DHANALAKSHMI COLLEGE OF ENGINEERING, CHENNAI
|
|
|
- Beverly Parsons
- 5 years ago
- Views:
Transcription
1 DHANALAKSHMI COLLEGE OF ENGINEERING, CHENNAI Department of Computer Science and Engineering CS6503 THEORY OF COMPUTATION 2 Mark Questions & Answers Year / Semester: III / V Regulation: 2013 Academic year:
2 Q is a finite set of states. q0 in Q is called start state. F is the set of final states. 2. What is a Turning Machine? A finite state machine with storage is called as Turing Machine. Turing machine is a simple mathematical model of a computer. TM has unlimited and unrestricted memory and is a much more accurate model of a general purpose computer. The Turing machine is a FA with an R/W Head. It has an infinite tape divided into cells, each cell holding one symbol. 3. What are the special features of TM? In one move, TM depending upon the symbol scanned by the tape head and state of the finite control listed as below: 1. Changes state 2. Prints a symbol on the scanned tape cell
3 3. Moves the R/w head left or right 4. What is multiple tracks Turing machine? A Turing Machine in which the input tape is divided into multiple tracks where each track is having different inputs is called multiple tracks Turing machine. 5. What is a multidimensional Turing machine? The Turing Machine which has the useful finite control consists of a k-dimensional array of cells in all 2K directions for some fixed K in a tape cell. Depending on the state and symbol scanned, the device changes state, prints a new symbol and moves its tape head in one of 2K directions, along one of the K axes. 6. Differentiate 2-way FA from TM. Turing machine can change symbols on its tape, whereas the FA cannot change symbols on tape. Also TM has a tape head that moves both left and right side, whereas the FA doesn t have such a tape head. on of TM symbol or the symbol to the left of the head, whichever is the rightmost. 8.What are the applications of TM? TM can be used as: 1. Recognizers of languages 2. Computers of functions on non negative integers 3. Generating devices 9.What is off-line Turing machine?
4 An Off-line Turing Machine is a multitape TM whose input tape is read only. The Turing Machine is not allowed to move the input tape head off the region between left and right end markers. 10.When is a function f said to be Turing computable? (N/D-09) A Turing Machine defines a function y = f(x) for strings x,y *, if q0 x --* qfy. A function f is Turing Computable if there exists a Turing Machine that performs a specific function. 11.List out the various representation of TM. We can describe TM using: 7. Instantaneous description 8. Transition table 9. Transition diagram 12.List out the techniques for Turing machine construction. The various techniques used for Turing Machine construction are as follows: 1. Storage in finite control 2. Multiple tracks 3. Checking off symbols 4. Shifting over 5. Subroutines 13. What are UTMs or Universal Turing machines? (N/D-13) Universal TMs are TMs that can be programmed to solve any problem that can be solved by any Turing machine. A specific Universal Turing machine U is Input to U: The encoding M of a Tm M and encoding w of a string w. Behavior: U halts on input M w if and only if M halts on input w.
5 14. State the halting problem of Turing Machine. The halting problem for TMs is: Given any Turing Machine M and an input string w, does M halt on w? This problem is undecidable as there is no algorithm to solve this problem. 15. What is the weak-form of Turing thesis? A Turing Machine can compute anything that can be computed by a general purpose digital computer which is said to be a weak form of Turing thesis. 16. State the usage of checking off symbol in TM. (N/D-09) Checking off symbols is useful method when a TM recognizes a language with repeated strings and also to compare the length of substrings. (eg) : { ww w * } or {a i b i i>=1}. This is implemented by using an extra track on the 17. How can a TM used as a transducer? A TM can be used as a transducer. The most obvious way to do this is to treat the entire nonblank portion of the initial tape as input, and to treat the entire blank portion of the tape when the machine halts as output. Or a TM defines a function y=f(x) for strings x,y * if: q0x --- qfy, where qf is the final state.mathematical concepts and the real
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Technical framework of Operating System using Turing Machines
 Reviewed Paper Technical framework of Operating System using Turing Machines Paper ID IJIFR/ V2/ E2/ 028 Page No 465-470 Subject Area Computer Science Key Words Turing, Undesirability, Complexity, Snapshot
Reviewed Paper Technical framework of Operating System using Turing Machines Paper ID IJIFR/ V2/ E2/ 028 Page No 465-470 Subject Area Computer Science Key Words Turing, Undesirability, Complexity, Snapshot
Automata and Formal Languages - CM0081 Turing Machines
 Automata and Formal Languages - CM0081 Turing Machines Andrés Sicard-Ramírez Universidad EAFIT Semester 2018-1 Turing Machines Alan Mathison Turing (1912 1954) Automata and Formal Languages - CM0081. Turing
Automata and Formal Languages - CM0081 Turing Machines Andrés Sicard-Ramírez Universidad EAFIT Semester 2018-1 Turing Machines Alan Mathison Turing (1912 1954) Automata and Formal Languages - CM0081. Turing
Computability. What can be computed?
 Computability What can be computed? Computability What can be computed? read/write tape 0 1 1 0 control Computability What can be computed? read/write tape 0 1 1 0 control Computability What can be computed?
Computability What can be computed? Computability What can be computed? read/write tape 0 1 1 0 control Computability What can be computed? read/write tape 0 1 1 0 control Computability What can be computed?
Turing Machines (TM)
 1 Introduction Turing Machines (TM) Jay Bagga A Turing Machine (TM) is a powerful model which represents a general purpose computer. The Church-Turing thesis states that our intuitive notion of algorithms
1 Introduction Turing Machines (TM) Jay Bagga A Turing Machine (TM) is a powerful model which represents a general purpose computer. The Church-Turing thesis states that our intuitive notion of algorithms
Oracle Turing Machine. Kaixiang Wang
 Oracle Turing Machine Kaixiang Wang Pre-background: What is Turing machine Oracle Turing Machine Definition Function Complexity Why Oracle Turing Machine is important Application of Oracle Turing Machine
Oracle Turing Machine Kaixiang Wang Pre-background: What is Turing machine Oracle Turing Machine Definition Function Complexity Why Oracle Turing Machine is important Application of Oracle Turing Machine
of the hypothesis, but it would not lead to a proof. P 1
 Church-Turing thesis The intuitive notion of an effective procedure or algorithm has been mentioned several times. Today the Turing machine has become the accepted formalization of an algorithm. Clearly
Church-Turing thesis The intuitive notion of an effective procedure or algorithm has been mentioned several times. Today the Turing machine has become the accepted formalization of an algorithm. Clearly
Implementation of Recursively Enumerable Languages in Universal Turing Machine
 Implementation of Recursively Enumerable Languages in Universal Turing Machine Sumitha C.H, Member, ICMLC and Krupa Ophelia Geddam Abstract This paper presents the design and working of a Universal Turing
Implementation of Recursively Enumerable Languages in Universal Turing Machine Sumitha C.H, Member, ICMLC and Krupa Ophelia Geddam Abstract This paper presents the design and working of a Universal Turing
CDT314 FABER Formal Languages, Automata and Models of Computation MARK BURGIN INDUCTIVE TURING MACHINES
 CDT314 FABER Formal Languages, Automata and Models of Computation MARK BURGIN INDUCTIVE TURING MACHINES 2012 1 Inductive Turing Machines Burgin, M. Inductive Turing Machines, Notices of the Academy of
CDT314 FABER Formal Languages, Automata and Models of Computation MARK BURGIN INDUCTIVE TURING MACHINES 2012 1 Inductive Turing Machines Burgin, M. Inductive Turing Machines, Notices of the Academy of
CITS2211 Discrete Structures Turing Machines
 CITS2211 Discrete Structures Turing Machines October 23, 2017 Highlights We have seen that FSMs and PDAs are surprisingly powerful But there are some languages they can not recognise We will study a new
CITS2211 Discrete Structures Turing Machines October 23, 2017 Highlights We have seen that FSMs and PDAs are surprisingly powerful But there are some languages they can not recognise We will study a new
CSCI3390-Lecture 8: Undecidability of a special case of the tiling problem
 CSCI3390-Lecture 8: Undecidability of a special case of the tiling problem February 16, 2016 Here we show that the constrained tiling problem from the last lecture (tiling the first quadrant with a designated
CSCI3390-Lecture 8: Undecidability of a special case of the tiling problem February 16, 2016 Here we show that the constrained tiling problem from the last lecture (tiling the first quadrant with a designated
Tiling Problems. This document supersedes the earlier notes posted about the tiling problem. 1 An Undecidable Problem about Tilings of the Plane
 Tiling Problems This document supersedes the earlier notes posted about the tiling problem. 1 An Undecidable Problem about Tilings of the Plane The undecidable problems we saw at the start of our unit
Tiling Problems This document supersedes the earlier notes posted about the tiling problem. 1 An Undecidable Problem about Tilings of the Plane The undecidable problems we saw at the start of our unit
Enhanced Turing Machines
 Enhanced Turing Machines Lecture 28 Sections 10.1-10.2 Robb T. Koether Hampden-Sydney College Wed, Nov 2, 2016 Robb T. Koether (Hampden-Sydney College) Enhanced Turing Machines Wed, Nov 2, 2016 1 / 21
Enhanced Turing Machines Lecture 28 Sections 10.1-10.2 Robb T. Koether Hampden-Sydney College Wed, Nov 2, 2016 Robb T. Koether (Hampden-Sydney College) Enhanced Turing Machines Wed, Nov 2, 2016 1 / 21
Digital Integrated CircuitDesign
 Digital Integrated CircuitDesign Lecture 13 Building Blocks (Multipliers) Register Adder Shift Register Adib Abrishamifar EE Department IUST Acknowledgement This lecture note has been summarized and categorized
Digital Integrated CircuitDesign Lecture 13 Building Blocks (Multipliers) Register Adder Shift Register Adib Abrishamifar EE Department IUST Acknowledgement This lecture note has been summarized and categorized
Computing Permutations with Stacks and Deques
 Michael Albert 1 Mike Atkinson 1 Steve Linton 2 1 Department of Computer Science, University of Otago 2 School of Computer Science, University of St Andrews 7th Australia New Zealand Mathematics Convention
Michael Albert 1 Mike Atkinson 1 Steve Linton 2 1 Department of Computer Science, University of Otago 2 School of Computer Science, University of St Andrews 7th Australia New Zealand Mathematics Convention
Midterm for Name: Good luck! Midterm page 1 of 9
 Midterm for 6.864 Name: 40 30 30 30 Good luck! 6.864 Midterm page 1 of 9 Part #1 10% We define a PCFG where the non-terminals are {S, NP, V P, V t, NN, P P, IN}, the terminal symbols are {Mary,ran,home,with,John},
Midterm for 6.864 Name: 40 30 30 30 Good luck! 6.864 Midterm page 1 of 9 Part #1 10% We define a PCFG where the non-terminals are {S, NP, V P, V t, NN, P P, IN}, the terminal symbols are {Mary,ran,home,with,John},
Introduction to Computer Engineering. CS/ECE 252, Spring 2013 Prof. Mark D. Hill Computer Sciences Department University of Wisconsin Madison
 Introduction to Computer Engineering CS/ECE 252, Spring 2013 Prof. Mark D. Hill Computer Sciences Department University of Wisconsin Madison Chapter 1 Welcome Aboard Slides based on set prepared by Gregory
Introduction to Computer Engineering CS/ECE 252, Spring 2013 Prof. Mark D. Hill Computer Sciences Department University of Wisconsin Madison Chapter 1 Welcome Aboard Slides based on set prepared by Gregory
Membrane Computing as Multi Turing Machines
 Volume 4 No.8, December 2012 www.ijais.org Membrane Computing as Multi Turing Machines Mahmoud Abdelaziz Amr Badr Ibrahim Farag ABSTRACT A Turing machine (TM) can be adapted to simulate the logic of any
Volume 4 No.8, December 2012 www.ijais.org Membrane Computing as Multi Turing Machines Mahmoud Abdelaziz Amr Badr Ibrahim Farag ABSTRACT A Turing machine (TM) can be adapted to simulate the logic of any
2359 (i.e. 11:59:00 pm) on 4/16/18 via Blackboard
 CS 109: Introduction to Computer Science Goodney Spring 2018 Homework Assignment 4 Assigned: 4/2/18 via Blackboard Due: 2359 (i.e. 11:59:00 pm) on 4/16/18 via Blackboard Notes: a. This is the fourth homework
CS 109: Introduction to Computer Science Goodney Spring 2018 Homework Assignment 4 Assigned: 4/2/18 via Blackboard Due: 2359 (i.e. 11:59:00 pm) on 4/16/18 via Blackboard Notes: a. This is the fourth homework
7/22/14. Lecture Notes. Chapter 1 Welcome Aboard. Introduction to Computing Systems: From Bits and Gates to C and Beyond 2 nd Edition
 Computer Science 210 Computer Systems 1 Lecture Notes Lecture 2 Introduction Credits: Slides adapted from Gregory T. Byrd, North Carolina State University Introduction to Computing Systems: From Bits and
Computer Science 210 Computer Systems 1 Lecture Notes Lecture 2 Introduction Credits: Slides adapted from Gregory T. Byrd, North Carolina State University Introduction to Computing Systems: From Bits and
The Tiling Problem. Nikhil Gopalkrishnan. December 08, 2008
 The Tiling Problem Nikhil Gopalkrishnan December 08, 2008 1 Introduction A Wang tile [12] is a unit square with each edge colored from a finite set of colors Σ. A set S of Wang tiles is said to tile a
The Tiling Problem Nikhil Gopalkrishnan December 08, 2008 1 Introduction A Wang tile [12] is a unit square with each edge colored from a finite set of colors Σ. A set S of Wang tiles is said to tile a
Forward and backward DAWG matching. Slobodan Petrović
 Forward and backward DAWG matching Slobodan Petrović 08.10.2013 Contents Introduction Forward DAWG matching (FDM) Backward DAWG matching (BDM) 2/29 Introduction A DAWG (Directed Acyclic Word Graph) representation
Forward and backward DAWG matching Slobodan Petrović 08.10.2013 Contents Introduction Forward DAWG matching (FDM) Backward DAWG matching (BDM) 2/29 Introduction A DAWG (Directed Acyclic Word Graph) representation
Sequential program, state machine, Concurrent process models
 INSIGHT Sequential program, state machine, Concurrent process models Finite State Machines, or automata, originated in computational theory and mathematical models in support of various fields of bioscience.
INSIGHT Sequential program, state machine, Concurrent process models Finite State Machines, or automata, originated in computational theory and mathematical models in support of various fields of bioscience.
II. Basic Concepts in Display Systems
 Special Topics in Display Technology 1 st semester, 2016 II. Basic Concepts in Display Systems * Reference book: [Display Interfaces] (R. L. Myers, Wiley) 1. Display any system through which ( people through
Special Topics in Display Technology 1 st semester, 2016 II. Basic Concepts in Display Systems * Reference book: [Display Interfaces] (R. L. Myers, Wiley) 1. Display any system through which ( people through
CSCI 2570 Introduction to Nanocomputing
 CSCI 2570 Introduction to Nanocomputing DNA Tiling John E Savage Computing with DNA Prepare oligonucleotides ( program them ) Prepare solution with multiple strings. Only complementary substrings q and
CSCI 2570 Introduction to Nanocomputing DNA Tiling John E Savage Computing with DNA Prepare oligonucleotides ( program them ) Prepare solution with multiple strings. Only complementary substrings q and
Lecture 20 November 13, 2014
 6.890: Algorithmic Lower Bounds: Fun With Hardness Proofs Fall 2014 Prof. Erik Demaine Lecture 20 November 13, 2014 Scribes: Chennah Heroor 1 Overview This lecture completes our lectures on game characterization.
6.890: Algorithmic Lower Bounds: Fun With Hardness Proofs Fall 2014 Prof. Erik Demaine Lecture 20 November 13, 2014 Scribes: Chennah Heroor 1 Overview This lecture completes our lectures on game characterization.
14.2 Limits and Continuity
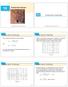 14 Partial Derivatives 14.2 Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Let s compare the behavior of the functions Tables 1 2 show values of f(x,
14 Partial Derivatives 14.2 Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Let s compare the behavior of the functions Tables 1 2 show values of f(x,
CSCE 315: Programming Studio
 CSCE 315: Programming Studio Introduction to Artificial Intelligence Textbook Definitions Thinking like humans What is Intelligence Acting like humans Thinking rationally Acting rationally However, it
CSCE 315: Programming Studio Introduction to Artificial Intelligence Textbook Definitions Thinking like humans What is Intelligence Acting like humans Thinking rationally Acting rationally However, it
CS10: The Beauty and Joy of Computing Lecture #6: Algorithms
 CS10: The Beauty and Joy of Computing Lecture #6: Algorithms In the news: A recently security study suggests that a computer worm that ran rampant several years ago is still running on many machines, including
CS10: The Beauty and Joy of Computing Lecture #6: Algorithms In the news: A recently security study suggests that a computer worm that ran rampant several years ago is still running on many machines, including
One computer theorist s view of cognitive systems
 One computer theorist s view of cognitive systems Jiri Wiedermann Institute of Computer Science, Prague Academy of Sciences of the Czech Republic Partially supported by grant 1ET100300419 Outline 1. The
One computer theorist s view of cognitive systems Jiri Wiedermann Institute of Computer Science, Prague Academy of Sciences of the Czech Republic Partially supported by grant 1ET100300419 Outline 1. The
Final Project: Verify a Sudoku Solution Due Fri Apr 29 (2400 hrs)? Wed May 4 (1200 hrs)? 1
 Final Project: Verify a Sudoku Solution Due Fri Apr 29 (2400 hrs)? Wed May 4 (1200 hrs)? 1 A. Why? A final project is a good way to have students combine topics from the entire semester, to see how they
Final Project: Verify a Sudoku Solution Due Fri Apr 29 (2400 hrs)? Wed May 4 (1200 hrs)? 1 A. Why? A final project is a good way to have students combine topics from the entire semester, to see how they
SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY
 SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY SCHOOL OF COMPUTER SCIENCE AND ENGINEERING DEPARTMENT OF CSE COURSE PLAN Course Code : CS0204 Course Title : Theory of Computation Semester : IV Course
SRM UNIVERSITY FACULTY OF ENGINEERING AND TECHNOLOGY SCHOOL OF COMPUTER SCIENCE AND ENGINEERING DEPARTMENT OF CSE COURSE PLAN Course Code : CS0204 Course Title : Theory of Computation Semester : IV Course
14.4. Tangent Planes. Tangent Planes. Tangent Planes. Tangent Planes. Partial Derivatives. Tangent Planes and Linear Approximations
 14 Partial Derivatives 14.4 and Linear Approximations Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Suppose a surface S has equation z = f(x, y), where
14 Partial Derivatives 14.4 and Linear Approximations Copyright Cengage Learning. All rights reserved. Copyright Cengage Learning. All rights reserved. Suppose a surface S has equation z = f(x, y), where
One-Dimensional Peg Solitaire, and Duotaire
 More Games of No Chance MSRI Publications Volume 42, 2002 One-Dimensional Peg Solitaire, and Duotaire CRISTOPHER MOORE AND DAVID EPPSTEIN Abstract. We solve the problem of one-dimensional Peg Solitaire.
More Games of No Chance MSRI Publications Volume 42, 2002 One-Dimensional Peg Solitaire, and Duotaire CRISTOPHER MOORE AND DAVID EPPSTEIN Abstract. We solve the problem of one-dimensional Peg Solitaire.
Formulas for Primes. Eric Rowland Hofstra University. Eric Rowland Formulas for Primes / 27
 Formulas for Primes Eric Rowland Hofstra University 2018 2 14 Eric Rowland Formulas for Primes 2018 2 14 1 / 27 The sequence of primes 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
Formulas for Primes Eric Rowland Hofstra University 2018 2 14 Eric Rowland Formulas for Primes 2018 2 14 1 / 27 The sequence of primes 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
In the game of Chess a queen can move any number of spaces in any linear direction: horizontally, vertically, or along a diagonal.
 CMPS 12A Introduction to Programming Winter 2013 Programming Assignment 5 In this assignment you will write a java program finds all solutions to the n-queens problem, for 1 n 13. Begin by reading the
CMPS 12A Introduction to Programming Winter 2013 Programming Assignment 5 In this assignment you will write a java program finds all solutions to the n-queens problem, for 1 n 13. Begin by reading the
Overview of Signal Processing
 Overview of Signal Processing Chapter Intended Learning Outcomes: (i) Understand basic terminology in signal processing (ii) Differentiate digital signal processing and analog signal processing (iii) Describe
Overview of Signal Processing Chapter Intended Learning Outcomes: (i) Understand basic terminology in signal processing (ii) Differentiate digital signal processing and analog signal processing (iii) Describe
AC : A TURING MACHINE FOR THE 21ST CENTURY
 AC 2007-745: A TURING MACHINE FOR THE 21ST CENTURY Christopher Carroll, University of Minnesota-Duluth CHRISTOPHER R. CARROLL Christopher R. Carroll earned his academic degrees from Georgia Tech and from
AC 2007-745: A TURING MACHINE FOR THE 21ST CENTURY Christopher Carroll, University of Minnesota-Duluth CHRISTOPHER R. CARROLL Christopher R. Carroll earned his academic degrees from Georgia Tech and from
II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing
 Class Subject Code Subject II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing 1.CONTENT LIST: Introduction to Unit I - Signals and Systems 2. SKILLS ADDRESSED: Listening 3. OBJECTIVE
Class Subject Code Subject II Year (04 Semester) EE6403 Discrete Time Systems and Signal Processing 1.CONTENT LIST: Introduction to Unit I - Signals and Systems 2. SKILLS ADDRESSED: Listening 3. OBJECTIVE
An Aperiodic Tiling from a Dynamical System: An Exposition of An Example of Culik and Kari. S. Eigen J. Navarro V. Prasad
 An Aperiodic Tiling from a Dynamical System: An Exposition of An Example of Culik and Kari S. Eigen J. Navarro V. Prasad These tiles can tile the plane But only Aperiodically Example A (Culik-Kari) Dynamical
An Aperiodic Tiling from a Dynamical System: An Exposition of An Example of Culik and Kari S. Eigen J. Navarro V. Prasad These tiles can tile the plane But only Aperiodically Example A (Culik-Kari) Dynamical
Stencil Pattern. CS 472 Concurrent & Parallel Programming University of Evansville
 Stencil Pattern CS 472 Concurrent & Parallel Programming University of Evansville Selection of slides from CIS 41/51 Introduction to Parallel Computing Department of Computer and Information Science, University
Stencil Pattern CS 472 Concurrent & Parallel Programming University of Evansville Selection of slides from CIS 41/51 Introduction to Parallel Computing Department of Computer and Information Science, University
Halting Problem. Implement HALT? Today. Halt does not exist. Halt and Turing. Another view of proof: diagonalization. P - program I - input.
 Today. Halting Problem. Implement HALT? Finish undecidability. Start counting. HALT (P,I) P - program I - input. Determines if P(I) (P run on I) halts or loops forever. Notice: Need a computer with the
Today. Halting Problem. Implement HALT? Finish undecidability. Start counting. HALT (P,I) P - program I - input. Determines if P(I) (P run on I) halts or loops forever. Notice: Need a computer with the
Overview of Digital Signal Processing
 Overview of Digital Signal Processing Chapter Intended Learning Outcomes: (i) Understand basic terminology in digital signal processing (ii) Differentiate digital signal processing and analog signal processing
Overview of Digital Signal Processing Chapter Intended Learning Outcomes: (i) Understand basic terminology in digital signal processing (ii) Differentiate digital signal processing and analog signal processing
 CMPS 12A Introduction to Programming Programming Assignment 5 In this assignment you will write a Java program that finds all solutions to the n-queens problem, for. Begin by reading the Wikipedia article
CMPS 12A Introduction to Programming Programming Assignment 5 In this assignment you will write a Java program that finds all solutions to the n-queens problem, for. Begin by reading the Wikipedia article
Reflector A Dynamic Manifestation of Turing Machines with Time and Space Complexity Analysis
 Reflector A Dynamic Manifestation of Turing Machines with Time and Space Complexity Analysis Behroz Mirza MS Computing, Shaheed Zulfikar Ali Bhutto Institute of Science and Technology 90 and 100 Clifton
Reflector A Dynamic Manifestation of Turing Machines with Time and Space Complexity Analysis Behroz Mirza MS Computing, Shaheed Zulfikar Ali Bhutto Institute of Science and Technology 90 and 100 Clifton
CS 480: GAME AI TACTIC AND STRATEGY. 5/15/2012 Santiago Ontañón
 CS 480: GAME AI TACTIC AND STRATEGY 5/15/2012 Santiago Ontañón santi@cs.drexel.edu https://www.cs.drexel.edu/~santi/teaching/2012/cs480/intro.html Reminders Check BBVista site for the course regularly
CS 480: GAME AI TACTIC AND STRATEGY 5/15/2012 Santiago Ontañón santi@cs.drexel.edu https://www.cs.drexel.edu/~santi/teaching/2012/cs480/intro.html Reminders Check BBVista site for the course regularly
intentionality Minds and Machines spring 2006 the Chinese room Turing machines digression on Turing machines recitations
 24.09 Minds and Machines intentionality underived: the belief that Fido is a dog the desire for a walk the intention to use Fido to refer to Fido recitations derived: the English sentence Fido is a dog
24.09 Minds and Machines intentionality underived: the belief that Fido is a dog the desire for a walk the intention to use Fido to refer to Fido recitations derived: the English sentence Fido is a dog
1. Functions and set sizes 2. Infinite set sizes. ! Let X,Y be finite sets, f:x!y a function. ! Theorem: If f is injective then X Y.
 2 Today s Topics: CSE 20: Discrete Mathematics for Computer Science Prof. Miles Jones 1. Functions and set sizes 2. 3 4 1. Functions and set sizes! Theorem: If f is injective then Y.! Try and prove yourself
2 Today s Topics: CSE 20: Discrete Mathematics for Computer Science Prof. Miles Jones 1. Functions and set sizes 2. 3 4 1. Functions and set sizes! Theorem: If f is injective then Y.! Try and prove yourself
Outline. In One Slide. LR Parsing. LR Parsing. No Stopping The Parsing! Bottom-Up Parsing. LR(1) Parsing Tables #2
 LR Parsing Bottom-Up Parsing #1 Outline No Stopping The Parsing! Bottom-Up Parsing LR Parsing Shift and Reduce LR(1) Parsing Algorithm LR(1) Parsing Tables #2 In One Slide An LR(1) parser reads tokens
LR Parsing Bottom-Up Parsing #1 Outline No Stopping The Parsing! Bottom-Up Parsing LR Parsing Shift and Reduce LR(1) Parsing Algorithm LR(1) Parsing Tables #2 In One Slide An LR(1) parser reads tokens
Sets. Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, Outline Sets Equality Subset Empty Set Cardinality Power Set
 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, 2012 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) Gazihan Alankuş (Based on original slides by Brahim Hnich
Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) August 6, 2012 Gazihan Alankuş (Based on original slides by Brahim Hnich et al.) Gazihan Alankuş (Based on original slides by Brahim Hnich
A Cryptosystem Based on the Composition of Reversible Cellular Automata
 A Cryptosystem Based on the Composition of Reversible Cellular Automata Adam Clarridge and Kai Salomaa Technical Report No. 2008-549 Queen s University, Kingston, Canada {adam, ksalomaa}@cs.queensu.ca
A Cryptosystem Based on the Composition of Reversible Cellular Automata Adam Clarridge and Kai Salomaa Technical Report No. 2008-549 Queen s University, Kingston, Canada {adam, ksalomaa}@cs.queensu.ca
The KNIME Image Processing Extension User Manual (DRAFT )
 The KNIME Image Processing Extension User Manual (DRAFT ) Christian Dietz and Martin Horn February 6, 2014 1 Contents 1 Introduction 3 1.1 Installation............................ 3 2 Basic Concepts 4
The KNIME Image Processing Extension User Manual (DRAFT ) Christian Dietz and Martin Horn February 6, 2014 1 Contents 1 Introduction 3 1.1 Installation............................ 3 2 Basic Concepts 4
Grandstream Networks, Inc. GWN76XX WiFi Access Points Antenna Radiation Patterns
 Grandstream Networks, Inc. GWN76XX WiFi Access Points Antenna Radiation Patterns Table of Content INTRODUCTION... 3 TERMINOLOGY... 4 TEST ENVIRONMENT... 5 GWN7610 ANTENNA CHARACTERISTICS... 6 Schematic
Grandstream Networks, Inc. GWN76XX WiFi Access Points Antenna Radiation Patterns Table of Content INTRODUCTION... 3 TERMINOLOGY... 4 TEST ENVIRONMENT... 5 GWN7610 ANTENNA CHARACTERISTICS... 6 Schematic
Tac Due: Sep. 26, 2012
 CS 195N 2D Game Engines Andy van Dam Tac Due: Sep. 26, 2012 Introduction This assignment involves a much more complex game than Tic-Tac-Toe, and in order to create it you ll need to add several features
CS 195N 2D Game Engines Andy van Dam Tac Due: Sep. 26, 2012 Introduction This assignment involves a much more complex game than Tic-Tac-Toe, and in order to create it you ll need to add several features
Problem Set pour from the receptacle to a bucket until the bucket is full or the receptacle is empty, whichever happens first,
 Massachusetts Institute of Technology 6.042J/18.062J, Fall 02: Mathematics for Computer Science Professor Albert Meyer and Dr. Radhika Nagpal Problem Set 5 Reading: Week 5 Notes Problem 1. You are given
Massachusetts Institute of Technology 6.042J/18.062J, Fall 02: Mathematics for Computer Science Professor Albert Meyer and Dr. Radhika Nagpal Problem Set 5 Reading: Week 5 Notes Problem 1. You are given
Precision power measurements for megawatt heating controls
 ARTICLE Precision power measurements for megawatt heating controls Lars Alsdorf (right) explains Jürgen Hillebrand (Yokogawa) the test of the power controller. Precision power measurements carried out
ARTICLE Precision power measurements for megawatt heating controls Lars Alsdorf (right) explains Jürgen Hillebrand (Yokogawa) the test of the power controller. Precision power measurements carried out
CS 262 Lecture 01: Digital Images and Video. John Magee Some material copyright Jones and Bartlett
 CS 262 Lecture 01: Digital Images and Video John Magee Some material copyright Jones and Bartlett 1 Overview/Questions What is digital information? What is color? How do pictures get encoded into binary
CS 262 Lecture 01: Digital Images and Video John Magee Some material copyright Jones and Bartlett 1 Overview/Questions What is digital information? What is color? How do pictures get encoded into binary
Minds and Machines spring Searle s Chinese room argument, contd. Armstrong library reserves recitations slides handouts
 Minds and Machines spring 2005 Image removed for copyright reasons. Searle s Chinese room argument, contd. Armstrong library reserves recitations slides handouts 1 intentionality underived: the belief
Minds and Machines spring 2005 Image removed for copyright reasons. Searle s Chinese room argument, contd. Armstrong library reserves recitations slides handouts 1 intentionality underived: the belief
LabVIEW 8" Student Edition
 LabVIEW 8" Student Edition Robert H. Bishop The University of Texas at Austin PEARSON Prentice Hall Upper Saddle River, NJ 07458 CONTENTS Preface xvii LabVIEW Basics 1.1 System Configuration Requirements
LabVIEW 8" Student Edition Robert H. Bishop The University of Texas at Austin PEARSON Prentice Hall Upper Saddle River, NJ 07458 CONTENTS Preface xvii LabVIEW Basics 1.1 System Configuration Requirements
arxiv:math/ v1 [math.co] 22 Aug 2000
![arxiv:math/ v1 [math.co] 22 Aug 2000 arxiv:math/ v1 [math.co] 22 Aug 2000](/thumbs/89/98952035.jpg) One-Dimensional Peg Solitaire, and Duotaire arxiv:math/0008172v1 [math.co] 22 Aug 2000 Cristopher Moore 1,2 and David Eppstein 3 1 Computer Science Department, University of New Mexico, Albuquerque NM
One-Dimensional Peg Solitaire, and Duotaire arxiv:math/0008172v1 [math.co] 22 Aug 2000 Cristopher Moore 1,2 and David Eppstein 3 1 Computer Science Department, University of New Mexico, Albuquerque NM
INTRODUCTION TO COMPUTER SCIENCE I PROJECT 6 Sudoku! Revision 2 [2010-May-04] 1
![INTRODUCTION TO COMPUTER SCIENCE I PROJECT 6 Sudoku! Revision 2 [2010-May-04] 1 INTRODUCTION TO COMPUTER SCIENCE I PROJECT 6 Sudoku! Revision 2 [2010-May-04] 1](/thumbs/77/76610688.jpg) INTRODUCTION TO COMPUTER SCIENCE I PROJECT 6 Sudoku! Revision 2 [2010-May-04] 1 1 The game of Sudoku Sudoku is a game that is currently quite popular and giving crossword puzzles a run for their money
INTRODUCTION TO COMPUTER SCIENCE I PROJECT 6 Sudoku! Revision 2 [2010-May-04] 1 1 The game of Sudoku Sudoku is a game that is currently quite popular and giving crossword puzzles a run for their money
Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011
 Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011 Lecture 9 In which we introduce the maximum flow problem. 1 Flows in Networks Today we start talking about the Maximum Flow
Stanford University CS261: Optimization Handout 9 Luca Trevisan February 1, 2011 Lecture 9 In which we introduce the maximum flow problem. 1 Flows in Networks Today we start talking about the Maximum Flow
Chapter 4 The Data Encryption Standard
 Chapter 4 The Data Encryption Standard History of DES Most widely used encryption scheme is based on DES adopted by National Bureau of Standards (now National Institute of Standards and Technology) in
Chapter 4 The Data Encryption Standard History of DES Most widely used encryption scheme is based on DES adopted by National Bureau of Standards (now National Institute of Standards and Technology) in
Analysis of Data Chemistry 838
 Chemistry 838 Thomas V. Atkinson, Ph.D. Senior Academic Specialist Department of Chemistry Michigan State University East Lansing, MI 4884 TABLE OF CONTENTS TABLE OF CONTENTS...1 TABLE OF TABLES...1 TABLE
Chemistry 838 Thomas V. Atkinson, Ph.D. Senior Academic Specialist Department of Chemistry Michigan State University East Lansing, MI 4884 TABLE OF CONTENTS TABLE OF CONTENTS...1 TABLE OF TABLES...1 TABLE
Overview. The Big Picture... CSC 580 Cryptography and Computer Security. January 25, Math Basics for Cryptography
 CSC 580 Cryptography and Computer Security Math Basics for Cryptography January 25, 2018 Overview Today: Math basics (Sections 2.1-2.3) To do before Tuesday: Complete HW1 problems Read Sections 3.1, 3.2
CSC 580 Cryptography and Computer Security Math Basics for Cryptography January 25, 2018 Overview Today: Math basics (Sections 2.1-2.3) To do before Tuesday: Complete HW1 problems Read Sections 3.1, 3.2
Implementing Logic with the Embedded Array
 Implementing Logic with the Embedded Array in FLEX 10K Devices May 2001, ver. 2.1 Product Information Bulletin 21 Introduction Altera s FLEX 10K devices are the first programmable logic devices (PLDs)
Implementing Logic with the Embedded Array in FLEX 10K Devices May 2001, ver. 2.1 Product Information Bulletin 21 Introduction Altera s FLEX 10K devices are the first programmable logic devices (PLDs)
DVA325 Formal Languages, Automata and Models of Computation (FABER)
 DVA325 Formal Languages, Automata and Models of Computation (FABER) Lecture 1 - Introduction School of Innovation, Design and Engineering Mälardalen University 11 November 2014 Abu Naser Masud FABER November
DVA325 Formal Languages, Automata and Models of Computation (FABER) Lecture 1 - Introduction School of Innovation, Design and Engineering Mälardalen University 11 November 2014 Abu Naser Masud FABER November
Math 259 Winter Recitation Handout 6: Limits in Two Dimensions
 Math 259 Winter 2009 Recitation Handout 6: its in Two Dimensions As we have discussed in lecture, investigating the behavior of functions with two variables, f(x, y), can be more difficult than functions
Math 259 Winter 2009 Recitation Handout 6: its in Two Dimensions As we have discussed in lecture, investigating the behavior of functions with two variables, f(x, y), can be more difficult than functions
Introduction (concepts and definitions)
 Objectives: Introduction (digital system design concepts and definitions). Advantages and drawbacks of digital techniques compared with analog. Digital Abstraction. Synchronous and Asynchronous Systems.
Objectives: Introduction (digital system design concepts and definitions). Advantages and drawbacks of digital techniques compared with analog. Digital Abstraction. Synchronous and Asynchronous Systems.
Using Analyst TM to Quickly and Accurately Optimize a Chip-Module-Board Transition
 Using Analyst TM to Quickly and Accurately Optimize a Chip-Module-Board Transition 36 High Frequency Electronics By Dr. John Dunn 3D electromagnetic Optimizing the transition (EM) simulators are commonly
Using Analyst TM to Quickly and Accurately Optimize a Chip-Module-Board Transition 36 High Frequency Electronics By Dr. John Dunn 3D electromagnetic Optimizing the transition (EM) simulators are commonly
Wang, October 2016 Page 1 of 5. Math 150, Fall 2015 Exam 2 Form A Multiple Choice Sections 3A-5A
 Wang, October 2016 Page 1 of 5 Math 150, Fall 2015 Exam 2 Form A Multiple Choice Sections 3A-5A Last Name: First Name: Section Number: Student ID number: Directions: 1. No calculators, cell phones, or
Wang, October 2016 Page 1 of 5 Math 150, Fall 2015 Exam 2 Form A Multiple Choice Sections 3A-5A Last Name: First Name: Section Number: Student ID number: Directions: 1. No calculators, cell phones, or
LabVIEW Day 2: Other loops, Other graphs
 LabVIEW Day 2: Other loops, Other graphs Vern Lindberg From now on, I will not include the Programming to indicate paths to icons for the block diagram. I assume you will be getting comfortable with the
LabVIEW Day 2: Other loops, Other graphs Vern Lindberg From now on, I will not include the Programming to indicate paths to icons for the block diagram. I assume you will be getting comfortable with the
Limits and Continuity
 Limits and Continuity February 26, 205 Previously, you learned about the concept of the it of a function, and an associated concept, continuity. These concepts can be generalised to functions of several
Limits and Continuity February 26, 205 Previously, you learned about the concept of the it of a function, and an associated concept, continuity. These concepts can be generalised to functions of several
CSCI 1590 Intro to Computational Complexity
 CSCI 1590 Intro to Computational Complexity Parallel Computation and Complexity Classes John Savage Brown University April 13, 2009 John Savage (Brown University) CSCI 1590 Intro to Computational Complexity
CSCI 1590 Intro to Computational Complexity Parallel Computation and Complexity Classes John Savage Brown University April 13, 2009 John Savage (Brown University) CSCI 1590 Intro to Computational Complexity
What are they? Cellular Automata. Automata? What are they? Binary Addition Automaton. Binary Addition. The game of life or a new kind of science?
 What are they? Cellular Automata The game of life or a new kind of science? Richard Ladner Cellular automata have been invented many times under different names In pure mathematics they can be recognized
What are they? Cellular Automata The game of life or a new kind of science? Richard Ladner Cellular automata have been invented many times under different names In pure mathematics they can be recognized
Module 3 Greedy Strategy
 Module 3 Greedy Strategy Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Introduction to Greedy Technique Main
Module 3 Greedy Strategy Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Introduction to Greedy Technique Main
Modular Arithmetic. Kieran Cooney - February 18, 2016
 Modular Arithmetic Kieran Cooney - kieran.cooney@hotmail.com February 18, 2016 Sums and products in modular arithmetic Almost all of elementary number theory follows from one very basic theorem: Theorem.
Modular Arithmetic Kieran Cooney - kieran.cooney@hotmail.com February 18, 2016 Sums and products in modular arithmetic Almost all of elementary number theory follows from one very basic theorem: Theorem.
Tile Complexity of Assembly of Length N Arrays and N x N Squares. by John Reif and Harish Chandran
 Tile Complexity of Assembly of Length N Arrays and N x N Squares by John Reif and Harish Chandran Wang Tilings Hao Wang, 1961: Proving theorems by Pattern Recognition II Class of formal systems Modeled
Tile Complexity of Assembly of Length N Arrays and N x N Squares by John Reif and Harish Chandran Wang Tilings Hao Wang, 1961: Proving theorems by Pattern Recognition II Class of formal systems Modeled
Math 232. Calculus III Limits and Continuity. Updated: January 13, 2016 Calculus III Section 14.2
 Math 232 Calculus III Brian Veitch Fall 2015 Northern Illinois University 14.2 Limits and Continuity In this section our goal is to evaluate its of the form f(x, y) = L Let s take a look back at its in
Math 232 Calculus III Brian Veitch Fall 2015 Northern Illinois University 14.2 Limits and Continuity In this section our goal is to evaluate its of the form f(x, y) = L Let s take a look back at its in
CS101 Lecture 12: Digital Images. What You ll Learn Today
 CS101 Lecture 12: Digital Images Sampling and Quantizing Using bits to Represent Colors and Images Aaron Stevens (azs@bu.edu) 20 February 2013 What You ll Learn Today What is digital information? How to
CS101 Lecture 12: Digital Images Sampling and Quantizing Using bits to Represent Colors and Images Aaron Stevens (azs@bu.edu) 20 February 2013 What You ll Learn Today What is digital information? How to
CS 445 HW#2 Solutions
 1. Text problem 3.1 CS 445 HW#2 Solutions (a) General form: problem figure,. For the condition shown in the Solving for K yields Then, (b) General form: the problem figure, as in (a) so For the condition
1. Text problem 3.1 CS 445 HW#2 Solutions (a) General form: problem figure,. For the condition shown in the Solving for K yields Then, (b) General form: the problem figure, as in (a) so For the condition
Intro to coding and convolutional codes
 Intro to coding and convolutional codes Lecture 11 Vladimir Stojanović 6.973 Communication System Design Spring 2006 Massachusetts Institute of Technology 802.11a Convolutional Encoder Rate 1/2 convolutional
Intro to coding and convolutional codes Lecture 11 Vladimir Stojanović 6.973 Communication System Design Spring 2006 Massachusetts Institute of Technology 802.11a Convolutional Encoder Rate 1/2 convolutional
CHAPTER 11 PARTIAL DERIVATIVES
 CHAPTER 11 PARTIAL DERIVATIVES 1. FUNCTIONS OF SEVERAL VARIABLES A) Definition: A function of two variables is a rule that assigns to each ordered pair of real numbers (x,y) in a set D a unique real number
CHAPTER 11 PARTIAL DERIVATIVES 1. FUNCTIONS OF SEVERAL VARIABLES A) Definition: A function of two variables is a rule that assigns to each ordered pair of real numbers (x,y) in a set D a unique real number
Module 3 Greedy Strategy
 Module 3 Greedy Strategy Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Introduction to Greedy Technique Main
Module 3 Greedy Strategy Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Introduction to Greedy Technique Main
Investigating control strategies for the Phicom 3 wirebonder
 Investigating control strategies for the Phicom 3 wirebonder T. Kok DCT 2006.103 Traineeship report Coach(es): Supervisor: H.M.J. van de Groes M. Steinbuch Technische Universiteit Eindhoven Department
Investigating control strategies for the Phicom 3 wirebonder T. Kok DCT 2006.103 Traineeship report Coach(es): Supervisor: H.M.J. van de Groes M. Steinbuch Technische Universiteit Eindhoven Department
Lesson 7. Digital Signal Processors
 Lesson 7 Digital Signal Processors Instructional Objectives After going through this lesson the student would learn o Architecture of a Real time Signal Processing Platform o Different Errors introduced
Lesson 7 Digital Signal Processors Instructional Objectives After going through this lesson the student would learn o Architecture of a Real time Signal Processing Platform o Different Errors introduced
Mathematics 205 HWK 19b Solutions Section 16.2 p750. (x 2 y) dy dx. 2x 2 3
 Mathematics 5 HWK 9b Solutions Section 6. p75 Problem, 6., p75. Evaluate (x y) dy dx. Solution. (x y) dy dx x ( ) y dy dx [ x x dx ] [ ] y x dx Problem 9, 6., p75. For the region as shown, write f da as
Mathematics 5 HWK 9b Solutions Section 6. p75 Problem, 6., p75. Evaluate (x y) dy dx. Solution. (x y) dy dx x ( ) y dy dx [ x x dx ] [ ] y x dx Problem 9, 6., p75. For the region as shown, write f da as
Chapter 1: Digital logic
 Chapter 1: Digital logic I. Overview In PHYS 252, you learned the essentials of circuit analysis, including the concepts of impedance, amplification, feedback and frequency analysis. Most of the circuits
Chapter 1: Digital logic I. Overview In PHYS 252, you learned the essentials of circuit analysis, including the concepts of impedance, amplification, feedback and frequency analysis. Most of the circuits
Discrete Mathematics and Probability Theory Spring 2018 Ayazifar and Rao Midterm 2 Solutions
 CS 70 Discrete Mathematics and Probability Theory Spring 2018 Ayazifar and Rao Midterm 2 Solutions PRINT Your Name: Oski Bear SIGN Your Name: OS K I PRINT Your Student ID: CIRCLE your exam room: Pimentel
CS 70 Discrete Mathematics and Probability Theory Spring 2018 Ayazifar and Rao Midterm 2 Solutions PRINT Your Name: Oski Bear SIGN Your Name: OS K I PRINT Your Student ID: CIRCLE your exam room: Pimentel
Local Search: Hill Climbing. When A* doesn t work AIMA 4.1. Review: Hill climbing on a surface of states. Review: Local search and optimization
 Outline When A* doesn t work AIMA 4.1 Local Search: Hill Climbing Escaping Local Maxima: Simulated Annealing Genetic Algorithms A few slides adapted from CS 471, UBMC and Eric Eaton (in turn, adapted from
Outline When A* doesn t work AIMA 4.1 Local Search: Hill Climbing Escaping Local Maxima: Simulated Annealing Genetic Algorithms A few slides adapted from CS 471, UBMC and Eric Eaton (in turn, adapted from
Mathematics Success Level C
 T675 LESSON 2: Line Plot [OBJECTIVE] The student will measure lengths to the nearest fourth of an inch, create line plots of the data, and answer questions about line plots. [PREREQUISITE SKILLS] know
T675 LESSON 2: Line Plot [OBJECTIVE] The student will measure lengths to the nearest fourth of an inch, create line plots of the data, and answer questions about line plots. [PREREQUISITE SKILLS] know
MAS336 Computational Problem Solving. Problem 3: Eight Queens
 MAS336 Computational Problem Solving Problem 3: Eight Queens Introduction Francis J. Wright, 2007 Topics: arrays, recursion, plotting, symmetry The problem is to find all the distinct ways of choosing
MAS336 Computational Problem Solving Problem 3: Eight Queens Introduction Francis J. Wright, 2007 Topics: arrays, recursion, plotting, symmetry The problem is to find all the distinct ways of choosing
New Sliding Puzzle with Neighbors Swap Motion
 Prihardono AriyantoA,B Kenichi KawagoeC Graduate School of Natural Science and Technology, Kanazawa UniversityA Faculty of Mathematics and Natural Sciences, Institut Teknologi Bandung, Email: prihardono.ari@s.itb.ac.id
Prihardono AriyantoA,B Kenichi KawagoeC Graduate School of Natural Science and Technology, Kanazawa UniversityA Faculty of Mathematics and Natural Sciences, Institut Teknologi Bandung, Email: prihardono.ari@s.itb.ac.id
Computer Vision. Howie Choset Introduction to Robotics
 Computer Vision Howie Choset http://www.cs.cmu.edu.edu/~choset Introduction to Robotics http://generalrobotics.org What is vision? What is computer vision? Edge Detection Edge Detection Interest points
Computer Vision Howie Choset http://www.cs.cmu.edu.edu/~choset Introduction to Robotics http://generalrobotics.org What is vision? What is computer vision? Edge Detection Edge Detection Interest points
Classical Cryptography
 Classical Cryptography CS 6750 Lecture 1 September 10, 2009 Riccardo Pucella Goals of Classical Cryptography Alice wants to send message X to Bob Oscar is on the wire, listening to all communications Alice
Classical Cryptography CS 6750 Lecture 1 September 10, 2009 Riccardo Pucella Goals of Classical Cryptography Alice wants to send message X to Bob Oscar is on the wire, listening to all communications Alice
Copyright 1974, by the author(s). All rights reserved.
 Copyright 1974, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are
Copyright 1974, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are
11.2 LIMITS AND CONTINUITY
 11. LIMITS AND CONTINUITY INTRODUCTION: Consider functions of one variable y = f(x). If you are told that f(x) is continuous at x = a, explain what the graph looks like near x = a. Formal definition of
11. LIMITS AND CONTINUITY INTRODUCTION: Consider functions of one variable y = f(x). If you are told that f(x) is continuous at x = a, explain what the graph looks like near x = a. Formal definition of
i + u 2 j be the unit vector that has its initial point at (a, b) and points in the desired direction. It determines a line in the xy-plane:
 1 Directional Derivatives and Gradients Suppose we need to compute the rate of change of f(x, y) with respect to the distance from a point (a, b) in some direction. Let u = u 1 i + u 2 j be the unit vector
1 Directional Derivatives and Gradients Suppose we need to compute the rate of change of f(x, y) with respect to the distance from a point (a, b) in some direction. Let u = u 1 i + u 2 j be the unit vector
It is important that you show your work. The total value of this test is 220 points.
 June 27, 2001 Your name It is important that you show your work. The total value of this test is 220 points. 1. (10 points) Use the Euclidean algorithm to solve the decanting problem for decanters of sizes
June 27, 2001 Your name It is important that you show your work. The total value of this test is 220 points. 1. (10 points) Use the Euclidean algorithm to solve the decanting problem for decanters of sizes
Counting Subsets with Repetitions. ICS 6C Sandy Irani
 Counting Subsets with Repetitions ICS 6C Sandy Irani Multi-sets A Multi-set can have more than one copy of an item. Order doesn t matter The number of elements of each type does matter: {1, 2, 2, 2, 3,
Counting Subsets with Repetitions ICS 6C Sandy Irani Multi-sets A Multi-set can have more than one copy of an item. Order doesn t matter The number of elements of each type does matter: {1, 2, 2, 2, 3,
Jong C. Park Computer Science Division, KAIST
 Jong C. Park Computer Science Division, KAIST Today s Topics Basic Principles Permutations and Combinations Algorithms for Generating Permutations Generalized Permutations and Combinations Binomial Coefficients
Jong C. Park Computer Science Division, KAIST Today s Topics Basic Principles Permutations and Combinations Algorithms for Generating Permutations Generalized Permutations and Combinations Binomial Coefficients
