Reliable Intersection Protocols Using Vehicular Networks
|
|
|
- Letitia McCormick
- 6 years ago
- Views:
Transcription
1 Reliable Intersection Protocols Using Vehicular Networks Seyed (Reza) Azimi, Gaurav Bhatia and Ragunthan (Raj) Rajkumar Carnegie Mellon Universtiy s: Priyantha Mudalige General Motors Company Abstract Autonomous driving will play an important role in the future of transportation. Various autonomous vehicles have been demonstrated at the DARPA Urban Challenge [3]. General Motors has recently unveiled their Electrical-Networked Vehicles (EN-V) in Shanghai, China [5]. One of the main challenges of autonomous driving in urban areas is transition through crossroads and intersections. In addition to safety concerns, current intersection management technologies such as stop signs and traffic lights can introduce significant traffic delays even under light traffic conditions. Our goal is to design and develop efficient and reliable intersection protocols to avoid vehicle collisions at intersections and increase the traffic throughput. The focus of this paper is investigating vehicle-to-vehicle (V2V) communications as a part of co-operative driving in the context of autonomous vehicles. We study how our proposed V2V intersection protocols can be beneficial for autonomous driving, and show significant improvements in throughput. We also prove that our protocols avoid deadlock situations inside the intersection area. The simulation results show that our new proposed V2V intersection protocols provide both safe passage through the intersection and significantly decrease the delay at the intersection and our latest V2V intersection protocol yields over 85% overall performance improvement over the common traffic light models. I. INTRODUCTION Road intersections are currently managed by stop signs and traffic lights. These technologies have been designed to manage traffic and increase the safety at intersections, but there is a growing concern about their efficiency and safety. Each year, more than 2.8 million intersection-related crashes occur in the United States, accounting for more than 44% of all reported crashes [6]. In addition, the delays introduced by stop signs and traffic lights significantly increase trip times. This leads to a huge waste of human and natural resources. The 2011 Urban Mobility Report, published by the Texas Transportation Institute, illustrates that the amount of delay endured by the average commuter was 34 hours which costs more than $100 billion each year [2]. Past work in this domain includes the use of Vehicle-to- Infrastructure (V2I) communications by having a centralized system in which all vehicles approaching an intersection communicate with the intersection manager. The intersection manager is a powerful computational infrastructure installed at intersections that tells all vehicles crossing the intersection [10, 16] when they should cross or stop. Installing a centralized infrastructure at every intersection is somewhat impractical due to the prohibitively high total system costs Also, as in all centralized systems, the intersection manager is a single point of failure, and vehicles must somewhat coordinate on their own, in the case that the intersection manager fails. To address these shortcomings, in our previous work, we have introduced a family of vehicular network protocols to manage the safe passage of traffic across intersections [14, 15]. These completely distributed protocols rely on vehicle-to-vehicle (V2V) communications and localization to control and navigate vehicles within the intersection area. Autonomous vehicles approaching an intersection use Dedicated Short Range Communications (DSRC) and Wireless Access in a Vehicular Environment (WAVE) [4] to periodically broadcast information such as position, heading and intersection crossing intentions to other vehicles. The vehicles then decide among themselves regarding who crosses, who stops, etc. However, communication reliability is crucial for safety applications such as intersection collision avoidance. High packet loss will affect approaching vehicles communication across the intersection corners. In urban intersections, signal propagation within DSRC channels may get affected by fading. Line-of-Sight (LOS) conditions are not always available due to the presence of big buildings and other obstacles at intersection corners. In our current work, we have therefore designed and developed a new intersection protocol with a realistic channel propagation model. They have been implemented in our hybrid emulator-simulator for vehicular networks, called AutoSim. The propagation model is based on the Nakagamim model [11] that has been proven to significantly match with empirical results for signal propagation using DSRC/WAVE. We formally prove the deadlock-freedom property of our family of intersection protocols, we also perform many experiments to study the effects of packet loss on our V2V intersection protocols and measure the reliability of these protocols in the presence of channel impairments. The rest of this paper is organized as follows. Section II includes our latest V2V Intersection protocols and the deadlock-freedom analysis and proofs. Section III includes the Nakagami-m propagation and communication loss model. Section IV includes the implementation of our V2V intersection protocols and the DSRC channel propagation model in AutoSim. In Section V, we evaluate these protocols under various wireless communication conditions. Section VI describes our conclusion and future work. II. V2V INTERSECTION PROTOCOLS A. Collision Detection In this section, we describe the two generations of our V2V intersection protocols. These protocols have been designed to
2 increase the throughput at intersections while avoiding collisions. Vehicles use V2V communications using DSRC/WAVE to broadcast intersection safety messages to other vehicles in their communication range. These protocols enable cooperative driving among approaching vehicles to ensure their safe passage through the intersection. Our assumption is that all the vehicles are equipped with Global Positioning System (GPS) devices and have access to a digital map database, which provide them with critical information such as position, heading, speed, road and lane details. Intersection safety messages are broadcast at 10Hz and they contain the trajectory details of the sender along the intersection area. The format of these safety messages is defined by SAE s J2735 standard [4] and we use the second part of Basic Safety Messages (BSM) for the extra information in our intersection safety messages. We have assumed that, in all our protocols, all vehicles have similar shape and physical dimensions. 1 The intersection area is modeled as a grid which is divided into small cells. Each cell in the intersection grid is associated with a unique identifier. Figure 1 shows an intersection with two lanes entering the intersection grid from all four directions. The Trajectory Cells List (TCL) is defined as the ordered list of the cell numbers which will be occupied by a vehicle along its trajectory inside the intersection box. In this example scenario, vehicle A s TCL is 8,7,6,5 and vehicle B s TCL includes cell numbers 15,11,7,3. Fig. 1: Intersection Grid Our proposed V2V intersection protocols make use of our Collision Detection Algorithm for Intersections (CDAI) [14]. CDAI runs on all vehicles, using the information obtained from received safety messages broadcast by surrounding vehicles. The algorithm uses the TCLs of the sender and the receiver of the safety messages and by comparing the two lists, it determines if there is any common cell along their trajectories while crossing the intersection. If a potential collision is detected by CDAI, the algorithm returns the first conflicting cell number which we refer to as Trajectory Intersecting Cell (TIC). For example in Figure 1, cell number 7 is the TIC between vehicles A and B. When no potential collision is detected among the sender and the receiver(s) of intersection safety messages, they can safely cross the intersection concurrently without stopping or slowing down. This behavior increases the throughput of the intersection by decreasing any unnecessary delays faced by 1 Relaxing this assumption is the subject of ongoing work. approaching vehicles. But if a potential collision is detected, vehicles identify the common cell(s) among their TCLs. In this case, vehicles use a pre-designed priority policy and follow the assigned Intersection Protocol (IP) rules to cross the intersection area. We have implemented a First-Come, First-Served (FCFS) as our priority policy, in which priorities are assigned to vehicles based on their arrival time to the intersection. In the case that two or more vehicles arrive at the intersection almost at the same time, ties can also be broken in favor of vehicles on a main road. If there is still a tie, it is broken by Vehicle Identification Number (VIN), which is uniquely assigned to each vehicle. In our intersection protocols, each vehicle uses 3 types of intersection safety messages to interact with other vehicles within its communication range. 1) An ENTER message is used to inform the neighboring vehicles that the vehicle is approaching the intersection area with specific crossing intentions. The ENTER message contains 9 parameters: Vehicle ID, Current Road Segment, Current Lane, Next Road Segment, Next Vertex, Arrival-Time, Exit-Time, Trajectory Cells List,Cells Arrival Time List, Message Sequence Number and Message Type, which is ENTER in this case. 2) A CROSS message is to inform that the vehicle is inside the intersection grid, this message contains the sender s identification and trajectory details, identifying the space that will be occupied by the vehicle while crossing the intersection. The CROSS message contains the same parameters as the ENTER message. Its Trajectory Cells List contains the updated list of trajectory cells and their related arrival times for the current cell and remaining cells along the vehicle s trajectory through the intersection area, and the CROSS Message Type. 3) An EXIT message indicates that the vehicle has exited the intersection boundaries. The EXIT message contains 3 parameters: Vehicle ID, Message Sequence Number, and EXIT Message Type. Every vehicle uses its own GPS coordinates, speed and also the map database to compute the distance to the approaching intersection and the distance passed from the previous intersection. We consider three intersection states for each vehicle based on its relative location to the intersection area. Intersection-Approach: when vehicle s distance to the approaching intersection is less than a threshold parameterd ENT ER. Intersection-Enter: when the vehicle is inside the intersection grid s boundaries. Intersection-Exit: when the vehicle exits the intersection, until it travels farther than a threshold value D EXIT from the exit point of the intersection. We have categorized our intersection protocols based on the actions taken by potentially conflicting vehicles to avoid collisions. Potentially conflicting vehicles are those vehicles which have trajectory conflicts with one or more crossing vehicles through the intersection area and may get into a potential collision. The first category includes Through-
3 put Enhancement Protocol (TEP) and Concurrent Crossing- Intersection Protocol (CC-IP) [14, 15]. In this category, the conflicting vehicle with higher priority can ignore the intersection safety messages from other lower-priority vehicles and cross the intersection without slowing down or stopping. However, any lower-priority vehicle is super-cautious and when it loses a competition, it comes to a complete stop before entering the intersection boundaries, and waits till it receives a CLEAR message, from the higher-priority vehicle. This message informs the lower-priority vehicle that the higherpriority vehicle has crossed the intersection and now the intersection area is safe for its passage. This protocol is applied across all priority levels. The second category of Intersection Protocols is referred to as Spatio-Temporal Intersection Protocols (STIP). The main goal is to increase the parallelism inside the intersection area by allowing more vehicles to cross the intersection at the same time. STIP includes the Maximum Progression Intersection Protocol (MP-IP) and the Advanced Maximum Progression Intersection Protocol (AMP-IP). We will present both these protocols in this paper and study their properties. B. Maximum Progression Intersection Protocol (MP-IP) MP-IP is designed to increase the intersection throughput by allowing even potentially conflicting vehicles to progress inside the intersection area, when the primary goal of safe passage of all vehicles across the intersection can be satisfied. Here we define the terms that will be used in our theorems. P v : Priority of vehicle v. This is determined by the priority policy. S v : Set of cells required for vehicle v to cross the intersection. It consists of the current cell and next cells that will be occupied by vehicle v. C v : Current cell occupied by vehicle v. N v : Next cell that will be occupied by vehicle v. T IC v,y : Trajectory Intersecting Cell between the higherpriority vehicle v and lower-priority vehicle y. Algorithm 2 MP-IP, Receiver Vehicle Input: Safety message received from vehicle A, RM Output: Vehicle B s movement at the intersection if (RM = ENT ER or RM = CROSS) then Run CDAI to detect trajectory conflicts with vehicle A and find T IC A,B if (T IC A,B = NULL) then else Run FCFS priority policy if (P B > P A ) then else Progress and stop before entering T IC A,B else if RM = EXIT then if T IC A,B is cleared then We now illustrate MP-IP with an example. Figure 2 shows two vehicles A and B, approaching an intersection. We assume that vehicle A has higher priority than vehicle B. In this case, vehicle A gets to cross the intersection without stopping or even slowing down. Vehicle B shall progress inside the intersection grid and stop before entering the TIC with vehicle A, which is cell number 6. As vehicle A leaves cell number 6, it updates its TCL to [10,14] and sends a CROSS message. This informs vehicle B that the TIC is now clear and it can continue its trajectory through the intersection by proceeding to cell number 6. Based on the above definitions, one can derive the following logical relations: C v N v and C v S v and N v S v The following rules are applicable to all vehicles: Algorithm 1 MP-IP, Sender Vehicle Input: Vehicle s intersection state Output: Broadcast intersection safety message if STATE=Intersection-Approach then Broadcast ENTER message else if STATE=Intersection-Enter then Broadcast CROSS message else if STATE=Intersection-Exit then Broadcast EXIT message And here are the rules applied to a vehicle B when it receives intersection messages from a vehicle A, where (A B). Fig. 2: An example scenario for MP-IP C. MP-IP Freedom from Deadlock A deadlock is a situation in which two or more competing actions are each waiting for another to finish, and thus neither ever does. A deadlock situation can occur inside the intersection area, among the vehicles which are trying to cross the intersection at the same time. To better explain such scenarios, we use wait-for graphs. A wait-for graph
4 is a directed graph used for deadlock detection in operating systems and relational database systems. A deadlock exists if the graph contains any cycles. We now investigate a possible deadlock scenario, in which all vehicles progress inside the intersection area as much as possible without getting into a collision. As we can see in Figure 3, vehicle A s next cell is occupied by vehicle D, vehicle D s next cell is occupied by vehicle C, vehicle C s next cell is occupied by vehicle D, and finally vehicles B s next cell is occupied by vehicle A. This means that none of these vehicles can progress inside the intersection grid as each of their next cells are occupied by other vehicles. For the purpose of this paper, we define the elements of our intersection wait-for graph as follows. Vehicles are represented as the nodes of our wait-for graph, and an edge from vehicle B to vehicle A implies the vehicle A is holding a cell that vehicle B needs, to complete its trajectory through the intersection grid. Thus, vehicle B is waiting for vehicle A to release (leave) that specific cell. It can be seen clearly in Figure 4 that the corresponding wait-for graph contains a cycle and therefore it is a deadlock situation. Suppose that P A > P B and we have, C B = N A S A S B φ (1) Based on the Trajectory Dependency and MP-IP Rule, from Equation (1): B A C B / S A (2) But from deadlock conditions, we have C B = N A, so: C B = N A C B S A (3) (2) and (3) cannot be true at the same time. This is a contradiction. So C B = N A cannot be true while C A = N B. We now consider the deadlock situation with n vehicles, n > 2. We must therefore have C A = N B and C B = N C and... C Y = N Z and C Z = N A. Suppose that P A > P B > P C >... > P Z So we have: P A > P B > P C >... > P Z P A > P Z C Z = N A S A S Z φ (4) Fig. 3: A Deadlock scenario Based on the Trajectory Dependency and the MP-IP Rule, from (4): Z A C Z / S A (5) Fig. 4: Wait-for graph for an example deadlock scenario Definition 1. Trajectory Dependency: Vehicle A s trajectory depends on vehicle B s trajectory iff two conditions are true at the same time: 1) The priority of vehicle A is lower than the priority of vehicle B. 2) There is a common cell along their trajectory cells. The above statement can be written as: [(P A < P B ) and S A S B φ] A B Rule 1. MP-IP Rule: If vehicle A s trajectory depends on vehicle B s trajectory, then vehicle A cannot enter any of the cells reserved by vehicle B. (A B) C A / S B Theorem 1. Without loss of generality, the MP-IP is deadlock-free. Proof: We prove the theorem by contradiction. Suppose we have two vehicles. Deadlock condition is as follows: C A = N B and C B = N A But deadlock conditions, states that C Z = N A, so: C Z = N A C Z S A (6) (5) and (6) are contradictory. So C Z = N A cannot be true while C A = N B and C B = N C and C Y = N Z So we can conclude that the deadlock situation is avoided by applying the MP-IP Rule. We now apply MP-IP to the deadlock scenario of Figure 3. Figure 5 shows that vehicle A can progress without worrying about other vehicles, as it has the highest priority among them. Vehicle B progresses to cell number 7, and stops before entering cell number 6, since it is a part of vehicle A s TCL. The same MP-IP rule applies to vehicles C and D. Since D has potential conflicts with vehicles A and C, and both of them have higher priorities than D, then D has to stop before entering any of those conflicting cells, numbers 10 and 11. As cell number 10 is the first conflicting cell along vehicle D s trajectory, it stops before entering this cell and waits in cell 9 until A crosses and leaves cell 10. So, no cycle is formed and the highest-priority vehicle A has all the cells cleared for its trajectory through the intersection area. After the last step showed in Figure 5, all the vehicles can progress to the next cell along their trajectory and cross the intersection area safely, without causing any deadlock situation.
5 Fig. 5: Deadlock is avoided by the MP-IP Rule D. Advanced Maximum Progression Intersection Protocol (AMP-IP) This protocol is built based on MP-IP s key idea that conflicting vehicles can make concurrent progress inside the intersection grid when collisions can still be avoided. Additionally, AMP-IP has the advantage of allowing the lowerpriority vehicles to cross the conflicting point and clear the conflicting cell before the arrival of the higher-priority vehicle to that cell. Each vehicle uses its GPS coordinates, controller model parameters and digital map information to calculate its current position, velocity and distance to any point at the intersection grid. All this information is used as inputs to measure the exact arrival time of the vehicle to each cell along its trajectory while crossing the intersection area. When a vehicle detects a potential collision with a higher-priority vehicle, it compares its own arrival time at the conflicting cell with the arrival time of the higher-priority vehicle to the same cell. If its arrival time is sufficiently earlier than the arrival time of the higherpriority vehicle, then it can go ahead and cross the conflicting cell without stopping for the higher-priority vehicle. To ensure the safe passage of both the potentially conflicting vehicles, we use a Safety Time Interval to increase the safety and make sure that the lower-priority vehicle has enough time to leave and clear the conflicting cell completely, before the arrival of the higher-priority vehicle to that cell. Based on the Newtonian equations of motion, we set the Safety Time Interval as follows: D(t) = D 0 + V 0 t + 1/2at 2 t = V 0 + V aD (7) 2a As of year 2010, the amount of time that an average vehicle takes to accelerate from 0 miles per hour (mph) to 60 mph is about 8.95 seconds. This value has been calculated by averaging the acceleration parameter of 1,807 car records [1]. Using this value, we calculate the maximum acceleration to be approximately m s. The width of each cell is assumed 2 to be 5 meters. The worst-case scenario is when the initial speed of the vehicle is 0 m s and the time to cross the cell is the maximum possible. By replacing these values in Equation (7), the Safety Time Interval is calculated as s, which has been rounded up to 2s for our protocol. We now define the terms that will be used in our proof. T IC V,Y : Trajectory Intersecting Cell between the higher-priority vehicle V and lower-priority vehicle Y. AT V,c : Arrival Time of vehicle V to cell c. ET V,c : Exit Time of vehicle V from cell c. Θ: The Safety Time Interval. Similar to MP-IP, vehicles make use of the intersection safety messages to inform their neighbors about their intentions to enter, cross and finally exit the intersection area. In AMP-IP, the ENTER and CROSS safety messages contain additional information about the cells that will be occupied by the vehicle while crossing the intersection grid. This information includes the estimated arrival time of the vehicle to each of the cells in its TCL through the intersection grid. The same rules as in Algorithm 1, apply to all sender vehicles. The following rules are applied to a vehicle B when it receives intersection messages from a vehicle A, where (A B). Algorithm 3 AMP-IP, Receiver Vehicle Input: Safety message received from vehicle A: RM Output: Vehicle B s movement at the intersection if RM = ENT ER or RM = CROSS then Run CDAI to detect trajectory conflicts with vehicle A and find T IC A,B if (T IC A,B = NULL) then else Use FCFS priority policy if (P B > P A ) then else c = T IC A,B if ([AT B,c + Θ] < AT B,c ) then else Progress and stop before entering T IC A,B else if RM = EXIT then if T IC A,B is cleared then Figure 6 shows the same scenario as Figure 2 but, with vehicles following AMP-IP rules. As before, since vehicle A has a higher-priority than vehicle B, it gets to cross the intersection without stopping or even slowing down. Vehicle B compares its own arrival time to the TIC, which is cell number 3 with the arrival time of vehicle A to the exact same cell. In the case that vehicle B arrives there earlier, and has enough time to clear the cell before the arrival of vehicle A, then instead of progressing only up to the TIC, it can progress into and clear the conflicting cell number 3. So, by using AMP-IP, we allow the lower-priority vehicle to go ahead and cross the conflicting cell before the arrival of the higher-priority vehicle. This action decreases the delay
6 C A = N B and C B = N C and... C Z = N A Suppose that P A > P B > P C >... > P Z Based on the Trajectory Dependency, [P A > P Z and S A S Z φ] Z A (12) From Deadlock conditions, we have C A = N Z = T IC A,Z, so vehicle A is already in cell T IC A,Z, C A = N Z ET Z,T ICA,Z > AT A,T ICA,Z (13) Fig. 6: An example scenario for AMP-IP time faced by this vehicle and increases the total throughput of the intersection. E. AMP-IP Freedom from Deadlock In this section, we prove that using AMP-IP cannot lead to a deadlock situation. Rule 2. AMP-IP Rule: If vehicle A s trajectory depends on vehicle B s trajectory, then A cannot enter the T IC B,A, unless it is able to leave T IC B,A before B arrives to that cell. Suppose that n = T IC B,A. The AMP-IP rule can also be stated as: {(A B) and (ET A,n > AT B,n )} C A / S B Theorem 2. There is no deadlock under AMP-IP. Proof. We prove these properties using contradiction. Suppose we have two vehicles. Deadlock condition is as follows: C A = N B and C B = N A By AMP-IP rule and from equations (12), (13): From the deadlock condition, we have: C Z / S A (14) C Z = N A C Z S A (15) (14) and (15) are contradictory. So C Z = N A cannot be true while C A = N B and C B = N C and C Y = N Z. Let us apply the AMP-IP rule to the deadlock scenario of Figure 3. Since vehicle D does not have enough time to clear T IC C,D before vehicle C arrives at that cell, it will not even enter the first TIC, which is T IC A,D. So the trajectory is not blocked for the higher-priority vehicle A and deadlock does not happen. Hence the same scenario as in Figure 5 occurs. However, if vehicle D has enough time to clear both T IC A,D before vehicle A gets there and clear T IC C,D before vehicle C gets there, it will cross both conflicting cells. As we can see in Figure 7, this behavior of vehicle D, will allow the road to be clear for higher-priority vehicles A and C, and again no deadlock occurs. Suppose thatp A > P B Based on the trajectory dependency: [P A > P B and S A S B φ] B A (8) From Deadlock conditions, we have C A = N B = T IC A,B, so vehicle A is already in cell T IC A,B : C A = N B ET B,T ICA,B > AT A,T ICA,B (9) By AMP-IP rule and from Equations (8), (9): From Deadlock, we have: C B / S A (10) C B = N A C B S A (11) (10) and (11) cannot be true at the same time. This is a contradiction. So C B = N A cannot be true while C A = N B. Now consider the deadlock situation with n vehicles, n > 2. Fig. 7: An example scenario for AMP-IP III. V2V SIGNAL PROPAGATION USING DSRC CHANNELS As explained in Section II, our intersection protocols rely on vehicle-to-vehicle communications. All vehicles use V2V messages to interact with one another and use the information within these messages to control their movements such as adjusting their speed during their trajectory through the intersection area. We know that wireless communication is not perfect and channel impairments decrease the reliability of vehicular communications. As vehicles approach an intersection with relatively high speeds, it is vital to receive the intersection safety messages within a very short time interval to be able to react, and get to a full stop before entering
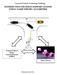
7 the intersection area when necessary. Channel impairments such as fading will decrease the communication reliability by increasing the packet loss ratio. Therefore, a high rate of packet loss will affect the communication as vehicles do not receive the information soon enough to avoid collisions at the intersection. Figure 8 illustrates an intersection crossing scenario from our hybrid emulator-simulator, AutoSim. In this scenario, vehicle A is attempting to enter the intersection from the North and turn left heading east. Vehicle B arrives at the intersection slightly after vehicle A, and attempts to go straight. As they have a trajectory conflict, they may get to a potential collision if they attempt to cross the intersection at the same time. When the communication medium is perfect and there is no packet loss, vehicle B will receive the intersection safety messages from vehicle A. As vehicle B is assigned a lower priority based on its arrival time, it allows vehicle A to safely cross the intersection first. In contrast, when the packet loss rate is too high, intersection safety messages among these vehicles can be lost, and vehicle B has no information about the higherpriority vehicle, A. So, it attempts to cross the intersection without stopping or slowing down and this leads to a collision between vehicles A and B. Fig. 8: Snapshots from AutoSim simulator. V2V intersection management: (a) No packet loss and safe passage of vehicles (b) High packet loss rate results in an accident An often used realistic and probabilistic model for wireless signal propagation using DSRC channels is the Nakagami-m model. This model estimates the received signal strength in multipath environments, in which the channel is influenced by various degrees of fading. Nakagami-m fading with the shape parameter m and distribution spread parameter is expressed as: f(x) = 2mm x (2m 1) Γ(m)Ω m exp(mx2 ) Ω, x > 0, Ω > 0, m > 1 2 When the signal amplitude follows the Nakagami distribution, the power follows the Gamma distribution, p(x) = ( m x(m 1) )m Ω Γ(m) exp( mx Ω ) where Γ(m) is a complete gamma function of parameter m. Taliwal et al. [17] have shown that this model agrees with empirical data. Figure 9 shows the probability of reception based on the distance between the transmitter and the receiver for various values of m and the communication range of 500 meters. Yin et al. [8, 9] have performed statistical fading analysis based on DSRC empirical data. Their analysis shows that, for distances less than 100m, the fading appears to follow a Rician fading distribution, in which m > 1. When the distance is greater than 100m, it generally follows a Rayleigh Fig. 9: Probability of successful packet reception. fading distribution, in which m = 1 and it models a harsh Non-Line-Of-Sight (NLOS) scenario. We will use the Nakagami-m model to study the impact of imperfect V2V communication on our intersection protocols. We will assume a deterministic model for the transmission power for the Nakagami-m model, that is, the power necessary to reach a communication range of certain meters. Increasing the transmission power will eventually increase the communication range. This results in higher Packet Delivery Ratio (PDR) and communication reliability. In sparse traffic conditions, the channel load is light and increasing the transmission power does not carry negative consequences. When dealing with busy urban intersections in which the traffic is dense, a high number of safety messages is broadcast, and results in higher channel load and may lead to channel congestion. We will evaluate such environments in the next section. In scenarios where V2V communications has a high packet loss ratio due to obstacles or channel congestion, local-sensing technologies can be used to avoid collisions at the intersection. We believe that by combining V2V communications with local-sensing information obtained by sensors, cameras, radars and thermal images, highly reliable collision avoidance is achievable even in extreme environment scenarios. IV. IMPLEMENTATION In this section, we describe the implementation of the V2V protocols and the V2V communication model. In order to analyze our intersection protocols and their communication reliability, the DSRC propagation model and the traffic flow at intersections need to be studied. For this purpose, we use a tool called AutoSim. This simulator-emulator is an extension to GrooveNet [12, 13]. AutoSim is a hybrid emulator-simulator for vehicular communication and interaction. It facilitates protocol design as well as in-vehicle deployment and uses real street-map-based topography. This enables city-wide simulations using different types of trip and messaging models. The simulator uses a model-based approach where different models interact with each other resulting in vehicular movement. Each simulated vehicle is made up of several types of models. The core individual modules are control, communication, mobility and pose estimation. The mobility models within AutoSim are used to implement different types of intersection protocols. AutoSim also has real-time emulation capability wherein real and simulated cars can co-exist and interact with each
8 other. The communication interfaces for DSRC communication as well as peripheral sensory interfaces are implemented to enable real cars instrumented with DSRC to react in realtime with simulated cars. The communication protocol uses Basic Safety Messages (BSM) [4] that are broadcast as part of the WAVE mechanism. A brief description of the relevant models follows: Traffic light model: This model simulates the traffic light intersections in the real world. We have used the two most common green light durations of 10 seconds and 30 seconds. V2V Intersection models: These models have been designed to implement our CC-IP, MP-IP and AMP-IP protocols. All vehicles use pure V2V communication to interact with each other. Controller model: This realistic model has been designed to control the movement of vehicles based on their speed, acceleration and deceleration profiles. This impacts the movement of vehicles through intersections. In our current work, all vehicles are assumed to have from similar shape, physical dimensions and dynamic capabilities. Communication model: This model has been used to simulate the wireless communication among the vehicles using DSRC/WAVE technologies. This model includes the Nakagami-m propagation model that matches with empirical results for vehicle-to-vehicle (V2V) communications. V. EVALUATION In this section, we evaluate the proposed protocols using various propagation models and mobility models that we have designed and simulated in AutoSim. A. Metric We define the trip time for a vehicle, as the time taken by that vehicle to go from a fixed start-point before the intersection to a fixed end point after the intersection. We calculate the trip time for each simulated car under each model and compare that against the trip time taken by the car assuming that it stays at a constant street speed and does not stop at the intersection. The difference between these two trip times is considered to be the Trip Delay due to the intersection. We take the average trip delays across all cars in a simulation sequence as our metric of comparison. Our other metric is Packet Delivery Ratio (PDR). PDR has been widely used as the major metric to evaluate radio channel characteristics. PDR is defined as the probability of successful packet reception and is measured as the ratio of the successfully received packets to the total number of packets transmitted within a pre-defined time interval. B. Scenarios Since there is a large variation in intersection types, we restrict our attention to Four-way Perfect-Cross Intersections, in which the intersection legs are at perfect right angles to the neighboring leg. In our simulations, the traffic generation follows the Poisson random distribution. We have looked at a wide range of traffic densities. Our simulations include very sparse traffic rural intersections with the mean value of 0.1 cars per second in each direction of the intersection, and also very busy urban intersections with the mean value of 1 car per second in each direction. We run all our simulations on 4-lane roads, with 2 lanes in each direction. The intersection type, vehicle routes and turn-types are generated offline. Each vehicle is removed from simulation when it reaches its destination. Each simulation run uses 1000 vehicles, and each run is terminated when the last vehicle reaches its destination. C. Experimental Results We have compared the traffic light model to our proposed V2V-based protocols, the Concurrent Crossing-Intersection Protocol (CC-IP), the Maximum Progression-Intersection Protocol (MP-IP) and the Advanced Maximum Progression- Intersection Protocol (AMP-IP). Figure 10 shows this comparison for a perfect-cross intersection. The traffic is assumed to be symmetric, meaning equal amount of traffic volume in every direction and an equal amount of turn ratios. The X- axis is the traffic volume determined as cars per second and the Y-axis is the delay in seconds. All our V2V-based models outperform the traffic light models. CC-IP, MP-IP and AMP-IP have respectively 48.78% and 70.82% and 85.75% overall performance improvements over the traffic light model with a 10-second green light time. The average delay is very negligible for lower traffic volumes in MP-IP and AMP-IP V2V-based models. Under MP-IP and AMP-IP, the delays stay very low even with higher traffic volumes. AMP-IP outperforms CC-IP and MP-IP respectively by 69.94% and 51.15%. Based on our results under AMP-IP, the average delay faced by vehicles at the intersection, even in very high traffic densities, is as low as 22 seconds. Note that this traffic volume is significantly higher than the traffic density in Manhattan area during rush hour. Fig. 10: Delay comparison among different mobility models We next studied the case where the traffic volume is significantly different on the intersection roads. We assume that the North-South directions of the intersection has higher traffic density and the intersecting East-West directions has the roads with lower traffic on them. However, the roads have the same type and priority to cross the intersection. Figure 11 shows that the Advanced Maximum Progression- Intersection Protocol (AMP-IP) performs better than other V2V-based models and also outperforms the traffic light model significantly. Figure 12 illustrates the performance
9 comparisons between the asymmetric traffic (various traffic volumes among the intersection roads) and the symmetric traffic under the rule of AMP-IP and the traffic light model. As we expect, the vehicles arriving on the higher traffic density roads face higher delays which increases the overall average delay. In the case of the traffic light model, this difference is huge and unfair, since vehicles arriving from the higher volume traffic direction are forced to face much higher delays. However, AMP-IP results in more fair passage of vehicles through the intersection. Fig. 13: AMP-IP Average delays. Higher priority for higher volume roads. Fig. 11: Delay comparison for asymmetric traffic. model and bigger values of m are used to model the intersections with less number of obstacles such as tall buildings. We use three values for the fading parameter m = 1, 2, 3 and transmission power of 20dBm. A deterministic Two-ray Ground propagation model has been assumed for the transmission power for the Nakagami model. Using this model, we have set the effective Communication Range (CR) of 200m in our simulation. Figure 14 shows the PDR comparison among intersection environments with different fading degrees. Based on the results of the Nakagami-m propagation model and as we expected, for the lower values of fading parameter m, the PDR values drop faster as the distance increases between the transmitter and the receiver of the intersection safety messages. Fig. 12: Delay comparison between traffic light and AMP-IP in symmetric and asymmetric traffic. We finally studied the scenario in which higher priorities have been assigned to high-traffic-volume roads, in order to allow more vehicles to cross the intersection coming from the higher-density roads. This reduces the backed-up traffic and accordingly increases the overall throughput of the intersection. Figure 13 shows the comparisons between two different scenarios using AMP-IP. Note that assigning higher priorities to higher traffic volume roads outperforms the scenario that all legs of the intersection have the same priority. The improvement is small at low volume traffic but it increases significantly as the traffic density increases. These results highlight the importance of an appropriate priority policy and how assigning higher priorities to vehicles on the high-volume traffic roads can decrease the overall delay and increase the throughput of the intersection significantly while dealing with a large number of vehicles at the intersection. We now measure the PDR value based on the distance between the transmitter and the receiver of intersection safety messages in various traffic scenarios. We look at the intersections with different amounts of obstacles which lead to different multipath degrees. To simulate a harsh NLOS environment, we use m = 1 in our Nakagami-m propagation Fig. 14: Packet Delivery Ratio with communication range of 200 meters The results in Figure 14 confirm that by increasing the transmission power and hence increasing the communication range, the PDR values are significantly higher for various distances between any transmitter and receiver pairs. But the main drawback is that in dense traffic environments, increasing the transmission power ends in involving more vehicles and higher chance of channel congestion as the channel load increases significantly. We have logged the statistics for all simulated vehicles such as their position information at any moment while crossing the intersection. This information has been used to log any accidents among the vehicles trying to concurrently pass through the intersection area. Our results show that absolutely no accidents happen in any tested traffic volumes at the intersection. All the vehicles make their decision about how to cross the intersection, while they are approaching it and, based on the intersection safety messages sent by other vehicles every 100ms. This surprisingly positive result is because of receiving at least one safety message from any other approaching vehicle is
10 sufficient to detect any potential collisions using the CDAI, and to come to a complete stop before entering the intersection boundaries. Since it takes seconds to cross an intersection, at least one such message is received on time. Fan Bai et al. [7] define the Safety application reliability as the probability of successfully receiving at least one single packet from neighbor vehicles during the tolerance time window T. This is calculated as follows: P Application = 1 (1 P Comm ) N Where, N is the number of messages sent during the time window T and P Comm is the communication reliability which is calculated as the probability of successfully receiving each packet. In our proposed protocols, vehicles start broadcasting the safety messages when their distance to the entrance of the intersection is less thand ENT ER, which is set to 20 meters in our simulations. As these safety messages are transmitted with the frequency of 10Hz, the tolerance time window T is at least 500ms. This has been calculated based on vehicle s speed and deceleration parameters, and the safe distance to get to a complete stop before entering the intersection box. Figure 15 shows the measured safety application reliability for our intersection protocols in various multipath environments. We notice that our proposed V2V intersection management protocols have the average application reliability very close to 100%, for distances of up to 100m between the transmitter and the receiver vehicles. Fig. 15: Application reliability, with communication range of 200 meters. We therefore conclude that our proposed intersection protocols support safe traversal through intersections at substantially higher throughput even with imperfect and practical wireless environments. environments such as intersections with tall buildings at all corners. Significant increase in traffic throughput with the least dependency on static infrastructure is the other benefit of using these intersection management protocols. Although our protocols are designed for autonomous vehicles that use V2V communication for co-operative driving in future intelligent transportation systems, they can be adapted to a driver-alert system for manual vehicles at traffic intersections. In our ongoing work, we are addressing the following limitations. As mentioned in this paper, we currently do not deal with position inaccuracies. Position accuracy will affect the protocols since each vehicle depends on its position and the known position of the other vehicles to make safetycritical decisions. We believe that in extreme environment scenarios where the channel is congested and the packet loss rate is very high, local sensing technologies such as cameras, radars, lasers and thermal images can be combined with V2V and V2I communications to avoid any potential collisions. REFERENCES [1] mph statistics, [2] The 2011 urban mobility report, published by the texas transportation institute. available: [3] Darpa. the darpa urban challenge, available: [4] Draft sae j dedicated short range (dsrc) message set dictionary. [5] General motors, en-v concept vehiclesat expo available: [6] Us department of transportation-federal highway administration publication, national agenda for intersection safety. available: [7] Fan Bai, Hariharan Krishnan. Reliability analysis of dsrc wireless communication for vehicle safety applications. April [8] J. Yin, T. ElBatt. Performance evaluation of safety applications over dsrc vehicular ad hoc networks [9] Jijun Yin; Holland, G.; ElBatt, T.; Fan Bai; Krishnan, H. Dsrc channel fading analysis from empirical measurement [10] K. Dresner, P. Stone. A multiagent approach to autonomous intersection management [11] M. Nakagami. The m-distribution, a general formula of intensity of rapid fading. June [12] R. Mangharam, D. S. Weller, R. Rajkumar,P. Mudalige and Fan Bai. Groovenet: A hybrid simulator for vehicle-to-vehicle networks. July [13] R. Mangharam, J. Meyers, R. Rajkumar, D. Stancil, J. Parikh, H. Krishnan, and C. Kellum. A multi-hop mobile networking test-bed for telematics. April [14] R.Azimi, G. Bhatia, R. Rajkumar, P. Mudalige. Vehicular networks for collision avoidance at intersections. April [15] R.Azimi, G. Bhatia, R. Rajkumar, P. Mudalige. Interesection mangement using vehicular networks. April [16] Richard K. Shulman, Mike; Deering. Crash avoidance metrics partnership (camp) - second annual report,sponsored by nhtsa, washington d.c., april march 2003, dot hs [17] V. Taliwal, H. Mangold, C. Chen, D. Jiang, R. Sengupta. Empirical determination of channel characteristics for dsrc vehicle-to-vehicle communication VI. CONCLUSIONS AND FUTURE WORK More than 44% of all reported vehicle crashes occur at intersections. This shows that current technologies such as traffic lights and stop signs are not so efficient in managing traffic safely and they also increase trip times significantly. In this paper, our goal was to design new V2V-based intersection protocols which significantly increase the throughput of the intersections and avoid collisions. We have also implemented DSRC signal propagation models and studied the effects of channel impairments such as packet loss due to fading on our V2V protocols. Our results indicate that our protocols benefit from properties such as freedom from deadlock and high application reliability even in harsh NLOS
V2V-Intersection Management at Roundabouts
 VV-Intersection Management at Roundabouts Reza Azimi, Gaurav Bhatia and Ragunathan (Raj) Rajkumar Carnegie Mellon University Priyantha Mudalige General Motors ABSTRACT More than % of all automotive crashes
VV-Intersection Management at Roundabouts Reza Azimi, Gaurav Bhatia and Ragunathan (Raj) Rajkumar Carnegie Mellon University Priyantha Mudalige General Motors ABSTRACT More than % of all automotive crashes
Co-operative Driving at Intersections using Vehicular Networks and Vehicle-Resident Sensing
 Carnegie Mellon University Research Showcase @ CMU Dissertations Theses and Dissertations Summer 7-7-2015 Co-operative Driving at Intersections using Vehicular Networks and Vehicle-Resident Sensing Reza
Carnegie Mellon University Research Showcase @ CMU Dissertations Theses and Dissertations Summer 7-7-2015 Co-operative Driving at Intersections using Vehicular Networks and Vehicle-Resident Sensing Reza
Connected Car Networking
 Connected Car Networking Teng Yang, Francis Wolff and Christos Papachristou Electrical Engineering and Computer Science Case Western Reserve University Cleveland, Ohio Outline Motivation Connected Car
Connected Car Networking Teng Yang, Francis Wolff and Christos Papachristou Electrical Engineering and Computer Science Case Western Reserve University Cleveland, Ohio Outline Motivation Connected Car
Deployment and Testing of Optimized Autonomous and Connected Vehicle Trajectories at a Closed- Course Signalized Intersection
 Deployment and Testing of Optimized Autonomous and Connected Vehicle Trajectories at a Closed- Course Signalized Intersection Clark Letter*, Lily Elefteriadou, Mahmoud Pourmehrab, Aschkan Omidvar Civil
Deployment and Testing of Optimized Autonomous and Connected Vehicle Trajectories at a Closed- Course Signalized Intersection Clark Letter*, Lily Elefteriadou, Mahmoud Pourmehrab, Aschkan Omidvar Civil
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks. Nathan Balon and Jinhua Guo University of Michigan - Dearborn
 Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Communication Networks. Braunschweiger Verkehrskolloquium
 Simulation of Car-to-X Communication Networks Braunschweiger Verkehrskolloquium DLR, 03.02.2011 02 2011 Henrik Schumacher, IKT Introduction VANET = Vehicular Ad hoc NETwork Originally used to emphasize
Simulation of Car-to-X Communication Networks Braunschweiger Verkehrskolloquium DLR, 03.02.2011 02 2011 Henrik Schumacher, IKT Introduction VANET = Vehicular Ad hoc NETwork Originally used to emphasize
Research Article A Joint Vehicle-Vehicle/Vehicle-Roadside Communication Protocol for Highway Traffic Safety
 Vehicular Technology Volume 211, Article ID 71848, 1 pages doi:1.1155/211/71848 Research Article A Joint Vehicle-Vehicle/Vehicle-Roadside Communication Protocol for Highway Traffic Safety Bin Hu and Hamid
Vehicular Technology Volume 211, Article ID 71848, 1 pages doi:1.1155/211/71848 Research Article A Joint Vehicle-Vehicle/Vehicle-Roadside Communication Protocol for Highway Traffic Safety Bin Hu and Hamid
Using Vision-Based Driver Assistance to Augment Vehicular Ad-Hoc Network Communication
 Using Vision-Based Driver Assistance to Augment Vehicular Ad-Hoc Network Communication Kyle Charbonneau, Michael Bauer and Steven Beauchemin Department of Computer Science University of Western Ontario
Using Vision-Based Driver Assistance to Augment Vehicular Ad-Hoc Network Communication Kyle Charbonneau, Michael Bauer and Steven Beauchemin Department of Computer Science University of Western Ontario
Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles
 Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles Bin Cheng, Ali Rostami, Marco Gruteser John B. Kenney Gaurav Bansal and Katrin Sjoberg Winlab, Rutgers University,
Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles Bin Cheng, Ali Rostami, Marco Gruteser John B. Kenney Gaurav Bansal and Katrin Sjoberg Winlab, Rutgers University,
Contextual Pedestrian-to-Vehicle DSRC Communication
 Contextual Pedestrian-to-Vehicle DSRC Communication Ali Rostami, Bin Cheng, Hongsheng Lu, John B. Kenney, and Marco Gruteser WINLAB, Rutgers University, USA Toyota InfoTechnology Center, USA December 2016
Contextual Pedestrian-to-Vehicle DSRC Communication Ali Rostami, Bin Cheng, Hongsheng Lu, John B. Kenney, and Marco Gruteser WINLAB, Rutgers University, USA Toyota InfoTechnology Center, USA December 2016
MIMO-Based Vehicle Positioning System for Vehicular Networks
 MIMO-Based Vehicle Positioning System for Vehicular Networks Abduladhim Ashtaiwi* Computer Networks Department College of Information and Technology University of Tripoli Libya. * Corresponding author.
MIMO-Based Vehicle Positioning System for Vehicular Networks Abduladhim Ashtaiwi* Computer Networks Department College of Information and Technology University of Tripoli Libya. * Corresponding author.
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS
 TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR P INCLUDING PROPAGATION MODELS
 PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR 802.11P INCLUDING PROPAGATION MODELS Mit Parmar 1, Kinnar Vaghela 2 1 Student M.E. Communication Systems, Electronics & Communication Department, L.D. College
PERFORMANCE ANALYSIS OF ROUTING PROTOCOLS FOR 802.11P INCLUDING PROPAGATION MODELS Mit Parmar 1, Kinnar Vaghela 2 1 Student M.E. Communication Systems, Electronics & Communication Department, L.D. College
CONNECTED VEHICLE-TO-INFRASTRUCTURE INITATIVES
 CONNECTED VEHICLE-TO-INFRASTRUCTURE INITATIVES Arizona ITE March 3, 2016 Faisal Saleem ITS Branch Manager & MCDOT SMARTDrive Program Manager Maricopa County Department of Transportation ONE SYSTEM MULTIPLE
CONNECTED VEHICLE-TO-INFRASTRUCTURE INITATIVES Arizona ITE March 3, 2016 Faisal Saleem ITS Branch Manager & MCDOT SMARTDrive Program Manager Maricopa County Department of Transportation ONE SYSTEM MULTIPLE
Qosmotec. Software Solutions GmbH. Technical Overview. QPER C2X - Car-to-X Signal Strength Emulator and HiL Test Bench. Page 1
 Qosmotec Software Solutions GmbH Technical Overview QPER C2X - Page 1 TABLE OF CONTENTS 0 DOCUMENT CONTROL...3 0.1 Imprint...3 0.2 Document Description...3 1 SYSTEM DESCRIPTION...4 1.1 General Concept...4
Qosmotec Software Solutions GmbH Technical Overview QPER C2X - Page 1 TABLE OF CONTENTS 0 DOCUMENT CONTROL...3 0.1 Imprint...3 0.2 Document Description...3 1 SYSTEM DESCRIPTION...4 1.1 General Concept...4
Chapter- 5. Performance Evaluation of Conventional Handoff
 Chapter- 5 Performance Evaluation of Conventional Handoff Chapter Overview This chapter immensely compares the different mobile phone technologies (GSM, UMTS and CDMA). It also presents the related results
Chapter- 5 Performance Evaluation of Conventional Handoff Chapter Overview This chapter immensely compares the different mobile phone technologies (GSM, UMTS and CDMA). It also presents the related results
Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles
 Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles Bin Cheng Joint work with Ali Rostami, Marco Gruteser WINLAB, Rutgers University, USA Gaurav Bansal, John B. Kenney
Performance Evaluation of a Mixed Vehicular Network with CAM-DCC and LIMERIC Vehicles Bin Cheng Joint work with Ali Rostami, Marco Gruteser WINLAB, Rutgers University, USA Gaurav Bansal, John B. Kenney
BASIC CONCEPTS OF HSPA
 284 23-3087 Uen Rev A BASIC CONCEPTS OF HSPA February 2007 White Paper HSPA is a vital part of WCDMA evolution and provides improved end-user experience as well as cost-efficient mobile/wireless broadband.
284 23-3087 Uen Rev A BASIC CONCEPTS OF HSPA February 2007 White Paper HSPA is a vital part of WCDMA evolution and provides improved end-user experience as well as cost-efficient mobile/wireless broadband.
Design of 5.9GHz DSRC-based Vehicular Safety Communication
 Design of 5.9GHz DSRC-based Vehicular Safety Communication Daniel Jiang 1, Vikas Taliwal 1, Andreas Meier 1, Wieland Holfelder 1, Ralf Herrtwich 2 1 DaimlerChrysler Research and Technology North America,
Design of 5.9GHz DSRC-based Vehicular Safety Communication Daniel Jiang 1, Vikas Taliwal 1, Andreas Meier 1, Wieland Holfelder 1, Ralf Herrtwich 2 1 DaimlerChrysler Research and Technology North America,
RECOMMENDATION ITU-R BS
 Rec. ITU-R BS.1350-1 1 RECOMMENDATION ITU-R BS.1350-1 SYSTEMS REQUIREMENTS FOR MULTIPLEXING (FM) SOUND BROADCASTING WITH A SUB-CARRIER DATA CHANNEL HAVING A RELATIVELY LARGE TRANSMISSION CAPACITY FOR STATIONARY
Rec. ITU-R BS.1350-1 1 RECOMMENDATION ITU-R BS.1350-1 SYSTEMS REQUIREMENTS FOR MULTIPLEXING (FM) SOUND BROADCASTING WITH A SUB-CARRIER DATA CHANNEL HAVING A RELATIVELY LARGE TRANSMISSION CAPACITY FOR STATIONARY
Adaptive Transmission Scheme for Vehicle Communication System
 Sangmi Moon, Sara Bae, Myeonghun Chu, Jihye Lee, Soonho Kwon and Intae Hwang Dept. of Electronics and Computer Engineering, Chonnam National University, 300 Yongbongdong Bukgu Gwangju, 500-757, Republic
Sangmi Moon, Sara Bae, Myeonghun Chu, Jihye Lee, Soonho Kwon and Intae Hwang Dept. of Electronics and Computer Engineering, Chonnam National University, 300 Yongbongdong Bukgu Gwangju, 500-757, Republic
INTRODUCTION TO WIRELESS SENSOR NETWORKS. CHAPTER 3: RADIO COMMUNICATIONS Anna Förster
 INTRODUCTION TO WIRELESS SENSOR NETWORKS CHAPTER 3: RADIO COMMUNICATIONS Anna Förster OVERVIEW 1. Radio Waves and Modulation/Demodulation 2. Properties of Wireless Communications 1. Interference and noise
INTRODUCTION TO WIRELESS SENSOR NETWORKS CHAPTER 3: RADIO COMMUNICATIONS Anna Förster OVERVIEW 1. Radio Waves and Modulation/Demodulation 2. Properties of Wireless Communications 1. Interference and noise
Mathematical Problems in Networked Embedded Systems
 Mathematical Problems in Networked Embedded Systems Miklós Maróti Institute for Software Integrated Systems Vanderbilt University Outline Acoustic ranging TDMA in globally asynchronous locally synchronous
Mathematical Problems in Networked Embedded Systems Miklós Maróti Institute for Software Integrated Systems Vanderbilt University Outline Acoustic ranging TDMA in globally asynchronous locally synchronous
ECE 476/ECE 501C/CS Wireless Communication Systems Winter Lecture 6: Fading
 ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2003 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2003 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
Traffic Control for a Swarm of Robots: Avoiding Group Conflicts
 Traffic Control for a Swarm of Robots: Avoiding Group Conflicts Leandro Soriano Marcolino and Luiz Chaimowicz Abstract A very common problem in the navigation of robotic swarms is when groups of robots
Traffic Control for a Swarm of Robots: Avoiding Group Conflicts Leandro Soriano Marcolino and Luiz Chaimowicz Abstract A very common problem in the navigation of robotic swarms is when groups of robots
V2X-Locate Positioning System Whitepaper
 V2X-Locate Positioning System Whitepaper November 8, 2017 www.cohdawireless.com 1 Introduction The most important piece of information any autonomous system must know is its position in the world. This
V2X-Locate Positioning System Whitepaper November 8, 2017 www.cohdawireless.com 1 Introduction The most important piece of information any autonomous system must know is its position in the world. This
Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes
 7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
Raising Awareness of Emergency Vehicles in Traffic Using Connected Vehicle Technologies
 Raising Awareness of Emergency Vehicles in Traffic Using Connected Vehicle Technologies Larry Head University of Arizona September 23, 2017 1 Connected Vehicles DSRC 5.9 GHz Wireless Basic Safety Message
Raising Awareness of Emergency Vehicles in Traffic Using Connected Vehicle Technologies Larry Head University of Arizona September 23, 2017 1 Connected Vehicles DSRC 5.9 GHz Wireless Basic Safety Message
Use of Probe Vehicles to Increase Traffic Estimation Accuracy in Brisbane
 Use of Probe Vehicles to Increase Traffic Estimation Accuracy in Brisbane Lee, J. & Rakotonirainy, A. Centre for Accident Research and Road Safety - Queensland (CARRS-Q), Queensland University of Technology
Use of Probe Vehicles to Increase Traffic Estimation Accuracy in Brisbane Lee, J. & Rakotonirainy, A. Centre for Accident Research and Road Safety - Queensland (CARRS-Q), Queensland University of Technology
ECE 476/ECE 501C/CS Wireless Communication Systems Winter Lecture 6: Fading
 ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2004 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2004 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
Traffic Control for a Swarm of Robots: Avoiding Target Congestion
 Traffic Control for a Swarm of Robots: Avoiding Target Congestion Leandro Soriano Marcolino and Luiz Chaimowicz Abstract One of the main problems in the navigation of robotic swarms is when several robots
Traffic Control for a Swarm of Robots: Avoiding Target Congestion Leandro Soriano Marcolino and Luiz Chaimowicz Abstract One of the main problems in the navigation of robotic swarms is when several robots
Application Note 37. Emulating RF Channel Characteristics
 Application Note 37 Emulating RF Channel Characteristics Wireless communication is one of the most demanding applications for the telecommunications equipment designer. Typical signals at the receiver
Application Note 37 Emulating RF Channel Characteristics Wireless communication is one of the most demanding applications for the telecommunications equipment designer. Typical signals at the receiver
Project = An Adventure : Wireless Networks. Lecture 4: More Physical Layer. What is an Antenna? Outline. Page 1
 Project = An Adventure 18-759: Wireless Networks Checkpoint 2 Checkpoint 1 Lecture 4: More Physical Layer You are here Done! Peter Steenkiste Departments of Computer Science and Electrical and Computer
Project = An Adventure 18-759: Wireless Networks Checkpoint 2 Checkpoint 1 Lecture 4: More Physical Layer You are here Done! Peter Steenkiste Departments of Computer Science and Electrical and Computer
Cognitive Wireless Network : Computer Networking. Overview. Cognitive Wireless Networks
 Cognitive Wireless Network 15-744: Computer Networking L-19 Cognitive Wireless Networks Optimize wireless networks based context information Assigned reading White spaces Online Estimation of Interference
Cognitive Wireless Network 15-744: Computer Networking L-19 Cognitive Wireless Networks Optimize wireless networks based context information Assigned reading White spaces Online Estimation of Interference
Localization (Position Estimation) Problem in WSN
 Localization (Position Estimation) Problem in WSN [1] Convex Position Estimation in Wireless Sensor Networks by L. Doherty, K.S.J. Pister, and L.E. Ghaoui [2] Semidefinite Programming for Ad Hoc Wireless
Localization (Position Estimation) Problem in WSN [1] Convex Position Estimation in Wireless Sensor Networks by L. Doherty, K.S.J. Pister, and L.E. Ghaoui [2] Semidefinite Programming for Ad Hoc Wireless
RECOMMENDATION ITU-R M.1310* TRANSPORT INFORMATION AND CONTROL SYSTEMS (TICS) OBJECTIVES AND REQUIREMENTS (Question ITU-R 205/8)
 Rec. ITU-R M.1310 1 RECOMMENDATION ITU-R M.1310* TRANSPORT INFORMATION AND CONTROL SYSTEMS (TICS) OBJECTIVES AND REQUIREMENTS (Question ITU-R 205/8) Rec. ITU-R M.1310 (1997) Summary This Recommendation
Rec. ITU-R M.1310 1 RECOMMENDATION ITU-R M.1310* TRANSPORT INFORMATION AND CONTROL SYSTEMS (TICS) OBJECTIVES AND REQUIREMENTS (Question ITU-R 205/8) Rec. ITU-R M.1310 (1997) Summary This Recommendation
Safety Message Power Transmission Control for Vehicular Ad hoc Networks
 Journal of Computer Science 6 (10): 1056-1061, 2010 ISSN 1549-3636 2010 Science Publications Safety Message Power Transmission Control for Vehicular Ad hoc Networks 1 Ghassan Samara, 1 Sureswaran Ramadas
Journal of Computer Science 6 (10): 1056-1061, 2010 ISSN 1549-3636 2010 Science Publications Safety Message Power Transmission Control for Vehicular Ad hoc Networks 1 Ghassan Samara, 1 Sureswaran Ramadas
Real Time Traffic Light Control System Using Image Processing
 Real Time Traffic Light Control System Using Image Processing Darshan J #1, Siddhesh L. #2, Hitesh B. #3, Pratik S.#4 Department of Electronics and Telecommunications Student of KC College Of Engineering
Real Time Traffic Light Control System Using Image Processing Darshan J #1, Siddhesh L. #2, Hitesh B. #3, Pratik S.#4 Department of Electronics and Telecommunications Student of KC College Of Engineering
GPS-Based Navigation & Positioning Challenges in Communications- Enabled Driver Assistance Systems
 GPS-Based Navigation & Positioning Challenges in Communications- Enabled Driver Assistance Systems Chaminda Basnayake, Ph.D. Senior Research Engineer General Motors Research & Development and Planning
GPS-Based Navigation & Positioning Challenges in Communications- Enabled Driver Assistance Systems Chaminda Basnayake, Ph.D. Senior Research Engineer General Motors Research & Development and Planning
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Josh Broch, David Maltz, David Johnson, Yih-Chun Hu and Jorjeta Jetcheva Computer Science Department Carnegie Mellon University
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Josh Broch, David Maltz, David Johnson, Yih-Chun Hu and Jorjeta Jetcheva Computer Science Department Carnegie Mellon University
WIRELESS COMMUNICATION TECHNOLOGIES (16:332:546) LECTURE 5 SMALL SCALE FADING
 WIRELESS COMMUNICATION TECHNOLOGIES (16:332:546) LECTURE 5 SMALL SCALE FADING Instructor: Dr. Narayan Mandayam Slides: SabarishVivek Sarathy A QUICK RECAP Why is there poor signal reception in urban clutters?
WIRELESS COMMUNICATION TECHNOLOGIES (16:332:546) LECTURE 5 SMALL SCALE FADING Instructor: Dr. Narayan Mandayam Slides: SabarishVivek Sarathy A QUICK RECAP Why is there poor signal reception in urban clutters?
ECE 476/ECE 501C/CS Wireless Communication Systems Winter Lecture 6: Fading
 ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2005 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
ECE 476/ECE 501C/CS 513 - Wireless Communication Systems Winter 2005 Lecture 6: Fading Last lecture: Large scale propagation properties of wireless systems - slowly varying properties that depend primarily
Distributed Transmit Power Control for Beacons in VANET
 Forough Goudarzi and Hamed S. Al-Raweshidy Department of Electrical Engineering, Brunel University, London, U.K. Keywords: Abstract: Beacon Power Control, Congestion Control, Game Theory, VANET. In vehicle
Forough Goudarzi and Hamed S. Al-Raweshidy Department of Electrical Engineering, Brunel University, London, U.K. Keywords: Abstract: Beacon Power Control, Congestion Control, Game Theory, VANET. In vehicle
DEVELOPMENT OF A MICROSCOPIC TRAFFIC SIMULATION MODEL FOR INTERACTIVE TRAFFIC ENVIRONMENT
 DEVELOPMENT OF A MICROSCOPIC TRAFFIC SIMULATION MODEL FOR INTERACTIVE TRAFFIC ENVIRONMENT Tomoyoshi SHIRAISHI, Hisatomo HANABUSA, Masao KUWAHARA, Edward CHUNG, Shinji TANAKA, Hideki UENO, Yoshikazu OHBA,
DEVELOPMENT OF A MICROSCOPIC TRAFFIC SIMULATION MODEL FOR INTERACTIVE TRAFFIC ENVIRONMENT Tomoyoshi SHIRAISHI, Hisatomo HANABUSA, Masao KUWAHARA, Edward CHUNG, Shinji TANAKA, Hideki UENO, Yoshikazu OHBA,
APS Implementation over Vehicular Ad Hoc Networks
 APS Implementation over Vehicular Ad Hoc Networks Soumen Kanrar Vehere Interactive Pvt Ltd Calcutta India Abstract: The real world scenario has changed from the wired connection to wireless connection.
APS Implementation over Vehicular Ad Hoc Networks Soumen Kanrar Vehere Interactive Pvt Ltd Calcutta India Abstract: The real world scenario has changed from the wired connection to wireless connection.
Roadside Range Sensors for Intersection Decision Support
 Roadside Range Sensors for Intersection Decision Support Arvind Menon, Alec Gorjestani, Craig Shankwitz and Max Donath, Member, IEEE Abstract The Intelligent Transportation Institute at the University
Roadside Range Sensors for Intersection Decision Support Arvind Menon, Alec Gorjestani, Craig Shankwitz and Max Donath, Member, IEEE Abstract The Intelligent Transportation Institute at the University
AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS)
 AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS) 1.3 NA-14-0267-0019-1.3 Document Information Document Title: Document Version: 1.3 Current Date: 2016-05-18 Print Date: 2016-05-18 Document
AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS) 1.3 NA-14-0267-0019-1.3 Document Information Document Title: Document Version: 1.3 Current Date: 2016-05-18 Print Date: 2016-05-18 Document
A novel, broadcasting-based algorithm for vehicle speed estimation in Intelligent Transportation Systems using ad-hoc networks
 A novel, broadcasting-based algorithm for vehicle speed estimation in Intelligent Transportation Systems using ad-hoc networks Boyan Petrov 1, Dr Evtim Peytchev 2 1 Faculty of Computer Systems and Control,
A novel, broadcasting-based algorithm for vehicle speed estimation in Intelligent Transportation Systems using ad-hoc networks Boyan Petrov 1, Dr Evtim Peytchev 2 1 Faculty of Computer Systems and Control,
Fast and efficient randomized flooding on lattice sensor networks
 Fast and efficient randomized flooding on lattice sensor networks Ananth Kini, Vilas Veeraraghavan, Steven Weber Department of Electrical and Computer Engineering Drexel University November 19, 2004 presentation
Fast and efficient randomized flooding on lattice sensor networks Ananth Kini, Vilas Veeraraghavan, Steven Weber Department of Electrical and Computer Engineering Drexel University November 19, 2004 presentation
Utilization-Aware Adaptive Back-Pressure Traffic Signal Control
 Utilization-Aware Adaptive Back-Pressure Traffic Signal Control Wanli Chang, Samarjit Chakraborty and Anuradha Annaswamy Abstract Back-pressure control of traffic signal, which computes the control phase
Utilization-Aware Adaptive Back-Pressure Traffic Signal Control Wanli Chang, Samarjit Chakraborty and Anuradha Annaswamy Abstract Back-pressure control of traffic signal, which computes the control phase
Vehicle speed and volume measurement using V2I communication
 Vehicle speed and volume measurement using VI communication Quoc Chuyen DOAN IRSEEM-ESIGELEC ITS division Saint Etienne du Rouvray 76801 - FRANCE doan@esigelec.fr Tahar BERRADIA IRSEEM-ESIGELEC ITS division
Vehicle speed and volume measurement using VI communication Quoc Chuyen DOAN IRSEEM-ESIGELEC ITS division Saint Etienne du Rouvray 76801 - FRANCE doan@esigelec.fr Tahar BERRADIA IRSEEM-ESIGELEC ITS division
Analysis of Fast Fading in Wireless Communication Channels M.Siva Ganga Prasad 1, P.Siddaiah 1, L.Pratap Reddy 2, K.Lekha 1
 International Journal of ISSN 0974-2107 Systems and Technologies IJST Vol.3, No.1, pp 139-145 KLEF 2010 Fading in Wireless Communication Channels M.Siva Ganga Prasad 1, P.Siddaiah 1, L.Pratap Reddy 2,
International Journal of ISSN 0974-2107 Systems and Technologies IJST Vol.3, No.1, pp 139-145 KLEF 2010 Fading in Wireless Communication Channels M.Siva Ganga Prasad 1, P.Siddaiah 1, L.Pratap Reddy 2,
Evolution of Vehicular Congestion Control Without Degrading Legacy Vehicle Performance
 Evolution of Vehicular Congestion Control Without Degrading Legacy Vehicle Performance Bin Cheng, Ali Rostami, Marco Gruteser Hongsheng Lu John B. Kenney and Gaurav Bansal Winlab, Rutgers University, USA
Evolution of Vehicular Congestion Control Without Degrading Legacy Vehicle Performance Bin Cheng, Ali Rostami, Marco Gruteser Hongsheng Lu John B. Kenney and Gaurav Bansal Winlab, Rutgers University, USA
Antennas & Propagation. CSG 250 Fall 2007 Rajmohan Rajaraman
 Antennas & Propagation CSG 250 Fall 2007 Rajmohan Rajaraman Introduction An antenna is an electrical conductor or system of conductors o Transmission - radiates electromagnetic energy into space o Reception
Antennas & Propagation CSG 250 Fall 2007 Rajmohan Rajaraman Introduction An antenna is an electrical conductor or system of conductors o Transmission - radiates electromagnetic energy into space o Reception
Advanced Vehicle Control Systems (AVCS) Supporting Intelligent Transportation Systems
 Ministry of Transportation Provincial Highways Management Division Report Highway Infrastructure Innovation Funding Program Advanced Vehicle Control Systems (AVCS) Supporting Intelligent Transportation
Ministry of Transportation Provincial Highways Management Division Report Highway Infrastructure Innovation Funding Program Advanced Vehicle Control Systems (AVCS) Supporting Intelligent Transportation
AI Approaches to Ultimate Tic-Tac-Toe
 AI Approaches to Ultimate Tic-Tac-Toe Eytan Lifshitz CS Department Hebrew University of Jerusalem, Israel David Tsurel CS Department Hebrew University of Jerusalem, Israel I. INTRODUCTION This report is
AI Approaches to Ultimate Tic-Tac-Toe Eytan Lifshitz CS Department Hebrew University of Jerusalem, Israel David Tsurel CS Department Hebrew University of Jerusalem, Israel I. INTRODUCTION This report is
Comparing the ns 3 Propagation Models
 Comparing the ns 3 Propagation Models Mirko Stoffers School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta, Georgia, USA Email: stoffers@gatech.edu George Riley School of
Comparing the ns 3 Propagation Models Mirko Stoffers School of Electrical and Computer Engineering Georgia Institute of Technology Atlanta, Georgia, USA Email: stoffers@gatech.edu George Riley School of
INTERSECTION DECISION SUPPORT SYSTEM USING GAME THEORY ALGORITHM
 Connected Vehicle Technology Challenge INTERSECTION DECISION SUPPORT SYSTEM USING GAME THEORY ALGORITHM Dedicated Short Range Communications (DSRC) Game Theory Ismail Zohdy 2011 INTRODUCTION Many of the
Connected Vehicle Technology Challenge INTERSECTION DECISION SUPPORT SYSTEM USING GAME THEORY ALGORITHM Dedicated Short Range Communications (DSRC) Game Theory Ismail Zohdy 2011 INTRODUCTION Many of the
5.9 GHz V2X Modem Performance Challenges with Vehicle Integration
 5.9 GHz V2X Modem Performance Challenges with Vehicle Integration October 15th, 2014 Background V2V DSRC Why do the research? Based on 802.11p MAC PHY ad-hoc network topology at 5.9 GHz. Effective Isotropic
5.9 GHz V2X Modem Performance Challenges with Vehicle Integration October 15th, 2014 Background V2V DSRC Why do the research? Based on 802.11p MAC PHY ad-hoc network topology at 5.9 GHz. Effective Isotropic
DOPPLER SHIFT. Thus, the frequency of the received signal is
 DOPPLER SHIFT Radio Propagation Doppler Effect: When a wave source and a receiver are moving towards each other, the frequency of the received signal will not be the same as the source. When they are moving
DOPPLER SHIFT Radio Propagation Doppler Effect: When a wave source and a receiver are moving towards each other, the frequency of the received signal will not be the same as the source. When they are moving
arxiv: v1 [cs.ni] 10 Jan 2017
![arxiv: v1 [cs.ni] 10 Jan 2017 arxiv: v1 [cs.ni] 10 Jan 2017](/thumbs/89/100390602.jpg) 1 Distributed Algorithm for Collision Avoidance at Road Intersections in the Presence of Communication Failures Vladimir Savic, Elad M. Schiller, and Marina Papatriantafilou Dept. of Computer Science and
1 Distributed Algorithm for Collision Avoidance at Road Intersections in the Presence of Communication Failures Vladimir Savic, Elad M. Schiller, and Marina Papatriantafilou Dept. of Computer Science and
Wireless Transmission & Media Access
 Wireless Transmission & Media Access Signals and Signal Propagation Multiplexing Modulation Media Access 1 Significant parts of slides are based on original material by Prof. Dr.-Ing. Jochen Schiller,
Wireless Transmission & Media Access Signals and Signal Propagation Multiplexing Modulation Media Access 1 Significant parts of slides are based on original material by Prof. Dr.-Ing. Jochen Schiller,
Comments of Shared Spectrum Company
 Before the DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Washington, D.C. 20230 In the Matter of ) ) Developing a Sustainable Spectrum ) Docket No. 181130999 8999 01
Before the DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Washington, D.C. 20230 In the Matter of ) ) Developing a Sustainable Spectrum ) Docket No. 181130999 8999 01
Overview. Cognitive Radio: Definitions. Cognitive Radio. Multidimensional Spectrum Awareness: Radio Space
 Overview A Survey of Spectrum Sensing Algorithms for Cognitive Radio Applications Tevfik Yucek and Huseyin Arslan Cognitive Radio Multidimensional Spectrum Awareness Challenges Spectrum Sensing Methods
Overview A Survey of Spectrum Sensing Algorithms for Cognitive Radio Applications Tevfik Yucek and Huseyin Arslan Cognitive Radio Multidimensional Spectrum Awareness Challenges Spectrum Sensing Methods
From. Power Control for Reliable M2M Communication. Ling Wang Wayne State University. Hongwei Zhang Wayne State University CONTENTS
 CHAPTER1 Power Control for Reliable M2M Communication Ling Wang Wayne State University Hongwei Zhang Wayne State University CONTENTS 1.1 Introduction... 4 1.1.1 History of power control in cellular networks...
CHAPTER1 Power Control for Reliable M2M Communication Ling Wang Wayne State University Hongwei Zhang Wayne State University CONTENTS 1.1 Introduction... 4 1.1.1 History of power control in cellular networks...
Multiple Receiver Strategies for Minimizing Packet Loss in Dense Sensor Networks
 Multiple Receiver Strategies for Minimizing Packet Loss in Dense Sensor Networks Bernhard Firner Chenren Xu Yanyong Zhang Richard Howard Rutgers University, Winlab May 10, 2011 Bernhard Firner (Winlab)
Multiple Receiver Strategies for Minimizing Packet Loss in Dense Sensor Networks Bernhard Firner Chenren Xu Yanyong Zhang Richard Howard Rutgers University, Winlab May 10, 2011 Bernhard Firner (Winlab)
Bluetooth Low Energy Sensing Technology for Proximity Construction Applications
 Bluetooth Low Energy Sensing Technology for Proximity Construction Applications JeeWoong Park School of Civil and Environmental Engineering, Georgia Institute of Technology, 790 Atlantic Dr. N.W., Atlanta,
Bluetooth Low Energy Sensing Technology for Proximity Construction Applications JeeWoong Park School of Civil and Environmental Engineering, Georgia Institute of Technology, 790 Atlantic Dr. N.W., Atlanta,
The impact of different radio propagation models for Mobile Ad-hoc NETworks (MANET) in urban area environment
 ISSN 1 746-7233, England, UK World Journal of Modelling and Simulation Vol. 5 (2009) No. 1, pp. 45-52 The impact of different radio propagation models for Mobile Ad-hoc NETworks (MANET) in urban area environment
ISSN 1 746-7233, England, UK World Journal of Modelling and Simulation Vol. 5 (2009) No. 1, pp. 45-52 The impact of different radio propagation models for Mobile Ad-hoc NETworks (MANET) in urban area environment
EENG473 Mobile Communications Module 3 : Week # (12) Mobile Radio Propagation: Small-Scale Path Loss
 EENG473 Mobile Communications Module 3 : Week # (12) Mobile Radio Propagation: Small-Scale Path Loss Introduction Small-scale fading is used to describe the rapid fluctuation of the amplitude of a radio
EENG473 Mobile Communications Module 3 : Week # (12) Mobile Radio Propagation: Small-Scale Path Loss Introduction Small-scale fading is used to describe the rapid fluctuation of the amplitude of a radio
An Architecture for Intelligent Automotive Collision Avoidance Systems
 IVSS-2003-UMS-07 An Architecture for Intelligent Automotive Collision Avoidance Systems Syed Masud Mahmud and Shobhit Shanker Department of Electrical and Computer Engineering, Wayne State University,
IVSS-2003-UMS-07 An Architecture for Intelligent Automotive Collision Avoidance Systems Syed Masud Mahmud and Shobhit Shanker Department of Electrical and Computer Engineering, Wayne State University,
V2V Safety Communication Scalability Based on the SAE J2945/1 Standard
 V2V Safety Communication Scalability Based on the SAE J2945/1 Standard Ali Rostami WINLAB, Rutgers University, North Brunswick, New Jersey, USA Hariharan Krishnan General Motors, Warren, Michigan, USA
V2V Safety Communication Scalability Based on the SAE J2945/1 Standard Ali Rostami WINLAB, Rutgers University, North Brunswick, New Jersey, USA Hariharan Krishnan General Motors, Warren, Michigan, USA
Dynamic Zonal Broadcasting for Effective Data Dissemination in VANET
 Dynamic Zonal Broadcasting for Effective Data Dissemination in VANET Masters Project Final Report Author: Madhukesh Wali Email: mwali@cs.odu.edu Project Advisor: Dr. Michele Weigle Email: mweigle@cs.odu.edu
Dynamic Zonal Broadcasting for Effective Data Dissemination in VANET Masters Project Final Report Author: Madhukesh Wali Email: mwali@cs.odu.edu Project Advisor: Dr. Michele Weigle Email: mweigle@cs.odu.edu
Frank Heymann 1.
 Plausibility analysis of navigation related AIS parameter based on time series Frank Heymann 1 1 Deutsches Zentrum für Luft und Raumfahrt ev, Neustrelitz, Germany email: frank.heymann@dlr.de In this paper
Plausibility analysis of navigation related AIS parameter based on time series Frank Heymann 1 1 Deutsches Zentrum für Luft und Raumfahrt ev, Neustrelitz, Germany email: frank.heymann@dlr.de In this paper
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks
 Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
Avoid Impact of Jamming Using Multipath Routing Based on Wireless Mesh Networks M. KIRAN KUMAR 1, M. KANCHANA 2, I. SAPTHAMI 3, B. KRISHNA MURTHY 4 1, 2, M. Tech Student, 3 Asst. Prof 1, 4, Siddharth Institute
Positioning Challenges in Cooperative Vehicular Safety Systems
 Positioning Challenges in Cooperative Vehicular Safety Systems Dr. Luca Delgrossi Mercedes-Benz Research & Development North America, Inc. October 15, 2009 Positioning for Automotive Navigation Personal
Positioning Challenges in Cooperative Vehicular Safety Systems Dr. Luca Delgrossi Mercedes-Benz Research & Development North America, Inc. October 15, 2009 Positioning for Automotive Navigation Personal
Throughput-optimal number of relays in delaybounded multi-hop ALOHA networks
 Page 1 of 10 Throughput-optimal number of relays in delaybounded multi-hop ALOHA networks. Nekoui and H. Pishro-Nik This letter addresses the throughput of an ALOHA-based Poisson-distributed multihop wireless
Page 1 of 10 Throughput-optimal number of relays in delaybounded multi-hop ALOHA networks. Nekoui and H. Pishro-Nik This letter addresses the throughput of an ALOHA-based Poisson-distributed multihop wireless
TRB Workshop on the Future of Road Vehicle Automation
 TRB Workshop on the Future of Road Vehicle Automation Steven E. Shladover University of California PATH Program ITFVHA Meeting, Vienna October 21, 2012 1 Outline TRB background Workshop organization Automation
TRB Workshop on the Future of Road Vehicle Automation Steven E. Shladover University of California PATH Program ITFVHA Meeting, Vienna October 21, 2012 1 Outline TRB background Workshop organization Automation
Safe and Efficient Autonomous Navigation in the Presence of Humans at Control Level
 Safe and Efficient Autonomous Navigation in the Presence of Humans at Control Level Klaus Buchegger 1, George Todoran 1, and Markus Bader 1 Vienna University of Technology, Karlsplatz 13, Vienna 1040,
Safe and Efficient Autonomous Navigation in the Presence of Humans at Control Level Klaus Buchegger 1, George Todoran 1, and Markus Bader 1 Vienna University of Technology, Karlsplatz 13, Vienna 1040,
Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks
 Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks Ying Dai and Jie Wu Department of Computer and Information Sciences Temple University, Philadelphia, PA 19122 Email: {ying.dai,
Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks Ying Dai and Jie Wu Department of Computer and Information Sciences Temple University, Philadelphia, PA 19122 Email: {ying.dai,
OSPF Fundamentals. Agenda. OSPF Principles. L41 - OSPF Fundamentals. Open Shortest Path First Routing Protocol Internet s Second IGP
 OSPF Fundamentals Open Shortest Path First Routing Protocol Internet s Second IGP Agenda OSPF Principles Introduction The Dijkstra Algorithm Communication Procedures LSA Broadcast Handling Splitted Area
OSPF Fundamentals Open Shortest Path First Routing Protocol Internet s Second IGP Agenda OSPF Principles Introduction The Dijkstra Algorithm Communication Procedures LSA Broadcast Handling Splitted Area
OSPF - Open Shortest Path First. OSPF Fundamentals. Agenda. OSPF Topology Database
 OSPF - Open Shortest Path First OSPF Fundamentals Open Shortest Path First Routing Protocol Internet s Second IGP distance vector protocols like RIP have several dramatic disadvantages: slow adaptation
OSPF - Open Shortest Path First OSPF Fundamentals Open Shortest Path First Routing Protocol Internet s Second IGP distance vector protocols like RIP have several dramatic disadvantages: slow adaptation
Ray-Tracing Analysis of an Indoor Passive Localization System
 EUROPEAN COOPERATION IN THE FIELD OF SCIENTIFIC AND TECHNICAL RESEARCH EURO-COST IC1004 TD(12)03066 Barcelona, Spain 8-10 February, 2012 SOURCE: Department of Telecommunications, AGH University of Science
EUROPEAN COOPERATION IN THE FIELD OF SCIENTIFIC AND TECHNICAL RESEARCH EURO-COST IC1004 TD(12)03066 Barcelona, Spain 8-10 February, 2012 SOURCE: Department of Telecommunications, AGH University of Science
Channel. Muhammad Ali Jinnah University, Islamabad Campus, Pakistan. Multi-Path Fading. Dr. Noor M Khan EE, MAJU
 Instructor: Prof. Dr. Noor M. Khan Department of Electronic Engineering, Muhammad Ali Jinnah University, Islamabad Campus, Islamabad, PAKISTAN Ph: +9 (51) 111-878787, Ext. 19 (Office), 186 (Lab) Fax: +9
Instructor: Prof. Dr. Noor M. Khan Department of Electronic Engineering, Muhammad Ali Jinnah University, Islamabad Campus, Islamabad, PAKISTAN Ph: +9 (51) 111-878787, Ext. 19 (Office), 186 (Lab) Fax: +9
Moving Obstacle Avoidance for Mobile Robot Moving on Designated Path
 Moving Obstacle Avoidance for Mobile Robot Moving on Designated Path Taichi Yamada 1, Yeow Li Sa 1 and Akihisa Ohya 1 1 Graduate School of Systems and Information Engineering, University of Tsukuba, 1-1-1,
Moving Obstacle Avoidance for Mobile Robot Moving on Designated Path Taichi Yamada 1, Yeow Li Sa 1 and Akihisa Ohya 1 1 Graduate School of Systems and Information Engineering, University of Tsukuba, 1-1-1,
Robust Positioning for Urban Traffic
 Robust Positioning for Urban Traffic Motivations and Activity plan for the WG 4.1.4 Dr. Laura Ruotsalainen Research Manager, Department of Navigation and positioning Finnish Geospatial Research Institute
Robust Positioning for Urban Traffic Motivations and Activity plan for the WG 4.1.4 Dr. Laura Ruotsalainen Research Manager, Department of Navigation and positioning Finnish Geospatial Research Institute
Wireless Channel Propagation Model Small-scale Fading
 Wireless Channel Propagation Model Small-scale Fading Basic Questions T x What will happen if the transmitter - changes transmit power? - changes frequency? - operates at higher speed? Transmit power,
Wireless Channel Propagation Model Small-scale Fading Basic Questions T x What will happen if the transmitter - changes transmit power? - changes frequency? - operates at higher speed? Transmit power,
SOUND: A Traffic Simulation Model for Oversaturated Traffic Flow on Urban Expressways
 SOUND: A Traffic Simulation Model for Oversaturated Traffic Flow on Urban Expressways Toshio Yoshii 1) and Masao Kuwahara 2) 1: Research Assistant 2: Associate Professor Institute of Industrial Science,
SOUND: A Traffic Simulation Model for Oversaturated Traffic Flow on Urban Expressways Toshio Yoshii 1) and Masao Kuwahara 2) 1: Research Assistant 2: Associate Professor Institute of Industrial Science,
Proceedings Statistical Evaluation of the Positioning Error in Sequential Localization Techniques for Sensor Networks
 Proceedings Statistical Evaluation of the Positioning Error in Sequential Localization Techniques for Sensor Networks Cesar Vargas-Rosales *, Yasuo Maidana, Rafaela Villalpando-Hernandez and Leyre Azpilicueta
Proceedings Statistical Evaluation of the Positioning Error in Sequential Localization Techniques for Sensor Networks Cesar Vargas-Rosales *, Yasuo Maidana, Rafaela Villalpando-Hernandez and Leyre Azpilicueta
Current Technologies in Vehicular Communications
 Current Technologies in Vehicular Communications George Dimitrakopoulos George Bravos Current Technologies in Vehicular Communications George Dimitrakopoulos Department of Informatics and Telematics Harokopio
Current Technologies in Vehicular Communications George Dimitrakopoulos George Bravos Current Technologies in Vehicular Communications George Dimitrakopoulos Department of Informatics and Telematics Harokopio
SAE-DCC evaluation and comparison with popular congestion control algorithms of V2X communication
 Eindhoven University of Technology MASTER SAE-DCC evaluation and comparison with popular congestion control algorithms of V2X communication Wei, Y. Award date: 2017 Link to publication Disclaimer This
Eindhoven University of Technology MASTER SAE-DCC evaluation and comparison with popular congestion control algorithms of V2X communication Wei, Y. Award date: 2017 Link to publication Disclaimer This
Link State Routing. Stefano Vissicchio UCL Computer Science CS 3035/GZ01
 Link State Routing Stefano Vissicchio UCL Computer Science CS 335/GZ Reminder: Intra-domain Routing Problem Shortest paths problem: What path between two vertices offers minimal sum of edge weights? Classic
Link State Routing Stefano Vissicchio UCL Computer Science CS 335/GZ Reminder: Intra-domain Routing Problem Shortest paths problem: What path between two vertices offers minimal sum of edge weights? Classic
Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network
 International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
for Vehicular Ad Hoc Networks
 Distributed Fair Transmit Power Adjustment for Vehicular Ad Hoc Networks Third Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON 06) Reston, VA,
Distributed Fair Transmit Power Adjustment for Vehicular Ad Hoc Networks Third Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON 06) Reston, VA,
Chapter 2 Overview. Duplexing, Multiple Access - 1 -
 Chapter 2 Overview Part 1 (2 weeks ago) Digital Transmission System Frequencies, Spectrum Allocation Radio Propagation and Radio Channels Part 2 (last week) Modulation, Coding, Error Correction Part 3
Chapter 2 Overview Part 1 (2 weeks ago) Digital Transmission System Frequencies, Spectrum Allocation Radio Propagation and Radio Channels Part 2 (last week) Modulation, Coding, Error Correction Part 3
Multi-Path Fading Channel
 Instructor: Prof. Dr. Noor M. Khan Department of Electronic Engineering, Muhammad Ali Jinnah University, Islamabad Campus, Islamabad, PAKISTAN Ph: +9 (51) 111-878787, Ext. 19 (Office), 186 (Lab) Fax: +9
Instructor: Prof. Dr. Noor M. Khan Department of Electronic Engineering, Muhammad Ali Jinnah University, Islamabad Campus, Islamabad, PAKISTAN Ph: +9 (51) 111-878787, Ext. 19 (Office), 186 (Lab) Fax: +9
International Journal of Advance Engineering and Research Development. Performance Comparison of Rayleigh and Rician Fading Channel Models: A Review
 Scientific Journal of Impact Factor (SJIF): 5.71 International Journal of Advance Engineering and Research Development Volume 5, Issue 02, February -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 Performance
Scientific Journal of Impact Factor (SJIF): 5.71 International Journal of Advance Engineering and Research Development Volume 5, Issue 02, February -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 Performance
Minnesota Department of Transportation Rural Intersection Conflict Warning System (RICWS) Reliability Evaluation
 LLLK CENTER FOR TRANSPORTATION STUDIES Minnesota Department of Transportation Rural Intersection Conflict Warning System (RICWS) Reliability Evaluation Final Report Arvind Menon Max Donath Department of
LLLK CENTER FOR TRANSPORTATION STUDIES Minnesota Department of Transportation Rural Intersection Conflict Warning System (RICWS) Reliability Evaluation Final Report Arvind Menon Max Donath Department of
Indoor Localization in Wireless Sensor Networks
 International Journal of Engineering Inventions e-issn: 2278-7461, p-issn: 2319-6491 Volume 4, Issue 03 (August 2014) PP: 39-44 Indoor Localization in Wireless Sensor Networks Farhat M. A. Zargoun 1, Nesreen
International Journal of Engineering Inventions e-issn: 2278-7461, p-issn: 2319-6491 Volume 4, Issue 03 (August 2014) PP: 39-44 Indoor Localization in Wireless Sensor Networks Farhat M. A. Zargoun 1, Nesreen
Simulation of Outdoor Radio Channel
 Simulation of Outdoor Radio Channel Peter Brída, Ján Dúha Department of Telecommunication, University of Žilina Univerzitná 815/1, 010 6 Žilina Email: brida@fel.utc.sk, duha@fel.utc.sk Abstract Wireless
Simulation of Outdoor Radio Channel Peter Brída, Ján Dúha Department of Telecommunication, University of Žilina Univerzitná 815/1, 010 6 Žilina Email: brida@fel.utc.sk, duha@fel.utc.sk Abstract Wireless
Notations. Background
 Modeling Interplanetary Communications after Telecommunication Networks, With Layering and Dynamic Satellite Management Examiner Jeffrey Nickerson, USPTO Abstract: Interplanetary communications can be
Modeling Interplanetary Communications after Telecommunication Networks, With Layering and Dynamic Satellite Management Examiner Jeffrey Nickerson, USPTO Abstract: Interplanetary communications can be
