Kalman Filters and Adaptive Windows for Learning in Data Streams
|
|
|
- Janice Wood
- 5 years ago
- Views:
Transcription
1 Kalman Filters and Adaptive Windows for Learning in Data Streams Albert Bifet Ricard Gavaldà Universitat Politècnica de Catalunya DS 06 Barcelona A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 1 / 29
2 Outline 1 Introduction 2 The Kalman Filter and the CUSUM Test 3 The ADWIN Algorithm 4 General Framework 5 K-ADWIN 6 Experimental Validation of K-ADWIN 7 Conclusions A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 2 / 29
3 Introduction Introduction Data Streams Sequence potentially infinite High amount of data: sublinear space High Speed of arrival: small constant time per example Estimation and prediction Distribution and concept drift K-ADWIN : Combination Kalman filter ADWIN : Adaptive window of recently seen data items. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 3 / 29
4 Introduction Introduction Problem Given an input sequence x 1, x 2,..., x t,... we want to output at instant t a prediction x t+1 minimizing prediction error: x t+1 x t+1 considering distribution changes overtime. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 4 / 29
5 Introduction Time Change Detectors and Predictors: A General Framework x t Estimator Estimation A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 5 / 29
6 Introduction Time Change Detectors and Predictors: A General Framework x t Estimator Change Detect. Estimation Alarm A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 5 / 29
7 Introduction Time Change Detectors and Predictors: A General Framework x t Estimator Change Detect. Estimation Alarm Memory A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 5 / 29
8 Introduction Introduction Our generic proposal: Use change detector Use memory Our particular proposal: K-ADWIN Kalman filter as estimator Use ADWIN as change detector with memory [BG06] Application Estimate statistics from data streams In Data Mining Algorithms based on counters, replace them for estimators. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 6 / 29
9 Introduction Data Mining Algorithms with Concept Drift No Concept Drift Concept drift input DM Algorithm Counter 5 Counter 4 Counter 3 output input DM Algorithm Static Model output Counter 2 Counter 1 Change Detect. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 7 / 29
10 Introduction Data Mining Algorithms with Concept Drift No Concept Drift Concept Drift DM Algorithm DM Algorithm input Counter 5 output input Estimator 5 output Counter 4 Estimator 4 Counter 3 Estimator 3 Counter 2 Estimator 2 Counter 1 Estimator 1 A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 7 / 29
11 The Kalman Filter and the CUSUM Test The Kalman Filter Optimal recursive algorithm Minimum mean-square error estimator Estimate the state x R n of a discrete-time controlled process x k = Ax k 1 + Bu k + w k 1 with a measurement z R m that is Z k = Hx k + v k. The random variables w k and v k represent the process and measurement noise (respectively). They are assumed to be independent (of each other), white, and with normal probability distributions p(w) N(0, Q) p(v) N(0, R). A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 8 / 29
12 The Kalman Filter The Kalman Filter and the CUSUM Test The difference equation of our discrete-time controlled process is K k = P k 1 /(P k 1 + R) X k = X k 1 + K k (z k X k 1 ) P k = P k (1 K k ) + Q A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 9 / 29
13 The Kalman Filter and the CUSUM Test The Kalman Filter The difference equation of our discrete-time controlled process is K k = P k 1 /(P k 1 + R) X k = X k 1 + K k (z k X k 1 ) P k = P k (1 K k ) + Q The performance of the Kalman filter depends on the accuracy of the a-priori assumptions: linearity of the difference stochastic equation estimation of covariances Q and R, assumed to be fixed, known, and follow normal distributions with zero mean. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 9 / 29
14 The Kalman Filter and the CUSUM Test The CUSUM Test The cumulative sum (CUSUM algorithm),is a change detection algorithm that gives an alarm when the mean of the input data is significantly different from zero. The CUSUM test is memoryless, and its accuracy depends on the choice of parameters υ and h. It is as follows: g 0 = 0, g t = max (0, g t 1 + ɛ t υ) if g t > h then alarm and g t = 0 A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 10 / 29
15 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
16 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = 1 W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
17 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = 10 W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
18 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = 101 W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
19 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = 1010 W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
20 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
21 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
22 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
23 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
24 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = ˆµ W0 ˆµ W1 ɛ c : CHANGE DETECTED! W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
25 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = Drop elements from the tail of W W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
26 The ADWIN Algorithm Algorithm ADWIN [BG06] Example W = Drop elements from the tail of W W 0 = W 1 = ADWIN: ADAPTIVE WINDOWING ALGORITHM 1 Initialize Window W 2 for each t > 0 3 do W W {x t } (i.e., add x t to the head of W ) 4 repeat Drop elements from the tail of W 5 until ˆµ W0 ˆµ W1 ɛ c holds 6 for every split of W into W = W 0 W 1 7 Output ˆµ W A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 11 / 29
27 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
28 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
29 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
30 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
31 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
32 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
33 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
34 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
35 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
36 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
37 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
38 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
39 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
40 The ADWIN Algorithm Window Management Models W = Equal & fixed size subwindows D. Kifer, S. Ben-David, and J. Gehrke. Detecting change in data streams Total window against subwindow J. Gama, P. Medas, G. Castillo, and P. Rodrigues. Learning with drift detection ADWIN: All Adjacent subwindows A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 12 / 29
41 The ADWIN Algorithm Algorithm ADWIN [BG06] ADWIN has rigorous guarantees On ratio of false positives On ratio of false negatives On the relation of the size of the current window and change rates A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 13 / 29
42 The ADWIN Algorithm Algorithm ADWIN [BG06] Theorem At every time step we have: 1 (Few false positives guarantee) If µ t remains constant within W, the probability that ADWIN shrinks the window at this step is at most δ. 2 (Few false negatives guarantee) If for any partition W in two parts W 0 W 1 (where W 1 contains the most recent items) we have µ W0 µ W1 > ɛ, and if ɛ 4 3 max{µ W0, µ W1 } ln 4n min{n 0, n 1 } δ then with probability 1 δ ADWIN shrinks W to W 1, or shorter. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 14 / 29
43 The ADWIN Algorithm Data Streams Algorithm ADWIN2 [BG06] ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Sliding Window Model Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 15 / 29
44 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Insert new Item Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 16 / 29
45 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Insert new Item Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 16 / 29
46 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Compressing Buckets Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 16 / 29
47 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Compressing Buckets Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 17 / 29
48 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Compressing Buckets Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 17 / 29
49 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Compressing Buckets Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 18 / 29
50 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Detecting Change: Delete last Bucket Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 19 / 29
51 Algorithm ADWIN2 The ADWIN Algorithm ADWIN2 using a Data Stream Sliding Window Model, can provide the exact counts of 1 s in O(1) time per point. tries O(log W ) cutpoints uses O( 1 ɛ log W ) memory words the processing time per example is O(log W ) (amortized) and O(log 2 W ) (worst-case). Detecting Change: Delete last Bucket Content: Capacity: A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 19 / 29
52 General Framework General Framework Time Change Detectors and Predictors : Type I Example (Kalman Filter) x t Estimator Estimation A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 20 / 29
53 General Framework General Framework Time Change Detectors and Predictors : Type II Example (Kalman Filter + CUSUM) x t Estimator Change Detect. Estimation Alarm A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 20 / 29
54 General Framework General Framework Time Change Detectors and Predictors : Type III Example (Adaptive Kalman Filter) x t Estimator Estimation Memory A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 20 / 29
55 General Framework General Framework Time Change Detectors and Predictors : Type IV Example (ADWIN, Kalman Filter+ADWIN) x t Estimator Change Detect. Estimation Alarm Memory A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 20 / 29
56 General Framework Time Change Detectors and Predictors: A General Framework No memory Memory No Change Type I Type III Detector Kalman Filter Adaptive Kalman Filter Change Type II Type IV Detector Kalman Filter + CUSUM ADWIN Kalman Filter + ADWIN A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 21 / 29
57 General Framework Time Change Detectors and Predictors: A General Framework No memory Memory No Change Type I Type III Detector Kalman Filter Adaptive Kalman Filter Q,R estimated from window Change Type II Type IV Detector Kalman Filter + CUSUM ADWIN Kalman Filter + ADWIN Q,R estimated from window A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 21 / 29
58 K-ADWIN K-ADWIN = ADWIN + Kalman Filtering x t Kalman ADWIN Estimation Alarm ADWIN Memory R = W 2 /50 and Q = 200/W, where W is the length of the window maintained by ADWIN. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 22 / 29
59 Experimental Validation of K-ADWIN Tracking Experiments KALMAN: R=1000;Q=1 Error= A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 23 / 29
60 Experimental Validation of K-ADWIN Tracking Experiments ADWIN : Error= KALMAN: R=1000;Q=1 Error= A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 23 / 29
61 Experimental Validation of K-ADWIN Tracking Experiments K-ADWIN Error= ADWIN : Error= A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 23 / 29
62 Naïve Bayes Experimental Validation of K-ADWIN Data set that describes the weather conditions for playing some game. Example outlook temp. humidity windy play sunny hot high false no sunny hot high true no overcast hot high false yes rainy mild high false yes rainy cool normal false yes rainy cool normal true no overcast cool normal true yes Assume we have to classify the following new instance: outlook temp. humidity windy play sunny cool high true? A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 24 / 29
63 Naïve Bayes Experimental Validation of K-ADWIN Assume we have to classify the following new instance: outlook temp. humidity windy play sunny cool high true? We classify the new instance: ν NB = arg max P(ν j)p(sunny ν j )P(cool ν j )P(high ν j )P(true ν j ) ν {yes,no} Conditional probabilities can be estimated directly as frequencies: P(a i ν j ) = number of instances with attribute a i and class ν j total number of training instances with class ν j Create one estimator for each frequence that needs estimation A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 24 / 29
64 Experimental Validation of K-ADWIN Experimental Validation of K-ADWIN We test Naïve Bayes Predictor and k-means clustering Method: replace counters by estimators Synthetic data where change is controllable Naïve Bayes: We compare accuracy of Static model: Training of 1000 samples every instant Dynamic model: replace probabilities counters by estimators computing the ratio %Dynamic Static with tests using 2000 samples. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 25 / 29
65 Experimental Validation of K-ADWIN Naïve Bayes Predictor Width %Static %Dynamic % Dynamic/Static ADWIN 83,36% 80,30% 96,33% Kalman Q = 1, R = ,22% 71,13% 85,48% Kalman Q = 1, R = 1 83,21% 56,91% 68,39% Kalman Q =.25, R =.25 83,26% 56,91% 68,35% Adaptive Kalman 83,24% 76,21% 91,56% CUSUM Kalman 83,30% 50,65% 60,81% K-ADWIN 83,24% 81,39% 97,77% Fixed-sized Window 32 83,28% 67,64% 81,22% Fixed-sized Window ,30% 75,40% 90,52% Fixed-sized Window ,28% 80,47% 96,62% Fixed-sized Window ,24% 82,19% 98,73% A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 26 / 29
66 Experimental Validation of K-ADWIN k-means Clustering σ = 0.15 Width Static Dynamic ADWIN 9,72 21,54 Kalman Q = 1, R = ,72 19,72 Kalman Q = 1, R = 100 9,71 17,60 Kalman Q =.25, R =.25 9,71 22,63 Adaptive Kalman 9,72 18,98 CUSUM Kalman 9,72 18,29 K-ADWIN 9,72 17,30 Fixed-sized Window 32 9,72 25,70 Fixed-sized Window 128 9,72 36,42 Fixed-sized Window 512 9,72 38,75 Fixed-sized Window ,72 39,64 Fixed-sized Window ,72 43,39 Fixed-sized Window ,72 53,82 A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 27 / 29
67 Experimental Validation of K-ADWIN Results No estimator ever does much better than K-ADWIN K-ADWIN does much better than every other estimators in at least one context. Tracking problem K-ADWIN and ADWIN automatically do about as well as the Kalman filter with the best set of fixed covariance parameters. Naïve Bayes and k-means: K-ADWIN does somewhat better than ADWIN and far better than any memoryless Kalman filter. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 28 / 29
68 Conclusions Conclusions and Future Work K-ADWIN tunes itself to the data stream at hand, with no need for the user to hardwire or precompute parameters. Better results than either memoryless Kalman Filtering or sliding windows with linear estimators. Future work : Tests on real-world, not only synthetic data. Other learning algorithms: algorithms for induction of decision trees. A. Bifet, R. Gavaldà (UPC) Kalman Filters and Adaptive Windows for Learning in Data Streams DS 06 Barcelona 29 / 29
Kalman Filters and Adaptive Windows for Learning in Data Streams
 Kalman Filters and Adaptive Windows for Learning in Data Streams Albert Bifet and Ricard Gavaldà Universitat Politècnica de Catalunya, Barcelona, Spain {abifet,gavalda}@lsi.upc.edu Abstract. We study the
Kalman Filters and Adaptive Windows for Learning in Data Streams Albert Bifet and Ricard Gavaldà Universitat Politècnica de Catalunya, Barcelona, Spain {abifet,gavalda}@lsi.upc.edu Abstract. We study the
Kalman Filters and Adaptive Windows for Learning in Data Streams
 Kalman Filters and Adaptive Windows for Learning in Data Streams Albert Bifet and Ricard Gavaldà Universitat Politècnica de Catalunya, Barcelona, Spain {abifet,gavalda}@lsi.upc.edu July 12th, 2006 Abstract.
Kalman Filters and Adaptive Windows for Learning in Data Streams Albert Bifet and Ricard Gavaldà Universitat Politècnica de Catalunya, Barcelona, Spain {abifet,gavalda}@lsi.upc.edu July 12th, 2006 Abstract.
Introduction to Source Coding
 Comm. 52: Communication Theory Lecture 7 Introduction to Source Coding - Requirements of source codes - Huffman Code Length Fixed Length Variable Length Source Code Properties Uniquely Decodable allow
Comm. 52: Communication Theory Lecture 7 Introduction to Source Coding - Requirements of source codes - Huffman Code Length Fixed Length Variable Length Source Code Properties Uniquely Decodable allow
Chapter 4 SPEECH ENHANCEMENT
 44 Chapter 4 SPEECH ENHANCEMENT 4.1 INTRODUCTION: Enhancement is defined as improvement in the value or Quality of something. Speech enhancement is defined as the improvement in intelligibility and/or
44 Chapter 4 SPEECH ENHANCEMENT 4.1 INTRODUCTION: Enhancement is defined as improvement in the value or Quality of something. Speech enhancement is defined as the improvement in intelligibility and/or
CS188 Spring 2014 Section 3: Games
 CS188 Spring 2014 Section 3: Games 1 Nearly Zero Sum Games The standard Minimax algorithm calculates worst-case values in a zero-sum two player game, i.e. a game in which for all terminal states s, the
CS188 Spring 2014 Section 3: Games 1 Nearly Zero Sum Games The standard Minimax algorithm calculates worst-case values in a zero-sum two player game, i.e. a game in which for all terminal states s, the
On Kalman Filtering. The 1960s: A Decade to Remember
 On Kalman Filtering A study of A New Approach to Linear Filtering and Prediction Problems by R. E. Kalman Mehul Motani February, 000 The 960s: A Decade to Remember Rudolf E. Kalman in 960 Research Institute
On Kalman Filtering A study of A New Approach to Linear Filtering and Prediction Problems by R. E. Kalman Mehul Motani February, 000 The 960s: A Decade to Remember Rudolf E. Kalman in 960 Research Institute
Wireless Network Delay Estimation for Time-Sensitive Applications
 Wireless Network Delay Estimation for Time-Sensitive Applications Rafael Camilo Lozoya Gámez, Pau Martí, Manel Velasco and Josep M. Fuertes Automatic Control Department Technical University of Catalonia
Wireless Network Delay Estimation for Time-Sensitive Applications Rafael Camilo Lozoya Gámez, Pau Martí, Manel Velasco and Josep M. Fuertes Automatic Control Department Technical University of Catalonia
Anomaly Detection based Secure In-Network Aggregation for Wireless Sensor Networks
 Anomaly Detection based Secure In-Network Aggregation for Wireless Sensor Networks Bo Sun, Member, IEEE, Xuemei Shan, Kui Wu, Member, IEEE, and Yang Xiao, Senior Member, IEEE Abstract - Secure in-network
Anomaly Detection based Secure In-Network Aggregation for Wireless Sensor Networks Bo Sun, Member, IEEE, Xuemei Shan, Kui Wu, Member, IEEE, and Yang Xiao, Senior Member, IEEE Abstract - Secure in-network
Outlier-Robust Estimation of GPS Satellite Clock Offsets
 Outlier-Robust Estimation of GPS Satellite Clock Offsets Simo Martikainen, Robert Piche and Simo Ali-Löytty Tampere University of Technology. Tampere, Finland Email: simo.martikainen@tut.fi Abstract A
Outlier-Robust Estimation of GPS Satellite Clock Offsets Simo Martikainen, Robert Piche and Simo Ali-Löytty Tampere University of Technology. Tampere, Finland Email: simo.martikainen@tut.fi Abstract A
Machine Learning, Data Mining, and Knowledge Discovery: An Introduction
 Machine Learning, Data Mining, and Kwledge Discovery: An Introduction Outline Data Mining Application Examples Data Mining & Kwledge Discovery Data Mining with Weka AHPCRC Workshop - 8/16/11 - Dr. Martin
Machine Learning, Data Mining, and Kwledge Discovery: An Introduction Outline Data Mining Application Examples Data Mining & Kwledge Discovery Data Mining with Weka AHPCRC Workshop - 8/16/11 - Dr. Martin
Knowledge discovery & data mining Classification & fraud detection
 Knowledge discovery & data mining Classification & fraud detection Knowledge discovery & data mining Classification & fraud detection 5/24/00 Click here to start Table of Contents Author: Dino Pedreschi
Knowledge discovery & data mining Classification & fraud detection Knowledge discovery & data mining Classification & fraud detection 5/24/00 Click here to start Table of Contents Author: Dino Pedreschi
IMPROVEMENTS TO A QUEUE AND DELAY ESTIMATION ALGORITHM UTILIZED IN VIDEO IMAGING VEHICLE DETECTION SYSTEMS
 IMPROVEMENTS TO A QUEUE AND DELAY ESTIMATION ALGORITHM UTILIZED IN VIDEO IMAGING VEHICLE DETECTION SYSTEMS A Thesis Proposal By Marshall T. Cheek Submitted to the Office of Graduate Studies Texas A&M University
IMPROVEMENTS TO A QUEUE AND DELAY ESTIMATION ALGORITHM UTILIZED IN VIDEO IMAGING VEHICLE DETECTION SYSTEMS A Thesis Proposal By Marshall T. Cheek Submitted to the Office of Graduate Studies Texas A&M University
Communication Theory II
 Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Communication Theory II Lecture 13: Information Theory (cont d) Ahmed Elnakib, PhD Assistant Professor, Mansoura University, Egypt March 22 th, 2015 1 o Source Code Generation Lecture Outlines Source Coding
Skip Lists S 3 S 2 S 1. 2/6/2016 7:04 AM Skip Lists 1
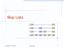 Skip Lists S 3 15 15 23 10 15 23 36 2/6/2016 7:04 AM Skip Lists 1 Outline and Reading What is a skip list Operations Search Insertion Deletion Implementation Analysis Space usage Search and update times
Skip Lists S 3 15 15 23 10 15 23 36 2/6/2016 7:04 AM Skip Lists 1 Outline and Reading What is a skip list Operations Search Insertion Deletion Implementation Analysis Space usage Search and update times
UNIVERSITY OF MICHIGAN DEPARTMENT OF ELECTRICAL ENGINEERING : SYSTEMS EECS 555 DIGITAL COMMUNICATION THEORY
 UNIVERSITY OF MICHIGAN DEPARTMENT OF ELECTRICAL ENGINEERING : SYSTEMS EECS 555 DIGITAL COMMUNICATION THEORY Study Of IEEE P802.15.3a physical layer proposals for UWB: DS-UWB proposal and Multiband OFDM
UNIVERSITY OF MICHIGAN DEPARTMENT OF ELECTRICAL ENGINEERING : SYSTEMS EECS 555 DIGITAL COMMUNICATION THEORY Study Of IEEE P802.15.3a physical layer proposals for UWB: DS-UWB proposal and Multiband OFDM
Chapter 7: Sorting 7.1. Original
 Chapter 7: Sorting 7.1 Original 3 1 4 1 5 9 2 6 5 after P=2 1 3 4 1 5 9 2 6 5 after P=3 1 3 4 1 5 9 2 6 5 after P=4 1 1 3 4 5 9 2 6 5 after P=5 1 1 3 4 5 9 2 6 5 after P=6 1 1 3 4 5 9 2 6 5 after P=7 1
Chapter 7: Sorting 7.1 Original 3 1 4 1 5 9 2 6 5 after P=2 1 3 4 1 5 9 2 6 5 after P=3 1 3 4 1 5 9 2 6 5 after P=4 1 1 3 4 5 9 2 6 5 after P=5 1 1 3 4 5 9 2 6 5 after P=6 1 1 3 4 5 9 2 6 5 after P=7 1
Change detection with Kalman Filter and CUSUM
 Change detection with Kalman Filter and CUSUM Milton Severo 1,2 and João Gama 1,3 1 Fac. of Economy, University of Porto, Portugal 2 Department of Hygiene and Epidemiology, Fac. of Medicine, University
Change detection with Kalman Filter and CUSUM Milton Severo 1,2 and João Gama 1,3 1 Fac. of Economy, University of Porto, Portugal 2 Department of Hygiene and Epidemiology, Fac. of Medicine, University
Adaptive Filters Linear Prediction
 Adaptive Filters Gerhard Schmidt Christian-Albrechts-Universität zu Kiel Faculty of Engineering Institute of Electrical and Information Engineering Digital Signal Processing and System Theory Slide 1 Contents
Adaptive Filters Gerhard Schmidt Christian-Albrechts-Universität zu Kiel Faculty of Engineering Institute of Electrical and Information Engineering Digital Signal Processing and System Theory Slide 1 Contents
Lecture5: Lossless Compression Techniques
 Fixed to fixed mapping: we encoded source symbols of fixed length into fixed length code sequences Fixed to variable mapping: we encoded source symbols of fixed length into variable length code sequences
Fixed to fixed mapping: we encoded source symbols of fixed length into fixed length code sequences Fixed to variable mapping: we encoded source symbols of fixed length into variable length code sequences
Fundamentals of Statistical Monitoring: The Good, Bad, & Ugly in Biosurveillance
 Fundamentals of Statistical Monitoring: The Good, Bad, & Ugly in Biosurveillance Galit Shmuéli Dept of Decision & Info Technologies Robert H Smith School of Business University of Maryland, College Park
Fundamentals of Statistical Monitoring: The Good, Bad, & Ugly in Biosurveillance Galit Shmuéli Dept of Decision & Info Technologies Robert H Smith School of Business University of Maryland, College Park
Mikko Myllymäki and Tuomas Virtanen
 NON-STATIONARY NOISE MODEL COMPENSATION IN VOICE ACTIVITY DETECTION Mikko Myllymäki and Tuomas Virtanen Department of Signal Processing, Tampere University of Technology Korkeakoulunkatu 1, 3370, Tampere,
NON-STATIONARY NOISE MODEL COMPENSATION IN VOICE ACTIVITY DETECTION Mikko Myllymäki and Tuomas Virtanen Department of Signal Processing, Tampere University of Technology Korkeakoulunkatu 1, 3370, Tampere,
Privacy preserving data mining multiplicative perturbation techniques
 Privacy preserving data mining multiplicative perturbation techniques Li Xiong CS573 Data Privacy and Anonymity Outline Review and critique of randomization approaches (additive noise) Multiplicative data
Privacy preserving data mining multiplicative perturbation techniques Li Xiong CS573 Data Privacy and Anonymity Outline Review and critique of randomization approaches (additive noise) Multiplicative data
Digital Audio. Lecture-6
 Digital Audio Lecture-6 Topics today Digitization of sound PCM Lossless predictive coding 2 Sound Sound is a pressure wave, taking continuous values Increase / decrease in pressure can be measured in amplitude,
Digital Audio Lecture-6 Topics today Digitization of sound PCM Lossless predictive coding 2 Sound Sound is a pressure wave, taking continuous values Increase / decrease in pressure can be measured in amplitude,
Mining multi-dimensional concept-drifting data streams using Bayesian network classifiers
 Intelligent Data Analysis 20 (2016) 257 280 257 DOI 10.3233/IDA-160804 IOS Press Mining multi-dimensional concept-drifting data streams using Bayesian network classifiers Hanen Borchani a,, Pedro Larrañaga
Intelligent Data Analysis 20 (2016) 257 280 257 DOI 10.3233/IDA-160804 IOS Press Mining multi-dimensional concept-drifting data streams using Bayesian network classifiers Hanen Borchani a,, Pedro Larrañaga
Closing the loop around Sensor Networks
 Closing the loop around Sensor Networks Bruno Sinopoli Shankar Sastry Dept of Electrical Engineering, UC Berkeley Chess Review May 11, 2005 Berkeley, CA Conceptual Issues Given a certain wireless sensor
Closing the loop around Sensor Networks Bruno Sinopoli Shankar Sastry Dept of Electrical Engineering, UC Berkeley Chess Review May 11, 2005 Berkeley, CA Conceptual Issues Given a certain wireless sensor
Picking microseismic first arrival times by Kalman filter and wavelet transform
 Picking first arrival times Picking microseismic first arrival times by Kalman filter and wavelet transform Baolin Qiao and John C. Bancroft ABSTRACT Due to the high energy content of the ambient noise,
Picking first arrival times Picking microseismic first arrival times by Kalman filter and wavelet transform Baolin Qiao and John C. Bancroft ABSTRACT Due to the high energy content of the ambient noise,
Background Pixel Classification for Motion Detection in Video Image Sequences
 Background Pixel Classification for Motion Detection in Video Image Sequences P. Gil-Jiménez, S. Maldonado-Bascón, R. Gil-Pita, and H. Gómez-Moreno Dpto. de Teoría de la señal y Comunicaciones. Universidad
Background Pixel Classification for Motion Detection in Video Image Sequences P. Gil-Jiménez, S. Maldonado-Bascón, R. Gil-Pita, and H. Gómez-Moreno Dpto. de Teoría de la señal y Comunicaciones. Universidad
Chapter 1. Probability
 Chapter 1. Probability 1.1 Basic Concepts Scientific method a. For a given problem, we define measures that explains the problem well. b. Data is collected with observation and the measures are calculated.
Chapter 1. Probability 1.1 Basic Concepts Scientific method a. For a given problem, we define measures that explains the problem well. b. Data is collected with observation and the measures are calculated.
Kalman Tracking and Bayesian Detection for Radar RFI Blanking
 Kalman Tracking and Bayesian Detection for Radar RFI Blanking Weizhen Dong, Brian D. Jeffs Department of Electrical and Computer Engineering Brigham Young University J. Richard Fisher National Radio Astronomy
Kalman Tracking and Bayesian Detection for Radar RFI Blanking Weizhen Dong, Brian D. Jeffs Department of Electrical and Computer Engineering Brigham Young University J. Richard Fisher National Radio Astronomy
Energy Measurement in EXO-200 using Boosted Regression Trees
 Energy Measurement in EXO-2 using Boosted Regression Trees Mike Jewell, Alex Rider June 6, 216 1 Introduction The EXO-2 experiment uses a Liquid Xenon (LXe) time projection chamber (TPC) to search for
Energy Measurement in EXO-2 using Boosted Regression Trees Mike Jewell, Alex Rider June 6, 216 1 Introduction The EXO-2 experiment uses a Liquid Xenon (LXe) time projection chamber (TPC) to search for
Information Theory and Communication Optimal Codes
 Information Theory and Communication Optimal Codes Ritwik Banerjee rbanerjee@cs.stonybrook.edu c Ritwik Banerjee Information Theory and Communication 1/1 Roadmap Examples and Types of Codes Kraft Inequality
Information Theory and Communication Optimal Codes Ritwik Banerjee rbanerjee@cs.stonybrook.edu c Ritwik Banerjee Information Theory and Communication 1/1 Roadmap Examples and Types of Codes Kraft Inequality
Data Dissemination and Broadcasting Systems Lesson 06 Adaptive Dispersal Algorithms, Bandwidth allocation and Scheduling
 Data Dissemination and Broadcasting Systems Lesson 06 Adaptive Dispersal Algorithms, Bandwidth allocation and Scheduling Oxford University Press 2007. All rights reserved. 1 Functions of Information dispersal
Data Dissemination and Broadcasting Systems Lesson 06 Adaptive Dispersal Algorithms, Bandwidth allocation and Scheduling Oxford University Press 2007. All rights reserved. 1 Functions of Information dispersal
Statistics, Probability and Noise
 Statistics, Probability and Noise Claudia Feregrino-Uribe & Alicia Morales-Reyes Original material: Rene Cumplido Autumn 2015, CCC-INAOE Contents Signal and graph terminology Mean and standard deviation
Statistics, Probability and Noise Claudia Feregrino-Uribe & Alicia Morales-Reyes Original material: Rene Cumplido Autumn 2015, CCC-INAOE Contents Signal and graph terminology Mean and standard deviation
State-Space Models with Kalman Filtering for Freeway Traffic Forecasting
 State-Space Models with Kalman Filtering for Freeway Traffic Forecasting Brian Portugais Boise State University brianportugais@u.boisestate.edu Mandar Khanal Boise State University mkhanal@boisestate.edu
State-Space Models with Kalman Filtering for Freeway Traffic Forecasting Brian Portugais Boise State University brianportugais@u.boisestate.edu Mandar Khanal Boise State University mkhanal@boisestate.edu
A. Siffer, P-A Fouque, A. Termier and C. Largouet April 26, 2017
 A. Siffer, P-A Fouque, A. Termier and C. Largouet April 26, 2017 Context Providing better thresholds Finding anomalies in streams Application to intrusion detection A more general framework 1 Massive
A. Siffer, P-A Fouque, A. Termier and C. Largouet April 26, 2017 Context Providing better thresholds Finding anomalies in streams Application to intrusion detection A more general framework 1 Massive
Bandit Algorithms Continued: UCB1
 Bandit Algorithms Continued: UCB1 Noel Welsh 09 November 2010 Noel Welsh () Bandit Algorithms Continued: UCB1 09 November 2010 1 / 18 Annoucements Lab is busy Wednesday afternoon from 13:00 to 15:00 (Some)
Bandit Algorithms Continued: UCB1 Noel Welsh 09 November 2010 Noel Welsh () Bandit Algorithms Continued: UCB1 09 November 2010 1 / 18 Annoucements Lab is busy Wednesday afternoon from 13:00 to 15:00 (Some)
The fundamentals of detection theory
 Advanced Signal Processing: The fundamentals of detection theory Side 1 of 18 Index of contents: Advanced Signal Processing: The fundamentals of detection theory... 3 1 Problem Statements... 3 2 Detection
Advanced Signal Processing: The fundamentals of detection theory Side 1 of 18 Index of contents: Advanced Signal Processing: The fundamentals of detection theory... 3 1 Problem Statements... 3 2 Detection
The tenure game. The tenure game. Winning strategies for the tenure game. Winning condition for the tenure game
 The tenure game The tenure game is played by two players Alice and Bob. Initially, finitely many tokens are placed at positions that are nonzero natural numbers. Then Alice and Bob alternate in their moves
The tenure game The tenure game is played by two players Alice and Bob. Initially, finitely many tokens are placed at positions that are nonzero natural numbers. Then Alice and Bob alternate in their moves
Wireless Communication Technologies (16:332:546)
 Wireless Communication Technologies (16:332:546) Taught by Professor Narayan Mandayam Lecture 7 : Co-Channel Interference Slides prepared by : Shuangyu Luo Outline Co-channel interference 4 Examples of
Wireless Communication Technologies (16:332:546) Taught by Professor Narayan Mandayam Lecture 7 : Co-Channel Interference Slides prepared by : Shuangyu Luo Outline Co-channel interference 4 Examples of
Topic 23 Red Black Trees
 Topic 23 "People in every direction No words exchanged No time to exchange And all the little ants are marching Red and Black antennas waving" -Ants Marching, Dave Matthew's Band "Welcome to L.A.'s Automated
Topic 23 "People in every direction No words exchanged No time to exchange And all the little ants are marching Red and Black antennas waving" -Ants Marching, Dave Matthew's Band "Welcome to L.A.'s Automated
Pulse Code Modulation
 Pulse Code Modulation EE 44 Spring Semester Lecture 9 Analog signal Pulse Amplitude Modulation Pulse Width Modulation Pulse Position Modulation Pulse Code Modulation (3-bit coding) 1 Advantages of Digital
Pulse Code Modulation EE 44 Spring Semester Lecture 9 Analog signal Pulse Amplitude Modulation Pulse Width Modulation Pulse Position Modulation Pulse Code Modulation (3-bit coding) 1 Advantages of Digital
Dipl.-Ing. Wanda Benešová PhD., vgg.fiit.stuba.sk, FIIT, Bratislava, Vision & Graphics Group. Kalman Filter
 Kalman Filter Published In 1960 by R.E. Kalman The Kalman filter is an efficient recursive filter that estimates the state of a dynamic system from a series of incomplete and noisy measurements. Kalman
Kalman Filter Published In 1960 by R.E. Kalman The Kalman filter is an efficient recursive filter that estimates the state of a dynamic system from a series of incomplete and noisy measurements. Kalman
Travel time uncertainty and network models
 Travel time uncertainty and network models CE 392C TRAVEL TIME UNCERTAINTY One major assumption throughout the semester is that travel times can be predicted exactly and are the same every day. C = 25.87321
Travel time uncertainty and network models CE 392C TRAVEL TIME UNCERTAINTY One major assumption throughout the semester is that travel times can be predicted exactly and are the same every day. C = 25.87321
Antennas and Propagation. Chapter 6b: Path Models Rayleigh, Rician Fading, MIMO
 Antennas and Propagation b: Path Models Rayleigh, Rician Fading, MIMO Introduction From last lecture How do we model H p? Discrete path model (physical, plane waves) Random matrix models (forget H p and
Antennas and Propagation b: Path Models Rayleigh, Rician Fading, MIMO Introduction From last lecture How do we model H p? Discrete path model (physical, plane waves) Random matrix models (forget H p and
Applications of Monte Carlo Methods in Charged Particles Optics
 Sydney 13-17 February 2012 p. 1/3 Applications of Monte Carlo Methods in Charged Particles Optics Alla Shymanska alla.shymanska@aut.ac.nz School of Computing and Mathematical Sciences Auckland University
Sydney 13-17 February 2012 p. 1/3 Applications of Monte Carlo Methods in Charged Particles Optics Alla Shymanska alla.shymanska@aut.ac.nz School of Computing and Mathematical Sciences Auckland University
Transient detection and classification in energy meters. M. Nagaraju, M. Naresh and S. Jayasimha Signion Systems Ltd., Hyderabad
 Transient detection and classification in energy meters M. Nagaraju, M. Naresh and S. Jayasimha Signion Systems Ltd., Hyderabad Abstract Power quality tariffs/ incentives provide an impetus to increased
Transient detection and classification in energy meters M. Nagaraju, M. Naresh and S. Jayasimha Signion Systems Ltd., Hyderabad Abstract Power quality tariffs/ incentives provide an impetus to increased
Report 3. Kalman or Wiener Filters
 1 Embedded Systems WS 2014/15 Report 3: Kalman or Wiener Filters Stefan Feilmeier Facultatea de Inginerie Hermann Oberth Master-Program Embedded Systems Advanced Digital Signal Processing Methods Winter
1 Embedded Systems WS 2014/15 Report 3: Kalman or Wiener Filters Stefan Feilmeier Facultatea de Inginerie Hermann Oberth Master-Program Embedded Systems Advanced Digital Signal Processing Methods Winter
Lecture - 06 Large Scale Propagation Models Path Loss
 Fundamentals of MIMO Wireless Communication Prof. Suvra Sekhar Das Department of Electronics and Communication Engineering Indian Institute of Technology, Kharagpur Lecture - 06 Large Scale Propagation
Fundamentals of MIMO Wireless Communication Prof. Suvra Sekhar Das Department of Electronics and Communication Engineering Indian Institute of Technology, Kharagpur Lecture - 06 Large Scale Propagation
Permutation Editing and Matching via Embeddings
 Permutation Editing and Matching via Embeddings Graham Cormode, S. Muthukrishnan, Cenk Sahinalp (grahamc@dcs.warwick.ac.uk) Permutation Editing and Matching Why study permutations? Distances between permutations
Permutation Editing and Matching via Embeddings Graham Cormode, S. Muthukrishnan, Cenk Sahinalp (grahamc@dcs.warwick.ac.uk) Permutation Editing and Matching Why study permutations? Distances between permutations
Automatic High Dynamic Range Image Generation for Dynamic Scenes
 Automatic High Dynamic Range Image Generation for Dynamic Scenes IEEE Computer Graphics and Applications Vol. 28, Issue. 2, April 2008 Katrien Jacobs, Celine Loscos, and Greg Ward Presented by Yuan Xi
Automatic High Dynamic Range Image Generation for Dynamic Scenes IEEE Computer Graphics and Applications Vol. 28, Issue. 2, April 2008 Katrien Jacobs, Celine Loscos, and Greg Ward Presented by Yuan Xi
Animation Demos. Shows time complexities on best, worst and average case.
 Animation Demos http://cg.scs.carleton.ca/~morin/misc/sortalg/ http://home.westman.wave.ca/~rhenry/sort/ Shows time complexities on best, worst and average case http://vision.bc.edu/~dmartin/teaching/sorting/animhtml/quick3.html
Animation Demos http://cg.scs.carleton.ca/~morin/misc/sortalg/ http://home.westman.wave.ca/~rhenry/sort/ Shows time complexities on best, worst and average case http://vision.bc.edu/~dmartin/teaching/sorting/animhtml/quick3.html
Estimation Theory - ENEL 625 Project as a sub for Assignment Five
 Estimation Theory - ENEL 625 Project as a sub for Assignment Five Moustafa Youssef 30015452 April 25th, 2016 1 Introduction An off-grid solar photovoltaic system is an independent energy system that is
Estimation Theory - ENEL 625 Project as a sub for Assignment Five Moustafa Youssef 30015452 April 25th, 2016 1 Introduction An off-grid solar photovoltaic system is an independent energy system that is
Merge Sort. Note that the recursion bottoms out when the subarray has just one element, so that it is trivially sorted.
 1 of 10 Merge Sort Merge sort is based on the divide-and-conquer paradigm. Its worst-case running time has a lower order of growth than insertion sort. Since we are dealing with subproblems, we state each
1 of 10 Merge Sort Merge sort is based on the divide-and-conquer paradigm. Its worst-case running time has a lower order of growth than insertion sort. Since we are dealing with subproblems, we state each
Kalman Filtering, Factor Graphs and Electrical Networks
 Kalman Filtering, Factor Graphs and Electrical Networks Pascal O. Vontobel, Daniel Lippuner, and Hans-Andrea Loeliger ISI-ITET, ETH urich, CH-8092 urich, Switzerland. Abstract Factor graphs are graphical
Kalman Filtering, Factor Graphs and Electrical Networks Pascal O. Vontobel, Daniel Lippuner, and Hans-Andrea Loeliger ISI-ITET, ETH urich, CH-8092 urich, Switzerland. Abstract Factor graphs are graphical
Animation Demos. Shows time complexities on best, worst and average case.
 Animation Demos http://cg.scs.carleton.ca/~morin/misc/sortalg/ http://home.westman.wave.ca/~rhenry/sort/ Shows time complexities on best, worst and average case http://vision.bc.edu/~dmartin/teaching/sorting/animhtml/quick3.html
Animation Demos http://cg.scs.carleton.ca/~morin/misc/sortalg/ http://home.westman.wave.ca/~rhenry/sort/ Shows time complexities on best, worst and average case http://vision.bc.edu/~dmartin/teaching/sorting/animhtml/quick3.html
k-means Clustering David S. Rosenberg December 15, 2017 Bloomberg ML EDU David S. Rosenberg (Bloomberg ML EDU) ML 101 December 15, / 18
 k-means Clustering David S. Rosenberg Bloomberg ML EDU December 15, 2017 David S. Rosenberg (Bloomberg ML EDU) ML 101 December 15, 2017 1 / 18 k-means Clustering David S. Rosenberg (Bloomberg ML EDU) ML
k-means Clustering David S. Rosenberg Bloomberg ML EDU December 15, 2017 David S. Rosenberg (Bloomberg ML EDU) ML 101 December 15, 2017 1 / 18 k-means Clustering David S. Rosenberg (Bloomberg ML EDU) ML
Efficiency and detectability of random reactive jamming in wireless networks
 Efficiency and detectability of random reactive jamming in wireless networks Ni An, Steven Weber Modeling & Analysis of Networks Laboratory Drexel University Department of Electrical and Computer Engineering
Efficiency and detectability of random reactive jamming in wireless networks Ni An, Steven Weber Modeling & Analysis of Networks Laboratory Drexel University Department of Electrical and Computer Engineering
CG401 Advanced Signal Processing. Dr Stuart Lawson Room A330 Tel: January 2003
 CG40 Advanced Dr Stuart Lawson Room A330 Tel: 23780 e-mail: ssl@eng.warwick.ac.uk 03 January 2003 Lecture : Overview INTRODUCTION What is a signal? An information-bearing quantity. Examples of -D and 2-D
CG40 Advanced Dr Stuart Lawson Room A330 Tel: 23780 e-mail: ssl@eng.warwick.ac.uk 03 January 2003 Lecture : Overview INTRODUCTION What is a signal? An information-bearing quantity. Examples of -D and 2-D
Wireless Sensor Network Assited Fire Detection And Prevention With Classification Algorithms
 International Journal of Emerging Trends in Science and Technology Wireless Sensor Network Assited Fire Detection And Prevention With Classification Algorithms Brinda.s Student of M.Tech Information and
International Journal of Emerging Trends in Science and Technology Wireless Sensor Network Assited Fire Detection And Prevention With Classification Algorithms Brinda.s Student of M.Tech Information and
CSc 110, Spring Lecture 40: Sorting Adapted from slides by Marty Stepp and Stuart Reges
 CSc 110, Spring 2017 Lecture 40: Sorting Adapted from slides by Marty Stepp and Stuart Reges 1 Searching How many items are examined worse case for sequential search? How many items are examined worst
CSc 110, Spring 2017 Lecture 40: Sorting Adapted from slides by Marty Stepp and Stuart Reges 1 Searching How many items are examined worse case for sequential search? How many items are examined worst
Chapter 11. Sampling Distributions. BPS - 5th Ed. Chapter 11 1
 Chapter 11 Sampling Distributions BPS - 5th Ed. Chapter 11 1 Sampling Terminology Parameter fixed, unknown number that describes the population Statistic known value calculated from a sample a statistic
Chapter 11 Sampling Distributions BPS - 5th Ed. Chapter 11 1 Sampling Terminology Parameter fixed, unknown number that describes the population Statistic known value calculated from a sample a statistic
CS510 \ Lecture Ariel Stolerman
 CS510 \ Lecture04 2012-10-15 1 Ariel Stolerman Administration Assignment 2: just a programming assignment. Midterm: posted by next week (5), will cover: o Lectures o Readings A midterm review sheet will
CS510 \ Lecture04 2012-10-15 1 Ariel Stolerman Administration Assignment 2: just a programming assignment. Midterm: posted by next week (5), will cover: o Lectures o Readings A midterm review sheet will
Effective prediction of dynamic bandwidth for exchange of Variable bit rate Video Traffic
 Effective prediction of dynamic bandwidth for exchange of Variable bit rate Video Traffic Mrs. Ch.Devi 1, Mr. N.Mahendra 2 1,2 Assistant Professor,Dept.of CSE WISTM, Pendurthy, Visakhapatnam,A.P (India)
Effective prediction of dynamic bandwidth for exchange of Variable bit rate Video Traffic Mrs. Ch.Devi 1, Mr. N.Mahendra 2 1,2 Assistant Professor,Dept.of CSE WISTM, Pendurthy, Visakhapatnam,A.P (India)
THE use of balanced codes is crucial for some information
 A Construction for Balancing Non-Binary Sequences Based on Gray Code Prefixes Elie N. Mambou and Theo G. Swart, Senior Member, IEEE arxiv:70.008v [cs.it] Jun 07 Abstract We introduce a new construction
A Construction for Balancing Non-Binary Sequences Based on Gray Code Prefixes Elie N. Mambou and Theo G. Swart, Senior Member, IEEE arxiv:70.008v [cs.it] Jun 07 Abstract We introduce a new construction
Divide & conquer. Which works better for multi-cores: insertion sort or merge sort? Why?
 1 Sorting... more 2 Divide & conquer Which works better for multi-cores: insertion sort or merge sort? Why? 3 Divide & conquer Which works better for multi-cores: insertion sort or merge sort? Why? Merge
1 Sorting... more 2 Divide & conquer Which works better for multi-cores: insertion sort or merge sort? Why? 3 Divide & conquer Which works better for multi-cores: insertion sort or merge sort? Why? Merge
Fourier Analysis and Change Detection. Dynamic Network Analysis
 Fourier Analysis and Change Detection Prof. L. Richard Carley carley@ece.cmu.edu 1 Dynamic Network Analysis Key focus Networks change over time Summary statistics typically average all data Useless for
Fourier Analysis and Change Detection Prof. L. Richard Carley carley@ece.cmu.edu 1 Dynamic Network Analysis Key focus Networks change over time Summary statistics typically average all data Useless for
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute. Module 6 Lecture - 37 Divide and Conquer: Counting Inversions
 Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Module 6 Lecture - 37 Divide and Conquer: Counting Inversions Let us go back and look at Divide and Conquer again.
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Module 6 Lecture - 37 Divide and Conquer: Counting Inversions Let us go back and look at Divide and Conquer again.
Entropy, Coding and Data Compression
 Entropy, Coding and Data Compression Data vs. Information yes, not, yes, yes, not not In ASCII, each item is 3 8 = 24 bits of data But if the only possible answers are yes and not, there is only one bit
Entropy, Coding and Data Compression Data vs. Information yes, not, yes, yes, not not In ASCII, each item is 3 8 = 24 bits of data But if the only possible answers are yes and not, there is only one bit
Lectures: Feb 27 + Mar 1 + Mar 3, 2017
 CS420+500: Advanced Algorithm Design and Analysis Lectures: Feb 27 + Mar 1 + Mar 3, 2017 Prof. Will Evans Scribe: Adrian She In this lecture we: Summarized how linear programs can be used to model zero-sum
CS420+500: Advanced Algorithm Design and Analysis Lectures: Feb 27 + Mar 1 + Mar 3, 2017 Prof. Will Evans Scribe: Adrian She In this lecture we: Summarized how linear programs can be used to model zero-sum
Permutations with short monotone subsequences
 Permutations with short monotone subsequences Dan Romik Abstract We consider permutations of 1, 2,..., n 2 whose longest monotone subsequence is of length n and are therefore extremal for the Erdős-Szekeres
Permutations with short monotone subsequences Dan Romik Abstract We consider permutations of 1, 2,..., n 2 whose longest monotone subsequence is of length n and are therefore extremal for the Erdős-Szekeres
Algorithms and Data Structures CS 372. The Sorting Problem. Insertion Sort - Summary. Merge Sort. Input: Output:
 Algorithms and Data Structures CS Merge Sort (Based on slides by M. Nicolescu) The Sorting Problem Input: A sequence of n numbers a, a,..., a n Output: A permutation (reordering) a, a,..., a n of the input
Algorithms and Data Structures CS Merge Sort (Based on slides by M. Nicolescu) The Sorting Problem Input: A sequence of n numbers a, a,..., a n Output: A permutation (reordering) a, a,..., a n of the input
Paper Presentation. Steve Jan. March 5, Virginia Tech. Steve Jan (Virginia Tech) Paper Presentation March 5, / 28
 Paper Presentation Steve Jan Virginia Tech March 5, 2015 Steve Jan (Virginia Tech) Paper Presentation March 5, 2015 1 / 28 2 paper to present Nonparametric Multi-group Membership Model for Dynamic Networks,
Paper Presentation Steve Jan Virginia Tech March 5, 2015 Steve Jan (Virginia Tech) Paper Presentation March 5, 2015 1 / 28 2 paper to present Nonparametric Multi-group Membership Model for Dynamic Networks,
CSE 100: BST AVERAGE CASE AND HUFFMAN CODES
 CSE 100: BST AVERAGE CASE AND HUFFMAN CODES Recap: Average Case Analysis of successful find in a BST N nodes Expected total depth of all BSTs with N nodes Recap: Probability of having i nodes in the left
CSE 100: BST AVERAGE CASE AND HUFFMAN CODES Recap: Average Case Analysis of successful find in a BST N nodes Expected total depth of all BSTs with N nodes Recap: Probability of having i nodes in the left
A Brief Introduction to Information Theory and Lossless Coding
 A Brief Introduction to Information Theory and Lossless Coding 1 INTRODUCTION This document is intended as a guide to students studying 4C8 who have had no prior exposure to information theory. All of
A Brief Introduction to Information Theory and Lossless Coding 1 INTRODUCTION This document is intended as a guide to students studying 4C8 who have had no prior exposure to information theory. All of
Cognitive Radar Experiments At The Ohio State University. Graeme E. Smith The OSU ElectroScience Lab
 Cognitive Radar Experiments At The Ohio State University Graeme E. Smith The OSU ElectroScience Lab All Radar Systems Are Cognitive Consider an air traffic control radar The turn-and-burn sensor is not
Cognitive Radar Experiments At The Ohio State University Graeme E. Smith The OSU ElectroScience Lab All Radar Systems Are Cognitive Consider an air traffic control radar The turn-and-burn sensor is not
SSB Debate: Model-based Inference vs. Machine Learning
 SSB Debate: Model-based nference vs. Machine Learning June 3, 2018 SSB 2018 June 3, 2018 1 / 20 Machine learning in the biological sciences SSB 2018 June 3, 2018 2 / 20 Machine learning in the biological
SSB Debate: Model-based nference vs. Machine Learning June 3, 2018 SSB 2018 June 3, 2018 1 / 20 Machine learning in the biological sciences SSB 2018 June 3, 2018 2 / 20 Machine learning in the biological
Population Structure and Genealogies
 Population Structure and Genealogies One of the key properties of Kingman s coalescent is that each pair of lineages is equally likely to coalesce whenever a coalescent event occurs. This condition is
Population Structure and Genealogies One of the key properties of Kingman s coalescent is that each pair of lineages is equally likely to coalesce whenever a coalescent event occurs. This condition is
Efficient RFID Data Cleaning Method
 TELKOMNIKA, Vol.11, No.3, March 2013, pp. 1707~ 1713 e-issn: 2087-278X 1707 Efficient RFID Data Cleaning Method Li Xing, Fu Wen-Xiu School of Electronic and Information Engineering, Beijing Jiaotong University.
TELKOMNIKA, Vol.11, No.3, March 2013, pp. 1707~ 1713 e-issn: 2087-278X 1707 Efficient RFID Data Cleaning Method Li Xing, Fu Wen-Xiu School of Electronic and Information Engineering, Beijing Jiaotong University.
Supplementary Materials for
 advances.sciencemag.org/cgi/content/full/1/11/e1501057/dc1 Supplementary Materials for Earthquake detection through computationally efficient similarity search The PDF file includes: Clara E. Yoon, Ossian
advances.sciencemag.org/cgi/content/full/1/11/e1501057/dc1 Supplementary Materials for Earthquake detection through computationally efficient similarity search The PDF file includes: Clara E. Yoon, Ossian
Honors Algebra 2 Assignment Sheet - Chapter 1
 Assignment Sheet - Chapter 1 #01: Read the text and the examples in your book for the following sections: 1.1, 1., and 1.4. Be sure you read and understand the handshake problem. Also make sure you copy
Assignment Sheet - Chapter 1 #01: Read the text and the examples in your book for the following sections: 1.1, 1., and 1.4. Be sure you read and understand the handshake problem. Also make sure you copy
TSIN01 Information Networks Lecture 9
 TSIN01 Information Networks Lecture 9 Danyo Danev Division of Communication Systems Department of Electrical Engineering Linköping University, Sweden September 26 th, 2017 Danyo Danev TSIN01 Information
TSIN01 Information Networks Lecture 9 Danyo Danev Division of Communication Systems Department of Electrical Engineering Linköping University, Sweden September 26 th, 2017 Danyo Danev TSIN01 Information
Data processing framework for decision making
 Data processing framework for decision making Jan Larsen Intelligent Signal Processing Group Department of Informatics and Mathematical Modelling Technical University of Denmark jl@imm.dtu.dk, www.imm.dtu.dk/~jl
Data processing framework for decision making Jan Larsen Intelligent Signal Processing Group Department of Informatics and Mathematical Modelling Technical University of Denmark jl@imm.dtu.dk, www.imm.dtu.dk/~jl
Link State Routing. Brad Karp UCL Computer Science. CS 3035/GZ01 3 rd December 2013
 Link State Routing Brad Karp UCL Computer Science CS 33/GZ 3 rd December 3 Outline Link State Approach to Routing Finding Links: Hello Protocol Building a Map: Flooding Protocol Healing after Partitions:
Link State Routing Brad Karp UCL Computer Science CS 33/GZ 3 rd December 3 Outline Link State Approach to Routing Finding Links: Hello Protocol Building a Map: Flooding Protocol Healing after Partitions:
GIDE: Graphical Image Deblurring Exploration
 GIDE: Graphical Image Deblurring Exploration Brianna R. Cash and Dianne P. O Leary We explore the use of a Matlab tool called gide that allows useraided deblurring of images. gide helps practitioners restore
GIDE: Graphical Image Deblurring Exploration Brianna R. Cash and Dianne P. O Leary We explore the use of a Matlab tool called gide that allows useraided deblurring of images. gide helps practitioners restore
Small power load disaggregation in office buildings based on electrical signature classification
 Small power load disaggregation in office buildings based on electrical signature classification Conference or Workshop Item Accepted Version Rodriguez, A., Smith, S. T., Kiff, A. and Potter, B. (2016)
Small power load disaggregation in office buildings based on electrical signature classification Conference or Workshop Item Accepted Version Rodriguez, A., Smith, S. T., Kiff, A. and Potter, B. (2016)
Research Article n-digit Benford Converges to Benford
 International Mathematics and Mathematical Sciences Volume 2015, Article ID 123816, 4 pages http://dx.doi.org/10.1155/2015/123816 Research Article n-digit Benford Converges to Benford Azar Khosravani and
International Mathematics and Mathematical Sciences Volume 2015, Article ID 123816, 4 pages http://dx.doi.org/10.1155/2015/123816 Research Article n-digit Benford Converges to Benford Azar Khosravani and
PROCESS-VOLTAGE-TEMPERATURE (PVT) VARIATIONS AND STATIC TIMING ANALYSIS
 PROCESS-VOLTAGE-TEMPERATURE (PVT) VARIATIONS AND STATIC TIMING ANALYSIS The major design challenges of ASIC design consist of microscopic issues and macroscopic issues [1]. The microscopic issues are ultra-high
PROCESS-VOLTAGE-TEMPERATURE (PVT) VARIATIONS AND STATIC TIMING ANALYSIS The major design challenges of ASIC design consist of microscopic issues and macroscopic issues [1]. The microscopic issues are ultra-high
Information Management course
 Università degli Studi di Mila Master Degree in Computer Science Information Management course Teacher: Alberto Ceselli Lecture 19: 10/12/2015 Data Mining: Concepts and Techniques (3rd ed.) Chapter 8 Jiawei
Università degli Studi di Mila Master Degree in Computer Science Information Management course Teacher: Alberto Ceselli Lecture 19: 10/12/2015 Data Mining: Concepts and Techniques (3rd ed.) Chapter 8 Jiawei
LECTURE VI: LOSSLESS COMPRESSION ALGORITHMS DR. OUIEM BCHIR
 1 LECTURE VI: LOSSLESS COMPRESSION ALGORITHMS DR. OUIEM BCHIR 2 STORAGE SPACE Uncompressed graphics, audio, and video data require substantial storage capacity. Storing uncompressed video is not possible
1 LECTURE VI: LOSSLESS COMPRESSION ALGORITHMS DR. OUIEM BCHIR 2 STORAGE SPACE Uncompressed graphics, audio, and video data require substantial storage capacity. Storing uncompressed video is not possible
COMP Online Algorithms. Paging and k-server Problem. Shahin Kamali. Lecture 11 - Oct. 11, 2018 University of Manitoba
 COMP 7720 - Online Algorithms Paging and k-server Problem Shahin Kamali Lecture 11 - Oct. 11, 2018 University of Manitoba COMP 7720 - Online Algorithms Paging and k-server Problem 1 / 19 Review & Plan
COMP 7720 - Online Algorithms Paging and k-server Problem Shahin Kamali Lecture 11 - Oct. 11, 2018 University of Manitoba COMP 7720 - Online Algorithms Paging and k-server Problem 1 / 19 Review & Plan
Students: Avihay Barazany Royi Levy Supervisor: Kuti Avargel In Association with: Zoran, Haifa
 Students: Avihay Barazany Royi Levy Supervisor: Kuti Avargel In Association with: Zoran, Haifa Spring 2008 Introduction Problem Formulation Possible Solutions Proposed Algorithm Experimental Results Conclusions
Students: Avihay Barazany Royi Levy Supervisor: Kuti Avargel In Association with: Zoran, Haifa Spring 2008 Introduction Problem Formulation Possible Solutions Proposed Algorithm Experimental Results Conclusions
Scheduling and Communication Synthesis for Distributed Real-Time Systems
 Scheduling and Communication Synthesis for Distributed Real-Time Systems Department of Computer and Information Science Linköpings universitet 1 of 30 Outline Motivation System Model and Architecture Scheduling
Scheduling and Communication Synthesis for Distributed Real-Time Systems Department of Computer and Information Science Linköpings universitet 1 of 30 Outline Motivation System Model and Architecture Scheduling
DeepStack: Expert-Level AI in Heads-Up No-Limit Poker. Surya Prakash Chembrolu
 DeepStack: Expert-Level AI in Heads-Up No-Limit Poker Surya Prakash Chembrolu AI and Games AlphaGo Go Watson Jeopardy! DeepBlue -Chess Chinook -Checkers TD-Gammon -Backgammon Perfect Information Games
DeepStack: Expert-Level AI in Heads-Up No-Limit Poker Surya Prakash Chembrolu AI and Games AlphaGo Go Watson Jeopardy! DeepBlue -Chess Chinook -Checkers TD-Gammon -Backgammon Perfect Information Games
Jitter in Digital Communication Systems, Part 1
 Application Note: HFAN-4.0.3 Rev.; 04/08 Jitter in Digital Communication Systems, Part [Some parts of this application note first appeared in Electronic Engineering Times on August 27, 200, Issue 8.] AVAILABLE
Application Note: HFAN-4.0.3 Rev.; 04/08 Jitter in Digital Communication Systems, Part [Some parts of this application note first appeared in Electronic Engineering Times on August 27, 200, Issue 8.] AVAILABLE
Math 58. Rumbos Fall Solutions to Exam Give thorough answers to the following questions:
 Math 58. Rumbos Fall 2008 1 Solutions to Exam 2 1. Give thorough answers to the following questions: (a) Define a Bernoulli trial. Answer: A Bernoulli trial is a random experiment with two possible, mutually
Math 58. Rumbos Fall 2008 1 Solutions to Exam 2 1. Give thorough answers to the following questions: (a) Define a Bernoulli trial. Answer: A Bernoulli trial is a random experiment with two possible, mutually
Module 8. Some multi-sample examples. Prof. Stephen B. Vardeman Statistics and IMSE Iowa State University. March 5, 2008
 Module 8 Some multi-sample examples Prof. Stephen B. Vardeman Statistics and IMSE Iowa State University March 5, 2008 Steve Vardeman (ISU) Module 8 March 5, 2008 1 / 23 Example 7 We finish up with a couple
Module 8 Some multi-sample examples Prof. Stephen B. Vardeman Statistics and IMSE Iowa State University March 5, 2008 Steve Vardeman (ISU) Module 8 March 5, 2008 1 / 23 Example 7 We finish up with a couple
CODING TECHNIQUES FOR ANALOG SOURCES
 CODING TECHNIQUES FOR ANALOG SOURCES Prof.Pratik Tawde Lecturer, Electronics and Telecommunication Department, Vidyalankar Polytechnic, Wadala (India) ABSTRACT Image Compression is a process of removing
CODING TECHNIQUES FOR ANALOG SOURCES Prof.Pratik Tawde Lecturer, Electronics and Telecommunication Department, Vidyalankar Polytechnic, Wadala (India) ABSTRACT Image Compression is a process of removing
Virtual Digital Control Experimental System
 Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 205, 9, 329-334 329 Virtual Digital Control Experimental System Open Access Yumin Chen,*, Liyong Ma, Xianmin
Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 205, 9, 329-334 329 Virtual Digital Control Experimental System Open Access Yumin Chen,*, Liyong Ma, Xianmin
Characteristics of Routes in a Road Traffic Assignment
 Characteristics of Routes in a Road Traffic Assignment by David Boyce Northwestern University, Evanston, IL Hillel Bar-Gera Ben-Gurion University of the Negev, Israel at the PTV Vision Users Group Meeting
Characteristics of Routes in a Road Traffic Assignment by David Boyce Northwestern University, Evanston, IL Hillel Bar-Gera Ben-Gurion University of the Negev, Israel at the PTV Vision Users Group Meeting
Introduction to Spring 2009 Artificial Intelligence Final Exam
 CS 188 Introduction to Spring 2009 Artificial Intelligence Final Exam INSTRUCTIONS You have 3 hours. The exam is closed book, closed notes except a two-page crib sheet, double-sided. Please use non-programmable
CS 188 Introduction to Spring 2009 Artificial Intelligence Final Exam INSTRUCTIONS You have 3 hours. The exam is closed book, closed notes except a two-page crib sheet, double-sided. Please use non-programmable
