2/15/2017 3:56 PM KEYNOTE ADDRESS
|
|
|
- Owen Freeman
- 5 years ago
- Views:
Transcription
1 KEYNOTE ADDRESS THE DIGITAL FOREVERMORE Thomas J. Ridge * We now live in what I call the digital forevermore. It was not that long ago that the original computer base data transmission protocol was created simply to facilitate telecommunications between the United States Department of Defense and research universities. While certainly primitive compared to the digital global ecosystem that drives commerce and culture throughout the world today, its core features remain the same. The Internet is an open system based on anonymity. It was never designed to be a secure communication platform. The opportunities and vulnerabilities within this global network, with electrons racing everywhere, much of it with personal information about all of us, are probably beyond our individual comprehension. The ubiquity of the Internet is its strength, and the ubiquity of the Internet is its weakness. And we are all potentially exposed to the potential malignant use of the Internet and the nefarious use of our information that is on it. I say to friends, lawyers, or non-lawyers, all of us have a role and a need to combat its improper use. Its misuse, even potentially by our own government, is a clear and, I think, ever-present danger. We can never take for granted that our government, acting on its own, has the capability to protect us from its destruc- * Secretary of the Department of Homeland Security, This speech was delivered by Thomas J. Ridge at the 2016 University of Richmond Law Review Symposium, National Security in the Information Age: Are We Heading Towards Big Brother, on October 28, 2016, at the University of Richmond School of Law. 665
2 666 UNIVERSITY OF RICHMOND LAW REVIEW [Vol. 51:665 tive use. All of us interact with the Internet as users, consumers, and citizens. Most of us are unaware of the total amount of personal information the government and the commercial sector have about us. We know the Chinese have the profiles of 22 million Americans after the Office of Personnel Management breach (in 2015), including mine. We were required to provide that information to government to serve our country. Understandable. But add on top of that a layer of information that those 22 million and, I might add, all of you voluntarily surrender. Do you have the slightest idea of the depth and breadth of information they have about you? I would dare say not, and I say this respectfully. On that click consent, when you agree to the terms of service and privacy statement, how many of you have thoroughly read it and understand its implications? Do not raise your hand because you will be like the lone ranger, probably. It is not a criticism. I plead guilty. When you automatically, and I think without hesitation, hit the click consent to the terms of service and privacy policy, you probably empower the ISP the right to accumulate and sell the following: things you search, websites you visit, videos you watch, ads you click on, your location information, IP address, and cookie data, and I suspect some missing other elements which could probably be described as data exhaust. Do you think that click consent, law students, is tantamount to informed consent? Interesting question, isn t it? Could you function without ISP platforms in your personal or professional life? Let us not forget the information citizens share with organizations with whom they are associated, telecommunication companies, financial firms, health care providers a pretty long list. Much of it is mandated, and unprecedented levels are volunteered and, yes, some surreptitiously acquired. Now, I rarely applaud the United Nations, and particularly the United Nations Human Rights Council, but I have to admit it addressed the issue of privacy several years ago when it affirmed for the first time that human rights in the digital realm should be afforded the same protection as human rights in the physical world. One of the participants in the council meeting, Ambassador Hans
3 2017] THE DIGITAL FOREVERMORE 667 Schumacher of Germany, observed, Every person is entitled to a private sphere, free from undue interference or surveillance by the state or by other actors. He urged the global community to strike a balance between legitimate public security concerns and the fundamental right to privacy in the digital age. We all know there are UN members who do not share that point of view. I happened to be in China talking about cybersecurity about a year and a half ago, and I assure you, they do not share that. But the United States does, and must, if our democracy is to remain the strongest and most respected expression of self-government in the world. The relationship between countries and their citizens on this matter varies dramatically. Rarely is there complete transparency of the government s role. Governments, for legitimate reasons, have access to and retain personal information about its citizens. But with the advent of Facebook, Twitter, LinkedIn, and so many social media alternatives, citizens living in the modern world surrender information about themselves with astonishing regularity and without hesitation. Think about this a moment: Devices used by the population every day can be used to determine where you are; you do have a GPS-enabled iphone or ipad, don t you? Or what you are thinking let us see what website you just clicked on. We take it for granted. It says a lot about each and every one of us. Some or all of this information can be collected, sorted, analyzed, and used to profile and target individuals and groups through the digital networks for economic, social, national security, even political reasons. It is all out there, available for use or abuse. The embrace of all that is digital which means all that is accessible may suggest that we Americans do not cherish our privacy. Be assured, we do. We must. Preserving our civil liberties and privacy was clearly a concern of the administration and Congress. In response to the attack of 9/11, the Department of Homeland Security was created and the first-ever congressionally mandated privacy office was included. The country believed then, it believes now, that no matter how effective the technology might be to identify terrorists before they strike a worthy, laudable, and essential goal no matter how grave the threat may be, pre-
4 668 UNIVERSITY OF RICHMOND LAW REVIEW [Vol. 51:665 serving civil liberties is itself an essential part of protecting the homeland. The privacy office was built to look carefully at what was collected, how it should be stored, whether or not it could be collated, whether it contained personally identifiable information, how long the data could be held, and finally for what purpose it should be made available to the government. In 2004, on the recommendation of the 9/11 Commission, a privacy and civil liberties oversight board was created and housed in the executive branch. Listen carefully to the following: Although President Bush submitted four names in 2008, the Senate took no action. President Obama made several nominations in 2010, but it took until August of 2012 for Congress to confirm them. This may surprise or it may disappoint you, but it was only earlier this year that a highly regarded technology adviser became part of that indispensable team. This short history is troubling and very revealing. If we rely exclusively on government to monitor the use of technology and its impact on our privacy, I say, respectfully, our faith will be somewhat misplaced. Attempts to create permanent and rigorous oversight capabilities within the government have certainly been well-intentioned, but that limited track record says they are feeble at best. We can only hope they improve. We must remind ourselves that technology moves more quickly than government. Then again, so do icebergs. I recently read that the amount of stored information grows four times faster than the economy, while the processing power of computers has grown nine times faster. Authors Viktor Mayer- Schönberger and Kenneth Cukier concluded, The real revolution is not in the machines, but in the data itself and how we use it. The analysis that big data has and will contribute to more efficient manufacturing, more productive agriculture, improved health care, safer transportation, a cleaner environment the actual potential benefits are almost limitless. We should and can celebrate the positives, but we cannot ignore the negative. The benefits are derived, in many instances, from using complicated math algorithms to make predictions.
5 2017] THE DIGITAL FOREVERMORE 669 When the analysis involves personal information and the possibility or probability of certain actions or certain kinds of behavior, I think government and society must proceed with caution. Let me share with you both a personal example of predictive analysis and the concerns that I think we legitimately need to pay attention to. I gave a graduation speech at another law school, and one of the students who was the daughter of a friend of mine gave me four unidentified, untitled books as a present. Imagine that. It is an interesting gift certificate. I was asked to provide basic personal information about myself and then express on one sheet of paper, fill-in-the-blanks, a couple questions my literary tastes and the kinds of things that interest me. I have got a pretty wide range, so I put most of them down there. The algorithm used by the company to select these books was amazingly and I must admit, uncomfortably accurate. They may not have been on my choices walking through Barnes & Noble, but the computer made superb choices for me. It does not take too great an imagination to foresee the potential abuse of personal information and predictive analysis if the capability is in the wrong hands. That capability exists in our world today. We need not take a leap of faith into the future when government s misuse of its access to big data surveillance cameras, sensors, supercomputers initially designed and offered to protect us from terrorist attacks is used to undermine our democracy. There must be rules circumscribing who has access to the data and how it is used. In the information age, pieces of digital DNA, our digital soul, are scattered everywhere. We must be vigilant that government never gathers the information that subjects us to the tyranny of the algorithm. As you are aware, at least the law students here are aware, there is a series of Supreme Court opinions that affirm the notion that a person has no legitimate expectation of privacy in information he voluntarily turns over to third parties. Third party doctrine. I personally think it is time for policymakers to reconsider that notion. I think that blanket approach is ill-suited in the digital forevermore. I believe citizens should be able to control the use of their own personal information in the cyber age.
6 670 UNIVERSITY OF RICHMOND LAW REVIEW [Vol. 51:665 I think that is worthy of a national discussion that should include the tech giants of our world. They are the ones that gather the information, sell it, and have access to it through all sorts of captive audience. The belief that the most effective means of protecting our privacy and civil liberties is controlling the collection and storage of data is both obsolete and impossible. I have read estimates from 50 billion to 70 billion devices will be hooked on the Internet by I have no idea how that translates into the data that is going to be available. No idea. Nobody does. We are not going to put the data genie back in the bottle. It is exploding exponentially in the digital forevermore. It will continue to do so. Limiting government s reach into the private domain of the citizen will be a permanent challenge in this digitally engaged, digitally promising, and potentially digitally dangerous world. Technology must surely be an instrument of government to combat threats regardless of their nature. Technology can never be a weapon against its citizens. As we combat radical terrorism, as we confront social and political unrest, as we fight the never-ending battle against crime, there will be in the digital forevermore a permanent tension between safety, security, and privacy. Given the gigabytes of information that exist about people, places, and things, the surveillance and sensor systems that become more embedded in our community and our daily lives, we have to be mindful of not only the enabling use but the potential for misuse. Here is where I strongly believe the professional and private voices of the legal profession must be heard. And I suspect, when you graduate from the University of Richmond Law School, you will be prepared to raise those voices. When it comes to protection of our privacy, I also hope and expect, in a certain prayerful way, that you do.
Internet 2020: The Next Billion Users
 Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Internet 2020: The Next Billion Users Lawrence E. Strickling I. INTRODUCTION I am honored to have the opportunity to preface this edition of CommLaw Conspectus and discuss the Internet policy priorities
Executive Summary Industry s Responsibility in Promoting Responsible Development and Use:
 Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
RAW FILE ITU MAY 15, 2018 LUNCH BREAK AND DEMO STAGE ****** This text, document, or file is based on live transcription.
 1 RAW FILE Services provided by: Caption First, Inc. P.O. Box 3066 Monument, CO 80132 800-825-5234 www.captionfirst.com ITU MAY 15, 2018 LUNCH BREAK AND DEMO STAGE ****** This text, document, or file is
1 RAW FILE Services provided by: Caption First, Inc. P.O. Box 3066 Monument, CO 80132 800-825-5234 www.captionfirst.com ITU MAY 15, 2018 LUNCH BREAK AND DEMO STAGE ****** This text, document, or file is
Violent Intent Modeling System
 for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
for the Violent Intent Modeling System April 25, 2008 Contact Point Dr. Jennifer O Connor Science Advisor, Human Factors Division Science and Technology Directorate Department of Homeland Security 202.254.6716
Personal Data Protection Competency Framework for School Students. Intended to help Educators
 Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
Conférence INTERNATIONAL internationale CONFERENCE des OF PRIVACY commissaires AND DATA à la protection PROTECTION des données COMMISSIONERS et à la vie privée Personal Data Protection Competency Framework
Towards a Magna Carta for Data
 Towards a Magna Carta for Data Expert Opinion Piece: Engineering and Computer Science Committee February 2017 Expert Opinion Piece: Engineering and Computer Science Committee Context Big Data is a frontier
Towards a Magna Carta for Data Expert Opinion Piece: Engineering and Computer Science Committee February 2017 Expert Opinion Piece: Engineering and Computer Science Committee Context Big Data is a frontier
Surveillance and Privacy in the Information Age. Image courtesy of Josh Bancroft on flickr. License CC-BY-NC.
 Surveillance and Privacy in the Information Age Image courtesy of Josh Bancroft on flickr. License CC-BY-NC. 1 Basic attributes (Kitchin, 2014) High-volume High-velocity High-variety Exhaustivity (n=all)
Surveillance and Privacy in the Information Age Image courtesy of Josh Bancroft on flickr. License CC-BY-NC. 1 Basic attributes (Kitchin, 2014) High-volume High-velocity High-variety Exhaustivity (n=all)
Section 1: Internet Governance Principles
 Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
Internet Governance Principles and Roadmap for the Further Evolution of the Internet Governance Ecosystem Submission to the NetMundial Global Meeting on the Future of Internet Governance Sao Paolo, Brazil,
ICC POSITION ON LEGITIMATE INTERESTS
 ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
ICC POSITION ON LEGITIMATE INTERESTS POLICY STATEMENT Prepared by the ICC Commission on the Digital Economy Summary and highlights This statement outlines the International Chamber of Commerce s (ICC)
Building DIGITAL TRUST People s Plan for Digital: A discussion paper
 Building DIGITAL TRUST People s Plan for Digital: A discussion paper We want Britain to be the world s most advanced digital society. But that won t happen unless the digital world is a world of trust.
Building DIGITAL TRUST People s Plan for Digital: A discussion paper We want Britain to be the world s most advanced digital society. But that won t happen unless the digital world is a world of trust.
Raising your Profile
 Raising your Profile RAISE YOUR OWN PROFILE You are your own Chief Marketing Officer, go sell Tom Peters From a cultural perspective we are not taught to sing our own praises or talk about our successes.
Raising your Profile RAISE YOUR OWN PROFILE You are your own Chief Marketing Officer, go sell Tom Peters From a cultural perspective we are not taught to sing our own praises or talk about our successes.
Our position. ICDPPC declaration on ethics and data protection in artificial intelligence
 ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
RSAC Podcast Transcript Episode 3: You Cannot Have Privacy Without Security TREVOR HUGHES & ART COVIELLO, APRIL 7, 2016
 StoryCorps @ RSAC Podcast Transcript Episode 3: You Cannot Have Privacy Without Security TREVOR HUGHES & ART COVIELLO, APRIL 7, 2016 NARRATOR: Welcome to the RSA Conference 2016 StoryCorps podcasts. Please
StoryCorps @ RSAC Podcast Transcript Episode 3: You Cannot Have Privacy Without Security TREVOR HUGHES & ART COVIELLO, APRIL 7, 2016 NARRATOR: Welcome to the RSA Conference 2016 StoryCorps podcasts. Please
Warning a client of risks 1/2
 Legal English Warning a client of risks 1/2 Let me caution you that in this jurisdiction the fines can be very high for this sort of activity. I must warn you that individuals directly involved in serious
Legal English Warning a client of risks 1/2 Let me caution you that in this jurisdiction the fines can be very high for this sort of activity. I must warn you that individuals directly involved in serious
Report to Congress regarding the Terrorism Information Awareness Program
 Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
Report to Congress regarding the Terrorism Information Awareness Program In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, 111(b) Executive Summary May 20, 2003
(Beijing, China,25 May2017)
 Remarks by the Secretary General of the International Civil Aviation Organization (ICAO), Dr. Fang Liu, to the First Session of the 2017 China Civil Aviation Development Forum: New Opportunities for Aviation
Remarks by the Secretary General of the International Civil Aviation Organization (ICAO), Dr. Fang Liu, to the First Session of the 2017 China Civil Aviation Development Forum: New Opportunities for Aviation
TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV
 Tech EUROPE TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV Brussels, 14 January 2014 TechAmerica Europe represents
Tech EUROPE TechAmerica Europe comments for DAPIX on Pseudonymous Data and Profiling as per 19/12/2013 paper on Specific Issues of Chapters I-IV Brussels, 14 January 2014 TechAmerica Europe represents
Computers, Privacy & Data Protection 2015 Data Protection on the Move Brussels, 23 January 2015
 Computers, Privacy & Data Protection 2015 Data Protection on the Move Brussels, 23 January 2015 Giovanni Buttarelli European Data Protection Supervisor Concluding remarks Ladies and gentlemen, It s my
Computers, Privacy & Data Protection 2015 Data Protection on the Move Brussels, 23 January 2015 Giovanni Buttarelli European Data Protection Supervisor Concluding remarks Ladies and gentlemen, It s my
Children s rights in the digital environment: Challenges, tensions and opportunities
 Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Children s rights in the digital environment: Challenges, tensions and opportunities Presentation to the Conference on the Council of Europe Strategy for the Rights of the Child (2016-2021) Sofia, 6 April
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA Health Insurance Portability and Accountability Act (HIPAA)
 Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
Diana Gordick, Ph.D. 150 E Ponce de Leon, Suite 350 Decatur, GA 30030 Health Insurance Portability and Accountability Act (HIPAA) NOTICE OF PRIVACY PRACTICES I. COMMITMENT TO YOUR PRIVACY: DIANA GORDICK,
Future of Financing. For more information visit ifrc.org/s2030
 Future of Financing The gap between humanitarian and development needs and financing is growing, yet largely we still rely on just a few traditional sources of funding. How do we mobilize alternate sources
Future of Financing The gap between humanitarian and development needs and financing is growing, yet largely we still rely on just a few traditional sources of funding. How do we mobilize alternate sources
The Internet of Things And what it mean for librarians
 The Internet of Things And what it mean for librarians Lee Rainie Pew Research Center Internet Project Presented to: Internet Librarian October 28, 2014 Oxford English Dictionary Internet of things: Development
The Internet of Things And what it mean for librarians Lee Rainie Pew Research Center Internet Project Presented to: Internet Librarian October 28, 2014 Oxford English Dictionary Internet of things: Development
Federal Trade Commission Address. Delivered 12 January 2015, Constitution Center, Washington, D.C.
 Barack Obama Federal Trade Commission Address Delivered 12 January 2015, Constitution Center, Washington, D.C. AUTHENTICITY CERTIFIED: Text version below transcribed directly from audio Thank you so much.
Barack Obama Federal Trade Commission Address Delivered 12 January 2015, Constitution Center, Washington, D.C. AUTHENTICITY CERTIFIED: Text version below transcribed directly from audio Thank you so much.
Congress doesn t know how Facebook works and other things we learned from Mark Zuckerberg s testimony
 Congress doesn t know how Facebook works and other things we learned from Mark Zuckerberg s testimony Zuckerberg survived Washington but what is Washington going to do about Facebook? By Kurt Wagner Apr
Congress doesn t know how Facebook works and other things we learned from Mark Zuckerberg s testimony Zuckerberg survived Washington but what is Washington going to do about Facebook? By Kurt Wagner Apr
NATIONAL TOURISM CONFERENCE 2018
 NATIONAL TOURISM CONFERENCE 2018 POSITIONING CURAÇAO AS A SMART TOURISM DESTINATION KEYNOTE ADDRESS by Mr. Franklin Sluis CEO Bureau Telecommunication, Post & Utilities Secretariat Taskforce Smart Nation
NATIONAL TOURISM CONFERENCE 2018 POSITIONING CURAÇAO AS A SMART TOURISM DESTINATION KEYNOTE ADDRESS by Mr. Franklin Sluis CEO Bureau Telecommunication, Post & Utilities Secretariat Taskforce Smart Nation
November 2, 2009 FILED ELECTRONICALLY
 November 2, 2009 FILED ELECTRONICALLY Mr. Robert A. Morin Secretary General Canadian Radio-television and Telecommunications Commission Les Terrasses de la Chaudière Central Building 1 Promenade du Portage
November 2, 2009 FILED ELECTRONICALLY Mr. Robert A. Morin Secretary General Canadian Radio-television and Telecommunications Commission Les Terrasses de la Chaudière Central Building 1 Promenade du Portage
IN THE MATTER OF THE ANTI-CONTERFEITING TRADE AGREEMENT. Docket No.: USTR COMMENTS OF PUBLIC KNOWLEDGE
 IN THE MATTER OF THE ANTI-CONTERFEITING TRADE AGREEMENT Docket No.: USTR-2010-0014 Introduction COMMENTS OF PUBLIC KNOWLEDGE Public Knowledge submits these comments in the above-mentioned docket. As the
IN THE MATTER OF THE ANTI-CONTERFEITING TRADE AGREEMENT Docket No.: USTR-2010-0014 Introduction COMMENTS OF PUBLIC KNOWLEDGE Public Knowledge submits these comments in the above-mentioned docket. As the
Voters Attitudes toward Science and Technology Research and the Role of the Federal Government
 Voters Attitudes toward Science and Technology Research and the Role of the Federal Government Key findings from online national survey among 1,500 registered voters conducted September 28 to October 8,
Voters Attitudes toward Science and Technology Research and the Role of the Federal Government Key findings from online national survey among 1,500 registered voters conducted September 28 to October 8,
Executive Summary. The process. Intended use
 ASIS Scouting the Future Summary: Terror attacks, data breaches, ransomware there is constant need for security, but the form it takes is evolving in the face of new technological capabilities and social
ASIS Scouting the Future Summary: Terror attacks, data breaches, ransomware there is constant need for security, but the form it takes is evolving in the face of new technological capabilities and social
Two Presidents, Two Parties, Two Times, One Challenge
 Two Presidents, Two Parties, Two Times, One Challenge David D. Thornburg, PhD Executive Director, Thornburg Center for Space Exploration dthornburg@aol.com www.tcse-k12.org Dwight Eisenhower and Barack
Two Presidents, Two Parties, Two Times, One Challenge David D. Thornburg, PhD Executive Director, Thornburg Center for Space Exploration dthornburg@aol.com www.tcse-k12.org Dwight Eisenhower and Barack
Lesson 2: What is the Mary Kay Way?
 Lesson 2: What is the Mary Kay Way? This lesson focuses on the Mary Kay way of doing business, specifically: The way Mary Kay, the woman, might have worked her business today if she were an Independent
Lesson 2: What is the Mary Kay Way? This lesson focuses on the Mary Kay way of doing business, specifically: The way Mary Kay, the woman, might have worked her business today if she were an Independent
Big Data & AI Governance: The Laws and Ethics
 Institute of Big Data Governance (IBDG): Inauguration-cum-Digital Economy and Big Data Governance Symposium 5 December 2018 InnoCentre, Kowloon Tong Big Data & AI Governance: The Laws and Ethics Stephen
Institute of Big Data Governance (IBDG): Inauguration-cum-Digital Economy and Big Data Governance Symposium 5 December 2018 InnoCentre, Kowloon Tong Big Data & AI Governance: The Laws and Ethics Stephen
Scenario Development Process
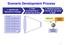 Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
Scenario Development Process 1. Identify Key Elements of Change 2. Filter uncertainties to identify key drivers 3. Develop scenario stories for the world in 2020 Key Uncertainties Text about uncertainties;
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION
 28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
28 TH INTERNATIONAL CONFERENCE OF DATA PROTECTION AND PRIVACY COMMISSIONERS 2 ND & 3 RD NOVEMBER 2006 LONDON, UNITED KINGDOM CLOSING COMMUNIQUÉ The 28 th International Conference of Data Protection and
5. Why does the government need this information?
 U.S. Data Collection Fact Sheet (CNN) -- Government surveillance of telephone records and conversations in the name of national security is a controversial topic that goes back decades. Recently there
U.S. Data Collection Fact Sheet (CNN) -- Government surveillance of telephone records and conversations in the name of national security is a controversial topic that goes back decades. Recently there
April 21, By to:
 April 21, 2017 Mr. Qiu Yang Office of the Anti-Monopoly Commission Of the State Council of the People s Republic of China No. 2 East Chang an Avenue, Beijing P.R. China 100731 By Email to: qiuyang@mofcom.gov.cn
April 21, 2017 Mr. Qiu Yang Office of the Anti-Monopoly Commission Of the State Council of the People s Republic of China No. 2 East Chang an Avenue, Beijing P.R. China 100731 By Email to: qiuyang@mofcom.gov.cn
Frequently Asked Questions for the Pathway to Chartership
 Frequently Asked Questions for the Pathway to Chartership Index Answers for everyone... 2 What is the pathway?... 2 How does the pathway work?... 2 How do I register... 3 What is a Mentor... 3 Does my
Frequently Asked Questions for the Pathway to Chartership Index Answers for everyone... 2 What is the pathway?... 2 How does the pathway work?... 2 How do I register... 3 What is a Mentor... 3 Does my
The Initiative of the Government of Portugal and the TaC-Together against Cybercrime International
 Version 30th of June, 2014 IGF Outcome The Initiative of the Government of Portugal and the TaC-Together against Cybercrime International Under the High Patronage of Mr Henri MALOSSE 1, President of the
Version 30th of June, 2014 IGF Outcome The Initiative of the Government of Portugal and the TaC-Together against Cybercrime International Under the High Patronage of Mr Henri MALOSSE 1, President of the
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT. 15 May :00-21:00
 DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
DATA COLLECTION AND SOCIAL MEDIA INNOVATION OR CHALLENGE FOR HUMANITARIAN AID? EVENT REPORT Rue de la Loi 42, Brussels, Belgium 15 May 2017 18:00-21:00 JUNE 2017 PAGE 1 SUMMARY SUMMARY On 15 May 2017,
Understanding Social Computing: Challenges and Opportunities for Europe
 IRIS Major Findings Workshop on: Socio-economic implications of Digital Identity and Social Computing JRC IPTS, Information Society Unit Brussels, 12-13 th November 2009 Understanding Social Computing:
IRIS Major Findings Workshop on: Socio-economic implications of Digital Identity and Social Computing JRC IPTS, Information Society Unit Brussels, 12-13 th November 2009 Understanding Social Computing:
ENHANCED HUMAN-AGENT INTERACTION: AUGMENTING INTERACTION MODELS WITH EMBODIED AGENTS BY SERAFIN BENTO. MASTER OF SCIENCE in INFORMATION SYSTEMS
 BY SERAFIN BENTO MASTER OF SCIENCE in INFORMATION SYSTEMS Edmonton, Alberta September, 2015 ABSTRACT The popularity of software agents demands for more comprehensive HAI design processes. The outcome of
BY SERAFIN BENTO MASTER OF SCIENCE in INFORMATION SYSTEMS Edmonton, Alberta September, 2015 ABSTRACT The popularity of software agents demands for more comprehensive HAI design processes. The outcome of
Fundraising Guide Here are some tips for you: Understand that there will be No s But Expect a Yes Who to ask? everyone
 Fundraising Guide An icare fundraiser is an individual who uses the philanthropy platform of the Airtel Delhi Half Marathon and raises funds of any amount in support of a CSO or cause he/ she chooses.
Fundraising Guide An icare fundraiser is an individual who uses the philanthropy platform of the Airtel Delhi Half Marathon and raises funds of any amount in support of a CSO or cause he/ she chooses.
VDMA Response to the Public Consultation Towards a 7 th EU Environmental Action Programme
 European Office VDMA Response to the Public Consultation Towards a 7 th EU Environmental Action Programme Registration number in the register of representative bodies: 976536291-45 May 2012 1. Introduction
European Office VDMA Response to the Public Consultation Towards a 7 th EU Environmental Action Programme Registration number in the register of representative bodies: 976536291-45 May 2012 1. Introduction
DC Core Internet Values discussion paper 2017
 DC Core Internet Values discussion paper 2017 Focus on Freedom from Harm Introduction The Internet connects a world of multiple languages, connects people dispersed across cultures, places knowledge dispersed
DC Core Internet Values discussion paper 2017 Focus on Freedom from Harm Introduction The Internet connects a world of multiple languages, connects people dispersed across cultures, places knowledge dispersed
Delhi High Level Conference on Climate Change: Technology Development and Transfer Chair s Summary
 Delhi High Level Conference on Climate Change: Technology Development and Transfer 23.10.2009 Chair s Summary Dear Colleagues, 1. This brings us to the conclusion of the Delhi Conference on Climate Change:
Delhi High Level Conference on Climate Change: Technology Development and Transfer 23.10.2009 Chair s Summary Dear Colleagues, 1. This brings us to the conclusion of the Delhi Conference on Climate Change:
ADDENDUM 1. Changes Related to the Bachelor of Science in Intelligence Degree:
 ADDENDUM 1 CE UNIVERSITY 2017 2018 CATALOG ADDENDUM 1 National Intelligence University (NIU) produced this Catalog Addendum to supplement the NIU Catalog and Defense Intelligence Agency publications. You
ADDENDUM 1 CE UNIVERSITY 2017 2018 CATALOG ADDENDUM 1 National Intelligence University (NIU) produced this Catalog Addendum to supplement the NIU Catalog and Defense Intelligence Agency publications. You
Ensuring Adequate Policies and Resources for the 2020 Census
 Ensuring Adequate Policies and Resources for the 2020 Census Background The census is one of the most important elements of U.S. democracy. Article I, Section 2, Clause 3 of the U.S. Constitution mandates
Ensuring Adequate Policies and Resources for the 2020 Census Background The census is one of the most important elements of U.S. democracy. Article I, Section 2, Clause 3 of the U.S. Constitution mandates
Committee on the Internal Market and Consumer Protection. of the Committee on the Internal Market and Consumer Protection
 European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
European Parliament 2014-2019 Committee on the Internal Market and Consumer Protection 2018/2088(INI) 7.12.2018 OPINION of the Committee on the Internal Market and Consumer Protection for the Committee
CCTV Policy. Policy reviewed by Academy Transformation Trust on June This policy links to: T:Drive. Safeguarding Policy Data Protection Policy
 CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Safeguarding Policy Data Protection Policy Located: T:Drive Review Date May 2019 Our Mission To provide the
CCTV Policy Policy reviewed by Academy Transformation Trust on June 2018 This policy links to: Safeguarding Policy Data Protection Policy Located: T:Drive Review Date May 2019 Our Mission To provide the
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase. Term Paper Sample Topics
 A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
A Gift of Fire: Social, Legal, and Ethical Issues for Computing Technology (Fourth edition) by Sara Baase Term Paper Sample Topics Your topic does not have to come from this list. These are suggestions.
Australian Census 2016 and Privacy Impact Assessment (PIA)
 http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
http://www.privacy.org.au Secretary@privacy.org.au http://www.privacy.org.au/about/contacts.html 12 February 2016 Mr David Kalisch Australian Statistician Australian Bureau of Statistics Locked Bag 10,
Summary Remarks By David A. Olive. WITSA Public Policy Chairman. November 3, 2009
 Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
Summary Remarks By David A. Olive WITSA Public Policy Chairman November 3, 2009 I was asked to do a wrap up of the sessions that we have had for two days. And I would ask you not to rate me with your electronic
Measuring Intangible Assets (IP & Data) for the Knowledge-based and Data-driven Economy
 Measuring Intangible Assets (IP & Data) for the Knowledge-based and Data-driven Economy Jim Balsillie Chair and Co-founder of CIGI IMF Statistical Forum November 20, 2018 Big Data, Artificial Intelligence
Measuring Intangible Assets (IP & Data) for the Knowledge-based and Data-driven Economy Jim Balsillie Chair and Co-founder of CIGI IMF Statistical Forum November 20, 2018 Big Data, Artificial Intelligence
SOCIAL DECODING OF SOCIAL MEDIA: AN INTERVIEW WITH ANABEL QUAN-HAASE
 KONTEKSTY SPOŁECZNE, 2016, Vol. 4, No. 1 (7), 13 17 SOCIAL DECODING OF SOCIAL MEDIA: AN INTERVIEW WITH ANABEL QUAN-HAASE In this interview Professor Anabel Quan-Haase, one of the world s leading researchers
KONTEKSTY SPOŁECZNE, 2016, Vol. 4, No. 1 (7), 13 17 SOCIAL DECODING OF SOCIAL MEDIA: AN INTERVIEW WITH ANABEL QUAN-HAASE In this interview Professor Anabel Quan-Haase, one of the world s leading researchers
ABOUT THE MINISTERIAL PROGRAMME
 Official Sponsor 1 2 ABOUT THE MINISTERIAL PROGRAMME The Ministerial Programme at Mobile World Congress is an influential forum offering senior government representatives an opportunity to expand their
Official Sponsor 1 2 ABOUT THE MINISTERIAL PROGRAMME The Ministerial Programme at Mobile World Congress is an influential forum offering senior government representatives an opportunity to expand their
You Can Do 100+ Deals a Year!
 Yes You Can Do 100+ Deals a Year! By Mike Ferry Page 1 of 13 YES, YOU CAN DO 100+ DEALS A YEAR! I believe this statement as much as I believe anything and my job today is to convince you that you can do
Yes You Can Do 100+ Deals a Year! By Mike Ferry Page 1 of 13 YES, YOU CAN DO 100+ DEALS A YEAR! I believe this statement as much as I believe anything and my job today is to convince you that you can do
Office of the Director of National Intelligence. Data Mining Report for Calendar Year 2013
 Office of the Director of National Intelligence Data Mining Report for Calendar Year 2013 Office of the Director of National Intelligence Data Mining Report for Calendar Year 2013 I. Introduction The Office
Office of the Director of National Intelligence Data Mining Report for Calendar Year 2013 Office of the Director of National Intelligence Data Mining Report for Calendar Year 2013 I. Introduction The Office
The Four Paths to Publishing Interview with Keith Ogorek, Author Solutions. For podcast release Tuesday, December 25, 2012
 The Four Paths to Publishing Interview with Keith Ogorek, Author Solutions For podcast release Tuesday, December 25, 2012 KENNEALLY: You can almost hear Optimist Prime making his call to action: transform
The Four Paths to Publishing Interview with Keith Ogorek, Author Solutions For podcast release Tuesday, December 25, 2012 KENNEALLY: You can almost hear Optimist Prime making his call to action: transform
Human Rights in the era of Information and Communication Technology
 Human Rights in the era of Information and Communication Technology May 31, 2017 Interdisciplinary Centre for Security, Reliability and Trust (SnT), University of Luxembourg Outline 1 Human rights 2 Human
Human Rights in the era of Information and Communication Technology May 31, 2017 Interdisciplinary Centre for Security, Reliability and Trust (SnT), University of Luxembourg Outline 1 Human rights 2 Human
APEC Internet and Digital Economy Roadmap
 2017/CSOM/006 Agenda Item: 3 APEC Internet and Digital Economy Roadmap Purpose: Consideration Submitted by: AHSGIE Concluding Senior Officials Meeting Da Nang, Viet Nam 6-7 November 2017 INTRODUCTION APEC
2017/CSOM/006 Agenda Item: 3 APEC Internet and Digital Economy Roadmap Purpose: Consideration Submitted by: AHSGIE Concluding Senior Officials Meeting Da Nang, Viet Nam 6-7 November 2017 INTRODUCTION APEC
Cyberspace: The new international legal frontier
 Cyberspace: The new international legal frontier Keynote address to the Council of Europe Convention on Cybercrime 23 November 2011 CHECK AGAINST DELIVERY Acknowledgements Thorbjorn Jagland - Secretary
Cyberspace: The new international legal frontier Keynote address to the Council of Europe Convention on Cybercrime 23 November 2011 CHECK AGAINST DELIVERY Acknowledgements Thorbjorn Jagland - Secretary
Enabling ICT for. development
 Enabling ICT for development Interview with Dr M-H Carolyn Nguyen, who explains why governments need to start thinking seriously about how to leverage ICT for their development goals, and why an appropriate
Enabling ICT for development Interview with Dr M-H Carolyn Nguyen, who explains why governments need to start thinking seriously about how to leverage ICT for their development goals, and why an appropriate
Navigating The Fourth Industrial Revolution: Is All Change Good?
 Navigating The Fourth Industrial Revolution: Is All Change Good? A REPORT BY THE ECONOMIST INTELLIGENCE UNIT, SPONSORED BY SALESFORCE Written by Forward In almost every aspect of society, the Fourth Industrial
Navigating The Fourth Industrial Revolution: Is All Change Good? A REPORT BY THE ECONOMIST INTELLIGENCE UNIT, SPONSORED BY SALESFORCE Written by Forward In almost every aspect of society, the Fourth Industrial
Mark Coeckelbergh (University of Twente, NL) FREEDOM, SECURITY, PRIVACY OR HOW TO LIVE WITH NEW INFORMATION AND COMMUNICATION TECHNOLOGIES
 Mark Coeckelbergh (University of Twente, NL) FREEDOM, SECURITY, PRIVACY OR HOW TO LIVE WITH NEW INFORMATION AND COMMUNICATION TECHNOLOGIES overview ICTs: hopes and fears some discussions in ethics of ICTs
Mark Coeckelbergh (University of Twente, NL) FREEDOM, SECURITY, PRIVACY OR HOW TO LIVE WITH NEW INFORMATION AND COMMUNICATION TECHNOLOGIES overview ICTs: hopes and fears some discussions in ethics of ICTs
The Value of Membership.
 The Value of Membership. Driving the global transformation to a smarter, more sustainable world with digital solutions at its core. 2018 gesi.org Information and Communications Technology (ICT) innovators
The Value of Membership. Driving the global transformation to a smarter, more sustainable world with digital solutions at its core. 2018 gesi.org Information and Communications Technology (ICT) innovators
Notice of Privacy Practices
 Notice of Privacy Practices THIS NOTICE DESCRIBES HOW MEDICAL INFORMATION ABOUT YOU MAY BE USED AND DISCLOSED AND HOW YOU CAN GET ACCESS TO THIS INFORMATION. PLEASE REVIEW IT CAREFULLY. Privacy is a very
Notice of Privacy Practices THIS NOTICE DESCRIBES HOW MEDICAL INFORMATION ABOUT YOU MAY BE USED AND DISCLOSED AND HOW YOU CAN GET ACCESS TO THIS INFORMATION. PLEASE REVIEW IT CAREFULLY. Privacy is a very
30s THE GREAT DEPRESSION
 30s THE GREAT DEPRESSION During his 1933 inaugural address, Franklin Delano Roosevelt proclaimed, The only thing we have to fear is fear itself. He later pledged a New Deal to aid the economy, introducing
30s THE GREAT DEPRESSION During his 1933 inaugural address, Franklin Delano Roosevelt proclaimed, The only thing we have to fear is fear itself. He later pledged a New Deal to aid the economy, introducing
Ethics Guideline for the Intelligent Information Society
 Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
Ethics Guideline for the Intelligent Information Society April 2018 Digital Culture Forum CONTENTS 1. Background and Rationale 2. Purpose and Strategies 3. Definition of Terms 4. Common Principles 5. Guidelines
Danielle Vanderzanden
 Danielle Vanderzanden Shareholder Boston 617-994-5724 dani.vanderzanden@ogletreedeakins.com Ms. Vanderzanden is a Shareholder in the Boston Office and Co-Chair of the Firm s Data Privacy Practice Group.
Danielle Vanderzanden Shareholder Boston 617-994-5724 dani.vanderzanden@ogletreedeakins.com Ms. Vanderzanden is a Shareholder in the Boston Office and Co-Chair of the Firm s Data Privacy Practice Group.
Pan-Canadian Trust Framework Overview
 Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Human Rights Grievance Mechanisms and Remedies
 Human Rights Grievance Mechanisms and Remedies Business and Human Rights: Trends, Challenges and the Road Ahead, Day 2 American University, Washington School of Law April 24, 2015 Dr Chris Anderson, Principal,
Human Rights Grievance Mechanisms and Remedies Business and Human Rights: Trends, Challenges and the Road Ahead, Day 2 American University, Washington School of Law April 24, 2015 Dr Chris Anderson, Principal,
The Citizen View of Government Digital Transformation 2017 Findings
 WHITE PAPER The Citizen View of Government Digital Transformation 2017 Findings Delivering Transformation. Together. Shining a light on digital public services Digital technologies are fundamentally changing
WHITE PAPER The Citizen View of Government Digital Transformation 2017 Findings Delivering Transformation. Together. Shining a light on digital public services Digital technologies are fundamentally changing
GLOBAL TRADEMARK PORTFOLIO STRATEGIES
 GLOBAL TRADEMARK PORTFOLIO STRATEGIES By Paul W. Reidl Associate General Counsel E. & J. Gallo Winery Modesto, California, USA Presented at the INTERNATIONAL TRADEMARK ASSOCIATION FORUM ON BEST PRACTICES
GLOBAL TRADEMARK PORTFOLIO STRATEGIES By Paul W. Reidl Associate General Counsel E. & J. Gallo Winery Modesto, California, USA Presented at the INTERNATIONAL TRADEMARK ASSOCIATION FORUM ON BEST PRACTICES
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy?
 Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Global Trade and Personal Data Flows Are the Rules of Engagement Incompatible with Privacy? Damon Greer Director U.S.-EU and Swiss Safe Harbor Frameworks U.S. Department of Commerce Trade and investment
Technologists and economists both think about the future sometimes, but they each have blind spots.
 The Economics of Brain Simulations By Robin Hanson, April 20, 2006. Introduction Technologists and economists both think about the future sometimes, but they each have blind spots. Technologists think
The Economics of Brain Simulations By Robin Hanson, April 20, 2006. Introduction Technologists and economists both think about the future sometimes, but they each have blind spots. Technologists think
Economic and Social Council
 UNITED NATIONS E Economic and Social Council Distr. GENERAL ECE/CES/GE.41/2009/18 19 August 2009 Original: ENGLISH ECONOMIC COMMISSION FOR EUROPE CONFERENCE OF EUROPEAN STATISTICIANS Group of Experts on
UNITED NATIONS E Economic and Social Council Distr. GENERAL ECE/CES/GE.41/2009/18 19 August 2009 Original: ENGLISH ECONOMIC COMMISSION FOR EUROPE CONFERENCE OF EUROPEAN STATISTICIANS Group of Experts on
Front Digital page Strategy and leadership
 Front Digital page Strategy and leadership Who am I? Prof. Dr. Bob de Wit What concerns me? - How to best lead a firm - How to design the strategy process - How to best govern a country - How to adapt
Front Digital page Strategy and leadership Who am I? Prof. Dr. Bob de Wit What concerns me? - How to best lead a firm - How to design the strategy process - How to best govern a country - How to adapt
SPEECH BY CLR MPHO PARKS TAU, EXECUTIVE MAYOR OF JOHANNESBURG, AT THE GO DIGITAL SUMMIT, SOWETO, 14 April 2015
 SPEECH BY CLR MPHO PARKS TAU, EXECUTIVE MAYOR OF JOHANNESBURG, AT THE GO DIGITAL SUMMIT, SOWETO, 14 April 2015 Kasi to Kasi Officials Senior Government Officials The Business Community Academics Ladies
SPEECH BY CLR MPHO PARKS TAU, EXECUTIVE MAYOR OF JOHANNESBURG, AT THE GO DIGITAL SUMMIT, SOWETO, 14 April 2015 Kasi to Kasi Officials Senior Government Officials The Business Community Academics Ladies
Interview Recorded at Yale Publishing Course 2013
 Interview Recorded at Yale Publishing Course 2013 With Maria Campbell, president, Maria B. Campbell Associates Gail Hochman, president, Brandt & Hochman Literary Agents For podcast release Monday, August
Interview Recorded at Yale Publishing Course 2013 With Maria Campbell, president, Maria B. Campbell Associates Gail Hochman, president, Brandt & Hochman Literary Agents For podcast release Monday, August
INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016
 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Executive Summary JUNE 2016 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Commissioned to GfK Belgium by the European
www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Executive Summary JUNE 2016 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Commissioned to GfK Belgium by the European
INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016
 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Executive Summary JUNE 2016 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Commissioned to GfK Belgium by the European
www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Executive Summary JUNE 2016 www.euipo.europa.eu INTELLECTUAL PROPERTY (IP) SME SCOREBOARD 2016 Commissioned to GfK Belgium by the European
 Introduction Pervasive Computing and Urban Development Issues for the individual and society JSY Chin, V Callaghan, G Clarke, H Hagras, M Colley Intelligent Inhabited Environments Group http://iieg.essex.ac.uk
Introduction Pervasive Computing and Urban Development Issues for the individual and society JSY Chin, V Callaghan, G Clarke, H Hagras, M Colley Intelligent Inhabited Environments Group http://iieg.essex.ac.uk
Activity Guide - Primary Source: The Internet is for Everyone
 Name(s) Period Date Activity Guide - Primary Source: The Internet is for Everyone Introduction So far in this class, you have solved a few problems by creating and using small protocols for transmitting
Name(s) Period Date Activity Guide - Primary Source: The Internet is for Everyone Introduction So far in this class, you have solved a few problems by creating and using small protocols for transmitting
Tren ds i n Nuclear Security Assessm ents
 2 Tren ds i n Nuclear Security Assessm ents The l ast deca de of the twentieth century was one of enormous change in the security of the United States and the world. The torrent of changes in Eastern Europe,
2 Tren ds i n Nuclear Security Assessm ents The l ast deca de of the twentieth century was one of enormous change in the security of the United States and the world. The torrent of changes in Eastern Europe,
DIMACS/PORTIA Workshop on Privacy Preserving
 DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
DIMACS/PORTIA Workshop on Privacy Preserving Data Mining Data Mining & Information Privacy: New Problems and the Search for Solutions March 15 th, 2004 Tal Zarsky The Information Society Project, Yale
Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY
 Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY The Internet is changing the way that individuals launch businesses, established companies function, and
Encouraging Economic Growth in the Digital Age A POLICY CHECKLIST FOR THE GLOBAL DIGITAL ECONOMY The Internet is changing the way that individuals launch businesses, established companies function, and
Front Digital page Strategy and Leadership
 Front Digital page Strategy and Leadership Who am I? Prof. Dr. Bob de Wit What concerns me? - How to best lead a firm - How to design the strategy process - How to best govern a country - How to adapt
Front Digital page Strategy and Leadership Who am I? Prof. Dr. Bob de Wit What concerns me? - How to best lead a firm - How to design the strategy process - How to best govern a country - How to adapt
THE EUROPEAN DATA PROTECTION SUPERVISOR PRESENTS: THE CARTOON INTRODUCTION TO DIGITAL ETHICS. BY GRADY KLEIN AND YORAM BAUMAN, Ph.D.
 THE EUROPEAN DATA PROTECTION SUPERVISOR PRESENTS: THE CARTOON INTRODUCTION TO DIGITAL ETHICS BY GRADY KLEIN AND YORAM BAUMAN, Ph.D. THE WORLD S FIRST AND ONLY STAND-UP ECONOMIST PRINTED BY IMPRIMERIE CENTRALE
THE EUROPEAN DATA PROTECTION SUPERVISOR PRESENTS: THE CARTOON INTRODUCTION TO DIGITAL ETHICS BY GRADY KLEIN AND YORAM BAUMAN, Ph.D. THE WORLD S FIRST AND ONLY STAND-UP ECONOMIST PRINTED BY IMPRIMERIE CENTRALE
DEFENDER S TOOLKIT FOR PHONE BANKING
 DEFENDER S TOOLKIT FOR PHONE BANKING Welcome to our Defender s Toolkit for Phone Banking. In 2016, while running for president, Donald Trump said that if he was able to appoint two or three justices to
DEFENDER S TOOLKIT FOR PHONE BANKING Welcome to our Defender s Toolkit for Phone Banking. In 2016, while running for president, Donald Trump said that if he was able to appoint two or three justices to
Wombat Security s Beyond the Phish. Report. security technologies. #BeyondthePhish
 Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
Wombat Security s 2016 Beyond the Phish Report security technologies #BeyondthePhish Beyond the Phish As our State of the Phish Report reinforced earlier this year phishing is still a large and growing
Women in Software and Cybersecurity: Dr. Lorrie Cranor
 Women in Software and Cybersecurity: Dr. Lorrie Cranor featuring Dr. Lorrie Cranor as Interviewed by Summer Craze Fowler ---------------------------------------------------------------------------------------------Summer
Women in Software and Cybersecurity: Dr. Lorrie Cranor featuring Dr. Lorrie Cranor as Interviewed by Summer Craze Fowler ---------------------------------------------------------------------------------------------Summer
THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR
 THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR THE NEXT DIRECTOR AND DEPUTY DIRECTOR OF THE U.S. PATENT AND TRADEMARK OFFICE Revised and approved, AIPLA
THE AMERICAN INTELLECTUAL PROPERTY LAW ASSOCIATION RECOMMENDATIONS REGARDING QUALIFICATIONS FOR THE NEXT DIRECTOR AND DEPUTY DIRECTOR OF THE U.S. PATENT AND TRADEMARK OFFICE Revised and approved, AIPLA
March 27, The Information Technology Industry Council (ITI) appreciates this opportunity
 Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Submission to the White House Office of Science and Technology Policy Response to the Big Data Request for Information Comments of the Information Technology Industry Council I. Introduction March 27,
Privacy and Security in Europe Technology development and increasing pressure on the private sphere
 Interview Meeting 2 nd CIPAST Training Workshop 17 21 June 2007 Procida, Italy Support Materials by Åse Kari Haugeto, The Norwegian Board of Technology Privacy and Security in Europe Technology development
Interview Meeting 2 nd CIPAST Training Workshop 17 21 June 2007 Procida, Italy Support Materials by Åse Kari Haugeto, The Norwegian Board of Technology Privacy and Security in Europe Technology development
The Dark Side of Data The NSA ThinThread Tale
 The Dark Side of Data The NSA ThinThread Tale Thomas A. Drake Knowpari Systems LLC 18 Oct 2011 Or?? Or?? Orwell ian?? NSA in Action! Purpose Provoke thought, reflection, as well as introspection from
The Dark Side of Data The NSA ThinThread Tale Thomas A. Drake Knowpari Systems LLC 18 Oct 2011 Or?? Or?? Orwell ian?? NSA in Action! Purpose Provoke thought, reflection, as well as introspection from
DELEGATE WORKSHEET: ASKING PEOPLE TO JOIN OUR UNION
 DELEGATE WORKSHEET: ASKING PEOPLE TO JOIN OUR UNION The best way to get workers to join our Union or take action in support of union members is when they are asked by a work colleague who they trust and
DELEGATE WORKSHEET: ASKING PEOPLE TO JOIN OUR UNION The best way to get workers to join our Union or take action in support of union members is when they are asked by a work colleague who they trust and
What Ethical and Governance Frameworks must prevail on the face of Technological Challenges?
 CPA PNG & CPA Australia (PNG Branch) Annual National Conference - 2016 Bridging Expectation with Reality, 2017 and Beyond What Ethical and Governance Frameworks must prevail on the face of Technological
CPA PNG & CPA Australia (PNG Branch) Annual National Conference - 2016 Bridging Expectation with Reality, 2017 and Beyond What Ethical and Governance Frameworks must prevail on the face of Technological
The BGF-G7 Summit Report The AIWS 7-Layer Model to Build Next Generation Democracy
 The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
The AIWS 7-Layer Model to Build Next Generation Democracy 6/2018 The Boston Global Forum - G7 Summit 2018 Report Michael Dukakis Nazli Choucri Allan Cytryn Alex Jones Tuan Anh Nguyen Thomas Patterson Derek
April 10, Develop and demonstrate technologies needed to remotely detect the early stages of a proliferant nation=s nuclear weapons program.
 Statement of Robert E. Waldron Assistant Deputy Administrator for Nonproliferation Research and Engineering National Nuclear Security Administration U. S. Department of Energy Before the Subcommittee on
Statement of Robert E. Waldron Assistant Deputy Administrator for Nonproliferation Research and Engineering National Nuclear Security Administration U. S. Department of Energy Before the Subcommittee on
Responsibility in Wealth
 Responsibility in Wealth The Kaiser Partner Special Report Series Issue #1/June 2012 With great wealth comes great responsibility. Introduction At Kaiser Partner, we understand that the world is changing
Responsibility in Wealth The Kaiser Partner Special Report Series Issue #1/June 2012 With great wealth comes great responsibility. Introduction At Kaiser Partner, we understand that the world is changing
