A Routing Approach to Jamming Effects Mitigation in Wireless Multihop Networks. by Umang Sureshbhai Patel
|
|
|
- Erin Hunt
- 5 years ago
- Views:
Transcription
1 ABSTRACT PATEL, UMANG SURESHBHAI. A Routing Approach to Jamming Effects Mitigation in Wireless Multihop Networks. (Under the direction of Dr. Rudra Dutta.) Wireless networks are susceptible to radio jamming attacks, due to the shared nature of wireless medium. Radio jamming refers to the intentional act of emitting radio signals on the spectrum used by a wireless network, in order to disrupt wireless communication among network nodes. Radio jamming causes wireless link failures and disrupts network traffic. Radio jamming is often viewed as a special type of DoS (Denial of Service) attack on wireless networks. Jamming mitigation research is typically focused on improving jamming resistance at physical and MAC (Medium Access and Control) layers. Although jamming mitigation at physical and MAC layers is effective, it often comes with added complexities and typically requires specialized hardware. In this thesis work, we have focused on a generally applicable routing approach for mitigating jamming effects on the network traffic. We are proposing (1) proactive protection and (2) reactive protection techniques at the network layer for jamming effects mitigation in wireless multihop networks with fixed nodes. The goal of proactive protection is to prevent network traffic from the disruptions caused by jamming. Proactive protection is applicable when jamming conditions in the network (e.g. jammer s power, number of jammers) are known to network nodes. We have developed a multipath routing and power control approach for proactive protection against jamming. In this approach, data is routed redundantly on node disjoint paths to increase resistance against jamming. Power control is performed on the links of the node disjoint paths to defend against simultaneous jamming of the node disjoint paths. We have developed an algorithm that selects a node disjoint path pair from all available node disjoint paths, such that total power assigned to defend a jammer is minimum for the path pair. We have shown how to embed this algorithm on a table driven multipath routing scheme and on an on-demand multipath routing scheme. We have evaluated performance of the algorithm using OPNET simulations. The goal of reactive protection is to restore network traffic which has been disrupted by jamming. Reactive protection is applicable when jamming conditions in the network are unknown to network nodes. In reactive protection, alternative route to the destination node is discovered on-the-fly, when any link on the path from a source to a destination fails due to jamming. We have developed a distributed geographic routing algorithm that finds alternative route to the destination, starting from the first node with failed link on the original path. We have evaluated performance of the algorithm on different topologies.
2 A Routing Approach to Jamming Effects Mitigation in Wireless Multihop Networks by Umang Sureshbhai Patel A thesis submitted to the Graduate Faculty of North Carolina State University in partial fulfillment of the requirements for the Degree of Master of Science Computer Science Raleigh, North Carolina 2010 APPROVED BY: Dr. Peng Ning Dr. Injong Rhee Dr. Rudra Dutta Chair of Advisory Committee
3 DEDICATION To my parents Suresh & Harshida, my grandparents Natwarlal & Pushpa, my brother Mehal, and my fiancée Kanan. ii
4 BIOGRAPHY Umang Patel was born in Ahmedabad, India in He graduated with Bachelor of Engineering (BE) degree in Computer Engineering from L.D. College of Engineering (affiliated with Gujarat University) in From 2005 to 2008, he worked for Sasken Communications Technologies as a Software Engineer in various embedded software projects. He then joined North Carolina State University in fall, 2008 to pursue Master of Science (MS) degree in Computer Science. He worked as an Engineering Intern with the WLAN chipset design group at QualComm Inc. from May, 2009 to December, iii
5 ACKNOWLEDGEMENTS I am grateful to my advisor Dr. Rudra Dutta for invaluable guidance. I admire him a lot, both as an advisor and as a person. I am thankful to Dr. Peng Ning and Dr. Injong Rhee for serving on my advisory committee and for providing valuable suggestions. I am deeply grateful to my wonderful family. My graduate studies in US would not have been possible without my family s great support, love and sacrifices they made. Parth, my friend since undergrad days, is pursuing PhD at NCSU. He has helped me a lot in numerous ways. Thank you, Parth! iv
6 TABLE OF CONTENTS List of Tables vi List of Figures vii Chapter 1 Introduction Motivation Contributions Chapter 2 Related Work Jamming Classification Jamming Detection and Mitigation Chapter 3 Jamming Effects Modeling R n Propagation Model Jamming-to-Signal Ratio (JSR) Jamming Vulnerability of a Link Jamming Vulnerability of a Path Chapter 4 Proactive Protection against Jamming Multipath Routing and Power Control Approach Algorithm for Preplanned Protection Terminology Algorithm Description Complexity Embedding the Algorithm Non-linear Programming for Optimal Power Assignments Chapter 5 Reactive Protection against Jamming Link Failure Detection Algorithm for finding an Alternate Path Packets Formats Terminology Algorithm Description Chapter 6 Evaluations and Results Algorithm 1 Evaluations OPNET Simulation Design Simulations and Results Algorithm 2 Evaluations Chapter 7 Conclusions and Future Work Future Work References Appendix Appendix A An Example of Optimal Power Assignments using NLP v
7 LIST OF TABLES Table 4.1 Algorithm 1 Terminology Table 4.2 NLP Formulation Terminology Table 5.1 Algorithm 2 Terminology Table 6.1 Algorithm 1 Parameters for Simulations Table A.1 NLP Solution Variables vi
8 LIST OF FIGURES Figure 2.1 (a) Channelized Spectrum, Jamming Strategies: (b) Full Band Jamming, (c) Continuous Partial Band Jamming, (d) Noncontiguous Partial Band Jamming, (e) Narrowband Noise Jamming, (f) Single-tone Jamming and (g) Multi-tone Jamming Figure 3.1 Jamming Vulnerability of a Link Figure 3.2 Jamming Vulnerability of a Path Figure 4.1 Multipath Routing and Power Control Approach Figure 4.2 Embedding the Algorithm 1 (Step 1) Figure 4.3 Embedding the Algorithm 1 (Step 2) Figure 4.4 Embedding the Algorithm 1 (Step 3) Figure 5.1 Algorithm 2 Packets Formats Figure 5.2 Algorithm 2 Example Figure 6.1 Simulation Steps Figure 6.2 Modified DSR source route option Figure 6.3 Grid Topology, Node Disjoint Path Pairs for the Traffic Flows Figure 6.4 Grid Topology, Shortest Paths for Traffic Flows Figure 6.5 Grid Topology, Randomly Moving Jammer in the Network, Jammer s Power watt Figure 6.6 Grid Topology, Randomly Moving Jammer, Jammer s Power watt. 42 Figure 6.7 Grid Topology, Stationary Jammer Near Node 41, Jammer s Power watt Figure 6.8 Grid Topology, Stationary Jammer Near Node 41, Jammer s Power watt Figure 6.9 Grid Topology, Stationary Jammer Near Node 11, Jammer s Power watt Figure 6.10 Grid Topology, Stationary Jammer Near Node 11, Jammer s Power watt Figure 6.11 Grid Topology, Stationary Jammer Near Node 17, Jammer s Power watt Figure 6.12 Grid Topology, Stationary Jammer Near Node 17, Jammer s Power watt Figure 6.13 Grid Topology, Stationary Jammer Near Node 65, Jammer s Power watt Figure 6.14 Grid Topology, Stationary Jammer Near Node 65, Jammer s Power watt Figure 6.15 Grid Topology, Stationary Jammer Near Node 71, Jammer s Power watt Figure 6.16 Grid Topology, Stationary Jammer Near Node 71, Jammer s Power watt vii
9 Figure 6.17 Grid Topology, No Jammer Figure 6.18 Randomly Perturbed Grid Topology, Node Disjoint Path Pairs for Traffic Flows Figure 6.19 Randomly Perturbed Grid Topology, Shortest Paths for Traffic Flows.. 50 Figure 6.20 Randomly Perturbed Grid Topology, Randomly Moving Jammer, Jammer s Power watt Figure 6.21 Randomly Perturbed Grid Topology, Randomly Moving Jammer, Jammer s Power watt Figure 6.22 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 41, Jammer s Power watt Figure 6.23 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 41, Jammer s Power watt Figure 6.24 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 11, Jammer s Power watt Figure 6.25 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 11, Jammer s Power watt Figure 6.26 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 17, Jammer s Power watt Figure 6.27 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 17, Jammer s Power watt Figure 6.28 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 65, Jammer s Power watt Figure 6.29 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 65, Jammer s Power watt Figure 6.30 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 71, Jammer s Power watt Figure 6.31 Randomly Perturbed Grid Topology, Stationary Jammer Near Node 71, Jammer s Power watt Figure 6.32 Randomly Perturbed Grid Topology, No Jammer Figure 6.33 Topology 1 for Algorithm 2 Evaluation Figure 6.34 Algorithm 2 Results for Topology Figure 6.35 Topology 2 for Algorithm 2 Evaluation Figure 6.36 Algorithm 2 Results for Topology Figure 6.37 Topology 3 for Algorithm 2 Evaluation Figure 6.38 Algorithm 2 Results for Topology Figure A.1 Example Problem for NLP Figure A.2 Power Assignments by NLP viii
10 Chapter 1 Introduction We consider wireless multihop networks with fixed nodes in our study. Wireless communication in such networks is susceptible to radio jamming attacks due to the shared nature of wireless medium. Radio jamming refers to the intentional act of emitting radio signals on the spectrum used by a wireless network, in order to disrupt wireless communication among network nodes. Radio jamming causes wireless link failures and disrupts network traffic. Radio jamming is a serious security threat and it is often viewed as a DoS (Denial of Service) attack. Radio jamming has immediate and direct impact on the physical and MAC (Medium Access and Control) layers functionalities. For example, higher background noise caused by jamming, adversely affects packet reception at physical layer. Packet delivery ratio at MAC layer drops significantly in the presence of powerful jamming. Therefore, jamming effects mitigation research is typically focused on the MAC and physical layers enhancements to defend jamming. For example, spread spectrum techniques at physical layer such as DSSS (Direct Sequence Spread Spectrum) and FHSS (Frequency Hopping Spread Spectrum) improve robustness of wireless communication in the presence of narrow band noise. However, in the section 1.1, we present reasons for considering network layer solution for mitigating jamming effects on the network traffic. 1.1 Motivation DSSS and FHSS are widely used physical layer techniques for jamming resistant wireless communication [15]. Also, various MAC layer enhancements (e.g. [23],[11],[10],[26]) are proposed in the research literature for increasing jamming resistance of a wireless link. However, physical and MAC layers enhancements cannot defend jamming beyond a certain limit. For example, IEEE b based devices can be jammed by a relatively low power jammer, even though IEEE b has DSSS physical layer. For each data rate in the IEEE b, experiments in [9] show that received Packet Error Rate (PER) becomes 1 and wireless link fails completely 1
11 for a relatively low threshold of Jamming-to-signal power ratio (JSR) at the receiver. [8] also shows that IEEE b DSSS physical layer has poor jamming margin. Experiments in [9] show that IEEE g physical layer based on the Orthogonal Frequency Division Multiplexing (OFDM) cannot operate at any data rate when jamming signal becomes stronger than the desired signal at the receiver. [13] shows that protecting IEEE communication using FHSS in the 2.4 and 5 GHz Industrial, Scientific and Medical (ISM) bands is not effective against sweep jamming. It is becoming relatively easy to build a sophisticated radio jammer due to the availability of configurable radio platforms such as GNU Radio, Cognitive Radio etc. Cognitive radio provides advanced capabilities such as real-time spectrum sensing, fast channel switching and software control for radio operations. Simulations results in [17] show that a single jammer using a cognitive radio can jam multiple channels using the fast channel switching capability and it poses a serious threat to the wireless networks that rely on the channel switching to defend jamming. Although jamming is illegal in many countries, wide band jamming devices for popular technologies such as IEEE , Bluetooth and ZigBee are available for purchase on many websites. (e.g. [1]). [7] and [8] consider impact of jamming on the network connectivity and throughput. Simulations results in [8] show that a jammer using higher power than target network nodes causes substantial number of links failures and network loses its connectivity. Simulations results in [7] show that large number of distributed, low power jammers in the target network area causes substantial reduction in the network throughput and increases end-to-end delay in the network. Distributed low power jammers are energy efficient, hard to detect and they can survive for a long time. These studies suggest that it is important to consider jamming effects not only at physical and MAC layers, but also at network layer. Moreover, effective jamming defense techniques at MAC and physical layers typically requires hardware enhancements [12] and hence they cannot be deployed easily to the existing networks. Based on the above finding, we have focused on a generally applicable routing approach for mitigating jamming effects in wireless multihop networks with fixed nodes. 1.2 Contributions We have made the following contributions in this thesis. 1. We have identified a link failure model to represent jamming effects that is pertinent to the network layer. In this model, each unidirectional wireless link in a network has jamming vulnerable area around the receiver. Jammer s presence in this area causes the link failure. 2
12 Jamming vulnerable area is considered circular under simple constant range model. Jamming vulnerable area is termed as a Jamming Circle. Jamming circle radius is derived from the JSR formula based on the R n propagation model. Based on this link failure mode, jamming vulnerability of a path is given by the total area occupied by the jamming circles of all links on the path. Chapter 3 discusses jamming effects modeling in detail. 2. Wireless network survivability techniques for defending jamming can be classified in two categories: (1) proactive protection and (2) reactive protection. The goal of proactive protection is to prevent network traffic from the disruptions caused by jamming. The goal of reactive protection is to restore network traffic which has been disrupted by jamming. Proactive protection technique is applicable when jamming conditions in the network (e.g. jammer s max power, number of jammers etc.) are known to network nodes. Reactive protection is applicable when jamming conditions in the network are unknown to network nodes. We have developed proactive protection and reactive protection techniques at network layer, for defending jamming. 3. We have developed a multipath routing and power control approach for proactive protection against jamming. In this approach, data is routed redundantly on node disjoint paths from a source to a destination for increasing resistance against jamming. Power control is performed on the links of node disjoint paths to defend against simultaneous jamming of the node disjoint paths. We have developed an algorithm that selects a node disjoint path pair from all available node disjoint paths, such that total power required to defend a jammer is minimum for the path pair. We have shown how to embed this algorithm on a table driven multipath routing scheme and on an on-demand multipath routing scheme. We have evaluated performance of the algorithm by doing simulations in OPNET [2]. Chapter 4 describes the proactive protection technique in detail. Chapter 6 presents simulations results. 4. In reactive protection, alternative route to the destination node is discovered on-the-fly, when any link on the path from a source to a destination fails due to jamming. We have developed a distributed geographic routing algorithm that finds alternative route to the destination, starting from the first node with failed link on the original path. We have evaluated performance of this algorithm on different topologies. Chapter 5 describes the reactive protection technique in detail. Chapter 6 presents simulations results. 3
13 Chapter 2 Related Work We review and summarize some of the research literature on wireless jamming classification, detection and mitigation. 2.1 Jamming Classification Poisel in the book [15] described the following jamming strategies, based on the channelized spectrum shown in the figure 2.1(a). Broadband Noise (BBN) jamming: BBN jamming (figure 2.1(b)) places noise on the entire frequency spectrum used by the target network radios. It is also called full band or barrage jamming. Partial-band Noise (PBN) jamming: PBN jamming places noise on multiple channels of the spectrum used by the target network radios. These channels can be continuous (figure 2.1(c)) or non-continuous(figure 2.1(d)). Narrowband Noise (NBN) jamming: NBN jamming places noise on a single channel from the spectrum used by the target network radios. Tone jamming: In tone jamming, single jamming tone(figure 2.1(e)) or multiple jamming tones(figure 2.1(f)) are placed strategically, on the spectrum used by the target network radios. Number of tones and their placements have significant impact on jamming performance. [15] discusses BER (Bit Error Rate) performance of the above jamming strategies on DSSS and FHSS systems in detail. 4
14 Channel Amplitude (a) Frequency Amplitude (b) Frequency Amplitude (c) Frequency Amplitude (d) Frequency Amplitude (e) Frequency Amplitude (f) Frequency Amplitude (g) Frequency Figure 2.1: (a) Channelized Spectrum, Jamming Strategies: (b) Full Band Jamming, (c) Continuous Partial Band Jamming, (d) Noncontiguous Partial Band Jamming, (e) Narrowband Noise Jamming, (f) Single-tone Jamming and (g) Multi-tone Jamming Xu et al. in the paper [25] classified jammers in the following four categories. Constant jammer: Constant jammer continuously emits noise like radio signals for keeping the channel busy and for disrupting wireless communication on the channel. Random jammer: Random jammer alternates between sleeping and jamming on the channel. Random jammer can achieve power saving and different levels of jamming effectiveness by adjusting the amount of sleep and the jamming period. Reactive jammer: Reactive jammer listens to the channel for activity from the target network. It transmits noise like signal as soon as there is some activity on the channel, in order to corrupt the transmitted packet. Deceptive jammer: Deceptive jammer floods the network with bogus packets that seem like regular packets. Deceptive jammers are hard to detect; they consume bandwidth and they can cause unnecessary computations on the network nodes. They are also called Intelligent 5
15 Jammers. Intelligent jammers require some knowledge about the target network protocols for jamming attacks. 2.2 Jamming Detection and Mitigation [25] focuses on the analysis and detection of jamming signals by performing various experiments using three MICA2 motes (one sender, one receiver and one jammer). Experiments results from the paper show that jammer s presence cannot be concluded definitively by using simple statistics (e.g. energy on channel, carrier sensing time, Packet Delivery Ratio (PDR)) individually. [25] also shows that time varying analysis (spectral analysis) of the channel using techniques such as Higher Order Crossings do not work in some jamming scenarios. Two enhanced jamming detection algorithms are proposed and evaluated in [25]. These algorithms first use PDR to classify links which have poor utility and then use consistency check based on the signal strength information or based on the location information to detect jammer s presence. Empirical results show that both the algorithms work reliably for different jamming attack models. [22] proposes a distributed jamming area mapping protocol for the boundary nodes of a jammed region in the network. Jamming area mapped by the algorithm is useful for other network services (e.g. routing) to avoid the jammed region. The algorithm maps jammed region in about 1 to 5 seconds and it is robust against links failure rates as high as 25%. [20] and [21] highlights jamming vulnerability of IEEE b and e MAC layers. Simulation results from the paper shows that MAC parameters (e.g. contention window size) can be tweaked within the standard imposed limit such that a compromised network node can consume much of the available bandwidth and it can starve other network nodes, without getting detected. [11] devises very effective and energy efficient algorithms for intelligent jamming against popular WSN (Wireless Sensor Network) MAC protocols: L-MAC, S-MAC and B-MAC. [11] proposes high duty cycle for S-MAC and shorter data packets for L-MAC to increase their resistance against link layer jamming. L-MAC fares better than S-MAC and B-MAC in terms of jamming resistance. Comprehensive study in this paper suggests that no effective link layer countermeasures are possible for typical WSNs in use today. [23] proposes and evaluates new MAC layer protocol DEEJAM to defend jammers based on the IEEE based radio hardware. The following techniques are used in DEEJAM to defend such jammers. (1) Frame masking: sender and receiver changes SFD (Start Frame Delimiter) in each packet using the pre-shared secret pseudorandom sequence. On the jammer, IEEE based radio silently discards packets as they do not match with fixed SFD. 6
16 So, this technique defends interrupt jamming in which a jammer initiates jamming only upon packet reception indication from the radio hardware. (2) Frequency hopping: this technique defends jammers that use RSSI (Received Signal Strength Indicator) threshold based trigger to initiate jamming. (3) Frequency hopping and packet fragmentation: this technique defends scan jamming when scanning rate is less than hopping rate. Short packets reduce dwelve time at each hop and thus reduce detection chances. (4) Frequency hopping, packet fragmentation and redundant coding: this technique is effective when a jammer performs random pulse jamming on the spectrum used by the target radio. Redundant coding helps a receiver to recover corrupted fragments. [26] proposes channel surfing and spatial retreat techniques for jamming defense. Channel surfing is an adaptive FHSS. Node moves to a different and orthogonal frequency only when it discovers that current frequency is jammed. Spatial retreat is an algorithm that specifies how two communicating nodes can move away from the jammed region. Spatial retreat algorithm is applicable to the networks with mobile nodes. [24] shows by experiments that jamming effects in a network is not isotropic. Jamming vulnerability of a link is highly dependent on the distances among source, destination and jammer. [24] also suggests that per link power control is useful in defending jamming. [18] performs systematic study of bit and packet level corruptions caused by jamming. [18] uses multiple hardware platforms, multiple transmission power levels, various node placements and different communication contents in the experiments. [18] shows that it is easy for a jammer to choose a location and a power level for corrupting a bit or a packet transmitted from a given source to a given destination. It is easy for a receiver to detect corruptions at packet level, but it is hard for a receiver to detect corruptions at individual bits level. It is also hard for a receiver to recover corrupted bits even if the receiver knows the bit values used in the jammer s packets. 7
17 Chapter 3 Jamming Effects Modeling Many research papers (e.g.[22]) have modeled jamming effects in a wireless network as a jammed region around the jammer. Network nodes in the jammed region finds the medium busy all the time due to higher energy (noise) on the medium. They do not get any transmission opportunity and they lose connectivity to the rest of the network. Jamming effects modeling in this way is not accurate for all networks. For example, jammed region model is applicable to the networks which use fixed energy threshold for CCA (Clear Channel Assessment). But the model is not accurate for the networks which use adaptive energy threshold for CCA, or for the networks in which CCA is based on the valid signal reception (e.g. IEEE CCA mode 2 [3]). In this chapter, we present a better way to model jamming effects, pertinent to the network layer. We have modeled jamming effects for each unidirectional link in the network individually. We find jamming vulnerable region for each link in the network using the Jamming-to-Signal Ratio (JSR) formula based on the R n propagation model. Jamming vulnerability a path is given by the jamming vulnerable regions of all links on the path. We discuss R n propagation model in the section 3.1. JSR based on the R n propagation model is discussed in the section 3.2. Jamming vulnerability of a link and jamming vulnerability of a path are discussed in the sections 3.3 and 3.4 respectively. 3.1 R n Propagation Model Both theoretical and empirical results show that average received signal power decreases exponentially with the increase in distance between a transmitter and a receiver. [16]. As per the R n propagation model, path loss at a receiver with the distance d from a transmitter is given by the equation 3.1. ( ) d n P L(dB) = P L(d 0 ) + 10 log 10 (3.1) d 0 8
18 where d 0 is a reference point near the transmitter with known path loss P L(d 0 ), n is the path loss exponent which indicates the rate at which path loss increases with the distance. Absolute received power based on the R n propagation model is given by the equation 3.2 [15]. P R = P T G T G R 10 (P L(d 0)+10 log 10 (d/d 0 ) n )/10 (3.2) where P R is received power, P T is transmit power, G T is transmit antenna gain, G R is receive antenna gain and other terms have the same meaning as in the path loss equation 3.1. We have chosen R n propagation model because it is widely applicable to the indoor and outdoor environments by choosing an appropriate path loss exponent. 3.2 Jamming-to-Signal Ratio (JSR) The jamming power to signal power ratio (JSR) at the receiver determines the degree to which jamming is successful. Jammer s goal is to raise JSR to a level where BER (Bit Error Rate) in the network traffic exceeds certain threshold (e.g ). No coding scheme can recover corrupted bits at high BER and hence link fails for the duration of jamming. [15] derives JSR formula based on R n propagation model as shown in the equation 3.3. JSR = Jamming power received Signal power received = P J G JR G RJ 10 (P L(D 0)+10 log 10 (D JR /D 0 ) n )/10 P T G T R G RT 10 (P L(D 0)+10 log 10 (D T R /D 0 ) n )/10 = P JG JR G RJ P T G T R G RT 10 (n log 10 (D T R/D JR )) = P J P T ( DT R D JR ) n (3.3) where P J is jamming signal s transmit power, P T is signal s transmit power, G JR and G RJ are transmit and receive antenna gains for the jamming signal, G T R and G RT are transmit and receive antenna gains for the transmitted signal, D T R is the distance between transmitter and receiver, D JR is the distance between jammer and receiver. 9
19 D 0 is a reference point where path loss P L(D 0 ) is computed, n is path loss exponent. We assume that ground characteristics between a transmitter and a receiver and between a jammer and a receiver are same and hence P L(D 0 ) is same for both the transmitted signals and the jamming signals. We also assume that antenna gains are same for both the transmitted signals and the jamming signals. A jammer cannot measure actual jamming levels in the field and propagation models cannot capture all propagation loses accurately; they provide an approximation to the actual jamming levels. Therefore, it is necessary to design a jammer with margins. If propagation models suggest a power level x at a distance d to achieve the target JSR, then it is better to operate jammer with a higher power level than x to accommodate unknown propagation loses in practice. 3.3 Jamming Vulnerability of a Link Jamming vulnerability of a link is a region around the receiver in which jammer s presence causes link to fail. Jamming vulnerable region is considered circular under simple constant range model and the region is termed as a Jamming Circle. Jamming circle radius formula 3.4 is derived from the JSR formula 3.3 by rearranging the terms. D JR = D T R ( P J P T JSR ) 1/n (3.4) T DTR R DJR Figure 3.1: Jamming Vulnerability of a Link 10
20 Jamming circle radius in the equation 3.4 depends on the link length, transmitter s power, jammer s power, path loss exponent and minimum JSR that breaks a link. Networks which use robust spread spectrum physical layer and lower physical data rates have comparatively high JSR requirement for failing a link. Jamming circle radius increases linearly with the increase in a link length. Jamming circle radius increases lower than linearly with the increase in jammer s power. Jamming circle radius decreases lower than linearly with the increase in transmitter s power. 3.4 Jamming Vulnerability of a Path If jammer s power and minimum JSR to break a link are given, then jamming circle radius for each link on a path can be found using the equation 3.4. Jamming vulnerability of a path is the total region occupied by these jamming circles. Jammer s presence in any of the jamming circles causes link failure and disrupts traffic on the path. Figure 3.2 shows an example of jamming vulnerability of a path. Bi-directional data transfer (DATA + ACK) is assumed at each hop on the path. S D Figure 3.2: Jamming Vulnerability of a Path 11
21 Chapter 4 Proactive Protection against Jamming This chapter presents proactive protection technique for mitigating jamming effects in wireless multihop networks with fixed nodes. 4.1 Multipath Routing and Power Control Approach We assume that jamming conditions in the network (number of jammers, jammer s maximum power and jamming strategy (BBN, PBN etc.)) are known to the network nodes. Distributed jamming detection and localization techniques (e.g. [14],[25]) can provide this information to the network nodes. Using this information, jamming vulnerable region for a traffic flow which uses a single path, can be computed as described in the section 3.4. We are proposing multipath routing and power control approach for reducing jamming vulnerability of the traffic flow. In this approach, a traffic flow is routed redundantly on node disjoint paths and power control is performed on the links of the node disjoint paths. Redundant routing on the node dijoint paths ensures that any one path s failure due to jamming doesn t disrupt the traffic flow. Power control on the links of the node disjoint paths is required to defend against simultaneous jamming of the paths by a jammer. Power control is performed such that the following two conditions are satisfied. Condition 1: Jamming vulnerable regions around the source and destination of the node disjoint paths are minimum possible. Condition 2: Jamming circles around the intermediate nodes on one path do not overlap with any jamming circles on the other paths. 12
22 S D Figure 4.1: Multipath Routing and Power Control Approach Figure 4.1 shows an example of the two node disjoint paths. As per the condition 1, jamming vulnerable regions around S and D (region filled with grey color) are minimum possible. As per the condition 2, none of the red jamming circles around the intermediate nodes on the red path overlap with any of the blue jamming circles on the blue path and vice versa. Also, it is desirable to satisfy conditions 1 and 2 such that summation of the power used on the links of the paths is minimum possible, in order to reduce unnecessary interference and to reduce energy expenditure. The following are key benefits of the multipath routing and power control approach. Irrespective of the jammer s location, jamming vulnerable region is reduced to the small shaded area around the source S and the destination D as shown in the figure 4.1. So, the strength of the path set in defending jamming is much improved over a single path. In figure 4.1, a single jammer cannot disrupt traffic on both the red and blue paths simultaneously except when it is jamming in the small shaded region around the source S or the destination D. So, two node disjoint paths and power control on the links of the paths provide protection against a single jammer. Similarly, power control on the links of the K + 1 node disjoint paths provide protection against K jammers. Power control is performed such that minimum required power is used. visibility, unnecessary interference and energy expenditure. This reduces This approach can be applied to any radio with power control ability. 13
23 4.2 Algorithm for Preplanned Protection Based on the multipath routing and power control approach, we have developed an algorithm 1 for providing proactive protection against a single jammer. For a given source and destination in the network, algorithm 1 takes node disjoint paths between them as an input; it forms distinct path pairs and assigns power to the links of the path pairs. Algorithm 1 performs power assignments such that conditions 1 and 2 from the section 4.1 are satisfied. Algorithm 1 outputs a path pair for which total power assigned is minimum. Algorithm 1 also outputs power assignments for the selected path pair Terminology Table 4.1: Algorithm 1 Terminology P athset(u, v) set containing node disjoint paths between nodes u and v LocSet(u, v) set containing locations of the nodes on the node disjoint paths between nodes u and v P d (u, v) set containing default power for the links on the node disjoint paths between nodes u and v P d (X) set containing default power assigned to the links on a path X Ph a d default power for a link h a P X set containing power assigned to the links on a path X by the algorithm P h a power assigned to a link h a by the algorithm P max maximum transmit power that can be assigned to a link P jam jammer s maximum power P La transmit power assigned to the node a s incoming link of length L a JSR minimum jammer-to-signal ratio (JSR) that breaks an incoming link n path-loss exponent in the R n propagation model X, Y, A, B paths P airset set containing pairs of node disjoint paths R La jamming circle radius for the node a s incoming link of length L a jamming circle radius at node u R u 14
24 4.2.2 Algorithm 1 Algorithm 1 Input: P athset(u, v), LocSet(u, v), P d (u, v), P max, P jam, JSR, n Output: One of the following outputs: (1) X, Y, P X, P Y (2) NULL 1: MinP owsum, Output NULL 2: P airset {(X, Y ) / X, Y ɛ P athset(u, v) and X Y } 3: In P airset, replace pairs (M, N) and (P, Q) with (M, N), where M = Q and N = P 4: for all (A, B) ɛ P airset do 5: P A NIL, P B NIL 6: R u 0, R v 0 7: for all intermediate node a on path A do jamming circle radius for nodes on A 8: R a 9: for all node b on path B do 10: L a length of biggest incoming link to node a, on path A 11: L b length of biggest incoming link to node b, on path B 12: D linear distance between nodes a and b 13: if b = u OR b = v then 14: R Lb L b ((1/JSR) (P jam /P max )) 1/n 15: if R Lb > D then 16: Goto step 4 impossible to avoid overlap on two paths 17: end if 18: R La D R Lb 19: P (P jam /JSR) (L a /R La )) n 20: if P > P max then 21: Goto step 4 required power to avoid overlap exceeds P max 22: end if 23: else 24: R La (L a /(L a + L b )) D compute jamming circle radius 25: R Lb (L b /(L a + L b )) D compute jamming circle radius 26: P La (P jam /JSR) (L a /R La ) n compute required transmit power 27: P Lb (P jam /JSR) (L b /R Lb ) n compute required transmit power 28: if P La > P max then adjust jamming circle radius if require 29: R L a ((1/JSR) (P jam /P max )) 1/n 15
25 30: if R > D then 31: Goto step 4 impossible to avoid overlap on two paths 32: end if 33: P (P jam /JSR) (L b /(D R)) n 34: if P > P max then 35: Goto step 4 required power to avoid overlap exceeds P max 36: end if 37: R La R, R Lb D R 38: P La P max, P Lb P 39: end if 40: if P Lb > P max then adjust jamming circle radius if require 41: R L b ((1/JSR) (P jam /P max )) 1/n 42: if R > D then impossible to avoid overlap on two paths 43: Goto step 4 44: end if 45: P (P jam /JSR) (L a /(D R)) n 46: if P > P max then 47: Goto step 4 required power to avoid overlap exceeds P max 48: end if 49: R Lb R, R La D R 50: P Lb P max, P La P 51: end if 52: end if 53: if R a > R La then 54: R a R La update final jamming circle radius for a 55: end if 56: end for 57: end for 58: for all intermediate node b on path B do jamming circle radius for nodes on B 59: R b 60: for all node a on path A do 61: L a length of biggest incoming link to node a, on path A 62: L b length of biggest incoming link to node b, on path B 63: D linear distance between nodes a and b 64: if a = u OR a = v then 65: R La L a ((1/JSR) (P jam /P max )) 1/n 66: if R La > D then 67: Goto step 4 impossible to avoid overlap on two paths 68: end if 69: R Lb D R La 70: P (P jam /JSR) (L b /R Lb )) n 16
26 71: if P > P max then 72: Goto step 4 required power to avoid overlap exceeds P max 73: end if 74: else 75: if (D R a ) < R b then 76: R b D R a 77: end if 78: end if 79: end for 80: end for 81: for all node a on path A do find power-assignments for links on path A 82: for all node h on A, such that (h, a)ɛa do 83: L ha linear distance between nodes a and h 84: if a = u OR a = v then 85: P h a P max 86: R L ha ((1/JSR) (P jam /P max )) 1/n 87: if R > R a then 88: R a R 89: end if 90: else 91: P h a (P jam /JSR) (L ha /R a ) n 92: end if 93: if Ph a d > P A ha then 94: P h a Ph a d 95: end if 96: P A P A P h a 97: end for 98: end for 99: for all node b on path B do find power-assignment for links on path B 100: for all node h on path B, such that (h, b)ɛb do 101: L hb linear distance between nodes b and h 102: if b = u OR b = v then 103: P h b P max 104: R L hb ((1/JSR) (P jam /P max )) 1/n 105: if R > R b then 106: R b R 107: end if 108: else 109: P h b (P jam /JSR) (L hb /R b ) n 110: end if 17
27 111: if P d h b > P h b then 112: P h b Ph b d 113: end if 114: P B P B P h b 115: end for 116: end for 117: P owsum(a, B) summation of power assigned to links of paths A and B 118: if P owsum(a, B) < MinP owsum then 119: MinP owsum P owsum(a, B) 120: Output {A, B, P A, P B } update, as paths A, B has minimum total power 121: end if 122: end for 123: Return Output 18
28 4.2.3 Description For the given source and destination, algorithm 1 outputs a node disjoint path pair from all the node disjoint paths between them given in the input. Algorithm 1 also outputs power assigned to the links of the selected path pair. Algorithm 1 performs power assignments such that conditions 1 and 2 from the section 4.1 are satisfied. Algorithm 1 outputs the path pair for which total power assigned is minimum. Algorithm 1 returns NULL if and only if, for any path pair, conditions 1 and 2 from the section 4.1 cannot be fulfilled by any power assignment. Algorithm 1 forms distinct path pairs from the input paths, in the step 3. Loop at the step 4 iterates over all the path pairs, performs power assignments and selects a path pair which has least total power. For each path pair (A, B), jamming circle radius for intermediate nodes on the paths A and B are found in the loops at the steps 7 and 58, such that condition 2 from the section 4.1 is satisfied. If power assignments that satisfy condition 2 from the section 4.1 are not possible, then path pair (A, B) is ignored. Loops at the steps 81 and 99 assign power to the links on the paths A and B as per the jamming circles found for the nodes on the paths A and B. Steps select a path pair for output which has least total power. Theorem : Algorithm 1 assigns power to the links of a path pair (A, B) if and only if there exist power assignments that can satisfy conditions 1 and 2 from the section 4.1. Proof : Condition 1 from the section 4.1 is not possible to satisfy in the following two cases. Case 1: P max assignment to any link h a on the path A gives a jamming circle which covers any node on the path B. Similarly, P max assignment to any link h b on the path B gives a jamming circle which covers any node on the path A. Case 2: Jamming circle given by the P max assignment to any incoming link to an intermediate node a on the path A overlaps with the jamming circle given by the P max assignment to any link on the path B. Similarly, jamming circle given by the P max assignment to any incoming link to an intermediate node b on the path B overlaps with the jamming circle given by P max assignment to any link on the path A. Algorithm 1 doesn t find power assignments for a path pair (A, B) if and only if any of the conditions in steps 15, 20, 30, 34, 42, 46, 66, 71 is true for the path pair (A, B). Conditions in steps 15, 20, 30, 34, 42, 46, 66, 71 are true only when power assignments are not possible due to either the case 1 or the case 2. In all other cases, algorithm 1 finds power assignments for the path pair (A, B). 19
29 For a path pair (A, B) which has already satisfied condition 1 from the section 4.1, algorithm 1 assigns P max to the incoming links of the end nodes u and v. Therefore, jamming circles around the end nodes u and v are minimum possible and condition 2 from the section 4.1 is also satisfied Complexity Suppose there are total n nodes in the network. In such a case, node disjoint paths given in the input to algorithm 1 can contain n nodes at most. For such an input, algorithm 1 matches a node x to n 1 other nodes at most, for deciding x s jamming circle radius and for assigning power to x s incoming links. Determining jamming circle radius and assigning power to the incoming links of a node are constant time operations and therefore n 1 matches takes total O(n) time. These operations are performed for n nodes at most. So, worst case running time of the algorithm 1 is O(n 2 ). 4.3 Embedding the Algorithm 1 The following steps describe how to embed the algorithm 1 on a table driven multipath routing scheme and on an on-demand multipath routing scheme for providing proactive protection against jamming. Step 1: Establish node disjoint paths between a source and a destination using a table driven multipath routing algorithm or using an on-demand multipath routing algorithm. Nodes transmit route establishment packets (e.g. Route Request, Route Reply) at maximum power in order to minimize chances of getting lost due to jamming. For example, figure 4.2 shows three node disjoint paths S A B D, S G H D, S M N D discovered between the nodes S and D. A B S G H D M N Figure 4.2: Embedding the Algorithm 1 (Step 1) 20
30 Step 2: Once node disjoint paths are established, the source sends a special packet to the destination on each node disjoint path. Each node on a path appends its location and default transmit power information in the received special packet and forwards it to the next hop. The destination collects location and default power information of all nodes on the node disjoint paths. For example, D collects location and default transmit power information about all nodes on the three paths, as shown in the figure 4.3. L i refers to the location of node i and P i refers to the default transmit power for node i. A B S G H D L S, P S L A, P A L B, P B L S, P S L G, P G L H,P H M N L S, P S L M, P M L N, P N Figure 4.3: Embedding the Algorithm 1 (Step 2) Step 3: The destination has location and default transmit power information about all nodes on the node disjoint paths. Also, we have assumed in the section 4.1 that jammer s maximum power and jamming type are known to the network nodes. So, destination has all required inputs for the algorithm 1. The destination runs the algorithm 1. If algorithm 1 outputs NULL, then the destination sends error message to the source indicating that power assignments for proactive protection against jamming are not feasible for any path pair. If algorithm 1 outputs a path pair and power assignments for the path pair, then the destination sends a power assignment packet on each path of the output path pair. For example, D chooses path pairs S A B D, S M N D and sends power assignment packets to the source S on the chosen path pair, as shown in the figure 4.4. P S A refers to the power assigned to the link S A. For table driven routing, power assignments are stored in the forwarding table entries of the nodes on the path pair. Data packets are forwarded to the next hop at the power specified in the forwarding table entry. For on-demand routing, each data packet from the source contains the entire path as well as power to be used at each hop. 21
31 S A G H B D Run algorithm 1, select path pair and send power assignment packets. M N P S-A, P A-S P A-B, P B-A P B-D, P D-B P S-M, P M-S P M-N, P N-M P N-D, P D-N Source ID Destination ID Next Hop ID TX Power Ack. Power Forwarding Table Entry For Table Driven Routing Header (M,P M-N,P N-M ) (N,P N-D,P D-N ) Data Data Packet For On Demand Routing Figure 4.4: Embedding the Algorithm 1 (Step 3) 4.4 Non-linear Programming for Optimal Power Assignments Power assignments performed by the algorithm 1 are not optimal. In other words, there can be power assignments for a path pair (A, B) such that the power assignments satisfy conditions 1 and 2 from the section 4.1 and the total power assigned is less than total power assigned by the algorithm 1. It is hard to find optimal power assignments as it requires minimizing an equation of the following form. P total = C 1 R n 1 + C 2 R n 2 + C 3 R n C m R n m Where m is the number of intermediate nodes on the paths A and B, C 1, C 2,...,C m are known constants, n(>= 2) is a path loss exponent in the R n propagation model and R 1, R 2,...,R m are unknown variables. Values of R 1, R 2,...,R m are interdependent and they are constrained by equations of the form R i + R j D ij, where D ij is a known constant. (4.1) We have developed a Non-linear Programming (NLP) formulation for finding optimal (minimum) power assignments for a path pair (A, B) such that conditions 1 and 2 from the section 4.1 are satisfied. 22
32 Table 4.2: NLP Formulation Terminology (X, Y ) node-disjoint path pair for the nodes u and v R a Radius of the jamming circle around the node a R ux Radius of the jamming circle around the node u on the path X n path-loss exponent in the R n propagation model L (a b) link (a b) length D (a,b) linear distance between nodes a and b P (a b) power assignment to the link (a b) P(a b) d default power on the link (a b) P(a b) min minimum power that can be assigned to the link (a b) P(a b) max maximum power that can be assigned to the link (a b) P total summation of the power assigned to the links on paths X and Y P max maximum transmit power P jam jammer s maximum transmit power JSR minimum jammer-to-signal ratio (JSR) required for breaking a link NLP formulation: Given: 1. L (a b), (a, b)ɛx Y 2. D (a,b), (a, b), a is an intermediate node on X, b is a node on Y 3. D (a,b), (a, b), a is an intermediate node on Y, b is a node on X 4. P max (a b) = P max, 5. P min (a b) = P d (a b), (a, b)ɛx Y, b u, b v (a, b)ɛx Y, b u, b v 6. P (x u) = P max, (x, u)ɛx 7. P (x v) = P max, (x, v)ɛx 8. P (y u) = P max, (y, u)ɛy 9. P (y v) = P max, (y, v)ɛy 10. P jam 11. JSR 23
Wireless Sensor Networks
 DEEJAM: Defeating Energy-Efficient Jamming in IEEE 802.15.4-based Wireless Networks Anthony D. Wood, John A. Stankovic, Gang Zhou Department of Computer Science University of Virginia June 19, 2007 Wireless
DEEJAM: Defeating Energy-Efficient Jamming in IEEE 802.15.4-based Wireless Networks Anthony D. Wood, John A. Stankovic, Gang Zhou Department of Computer Science University of Virginia June 19, 2007 Wireless
DEEJAM: Defeating Energy-Efficient Jamming in IEEE based Wireless Networks
 DEEJAM: Defeating Energy-Efficient Jamming in IEEE 802.15.4-based Wireless Networks Anthony D. Wood, John A. Stankovic, Gang Zhou Department of Computer Science University of Virginia Wireless Sensor Networks
DEEJAM: Defeating Energy-Efficient Jamming in IEEE 802.15.4-based Wireless Networks Anthony D. Wood, John A. Stankovic, Gang Zhou Department of Computer Science University of Virginia Wireless Sensor Networks
Vulnerability modelling of ad hoc routing protocols a comparison of OLSR and DSR
 5 th Scandinavian Workshop on Wireless Ad-hoc Networks May 3-4, 2005 Vulnerability modelling of ad hoc routing protocols a comparison of OLSR and DSR Mikael Fredin - Ericsson Microwave Systems, Sweden
5 th Scandinavian Workshop on Wireless Ad-hoc Networks May 3-4, 2005 Vulnerability modelling of ad hoc routing protocols a comparison of OLSR and DSR Mikael Fredin - Ericsson Microwave Systems, Sweden
Wireless Network Security Spring 2014
 Wireless Network Security 14-814 Spring 2014 Patrick Tague Class #5 Jamming 2014 Patrick Tague 1 Travel to Pgh: Announcements I'll be on the other side of the camera on Feb 4 Let me know if you'd like
Wireless Network Security 14-814 Spring 2014 Patrick Tague Class #5 Jamming 2014 Patrick Tague 1 Travel to Pgh: Announcements I'll be on the other side of the camera on Feb 4 Let me know if you'd like
Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network
 International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks
 Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS
 TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
Understanding and Mitigating the Impact of Interference on Networks. By Gulzar Ahmad Sanjay Bhatt Morteza Kheirkhah Adam Kral Jannik Sundø
 Understanding and Mitigating the Impact of Interference on 802.11 Networks By Gulzar Ahmad Sanjay Bhatt Morteza Kheirkhah Adam Kral Jannik Sundø 1 Outline Background Contributions 1. Quantification & Classification
Understanding and Mitigating the Impact of Interference on 802.11 Networks By Gulzar Ahmad Sanjay Bhatt Morteza Kheirkhah Adam Kral Jannik Sundø 1 Outline Background Contributions 1. Quantification & Classification
Wireless Network Security Spring 2015
 Wireless Network Security Spring 2015 Patrick Tague Class #5 Jamming, Physical Layer Security 2015 Patrick Tague 1 Class #5 Jamming attacks and defenses Secrecy using physical layer properties Authentication
Wireless Network Security Spring 2015 Patrick Tague Class #5 Jamming, Physical Layer Security 2015 Patrick Tague 1 Class #5 Jamming attacks and defenses Secrecy using physical layer properties Authentication
Jamming Wireless Networks: Attack and Defense Strategies
 Jamming Wireless Networks: Attack and Defense Strategies Wenyuan Xu, Ke Ma, Wade Trappe, Yanyong Zhang, WINLAB, Rutgers University IAB, Dec. 6 th, 2005 Roadmap Introduction and Motivation Jammer Models
Jamming Wireless Networks: Attack and Defense Strategies Wenyuan Xu, Ke Ma, Wade Trappe, Yanyong Zhang, WINLAB, Rutgers University IAB, Dec. 6 th, 2005 Roadmap Introduction and Motivation Jammer Models
LOCALIZATION AND ROUTING AGAINST JAMMERS IN WIRELESS NETWORKS
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 5, May 2015, pg.955
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 5, May 2015, pg.955
On Practical Selective Jamming of Bluetooth Low Energy Advertising
 On Practical Selective Jamming of Bluetooth Low Energy Advertising S. Brauer, A. Zubow, S. Zehl, M. Roshandel, S. M. Sohi Technical University Berlin & Deutsche Telekom Labs Germany Outline Motivation,
On Practical Selective Jamming of Bluetooth Low Energy Advertising S. Brauer, A. Zubow, S. Zehl, M. Roshandel, S. M. Sohi Technical University Berlin & Deutsche Telekom Labs Germany Outline Motivation,
Introduction. Introduction ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS. Smart Wireless Sensor Systems 1
 ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS Xiang Ji and Hongyuan Zha Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley,
ROBUST SENSOR POSITIONING IN WIRELESS AD HOC SENSOR NETWORKS Xiang Ji and Hongyuan Zha Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley,
Wireless Network Security Spring 2016
 Wireless Network Security Spring 2016 Patrick Tague Class #4 Physical Layer Threats; Jamming 2016 Patrick Tague 1 Class #4 PHY layer basics and threats Jamming 2016 Patrick Tague 2 PHY 2016 Patrick Tague
Wireless Network Security Spring 2016 Patrick Tague Class #4 Physical Layer Threats; Jamming 2016 Patrick Tague 1 Class #4 PHY layer basics and threats Jamming 2016 Patrick Tague 2 PHY 2016 Patrick Tague
By Ryan Winfield Woodings and Mark Gerrior, Cypress Semiconductor
 Avoiding Interference in the 2.4-GHz ISM Band Designers can create frequency-agile 2.4 GHz designs using procedures provided by standards bodies or by building their own protocol. By Ryan Winfield Woodings
Avoiding Interference in the 2.4-GHz ISM Band Designers can create frequency-agile 2.4 GHz designs using procedures provided by standards bodies or by building their own protocol. By Ryan Winfield Woodings
Book Title: XXXXXXXXXXXXXXXXXXXXXXXXXX. Editors
 Book Title: XXXXXXXXXXXXXXXXXXXXXXXXXX Editors March 24, 2008 ii Contents 1 Jamming in Wireless Sensor Networks 1 1.1 Introduction.................................... 2 1.2 Communication in WSNs.............................
Book Title: XXXXXXXXXXXXXXXXXXXXXXXXXX Editors March 24, 2008 ii Contents 1 Jamming in Wireless Sensor Networks 1 1.1 Introduction.................................... 2 1.2 Communication in WSNs.............................
Wireless Network Security Spring 2016
 Wireless Network Security Spring 2016 Patrick Tague Class #5 Jamming (cont'd); Physical Layer Security 2016 Patrick Tague 1 Class #5 Anti-jamming Physical layer security Secrecy using physical layer properties
Wireless Network Security Spring 2016 Patrick Tague Class #5 Jamming (cont'd); Physical Layer Security 2016 Patrick Tague 1 Class #5 Anti-jamming Physical layer security Secrecy using physical layer properties
Wireless Network Security Spring 2012
 Wireless Network Security 14-814 Spring 2012 Patrick Tague Class #8 Interference and Jamming Announcements Homework #1 is due today Questions? Not everyone has signed up for a Survey These are required,
Wireless Network Security 14-814 Spring 2012 Patrick Tague Class #8 Interference and Jamming Announcements Homework #1 is due today Questions? Not everyone has signed up for a Survey These are required,
ENERGY EFFICIENT SENSOR NODE DESIGN IN WIRELESS SENSOR NETWORKS
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
RESEARCH ON METHODS FOR ANALYZING AND PROCESSING SIGNALS USED BY INTERCEPTION SYSTEMS WITH SPECIAL APPLICATIONS
 Abstract of Doctorate Thesis RESEARCH ON METHODS FOR ANALYZING AND PROCESSING SIGNALS USED BY INTERCEPTION SYSTEMS WITH SPECIAL APPLICATIONS PhD Coordinator: Prof. Dr. Eng. Radu MUNTEANU Author: Radu MITRAN
Abstract of Doctorate Thesis RESEARCH ON METHODS FOR ANALYZING AND PROCESSING SIGNALS USED BY INTERCEPTION SYSTEMS WITH SPECIAL APPLICATIONS PhD Coordinator: Prof. Dr. Eng. Radu MUNTEANU Author: Radu MITRAN
IFH SS CDMA Implantation. 6.0 Introduction
 6.0 Introduction Wireless personal communication systems enable geographically dispersed users to exchange information using a portable terminal, such as a handheld transceiver. Often, the system engineer
6.0 Introduction Wireless personal communication systems enable geographically dispersed users to exchange information using a portable terminal, such as a handheld transceiver. Often, the system engineer
UNDERSTANDING AND MITIGATING
 UNDERSTANDING AND MITIGATING THE IMPACT OF RF INTERFERENCE ON 802.11 NETWORKS RAMAKRISHNA GUMMADI UCS DAVID WETHERALL INTEL RESEARCH BEN GREENSTEIN UNIVERSITY OF WASHINGTON SRINIVASAN SESHAN CMU 1 Presented
UNDERSTANDING AND MITIGATING THE IMPACT OF RF INTERFERENCE ON 802.11 NETWORKS RAMAKRISHNA GUMMADI UCS DAVID WETHERALL INTEL RESEARCH BEN GREENSTEIN UNIVERSITY OF WASHINGTON SRINIVASAN SESHAN CMU 1 Presented
Simple Algorithm in (older) Selection Diversity. Receiver Diversity Can we Do Better? Receiver Diversity Optimization.
 18-452/18-750 Wireless Networks and Applications Lecture 6: Physical Layer Diversity and Coding Peter Steenkiste Carnegie Mellon University Spring Semester 2017 http://www.cs.cmu.edu/~prs/wirelesss17/
18-452/18-750 Wireless Networks and Applications Lecture 6: Physical Layer Diversity and Coding Peter Steenkiste Carnegie Mellon University Spring Semester 2017 http://www.cs.cmu.edu/~prs/wirelesss17/
Channel Surfing and Spatial Retreats: Defenses against Wireless Denial of Service
 Channel Surfing and Spatial Retreats: Defenses against Wireless Denial of Service Wenyuan Xu, Timothy Wood, Wade Trappe, Yanyong Zhang WINLAB, Rutgers University IAB 2004 Roadmap Motivation and Introduction
Channel Surfing and Spatial Retreats: Defenses against Wireless Denial of Service Wenyuan Xu, Timothy Wood, Wade Trappe, Yanyong Zhang WINLAB, Rutgers University IAB 2004 Roadmap Motivation and Introduction
Pseudo-random Polarization Hopping ( PPH ) Technology Brief
 Pseudo-random Polarization Hopping ( PPH ) Technology Brief 1. PPH AT A GLANCE Unique features: Signal hops in polarization domain,occupying a narrow spectrum Employs multiple constellations in polarization
Pseudo-random Polarization Hopping ( PPH ) Technology Brief 1. PPH AT A GLANCE Unique features: Signal hops in polarization domain,occupying a narrow spectrum Employs multiple constellations in polarization
IEEE g,n Multi-Network Jamming Attacks - A Cognitive Radio Based Approach. by Sudarshan Prasad
 ABSTRACT PRASAD, SUDARSHAN. IEEE 802.11g,n Multi-Network Jamming Attacks - A Cognitive Radio Based Approach. (Under the direction of Dr. David Thuente.) Wireless networks are susceptible to jamming attacks,
ABSTRACT PRASAD, SUDARSHAN. IEEE 802.11g,n Multi-Network Jamming Attacks - A Cognitive Radio Based Approach. (Under the direction of Dr. David Thuente.) Wireless networks are susceptible to jamming attacks,
Wireless LAN Applications LAN Extension Cross building interconnection Nomadic access Ad hoc networks Single Cell Wireless LAN
 Wireless LANs Mobility Flexibility Hard to wire areas Reduced cost of wireless systems Improved performance of wireless systems Wireless LAN Applications LAN Extension Cross building interconnection Nomadic
Wireless LANs Mobility Flexibility Hard to wire areas Reduced cost of wireless systems Improved performance of wireless systems Wireless LAN Applications LAN Extension Cross building interconnection Nomadic
Cognitive Wireless Network : Computer Networking. Overview. Cognitive Wireless Networks
 Cognitive Wireless Network 15-744: Computer Networking L-19 Cognitive Wireless Networks Optimize wireless networks based context information Assigned reading White spaces Online Estimation of Interference
Cognitive Wireless Network 15-744: Computer Networking L-19 Cognitive Wireless Networks Optimize wireless networks based context information Assigned reading White spaces Online Estimation of Interference
Partial overlapping channels are not damaging
 Journal of Networking and Telecomunications (2018) Original Research Article Partial overlapping channels are not damaging Jing Fu,Dongsheng Chen,Jiafeng Gong Electronic Information Engineering College,
Journal of Networking and Telecomunications (2018) Original Research Article Partial overlapping channels are not damaging Jing Fu,Dongsheng Chen,Jiafeng Gong Electronic Information Engineering College,
CIS 632 / EEC 687 Mobile Computing. Mobile Communications (for Dummies) Chansu Yu. Contents. Modulation Propagation Spread spectrum
 CIS 632 / EEC 687 Mobile Computing Mobile Communications (for Dummies) Chansu Yu Contents Modulation Propagation Spread spectrum 2 1 Digital Communication 1 0 digital signal t Want to transform to since
CIS 632 / EEC 687 Mobile Computing Mobile Communications (for Dummies) Chansu Yu Contents Modulation Propagation Spread spectrum 2 1 Digital Communication 1 0 digital signal t Want to transform to since
Unit 1 Introduction to Spread- Spectrum Systems. Department of Communication Engineering, NCTU 1
 Unit 1 Introduction to Spread- Spectrum Systems Department of Communication Engineering, NCTU 1 What does it mean by spread spectrum communications Spread the energy of an information bit over a bandwidth
Unit 1 Introduction to Spread- Spectrum Systems Department of Communication Engineering, NCTU 1 What does it mean by spread spectrum communications Spread the energy of an information bit over a bandwidth
Mobile & Wireless Networking. Lecture 2: Wireless Transmission (2/2)
 192620010 Mobile & Wireless Networking Lecture 2: Wireless Transmission (2/2) [Schiller, Section 2.6 & 2.7] [Reader Part 1: OFDM: An architecture for the fourth generation] Geert Heijenk Outline of Lecture
192620010 Mobile & Wireless Networking Lecture 2: Wireless Transmission (2/2) [Schiller, Section 2.6 & 2.7] [Reader Part 1: OFDM: An architecture for the fourth generation] Geert Heijenk Outline of Lecture
An Effective Defensive Node against Jamming Attacks in Sensor Networks
 International Journal of Engineering Science Invention ISSN (Online): 2319 6734, ISSN (Print): 2319 6726 Volume 2 Issue 6ǁ June. 2013 ǁ PP.41-46 An Effective Defensive Node against Jamming Attacks in Sensor
International Journal of Engineering Science Invention ISSN (Online): 2319 6734, ISSN (Print): 2319 6726 Volume 2 Issue 6ǁ June. 2013 ǁ PP.41-46 An Effective Defensive Node against Jamming Attacks in Sensor
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks. Nathan Balon and Jinhua Guo University of Michigan - Dearborn
 Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Introduction to Wireless and Mobile Networking. Hung-Yu Wei g National Taiwan University
 Introduction to Wireless and Mobile Networking Lecture 3: Multiplexing, Multiple Access, and Frequency Reuse Hung-Yu Wei g National Taiwan University Multiplexing/Multiple Access Multiplexing Multiplexing
Introduction to Wireless and Mobile Networking Lecture 3: Multiplexing, Multiple Access, and Frequency Reuse Hung-Yu Wei g National Taiwan University Multiplexing/Multiple Access Multiplexing Multiplexing
USD-FH: Jamming-resistant Wireless Communication using Frequency Hopping with Uncoordinated Seed Disclosure
 USD-FH: Jamming-resistant Wireless Communication using Frequency Hopping with Uncoordinated Seed Disclosure An Liu, Peng Ning, Huaiyu Dai, Yao Liu North Carolina State University, Raleigh, NC 27695 {aliu3,
USD-FH: Jamming-resistant Wireless Communication using Frequency Hopping with Uncoordinated Seed Disclosure An Liu, Peng Ning, Huaiyu Dai, Yao Liu North Carolina State University, Raleigh, NC 27695 {aliu3,
Multiple Antenna Processing for WiMAX
 Multiple Antenna Processing for WiMAX Overview Wireless operators face a myriad of obstacles, but fundamental to the performance of any system are the propagation characteristics that restrict delivery
Multiple Antenna Processing for WiMAX Overview Wireless operators face a myriad of obstacles, but fundamental to the performance of any system are the propagation characteristics that restrict delivery
Wi-Fi. Wireless Fidelity. Spread Spectrum CSMA. Ad-hoc Networks. Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering
 Wi-Fi Wireless Fidelity Spread Spectrum CSMA Ad-hoc Networks Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Outline for Today We learned how to setup a WiFi network. This
Wi-Fi Wireless Fidelity Spread Spectrum CSMA Ad-hoc Networks Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Outline for Today We learned how to setup a WiFi network. This
CS263: Wireless Communications and Sensor Networks
 CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 3: Antennas, Propagation, and Spread Spectrum September 30, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Antennas and
CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 3: Antennas, Propagation, and Spread Spectrum September 30, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Antennas and
Lecture on Sensor Networks
 Lecture on Sensor Networks Copyright (c) 2008 Dr. Thomas Haenselmann (University of Mannheim, Germany). Permission is granted to copy, distribute and/or modify this document under the terms of the GNU
Lecture on Sensor Networks Copyright (c) 2008 Dr. Thomas Haenselmann (University of Mannheim, Germany). Permission is granted to copy, distribute and/or modify this document under the terms of the GNU
Fine-grained Channel Access in Wireless LAN. Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012
 Fine-grained Channel Access in Wireless LAN Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012 Physical-layer data rate PHY layer data rate in WLANs is increasing rapidly Wider channel
Fine-grained Channel Access in Wireless LAN Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012 Physical-layer data rate PHY layer data rate in WLANs is increasing rapidly Wider channel
Interleaving And Channel Encoding Of Data Packets In Wireless Communications
 Interleaving And Channel Encoding Of Data Packets In Wireless Communications B. Aparna M. Tech., Computer Science & Engineering Department DR.K.V.Subbareddy College Of Engineering For Women, DUPADU, Kurnool-518218
Interleaving And Channel Encoding Of Data Packets In Wireless Communications B. Aparna M. Tech., Computer Science & Engineering Department DR.K.V.Subbareddy College Of Engineering For Women, DUPADU, Kurnool-518218
Syed Obaid Amin. Date: February 11 th, Networking Lab Kyung Hee University
 Detecting Jamming Attacks in Ubiquitous Sensor Networks Networking Lab Kyung Hee University Date: February 11 th, 2008 Syed Obaid Amin obaid@networking.khu.ac.kr Contents Background Introduction USN (Ubiquitous
Detecting Jamming Attacks in Ubiquitous Sensor Networks Networking Lab Kyung Hee University Date: February 11 th, 2008 Syed Obaid Amin obaid@networking.khu.ac.kr Contents Background Introduction USN (Ubiquitous
Localization in Wireless Sensor Networks
 Localization in Wireless Sensor Networks Part 2: Localization techniques Department of Informatics University of Oslo Cyber Physical Systems, 11.10.2011 Localization problem in WSN In a localization problem
Localization in Wireless Sensor Networks Part 2: Localization techniques Department of Informatics University of Oslo Cyber Physical Systems, 11.10.2011 Localization problem in WSN In a localization problem
A survey on broadcast protocols in multihop cognitive radio ad hoc network
 A survey on broadcast protocols in multihop cognitive radio ad hoc network Sureshkumar A, Rajeswari M Abstract In the traditional ad hoc network, common channel is present to broadcast control channels
A survey on broadcast protocols in multihop cognitive radio ad hoc network Sureshkumar A, Rajeswari M Abstract In the traditional ad hoc network, common channel is present to broadcast control channels
Chapter 1 Acknowledgment:
 Chapter 1 Acknowledgment: This material is based on the slides formatted by Dr Sunilkumar S. Manvi and Dr Mahabaleshwar S. Kakkasageri, the authors of the textbook: Wireless and Mobile Networks, concepts
Chapter 1 Acknowledgment: This material is based on the slides formatted by Dr Sunilkumar S. Manvi and Dr Mahabaleshwar S. Kakkasageri, the authors of the textbook: Wireless and Mobile Networks, concepts
Chapter XIII Short Range Wireless Devices - Building a global license-free system at frequencies below 1GHz By Austin Harney and Conor O Mahony
 Chapter XIII Short Range Wireless Devices - Building a global license-free system at frequencies below 1GHz By Austin Harney and Conor O Mahony Introduction: The term Short Range Device (SRD) is intended
Chapter XIII Short Range Wireless Devices - Building a global license-free system at frequencies below 1GHz By Austin Harney and Conor O Mahony Introduction: The term Short Range Device (SRD) is intended
ZigBee Propagation Testing
 ZigBee Propagation Testing EDF Energy Ember December 3 rd 2010 Contents 1. Introduction... 3 1.1 Purpose... 3 2. Test Plan... 4 2.1 Location... 4 2.2 Test Point Selection... 4 2.3 Equipment... 5 3 Results...
ZigBee Propagation Testing EDF Energy Ember December 3 rd 2010 Contents 1. Introduction... 3 1.1 Purpose... 3 2. Test Plan... 4 2.1 Location... 4 2.2 Test Point Selection... 4 2.3 Equipment... 5 3 Results...
CHANNEL ASSIGNMENT AND LOAD DISTRIBUTION IN A POWER- MANAGED WLAN
 CHANNEL ASSIGNMENT AND LOAD DISTRIBUTION IN A POWER- MANAGED WLAN Mohamad Haidar Robert Akl Hussain Al-Rizzo Yupo Chan University of Arkansas at University of Arkansas at University of Arkansas at University
CHANNEL ASSIGNMENT AND LOAD DISTRIBUTION IN A POWER- MANAGED WLAN Mohamad Haidar Robert Akl Hussain Al-Rizzo Yupo Chan University of Arkansas at University of Arkansas at University of Arkansas at University
PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR P INCLUDING PROPAGATION MODELS
 PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR 802.11P INCLUDING PROPAGATION MODELS Mit Parmar 1, Kinnar Vaghela 2 1 Student M.E. Communication Systems, Electronics & Communication Department, L.D. College
PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR 802.11P INCLUDING PROPAGATION MODELS Mit Parmar 1, Kinnar Vaghela 2 1 Student M.E. Communication Systems, Electronics & Communication Department, L.D. College
INTRODUCTION TO WIRELESS SENSOR NETWORKS. CHAPTER 3: RADIO COMMUNICATIONS Anna Förster
 INTRODUCTION TO WIRELESS SENSOR NETWORKS CHAPTER 3: RADIO COMMUNICATIONS Anna Förster OVERVIEW 1. Radio Waves and Modulation/Demodulation 2. Properties of Wireless Communications 1. Interference and noise
INTRODUCTION TO WIRELESS SENSOR NETWORKS CHAPTER 3: RADIO COMMUNICATIONS Anna Förster OVERVIEW 1. Radio Waves and Modulation/Demodulation 2. Properties of Wireless Communications 1. Interference and noise
Jamming Attacks with its Various Techniques and AODV in Wireless Networks
 IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676,p-ISSN: 2320-3331, Volume 11, Issue 4 Ver. II (Jul. Aug. 2016), PP 48-52 www.iosrjournals.org Jamming Attacks with its
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676,p-ISSN: 2320-3331, Volume 11, Issue 4 Ver. II (Jul. Aug. 2016), PP 48-52 www.iosrjournals.org Jamming Attacks with its
Simplified Reference Model
 ITCE 720A Autonomic Wireless Networking (Fall, 2009) Mobile Communications Prof. Chansu Yu chansuyu@postech.ac.kr c.yu91@csuohio.edu Simplified Reference Model Mobile Terminals P ro t o c o l S ta c k
ITCE 720A Autonomic Wireless Networking (Fall, 2009) Mobile Communications Prof. Chansu Yu chansuyu@postech.ac.kr c.yu91@csuohio.edu Simplified Reference Model Mobile Terminals P ro t o c o l S ta c k
An Opportunistic Frequency Channels Selection Scheme for Interference Minimization
 Proceedings of 2014 Zone 1 Conference of the American Society for Engineering Education (ASEE Zone 1) An Opportunistic Frequency Channels Selection Scheme for Interference Minimization 978-1-4799-5233-5/14/$31.00
Proceedings of 2014 Zone 1 Conference of the American Society for Engineering Education (ASEE Zone 1) An Opportunistic Frequency Channels Selection Scheme for Interference Minimization 978-1-4799-5233-5/14/$31.00
Modern Communications Jamming Principles and Techniques
 Modern Communications Jamming Principles and Techniques Richard A. Poisel m Artech House Boston London www.artechhouse.com Contents Preface Acknowledgments xiii xv Chapter 1 Antijam Communications and
Modern Communications Jamming Principles and Techniques Richard A. Poisel m Artech House Boston London www.artechhouse.com Contents Preface Acknowledgments xiii xv Chapter 1 Antijam Communications and
THE SELF-ORGANIZING RADIO NETWORKS AND ULTRA WIDE BAND SIGNALS
 3 UDC 381.324 THE SELF-ORGANIZING RADIO NETWORKS AND ULTRA WIDE BAND SIGNALS Sergey G. Bunin Institute of Telecommunication Systems, National Polytechnic University, Kyiv, Ukraine Abstract The paper proposes
3 UDC 381.324 THE SELF-ORGANIZING RADIO NETWORKS AND ULTRA WIDE BAND SIGNALS Sergey G. Bunin Institute of Telecommunication Systems, National Polytechnic University, Kyiv, Ukraine Abstract The paper proposes
A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks
 A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks Eiman Alotaibi, Sumit Roy Dept. of Electrical Engineering U. Washington Box 352500 Seattle, WA 98195 eman76,roy@ee.washington.edu
A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks Eiman Alotaibi, Sumit Roy Dept. of Electrical Engineering U. Washington Box 352500 Seattle, WA 98195 eman76,roy@ee.washington.edu
ICT 5305 Mobile Communications. Lecture - 4 April Dr. Hossen Asiful Mustafa
 ICT 5305 Mobile Communications Lecture - 4 April 2016 Dr. Hossen Asiful Mustafa Media Access Motivation Can we apply media access methods from fixed networks? Example CSMA/CD Carrier Sense Multiple Access
ICT 5305 Mobile Communications Lecture - 4 April 2016 Dr. Hossen Asiful Mustafa Media Access Motivation Can we apply media access methods from fixed networks? Example CSMA/CD Carrier Sense Multiple Access
Wireless Network Security Spring 2015
 Wireless Network Security Spring 2015 Patrick Tague Class #4 OMNET++ Intro; Physical Layer Threats 2015 Patrick Tague 1 Class #4 OMNET++ Intro PHY layer basics and threats 2015 Patrick Tague 2 Intro to
Wireless Network Security Spring 2015 Patrick Tague Class #4 OMNET++ Intro; Physical Layer Threats 2015 Patrick Tague 1 Class #4 OMNET++ Intro PHY layer basics and threats 2015 Patrick Tague 2 Intro to
Wireless Transmission & Media Access
 Wireless Transmission & Media Access Signals and Signal Propagation Multiplexing Modulation Media Access 1 Significant parts of slides are based on original material by Prof. Dr.-Ing. Jochen Schiller,
Wireless Transmission & Media Access Signals and Signal Propagation Multiplexing Modulation Media Access 1 Significant parts of slides are based on original material by Prof. Dr.-Ing. Jochen Schiller,
Multiple Access Schemes
 Multiple Access Schemes Dr Yousef Dama Faculty of Engineering and Information Technology An-Najah National University 2016-2017 Why Multiple access schemes Multiple access schemes are used to allow many
Multiple Access Schemes Dr Yousef Dama Faculty of Engineering and Information Technology An-Najah National University 2016-2017 Why Multiple access schemes Multiple access schemes are used to allow many
Mobile Computing. Chapter 3: Medium Access Control
 Mobile Computing Chapter 3: Medium Access Control Prof. Sang-Jo Yoo Contents Motivation Access methods SDMA/FDMA/TDMA Aloha Other access methods Access method CDMA 2 1. Motivation Can we apply media access
Mobile Computing Chapter 3: Medium Access Control Prof. Sang-Jo Yoo Contents Motivation Access methods SDMA/FDMA/TDMA Aloha Other access methods Access method CDMA 2 1. Motivation Can we apply media access
A White Paper from Laird Technologies
 Originally Published: November 2011 Updated: October 2012 A White Paper from Laird Technologies Bluetooth and Wi-Fi transmit in different ways using differing protocols. When Wi-Fi operates in the 2.4
Originally Published: November 2011 Updated: October 2012 A White Paper from Laird Technologies Bluetooth and Wi-Fi transmit in different ways using differing protocols. When Wi-Fi operates in the 2.4
Redline Communications Inc. Combining Fixed and Mobile WiMAX Networks Supporting the Advanced Communication Services of Tomorrow.
 Redline Communications Inc. Combining Fixed and Mobile WiMAX Networks Supporting the Advanced Communication Services of Tomorrow WiMAX Whitepaper Author: Frank Rayal, Redline Communications Inc. Redline
Redline Communications Inc. Combining Fixed and Mobile WiMAX Networks Supporting the Advanced Communication Services of Tomorrow WiMAX Whitepaper Author: Frank Rayal, Redline Communications Inc. Redline
Multiple Input Multiple Output (MIMO) Operation Principles
 Afriyie Abraham Kwabena Multiple Input Multiple Output (MIMO) Operation Principles Helsinki Metropolia University of Applied Sciences Bachlor of Engineering Information Technology Thesis June 0 Abstract
Afriyie Abraham Kwabena Multiple Input Multiple Output (MIMO) Operation Principles Helsinki Metropolia University of Applied Sciences Bachlor of Engineering Information Technology Thesis June 0 Abstract
Medium Access Schemes
 Medium Access Schemes Winter Semester 2010/11 Integrated Communication Systems Group Ilmenau University of Technology Media Access: Motivation The problem: multiple users compete for a common, shared resource
Medium Access Schemes Winter Semester 2010/11 Integrated Communication Systems Group Ilmenau University of Technology Media Access: Motivation The problem: multiple users compete for a common, shared resource
Page 1. Outline : Wireless Networks Lecture 6: Final Physical Layer. Direct Sequence Spread Spectrum (DSSS) Spread Spectrum
 Outline 18-759 : Wireless Networks Lecture 6: Final Physical Layer Peter Steenkiste Dina Papagiannaki Spring Semester 2009 http://www.cs.cmu.edu/~prs/wireless09/ Peter A. Steenkiste 1 RF introduction Modulation
Outline 18-759 : Wireless Networks Lecture 6: Final Physical Layer Peter Steenkiste Dina Papagiannaki Spring Semester 2009 http://www.cs.cmu.edu/~prs/wireless09/ Peter A. Steenkiste 1 RF introduction Modulation
Detection and Prevention of Physical Jamming Attacks in Vehicular Environment
 Detection and Prevention of Physical Jamming Attacks in Vehicular Environment M-Tech Student 1 Mahendri 1, Neha Sawal 2 Assit. Prof. 2 &Department of CSE & NGF College of Engineering &Technology Palwal,
Detection and Prevention of Physical Jamming Attacks in Vehicular Environment M-Tech Student 1 Mahendri 1, Neha Sawal 2 Assit. Prof. 2 &Department of CSE & NGF College of Engineering &Technology Palwal,
Chapter 3 : Media Access. Mobile Communications. Collision avoidance, MACA
 Mobile Communications Chapter 3 : Media Access Motivation Collision avoidance, MACA SDMA, FDMA, TDMA Polling Aloha CDMA Reservation schemes SAMA Comparison Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/
Mobile Communications Chapter 3 : Media Access Motivation Collision avoidance, MACA SDMA, FDMA, TDMA Polling Aloha CDMA Reservation schemes SAMA Comparison Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/
IEEE Wireless Access Method and Physical Layer Specification. Proposal For the Use of Packet Detection in Clear Channel Assessment
 IEEE 802.11 Wireless Access Method and Physical Layer Specification Title: Author: Proposal For the Use of Packet Detection in Clear Channel Assessment Jim McDonald Motorola, Inc. 50 E. Commerce Drive
IEEE 802.11 Wireless Access Method and Physical Layer Specification Title: Author: Proposal For the Use of Packet Detection in Clear Channel Assessment Jim McDonald Motorola, Inc. 50 E. Commerce Drive
Prevention of Selective Jamming Attack Using Cryptographic Packet Hiding Methods
 Prevention of Selective Jamming Attack Using Cryptographic Packet Hiding Methods S.B.Gavali 1, A. K. Bongale 2 and A.B.Gavali 3 1 Department of Computer Engineering, Dr.D.Y.Patil College of Engineering,
Prevention of Selective Jamming Attack Using Cryptographic Packet Hiding Methods S.B.Gavali 1, A. K. Bongale 2 and A.B.Gavali 3 1 Department of Computer Engineering, Dr.D.Y.Patil College of Engineering,
Digi-Wave Technology Williams Sound Digi-Wave White Paper
 Digi-Wave Technology Williams Sound Digi-Wave White Paper TECHNICAL DESCRIPTION Operating Frequency: The Digi-Wave System operates on the 2.4 GHz Industrial, Scientific, and Medical (ISM) Band, which is
Digi-Wave Technology Williams Sound Digi-Wave White Paper TECHNICAL DESCRIPTION Operating Frequency: The Digi-Wave System operates on the 2.4 GHz Industrial, Scientific, and Medical (ISM) Band, which is
Performance Analysis of DSSS and FHSS Techniques over AWGN Channel
 Performance Analysis of DSSS and FHSS Techniques over AWGN Channel M. Katta Swamy, M.Deepthi, V.Mounika, R.N.Saranya Vignana Bharathi Institute of Technology, Hyderabad, and Andhra Pradesh, India. Corresponding
Performance Analysis of DSSS and FHSS Techniques over AWGN Channel M. Katta Swamy, M.Deepthi, V.Mounika, R.N.Saranya Vignana Bharathi Institute of Technology, Hyderabad, and Andhra Pradesh, India. Corresponding
UTILIZATION OF AN IEEE 1588 TIMING REFERENCE SOURCE IN THE inet RF TRANSCEIVER
 UTILIZATION OF AN IEEE 1588 TIMING REFERENCE SOURCE IN THE inet RF TRANSCEIVER Dr. Cheng Lu, Chief Communications System Engineer John Roach, Vice President, Network Products Division Dr. George Sasvari,
UTILIZATION OF AN IEEE 1588 TIMING REFERENCE SOURCE IN THE inet RF TRANSCEIVER Dr. Cheng Lu, Chief Communications System Engineer John Roach, Vice President, Network Products Division Dr. George Sasvari,
HOW DO MIMO RADIOS WORK? Adaptability of Modern and LTE Technology. By Fanny Mlinarsky 1/12/2014
 By Fanny Mlinarsky 1/12/2014 Rev. A 1/2014 Wireless technology has come a long way since mobile phones first emerged in the 1970s. Early radios were all analog. Modern radios include digital signal processing
By Fanny Mlinarsky 1/12/2014 Rev. A 1/2014 Wireless technology has come a long way since mobile phones first emerged in the 1970s. Early radios were all analog. Modern radios include digital signal processing
Spectrum Sensing Brief Overview of the Research at WINLAB
 Spectrum Sensing Brief Overview of the Research at WINLAB P. Spasojevic IAB, December 2008 What to Sense? Occupancy. Measuring spectral, temporal, and spatial occupancy observation bandwidth and observation
Spectrum Sensing Brief Overview of the Research at WINLAB P. Spasojevic IAB, December 2008 What to Sense? Occupancy. Measuring spectral, temporal, and spatial occupancy observation bandwidth and observation
Anti-Jamming: A Study
 Anti-Jamming: A Study Karthikeyan Mahadevan, Sojeong Hong, John Dullum December 14, 25 Abstract Addressing jamming in wireless networks is important as the number of wireless networks is on the increase.
Anti-Jamming: A Study Karthikeyan Mahadevan, Sojeong Hong, John Dullum December 14, 25 Abstract Addressing jamming in wireless networks is important as the number of wireless networks is on the increase.
GAME THEORY MANET ROUTING FOR JAMMING ENVIRONMENT. Yi Zhu
 GAME THEORY MANET ROUTING FOR JAMMING ENVIRONMENT by Yi Zhu A thesis submitted to the Faculty of the University of Delaware in partial fulfillment of the requirements for the degree of Master of Science
GAME THEORY MANET ROUTING FOR JAMMING ENVIRONMENT by Yi Zhu A thesis submitted to the Faculty of the University of Delaware in partial fulfillment of the requirements for the degree of Master of Science
OPTIMAL ACCESS POINT SELECTION AND CHANNEL ASSIGNMENT IN IEEE NETWORKS. Sangtae Park, B.S. Thesis Prepared for the Degree of MASTER OF SCIENCE
 OPTIMAL ACCESS POINT SELECTION AND CHANNEL ASSIGNMENT IN IEEE 802.11 NETWORKS Sangtae Park, B.S. Thesis Prepared for the Degree of MASTER OF SCIENCE UNIVERSITY OF NORTH TEXAS December 2004 APPROVED: Robert
OPTIMAL ACCESS POINT SELECTION AND CHANNEL ASSIGNMENT IN IEEE 802.11 NETWORKS Sangtae Park, B.S. Thesis Prepared for the Degree of MASTER OF SCIENCE UNIVERSITY OF NORTH TEXAS December 2004 APPROVED: Robert
SPREAD SPECTRUM (SS) SIGNALS FOR DIGITAL COMMUNICATIONS
 Dr. Ali Muqaibel SPREAD SPECTRUM (SS) SIGNALS FOR DIGITAL COMMUNICATIONS VERSION 1.1 Dr. Ali Hussein Muqaibel 1 Introduction Narrow band signal (data) In Spread Spectrum, the bandwidth W is much greater
Dr. Ali Muqaibel SPREAD SPECTRUM (SS) SIGNALS FOR DIGITAL COMMUNICATIONS VERSION 1.1 Dr. Ali Hussein Muqaibel 1 Introduction Narrow band signal (data) In Spread Spectrum, the bandwidth W is much greater
Innovative frequency hopping radio transmission probe provides robust and flexible inspection on large machine tools
 White paper Innovative frequency hopping radio transmission probe provides robust and flexible inspection on large machine tools Abstract Inspection probes have become a vital contributor to manufacturing
White paper Innovative frequency hopping radio transmission probe provides robust and flexible inspection on large machine tools Abstract Inspection probes have become a vital contributor to manufacturing
ELEC E7210: Communication Theory. Lecture 11: MIMO Systems and Space-time Communications
 ELEC E7210: Communication Theory Lecture 11: MIMO Systems and Space-time Communications Overview of the last lecture MIMO systems -parallel decomposition; - beamforming; - MIMO channel capacity MIMO Key
ELEC E7210: Communication Theory Lecture 11: MIMO Systems and Space-time Communications Overview of the last lecture MIMO systems -parallel decomposition; - beamforming; - MIMO channel capacity MIMO Key
Chapter 2 Overview - 1 -
 Chapter 2 Overview Part 1 (last week) Digital Transmission System Frequencies, Spectrum Allocation Radio Propagation and Radio Channels Part 2 (today) Modulation, Coding, Error Correction Part 3 (next
Chapter 2 Overview Part 1 (last week) Digital Transmission System Frequencies, Spectrum Allocation Radio Propagation and Radio Channels Part 2 (today) Modulation, Coding, Error Correction Part 3 (next
Wireless Networked Systems
 Wireless Networked Systems CS 795/895 - Spring 2013 Lec #4: Medium Access Control Power/CarrierSense Control, Multi-Channel, Directional Antenna Tamer Nadeem Dept. of Computer Science Power & Carrier Sense
Wireless Networked Systems CS 795/895 - Spring 2013 Lec #4: Medium Access Control Power/CarrierSense Control, Multi-Channel, Directional Antenna Tamer Nadeem Dept. of Computer Science Power & Carrier Sense
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Josh Broch, David Maltz, David Johnson, Yih-Chun Hu and Jorjeta Jetcheva Computer Science Department Carnegie Mellon University
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Josh Broch, David Maltz, David Johnson, Yih-Chun Hu and Jorjeta Jetcheva Computer Science Department Carnegie Mellon University
Medium Access Control. Wireless Networks: Guevara Noubir. Slides adapted from Mobile Communications by J. Schiller
 Wireless Networks: Medium Access Control Guevara Noubir Slides adapted from Mobile Communications by J. Schiller S200, COM3525 Wireless Networks Lecture 4, Motivation Can we apply media access methods
Wireless Networks: Medium Access Control Guevara Noubir Slides adapted from Mobile Communications by J. Schiller S200, COM3525 Wireless Networks Lecture 4, Motivation Can we apply media access methods
Are Wireless Sensors Feasible for Aircraft?
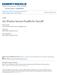 Department of Electrical, Computer, Software & Systems Engineering - Daytona Beach College of Engineering 5-2009 Are Wireless Sensors Feasible for Aircraft? Thomas Yang Embry-Riddle Aeronautical University,
Department of Electrical, Computer, Software & Systems Engineering - Daytona Beach College of Engineering 5-2009 Are Wireless Sensors Feasible for Aircraft? Thomas Yang Embry-Riddle Aeronautical University,
The Pennsylvania State University The Graduate School COMPROMISE-RESILIENT ANTI-JAMMING COMMUNICATION IN WIRELESS SENSOR NETWORKS
 The Pennsylvania State University The Graduate School COMPROMISE-RESILIENT ANTI-JAMMING COMMUNICATION IN WIRELESS SENSOR NETWORKS A Thesis in Computer Science and Engineering by Xuan Jiang c 2011 Xuan
The Pennsylvania State University The Graduate School COMPROMISE-RESILIENT ANTI-JAMMING COMMUNICATION IN WIRELESS SENSOR NETWORKS A Thesis in Computer Science and Engineering by Xuan Jiang c 2011 Xuan
Wireless Intro : Computer Networking. Wireless Challenges. Overview
 Wireless Intro 15-744: Computer Networking L-17 Wireless Overview TCP on wireless links Wireless MAC Assigned reading [BM09] In Defense of Wireless Carrier Sense [BAB+05] Roofnet (2 sections) Optional
Wireless Intro 15-744: Computer Networking L-17 Wireless Overview TCP on wireless links Wireless MAC Assigned reading [BM09] In Defense of Wireless Carrier Sense [BAB+05] Roofnet (2 sections) Optional
Channel selection for IEEE based wireless LANs using 2.4 GHz band
 Channel selection for IEEE 802.11 based wireless LANs using 2.4 GHz band Jihoon Choi 1a),KyubumLee 1, Sae Rom Lee 1, and Jay (Jongtae) Ihm 2 1 School of Electronics, Telecommunication, and Computer Engineering,
Channel selection for IEEE 802.11 based wireless LANs using 2.4 GHz band Jihoon Choi 1a),KyubumLee 1, Sae Rom Lee 1, and Jay (Jongtae) Ihm 2 1 School of Electronics, Telecommunication, and Computer Engineering,
Mohammed Ghowse.M.E 1, Mr. E.S.K.Vijay Anand 2
 AN ATTEMPT TO FIND A SOLUTION FOR DESTRUCTING JAMMING PROBLEMS USING GAME THERORITIC ANALYSIS Abstract Mohammed Ghowse.M.E 1, Mr. E.S.K.Vijay Anand 2 1 P. G Scholar, E-mail: ghowsegk2326@gmail.com 2 Assistant
AN ATTEMPT TO FIND A SOLUTION FOR DESTRUCTING JAMMING PROBLEMS USING GAME THERORITIC ANALYSIS Abstract Mohammed Ghowse.M.E 1, Mr. E.S.K.Vijay Anand 2 1 P. G Scholar, E-mail: ghowsegk2326@gmail.com 2 Assistant
/13/$ IEEE
 A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
Some Areas for PLC Improvement
 Some Areas for PLC Improvement Andrea M. Tonello EcoSys - Embedded Communication Systems Group University of Klagenfurt Klagenfurt, Austria email: andrea.tonello@aau.at web: http://nes.aau.at/tonello web:
Some Areas for PLC Improvement Andrea M. Tonello EcoSys - Embedded Communication Systems Group University of Klagenfurt Klagenfurt, Austria email: andrea.tonello@aau.at web: http://nes.aau.at/tonello web:
Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies
 Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com
Volume 2, Issue 9, September 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at: www.ijarcsms.com
Federal Communications Commission Office of Engineering and Technology Laboratory Division
 April 9, 2013 Federal Communications Commission Office of Engineering and Technology Laboratory Division Guidance for Performing Compliance Measurements on Digital Transmission Systems (DTS) Operating
April 9, 2013 Federal Communications Commission Office of Engineering and Technology Laboratory Division Guidance for Performing Compliance Measurements on Digital Transmission Systems (DTS) Operating
JADE: Jamming-Averse Routing on Cognitive Radio Mesh Networks
 JADE: Jamming-Averse Routing on Cognitive Radio Mesh Networks (Invited Paper) Yu Seung Kim, Bruce DeBruhl, and Patrick Tague Carnegie Mellon University Email: {yuseungk, bdebruhl, tague}@cmu.edu Abstract
JADE: Jamming-Averse Routing on Cognitive Radio Mesh Networks (Invited Paper) Yu Seung Kim, Bruce DeBruhl, and Patrick Tague Carnegie Mellon University Email: {yuseungk, bdebruhl, tague}@cmu.edu Abstract
Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks
 Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks Yuqun Zhang, Chen-Hsiang Feng, Ilker Demirkol, Wendi B. Heinzelman Department of Electrical and Computer
Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks Yuqun Zhang, Chen-Hsiang Feng, Ilker Demirkol, Wendi B. Heinzelman Department of Electrical and Computer
Frequency and Power Allocation for Low Complexity Energy Efficient OFDMA Systems with Proportional Rate Constraints
 Frequency and Power Allocation for Low Complexity Energy Efficient OFDMA Systems with Proportional Rate Constraints Pranoti M. Maske PG Department M. B. E. Society s College of Engineering Ambajogai Ambajogai,
Frequency and Power Allocation for Low Complexity Energy Efficient OFDMA Systems with Proportional Rate Constraints Pranoti M. Maske PG Department M. B. E. Society s College of Engineering Ambajogai Ambajogai,
Project = An Adventure : Wireless Networks. Lecture 4: More Physical Layer. What is an Antenna? Outline. Page 1
 Project = An Adventure 18-759: Wireless Networks Checkpoint 2 Checkpoint 1 Lecture 4: More Physical Layer You are here Done! Peter Steenkiste Departments of Computer Science and Electrical and Computer
Project = An Adventure 18-759: Wireless Networks Checkpoint 2 Checkpoint 1 Lecture 4: More Physical Layer You are here Done! Peter Steenkiste Departments of Computer Science and Electrical and Computer
