Analysis of energy consumption for multiple object identification system with active RFID tags
|
|
|
- Brent Arnold
- 6 years ago
- Views:
Transcription
1 WIRELESS COMMUNICATIONS AND MOBILE COMPUTING Wirel. Commun. Mob. Comput. 2008; 8: Published online 18 September 2007 in Wiley InterScience ( Analysis of energy consumption for multiple object identification system with active RFID tags Xu Su 1 and Yang Xiao 2, 1 Computer Science Department, The University of Texas at San Antonio, TX, U.S.A. 2 Computer Science Department, The University of Alabama, AL, U.S.A. Summary Radio frequency identification (RFID) systems are very effective for identifying objects. Existing published works focus on designing efficient collision resolution protocols for the tag identification problem in RFID systems with passive RFID tags. However, advances in low-cost and low-power sensing technologies will make active RFID tags more popular and affordable in the near future. In multiple object identification systems with active tags, the tags are designed for extremely low-cost large-scale applications such that battery replacement is not feasible. This imposes a critical energy-constraint on the communication protocols used in these systems. In this paper, we analyze energy consumption and identification times for several protocols. The objective is to decrease energy consumption of tags by reducing both the total identification time and the total active time. Copyright 2007 John Wiley & Sons, Ltd. KEY WORDS: radio frequency identification; anti-collision algorithms; conflict resolution; energy consumption; identification time 1. Introduction Radio Frequency Identification (RFID) systems can identify an object or a person using wireless transmission. An RFID system consists of RFID tags (also called transponders) and readers (also called interrogators). Readers broadcast queries to tags in their wireless transmission ranges for information contained in tags, and tags reply with required information such as identification (ID) numbers. RFID systems have been gaining more popularity in areas such as supply chain management, automated identification systems, and any place requiring identification of products or people. RFID systems can be divided into three classes: passive RFID systems, active RFID systems, and hybrid RFID systems. In a passive RFID system, all tags are passive tags which have no battery. While in an active RFID system, all tags are active tags which have their own batteries. Hybrid RFID systems consist of both passive and active tags. In all RFID systems, the reader must be able to identify tags as quickly as possible. However, signals of readers or tags collide because they communicate over the shared wireless channel and collisions interfere with fast identification. Therefore, anti-collision protocols which reduce collisions and identify tags regardless of the occurrence of collisions are required. *Correspondence to: Yang Xiao, Department of Computer Science, The University of Alabama, 101 Houser Hall, Box , Tuscaloosa, AL U.S.A. yangxiao@ieee.org Copyright 2007 John Wiley & Sons, Ltd.
2 954 X. SU AND Y. XIAO Collision can be divided into reader collisions and tag collisions [1]. Reader collisions occur when close readers communicate at the same time on the same frequency, or when neighboring readers attempt to communicate with the same tag at the same time. Tag collisions occur when more than one tag tries to respond to a reader at the same time and make the reader recognize no tags. Reader collisions can be easily resolved because RFID readers can detect collisions and communicate with one another. In Reference [2], Engels and Sarma define Reader Collision Problem and present several graph coloring formulations. Waldrop et al. [3] propose a simple, distributed, on-line algorithm: Colorwave algorithm for the Reader Collision Problem. Kim et al. [4] propose an adaptive and dynamic localized algorithm for hierarchical clustering in RFID networks. It minimizes the overlapping areas among clusters and the reader collision by regulating an RFID reader s cluster radius dynamically. In passive RFID systems, current tag anti-collision protocols can be categorized into ALOHA based protocols and tree based protocols. ALOHA based tag anti-collision protocols such as pure ALOHA, slotted ALOHA, and framed ALOHA [5 7] reduce the probability of the occurrence of tag collisions, in which tags respond at a distinct time. In a pure ALOHA protocol, upon receiving a query from the reader, each tag randomly selects its response time and sends its response message to the reader. In a slotted ALOHA protocol, time is slotted and each tag can respond only at the beginning of a time slot. A framed ALOHA protocol is a variant of slotted ALOHA protocol. After the reader has sent a query to tags, it waits a certain amount of time for their answers. This time frame is divided into a number of slots that can be occupied by tags and used for sending their answers so that it reduces collisions. Framed ALOHA shows the best performance among the ALOHA based protocols, followed by slotted ALOHA. However, ALOHA based protocols cannot perfectly prevent collisions. In addition, they have the serious problem that a tag may not be identified for a long time the so called tag starvation. Tree based tag anti-collision protocols such as the binary tree protocol [5] and its variant the query tree protocol [8,9] do not cause tag starvation though they have relatively long identification delay. They split the group of colliding tags into two or more subgroups until the reader recognizes the IDs of tags without collisions. In a passive RFID system, the objective is to reduce the identification time and simplify the implementation. While in the active RFID system, energy conservation for active tags is another critical system parameter for communications. Active tags are designed for extremely low-cost large-scale applications, such that battery replacement is not feasible. This imposes a critical energy-constraint on the communication protocols used in these systems, so that the total time a tag needs to be active for transmitting information should be minimized. At the same time, identification delay must be small too. Thus this gives rise to a trade-off between energy consumption and identification time. To the knowledge of the authors, existing works focus only on passive RFID systems. The major advantages of an active RFID tag over a passive tag are: (i) it has longer read range; (ii) it has larger storage capacity; (iii) data can be sent at designated times. Active RFID tags may have all or some of the following features: the capability to perform independent monitoring and control, the capability of initiating communications; the capability of performing diagnostics; the highest data bandwidth; active RFID tags may even be equipped with autonomous networking and the tags autonomously determine the best communication path. Active tags have been used in many different areas such as manufacturing, transportation and automotive, air industry, healthcare, military sector, logistics, and retails. For example, active tags are used for tracking of cargo, proof of tamper evidence on containers, long range asset tracking, peer to peer networks for sensing, real time location of assets and people, and remote identification in difficult environments. Advances in low-cost and low-power sensing technologies will make active RFID tags more popular and affordable in the near future. Therefore, in this paper, we focus on RFID systems with active tags. Since the main difference between active tags and passive ones is that active RFID tags have their own internal power source, and existing anti-collision protocols in passive RFID systems can still be used in active RFID systems. In this paper, we apply existing anti-collision protocols in passive RFID systems to active RFID systems, and analyze their energy-consumption and identification times. The rest of the paper is organized as follows. Section 2 gives the model for multiple object identification in active RFID systems. Section 3 introduces different
3 ANALYSIS OF ENERGY CONSUMPTION 955 anti-collision protocols for active RFID systems and analyzes their power consumption and identification times. Section 4 presents performance analysis of these protocols. Finally, we conclude the paper in Section Model Description In a multiple object identification system with active RFID tags, there are one reader and n active tags. The reader is a powerful entity with abundant memory and computational power. Active tags are limited in memory and computation power. The process, starting from time that a reader sends a query to the time that the reader receives messages from all tags within its radio range is called an identification process. Before formulating the problem, we introduce some notations to be used, as listed in Figure 1. There is a single communication channel between the reader and tags. However, tags are not able to exchange messages among each other. The reader can broadcast messages to tags. After receiving a message, each tag can send a response back to the reader optionally. If only one tag responds, the reader receives the message successfully. But if more than one tag responds, their messages would collide on the communication channel. Thus the reader detects a collision on the channel and cannot receive message from any of them. We will not take into consideration the capture effect by which a tag s message may be able to be recognized by the reader inspite of a collision. The capture effect is quite common if tags are placed close to each other. This means practically that data, which would normally be lost due to the collision, can be read, and thus the system performance rises. However, it seems that whenever such a weak collision between the same two tags occurs, one of them always wins and the data from the other one is lost. Therefore, the influence of the capture effect is only minimal and seems not to have great impact on the performance. Each active tag can be in one of the two states: listening state and transmitting state. Normally an active tag is in listening state and listens the query from the reader. When it is required to send a response back to the reader, it switches to transmitting state. Listening state consists of two states: receiving state and idle state. Since active tags consume much more power in transmitting state than in receiving and idle states, we do not differentiate the receiving state and idle state. For simplicity, we consider them as a single state listening state. We can reduce the power consumption of an active tag in an identification process by decreasing the number of messages that it transmits. This problem is equivalent to the collision minimization problem. At the same time, the identification time for all the tags within the radio range of the reader should be as short as possible. Otherwise, the system is useless if the identification time is too long. Without loss of generality, we assume that each message sent by tags has the same size, and the time needed for a tag to send a message is the same, denoted as T trans. The power consumption rate for sending each message is fixed and represented by P trans as given in Figure 1. Also we assume that the process time for reader and tags are negligible. In a multiple object identification system with one reader and n active RFID tags, the identification time, T total, is the time elapsed from the time the query is sent from the reader to the time all tags are identified by the reader. The total power consumption of all tags during transmitting state in an identification process, P total, is given by n P total = P trans T trans r i (1) i=1 Fig. 1. Notations used in the problem formulation. where r i is the number of messages sent by tag i in an identification process. The purpose of the anti-collision protocols for passive RFID systems is to minimize T total. However, in the active RFID system, energy conservation for active tags is another critical system parameter. If the objective is to minimize P total, the solution can be
4 956 X. SU AND Y. XIAO obtained easily, using min{p total }=np trans T trans (2) min{p total } can be obtained using protocols similar to query tree protocol (see Section 3). The reader broadcasts all possible tags IDs one by one in the queries to all tags such that no collision occurs, i.e., only 0 or 1 tag will respond at each time. However, identification time T total = (D t2r + D r2t )2 k is too long, where k is the length of the ID string. Therefore, the protocol is useless. As shown above, minimization of P total only is not desired, so we consider reduction of both P total and T total at the same time and define a protocol effectiveness function, E, as given in Equation (3). The objective is to find the most effective protocol which minimizes E: E = αp total + (1 α)t total P idle, where 0 α 1 (3) α is used to adjust weights on P total and T total. There are three special cases. When α = 0, the objective is to find a protocol which minimizes the identification time T total only. When α = 1, the objective is to find a protocol which minimizes the P total only (the solution is given in Equation (2)). When α = 0.5, the objective is to find a protocol which minimizes the total energy-consumption for all tags in an identification process, including both energy-consumption during transmitting state and during listening state. 3. Protocol Analysis In tag anti-collision protocols, at the beginning of an identification process, all tags are in listening state. When a tag needs to send a response message to the reader, it switches to the transmitting state. After the tag finishes sending response message, it goes back to the listening state ALOHA-based Protocol In ALOHA-based protocols, if a tag receives the confirmation message back from the reader which says that the reader has received the message from the tag successfully, it will not send messages any more during current identification process until a new identification process begins. If a tag does not receive the confirmation message from the reader, it has to resend the response message at different times in the following different protocols Pure ALOHA protocol In the pure ALOHA protocol, after a tag transmits its ID, it waits to see whether transmission is acknowledged by the reader; no response within a specified period of time (D r2t + D t2r ) indicates a collision with other transmission, or the reader will send an explicit message indicating the collision. If the presence of a collision is determined by the tag, it retransmits after some random wait time. The random time is different for different tags, thereby avoiding collision during the retransmission cycle. The worst case collision period is two times the length of each message (2 D t2r ), assuming all messages from the tags to the reader to be of equal length Slotted ALOHA protocol Slotted ALOHA improves on pure ALOHA protocol by cutting the vulnerable period for message collision by half. Time is slotted and packets must be transmitted within a slot (D t2r ). If the tag needs to send a message, it waits until the beginning of the next slot before sending. The tag listens to the broadcast and checks if the message was transmitted successfully. If there was a collision, indicated by explicit collision indication message or the absence of acknowledgment message from the reader within a pre-specified period of time (D r2t + D t2r ), the tag waits a random number of slots and attempts to send it again Framed ALOHA protocol In the framed ALOHA protocol [7], after the reader has sent its query to the tags, it waits a certain amount of time for their answers. This time frame is divided into a number of time slots that can be occupied by tags and used for sending their answers. When multiple tags use the same slot, a collision occurs and data get lost. The tag reading cycle consists of two steps. In the first step, the reader broadcasts a query for data, which contains the frame size m and a random value Rnd. In the second step, tags compute a random response slot number (say k, where 1 k m), using the frame size m and the random value Rnd as parameters, and correspond at slot k to avoid collisions occurring repeatedly. If the tag determines that it has sent the response message to the reader successfully, it will switch to listening state
5 ANALYSIS OF ENERGY CONSUMPTION 957 and will not respond during the current identification process. If there was a collision, in the next time frame the tag will compute a random response slot number and attempt to send it again Contention Tree Protocol In the contention tree protocol, every contention frame is divided into a number of time slots. Let us assume that there are n tags which want to send response messages after they receive the reader s query message. During the first contention frame, i.e., the frame at the root of the tree, each of the n tags picks at random a number (say k) between 1 and m with equal probabilities and transmits its response message during the kth contention slot, where m is the frame size (number of slots in the frame). After completion of the contention frame and pre-specified period of time, each tag knows whether its message has been successfully received by the reader. If not, a new contention frame is assigned to all tags that caused the collision during the particular slot. Therefore, if there were collisions in all contention slots, m new contention frames would become available. This leads to the formation of a tree with nodal degree m. The expansion of the tree stops at either empty or successful slots. Upon completion of the tree protocol, all the n tags have successfully sent their response messages. Let L n denote the number of contention frames required to complete the tree. Let d n denote the number of levels (number of time frames) required for a random tag to send response message successfully. Let D n denote the number of levels required to complete the tree. The expectation of L n can be expressed recursively according to References [10,11] L n = 1 (n = 1) m m 1 (n = 2) (1 m 1 n ) 1 [ 1 + n 1 k=2 (n 3) ( n k) (m 1) n k m n 1 L k ] (4) According to formulas given in Equation (5), we can compute the expectation value of the total identification time, T total. T total = L n (md t2r + D r2t ) nm (md t2r + D r2t ) (8) Let P tag denote the power consumption of a random tag (during transmitting state) to have successful contention. The expectation value of P tag can be written as P tag = d n P trans T trans log m (n 1)P trans T trans (9) Let max(p tag ) denote the maximum power consumption of the tag among all tags (during transmitting state) to have successful contention. The expectation value of max(p tag )isgivenby max(p tag ) = D n P trans T trans 2 log m np trans T trans (10) And the expected power consumption of all tags during transmitting state in one identification process can be denoted as P total = np tag n log m (n 1)P trans T trans (11) The expected value of effectiveness (E) of the protocol can be written as E = αp total + (1 α)t total P idle αn log m (n 1)P trans T trans + (1 α) nm (md t2r + D r2t )P idle = αn ln(n 1)P transt trans + (1 α)nm(md t2r + D r2t )P idle where 0 α 1 (12) The expectation values for L n, d n, and D n can be calculated [12] as follows: L n n (5) d n log m (n 1) (6) Given the total number of tags n and value of α, we can find a value for m which minimizes E. Let us rewrite E as a function of m as follows: E(m) = αn ln(n 1)P transt trans D n 2 log m n (7) + (1 α)nm(md t2r + D r2t )P idle (13)
6 958 X. SU AND Y. XIAO Let m be the value for m that minimizes E(m), as given by E(m ) = min {E(m)} (14) m Z,m 2 Both P total and T total are monotonic functions. When m increases, P total decreases and T total increases more dramatically. There exists a unique value m = m such that E(m) has the minimal value. Since m is an integer and m 2, intuitively we can find m by searching from m = 2 and increasing the m by 1 each time. We stop searching when E(m + 1) > E(m) holds at the first time, then set m = m and E(m ) = E(m) isthe minimal value. Search space of m from 2 to + is too huge. We limit the search space of m and give a small search space [2,m B ] such that m [2,m B ], as given in Lemma 1. We can also start searching from m = m B and decrease m by 1 each time to find the optimal value m = m which minimizes E(m). Lemma 1. Given the total number of tags (n) and α, m, which minimizes E(m) is in the range [2,m B ], where the upper bound ( ln(n 1)αP trans T trans m B = max 10, (1 α)d t2r P idle (2 ln 10 1) Proof is given in Appendix A Query-Tree Protocol The Query-Tree (QT) protocol [8] consists of queries and responses. In each round, the reader asks tags whether any of their IDs contains a certain prefix. If more than one tag answers, then the reader knows that there are at least two tags that have the same prefix. When a prefix matches a tag uniquely, that tag is identified. Therefore, by extending the prefixes until only one tag s ID matches, the algorithm can identify all tags. The query tree describes the complete dialog between the reader and the tags in an execution of the QT protocol, as follows. Suppose in an execution of the QT protocol, the reader has sent the set Q of query strings. The query tree of the QT protocol execution is defined recursively. If a tag receives the confirmation message back from the reader which says that the reader has received the message from the tag successfully, it will not send messages any more during the current identification process until a new identification process is initiated. If a tag does not receive the confirmation message from the reader, it has to resend the response message at different times determined by the query tree. The root of the query tree corresponds to the query string ε (empty string). If the query tree node x corresponds to the query string q, and both q0,q1 Q, then leftchild(x) and rightchild(x) are query tree nodes that correspond to the query strings q0 and q1 respectively. Otherwise, both leftchild(x) and rightchild(x) equal NIL. The above definition implies that an internal node of a query tree corresponds to a query string that results in a collision. A leaf corresponds to a query string that results in either no reply or a response from exactly one tag. The query tree is similar to a special case of contention tree protocol with frame size m = 2. But the sizes of messages sent from both the reader and the tags are different from those in the contention tree protocol. Each tag randomly chooses one of the two slots in contention tree protocol, and tags are assigned to different sub-trees according to their prefix bit value in QT protocol. Another difference is that every time after the reader sends query, it waits for (D r2t + D t2r ) time and sends another query with new prefix until all tags are identified. For simplicity, we also assume the time needed for a tag to send a message is same, denoted as D trans. Then, the expected total identification time is obtained as follows: T total = L n 2(D t2r + D r2t ) m=2 n 2(D t2r + D r2t ) m=2 = 2n ln 2 (D t2r + D r2t ) (15) The expected power consumption for a random tag in the transmitting state is given by P tag = d n P trans D trans m=2 log m (n 1)P trans T trans m=2 = log 2 (n 1)P trans T trans (16) The expected power consumption of all tags during transmitting state in one identification process can be denoted as P total = np tag n log 2 (n 1)P trans T trans (17)
7 ANALYSIS OF ENERGY CONSUMPTION 959 The expectation of total identification time (D) QT m = 2 m = 6 m = 10 m = Total number of tags: n Fig. 2. The expectation of total identification time T total. The expected maximum power consumption for a tag among all the tags in the transmitting state is given by max(p tag ) = D n P trans T trans m=2 2 log m np trans T trans m=2 4. Performance Evaluation = 2 log 2 np trans T trans (18) In this section, we give performance analysis of contention tree protocols. Without loss of generality, we assume the time for a message sent from the reader to a tag is the same as that for a message sent from a tag to the reader, i.e., D r2t = D t2r = D. Also we let P trans T trans = J. Figure 2 gives the expected total identification time (T total ) for n tags in an identification process. When the total number of tags increases, T total increases too. Given the total number of tags, when frame size (m) increases, T total decreases accordingly because less collisions occur. The expected total identification time for QT protocol is slightly less than that for contention tree protocol with frame size m = 2. Figures 3 and 4 give the expectation value of power consumption of a random tag and the expected maximum power consumption of a tag among all tags (during transmitting state) to have successful contention in an identification process, i.e., P tag and max(p tag ), respectively. When the number of tags n increases, both P tag and max(p tag ) increase because more tags cause more collisions and the average The expectation of total power consumption of all tags (J) m = 2, QT m = 6 m = 10 m = Total number of tags: n Fig. 3. The expectation of power consumption of a random tag P tag. number of messages sent by a tag to have a successful contention increases correspondingly. The P tag and max(p tag ) for Query-Tree protocol are same as those for contention tree protocol with frame size m = 2. Figure 5 gives the expectation of total power consumption of all tags (during transmitting state) in an identification process. The more tags are in the system, the more is the power is consumed correspondingly. Given a fixed number of tags in a system, when the frame size (m) increases, the power consumption of all tags during transmitting state decreases due to less collision. When the frame size (m) changes from 2 to 6, the total power consumption of all tags decreases a lot. Total power consumption of all tags does not change too much when the frame size is large enough (e.g., m from 6 to 14). The total power consumption of all tags The expectation of max power consumption of a tag (J) Total number of tags: n m = 2, QT m = 6 m = 10 m = 14 Fig. 4. The expectation of maximum power consumption of a tag max(p tag ).
8 960 X. SU AND Y. XIAO Probability that at least one tag sends message successfully in one frame n = 15 n = 25 n = 45 n = Frame size: m Fig. 5. The expectation of total power consumption of all tags P total. P total for Query-Tree protocol is the same as that for contention tree protocol with frame size m = 2. Given the total number of tags (n) and weight α, we can find m that minimizes E(m) by searching m. Figure 6 gives the expectation of effectiveness of protocols E(m), where α = 0.5 and DP idle = 0.01P trans D trans = 0.01J. When the total number of tags is small (e.g., 100), frame size m does not affect the performance too much. When the total number of tags is large (e.g., 2000), increasing the frame size does improve performance. However, frame size does not help any more if it is large enough. The optimal frame size m and the upper bound m B are shown in the legend of Figure 6. We can see that the upper bound given in Lemma 1 is very close to m. In order to find the optimal frame size m, we can either search from m = 2 and increase m by 1 each time, or search from m = m B and decrease m by 1 each time. Given the upper bound The expectation of effectiveness of protocols (J) x 10 4 n = 100 (m * = 10, m B = 12) n = 400 (m * = 11, m B = 13) n = 800 (m * = 12, m B = 14) n = 2000 (m * = 12, m B = 15) Frame size: m Fig. 6. The expectation of effectiveness of protocols: E. m B, it will save search time a lot by searching from m = m B back to m = 2. Figure 6 shows that we only need to search maximum 5 times (n = 2000) to find m starting from frame size m = m B back to m = Conclusions Radio Frequency Identification (RFID) system is an automatic identification system. Tag anti-collision protocols such as ALOHA, slotted ALOHA, framed ALOHA, content tree protocol, and query tree protocols are well studied in passive RFID systems. However, till now, anti-collision protocols for active RFID systems are not investigated. We believe that advances in low-cost, low-power sensing technologies will make active tags more popular and affordable in the near future. In the active RFID system, energy conservation for active tags is another critical system parameter besides identification time for communications. The active tags are designed for extremely lowcost large-scale applications, such that the replacement of batteries is not feasible. This imposes a critical energy-constraint on the communications protocols used in these systems, so that the total time a tag needs to be active for transmitting information should be as small as possible. At the same time identification delay must be small too. Thus this gives rise to a trade-off between energy consumption and delay. In this paper, we applied existing protocols in passive RFID systems into active RFID systems. We defined a new objective function, effectiveness of a protocol (E), which considers reduction of both total power consumption of all tags and total identification time at the same time. We compare and analyze the power consumption and identification time of these protocols in active RFID systems. Acknowledgment This work was partially supported by the US National Science Foundation (NSF) under grants CNS and CNS Appendix A: Proof of Lemma 1 Let a = αnp trans T trans, b = (1 α)nd t2r P idle, and c = (1 α)nd r2t P idle. then ( ) a ln(n 1) m B = max 10, b(2 ln 10 1)
9 ANALYSIS OF ENERGY CONSUMPTION 961 E(m) = a ln(n 1) + bm2 + cm Let m be the value of m which minimizes E(m), then m is the minimal value such that E(m) E(m ) > 0 We have to show that m B m. m >m if m 10, m B m holds obviously. if m > 10, according to the m s definition, it suffices to prove E(m) > E(m B ) m >m B 10 If m>m B holds, then a ln(n 1) m>m B = b(2 ln 10 1) and it can be rephrased as 2b ln 10m 2 bm 2 >aln(n 1) since >ln 10 and bm +cm cm > 0, it holds that 2b m 2 + bm + cm (bm 2 + cm) >aln(n 1) using the fact 0 < ln (1 + 1 m )m < 1, we have We can rephrase it as 2b m 2 + bm + cm ( (bm 2 + cm)ln ) m m ( >aln(n 1) ln ) m m 2b m 2 + bm + cm (bm 2 + cm)m [ln(m + 1) ] >aln(n 1)m [ln(m + 1) ] Divide m on both sides of the inequality, then 2b m+ b + c (bm 2 + cm) [ln(m + 1) ] >aln(n 1) [ln(m + 1) ] It can be rephrased as [ a ln(n 1) + b(m + 1) 2 + c(m + 1) ] [ a ln(n 1) + bm 2 ln(m + 1) + cm ] ln(m + 1) > 0 Divide ln(m)ln(m + 1) on both sides of the inequality, gives a ln(n 1) + b(m + 1) 2 + c(m + 1) ln(m + 1) a ln(n 1) + bm2 + cm > 0 then we have m B m. References E(m + 1) E(m) > 0 1. Sarma S, Brock D, Engels D. Radio frequency identification and the electronic product code. IEEE Micro 2001; 21(6): Engels DW, Sarma SE. The reader collision problem. In IEEE International Conference on Systems, Man and Cybernetics, Vol. 3, October Waldrop J, Engels DW, Sarma SE. Colorwave: an anticollision algorithms for the reader collision problem. IEEE International Conference on Communications, Vol. 2, May 2003, pp Kim J, Lee W, Yu J, Myung J, Kim E, Lee C. Effect of localized optimal clustering for reader anti-collision in rfid networks: fairness aspects to the readers, In Proceedings of International Conference on Computer Communications and Networks (ICCCN), 2005, pp Hush DR, Wood C. Analysis of tree algorithm for rfid arbitration. In IEEE International Symposium on Information Theory, Chan S, Hinrich H, Kandlur D, Krishna A. U.S. patent: multiple item radio frequency tag identification protocol. Patent number: US , Vogt H. Multiple object identification with passive rfid tags. IEEE International Conference on Systems, Man and Cybernetics, Vol. 3, October Law C, Lee K, Siu K-Y. Efficient memoryless protocol for tag identification. In Proceedings of the 4th International Workshop on Discrete Algorithm and Methods for Mobile Computing and Communications, August 2000, pp Zhou F, Chen C, Jin D, Huang C, Min H. Evaluating and optimizing power consumption of anticollision protocols for applications in rfid systems. In Proceedings of the International Symposium on Low Power Electronics and Design, August 2004, pp Massey JL. Collision resolution algorithms and random access algorithms. In Multi-User Communication Systems, Number 265 in CISM Courses and Lectures, Longo G (ed.). 1981; Huang J-C, Berger T. Delay analysis of interval searching contention resolution algorithms. IEEE Transactions on Information Theory 1985; 31(2): Janssen AJEM, de Jong MJM. Analysis of contention tree algorithms. IEEE Transactions on Information Theory 2000; 46(6):
10 962 X. SU AND Y. XIAO Authors Biographies Xu Su is currently pursuing the Ph.D. degree in Computer Science at the University of Texas at San Antonio. He received the B.E. degree in Computer Science and Application from Yanshan University, Qinhuangdao, China, in 1997, and the M.S. degree in Computer Science from Wright State University, Dayton, Ohio, USA in He was a research assistant from 2001 to 2002 at Wright State University. He was a teaching assistant from 2003 to 2005, and has been a research assistant since 2005, at the University of Texas at San Antonio. He received National Achievement Award in Defense Science and Technology by Commission of Science Technology and Industry for National Defense, Second Class, China, in He also received National Award in Science and Technology Progress by Ministry of Education, Second Class, China, in His research interests includes mobile ad hoc networks, wireless sensor networks, wireless network security, and networked multimedia. He is a student member of IEEE and ACM. Yang Xiao worked at Micro Linear as a Medium Access Control (MAC) architect involving the IEEE standard enhancement work before he joined Department of Computer Science at The University of Memphis in Dr. Xiao is currently with Department of Computer Science at The University of Alabama. He was a voting member of IEEE Working Group from 2001 to He is an IEEE senior member. He is a member of American Telemedicine Association. He currently serves as Editor-in-Chief for International Journal of Security and Networks (IJSN), International Journal of Sensor Networks (IJSNet), and International Journal of Telemedicine and Applications (IJTA). He serves as a referee/reviewer for many funding agencies, as well as a panelist for NSF and a member of Canada Foundation for Innovation (CFI) s Telecommunications expert committee. He serves as TPC for more than 90 conferences such as INFOCOM, ICDCS, ICC, GLOBECOM, WCNC, etc. His research areas are security, telemedicine, sensor networks, and wireless networks. He serves as an associate editor or on editorial boards for several journals (such as IEEE Transactions on Vehicular Technology, etc.). He has published more than 200 papers in major journals (more than 50 in various IEEE Journals/magazines), refereed conference proceedings, book chapters related to these research areas. Dr. Xiao s research has been supported by the US National Science Foundation (NSF).
Dynamic Framed Slotted ALOHA Algorithms using Fast Tag Estimation Method for RFID System
 Dynamic Framed Slotted AOHA Algorithms using Fast Tag Estimation Method for RFID System Jae-Ryong Cha School of Electrical and Computer Engineering Ajou Univ., Suwon, Korea builder@ajou.ac.kr Jae-Hyun
Dynamic Framed Slotted AOHA Algorithms using Fast Tag Estimation Method for RFID System Jae-Ryong Cha School of Electrical and Computer Engineering Ajou Univ., Suwon, Korea builder@ajou.ac.kr Jae-Hyun
DiCa: Distributed Tag Access with Collision-Avoidance among Mobile RFID Readers
 DiCa: Distributed Tag Access with Collision-Avoidance among Mobile RFID Readers Kwang-il Hwang, Kyung-tae Kim, and Doo-seop Eom Department of Electronics and Computer Engineering, Korea University 5-1ga,
DiCa: Distributed Tag Access with Collision-Avoidance among Mobile RFID Readers Kwang-il Hwang, Kyung-tae Kim, and Doo-seop Eom Department of Electronics and Computer Engineering, Korea University 5-1ga,
Double Time Slot RFID Anti-collision Algorithm based on Gray Code
 Double Time Slot RFID Anti-collision Algorithm based on Gray Code Hongwei Deng 1 School of Computer Science and Technology, Hengyang Normal University; School of Information Science and Engineering, Central
Double Time Slot RFID Anti-collision Algorithm based on Gray Code Hongwei Deng 1 School of Computer Science and Technology, Hengyang Normal University; School of Information Science and Engineering, Central
RFID Systems, an Introduction Sistemi Wireless, a.a. 2013/2014
 RFID Systems, an Introduction Sistemi Wireless, a.a. 2013/2014 Un. of Rome La Sapienza Chiara Petrioli, Gaia Maselli Department of Computer Science University of Rome Sapienza Italy RFID Technology Ø RFID
RFID Systems, an Introduction Sistemi Wireless, a.a. 2013/2014 Un. of Rome La Sapienza Chiara Petrioli, Gaia Maselli Department of Computer Science University of Rome Sapienza Italy RFID Technology Ø RFID
A Memory Efficient Anti-Collision Protocol to Identify Memoryless RFID Tags
 J Inf Process Syst, Vol., No., pp.95~3, March 25 http://dx.doi.org/.3745/jips.3. ISSN 976-93X (Print) ISSN 292-85X (Electronic) A Memory Efficient Anti-Collision Protocol to Identify Memoryless RFID Tags
J Inf Process Syst, Vol., No., pp.95~3, March 25 http://dx.doi.org/.3745/jips.3. ISSN 976-93X (Print) ISSN 292-85X (Electronic) A Memory Efficient Anti-Collision Protocol to Identify Memoryless RFID Tags
840 IEEE TRANSACTIONS ON AUTOMATION SCIENCE AND ENGINEERING, VOL. 7, NO. 4, OCTOBER 2010
 840 IEEE TRANSACTIONS ON AUTOMATION SCIENCE AND ENGINEERING, VOL. 7, NO. 4, OCTOBER 2010 Efficient Estimation and Collision-Group-Based Anticollision Algorithms for Dynamic Frame-Slotted ALOHA in RFID
840 IEEE TRANSACTIONS ON AUTOMATION SCIENCE AND ENGINEERING, VOL. 7, NO. 4, OCTOBER 2010 Efficient Estimation and Collision-Group-Based Anticollision Algorithms for Dynamic Frame-Slotted ALOHA in RFID
Dynamic Tag Estimation for Optimizing Tree Slotted Aloha in RFID Networks
 Dynamic Tag Estimation for Optimizing Tree Slotted Aloha in RFID Networks Gaia Maselli, Chiara Petrioli, Claudio Vicari Computer Science Department Rome University La Sapienza, Italy {maselli, petrioli,
Dynamic Tag Estimation for Optimizing Tree Slotted Aloha in RFID Networks Gaia Maselli, Chiara Petrioli, Claudio Vicari Computer Science Department Rome University La Sapienza, Italy {maselli, petrioli,
ANALYTICAL EVALUATION OF RFID IDENTIFICATION PROTOCOLS. Gaia Maselli
 ANALYTICAL EVALUATION OF RFID IDENTIFICATION PROTOCOLS Gaia Maselli maselli@di.uniroma1.it 2 RFID Technology Ø RFID - Radio Frequency Identification Technology enabling automatic object identification
ANALYTICAL EVALUATION OF RFID IDENTIFICATION PROTOCOLS Gaia Maselli maselli@di.uniroma1.it 2 RFID Technology Ø RFID - Radio Frequency Identification Technology enabling automatic object identification
IoT: lecture 2. Gaia Maselli Dept. of Computer Science. Internet of Things A.A
 IoT: lecture 2 Gaia Maselli Dept. of Computer Science Internet of Things A.A. 17-18 1 Course info Course web page twiki.di.uniroma1.it/twiki/view/reti_avanzate/internetofthings1718 Additional lecturers
IoT: lecture 2 Gaia Maselli Dept. of Computer Science Internet of Things A.A. 17-18 1 Course info Course web page twiki.di.uniroma1.it/twiki/view/reti_avanzate/internetofthings1718 Additional lecturers
Adaptive Splitting Protocols for RFID Tag Collision Arbitration
 Adaptive Splitting Protocols for RFID Tag Collision Arbitration Jihoon Myung Department of Computer Science and Engineering Korea University, Seoul, Korea jmyung@korea.ac.kr Wonjun Lee Department of Computer
Adaptive Splitting Protocols for RFID Tag Collision Arbitration Jihoon Myung Department of Computer Science and Engineering Korea University, Seoul, Korea jmyung@korea.ac.kr Wonjun Lee Department of Computer
Improving Reader Performance of an UHF RFID System Using Frequency Hopping Techniques
 1 Improving Reader Performance of an UHF RFID System Using Frequency Hopping Techniques Ju-Yen Hung and Venkatesh Sarangan *, MSCS 219, Computer Science Department, Oklahoma State University, Stillwater,
1 Improving Reader Performance of an UHF RFID System Using Frequency Hopping Techniques Ju-Yen Hung and Venkatesh Sarangan *, MSCS 219, Computer Science Department, Oklahoma State University, Stillwater,
Dynamic Framed-Slot ALOHA Anti-Collision using Precise Tag Estimation Scheme
 Dynamic Framed-Slot ALOHA Anti-Collision using Precise Tag Estimation Scheme Author Pupunwiwat, Prapassara, Stantic, Bela Published 2010 Conference Title Twenty-First Australasian Database Conference (ADC2010)
Dynamic Framed-Slot ALOHA Anti-Collision using Precise Tag Estimation Scheme Author Pupunwiwat, Prapassara, Stantic, Bela Published 2010 Conference Title Twenty-First Australasian Database Conference (ADC2010)
PAPER Novel Dynamic Framed-Slotted ALOHA Using Litmus Slots in RFID Systems
 IEICE TRANS. COMMUN., VOL.E95 B, NO.4 APRIL 2012 1375 PAPER Novel Dynamic Framed-Slotted ALOHA Using Litmus Slots in RFID Systems Soon-Bin YIM, Jongho PARK, Nonmembers, and Tae-Jin LEE a), Member SUMMARY
IEICE TRANS. COMMUN., VOL.E95 B, NO.4 APRIL 2012 1375 PAPER Novel Dynamic Framed-Slotted ALOHA Using Litmus Slots in RFID Systems Soon-Bin YIM, Jongho PARK, Nonmembers, and Tae-Jin LEE a), Member SUMMARY
Simple, Optimal, Fast, and Robust Wireless Random Medium Access Control
 Simple, Optimal, Fast, and Robust Wireless Random Medium Access Control Jianwei Huang Department of Information Engineering The Chinese University of Hong Kong KAIST-CUHK Workshop July 2009 J. Huang (CUHK)
Simple, Optimal, Fast, and Robust Wireless Random Medium Access Control Jianwei Huang Department of Information Engineering The Chinese University of Hong Kong KAIST-CUHK Workshop July 2009 J. Huang (CUHK)
An Energy-Oriented Collision Arbitration Protocol for Passive RFID Tag Identification
 An Energy-Oriented Collision Arbitration Protocol for Passive RFID Tag Identification Kyongjin Sok 1, Prof. Gon Hong 1, Kwangnam Choe 2, Kinam Sin 3, Changho Kim 4, Chongil Rim 5 1Institute of Information
An Energy-Oriented Collision Arbitration Protocol for Passive RFID Tag Identification Kyongjin Sok 1, Prof. Gon Hong 1, Kwangnam Choe 2, Kinam Sin 3, Changho Kim 4, Chongil Rim 5 1Institute of Information
PULSE: A MAC Protocol for RFID Networks
 PULSE: A MAC Protocol for RFID Networks Shailesh M. Birari and Sridhar Iyer K. R. School of Information Technology Indian Institute of Technology, Powai, Mumbai, India 400 076. (e-mail: shailesh,sri@it.iitb.ac.in)
PULSE: A MAC Protocol for RFID Networks Shailesh M. Birari and Sridhar Iyer K. R. School of Information Technology Indian Institute of Technology, Powai, Mumbai, India 400 076. (e-mail: shailesh,sri@it.iitb.ac.in)
Lecture on Sensor Networks
 Lecture on Sensor Networks Copyright (c) 2008 Dr. Thomas Haenselmann (University of Mannheim, Germany). Permission is granted to copy, distribute and/or modify this document under the terms of the GNU
Lecture on Sensor Networks Copyright (c) 2008 Dr. Thomas Haenselmann (University of Mannheim, Germany). Permission is granted to copy, distribute and/or modify this document under the terms of the GNU
A survey on broadcast protocols in multihop cognitive radio ad hoc network
 A survey on broadcast protocols in multihop cognitive radio ad hoc network Sureshkumar A, Rajeswari M Abstract In the traditional ad hoc network, common channel is present to broadcast control channels
A survey on broadcast protocols in multihop cognitive radio ad hoc network Sureshkumar A, Rajeswari M Abstract In the traditional ad hoc network, common channel is present to broadcast control channels
2. RFID COLISSION AND INTERFERENCE PROBLEMS 1. INTRODUCTION /07/$ IEEE
 Radio Frequency Identification (RFID): Evaluation of the Technology supporting the Development of Program Latihan Khidmat Negara (PLKN) Participants Tracking Application 1 Datuk Prof. Ishak Ismail, 2 George
Radio Frequency Identification (RFID): Evaluation of the Technology supporting the Development of Program Latihan Khidmat Negara (PLKN) Participants Tracking Application 1 Datuk Prof. Ishak Ismail, 2 George
Utilization Based Duty Cycle Tuning MAC Protocol for Wireless Sensor Networks
 Utilization Based Duty Cycle Tuning MAC Protocol for Wireless Sensor Networks Shih-Hsien Yang, Hung-Wei Tseng, Eric Hsiao-Kuang Wu, and Gen-Huey Chen Dept. of Computer Science and Information Engineering,
Utilization Based Duty Cycle Tuning MAC Protocol for Wireless Sensor Networks Shih-Hsien Yang, Hung-Wei Tseng, Eric Hsiao-Kuang Wu, and Gen-Huey Chen Dept. of Computer Science and Information Engineering,
Scheduling Data Collection with Dynamic Traffic Patterns in Wireless Sensor Networks
 Scheduling Data Collection with Dynamic Traffic Patterns in Wireless Sensor Networks Wenbo Zhao and Xueyan Tang School of Computer Engineering, Nanyang Technological University, Singapore 639798 Email:
Scheduling Data Collection with Dynamic Traffic Patterns in Wireless Sensor Networks Wenbo Zhao and Xueyan Tang School of Computer Engineering, Nanyang Technological University, Singapore 639798 Email:
RFID Multi-hop Relay Algorithms with Active Relay Tags in Tag-Talks-First Mode
 International Journal of Networking and Computing www.ijnc.org ISSN 2185-2839 (print) ISSN 2185-2847 (online) Volume 4, Number 2, pages 355 368, July 2014 RFID Multi-hop Relay Algorithms with Active Relay
International Journal of Networking and Computing www.ijnc.org ISSN 2185-2839 (print) ISSN 2185-2847 (online) Volume 4, Number 2, pages 355 368, July 2014 RFID Multi-hop Relay Algorithms with Active Relay
Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks
 Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks Mariam Kaynia and Nihar Jindal Dept. of Electrical and Computer Engineering, University of Minnesota Dept. of Electronics and Telecommunications,
Performance of ALOHA and CSMA in Spatially Distributed Wireless Networks Mariam Kaynia and Nihar Jindal Dept. of Electrical and Computer Engineering, University of Minnesota Dept. of Electronics and Telecommunications,
Politecnico di Milano Advanced Network Technologies Laboratory. Radio Frequency Identification
 Politecnico di Milano Advanced Network Technologies Laboratory Radio Frequency Identification RFID in Nutshell o To Enhance the concept of bar-codes for faster identification of assets (goods, people,
Politecnico di Milano Advanced Network Technologies Laboratory Radio Frequency Identification RFID in Nutshell o To Enhance the concept of bar-codes for faster identification of assets (goods, people,
Managing the Number of Tag Bits Transmitted in a Bit-Tracking RFID Collision Resolution Protocol
 Sensors 24, 4, -27; doi:.339/s4 Article OPEN ACCESS sensors ISSN 424-822 www.mdpi.com/journal/sensors Managing the Number of Tag Bits Transmitted in a Bit-Tracking RFID Collision Resolution Protocol Hugo
Sensors 24, 4, -27; doi:.339/s4 Article OPEN ACCESS sensors ISSN 424-822 www.mdpi.com/journal/sensors Managing the Number of Tag Bits Transmitted in a Bit-Tracking RFID Collision Resolution Protocol Hugo
Fairness Matters: Identification of Active RFID Tags with Statistically Guaranteed Fairness
 Fairness Matters: Identification of Active RFID Tags with Statistically Guaranteed Fairness Muhammad Shahzad Department of Computer Science North Carolina State University Raleigh, NC, USA mshahza@ncsu.edu
Fairness Matters: Identification of Active RFID Tags with Statistically Guaranteed Fairness Muhammad Shahzad Department of Computer Science North Carolina State University Raleigh, NC, USA mshahza@ncsu.edu
An Adaptive Multichannel Protocol for Large scale Machine-to-Machine (M2M) Networks
 1 An Adaptive Multichannel Protocol for Large scale Machine-to-Machine (MM) Networks Chen-Yu Hsu, Chi-Hsien Yen, and Chun-Ting Chou Department of Electrical Engineering National Taiwan University {b989117,
1 An Adaptive Multichannel Protocol for Large scale Machine-to-Machine (MM) Networks Chen-Yu Hsu, Chi-Hsien Yen, and Chun-Ting Chou Department of Electrical Engineering National Taiwan University {b989117,
Politecnico di Milano Advanced Network Technologies Laboratory. Radio Frequency Identification
 Politecnico di Milano Advanced Network Technologies Laboratory Radio Frequency Identification 1 RFID in Nutshell o To Enhance the concept of bar-codes for faster identification of assets (goods, people,
Politecnico di Milano Advanced Network Technologies Laboratory Radio Frequency Identification 1 RFID in Nutshell o To Enhance the concept of bar-codes for faster identification of assets (goods, people,
Medium Access Control via Nearest-Neighbor Interactions for Regular Wireless Networks
 Medium Access Control via Nearest-Neighbor Interactions for Regular Wireless Networks Ka Hung Hui, Dongning Guo and Randall A. Berry Department of Electrical Engineering and Computer Science Northwestern
Medium Access Control via Nearest-Neighbor Interactions for Regular Wireless Networks Ka Hung Hui, Dongning Guo and Randall A. Berry Department of Electrical Engineering and Computer Science Northwestern
Local Area Networks NETW 901
 Local Area Networks NETW 901 Lecture 2 Medium Access Control (MAC) Schemes Course Instructor: Dr. Ing. Maggie Mashaly maggie.ezzat@guc.edu.eg C3.220 1 Contents Why Multiple Access Random Access Aloha Slotted
Local Area Networks NETW 901 Lecture 2 Medium Access Control (MAC) Schemes Course Instructor: Dr. Ing. Maggie Mashaly maggie.ezzat@guc.edu.eg C3.220 1 Contents Why Multiple Access Random Access Aloha Slotted
An Anti-Collision Algorithm for RFID Based on an Array and Encoding Scheme
 information Article An Anti-Collision Algorithm for RFID Based on an Array and Encoding Scheme Baolong Liu * and Xiaohao Su School Computing Science & Engineering, Xi an Technological University, Xi an
information Article An Anti-Collision Algorithm for RFID Based on an Array and Encoding Scheme Baolong Liu * and Xiaohao Su School Computing Science & Engineering, Xi an Technological University, Xi an
Outline. EEC-484/584 Computer Networks. Homework #1. Homework #1. Lecture 8. Wenbing Zhao Homework #1 Review
 EEC-484/584 Computer Networks Lecture 8 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline Homework #1 Review Protocol verification Example
EEC-484/584 Computer Networks Lecture 8 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline Homework #1 Review Protocol verification Example
Energy-Aware Tag Anti-Collision Protocols for RFID Systems
 Energy-ware Tag nti-ollision Protocols for RID Systems Vinod Namboodiri, Lixin Gao Department of Electrical and omputer Engineering University of Massachusetts at mherst Email: {vnambood, lgao}@ecs.umass.edu
Energy-ware Tag nti-ollision Protocols for RID Systems Vinod Namboodiri, Lixin Gao Department of Electrical and omputer Engineering University of Massachusetts at mherst Email: {vnambood, lgao}@ecs.umass.edu
Bit Reversal Broadcast Scheduling for Ad Hoc Systems
 Bit Reversal Broadcast Scheduling for Ad Hoc Systems Marcin Kik, Maciej Gebala, Mirosław Wrocław University of Technology, Poland IDCS 2013, Hangzhou How to broadcast efficiently? Broadcasting ad hoc systems
Bit Reversal Broadcast Scheduling for Ad Hoc Systems Marcin Kik, Maciej Gebala, Mirosław Wrocław University of Technology, Poland IDCS 2013, Hangzhou How to broadcast efficiently? Broadcasting ad hoc systems
Performance Analysis of Sensor Nodes in a WSN With Sleep/Wakeup Protocol
 The Ninth International Symposium on Operations Research and Its Applications ISORA 10) Chengdu-Jiuzhaigou, China, August 19 23, 2010 Copyright 2010 ORSC & APORC, pp. 370 377 Performance Analysis of Sensor
The Ninth International Symposium on Operations Research and Its Applications ISORA 10) Chengdu-Jiuzhaigou, China, August 19 23, 2010 Copyright 2010 ORSC & APORC, pp. 370 377 Performance Analysis of Sensor
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS
 TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
TIME- OPTIMAL CONVERGECAST IN SENSOR NETWORKS WITH MULTIPLE CHANNELS A Thesis by Masaaki Takahashi Bachelor of Science, Wichita State University, 28 Submitted to the Department of Electrical Engineering
Fast RFID Polling Protocols
 Fast RFID Polling Protocols Jia Liu, Bin Xiao, Xuan Liu and Lijun Chen State Key Laboratory for Novel Software Technology, Nanjing University, China Department of Computing, The Hong Kong Polytechnic University,
Fast RFID Polling Protocols Jia Liu, Bin Xiao, Xuan Liu and Lijun Chen State Key Laboratory for Novel Software Technology, Nanjing University, China Department of Computing, The Hong Kong Polytechnic University,
Analysis of BFSA Based Anti-Collision Protocol in LF, HF, and UHF RFID Environments
 UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2014 Analysis of BFSA Based Anti-Collision Protocol in LF, HF, and UHF RFID Environments Varun Bhogal University of North Florida Suggested
UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2014 Analysis of BFSA Based Anti-Collision Protocol in LF, HF, and UHF RFID Environments Varun Bhogal University of North Florida Suggested
Cardinality Estimation for Large-scale RFID Systems
 IEEE TRANSACTION ON, VOL., NO., MON YEAR 1 Cardinality Estimation for Large-scale RFID Systems Chen Qian, Student Member, IEEE, Hoilun Ngan, Student Member, IEEE, Yunhao Liu, Senior Member, IEEE, Lionel
IEEE TRANSACTION ON, VOL., NO., MON YEAR 1 Cardinality Estimation for Large-scale RFID Systems Chen Qian, Student Member, IEEE, Hoilun Ngan, Student Member, IEEE, Yunhao Liu, Senior Member, IEEE, Lionel
Performance Limits of Fair-Access in Sensor Networks with Linear and Selected Grid Topologies John Gibson * Geoffrey G.
 In proceedings of GLOBECOM Ad Hoc and Sensor Networking Symposium, Washington DC, November 7 Performance Limits of Fair-Access in Sensor Networks with Linear and Selected Grid Topologies John Gibson *
In proceedings of GLOBECOM Ad Hoc and Sensor Networking Symposium, Washington DC, November 7 Performance Limits of Fair-Access in Sensor Networks with Linear and Selected Grid Topologies John Gibson *
Energy-Efficient MANET Routing: Ideal vs. Realistic Performance
 Energy-Efficient MANET Routing: Ideal vs. Realistic Performance Paper by: Thomas Knuz IEEE IWCMC Conference Aug. 2008 Presented by: Farzana Yasmeen For : CSE 6590 2013.11.12 Contents Introduction Review:
Energy-Efficient MANET Routing: Ideal vs. Realistic Performance Paper by: Thomas Knuz IEEE IWCMC Conference Aug. 2008 Presented by: Farzana Yasmeen For : CSE 6590 2013.11.12 Contents Introduction Review:
Energy-Efficient Random Access for Machine- to-machine (M2M) Communications
 Energy-Efficient Random Access for achine- to-achine (2) Communications Hano Wang 1 and Choongchae Woo 2 1 Information and Telecommunication Engineering, Sangmyung University, 2 Electronics, Computer and
Energy-Efficient Random Access for achine- to-achine (2) Communications Hano Wang 1 and Choongchae Woo 2 1 Information and Telecommunication Engineering, Sangmyung University, 2 Electronics, Computer and
A GRASP HEURISTIC FOR THE COOPERATIVE COMMUNICATION PROBLEM IN AD HOC NETWORKS
 A GRASP HEURISTIC FOR THE COOPERATIVE COMMUNICATION PROBLEM IN AD HOC NETWORKS C. COMMANDER, C.A.S. OLIVEIRA, P.M. PARDALOS, AND M.G.C. RESENDE ABSTRACT. Ad hoc networks are composed of a set of wireless
A GRASP HEURISTIC FOR THE COOPERATIVE COMMUNICATION PROBLEM IN AD HOC NETWORKS C. COMMANDER, C.A.S. OLIVEIRA, P.M. PARDALOS, AND M.G.C. RESENDE ABSTRACT. Ad hoc networks are composed of a set of wireless
A Novel Anti-Collision Algorithm for High-Density RFID Tags
 A Novel Anti-Collision Algorithm for High-Density RFID s 33 A Novel Anti-Collision Algorithm for High-Density RFID s Sarawut Makwimanloy 1, Piya Kovintavewat 2, Urachada Ketprom 3, and Charturong Tantibundhit
A Novel Anti-Collision Algorithm for High-Density RFID s 33 A Novel Anti-Collision Algorithm for High-Density RFID s Sarawut Makwimanloy 1, Piya Kovintavewat 2, Urachada Ketprom 3, and Charturong Tantibundhit
Analysis of Power Assignment in Radio Networks with Two Power Levels
 Analysis of Power Assignment in Radio Networks with Two Power Levels Miguel Fiandor Gutierrez & Manuel Macías Córdoba Abstract. In this paper we analyze the Power Assignment in Radio Networks with Two
Analysis of Power Assignment in Radio Networks with Two Power Levels Miguel Fiandor Gutierrez & Manuel Macías Córdoba Abstract. In this paper we analyze the Power Assignment in Radio Networks with Two
Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks
 Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks Ying Dai and Jie Wu Department of Computer and Information Sciences Temple University, Philadelphia, PA 19122 Email: {ying.dai,
Sense in Order: Channel Selection for Sensing in Cognitive Radio Networks Ying Dai and Jie Wu Department of Computer and Information Sciences Temple University, Philadelphia, PA 19122 Email: {ying.dai,
An Adaptive Multichannel Protocol for Large-Scale Machine-to-Machine (M2M) Networks
 An Adaptive Multichannel Protocol for Large-Scale Machine-to-Machine (MM) Networks Chen-Yu Hsu, Chi-Hsien Yen, and Chun-Ting Chou Department of Electrical Engineering National Taiwan University Intel-NTU
An Adaptive Multichannel Protocol for Large-Scale Machine-to-Machine (MM) Networks Chen-Yu Hsu, Chi-Hsien Yen, and Chun-Ting Chou Department of Electrical Engineering National Taiwan University Intel-NTU
Time-Efficient Protocols for Neighbor Discovery in Wireless Ad Hoc Networks
 1 Time-Efficient Protocols for Neighbor Discovery in Wireless Ad Hoc Networks Guobao Sun, Student Member, IEEE, Fan Wu, Member, IEEE, Xiaofeng Gao, Member, IEEE, Guihai Chen, Member, IEEE, and Wei Wang,
1 Time-Efficient Protocols for Neighbor Discovery in Wireless Ad Hoc Networks Guobao Sun, Student Member, IEEE, Fan Wu, Member, IEEE, Xiaofeng Gao, Member, IEEE, Guihai Chen, Member, IEEE, and Wei Wang,
Anti-Jamming: A Study
 Anti-Jamming: A Study Karthikeyan Mahadevan, Sojeong Hong, John Dullum December 14, 25 Abstract Addressing jamming in wireless networks is important as the number of wireless networks is on the increase.
Anti-Jamming: A Study Karthikeyan Mahadevan, Sojeong Hong, John Dullum December 14, 25 Abstract Addressing jamming in wireless networks is important as the number of wireless networks is on the increase.
doc.: IEEE d IEEE P Wireless Personal Area Networks
 August, 2008 doc.: IEEE 802. 15-08-0578-00-004d IEEE P802.15 Wireless Personal Area Networks Project Title IEEE P802.15 Working Group for Wireless Personal Area Networks (WPANs) English transl ation ofarib
August, 2008 doc.: IEEE 802. 15-08-0578-00-004d IEEE P802.15 Wireless Personal Area Networks Project Title IEEE P802.15 Working Group for Wireless Personal Area Networks (WPANs) English transl ation ofarib
Mobility Tolerant Broadcast in Mobile Ad Hoc Networks
 Mobility Tolerant Broadcast in Mobile Ad Hoc Networks Pradip K Srimani 1 and Bhabani P Sinha 2 1 Department of Computer Science, Clemson University, Clemson, SC 29634 0974 2 Electronics Unit, Indian Statistical
Mobility Tolerant Broadcast in Mobile Ad Hoc Networks Pradip K Srimani 1 and Bhabani P Sinha 2 1 Department of Computer Science, Clemson University, Clemson, SC 29634 0974 2 Electronics Unit, Indian Statistical
Cross Layer Design for Localization in Large-Scale Underwater Sensor Networks
 Sensors & Transducers, Vol. 64, Issue 2, February 204, pp. 49-54 Sensors & Transducers 204 by IFSA Publishing, S. L. http://www.sensorsportal.com Cross Layer Design for Localization in Large-Scale Underwater
Sensors & Transducers, Vol. 64, Issue 2, February 204, pp. 49-54 Sensors & Transducers 204 by IFSA Publishing, S. L. http://www.sensorsportal.com Cross Layer Design for Localization in Large-Scale Underwater
Randomized Channel Access Reduces Network Local Delay
 Randomized Channel Access Reduces Network Local Delay Wenyi Zhang USTC Joint work with Yi Zhong (Ph.D. student) and Martin Haenggi (Notre Dame) 2013 Joint HK/TW Workshop on ITC CUHK, January 19, 2013 Acknowledgement
Randomized Channel Access Reduces Network Local Delay Wenyi Zhang USTC Joint work with Yi Zhong (Ph.D. student) and Martin Haenggi (Notre Dame) 2013 Joint HK/TW Workshop on ITC CUHK, January 19, 2013 Acknowledgement
Framed ALOHA for Multiple RFID Objects Identification
 IEICE TRANS. COMMUN., VOL.E88 B, NO.3 MARCH 2005 991 PAPER Special Section on Ubiquitous Networks Framed ALOHA for Multiple RFID Objects Identification Bin ZHEN a), Mamoru KOBAYASHI b), Nonmembers, and
IEICE TRANS. COMMUN., VOL.E88 B, NO.3 MARCH 2005 991 PAPER Special Section on Ubiquitous Networks Framed ALOHA for Multiple RFID Objects Identification Bin ZHEN a), Mamoru KOBAYASHI b), Nonmembers, and
Research of RFID Tag Anti-collision Algorithm based on Binary Tree
 JOURNAL OF NETWORKS, VOL. 9, NO. 9, SEPTEMBER 2 25 Research of RFID Anti-collision Algorithm based on Binary Tree Bai Zhi and He Yigang College of Electrical and Information Engineering, Hunan University,
JOURNAL OF NETWORKS, VOL. 9, NO. 9, SEPTEMBER 2 25 Research of RFID Anti-collision Algorithm based on Binary Tree Bai Zhi and He Yigang College of Electrical and Information Engineering, Hunan University,
MOBILE COMPUTING 2/25/17. What is RFID? RFID. CSE 40814/60814 Spring Radio Frequency IDentification
 MOBILE COMPUTING CSE 40814/60814 Spring 2017 What is RFID? Radio Frequency IDentification Who Are You? I am Product X RFID ADC (automated data collection) technology that uses radio-frequency waves to
MOBILE COMPUTING CSE 40814/60814 Spring 2017 What is RFID? Radio Frequency IDentification Who Are You? I am Product X RFID ADC (automated data collection) technology that uses radio-frequency waves to
ScienceDirect. Optimal Placement of RFID Antennas for Outdoor Applications
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 236 241 The 9th International Conference on Future Networks and Communications (FNC-2014) Optimal Placement
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 236 241 The 9th International Conference on Future Networks and Communications (FNC-2014) Optimal Placement
Multiple Access Methods
 Helsinki University of Technology S-72.333 Postgraduate Seminar on Radio Communications Multiple Access Methods Er Liu liuer@cc.hut.fi Communications Laboratory 16.11.2004 Content of presentation Protocol
Helsinki University of Technology S-72.333 Postgraduate Seminar on Radio Communications Multiple Access Methods Er Liu liuer@cc.hut.fi Communications Laboratory 16.11.2004 Content of presentation Protocol
DEGRADED broadcast channels were first studied by
 4296 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 54, NO 9, SEPTEMBER 2008 Optimal Transmission Strategy Explicit Capacity Region for Broadcast Z Channels Bike Xie, Student Member, IEEE, Miguel Griot,
4296 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 54, NO 9, SEPTEMBER 2008 Optimal Transmission Strategy Explicit Capacity Region for Broadcast Z Channels Bike Xie, Student Member, IEEE, Miguel Griot,
Link Activation with Parallel Interference Cancellation in Multi-hop VANET
 Link Activation with Parallel Interference Cancellation in Multi-hop VANET Meysam Azizian, Soumaya Cherkaoui and Abdelhakim Senhaji Hafid Department of Electrical and Computer Engineering, Université de
Link Activation with Parallel Interference Cancellation in Multi-hop VANET Meysam Azizian, Soumaya Cherkaoui and Abdelhakim Senhaji Hafid Department of Electrical and Computer Engineering, Université de
Coding aware routing in wireless networks with bandwidth guarantees. IEEEVTS Vehicular Technology Conference Proceedings. Copyright IEEE.
 Title Coding aware routing in wireless networks with bandwidth guarantees Author(s) Hou, R; Lui, KS; Li, J Citation The IEEE 73rd Vehicular Technology Conference (VTC Spring 2011), Budapest, Hungary, 15-18
Title Coding aware routing in wireless networks with bandwidth guarantees Author(s) Hou, R; Lui, KS; Li, J Citation The IEEE 73rd Vehicular Technology Conference (VTC Spring 2011), Budapest, Hungary, 15-18
Multi-Radio Channel Detecting Jamming Attack Against Enhanced Jump-Stay Based Rendezvous in Cognitive Radio Networks
 Multi-Radio Channel Detecting Jamming Attack Against Enhanced Jump-Stay Based Rendezvous in Cognitive Radio Networks Yang Gao 1, Zhaoquan Gu 1, Qiang-Sheng Hua 2, Hai Jin 2 1 Institute for Interdisciplinary
Multi-Radio Channel Detecting Jamming Attack Against Enhanced Jump-Stay Based Rendezvous in Cognitive Radio Networks Yang Gao 1, Zhaoquan Gu 1, Qiang-Sheng Hua 2, Hai Jin 2 1 Institute for Interdisciplinary
LTE in Unlicensed Spectrum
 LTE in Unlicensed Spectrum Prof. Geoffrey Ye Li School of ECE, Georgia Tech. Email: liye@ece.gatech.edu Website: http://users.ece.gatech.edu/liye/ Contributors: Q.-M. Chen, G.-D. Yu, and A. Maaref Outline
LTE in Unlicensed Spectrum Prof. Geoffrey Ye Li School of ECE, Georgia Tech. Email: liye@ece.gatech.edu Website: http://users.ece.gatech.edu/liye/ Contributors: Q.-M. Chen, G.-D. Yu, and A. Maaref Outline
A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks
 MIC2005: The Sixth Metaheuristics International Conference??-1 A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks Clayton Commander Carlos A.S. Oliveira Panos M. Pardalos Mauricio
MIC2005: The Sixth Metaheuristics International Conference??-1 A GRASP heuristic for the Cooperative Communication Problem in Ad Hoc Networks Clayton Commander Carlos A.S. Oliveira Panos M. Pardalos Mauricio
Lecture 8: Media Access Control. CSE 123: Computer Networks Stefan Savage
 Lecture 8: Media Access Control CSE 123: Computer Networks Stefan Savage Overview Methods to share physical media: multiple access Fixed partitioning Random access Channelizing mechanisms Contention-based
Lecture 8: Media Access Control CSE 123: Computer Networks Stefan Savage Overview Methods to share physical media: multiple access Fixed partitioning Random access Channelizing mechanisms Contention-based
/13/$ IEEE
 A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
A Game-Theoretical Anti-Jamming Scheme for Cognitive Radio Networks Changlong Chen and Min Song, University of Toledo ChunSheng Xin, Old Dominion University Jonathan Backens, Old Dominion University Abstract
Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network
 International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
International Journal Of Computational Engineering Research (ijceronline.com) Vol. 3 Issue. 3 Lightweight Decentralized Algorithm for Localizing Reactive Jammers in Wireless Sensor Network 1, Vinothkumar.G,
Lecture 8: Media Access Control
 Lecture 8: Media Access Control CSE 123: Computer Networks Alex C. Snoeren HW 2 due NEXT WEDNESDAY Overview Methods to share physical media: multiple access Fixed partitioning Random access Channelizing
Lecture 8: Media Access Control CSE 123: Computer Networks Alex C. Snoeren HW 2 due NEXT WEDNESDAY Overview Methods to share physical media: multiple access Fixed partitioning Random access Channelizing
Distributed Broadcast Scheduling in Mobile Ad Hoc Networks with Unknown Topologies
 Distributed Broadcast Scheduling in Mobile Ad Hoc Networks with Unknown Topologies Guang Tan, Stephen A. Jarvis, James W. J. Xue, and Simon D. Hammond Department of Computer Science, University of Warwick,
Distributed Broadcast Scheduling in Mobile Ad Hoc Networks with Unknown Topologies Guang Tan, Stephen A. Jarvis, James W. J. Xue, and Simon D. Hammond Department of Computer Science, University of Warwick,
Lecture 2. 1 Nondeterministic Communication Complexity
 Communication Complexity 16:198:671 1/26/10 Lecture 2 Lecturer: Troy Lee Scribe: Luke Friedman 1 Nondeterministic Communication Complexity 1.1 Review D(f): The minimum over all deterministic protocols
Communication Complexity 16:198:671 1/26/10 Lecture 2 Lecturer: Troy Lee Scribe: Luke Friedman 1 Nondeterministic Communication Complexity 1.1 Review D(f): The minimum over all deterministic protocols
PHED: Pre-Handshaking Neighbor Discovery Protocols in Full Duplex Wireless Ad Hoc Networks
 PHED: Pre-Handshaking Neighbor Discovery Protocols in Full Duplex Wireless Ad Hoc Networks Guobao Sun, Fan Wu, Xiaofeng Gao, and Guihai Chen Shanghai Key Laboratory of Scalable Computing and Systems Department
PHED: Pre-Handshaking Neighbor Discovery Protocols in Full Duplex Wireless Ad Hoc Networks Guobao Sun, Fan Wu, Xiaofeng Gao, and Guihai Chen Shanghai Key Laboratory of Scalable Computing and Systems Department
Efficient rekeying algorithms for WiMAX networks
 SECURITY AND COMMUNICATION NETWORKS Security Comm. Networks. 2009; 2:392 400 Published online 30 July 2009 in Wiley InterScience (www.interscience.wiley.com).124 Efficient rekeying algorithms for WiMAX
SECURITY AND COMMUNICATION NETWORKS Security Comm. Networks. 2009; 2:392 400 Published online 30 July 2009 in Wiley InterScience (www.interscience.wiley.com).124 Efficient rekeying algorithms for WiMAX
Performance Analysis of Energy Consumption of AFECA in Wireless Sensor Networks
 Proceedings of the World Congress on Engineering 2 Vol II WCE 2, July 6-8, 2, London, U.K. Performance Analysis of Energy Consumption of AFECA in Wireless Sensor Networks Yun Won Chung Abstract Energy
Proceedings of the World Congress on Engineering 2 Vol II WCE 2, July 6-8, 2, London, U.K. Performance Analysis of Energy Consumption of AFECA in Wireless Sensor Networks Yun Won Chung Abstract Energy
Fine-grained Channel Access in Wireless LAN. Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012
 Fine-grained Channel Access in Wireless LAN Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012 Physical-layer data rate PHY layer data rate in WLANs is increasing rapidly Wider channel
Fine-grained Channel Access in Wireless LAN Cristian Petrescu Arvind Jadoo UCL Computer Science 20 th March 2012 Physical-layer data rate PHY layer data rate in WLANs is increasing rapidly Wider channel
Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes
 7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
Low-Latency Multi-Source Broadcast in Radio Networks
 Low-Latency Multi-Source Broadcast in Radio Networks Scott C.-H. Huang City University of Hong Kong Hsiao-Chun Wu Louisiana State University and S. S. Iyengar Louisiana State University In recent years
Low-Latency Multi-Source Broadcast in Radio Networks Scott C.-H. Huang City University of Hong Kong Hsiao-Chun Wu Louisiana State University and S. S. Iyengar Louisiana State University In recent years
Taxonomy and survey of RFID anti-collision protocols
 Computer Communications 29 (2006) 2150 2166 Short survey Taxonomy and survey of RFID anti-collision protocols Dong-Her Shih a, Po-Ling Sun a, David C. Yen b, *, Shi-Ming Huang c a Department of Information
Computer Communications 29 (2006) 2150 2166 Short survey Taxonomy and survey of RFID anti-collision protocols Dong-Her Shih a, Po-Ling Sun a, David C. Yen b, *, Shi-Ming Huang c a Department of Information
Fault-tolerant Coverage in Dense Wireless Sensor Networks
 Fault-tolerant Coverage in Dense Wireless Sensor Networks Akshaye Dhawan and Magdalena Parks Department of Mathematics and Computer Science, Ursinus College, 610 E Main Street, Collegeville, PA, USA {adhawan,
Fault-tolerant Coverage in Dense Wireless Sensor Networks Akshaye Dhawan and Magdalena Parks Department of Mathematics and Computer Science, Ursinus College, 610 E Main Street, Collegeville, PA, USA {adhawan,
Cooperative anti-collision algorithm based on relay sensor in RFID system Xinxian Li, Xiaoling Sun2, b, Weiqin Li2, c, Daisong Shi2, d
 rd International Conference on Materials Engineering, Manufacturing Technology and Control (ICMEMTC 0) Cooperative anti-collision algorithm based on relay sensor in RFID system, a Xinxian Li, Xiaoling
rd International Conference on Materials Engineering, Manufacturing Technology and Control (ICMEMTC 0) Cooperative anti-collision algorithm based on relay sensor in RFID system, a Xinxian Li, Xiaoling
TSIN01 Information Networks Lecture 9
 TSIN01 Information Networks Lecture 9 Danyo Danev Division of Communication Systems Department of Electrical Engineering Linköping University, Sweden September 26 th, 2017 Danyo Danev TSIN01 Information
TSIN01 Information Networks Lecture 9 Danyo Danev Division of Communication Systems Department of Electrical Engineering Linköping University, Sweden September 26 th, 2017 Danyo Danev TSIN01 Information
FPGA-BASED DESIGN AND IMPLEMENTATION OF THREE-PRIORITY PERSISTENT CSMA PROTOCOL
 U.P.B. Sci. Bull., Series C, Vol. 79, Iss. 4, 2017 ISSN 2286-3540 FPGA-BASED DESIGN AND IMPLEMENTATION OF THREE-PRIORITY PERSISTENT CSMA PROTOCOL Xu ZHI 1, Ding HONGWEI 2, Liu LONGJUN 3, Bao LIYONG 4,
U.P.B. Sci. Bull., Series C, Vol. 79, Iss. 4, 2017 ISSN 2286-3540 FPGA-BASED DESIGN AND IMPLEMENTATION OF THREE-PRIORITY PERSISTENT CSMA PROTOCOL Xu ZHI 1, Ding HONGWEI 2, Liu LONGJUN 3, Bao LIYONG 4,
Department of Computer Science and Engineering. CSE 3213: Computer Networks I (Fall 2009) Instructor: N. Vlajic Date: Dec 11, 2009.
 Department of Computer Science and Engineering CSE 3213: Computer Networks I (Fall 2009) Instructor: N. Vlajic Date: Dec 11, 2009 Final Examination Instructions: Examination time: 180 min. Print your name
Department of Computer Science and Engineering CSE 3213: Computer Networks I (Fall 2009) Instructor: N. Vlajic Date: Dec 11, 2009 Final Examination Instructions: Examination time: 180 min. Print your name
End-to-End Known-Interference Cancellation (E2E-KIC) with Multi-Hop Interference
 End-to-End Known-Interference Cancellation (EE-KIC) with Multi-Hop Interference Shiqiang Wang, Qingyang Song, Kailai Wu, Fanzhao Wang, Lei Guo School of Computer Science and Engnineering, Northeastern
End-to-End Known-Interference Cancellation (EE-KIC) with Multi-Hop Interference Shiqiang Wang, Qingyang Song, Kailai Wu, Fanzhao Wang, Lei Guo School of Computer Science and Engnineering, Northeastern
A Greedy Algorithm for Target Coverage Scheduling in Directional Sensor Networks
 A Greedy Algorithm for Target Coverage Scheduling in Directional Sensor Networks Youn-Hee Han, Chan-Myung Kim Laboratory of Intelligent Networks Advanced Technology Research Center Korea University of
A Greedy Algorithm for Target Coverage Scheduling in Directional Sensor Networks Youn-Hee Han, Chan-Myung Kim Laboratory of Intelligent Networks Advanced Technology Research Center Korea University of
Channel Sensing Order in Multi-user Cognitive Radio Networks
 2012 IEEE International Symposium on Dynamic Spectrum Access Networks Channel Sensing Order in Multi-user Cognitive Radio Networks Jie Zhao and Xin Wang Department of Electrical and Computer Engineering
2012 IEEE International Symposium on Dynamic Spectrum Access Networks Channel Sensing Order in Multi-user Cognitive Radio Networks Jie Zhao and Xin Wang Department of Electrical and Computer Engineering
Performance Evaluation of DV-Hop and NDV-Hop Localization Methods in Wireless Sensor Networks
 Performance Evaluation of DV-Hop and NDV-Hop Localization Methods in Wireless Sensor Networks Manijeh Keshtgary Dept. of Computer Eng. & IT ShirazUniversity of technology Shiraz,Iran, Keshtgari@sutech.ac.ir
Performance Evaluation of DV-Hop and NDV-Hop Localization Methods in Wireless Sensor Networks Manijeh Keshtgary Dept. of Computer Eng. & IT ShirazUniversity of technology Shiraz,Iran, Keshtgari@sutech.ac.ir
Hierarchical Agglomerative Aggregation Scheduling in Directional Wireless Sensor Networks
 Hierarchical Agglomerative Aggregation Scheduling in Directional Wireless Sensor Networks Min Kyung An Department of Computer Science Sam Houston State University Huntsville, Texas 77341, USA Email: an@shsu.edu
Hierarchical Agglomerative Aggregation Scheduling in Directional Wireless Sensor Networks Min Kyung An Department of Computer Science Sam Houston State University Huntsville, Texas 77341, USA Email: an@shsu.edu
The Z Channel. Nihar Jindal Department of Electrical Engineering Stanford University, Stanford, CA
 The Z Channel Sriram Vishwanath Dept. of Elec. and Computer Engg. Univ. of Texas at Austin, Austin, TX E-mail : sriram@ece.utexas.edu Nihar Jindal Department of Electrical Engineering Stanford University,
The Z Channel Sriram Vishwanath Dept. of Elec. and Computer Engg. Univ. of Texas at Austin, Austin, TX E-mail : sriram@ece.utexas.edu Nihar Jindal Department of Electrical Engineering Stanford University,
Self-Stabilizing Deterministic TDMA for Sensor Networks
 Self-Stabilizing Deterministic TDMA for Sensor Networks Mahesh Arumugam Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory Department of Computer Science and Engineering Michigan State
Self-Stabilizing Deterministic TDMA for Sensor Networks Mahesh Arumugam Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory Department of Computer Science and Engineering Michigan State
A survey and tutorial of RFID anti-collision protocols
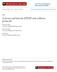 University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 A survey and tutorial of RFID anti-collision protocols Dheeraj K.
University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 A survey and tutorial of RFID anti-collision protocols Dheeraj K.
Analyzing Split Channel Medium Access Control Schemes
 IEEE TRANS. ON WIRELESS COMMNICATIONS, TO APPEAR Analyzing Split Channel Medium Access Control Schemes Jing Deng, Member, IEEE, Yunghsiang S. Han, Member, IEEE, and Zygmunt J. Haas, Senior Member, IEEE
IEEE TRANS. ON WIRELESS COMMNICATIONS, TO APPEAR Analyzing Split Channel Medium Access Control Schemes Jing Deng, Member, IEEE, Yunghsiang S. Han, Member, IEEE, and Zygmunt J. Haas, Senior Member, IEEE
Cryptanalysis of an Improved One-Way Hash Chain Self-Healing Group Key Distribution Scheme
 Cryptanalysis of an Improved One-Way Hash Chain Self-Healing Group Key Distribution Scheme Yandong Zheng 1, Hua Guo 1 1 State Key Laboratory of Software Development Environment, Beihang University Beiing
Cryptanalysis of an Improved One-Way Hash Chain Self-Healing Group Key Distribution Scheme Yandong Zheng 1, Hua Guo 1 1 State Key Laboratory of Software Development Environment, Beihang University Beiing
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks. Nathan Balon and Jinhua Guo University of Michigan - Dearborn
 Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Increasing Broadcast Reliability for Vehicular Ad Hoc Networks Nathan Balon and Jinhua Guo University of Michigan - Dearborn I n t r o d u c t i o n General Information on VANETs Background on 802.11 Background
Multi-Band Spectrum Allocation Algorithm Based on First-Price Sealed Auction
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 17, No 1 Sofia 2017 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.1515/cait-2017-0008 Multi-Band Spectrum Allocation
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 17, No 1 Sofia 2017 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.1515/cait-2017-0008 Multi-Band Spectrum Allocation
Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks
 Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks Yuqun Zhang, Chen-Hsiang Feng, Ilker Demirkol, Wendi B. Heinzelman Department of Electrical and Computer
Energy-Efficient Duty Cycle Assignment for Receiver-Based Convergecast in Wireless Sensor Networks Yuqun Zhang, Chen-Hsiang Feng, Ilker Demirkol, Wendi B. Heinzelman Department of Electrical and Computer
A Fast Initialization Algorithm for Single-Hop Wireless Networks
 A Fast Initialization Algorithm for ingle-hop Wireless Networks hyue-horng hiau hang-biau Yang Department of omputer cience and Engineering National un Yat-sen University Kaohsiung, Taiwan 804, R.O.. shiaush@cse.nsysu.edu.tw
A Fast Initialization Algorithm for ingle-hop Wireless Networks hyue-horng hiau hang-biau Yang Department of omputer cience and Engineering National un Yat-sen University Kaohsiung, Taiwan 804, R.O.. shiaush@cse.nsysu.edu.tw
Collision Avoidance in a Dense RFID Network
 Collision Avoidance in a Dense RFID Network Shweta Jain Computer Science Department Stony Brook University Stony Brook, NY shweta@cs.sunysb.edu Samir R. Das Computer Science Department Stony Brook University
Collision Avoidance in a Dense RFID Network Shweta Jain Computer Science Department Stony Brook University Stony Brook, NY shweta@cs.sunysb.edu Samir R. Das Computer Science Department Stony Brook University
DOPPLER SHIFT. Thus, the frequency of the received signal is
 DOPPLER SHIFT Radio Propagation Doppler Effect: When a wave source and a receiver are moving towards each other, the frequency of the received signal will not be the same as the source. When they are moving
DOPPLER SHIFT Radio Propagation Doppler Effect: When a wave source and a receiver are moving towards each other, the frequency of the received signal will not be the same as the source. When they are moving
3644 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 6, JUNE 2011
 3644 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 6, JUNE 2011 Asynchronous CSMA Policies in Multihop Wireless Networks With Primary Interference Constraints Peter Marbach, Member, IEEE, Atilla
3644 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 57, NO. 6, JUNE 2011 Asynchronous CSMA Policies in Multihop Wireless Networks With Primary Interference Constraints Peter Marbach, Member, IEEE, Atilla
Preamble MAC Protocols with Non-persistent Receivers in Wireless Sensor Networks
 Preamble MAC Protocols with Non-persistent Receivers in Wireless Sensor Networks Abdelmalik Bachir, Martin Heusse, and Andrzej Duda Grenoble Informatics Laboratory, Grenoble, France Abstract. In preamble
Preamble MAC Protocols with Non-persistent Receivers in Wireless Sensor Networks Abdelmalik Bachir, Martin Heusse, and Andrzej Duda Grenoble Informatics Laboratory, Grenoble, France Abstract. In preamble
