A SURVEY ON TECHNIQUES REQUIREMENTS FOR INTEGRATING SAFETY AND SECURITY ENGINEERING FOR CYBER-PHYSICAL SYSTEMS
|
|
|
- Ethelbert Parks
- 6 years ago
- Views:
Transcription
1 A SURVEY ON TECHNIQUES REQUIREMENTS FOR INTEGRATING SAFETY AND SECURITY ENGINEERING FOR CYBER-PHYSICAL SYSTEMS MOHAMMED F. H. ABULAMDDI Department of Software Engineering, University of Palestine, Palestine ABSTRACT Nowadays, safety and security have become a requirement, integrated to each other, for information systems as a new generation of infrastructure systems distributed throughout networks. That opened the door for questions on whether these systems are safety-critical especially since they were tested in a closed, separated environment and are now deployed in an uncontrollable environment, namely the internet, where the number of threats is enormous. So it opened the door to talk about new development approach methods that take safety and security into consideration during the system development life cycle and most importantly, identifying hazard, risks and threats. We will conduct a survey exploring technical languages that were created by the scholars to combine safety and security requirement engineering and accident analysis technique languages. KEYWORDS Dependability Requirements, Safety requirements, Security requirement, Cyber-Physical Systems, Accident Analysis Technique. 1. INTRODUCTION The fields of safety and security use different development tools and methods. Consequently, these two separate but related research areas utilise different concepts, tools and methods. The following analogy is commonly used to illustrate the difference between the fields of safety and security: a safety engineer believes that it is important for buildings to have easy accessible exit in case of emergency, whereas a security engineer sees the emergency door as a loophole that can provide access to the building to unauthorized personnel and therefore it must be secured. But, there is also another important distinction between the two: Security is concerned with the risks originating from the environment and potentially impacting the system, whereas safety deals with hazards arising from the system and potentially impacting the environment [1]. It is important, during system development and operations, to identify, analyse, evaluate and finally deal with as many relevant risks as possible. At the same time different techniques are used within the fields, specifically because safety deals with unintentional hazards and security with intentional threats. The safety techniques used to discover threats to a system are not the problem; problems arise when a system is connected to the internet and becomes subject to the rules of another environment that is open, which completely opposite to the closed environment for which the system was designed. Security and safety engineers usually work independently and employ different methods when developing a system: security engineers do not take in consideration safety aspects and safety engineers do not consider security. But, it makes little sense to invest effort in ensuring the dependability of a system while ignoring the possibility of security vulnerabilities. A basic level of security - in the sense that a software system behaves properly even in the presence of hostile inputs from its environment - should be required for any software DOI: /ijcses
2 system that is connected to the network, and used to process sensitive or personal data, or used by an organization for its critical business or operational functions. Safety and security models and tools have been under focus from different perspectives. Some researchers focused on the architectural framework while others focused on narrowing down the gap between the definitions and terminology adaptation in both safety and security or narrowing down techniques requirements and tools used in the system development life cycle. It is important to note that each and every technique built and used in a specific industry has its own threat analysis and mathematical formulas, even if they all under the safety engineering umbrella. Furthermore each of these techniques was built and used according to technical reports unlike how it is done in security engineering, which can lead to issues especially since these techniques are separated from their environments. So, potential risks might arise when these systems are functioning within their environments. 2. RELATED WORK In the studies conducted by Benjamin [2], researchers focused on security in a try to build a conceptual framework that deals with definitions and terminology related to security requirements from the beginning of the system development life cycle especially during the elicitation phase and analysis requirement which is reflected on the conceptual framework that the researches put as a base for comparison and focused on analysing the methods used like: Common Criteria, Secure Tropos, ISSRM, SREP, MSRA, Problem Frames, and the methods that depend on UML to the extent that these methods provide coverage in relation of the system development life cycle when used. Eames and Eames [3] surveyed the nature of integration whether it is consolidated, combined, synthesised, unified, or harmonised. The research addresses each of these states separately and the definition of each one of them when implemented on safety and security. Furthermore, the researches focused on the interaction requirements and proposed enhancing traceability in documentation using a case study on Military Air Traffic Control. System was addressed from both the safety and security perspectives and their respective techniques that separately were undertaken by two separate teams each serving a perspective. The integration between the two, however, took place during the case documentation phase through conflict resolution and integration of requirements. In the studies conducted by Firesmith [4] [5], he focused on developing the definitions for safety and security domains and comparing them to one another and to survivability engineering. He also created a unified definition that includes safety, security, and survivability engineering called defensibility and then created information models using UML class and founded relationships and definitions between safety engineering and security engineering. Allenby and Kelly [6] described the technique for eliciting and analysing functional safety requirement for aircraft engines by using scenario and deriving Use-Case (UC) and hazard analysis by addressing HAZOP and putting guidewords that comply with the UC, and then integrating HAZOP and scenario-base requirement leading to the conclusion that it is possible to limit mitigating risks. Srivatanakul et al. [7] worked on creating HAZOP-Based security analysis on misuse case model through extending guideword notation that is used in the HAZOP and merged its use with Misuse-Case UML notation. Alexander [8] has also addressed the use of Misuse-Case (MUC) and Failure Mode and Effect Analysis (FMEA) by facilitating the use of MUC during the first phase because the analysis that resulted from it, defines the risks and threats that might face the system and the pieces of information resulting from MUC are used as input for FMEA analysis. He also addressed the interplay of UC and MUC with functional and non-functional requirements in details. 2
3 In 2005, Zafar and Dromey applied the behavioral tree formalism and genetic software engineering approaches to deal with safety and security properties in system design [9]. In 2009, Sun et al. used the Maude rewriting logic formalism to automatically spot contradictory requirements between safety and security, for a very basic Use-Cases[10]. Sommerville [11] had created a new notion called Concerns which was the motive behind creating this notion and helped in having improved processing for eliciting and analysing safety requirements. Furthermore, this is also important in avoiding conflicts in requirements since notion concerns are basically requirements and organizational goals cross-checking which were applied on a case study. Tor and Guttorm [12] have prepared for an experimental comparison between Use-Case diagrams and textual Use-Cases in defining safety hazard identification. Their experiment concludes that by using the textual use cases, they were able to identify more failure modes or threats than using case diagrams. Tor et al. [13] have conducted two separate experiments to compare between sequence diagrams and textual use cases in hazard identification to find out which is more appropriate in discovering risks that might appear during the early stages of the system development life cycle. They concluded that sequence diagrams are better for the identification of hazards than textual use cases. Cambacédès and Bouissou [14] focused on finding new methods to deal with modeling safety and security interdependencies with Boolean logic Driven Markov Processes (BDMP), a technique that depends on graphical modeling and mathematical formalism. However, using this newly founded method is impractical because it requires knowledge and hands-on experience as it is much similar to attach tree and fault-tree. The newly founded technique was derived from a real case study used [15] where the focus was on modeling the Stuxnet Attack with BDMP hoping towards more formal risk assessments. In the field of graphical modeling, the work of Fovino and Masera [16] can be seen as relatively close to the BDMP. In fact, Fovino s work is based on a combination of classical fault trees and attack trees, which are static structures and do not provide advanced automatic treatment capacities of BDMPs. In the study conducted by Raspotnig et al. [17], the focus was on the techniques used in risk definition in safety and those used in defining risks in security and worked on defining each category of techniques separately. This study represents in-depth study on each technique. It also points out its weaknesses and strengths and in which phases of a system development life cycle, each technique could be used. In this article, we will conduct a survey according to the techniques requirments that combine safety and security. 3. SAFETY AND SECURITY TECHNIQUE REQUIREMENTS LANGUAGES There are many security technique languages that are used to analysis the risks during the system development stage.also for safety, there are many technique languages that are used for hazard analysis. In this section, we will only handle the technique languages that combine safety and security together. 3.1 HAZOP - The HAZard and Operability HAZOP, as its name suggests, is a technique for identifying and analyzing hazards and operational threats in a system. The technique originates from the chemical industry in the 1970s, but has been applied in different types of industries since that time. The ability of this technique is to be adapted to many types of systems taking different parts into consideration such as hardware equipment, software, procedures and humans. It is sought to be one of the reasons why this 3
4 technique is popular. An important part of the technique is the use and combination of parameters and guidewords for the risk identification, such as the parameter flow combined with the guidewords: more, less or other than. There are a few examples of applying HAZOP in the security field [18], but with specialized post- and pre-guidewords combined with attributes for security considerations, e.g., pre-guide-word, deliberately combined with the attribute manipulation and post-guide-word insider. HAZOP is used with a worksheet recording: a. Item a description of the function or purpose of item that is analyzed b. Parameter interaction description between the components or design intent of a component, affecting its operation, for example flow of data, isolate, absorb, start-up, etc... c. Guide-word the word combined with the two items above, to stimulate creativity among participants for imagining design deviation, e.g., no, less, other, early. (Table 2) shows guideword interpretations for attributes of Messages. d. Consequence a description of the deviation from design intent found with guideword e. Cause possible causal factor descriptions for the deviation found f. Hazard a description of the hazard and associated risk that occurs from the consequence description above g. Recommendations a description of the recommended mitigations for the hazard Diagrams are developed in early phases of the development, typically in an early design phase. The technique is also well suited for usage in the detailed design phase. The technique is used by safety personnel, and it is important that the process is led by an experienced team leader. When applying the technique, safety and system experts, developers, and users normally give input. HAZOP is one of the most popular generic techniques used for hazards identification. Although the technique was originally developed for chemical plants and processing systems, it has also been applied to a range of systems such as extensive chemical processing plants, large distributed defense systems and embedded aircraft braking systems [19], it has been used with different systems within various industries. Some parts of the technique are however modified for special purposes or to work with particular systems especially guidewords and the parameters for security [18]. As mentioned above, there is a range of application areas for HAZOP. It is assumed that the technique can be applied both to safety critical systems, such as reactor protection systems, and to safety related systems. There have also been examples of using the HAZOP within the security field [18], in a security critical context by adding guideword to security risk analysis. Table 2. Example of Suggested guideword interpretations for Messages attributes[20]. Entity=Message Attribute Guide word Interpretation predecessor/ No Message is not sent when it should be. successor Other than Message sent at a wrong time. As well as Message sent at a correct time and also at an incorrect time. Sooner Message sent earlier within message sequence than intended. Later Message sent later within message sequence than intended. 4
5 sender/ receiver No Message is not sent when intended (to any destination). Other than Message sent to a wrong object. As well as Message sent to a correct object and also an incorrect object. Reverse Source and destination objects are reversed. More Message sent to more objects than intended. Less Message sent to fewer objects than intended. The recommended steps in a HAZOP study, which is based on examining design representations of a system, are: identifying each entity in the design representation; descripting the interaction between the components of a component affecting its operation like flow of data; applying guidewords to attributes by investigating deviations from the design; investigating the causes and consequences of each deviation; and descripting the recommended mitigations for the hazard/risk. 3.2 BDMP - Boolean Logic Driven Markov Processes BDMP technique several researches [21] focused on finding new methods to deal with modeling safety and security interdependencies with BDMP. A technique depends on graphical modeling and mathematical formalism (Figure 1). However, using this newly founded method is impractical because it requires knowledge and hands-on experience because it is very much similar to attack tree and fault-tree with Markov processes. The ability to formulate BDMP enables modelling dynamic feature with triggers. BDMP is used to model the different combinations of events that may lead to undesired events, such as system. In a tree, these events represent the leaves. Each leaf is associated to a triggered Markov process that models its different states. This process can be in a required and Not-Required mode or in an Idle or Active mode for safety-related and security-related leaves respectively. This method, besides other outputs, gives quantitative results including the sequences that most probable lead to unwanted events. BDMP is suitable for risk evaluation process and it consists of three phases: a. Context definition defines the scope and boundaries of a system and the nature of the risks will be examined. b. System description addressing risks documents the scheme of the system intended to be built and its functions. c. Risk estimation this phase consists of three sub-phases: analysing data, representing and modelling system related risks, and exploiting the model. Prevention and mitigation choices: this phase depends on quantitative and qualitative risk estimation. 5
6 Figure 1 Modeling safety and security interdependencies with BDMP [21]. The newly founded technique was derived from a real case study [22] where the focus was on modeling case study about transporting a polluting substance with BDMP hoping towards more formal risk assessments. 3.3 KAOS for Safety Knowledge Acquisition in automated Specification (KAOS) is a methodology for engineering requirements that enables analysts to build models requirements and to derive documents requirements from KAOS models (Figure 2). The meta-model for KAOS has been discussed in [23]. KAOS is a goal-oriented requirements engineering method intend to support the entire process of requirements analysis and elaboration from high-level goals that need to be achieved to the requirements. Objects and operations notions assigned to various agents notion in the composite system provide a specification language, a tool support, and an elaboration method [24]. This section addresses KAOS for safety as well as artefact Safety Obstacles (Hazard). The Goal model of KAOS looks like a tree that expresses relationships among goals of a system by showing how low-level goals contribute to higher-level goals and how in this goal model, an AND-refinement link relates a parent goal to a set of sub-goals that must be satisfied for the parent goal to be satisfied. Using KAOS goal refinement patterns are considered an efficient way to build the model because proofs can be reused. These patterns are capable of reducing time and cost of goal model construction. An Obstacle meta-model is like a Goal meta-model notation (for security). However, the two are used to represent safety goals to reach obstacle treatment through the refinement into subobstacles. Each of these sub-obstacles is anchored with a new goal that works towards limiting and treating these obstacles. This method is implemented on the rest of the sub-obstacles until the goal Obstacle treatment is achieved, which is the main goal and is located on the top level of the KAOS diagram. 6
7 Figure 2. Legend KAOS For safety requirements, it is very important to deal with Obstacles (hazard) KAOS element, which capture undesired properties. It allows analysts to identify and address exceptional circumstances during requirements engineering in order to produce robust or new requirements to avoid or reduce the impact of obstacles giving more reliable software [24]. The more specific the goal, the more specific its obstructing obstacles will be. As mentioned earlier, a high-level goal produces high-level obstacles that will be refined into much smaller subobstacles. These sub-obstacles are used for precise obstacle identification in order to evaluate their feasibility through agent behaviour negative scenarios. It is much easier and preferable to refine what is wanted than what is not wanted. The level of how extensive obstacle identification is depends on the type and priority of the obstructed goal. For example, obstacle identification in Safety Goals needs to be adequately extensive. Domain-specific cost-benefit analysis needs to be performed to decide when the obstacle identification process should terminate. Obstacle OR-refinement yields sufficient sub-obstacles to establish the obstacle; each ORrefinement of an obstacle obstructs the goal that is obstructed by this obstacle. Goals and AND/OR refinement of obstacles proceed exactly the same way except for only a few alternative OR refinements that are generally considered, in the case of obstacles, one may identify as many alternative obstacles as possible. KAOS supports using semi-formal and linear formal specification language Linear Temporal Logic (LTL) to describe Goals, Obstacles and to perform logical proofs, which gives accuracy and reveals ambiguities. This is what sensitive and critical systems are in need for, which integrates between safety and security after identifying the requirements specifications of both and later reduced to formal languages that reveals complications resulted from achieving the goals of safety and security. Formal specifications can aid in correct design of system requirements specifications and improve the quality of system-to-be [25]. The semantic language of KAOS is necessary to ensure the correctness of the safety-critical requirements specifications described for developing the systems. The following are definitions of elements found in KAOS: 1. Goals descriptive milestones statements intended to be achieved. 2. Agents active components like humans, devices, and legacy software that play a role towards achieving goals. 7
8 3. Obstacle a condition if satisfied, may prevent a goal from being achieved and is used in producing an anti-model that shows why and by whom the original model can be threatened. 4. Requirements a terminal goal that an agent is responsible for in the software to be developed. 5. Object any entity defined in the system. An object has features and relations. 6. Action the interaction between inputs and outputs within an object. Each action has preaction, post-action, and triggers conditions. 7. Operation model description of all behaviours whose requirements need to be fulfilled by agents. Behaviours are expressed in terms of operations that agents performed. Operations work on objects: they can create objects, trigger, state transitions of objects, and activate other operations [26]. 8. Responsibility model the responsibility model contains all responsibility diagrams. Each diagram describes the requirements and expectations an agent is responsible for, or has been assigned to them. An agent is assigned to expectations in a goal model [26]. 3.4 KAOS for Security This section will focus on the security extension of KAOS, hereafter referred to KAOS Security Extension (SE). The KAOS-SE is highly interrelated with the original KAOS methodology, and uses the model artifacts for security: 1- Anti-goals attacker s own goals, including malicious obstacles to security goals. 2- Attackers or attacker agents malicious agents in the environment. 3- Anti-requirements terminal anti-goals that are realizable by the identified attacker agents. 4- Vulnerabilities terminal anti-goals that are realizable by attackee software agents. 5- Countermeasures a new security goal directed towards vulnerabilities or antirequirements. For security requirements analysis and elaboration by the use of Anti-Goals KAOS element, the goal notion allows the expression of security requirements patterns in terms of anti-goals notion and vulnerabilities of the system that is being studied. These patterns can also include a definition of the solution, or counter measure, to the attack in terms of goals that avoid a given vulnerability. 3.5 MUC - Misuse-Case MUC diagrams, the conception of use cases is used to create and relate corresponding misuse cases used to address particularly security requirements [27]. The functionality of a system is modeled in use cases focusing on interactions with users and responses from the system. MUC extend the positive use cases with the negative ones to ensure eliciting security requirements. A use case and a misuse case are related in using a directed association. If the association points line from a misuse case to a use case has the stereotype threaten while if the association points line from a security use case to a misuse case has the stereotype mitigate. It is stated that ordinary use cases represent requirements, security cases represent security requirements, and misuse cases represent security threats. The essence of the contained use cases is captured in an associated textual description since use case diagrams only give an overview of the system functionality. Misuse cases are applicable to design a system that covers different security needs. It is possible to consider all three CIA (Confidentiality, Integrity and availability ) goals. It incorporates common risk and threat analysis techniques. The new elements that are introduced by misuse cases and related with the use case elements are [27]: 8
9 1- Misuser an actor who initiates misuse cases, e.g., a hacker or thief. 2- Misuse case actions that can cause harm to some system or stakeholder, e.g., stealing sensitive information. 3- Threatens a relation where a use case is exploited by a misuse case, e.g., the registering of information in a system is exploited by stealing this information. 4- Security use case a use case intended to mitigate misuse cases. 5- Mitigates a relation where a security use case countermeasures a misuse case, e.g., protecting the sensitive information. There are three ways of describing misuse cases; a lightweight textual description, an extensive textual description and the misuse case diagram. These can either be used separately or in combination with each other. For both the textual descriptions there exist templates. The process consists of five steps, which consists of (1) Identify critical assets in the system, (2) Define security goals for each asset, (3) Identify threats for each security goal, (4) Identify and analyze risks for the threats, (5) Define security requirements using mitigatation. Misuse cases are applicable to design a system that covers different security needs. It is possible to consider all three CIA goals. It incorporates common risk and threat analysis techniques. Depending on the type of textual description used, it is in Sindre and Opdahl [27] described that the technique applies to security critical parts with the extensive description as well as the security related parts of a system through the lightweight description. It is stated that the technique has been used in E-shop and medical domains, along with a knowledge map and open web applications. Several researches focused on narrowing the gap and comparisons between tools and techniques used in safety engineering and security engineering like Tor and Guttorm [28] where two approaches were compared against each other in using them to perform safety analysis relying on a use case. The comparison was between two methods MUC and FMEA (Failure Mode and Effect Analysis) and an experiment was conducted by two groups of students each on a method. The results conclude that MUC is better than FMEA in analysing failure modes related to user interaction and that MUC is easier and less confusing than FMEA. However, the results show that FMEA is better for in-depth analysis on failure modes related to the inner working of the system. 4. ACCIDENT ANALYSIS TECHNIQUE LANGUAGES Accident techniques languages such as Swiss cheese model [29], AcciMap [30], STAMP [31] and STPA [32] classified as systems-based accident analysis methods. The approaches of these techniques are not domain-specific in accident analysis for a particular industry and what makes these approaches stand out is that the socio-technical aspect is taken into account during the analysis. Furthermore, these approaches are used in different industries such as aviation, defence, food, public health, oil and gas, and rail transport. In Figure 3, shows the development of the tools over years and illustrates the classification of the tools under four categories. We selected the Swiss-Cheese model which takes in consideration human factor, the AcciMap which takes in consideration the organizational factor and the STAMP which takes in consideration system theory factor. Previously, we mentioned HAZOP which takes in consideration technical factor. 9
10 4.1. SCM - Swiss-Cheese Model Figure 3. Accident Analysis and Risk Assessment Methods [33]. This model is considered one of the most famous accident causation models, also known as event-chain model. Reason [34] has famously developed a model based on the Swiss Cheese Metaphor (Figure 4) making use of slices and holes in cheese. The model suggests multiple contributors represented by the holes in cheese slices must be aligned for any adverse events to occur. Represented by the slices themselves, barriers in a system are intended to prevent errors that result in these unfavourable events. This SCM is not without drawbacks, and is not accepted uncritically [29]. Reason s model [34] describes the interaction between system wide latent conditions/potential conditions (a.k.a., inadequate designs and equipment, management and maintenance failures, lack in training and/or procedures) and unsafe acts made by human operators and their role in accidents. The model also describes the role of defences, such as protective equipment, rules and regulations, training, and engineered safety features, which are designed to prevent accidents. Weaknesses in these defences, created by latent conditions and unsafe acts [29], allow defences to be breached and accidents to occur. Figure 4.1, Illustrates that, in the Swiss-Cheese model, an organization's defences against failure are modelled as a series of barriers, represented as slices of cheese. The holes in the slices represent weaknesses in individual parts of the system and are continually varying in terms of size and position across the slices. The system produces failures when a hole in each slice shortly aligns. If these holes aligned, it can allow the accident to occur [29]. 10
11 4.2. AcciMap Figure 4. Reason's Swiss cheese model, Adapted from [29]. The AcciMap accident analysis technique is based on Rasmussen s risk management framework. AcciMap is a generic approach and does not use taxonomies of failures across the different levels that are considered and designed specifically for analysing the causes of accidents and incidents that occur in complex socio-technical systems [35][36]. The AcciMap method involves the construction of a multi-layered causal diagram in which the various causes of an accident are arranged according to their causal remoteness from the outcome (depicted at the bottom of the diagram). The lower levels typically represent the immediate precursors to the event, relating to the activities of workers and to physical events, processes and conditions that contributed to the outcome. The next highest levels typically represent company and organisational-level factors. The highest levels generally incorporate governmental or societal-level causal factors, which are external to the organisation(s) involved in the event [30]. This way, the full range of factors that contributed to the event is modelled. Figure 5, Illustrates that, Rasmussen s risk management framework [35] outlined the AcciMap method, which is used to graphically represent the system-wide failures, the precise format of the diagram varies depending on the purpose of analysis. Figure 5. Rasmussen s risk management framework using AcciMap method, Adapted from [30]. 11
12 4.3. STAMP - System-Theoretic Accident Model and Processes STAMP was developed by Nancy G. Leveson [31], and is similar in theory with traditional hazard analysis methods (for example, Rasmussen s risk management framework, AcciMap). However, Nancy [37] considers these traditional hazard analysis methods only to deal with monitoring the accident flow and how it occurred. The traditional methods cannot explain how the accident happened in a component-nested system and taking the Socio-technical aspects into consideration, which in turn interacts with this system. It is considered as a cognitive hazard analysis method because it integrates all aspects of risk, including organizational and social aspects to understand accident causation. Then, she published various publications extending the former, focussed on safety [38][39]. These publications are finally reinforced by some recent tutorials [40][41], presenting his work in-depth about safety engineering, which are part of resilience engineering [42]. STAMP [31] is the most recent approach to be developed, and considered a new accident causality model based on systems theory [43]. STAMP approach deals with safety through a technical language called Systems-Theoretic Process Analysis (STPA) that interacts with identifying hazards and hazard analysis; it can be used early in the system development life cycle to elicitation high level safety requirements and constraints in terms of identifying more causal factors and hazardous scenarios [43]. Young and Leveson [44][45] has developed an extension of Systems-Theoretic Process Analysis (STPA) to serve the hazard analysis for security engineering (Young used term cyber-security) and known as Systems-Theoretic Process Analysis for security (STPA-Sec). Young published some recent tutorials [32] presenting his work in-depth about security (Cyber- Security). Some tools that automate the activities of STPA were developed to support the hazard and accident analysis processes including A-STPA and SpecTRM. 5. CONCLUSIONS AND FURTHER WORK Integrating safety and security requirements should occur during the initial development phases of the system because it is a very important step for safety and security engineers in order to discover the causes of hazards and risks. Furthermore, it is vital since it s the only thing that covers the gap between safety engineers and security engineers especially since a security engineer knows the risks that a system could face and therefore has to protect the system and the equipment from any threats. On the other hand, a safety engineer does not know what the hazards would be or their effect on the environment. Therefore, a safety engineer will have to discover the unintentional hazard the system could possibly face. This is the critical point from which hazard and risks are derived by both types of engineers using an easy approach to communicate. The assumption exists that the current security and safety requirements techniques and approaches, are only dedicated to their specific engineering domain. We surveyed the similar terminology, standards and modelling approaches that are established to elicit and validate them. Our remarks also indicate that the techniques and approaches for security and safety requirements cannot be simply interplayed but they require a systematic conceptual integration. In the future work, we will develop a structured approach to integrate between security and safety by creating a SaS (Safety and Security) domain model. Furthermore, it will demonstrate that it is possible to use goal-oriented KAOS (Knowledge Acquisition in automated Specification) language in threat and hazard analysis to cover both safety and security domains making their outputs, or artifacts, well-structured and comprehensive, which will result in dependability due to the comprehensiveness of the analysis. The developed structured approach will act as an interface for active interactions in risk and hazard management in terms of universal coverage, finding solutions for differences and contradictions which can be overcome by integrating the safety and security domains and using a unified system analysis technique (KAOS) that will result in analysis centrality. 12
13 REFERENCES [1] Piètre-Cambacédès, L., & Chaudet, C. (2010). The SEMA referential framework: Avoiding ambiguities in the terms "security" and "safety". International Journal of Critical Infrastructure Protection, 3(2), [2] Fabian, B., Gürses, S., Heisel, M., Santen, T., & Schmidt, H. (2010). A comparison of security requirements engineering methods. Requirements engineering, 15(1), [3] Eames, D. P., & Moffett, J. (1999, September). The integration of safety and security requirements. In International Conference on Computer Safety, Reliability, and Security (pp ). Springer Berlin Heidelberg. [4] Firesmith, Donald G. Common Concepts Underlying Safety Security And Survivability Engineering. No. CMU/SEI-2003-TN-033. CARNEGIE-MELLON UNIV PITTSBURGH PA SOFTWARE ENGINEERING INST, [5] Firesmith, D. G. (2010, May). Engineering safety-and security-related requirements for softwareintensive systems: tutorial summary. In Proceedings of the 32nd ACM/IEEE International Conference on Software Engineering-Volume 2 (pp ). ACM. [6] Allenby, K., & Kelly, T. (2001). Deriving Safety Requirements Using Scenarios. In Requirements Engineering, Proceedings. Fifth IEEE International Symposium on (pp ). IEEE /ISRE [7] Srivatanakul, T., Clark, J. A., & Polack, F. (2004, September). Effective security requirements analysis: Hazop and use cases. In International Conference on Information Security (pp ). Springer Berlin Heidelberg. [8] Alexander, Ian. Misuse Cases: Use Cases With Hostile Intent, Software, IEEE, vol.20, no.1, pp.58,66, Jan/Feb [9] Zafar, Saad, and R. Geoff Dromey. Integrating Safety And Security Requirements Into Design Of An Embedded System. 12th Asia-Pacific Software Engineering Conference (APSEC'05). IEEE, [10] Sun, M., Mohan, S., Sha, L., & Gunter, C. (2009, July). Addressing safety and security contradictions in cyber-physical systems. In Proceedings of the 1st Workshop on Future Directions in Cyber-Physical Systems Security (CPSSW 09). [11] Sommerville, Ian. An Integrated Approach To Dependability Requirements Engineering. Current Issues in Safety-Critical Systems. Springer London, _1 [12] Stålhane, Tor, and Guttorm Sindre. Safety Hazard Identification By Misuse Cases: Experimental Comparison Of Text And Diagrams. International Conference on Model Driven Engineering Languages and Systems. Springer Berlin Heidelberg, [13] Stålhane, Tor, Guttorm Sindre, and Lydie Du Bousquet. Comparing Safety Analysis Based On Sequence Diagrams And Textual Use Cases. International Conference on Advanced Information Systems Engineering. Springer Berlin Heidelberg, _14 [14] Piètre-Cambacédès, Ludovic, and Marc Bouissou. Cross-Fertilization Between Safety And Security Engineering. Reliability Engineering & System Safety 110 (2013): [15] Kriaa, Siwar, Marc Bouissou, and Ludovic Piètre-Cambacédès. Modeling The Stuxnet Attack With BDMP: Towards More Formal Risk Assessments th International Conference on Risks and Security of Internet and Systems (CRiSIS). IEEE,
14 [16] Fovino, Igor Nai, and Marcelo Masera. Through The Description Of Attacks: A Multidimensional View. International Conference on Computer Safety, Reliability, and Security. Springer Berlin Heidelberg, [17] Raspotnig, Christian, and Andreas Opdahl. Comparing Risk Identification Techniques For Safety And Security Requirements. Journal of Systems and Software 86.4 (2013): [18] Winther, R., Johnsen, O. A., & Gran, B. A. (2001, September). Security assessments of safety critical systems using HAZOPs. In International Conference on Computer Safety, Reliability, and Security (pp ). Springer Berlin Heidelberg. [19] Ericson, C. A. (2015). Hazard analysis techniques for system safety. John Wiley & Sons. [20] Hansen, K. M., Wells, L., & Maier, T. (2004). HAZOP analysis of UML-based software architecture descriptions of safety-critical systems. Proceedings of NWUML, [21] Piètre-Cambacédès, L., & Bouissou, M. (2010, October). Modeling safety and security interdependencies with BDMP (Boolean logic Driven Markov Processes). In Systems Man and Cybernetics (SMC), 2010 IEEE International Conference on (pp ). IEEE. [22] Kriaa, S., Bouissou, M., & Piètre-Cambacédès, L. (2012, October). Modeling the Stuxnet attack with BDMP: Towards more formal risk assessments. In th International Conference on Risks and Security of Internet and Systems (CRiSIS) (pp. 1-8). IEEE. [23] Matulevičius, R., Heymans, P., & Sindre, G. (2015). COMPARING GOAL-MODELLING TOOLS WITH THE RE-TOOL EVALUATION APPROACH*. Information Technology And Control, 35(3). [24] Van Lamsweerde, A., & Letier, E. (2000). Handling obstacles in goal-oriented requirements engineering. IEEE Transactions on Software Engineering, 26(10), [25] Nakagawa, H., Taguchi, K., & Honiden, S. (2007, November). Formal specification generator for KAOS: model transformation approach to generate formal specifications from KAOS requirements models. In Proceedings of the twenty-second IEEE/ACM international conference on Automated software engineering (pp ). ACM. [26] Respect, I. T. (2007). A KAOS Tutorial. [27] Sindre, G., & Opdahl, A. L. (2005). Eliciting security requirements with misuse cases. Requirements engineering, 10(1), [28] Stålhane, T., & Sindre, G. (2007, November). A comparison of two approaches to safety analysis based on use cases. In International Conference on Conceptual Modeling (pp ). Springer Berlin Heidelberg. [29] Perneger, T. V. (2005). The Swiss cheese model of safety incidents: are there holes in the metaphor?. BMC health services research, 5(1), 1. PMid: PMCid:PMC [30] Salmon, P. M., Cornelissen, M., & Trotter, M. J. (2012). Systems-based accident analysis methods: A comparison of Accimap, HFACS, and STAMP. Safety science, 50(4), [31] Leveson, N. (2004). A new accident model for engineering safer systems. Safety science, 42(4), [32] Young Jr, W. E. (2014). STPA-SEC for cyber security mission assurance. Eng Syst. Div. Syst. Eng. Res. Lab. [33] EUROCONTROL, A. (2009). White Paper on Resilience Engineering for ATM. Report of the Project Resilience Engineering for ATM. [34] Reason, J. (1990). The contribution of latent human failures to the breakdown of complex systems. Philosophical Transactions of the Royal Society of London B: Biological Sciences, 327(1241), PMid:
15 [35] Rasmussen, Jens. "Risk management in a dynamic society: a modelling problem." Safety science 27.2 (1997): [36] Rasmussen, J., & Suedung, I. (2000). Proactive risk management in a dynamic society. Swedish Rescue Services Agency. [37] Leveson, N. G. (2004). A systems-theoretic approach to safety in software-intensive systems. IEEE Transactions on Dependable and Secure computing, 1(1), [38] Nancy G. Leveson, "An STPA Primer Version 1", August 2013b. [39] Nancy G. Leveson, "Tutorial: Engineering a Safer World", STAMP Conference, [40] Nancy G. Leveson, "Tutorial: Engineering a Safer World", STAMP Conference, [41] Nancy G. Leveson, "Tutorial: Engineering a Safer World", STAMP Conference, [42] Woods, D. D., Leveson, N., & Hollnagel, E. (Eds.). (2012). Resilience engineering: concepts and precepts. Ashgate Publishing, Ltd.. [43] Leveson, N. (2011). Engineering a safer world: Systems thinking applied to safety. Mit Press. PMid: [44] Young, W., & Leveson, N. (2013, December). Systems thinking for safety and security. In Proceedings of the 29th Annual Computer Security Applications Conference (pp. 1-8). ACM. [45] Young, W., & Leveson, N. G. (2014). An integrated approach to safety and security based on systems theory. Communications of the ACM, 57(2),
Deviational analyses for validating regulations on real systems
 REMO2V'06 813 Deviational analyses for validating regulations on real systems Fiona Polack, Thitima Srivatanakul, Tim Kelly, and John Clark Department of Computer Science, University of York, YO10 5DD,
REMO2V'06 813 Deviational analyses for validating regulations on real systems Fiona Polack, Thitima Srivatanakul, Tim Kelly, and John Clark Department of Computer Science, University of York, YO10 5DD,
Towards an MDA-based development methodology 1
 Towards an MDA-based development methodology 1 Anastasius Gavras 1, Mariano Belaunde 2, Luís Ferreira Pires 3, João Paulo A. Almeida 3 1 Eurescom GmbH, 2 France Télécom R&D, 3 University of Twente 1 gavras@eurescom.de,
Towards an MDA-based development methodology 1 Anastasius Gavras 1, Mariano Belaunde 2, Luís Ferreira Pires 3, João Paulo A. Almeida 3 1 Eurescom GmbH, 2 France Télécom R&D, 3 University of Twente 1 gavras@eurescom.de,
A New Systems-Theoretic Approach to Safety. Dr. John Thomas
 A New Systems-Theoretic Approach to Safety Dr. John Thomas Outline Goals for a systemic approach Foundations New systems approaches to safety Systems-Theoretic Accident Model and Processes STPA (hazard
A New Systems-Theoretic Approach to Safety Dr. John Thomas Outline Goals for a systemic approach Foundations New systems approaches to safety Systems-Theoretic Accident Model and Processes STPA (hazard
rones-vulnerable-to-terrorist-hijackingresearchers-say/
 http://www.youtube.com/v/jkbabvnunw0 http://www.foxnews.com/tech/2012/06/25/d rones-vulnerable-to-terrorist-hijackingresearchers-say/ 1 The Next Step: A Fully Integrated Global Multi-Modal Security and
http://www.youtube.com/v/jkbabvnunw0 http://www.foxnews.com/tech/2012/06/25/d rones-vulnerable-to-terrorist-hijackingresearchers-say/ 1 The Next Step: A Fully Integrated Global Multi-Modal Security and
A Hybrid Risk Management Process for Interconnected Infrastructures
 A Hybrid Management Process for Interconnected Infrastructures Stefan Schauer Workshop on Novel Approaches in and Security Management for Critical Infrastructures Vienna, 19.09.2017 Contents Motivation
A Hybrid Management Process for Interconnected Infrastructures Stefan Schauer Workshop on Novel Approaches in and Security Management for Critical Infrastructures Vienna, 19.09.2017 Contents Motivation
Socio-cognitive Engineering
 Socio-cognitive Engineering Mike Sharples Educational Technology Research Group University of Birmingham m.sharples@bham.ac.uk ABSTRACT Socio-cognitive engineering is a framework for the human-centred
Socio-cognitive Engineering Mike Sharples Educational Technology Research Group University of Birmingham m.sharples@bham.ac.uk ABSTRACT Socio-cognitive engineering is a framework for the human-centred
Grundlagen des Software Engineering Fundamentals of Software Engineering
 Software Engineering Research Group: Processes and Measurement Fachbereich Informatik TU Kaiserslautern Grundlagen des Software Engineering Fundamentals of Software Engineering Winter Term 2011/12 Prof.
Software Engineering Research Group: Processes and Measurement Fachbereich Informatik TU Kaiserslautern Grundlagen des Software Engineering Fundamentals of Software Engineering Winter Term 2011/12 Prof.
Empirical Studies of Methods for Safety and Security Co-analysis of Autonomous Boat
 Empirical Studies of Methods for Safety and Security Co-analysis of Autonomous Boat Erik Nilsen Torkildson, Jingyue Li, Stig Ole Johnsen Norwegian University of Science and Technology (NTNU) Jon Arne Glomsrud
Empirical Studies of Methods for Safety and Security Co-analysis of Autonomous Boat Erik Nilsen Torkildson, Jingyue Li, Stig Ole Johnsen Norwegian University of Science and Technology (NTNU) Jon Arne Glomsrud
An Ontology for Modelling Security: The Tropos Approach
 An Ontology for Modelling Security: The Tropos Approach Haralambos Mouratidis 1, Paolo Giorgini 2, Gordon Manson 1 1 University of Sheffield, Computer Science Department, UK {haris, g.manson}@dcs.shef.ac.uk
An Ontology for Modelling Security: The Tropos Approach Haralambos Mouratidis 1, Paolo Giorgini 2, Gordon Manson 1 1 University of Sheffield, Computer Science Department, UK {haris, g.manson}@dcs.shef.ac.uk
Design Science Research Methods. Prof. Dr. Roel Wieringa University of Twente, The Netherlands
 Design Science Research Methods Prof. Dr. Roel Wieringa University of Twente, The Netherlands www.cs.utwente.nl/~roelw UFPE 26 sept 2016 R.J. Wieringa 1 Research methodology accross the disciplines Do
Design Science Research Methods Prof. Dr. Roel Wieringa University of Twente, The Netherlands www.cs.utwente.nl/~roelw UFPE 26 sept 2016 R.J. Wieringa 1 Research methodology accross the disciplines Do
PRIMATECH WHITE PAPER COMPARISON OF FIRST AND SECOND EDITIONS OF HAZOP APPLICATION GUIDE, IEC 61882: A PROCESS SAFETY PERSPECTIVE
 PRIMATECH WHITE PAPER COMPARISON OF FIRST AND SECOND EDITIONS OF HAZOP APPLICATION GUIDE, IEC 61882: A PROCESS SAFETY PERSPECTIVE Summary Modifications made to IEC 61882 in the second edition have been
PRIMATECH WHITE PAPER COMPARISON OF FIRST AND SECOND EDITIONS OF HAZOP APPLICATION GUIDE, IEC 61882: A PROCESS SAFETY PERSPECTIVE Summary Modifications made to IEC 61882 in the second edition have been
Reconciling Systems-Theoretic and Component-Centric Methods for Safety and Security Co-Analysis
 Reconciling Systems-Theoretic and Component-Centric Methods for Safety and Security Co-Analysis William G. Temple 1, Yue Wu 1, Binbin Chen 1, Zbigniew Kalbarczyk 2 1 Advanced Digital Sciences Center, Illinois
Reconciling Systems-Theoretic and Component-Centric Methods for Safety and Security Co-Analysis William G. Temple 1, Yue Wu 1, Binbin Chen 1, Zbigniew Kalbarczyk 2 1 Advanced Digital Sciences Center, Illinois
A FRAMEWORK FOR PERFORMING V&V WITHIN REUSE-BASED SOFTWARE ENGINEERING
 A FRAMEWORK FOR PERFORMING V&V WITHIN REUSE-BASED SOFTWARE ENGINEERING Edward A. Addy eaddy@wvu.edu NASA/WVU Software Research Laboratory ABSTRACT Verification and validation (V&V) is performed during
A FRAMEWORK FOR PERFORMING V&V WITHIN REUSE-BASED SOFTWARE ENGINEERING Edward A. Addy eaddy@wvu.edu NASA/WVU Software Research Laboratory ABSTRACT Verification and validation (V&V) is performed during
Proposed Curriculum Master of Science in Systems Engineering for The MITRE Corporation
 Proposed Curriculum Master of Science in Systems Engineering for The MITRE Corporation Core Requirements: (9 Credits) SYS 501 Concepts of Systems Engineering SYS 510 Systems Architecture and Design SYS
Proposed Curriculum Master of Science in Systems Engineering for The MITRE Corporation Core Requirements: (9 Credits) SYS 501 Concepts of Systems Engineering SYS 510 Systems Architecture and Design SYS
Applying systems thinking to safety assurance of Nuclear Power Plants
 Applying systems thinking to safety assurance of Nuclear Power Plants Francisco Luiz de Lemos Instituto de Pesquisas Energeticas/ Comissao Nacional de Energia Nuclear IPEN/CNEN _ Brazil IMPRO Dialog Forum
Applying systems thinking to safety assurance of Nuclear Power Plants Francisco Luiz de Lemos Instituto de Pesquisas Energeticas/ Comissao Nacional de Energia Nuclear IPEN/CNEN _ Brazil IMPRO Dialog Forum
Intro to Systems Theory and STAMP John Thomas and Nancy Leveson. All rights reserved.
 Intro to Systems Theory and STAMP 1 Why do we need something different? Fast pace of technological change Reduced ability to learn from experience Changing nature of accidents New types of hazards Increasing
Intro to Systems Theory and STAMP 1 Why do we need something different? Fast pace of technological change Reduced ability to learn from experience Changing nature of accidents New types of hazards Increasing
A web-based early-warning service to monitor drinking-water treatment plant operations
 Snapshots of Doctoral Research at University College Cork 2010 A web-based early-warning service to monitor drinking-water treatment plant operations Franclin S. Foping Cork Constraint Computation Centre,
Snapshots of Doctoral Research at University College Cork 2010 A web-based early-warning service to monitor drinking-water treatment plant operations Franclin S. Foping Cork Constraint Computation Centre,
Leveraging 21st Century SE Concepts, Principles, and Practices to Achieve User, Healthcare Services, and Medical Device Development Success
 Leveraging 21st Century SE Concepts, Principles, and Practices to Achieve User, Healthcare Services, and Medical Device Development Success Charles Wasson, ESEP Wasson Strategics, LLC Professional Training
Leveraging 21st Century SE Concepts, Principles, and Practices to Achieve User, Healthcare Services, and Medical Device Development Success Charles Wasson, ESEP Wasson Strategics, LLC Professional Training
Methodology for Agent-Oriented Software
 ب.ظ 03:55 1 of 7 2006/10/27 Next: About this document... Methodology for Agent-Oriented Software Design Principal Investigator dr. Frank S. de Boer (frankb@cs.uu.nl) Summary The main research goal of this
ب.ظ 03:55 1 of 7 2006/10/27 Next: About this document... Methodology for Agent-Oriented Software Design Principal Investigator dr. Frank S. de Boer (frankb@cs.uu.nl) Summary The main research goal of this
STPA FOR LINAC4 AVAILABILITY REQUIREMENTS. A. Apollonio, R. Schmidt 4 th European STAMP Workshop, Zurich, 2016
 STPA FOR LINAC4 AVAILABILITY REQUIREMENTS A. Apollonio, R. Schmidt 4 th European STAMP Workshop, Zurich, 2016 LHC colliding particle beams at very high energy 26.8 km Circumference LHC Accelerator (100
STPA FOR LINAC4 AVAILABILITY REQUIREMENTS A. Apollonio, R. Schmidt 4 th European STAMP Workshop, Zurich, 2016 LHC colliding particle beams at very high energy 26.8 km Circumference LHC Accelerator (100
My 36 Years in System Safety: Looking Backward, Looking Forward
 My 36 Years in System : Looking Backward, Looking Forward Nancy Leveson System safety engineer (Gary Larsen, The Far Side) How I Got Started Topics How I Got Started Looking Backward Looking Forward 2
My 36 Years in System : Looking Backward, Looking Forward Nancy Leveson System safety engineer (Gary Larsen, The Far Side) How I Got Started Topics How I Got Started Looking Backward Looking Forward 2
Digital Engineering Support to Mission Engineering
 21 st Annual National Defense Industrial Association Systems and Mission Engineering Conference Digital Engineering Support to Mission Engineering Philomena Zimmerman Dr. Judith Dahmann Office of the Under
21 st Annual National Defense Industrial Association Systems and Mission Engineering Conference Digital Engineering Support to Mission Engineering Philomena Zimmerman Dr. Judith Dahmann Office of the Under
THREAT ANALYSIS FOR THE TRANSPORT OF RADIOACTIVE MATERIAL USING MORPHOLOGICAL ANALYSIS
 Proceedings of the 15th International Symposium on the Packaging and Transportation of Radioactive Materials PATRAM 2007 October 21-26, 2007, Miami, Florida, USA THREAT ANALYSIS FOR THE TRANSPORT OF RADIOACTIVE
Proceedings of the 15th International Symposium on the Packaging and Transportation of Radioactive Materials PATRAM 2007 October 21-26, 2007, Miami, Florida, USA THREAT ANALYSIS FOR THE TRANSPORT OF RADIOACTIVE
UNIT-III LIFE-CYCLE PHASES
 INTRODUCTION: UNIT-III LIFE-CYCLE PHASES - If there is a well defined separation between research and development activities and production activities then the software is said to be in successful development
INTRODUCTION: UNIT-III LIFE-CYCLE PHASES - If there is a well defined separation between research and development activities and production activities then the software is said to be in successful development
On the use of the Goal-Oriented Paradigm for System Design and Law Compliance Reasoning
 On the use of the Goal-Oriented Paradigm for System Design and Law Compliance Reasoning Mirko Morandini 1, Luca Sabatucci 1, Alberto Siena 1, John Mylopoulos 2, Loris Penserini 1, Anna Perini 1, and Angelo
On the use of the Goal-Oriented Paradigm for System Design and Law Compliance Reasoning Mirko Morandini 1, Luca Sabatucci 1, Alberto Siena 1, John Mylopoulos 2, Loris Penserini 1, Anna Perini 1, and Angelo
Architecture-Led Safety Process
 Architecture-Led Safety Process Peter H. Feiler Julien Delange David P. Gluch John D. McGregor December 2016 TECHNICAL REPORT CMU/SEI-2016-TR-012 Software Solutions Division http://www.sei.cmu.edu Copyright
Architecture-Led Safety Process Peter H. Feiler Julien Delange David P. Gluch John D. McGregor December 2016 TECHNICAL REPORT CMU/SEI-2016-TR-012 Software Solutions Division http://www.sei.cmu.edu Copyright
Principled Construction of Software Safety Cases
 Principled Construction of Software Safety Cases Richard Hawkins, Ibrahim Habli, Tim Kelly Department of Computer Science, University of York, UK Abstract. A small, manageable number of common software
Principled Construction of Software Safety Cases Richard Hawkins, Ibrahim Habli, Tim Kelly Department of Computer Science, University of York, UK Abstract. A small, manageable number of common software
Software-Intensive Systems Producibility
 Pittsburgh, PA 15213-3890 Software-Intensive Systems Producibility Grady Campbell Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University SSTC 2006. - page 1 Producibility
Pittsburgh, PA 15213-3890 Software-Intensive Systems Producibility Grady Campbell Sponsored by the U.S. Department of Defense 2006 by Carnegie Mellon University SSTC 2006. - page 1 Producibility
A Conceptual Modeling Method to Use Agents in Systems Analysis
 A Conceptual Modeling Method to Use Agents in Systems Analysis Kafui Monu 1 1 University of British Columbia, Sauder School of Business, 2053 Main Mall, Vancouver BC, Canada {Kafui Monu kafui.monu@sauder.ubc.ca}
A Conceptual Modeling Method to Use Agents in Systems Analysis Kafui Monu 1 1 University of British Columbia, Sauder School of Business, 2053 Main Mall, Vancouver BC, Canada {Kafui Monu kafui.monu@sauder.ubc.ca}
Managing the risk of major accidents
 Transatlantic Science Week - Synergies between Space and Offshore Exploration Hans A. Bratfos, DNV Major accidents happens We learn from them, but can we avoid them? Three Mile Island - 1979 Alexander
Transatlantic Science Week - Synergies between Space and Offshore Exploration Hans A. Bratfos, DNV Major accidents happens We learn from them, but can we avoid them? Three Mile Island - 1979 Alexander
Issues and Challenges in Coupling Tropos with User-Centred Design
 Issues and Challenges in Coupling Tropos with User-Centred Design L. Sabatucci, C. Leonardi, A. Susi, and M. Zancanaro Fondazione Bruno Kessler - IRST CIT sabatucci,cleonardi,susi,zancana@fbk.eu Abstract.
Issues and Challenges in Coupling Tropos with User-Centred Design L. Sabatucci, C. Leonardi, A. Susi, and M. Zancanaro Fondazione Bruno Kessler - IRST CIT sabatucci,cleonardi,susi,zancana@fbk.eu Abstract.
A New Approach to Safety in Software-Intensive Systems
 A New Approach to Safety in Software-Intensive Systems Nancy G. Leveson Aeronautics and Astronautics Dept. Engineering Systems Division MIT Why need a new approach? Without changing our patterns of thought,
A New Approach to Safety in Software-Intensive Systems Nancy G. Leveson Aeronautics and Astronautics Dept. Engineering Systems Division MIT Why need a new approach? Without changing our patterns of thought,
Modelling Critical Context in Software Engineering Experience Repository: A Conceptual Schema
 Modelling Critical Context in Software Engineering Experience Repository: A Conceptual Schema Neeraj Sharma Associate Professor Department of Computer Science Punjabi University, Patiala (India) ABSTRACT
Modelling Critical Context in Software Engineering Experience Repository: A Conceptual Schema Neeraj Sharma Associate Professor Department of Computer Science Punjabi University, Patiala (India) ABSTRACT
System of Systems Software Assurance
 System of Systems Software Assurance Introduction Under DoD sponsorship, the Software Engineering Institute has initiated a research project on system of systems (SoS) software assurance. The project s
System of Systems Software Assurance Introduction Under DoD sponsorship, the Software Engineering Institute has initiated a research project on system of systems (SoS) software assurance. The project s
Expression Of Interest
 Expression Of Interest Modelling Complex Warfighting Strategic Research Investment Joint & Operations Analysis Division, DST Points of Contact: Management and Administration: Annette McLeod and Ansonne
Expression Of Interest Modelling Complex Warfighting Strategic Research Investment Joint & Operations Analysis Division, DST Points of Contact: Management and Administration: Annette McLeod and Ansonne
Countering Capability A Model Driven Approach
 Countering Capability A Model Driven Approach Robbie Forder, Douglas Sim Dstl Information Management Portsdown West Portsdown Hill Road Fareham PO17 6AD UNITED KINGDOM rforder@dstl.gov.uk, drsim@dstl.gov.uk
Countering Capability A Model Driven Approach Robbie Forder, Douglas Sim Dstl Information Management Portsdown West Portsdown Hill Road Fareham PO17 6AD UNITED KINGDOM rforder@dstl.gov.uk, drsim@dstl.gov.uk
Resilience Engineering: The history of safety
 Resilience Engineering: The history of safety Professor & Industrial Safety Chair MINES ParisTech Sophia Antipolis, France Erik Hollnagel E-mail: erik.hollnagel@gmail.com Professor II NTNU Trondheim, Norge
Resilience Engineering: The history of safety Professor & Industrial Safety Chair MINES ParisTech Sophia Antipolis, France Erik Hollnagel E-mail: erik.hollnagel@gmail.com Professor II NTNU Trondheim, Norge
Putting the Systems in Security Engineering An Overview of NIST
 Approved for Public Release; Distribution Unlimited. 16-3797 Putting the Systems in Engineering An Overview of NIST 800-160 Systems Engineering Considerations for a multidisciplinary approach for the engineering
Approved for Public Release; Distribution Unlimited. 16-3797 Putting the Systems in Engineering An Overview of NIST 800-160 Systems Engineering Considerations for a multidisciplinary approach for the engineering
Towards the definition of a Science Base for Enterprise Interoperability: A European Perspective
 Towards the definition of a Science Base for Enterprise Interoperability: A European Perspective Keith Popplewell Future Manufacturing Applied Research Centre, Coventry University Coventry, CV1 5FB, United
Towards the definition of a Science Base for Enterprise Interoperability: A European Perspective Keith Popplewell Future Manufacturing Applied Research Centre, Coventry University Coventry, CV1 5FB, United
Requirements Analysis aka Requirements Engineering. Requirements Elicitation Process
 C870, Advanced Software Engineering, Requirements Analysis aka Requirements Engineering Defining the WHAT Requirements Elicitation Process Client Us System SRS 1 C870, Advanced Software Engineering, Requirements
C870, Advanced Software Engineering, Requirements Analysis aka Requirements Engineering Defining the WHAT Requirements Elicitation Process Client Us System SRS 1 C870, Advanced Software Engineering, Requirements
An Exploratory Study of Design Processes
 International Journal of Arts and Commerce Vol. 3 No. 1 January, 2014 An Exploratory Study of Design Processes Lin, Chung-Hung Department of Creative Product Design I-Shou University No.1, Sec. 1, Syuecheng
International Journal of Arts and Commerce Vol. 3 No. 1 January, 2014 An Exploratory Study of Design Processes Lin, Chung-Hung Department of Creative Product Design I-Shou University No.1, Sec. 1, Syuecheng
Evolving a Software Requirements Ontology
 Evolving a Software Requirements Ontology Ricardo de Almeida Falbo 1, Julio Cesar Nardi 2 1 Computer Science Department, Federal University of Espírito Santo Brazil 2 Federal Center of Technological Education
Evolving a Software Requirements Ontology Ricardo de Almeida Falbo 1, Julio Cesar Nardi 2 1 Computer Science Department, Federal University of Espírito Santo Brazil 2 Federal Center of Technological Education
An Introduction to Agent-based
 An Introduction to Agent-based Modeling and Simulation i Dr. Emiliano Casalicchio casalicchio@ing.uniroma2.it Download @ www.emilianocasalicchio.eu (talks & seminars section) Outline Part1: An introduction
An Introduction to Agent-based Modeling and Simulation i Dr. Emiliano Casalicchio casalicchio@ing.uniroma2.it Download @ www.emilianocasalicchio.eu (talks & seminars section) Outline Part1: An introduction
Component Based Mechatronics Modelling Methodology
 Component Based Mechatronics Modelling Methodology R.Sell, M.Tamre Department of Mechatronics, Tallinn Technical University, Tallinn, Estonia ABSTRACT There is long history of developing modelling systems
Component Based Mechatronics Modelling Methodology R.Sell, M.Tamre Department of Mechatronics, Tallinn Technical University, Tallinn, Estonia ABSTRACT There is long history of developing modelling systems
Domain Understanding and Requirements Elicitation
 and Requirements Elicitation CS/SE 3RA3 Ryszard Janicki Department of Computing and Software, McMaster University, Hamilton, Ontario, Canada Ryszard Janicki 1/24 Previous Lecture: The requirement engineering
and Requirements Elicitation CS/SE 3RA3 Ryszard Janicki Department of Computing and Software, McMaster University, Hamilton, Ontario, Canada Ryszard Janicki 1/24 Previous Lecture: The requirement engineering
Participatory backcasting: A tool for involving stakeholders in long term local development planning
 Erasmus Intensive Programme Equi Agry June 29 July 11, Foggia Participatory backcasting: A tool for involving stakeholders in long term local development planning Dr. Maurizio PROSPERI ( maurizio.prosperi@unifg.it
Erasmus Intensive Programme Equi Agry June 29 July 11, Foggia Participatory backcasting: A tool for involving stakeholders in long term local development planning Dr. Maurizio PROSPERI ( maurizio.prosperi@unifg.it
Designing for recovery New challenges for large-scale, complex IT systems
 Designing for recovery New challenges for large-scale, complex IT systems Prof. Ian Sommerville School of Computer Science St Andrews University Scotland St Andrews Small Scottish town, on the north-east
Designing for recovery New challenges for large-scale, complex IT systems Prof. Ian Sommerville School of Computer Science St Andrews University Scotland St Andrews Small Scottish town, on the north-east
Towards Integrated System and Software Modeling for Embedded Systems
 Towards Integrated System and Software Modeling for Embedded Systems Hassan Gomaa Department of Computer Science George Mason University, Fairfax, VA hgomaa@gmu.edu Abstract. This paper addresses the integration
Towards Integrated System and Software Modeling for Embedded Systems Hassan Gomaa Department of Computer Science George Mason University, Fairfax, VA hgomaa@gmu.edu Abstract. This paper addresses the integration
Design and Implementation Options for Digital Library Systems
 International Journal of Systems Science and Applied Mathematics 2017; 2(3): 70-74 http://www.sciencepublishinggroup.com/j/ijssam doi: 10.11648/j.ijssam.20170203.12 Design and Implementation Options for
International Journal of Systems Science and Applied Mathematics 2017; 2(3): 70-74 http://www.sciencepublishinggroup.com/j/ijssam doi: 10.11648/j.ijssam.20170203.12 Design and Implementation Options for
The AMADEOS SysML Profile for Cyber-physical Systems-of-Systems
 AMADEOS Architecture for Multi-criticality Agile Dependable Evolutionary Open System-of-Systems FP7-ICT-2013.3.4 - Grant Agreement n 610535 The AMADEOS SysML Profile for Cyber-physical Systems-of-Systems
AMADEOS Architecture for Multi-criticality Agile Dependable Evolutionary Open System-of-Systems FP7-ICT-2013.3.4 - Grant Agreement n 610535 The AMADEOS SysML Profile for Cyber-physical Systems-of-Systems
in the New Zealand Curriculum
 Technology in the New Zealand Curriculum We ve revised the Technology learning area to strengthen the positioning of digital technologies in the New Zealand Curriculum. The goal of this change is to ensure
Technology in the New Zealand Curriculum We ve revised the Technology learning area to strengthen the positioning of digital technologies in the New Zealand Curriculum. The goal of this change is to ensure
PACAS: A Gamified Platform for Participatory Change Management in ATM Systems
 PACAS: A Gamified Platform for Participatory Change Management in ATM Systems Elda Paja 1, Mauro Poggianella 1, Fatma Başak Aydemir 2, and Paolo Giorgini 1 1 University of Trento, Italy, elda.paja@unitn.it,
PACAS: A Gamified Platform for Participatory Change Management in ATM Systems Elda Paja 1, Mauro Poggianella 1, Fatma Başak Aydemir 2, and Paolo Giorgini 1 1 University of Trento, Italy, elda.paja@unitn.it,
Strategic Decision Support using Computerised Morphological Analysis
 9th International Command and Control Research and Technology Symposium Coalition Transformation: An Evolution of People, Processes and Technology to Enhance Interoperability Copenhagen, Denmark September
9th International Command and Control Research and Technology Symposium Coalition Transformation: An Evolution of People, Processes and Technology to Enhance Interoperability Copenhagen, Denmark September
The Next Step: A Fully Integrated Global Multi-Modal Security and Safety Management System. R. W. Fletcher, P. Eng., M. Sc.
 The Next Step: A Fully Integrated Global Multi-Modal Security and Safety Management System R. W. Fletcher, P. Eng., M. Sc., PMP, PCIP Keywords: system, security, safety, management, global, risk, hazard,
The Next Step: A Fully Integrated Global Multi-Modal Security and Safety Management System R. W. Fletcher, P. Eng., M. Sc., PMP, PCIP Keywords: system, security, safety, management, global, risk, hazard,
Catholijn M. Jonker and Jan Treur Vrije Universiteit Amsterdam, Department of Artificial Intelligence, Amsterdam, The Netherlands
 INTELLIGENT AGENTS Catholijn M. Jonker and Jan Treur Vrije Universiteit Amsterdam, Department of Artificial Intelligence, Amsterdam, The Netherlands Keywords: Intelligent agent, Website, Electronic Commerce
INTELLIGENT AGENTS Catholijn M. Jonker and Jan Treur Vrije Universiteit Amsterdam, Department of Artificial Intelligence, Amsterdam, The Netherlands Keywords: Intelligent agent, Website, Electronic Commerce
A Modelling Exercise
 Clayton Tunnel Disaster 1861 Modelling Complex Socio-Technical Systems 11-13 September 2013, Munich, Germany FRAM/iDEPEND Test David Slater - Cambrensis A Modelling Exercise 9/9/2013 FRAMILY 2013 2 1 Clayton
Clayton Tunnel Disaster 1861 Modelling Complex Socio-Technical Systems 11-13 September 2013, Munich, Germany FRAM/iDEPEND Test David Slater - Cambrensis A Modelling Exercise 9/9/2013 FRAMILY 2013 2 1 Clayton
Social Modeling for Requirements Engineering: An Introduction
 1 Social Modeling for Requirements Engineering: An Introduction Eric Yu, Paolo Giorgini, Neil Maiden, and John Mylopoulos Information technology can be used in innumerable ways and has great potential
1 Social Modeling for Requirements Engineering: An Introduction Eric Yu, Paolo Giorgini, Neil Maiden, and John Mylopoulos Information technology can be used in innumerable ways and has great potential
Meta-models, Environment and Layers: Agent-Oriented Engineering of Complex Systems
 Meta-models, Environment and Layers: Agent-Oriented Engineering of Complex Systems Ambra Molesini ambra.molesini@unibo.it DEIS Alma Mater Studiorum Università di Bologna Bologna, 07/04/2008 Ambra Molesini
Meta-models, Environment and Layers: Agent-Oriented Engineering of Complex Systems Ambra Molesini ambra.molesini@unibo.it DEIS Alma Mater Studiorum Università di Bologna Bologna, 07/04/2008 Ambra Molesini
SWEN 256 Software Process & Project Management
 SWEN 256 Software Process & Project Management What is quality? A definition of quality should emphasize three important points: 1. Software requirements are the foundation from which quality is measured.
SWEN 256 Software Process & Project Management What is quality? A definition of quality should emphasize three important points: 1. Software requirements are the foundation from which quality is measured.
Context Sensitive Interactive Systems Design: A Framework for Representation of contexts
 Context Sensitive Interactive Systems Design: A Framework for Representation of contexts Keiichi Sato Illinois Institute of Technology 350 N. LaSalle Street Chicago, Illinois 60610 USA sato@id.iit.edu
Context Sensitive Interactive Systems Design: A Framework for Representation of contexts Keiichi Sato Illinois Institute of Technology 350 N. LaSalle Street Chicago, Illinois 60610 USA sato@id.iit.edu
4 th European STAMP Workshop 2016
 4 th European STAMP Workshop 2016 STPA Tutorial - Part 1 Introduction Objectives and Content Overview 2 Objectives and Organization The goal of this tutorial is to give you an overview of STPA. Targeted
4 th European STAMP Workshop 2016 STPA Tutorial - Part 1 Introduction Objectives and Content Overview 2 Objectives and Organization The goal of this tutorial is to give you an overview of STPA. Targeted
School of Computing, National University of Singapore 3 Science Drive 2, Singapore ABSTRACT
 NUROP CONGRESS PAPER AGENT BASED SOFTWARE ENGINEERING METHODOLOGIES WONG KENG ONN 1 AND BIMLESH WADHWA 2 School of Computing, National University of Singapore 3 Science Drive 2, Singapore 117543 ABSTRACT
NUROP CONGRESS PAPER AGENT BASED SOFTWARE ENGINEERING METHODOLOGIES WONG KENG ONN 1 AND BIMLESH WADHWA 2 School of Computing, National University of Singapore 3 Science Drive 2, Singapore 117543 ABSTRACT
Applied Safety Science and Engineering Techniques (ASSET TM )
 Applied Safety Science and Engineering Techniques (ASSET TM ) The Evolution of Hazard Based Safety Engineering into the Framework of a Safety Management Process Applied Safety Science and Engineering Techniques
Applied Safety Science and Engineering Techniques (ASSET TM ) The Evolution of Hazard Based Safety Engineering into the Framework of a Safety Management Process Applied Safety Science and Engineering Techniques
Towards combined safety and security constraints analysis
 Towards combined safety and security constraints analysis Daniel Pereira 1, Celso Hirata 1, Rodrigo Pagliares 1,2, and Simin Nadjm-Tehrani 3 1 Instituto Tecnológico de Aeronáutica, SJ Campos 12228-900
Towards combined safety and security constraints analysis Daniel Pereira 1, Celso Hirata 1, Rodrigo Pagliares 1,2, and Simin Nadjm-Tehrani 3 1 Instituto Tecnológico de Aeronáutica, SJ Campos 12228-900
Outline. Outline. Assurance Cases: The Safety Case. Things I Like Safety-Critical Systems. Assurance Case Has To Be Right
 Assurance Cases: New Directions & New Opportunities* John C. Knight University of Virginia February, 2008 *Funded in part by: the National Science Foundation & NASA A summary of several research topics
Assurance Cases: New Directions & New Opportunities* John C. Knight University of Virginia February, 2008 *Funded in part by: the National Science Foundation & NASA A summary of several research topics
Pervasive Services Engineering for SOAs
 Pervasive Services Engineering for SOAs Dhaminda Abeywickrama (supervised by Sita Ramakrishnan) Clayton School of Information Technology, Monash University, Australia dhaminda.abeywickrama@infotech.monash.edu.au
Pervasive Services Engineering for SOAs Dhaminda Abeywickrama (supervised by Sita Ramakrishnan) Clayton School of Information Technology, Monash University, Australia dhaminda.abeywickrama@infotech.monash.edu.au
Patterns and their impact on system concerns
 Patterns and their impact on system concerns Michael Weiss Department of Systems and Computer Engineering Carleton University, Ottawa, Canada weiss@sce.carleton.ca Abstract Making the link between architectural
Patterns and their impact on system concerns Michael Weiss Department of Systems and Computer Engineering Carleton University, Ottawa, Canada weiss@sce.carleton.ca Abstract Making the link between architectural
Violent Intent Modeling System
 for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
Unit 5: Unified Software Development Process. 3C05: Unified Software Development Process USDP. USDP for your project. Iteration Workflows.
 Unit 5: Unified Software Development Process 3C05: Unified Software Development Process Objectives: Introduce the main concepts of iterative and incremental development Discuss the main USDP phases 1 2
Unit 5: Unified Software Development Process 3C05: Unified Software Development Process Objectives: Introduce the main concepts of iterative and incremental development Discuss the main USDP phases 1 2
The Human and Organizational Part of Nuclear Safety
 The Human and Organizational Part of Nuclear Safety International Atomic Energy Agency Safety is more than the technology The root causes Organizational & cultural root causes are consistently identified
The Human and Organizational Part of Nuclear Safety International Atomic Energy Agency Safety is more than the technology The root causes Organizational & cultural root causes are consistently identified
Co-evolution of agent-oriented conceptual models and CASO agent programs
 University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2006 Co-evolution of agent-oriented conceptual models and CASO agent programs
University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2006 Co-evolution of agent-oriented conceptual models and CASO agent programs
SAFETY CASE PATTERNS REUSING SUCCESSFUL ARGUMENTS. Tim Kelly, John McDermid
 SAFETY CASE PATTERNS REUSING SUCCESSFUL ARGUMENTS Tim Kelly, John McDermid Rolls-Royce Systems and Software Engineering University Technology Centre Department of Computer Science University of York Heslington
SAFETY CASE PATTERNS REUSING SUCCESSFUL ARGUMENTS Tim Kelly, John McDermid Rolls-Royce Systems and Software Engineering University Technology Centre Department of Computer Science University of York Heslington
Modeling Enterprise Systems
 Modeling Enterprise Systems A summary of current efforts for the SERC November 14 th, 2013 Michael Pennock, Ph.D. School of Systems and Enterprises Stevens Institute of Technology Acknowledgment This material
Modeling Enterprise Systems A summary of current efforts for the SERC November 14 th, 2013 Michael Pennock, Ph.D. School of Systems and Enterprises Stevens Institute of Technology Acknowledgment This material
2. CYBERSPACE Relevance to Sustainability? Critical Features Knowledge Aggregation and Facilitation Revolution Four Cases in the Middle East**
 ` 17.181/17.182 SUSTAINABLE DEVELOPMENT Week 4 Outline Cyberspace and Sustainability 1. ISSUES left over from WEEK 3 Brief Review Some Empirical Views 2. CYBERSPACE Relevance to Sustainability? Critical
` 17.181/17.182 SUSTAINABLE DEVELOPMENT Week 4 Outline Cyberspace and Sustainability 1. ISSUES left over from WEEK 3 Brief Review Some Empirical Views 2. CYBERSPACE Relevance to Sustainability? Critical
Towards a multi-view point safety contract Alejandra Ruiz 1, Tim Kelly 2, Huascar Espinoza 1
 Author manuscript, published in "SAFECOMP 2013 - Workshop SASSUR (Next Generation of System Assurance Approaches for Safety-Critical Systems) of the 32nd International Conference on Computer Safety, Reliability
Author manuscript, published in "SAFECOMP 2013 - Workshop SASSUR (Next Generation of System Assurance Approaches for Safety-Critical Systems) of the 32nd International Conference on Computer Safety, Reliability
Engineered Resilient Systems DoD Science and Technology Priority
 Engineered Resilient Systems DoD Science and Technology Priority Mr. Scott Lucero Deputy Director, Strategic Initiatives Office of the Deputy Assistant Secretary of Defense (Systems Engineering) Scott.Lucero@osd.mil
Engineered Resilient Systems DoD Science and Technology Priority Mr. Scott Lucero Deputy Director, Strategic Initiatives Office of the Deputy Assistant Secretary of Defense (Systems Engineering) Scott.Lucero@osd.mil
Introduction to Bowtie Methodology for a Laboratory Setting
 Introduction to Bowtie Methodology for a Laboratory Setting ACS 251st National Meeting Division of Chemical Health and Safety Developing, Implementing & Teaching Hazard Assessment Tools Mary Beth Mulcahy,
Introduction to Bowtie Methodology for a Laboratory Setting ACS 251st National Meeting Division of Chemical Health and Safety Developing, Implementing & Teaching Hazard Assessment Tools Mary Beth Mulcahy,
GOALS TO ASPECTS: DISCOVERING ASPECTS ORIENTED REQUIREMENTS
 GOALS TO ASPECTS: DISCOVERING ASPECTS ORIENTED REQUIREMENTS 1 A. SOUJANYA, 2 SIDDHARTHA GHOSH 1 M.Tech Student, Department of CSE, Keshav Memorial Institute of Technology(KMIT), Narayanaguda, Himayathnagar,
GOALS TO ASPECTS: DISCOVERING ASPECTS ORIENTED REQUIREMENTS 1 A. SOUJANYA, 2 SIDDHARTHA GHOSH 1 M.Tech Student, Department of CSE, Keshav Memorial Institute of Technology(KMIT), Narayanaguda, Himayathnagar,
Week 2 Class Notes 1
 Week 2 Class Notes 1 Plan for Today Accident Models Introduction to Systems Thinking STAMP: A new loss causality model 2 Accident Causality Models Underlie all our efforts to engineer for safety Explain
Week 2 Class Notes 1 Plan for Today Accident Models Introduction to Systems Thinking STAMP: A new loss causality model 2 Accident Causality Models Underlie all our efforts to engineer for safety Explain
Introduction to Systems Engineering
 p. 1/2 ENES 489P Hands-On Systems Engineering Projects Introduction to Systems Engineering Mark Austin E-mail: austin@isr.umd.edu Institute for Systems Research, University of Maryland, College Park Career
p. 1/2 ENES 489P Hands-On Systems Engineering Projects Introduction to Systems Engineering Mark Austin E-mail: austin@isr.umd.edu Institute for Systems Research, University of Maryland, College Park Career
An Introduction to a Taxonomy of Information Privacy in Collaborative Environments
 An Introduction to a Taxonomy of Information Privacy in Collaborative Environments GEOFF SKINNER, SONG HAN, and ELIZABETH CHANG Centre for Extended Enterprises and Business Intelligence Curtin University
An Introduction to a Taxonomy of Information Privacy in Collaborative Environments GEOFF SKINNER, SONG HAN, and ELIZABETH CHANG Centre for Extended Enterprises and Business Intelligence Curtin University
Scoping Paper for. Horizon 2020 work programme Societal Challenge 4: Smart, Green and Integrated Transport
 Scoping Paper for Horizon 2020 work programme 2018-2020 Societal Challenge 4: Smart, Green and Integrated Transport Important Notice: Working Document This scoping paper will guide the preparation of the
Scoping Paper for Horizon 2020 work programme 2018-2020 Societal Challenge 4: Smart, Green and Integrated Transport Important Notice: Working Document This scoping paper will guide the preparation of the
Using Dynamic Capability Evaluation to Organize a Team of Cooperative, Autonomous Robots
 Using Dynamic Capability Evaluation to Organize a Team of Cooperative, Autonomous Robots Eric Matson Scott DeLoach Multi-agent and Cooperative Robotics Laboratory Department of Computing and Information
Using Dynamic Capability Evaluation to Organize a Team of Cooperative, Autonomous Robots Eric Matson Scott DeLoach Multi-agent and Cooperative Robotics Laboratory Department of Computing and Information
Information Sociology
 Information Sociology Educational Objectives: 1. To nurture qualified experts in the information society; 2. To widen a sociological global perspective;. To foster community leaders based on Christianity.
Information Sociology Educational Objectives: 1. To nurture qualified experts in the information society; 2. To widen a sociological global perspective;. To foster community leaders based on Christianity.
Performance Evaluation of MANET Using Quality of Service Metrics
 Performance Evaluation of MANET Using Quality of Service Metrics C.Jinshong Hwang 1, Ashwani Kush 2, Ruchika,S.Tyagi 3 1 Department of Computer Science Texas State University, San Marcos Texas, USA 2,
Performance Evaluation of MANET Using Quality of Service Metrics C.Jinshong Hwang 1, Ashwani Kush 2, Ruchika,S.Tyagi 3 1 Department of Computer Science Texas State University, San Marcos Texas, USA 2,
Software Maintenance Cycles with the RUP
 Software Maintenance Cycles with the RUP by Philippe Kruchten Rational Fellow Rational Software Canada The Rational Unified Process (RUP ) has no concept of a "maintenance phase." Some people claim that
Software Maintenance Cycles with the RUP by Philippe Kruchten Rational Fellow Rational Software Canada The Rational Unified Process (RUP ) has no concept of a "maintenance phase." Some people claim that
Design Rationale as an Enabling Factor for Concurrent Process Engineering
 612 Rafael Batres, Atsushi Aoyama, and Yuji NAKA Design Rationale as an Enabling Factor for Concurrent Process Engineering Rafael Batres, Atsushi Aoyama, and Yuji NAKA Tokyo Institute of Technology, Yokohama
612 Rafael Batres, Atsushi Aoyama, and Yuji NAKA Design Rationale as an Enabling Factor for Concurrent Process Engineering Rafael Batres, Atsushi Aoyama, and Yuji NAKA Tokyo Institute of Technology, Yokohama
UMLEmb: UML for Embedded Systems. II. Modeling in SysML. Eurecom
 UMLEmb: UML for Embedded Systems II. Modeling in SysML Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Eurecom, office 470 http://soc.eurecom.fr/umlemb/ @UMLEmb Eurecom Goals Learning objective
UMLEmb: UML for Embedded Systems II. Modeling in SysML Ludovic Apvrille ludovic.apvrille@telecom-paristech.fr Eurecom, office 470 http://soc.eurecom.fr/umlemb/ @UMLEmb Eurecom Goals Learning objective
INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN ICED 03 STOCKHOLM, AUGUST 19-21, 2003
 INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN ICED 03 STOCKHOLM, AUGUST 19-21, 2003 A KNOWLEDGE MANAGEMENT SYSTEM FOR INDUSTRIAL DESIGN RESEARCH PROCESSES Christian FRANK, Mickaël GARDONI Abstract Knowledge
INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN ICED 03 STOCKHOLM, AUGUST 19-21, 2003 A KNOWLEDGE MANAGEMENT SYSTEM FOR INDUSTRIAL DESIGN RESEARCH PROCESSES Christian FRANK, Mickaël GARDONI Abstract Knowledge
Reconsidering the Role of Systems Engineering in DoD Software Problems
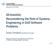 Pittsburgh, PA 15213-3890 SIS Acquisition Reconsidering the Role of Systems Engineering in DoD Software Problems Grady Campbell (ghc@sei.cmu.edu) Sponsored by the U.S. Department of Defense 2004 by Carnegie
Pittsburgh, PA 15213-3890 SIS Acquisition Reconsidering the Role of Systems Engineering in DoD Software Problems Grady Campbell (ghc@sei.cmu.edu) Sponsored by the U.S. Department of Defense 2004 by Carnegie
SOFTWARE ARCHITECTURE
 SOFTWARE ARCHITECTURE Foundations, Theory, and Practice Richard N. Taylor University of California, Irvine Nenad Medvidovic University of Southern California Eric M. Dashofy The Aerospace Corporation WILEY
SOFTWARE ARCHITECTURE Foundations, Theory, and Practice Richard N. Taylor University of California, Irvine Nenad Medvidovic University of Southern California Eric M. Dashofy The Aerospace Corporation WILEY
Apply Functional Modelling to Consequence Analysis in Supervision Systems. Abstract
 Template EHPG_paper version 8 2011-08-04 Apply Functional Modelling to Consequence Analysis in Supervision Systems Xinxin Zhang 1, Morten Lind 2, Giulio Gola 3, and Ole Ravn 4 1,2,4 Technical University
Template EHPG_paper version 8 2011-08-04 Apply Functional Modelling to Consequence Analysis in Supervision Systems Xinxin Zhang 1, Morten Lind 2, Giulio Gola 3, and Ole Ravn 4 1,2,4 Technical University
Project BONUS ESABALT
 Project BONUS ESABALT Economic and Non-Economic Feasibility Analysis dr Paweł Banaś Maritime University of Szczecin Content Assumptions 1. Analysis of navigational systems and devices 2. Expected ESABALT
Project BONUS ESABALT Economic and Non-Economic Feasibility Analysis dr Paweł Banaś Maritime University of Szczecin Content Assumptions 1. Analysis of navigational systems and devices 2. Expected ESABALT
THE AXIOMATIC APPROACH IN THE UNIVERSAL DESIGN THEORY
 THE AXIOMATIC APPROACH IN THE UNIVERSAL DESIGN THEORY Dr.-Ing. Ralf Lossack lossack@rpk.mach.uni-karlsruhe.de o. Prof. Dr.-Ing. Dr. h.c. H. Grabowski gr@rpk.mach.uni-karlsruhe.de University of Karlsruhe
THE AXIOMATIC APPROACH IN THE UNIVERSAL DESIGN THEORY Dr.-Ing. Ralf Lossack lossack@rpk.mach.uni-karlsruhe.de o. Prof. Dr.-Ing. Dr. h.c. H. Grabowski gr@rpk.mach.uni-karlsruhe.de University of Karlsruhe
A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE
 A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE Expert 1A Dan GROSU Executive Agency for Higher Education and Research Funding Abstract The paper presents issues related to a systemic
A SYSTEMIC APPROACH TO KNOWLEDGE SOCIETY FORESIGHT. THE ROMANIAN CASE Expert 1A Dan GROSU Executive Agency for Higher Education and Research Funding Abstract The paper presents issues related to a systemic
Introduction. Requirements Engineering: Why RE? What is RE? How to do RE? -> RE Processes. Why RE in SysE? Case Studies and The Standish Report
 Requirements Engineering: Why RE? Introduction Why RE in SysE? Software Lifecycle and Error Propagation Case Studies and The Standish Report What is RE? Role of Requirements How to do RE? -> RE Processes
Requirements Engineering: Why RE? Introduction Why RE in SysE? Software Lifecycle and Error Propagation Case Studies and The Standish Report What is RE? Role of Requirements How to do RE? -> RE Processes
WORKSHOP ON BASIC RESEARCH: POLICY RELEVANT DEFINITIONS AND MEASUREMENT ISSUES PAPER. Holmenkollen Park Hotel, Oslo, Norway October 2001
 WORKSHOP ON BASIC RESEARCH: POLICY RELEVANT DEFINITIONS AND MEASUREMENT ISSUES PAPER Holmenkollen Park Hotel, Oslo, Norway 29-30 October 2001 Background 1. In their conclusions to the CSTP (Committee for
WORKSHOP ON BASIC RESEARCH: POLICY RELEVANT DEFINITIONS AND MEASUREMENT ISSUES PAPER Holmenkollen Park Hotel, Oslo, Norway 29-30 October 2001 Background 1. In their conclusions to the CSTP (Committee for
Software LEIC/LETI. Lecture 21
 Software Engineering @ LEIC/LETI Lecture 21 Last Lecture Offline concurrency patterns (continuation) Object-relational behavioral patterns Session state patterns Presentation logic Services Domain logic
Software Engineering @ LEIC/LETI Lecture 21 Last Lecture Offline concurrency patterns (continuation) Object-relational behavioral patterns Session state patterns Presentation logic Services Domain logic
Assessing the Welfare of Farm Animals
 Assessing the Welfare of Farm Animals Part 1. Part 2. Review Development and Implementation of a Unified field Index (UFI) February 2013 Drewe Ferguson 1, Ian Colditz 1, Teresa Collins 2, Lindsay Matthews
Assessing the Welfare of Farm Animals Part 1. Part 2. Review Development and Implementation of a Unified field Index (UFI) February 2013 Drewe Ferguson 1, Ian Colditz 1, Teresa Collins 2, Lindsay Matthews
Cyber-Physical Systems: Challenges for Systems Engineering
 Cyber-Physical Systems: Challenges for Systems Engineering agendacps Closing Event April 12th, 2012, EIT ICT Labs, Berlin Eva Geisberger fortiss An-Institut der Technischen Universität München Cyber-Physical
Cyber-Physical Systems: Challenges for Systems Engineering agendacps Closing Event April 12th, 2012, EIT ICT Labs, Berlin Eva Geisberger fortiss An-Institut der Technischen Universität München Cyber-Physical
