP?
Challenges and opportunities of digital social research: Access and Anonymity
 Challenges and opportunities of digital social research: Access and Anonymity Dr. Dan Nunan Henley Business School, University of Reading www.henley.ac.uk Two narratives for social research: Evolution
Challenges and opportunities of digital social research: Access and Anonymity Dr. Dan Nunan Henley Business School, University of Reading www.henley.ac.uk Two narratives for social research: Evolution
FUNDING DUE DILIGENCE WHAT YOUR INVESTORS NEED YOU TO KNOW ABOUT COMPLIANCE. May 26, 2010
 FUNDING DUE DILIGENCE WHAT YOUR INVESTORS NEED YOU TO KNOW ABOUT COMPLIANCE May 26, 2010 Attorney Advertising Prior results do not guarantee a similar outcome Models used are not clients but may be representative
FUNDING DUE DILIGENCE WHAT YOUR INVESTORS NEED YOU TO KNOW ABOUT COMPLIANCE May 26, 2010 Attorney Advertising Prior results do not guarantee a similar outcome Models used are not clients but may be representative
Gender pay gap reporting tight for time
 People Advisory Services Gender pay gap reporting tight for time March 2018 Contents Introduction 01 Insights into emerging market practice 02 Timing of reporting 02 What do employers tell us about their
People Advisory Services Gender pay gap reporting tight for time March 2018 Contents Introduction 01 Insights into emerging market practice 02 Timing of reporting 02 What do employers tell us about their
Protection of Privacy Policy
 Protection of Privacy Policy Policy No. CIMS 006 Version No. 1.0 City Clerk's Office An Information Management Policy Subject: Protection of Privacy Policy Keywords: Information management, privacy, breach,
Protection of Privacy Policy Policy No. CIMS 006 Version No. 1.0 City Clerk's Office An Information Management Policy Subject: Protection of Privacy Policy Keywords: Information management, privacy, breach,
Programs for Academic and. Research Institutions
 Programs for Academic and Research Institutions Awards & Recognition #1 for Patent Litigation Corporate Counsel, 2004-2014 IP Litigation Department of the Year Finalist The American Lawyer, 2014 IP Litigation
Programs for Academic and Research Institutions Awards & Recognition #1 for Patent Litigation Corporate Counsel, 2004-2014 IP Litigation Department of the Year Finalist The American Lawyer, 2014 IP Litigation
Ethics Guideline for the Intelligent Information Society
 Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
CBD Request to WIPO on the Interrelation of Access to Genetic Resources and Disclosure Requirements
 CBD Request to WIPO on the Interrelation of Access to Genetic Resources and Disclosure Requirements Establishing an adequate framework for a WIPO Response 1 Table of Contents I. Introduction... 1 II. Supporting
CBD Request to WIPO on the Interrelation of Access to Genetic Resources and Disclosure Requirements Establishing an adequate framework for a WIPO Response 1 Table of Contents I. Introduction... 1 II. Supporting
