RAISE - A Raw Images Dataset for Digital Image Forensics
|
|
|
- Barbra Heath
- 5 years ago
- Views:
Transcription
1 RAISE - A Raw Images Dataset for Digital Image Forensics Duc-Tien Dang-Nguyen 1, Cecilia Pasquini 2, Valentina Conotter 2, Giulia Boato 2 1 DIEE - University of Cagliari, Italy 2 DISI - University of Trento, Italy ductien.dangnguyen@diee.unica.it, cecilia.pasquini@unitn.it, {conotter, boato}@disi.unitn.it ABSTRACT Digital forensics is a relatively new research area which aims at authenticating digital media by detecting possible digital forgeries. Indeed, the ever increasing availability of multimedia data on the web, coupled with the great advances reached by computer graphical tools, makes the modification of an image and the creation of visually compelling forgeries an easy task for any user. This in turns creates the need of reliable tools to validate the trustworthiness of the represented information. In such a context, we present here RAISE, a large dataset of 8156 high-resolution raw images, depicting various subjects and scenarios, properly annotated and available together with accompanying metadata. Such a wide collection of untouched and diverse data is intended to become a powerful resource for, but not limited to, forensic researchers by providing a common benchmark for a fair comparison, testing and evaluation of existing and next generation forensic algorithms. In this paper we describe how RAISE has been collected and organized, discuss how digital image forensics and many other multimedia research areas may benefit of this new publicly available benchmark dataset and test a very recent forensic technique for JPEG compression detection. Categories and Subject Descriptors H.3.7 [Digital Libraries]: Collection, dissemination; H.2.8 [Database applications]: Image database General Terms Experimentation; Security Keywords Data Set, Raw Images, Benchmark, Image Forensics 1. INTRODUCTION Thanks to the worldwide spreading of smart portable devices, every day an enormous amount of digital multimedia information is created, stored and shared among peer users (a) Original version. (b) Modified version. Figure 1: Both photos depict the construction site of the hydroelectric dam of Belo Monte, Brazil. The modified version on the right was used by The Spiegel newspaper in 2013, in an article evaluating the environmental impact of the structure. by means of social media, web portals, apps. Such tools enable the diffusion of user-generated multimedia contents in an extremely easy, fast and wide manner, providing the chance for anybody to disseminate images, video and audio tracks. However, the authenticity and trustworthiness of such multimedia data cannot be given for granted, as low-cost and user-friendly editing software allow nowadays for easy manipulations of such material even by non-expert people. Considering also the more intuitive and immediate impact of visual data with respect to textual documents, the potential diffusion of distorted or completely fake multimedia content on websites, information media, advertisement and legal proceedings represents an urgent issue to be addressed. Thus, the trustworthiness of such data has to be seriously assessed, so to avoid an illegitimate exploitation, be it malicious or not, of the semantic message they may convey. Fig. 1 serves as an example to show how digital modification may influence the users opinion towards a given topic. In particular, in panel (a) is the original image of the construction site for the Belo Monte Dam in Brazil, while in panel (b) is its digitally altered version, where the visual impact of the image is clearly altered to look more degradated due to the social and environmental consequences of the construction of the hydroelectric dam. Recently, the debate about the role of visual content manipulation used online has significantly attracted the attention of the international community 1, questioning the way that the use of manipulated images impacts users perceptions [5, 20]. Over the last decade, the field of digital multimedia forensics has emerged as a valuable mean for assessing and verifying 1
2 image trustworthiness, by developing passive techniques for a blind authentication of images (different from active techniques like [2]), videos and audio recordings. The idea behind digital forensics is that different kinds of processing will leave subtle specific numerical and statistical traces into the digital data, which can be detected and used as evidence of possible forgeries [8]. Although research on audio and video forensics is also gaining increasing attention, the study of images plays a central role in this field, addressing different goals, such as the detection of potential modifications applied to the content (e.g., splicing, enhancement, compression), the identification of the source device that created it (e.g., camera brand and model), or the differentiation between contents physically recorded by a device or generated by means of computer graphics software (see, e.g., [4, 6, 15, 17] and references therein). Given the wide variety of potential manipulations and the actual lack of a universal forensic framework, each forensic technique usually targets a single class of processing operations and needs to be carefully assessed under a number of controlled experimental settings (where order and parameters of different operations have to be known), in order to properly understand its potential effectiveness in a realworld scenario. Thus, images in raw uncompressed formats are extensively used in forensic research since their pristine condition is a valuable and essential starting point for building the testing sets needed, as it happens for the widely used UCID database [19]. To this extent, in this paper we present RAISE (RAw ImageS dataset), a new collection of 8156 raw images including a wide variety of both semantic contents and technical parameters, which is publicly available and can be downloaded in full or in smaller subsets. With this release, we aim at providing researchers in image forensics with a valuable benchmarking tool for the experimental evaluation of their novel forensic techniques. Differently from other existing datasets targeting a specific forensic task (like splicing [12] and copy-move detection [1, 3] or source identification [10]) where the images are processed accordingly, RAISE is conceived for a general purpose within the image forensics field, since raw images contain all the information related to the acquisition process and can be exploited to test any kind of processing (or chains of operators) according to the experimental setting needed. Even if the RAISE dataset has been primarily designed for digital forensics investigators, we foresee its potential use also within many other research fields where large and diverse data sets are needed in order to carry out meaningful investigations on multimedia. The structure of the paper is the following: in Section 2 the existing datasets used in image forensics are reviewed, while in Section 3 the new RAISE dataset is presented in details, by describing the collection and organization of the images, together with their basic statistics. In Section 4 an exemplifying experimental validation is presented, by testing a very recent JPEG compression detector, while Section 5 draws some concluding remarks. 2. RELATED WORK Digital image forensics has been developing at break-neck speeds over the last decade, while a common benchmarking image dataset for algorithm evaluation and fair comparison is still lagging behind. Several general image benchmark datasets are available in the literature (e.g., MIRFlickr [13]), but unfortunately none of them is suitable for forensic purposes due to the uncontrolled nature of the provided images (e.g., origin, compression, applied processing). In the forensic literature a few benchmarking image datasets have been proposed so far, each one designed for the detection of a specific type of manipulation. For instance, a couple of image datasets have been developed for supporting copy-move forgery detection. This manipulation is a common form of tampering that creates a spliced image by copying a portion of its content and pasting it within the same or into a different image, in order to remove or conceal objects. The Columbia Uncompressed Image Splicing Detection Evaluation Dataset [12] provides 183 authentic and 180 spliced images in uncompressed format (BMP or TIFF format), whose sizes range from to pixels. Since the splicing procedure is reached by quasirandomly copying a part of an image and pasting it into a different one without any post-processing, the spliced images result to be semantically meaningless and visually not compelling. The Casia dataset [9] tried to overcome this issue by providing more realistic spliced images. However, most of them are of size pixels, thus too small for a real scenario test-case. Amerini et al. released two benchmark datasets of realistic spliced images [1]: MICC F220 consists of 220 images, while MICC F2000 contains 2000 images, all of pixels. Since the processing operations employed for creating the forgeries are limited to only rotation and scaling and the source files are not available, the applicability of such datasets to realistic scenarios tests is limited. Finally, in 2012 a complete benchmark for copy-move detection has been proposed in [3]. The authors provided a code for generating as many as needed semantically meaningful spliced images, providing also the ground truth. In such a way, they were able to create a common benchmark for a fair comparison and an in-depth evaluation of all the state-of-the-art forensic techniques devoted to discovering copy-move forgeries. Other proposed forensic databases have slightly different goals, such as the identification of sensor fingerprint in order to link an image to the camera that took it. To support such research, Goljan et al. proposed a large-scale database [11], essential in order to include in the analysis all possible camera devices present is commerce nowadays, but, to the best of our knowledge, such dataset is not publicly available. Similarly, the Dresden Image Database [10] aims at targeting the source camera identification problem by providing replicas of 83 images, ranging from to pixels, taken from 73 different devices, for a total of JPEG images, 1491 RAW (unprocessed) images, 1491 RAW images processed in Lightroom 2.5 and 1491 RAW images processed in DCRaw 9.3. In the literature, such dataset has been exploited also for general digital forgery detection, such as single/multiple JPEG compression, CFA artifacts, median filtering. However, it lacks of diversity in the image contents, since the RAW images always depict the same set of predefined contents, just taken with each selected cameras.
3 Properties Resolution Image Quality (a) Original photo. (b) Modified photo. Figure 2: In panel (a) is a raw image taken from the RAISE dataset, while panel (b) shows its digitally modified version. To overcome this issue, in the last years the forensic community focused his attention on the UCID database [19] for the evaluation of digital forgery algorithms. Such dataset includes 1338 images stored in TIFF format, whose size is either or pixels. UCID dataset was originally designed for the evaluation of image retrieval techniques, thus providing the predefined query images with the corresponding model images that should be retrieved (released as ground truth). UCID is currently the most widely used benchmarking dataset for forensic purposes requiring uncompressed images for testing. Also within the European project REWIND [18] a set of 200 uncompressed images taken with a Nikon camera has been released (among several others for splicing detection, copy-move forgeries and recapture videos, all including a few number of samples). Unfortunately, the limited number of provided images (both in the UCID and REWIND datasets) and the poor resolution offered by the common UCID database make these benchmarks not fully reliable for extensive forensic evaluations. 3. DATASET DESCRIPTION In this work, we propose a challenging real-world image dataset, primarily designed for the evaluation of digital forgery detection algorithms. The RAISE dataset is intended to become a powerful and shared resource for forensic researchers and investigators allowing for a fair comparison of existing and forthcoming algorithms. Indeed, custom-made datasets undermine and strongly influence the performance of an algorithm, thus making reproducibility and comparison of results often a difficult issue. This in turns creates a huge obstacle to the technical and scientific growth of the given field of research. Besides this, RAISE dataset is also intended to overcome the copyright and privacy problems related to the use of commonly available images downloaded from the Web. Please note that such issues are not necessarily specific of digital image forensics research, but common to many other research fields where large and diverse data collections are needed in order to carry out meaningful investigations on multimedia. Thus, we expect that the proposed collection of images will be useful and constitute a valuable resource also within other domains dealing with image analysis and processing (e.g., multimedia retrieval, denoising). Digital image forensics aims at discovering the processing history of a content. The basic assumption is that any operators that have been applied to an image will leave subtle traces in the statistics of the image. To the extend that such traces can be detected, they can be used as evidence for image forgeries. Recently, the forensic community has started focusing its attention on the detection of chains of opera- Camera Model Color Spaces # of images Compress Raw 12-bit Lossless Compress Raw 14-bit Nikon D40 Nikon D90 Nikon D7000 srgb Adobe RGB Table 1: Main properties of the RAISE dataset. tors [18]. Fig. 2 serves as an example to show how different processing operators can be applied to an image in order to change its content. In particular, shown in panel (a) is an original untouched image taken from the RAISE dataset, while in panel (b) is the same image but processed with different operators, such as filtering, copy-pasting, geometric transformations, blending and color adjustments. Such scenario is challenging since any post-processing can influence and perturb the traces left by previously applied operators. In this context, it becomes clear that a benchmark collection of controlled and never-processed images is needed as a starting point for building a reliable test scenario, so to guarantee a stable and objective study and evaluation of the various tools performance. As described in Section 2, existing forensic databases lack in both an adequate number of images to guarantee an extensive validation setting and in a realistic resolution. The RAISE dataset has been built in order to cope with such issues, providing 8156 RAW images, uncompressed and guaranteed to be camera-native (i.e, never touched nor processed). In the following, we describe into details how the images have been collected, together with their relative statistics and associated metadata. Finally, we illustrate the main organization of the image collection, explaining the image annotation intended to add a significant value to the proposed dataset and wide its applicability to future algorithms in image forensics, as well as other multimedia research fields. 3.1 Dataset collection The images present in the RAISE dataset have been collected from 4 photographers over a period of 3 years ( ), capturing different scenes and moments in over 80 places in Europe. Three different camera were employed, i.e., a Nikon D40, a Nikon D90 and a Nikon D7000. The original number of captured images was 26964, but we had to manually revise them and discard those images that were meaningless for the defined purpose. At first, we deleted all the mostly dark and blurry images, such as those taken at night (mainly caused by too high shutter speed or vibration), since they cannot be used to extract any significant statistics for forensic purposes. Then, we discarded near-duplicated images (i.e., images shot within 1 second apart) since the RAISE dataset is intended to be as diverse as possible. To this aim, we automatically analyzed multiple instances on the same scene taken with different exposure values in order to obtain High-Dynamic-Range (HDR) photos. We only kept the ones with exposure value equal to 0 in
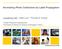
4 each HDR set. Finally, for copyright protection and privacy issues, we discarded personal pictures, such as depicting the photographers themselves. At the end of such selection process, the publicly available RAISE dataset contains a total of 8156 photos, saved in an uncompressed format (RAW) as natively provided by the employed cameras. We underline that the size of the the RAISE dataset is much larger compared to the existing forensics benchmarks, thus opening a new road for extensive analysis of existing and new-generation forensic techniques. 3.2 Dataset statistics and metadata All the images present in the RAISE dataset are taken in very high resolution ( , and pixels), overcoming by far the resolution limitation of current published data sets. All photos are stored in uncompressed formats, in high quality (Compress Raw 12-bit and Lossless Compress Raw 14-bit). Such information are shown in Table 1 in terms of number of images, together with the employed camera models and used color space. Besides such information, many other information about the images are available, since we allow users to download all the metadata associated to each image in the dataset. Among the others are the sensor focal lengths, flash modes (e.g., i-ttl-bl, i-ttl, i-ttl-bl -3.0), white balance settings (e.g., Shade, Direct sunlight, Cloudy, Color Temp, Incandescent) and the used lenses (e.g., 35mm f/1.8d, 50mm f/1.8d, 18-55mm f/ g), which could be seen as a valuable resource for studying the stability of lens aberrations in different scenes. 3.3 Dataset annotation On one hand, an extensive evaluation of any forensic algorithm needs a diverse benchmark in order to avoid contentdependent results. On the other hand, though, some specific techniques may require the analysis of specific image contents. In order to fulfill both requirements, we added an extra value to the proposed RAISE dataset and supplied all the images with tags. We labeled each image with 7 possible categories, namely, "outdoor", "indoor", "landscape", "nature", "people", "objects" and "buildings". In particular, "outdoor" indicates all those images taken outside, as opposite to "indoor", which includes those pictures taken inside a building. The tag "landscape" denotes those images depicting a section or expanse of rural inland or coastal scenery, usually extensive; "nature" denotes those contents representing a detail of a natural environment or animals, being the main subject, usually taken as a close-up picture; "people" indicates the presence of one or more persons within the image; "objects" refers to any image containing a physical object in a relevant position within the picture; finally, "buildings" indicates an enclosed construction over a plot of land, generally used for any of a wide variety of activities, as living, or manufacturing. Shown in Figure 3 are some examples of images from each category. Table 2 reports all the labeled categories along with the total number of images falling into that category. Please notice that the categories are not all mutually exclusive (except Category # of images Outdoor 6954 Indoor 1202 Landscape 2522 Nature 1167 People 1097 Objects 860 Buildings 2475 Table 2: Categories used for labeling the RAISE dataset. "indoor" and "outdoor"), so each image may have multiple labels. These tags result to be a valuable resource for many digital forensics areas. For instance, "outdoor"-tagged images may be helpful for studying light-based forensic algorithms (e.g., [14]), while the "building"-tagged images could be of great interest for all those geometric-based forensic techniques relying on the analysis of vanishing points, but also for more general photogrammetry studies (e.g., [7]). In fact, we foresee the utility of the RAISE tagged-images not limited to the forensic domain, but also for a wider range of investigations on multimedia processing and understanding. As an example, we could think of a visual privacy application for the "people"-tagged images, where the personal visual information should effectively be obscured (see the MediaEval 2014 task on visual privacy 2 ). 3.4 Dataset organization RAISE is available for scientific purposes at the following URL: We implemented an attractive and user-friendly interface in order to allow all the interested researchers to easily download the RAISE dataset. The website shows some examples from the image collection and allows for an easy and fast download of the whole dataset via ftp connection, either in TIFF or NEF format. Some guidelines are also provided to support stepby-step the download procedure. Since the whole dataset is quite large in terms of storage space (over 350 GB), we decided to make also smaller subsets available, namely RAISE- 1k, RAISE-2k, RAISE-4k and RAISE-6k, containing 1000, 2000, 4000 and 6000 images, respectively. Each subset is constructed so that the number of images belonging to each category is proportional to the total amount of images in each category present in the entire database. The user will have the possibility to choose to download either the entire RAISE dataset or a subset of it. As an option, the user could also select a specific image category of interest. Metadata are also provided, together with the embedded annotations, as previously described. Please note that all the images in the RAISE dataset are stored with a unique identifier (generated by the MD5 function) in order to ensure the image integrity. 2
5 Outdoor Indoor Landscape Nature People Objects Buildings Figure 3: Examples of images present in RAISE images have been carefully tagged by experts using 7 defined categories. 4. VALIDATION In this section, we report an experimental validation on the images contained in RAISE, as a demonstration of one of its possible use within an image forensic framework. In particular, we focus on the analysis of images stored in uncompressed format (like TIFF, BMP, PNG, and so on), with the aim of detecting traces of a previous JPEG compression. This problem arises, for instance, when the subject image of a forensic analysis supposedly comes from a device set to provide raw images (like professional or semiprofessional cameras), which are usually converted to uncompressed formats (like TIFF) for wide distribution. In this case, the presence of JPEG compression traces would suggest that the image has been taken from a different camera or it has been already processed by someone. In this framework, RAISE represents a suitable dataset for testing a recent forensic technique designed to identify traces of previous compression [16]. As it is extensively exploited in image forensics literature, the core of the JPEG compression algorithm is the quantization of the DCT coefficients (obtained by applying a 8 8 block-dct in the pixel domain), with the width of the quantization interval depending on the quality factor used. According to this, the method proposed in [16] is based on the extraction of a single feature from the DCT domain, namely the Benford-Fourier (BF) coefficient, which captures the difference between the DCT coefficients of an image that has never been compressed and of one that previously underwent a compression operation. In particular, in [16] the distribution of the BF coefficient magnitude under the hypothesis of no previous compression is theoretically derived, as reported in Fig. 4. This knowledge is then exploited to design a binary hypothesis test framework, where the pristine condition of the image is the null hypothesis and the occurrence of a previous compression is the alternative hypothesis. Since the analytical expression of the pdf is available, it is possible to determine an acceptance region so that the false alarm probability (a pristine image is classified as previously compressed) is equal to a chosen value. In other words, an upper and lower threshold on the magnitude of BF coefficients can be automatically determined: if such value lies beyond the two thresholds the null hypothesis is rejected and the image is classified as previously compressed. As such, there is no need for a training phase, but it is sufficient to fix a false
6 NC PC NC PC Table 3: Confusion matrix in the classification between never compressed (NC) and previously compressed (PC) images, testing the JPEG compression detector [16] on RAISE. alarm probability value. In order to test the performance of the technique, we divided the RAISE dataset (the TIFF version) into two halves and created two different classes, labeled as NC (never compressed) and PC (previously compressed), respectively. For the NC-labeled images, the BF coefficient was computed directly from the TIFF version; on the other hand, the PClabeled images were JPEG compressed with a random quality factor in {50, 51,..., 90}, re-saved as TIFF and finally the BF coefficient was computed. According to the hypothesis testing framework proposed in [16], the images were classified as NC or PC by thresholding the magnitude of the BF coefficient. Specifically, the threshold was automatically determined from a statistical model where the predicted false alarm probability was set to a certain value (in the tests we used 0.01). In Table 3, the obtained confusion matrix is reported. Based on this, we can assess the very good performances of the classification on the RAISE dataset, proving the effectiveness of the JPEG detector in [16] also on diverse and high-quality images. 5. CONCLUSION In this paper, we have presented RAISE, a new dataset of raw images, that is proposed as a valuable support tool for benchmarking within the research field of image forensics, as well as other image processing fields. The collection and organization modalities of the database have been thoroughly described, together with some basic statistics, and the results of an exemplifying experimental validation are reported. With this work, we intend to provide researchers in image forensics with a common benchmark for an in-depth evalu Magnitude of BF coefficient x 10 3 Figure 4: Shown is the histogram of the BF coefficients computed on 1000 TIFF images selected from RAISE, together with the corresponding pdf theoretically predicted by the method in [16] (red curve). ation and comparison of state-of-the-art and future forensic techniques, in order to better assessing their reliability in real-world applications. Moreover, the RAISE collection, by name and by nature, might grow in the future and include new images and categories, with the goal of meeting new potential needs of the research community in multimedia. 6. REFERENCES [1] I. Amerini et al. A sift-based forensic method for copy-move attack detection and transformation recovery,. IEEE Transactions on Information Forensics and Security, 6(3): , [2] F. Battisti et al. Watermarking and encryption of color images in the fibonacci domain. In SPIE Image Processing: Algorithms and Systems, volume 6812, [3] V. Christlein et al. An evaluation of popular copy-move forgery detection approaches. IEEE Transactions on Information Forensics and Security, 7(6): , [4] V. Conotter and G. Boato. Analysis of sensor fingerprint for source camera identification. IEEE Electronic Letters, 47(25): , [5] V. Conotter et al. A crowdsourced data set of edited images online. In ACM Workshop on Crowdsourcing for Multimedia, [6] V. Conotter et al. Physiologically-based detection of computer generated faces in video. In IEEE International Conference on Image Processing, [7] A. Criminisi. Single-view metrology: Algorithms and applications. In Pattern Recognition, volume 2449 of Lecture Notes in Computer Science, pages Springer Berlin Heidelberg, [8] E. Delp et al. Special issue on digital forensics. IEEE Signal Processing Magazine, 2(26), [9] J. Dong et al. Casia image tampering detection evaluation database. In IEEE International Conference on Signal and Information Processing, pages , Online at [10] T. Gloe and R. Böhme. The Dresden Image Database for benchmarking digital image forensics. In ACM Symposium On Applied Computing, volume 2, pages , Online at [11] M. Goljan et al. Large scale test of sensor fingerprint camera identification. In SPIE Media Forensics and Security, volume 7254, [12] Y.-F. Hsu and S.-F. Chang. Detecting image splicing using geometry invariants and camera characteristics consistency. In IEEE International Conference on Multimedia and Expo, pages , [13] M. J. Huiskes and M. S. Lew. The MIR Flickr retrieval evaluation. In ACM International Conference on Multimedia Information Retrieval, pages 39 43, Online at [14] P. Kakar and N. Sudha. Verifying temporal data in geotagged images via sun azimuth estimation. IEEE Transactions on Information Forensics and Security, 7(3): , [15] J. Lukas et al. Digital camera identification from sensor noise. IEEE Transactions on Information Forensics and Security, 1(2): , [16] C. Pasquini et al. A Benford-Fourier JPEG compression detector. In IEEE International Conference on Image Processing, pages , [17] A. Piva. An overview on image forensics. ISRN Signal Processing, 2013:1 22, [18] REWIND. Reverse engineering of audio-visual content data - datasets. Online at [19] G. Schaefer and M. Stich. UCID - an uncompressed colour image database. In SPIE Conference on Storage and Retrieval Methods and Applications for Multimedia, pages , San Jose (CA), January Online at cogs/datasets/ucid/ucid.html.
7 [20] P. Zontone et al. Impact of contrast modification on human feeling: an objective and subjective assessment. In IEEE International Conference on Image Processing, 2010.
Fragile Sensor Fingerprint Camera Identification
 Fragile Sensor Fingerprint Camera Identification Erwin Quiring Matthias Kirchner Binghamton University IEEE International Workshop on Information Forensics and Security Rome, Italy November 19, 2015 Camera
Fragile Sensor Fingerprint Camera Identification Erwin Quiring Matthias Kirchner Binghamton University IEEE International Workshop on Information Forensics and Security Rome, Italy November 19, 2015 Camera
Detecting Resized Double JPEG Compressed Images Using Support Vector Machine
 Detecting Resized Double JPEG Compressed Images Using Support Vector Machine Hieu Cuong Nguyen and Stefan Katzenbeisser Computer Science Department, Darmstadt University of Technology, Germany {cuong,katzenbeisser}@seceng.informatik.tu-darmstadt.de
Detecting Resized Double JPEG Compressed Images Using Support Vector Machine Hieu Cuong Nguyen and Stefan Katzenbeisser Computer Science Department, Darmstadt University of Technology, Germany {cuong,katzenbeisser}@seceng.informatik.tu-darmstadt.de
Camera identification from sensor fingerprints: why noise matters
 Camera identification from sensor fingerprints: why noise matters PS Multimedia Security 2010/2011 Yvonne Höller Peter Palfrader Department of Computer Science University of Salzburg January 2011 / PS
Camera identification from sensor fingerprints: why noise matters PS Multimedia Security 2010/2011 Yvonne Höller Peter Palfrader Department of Computer Science University of Salzburg January 2011 / PS
Detection of Image Forgery was Created from Bitmap and JPEG Images using Quantization Table
 Detection of Image Forgery was Created from Bitmap and JPEG Images using Quantization Tran Dang Hien University of Engineering and Eechnology, VietNam National Univerity, VietNam Pham Van At Department
Detection of Image Forgery was Created from Bitmap and JPEG Images using Quantization Tran Dang Hien University of Engineering and Eechnology, VietNam National Univerity, VietNam Pham Van At Department
PRIOR IMAGE JPEG-COMPRESSION DETECTION
 Applied Computer Science, vol. 12, no. 3, pp. 17 28 Submitted: 2016-07-27 Revised: 2016-09-05 Accepted: 2016-09-09 Compression detection, Image quality, JPEG Grzegorz KOZIEL * PRIOR IMAGE JPEG-COMPRESSION
Applied Computer Science, vol. 12, no. 3, pp. 17 28 Submitted: 2016-07-27 Revised: 2016-09-05 Accepted: 2016-09-09 Compression detection, Image quality, JPEG Grzegorz KOZIEL * PRIOR IMAGE JPEG-COMPRESSION
Global Contrast Enhancement Detection via Deep Multi-Path Network
 Global Contrast Enhancement Detection via Deep Multi-Path Network Cong Zhang, Dawei Du, Lipeng Ke, Honggang Qi School of Computer and Control Engineering University of Chinese Academy of Sciences, Beijing,
Global Contrast Enhancement Detection via Deep Multi-Path Network Cong Zhang, Dawei Du, Lipeng Ke, Honggang Qi School of Computer and Control Engineering University of Chinese Academy of Sciences, Beijing,
Retrieval of Large Scale Images and Camera Identification via Random Projections
 Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
TECHNICAL DOCUMENTATION
 TECHNICAL DOCUMENTATION NEED HELP? Call us on +44 (0) 121 231 3215 TABLE OF CONTENTS Document Control and Authority...3 Introduction...4 Camera Image Creation Pipeline...5 Photo Metadata...6 Sensor Identification
TECHNICAL DOCUMENTATION NEED HELP? Call us on +44 (0) 121 231 3215 TABLE OF CONTENTS Document Control and Authority...3 Introduction...4 Camera Image Creation Pipeline...5 Photo Metadata...6 Sensor Identification
Watermarking-based Image Authentication with Recovery Capability using Halftoning and IWT
 Watermarking-based Image Authentication with Recovery Capability using Halftoning and IWT Luis Rosales-Roldan, Manuel Cedillo-Hernández, Mariko Nakano-Miyatake, Héctor Pérez-Meana Postgraduate Section,
Watermarking-based Image Authentication with Recovery Capability using Halftoning and IWT Luis Rosales-Roldan, Manuel Cedillo-Hernández, Mariko Nakano-Miyatake, Héctor Pérez-Meana Postgraduate Section,
Content Based Image Retrieval Using Color Histogram
 Content Based Image Retrieval Using Color Histogram Nitin Jain Assistant Professor, Lokmanya Tilak College of Engineering, Navi Mumbai, India. Dr. S. S. Salankar Professor, G.H. Raisoni College of Engineering,
Content Based Image Retrieval Using Color Histogram Nitin Jain Assistant Professor, Lokmanya Tilak College of Engineering, Navi Mumbai, India. Dr. S. S. Salankar Professor, G.H. Raisoni College of Engineering,
A Guide to Image Management in Art Centres. Contact For further information about this guide, please contact
 A Guide to Image Management in Art Centres Contact For further information about this guide, please contact sam@desart.com.au. VERSION: 20 th June 2017 Contents Overview... 2 Setting the scene... 2 Digital
A Guide to Image Management in Art Centres Contact For further information about this guide, please contact sam@desart.com.au. VERSION: 20 th June 2017 Contents Overview... 2 Setting the scene... 2 Digital
Impeding Forgers at Photo Inception
 Impeding Forgers at Photo Inception Matthias Kirchner a, Peter Winkler b and Hany Farid c a International Computer Science Institute Berkeley, Berkeley, CA 97, USA b Department of Mathematics, Dartmouth
Impeding Forgers at Photo Inception Matthias Kirchner a, Peter Winkler b and Hany Farid c a International Computer Science Institute Berkeley, Berkeley, CA 97, USA b Department of Mathematics, Dartmouth
Tampering and Copy-Move Forgery Detection Using Sift Feature
 Tampering and Copy-Move Forgery Detection Using Sift Feature N.Anantharaj 1 M-TECH (IT) Final Year, Department of IT, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamilnadu, India 1 ABSTRACT:
Tampering and Copy-Move Forgery Detection Using Sift Feature N.Anantharaj 1 M-TECH (IT) Final Year, Department of IT, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamilnadu, India 1 ABSTRACT:
Image Forgery Identification Using JPEG Intrinsic Fingerprints
 1 Image Forgery Identification Using JPEG Intrinsic Fingerprints A. Garg, A. Hailu, and R. Sridharan Abstract In this paper a novel method for image forgery detection is presented. he method exploits the
1 Image Forgery Identification Using JPEG Intrinsic Fingerprints A. Garg, A. Hailu, and R. Sridharan Abstract In this paper a novel method for image forgery detection is presented. he method exploits the
Distinguishing between Camera and Scanned Images by Means of Frequency Analysis
 Distinguishing between Camera and Scanned Images by Means of Frequency Analysis Roberto Caldelli, Irene Amerini, and Francesco Picchioni Media Integration and Communication Center - MICC, University of
Distinguishing between Camera and Scanned Images by Means of Frequency Analysis Roberto Caldelli, Irene Amerini, and Francesco Picchioni Media Integration and Communication Center - MICC, University of
IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION
 IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION Sevinc Bayram a, Husrev T. Sencar b, Nasir Memon b E-mail: sevincbayram@hotmail.com, taha@isis.poly.edu, memon@poly.edu a Dept.
IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION Sevinc Bayram a, Husrev T. Sencar b, Nasir Memon b E-mail: sevincbayram@hotmail.com, taha@isis.poly.edu, memon@poly.edu a Dept.
Wavelet-based Image Splicing Forgery Detection
 Wavelet-based Image Splicing Forgery Detection 1 Tulsi Thakur M.Tech (CSE) Student, Department of Computer Technology, basiltulsi@gmail.com 2 Dr. Kavita Singh Head & Associate Professor, Department of
Wavelet-based Image Splicing Forgery Detection 1 Tulsi Thakur M.Tech (CSE) Student, Department of Computer Technology, basiltulsi@gmail.com 2 Dr. Kavita Singh Head & Associate Professor, Department of
Linear Gaussian Method to Detect Blurry Digital Images using SIFT
 IJCAES ISSN: 2231-4946 Volume III, Special Issue, November 2013 International Journal of Computer Applications in Engineering Sciences Special Issue on Emerging Research Areas in Computing(ERAC) www.caesjournals.org
IJCAES ISSN: 2231-4946 Volume III, Special Issue, November 2013 International Journal of Computer Applications in Engineering Sciences Special Issue on Emerging Research Areas in Computing(ERAC) www.caesjournals.org
CS 365 Project Report Digital Image Forensics. Abhijit Sharang (10007) Pankaj Jindal (Y9399) Advisor: Prof. Amitabha Mukherjee
 CS 365 Project Report Digital Image Forensics Abhijit Sharang (10007) Pankaj Jindal (Y9399) Advisor: Prof. Amitabha Mukherjee 1 Abstract Determining the authenticity of an image is now an important area
CS 365 Project Report Digital Image Forensics Abhijit Sharang (10007) Pankaj Jindal (Y9399) Advisor: Prof. Amitabha Mukherjee 1 Abstract Determining the authenticity of an image is now an important area
2018 IEEE Signal Processing Cup: Forensic Camera Model Identification Challenge
 2018 IEEE Signal Processing Cup: Forensic Camera Model Identification Challenge This competition is sponsored by the IEEE Signal Processing Society Introduction The IEEE Signal Processing Society s 2018
2018 IEEE Signal Processing Cup: Forensic Camera Model Identification Challenge This competition is sponsored by the IEEE Signal Processing Society Introduction The IEEE Signal Processing Society s 2018
Introduction to Video Forgery Detection: Part I
 Introduction to Video Forgery Detection: Part I Detecting Forgery From Static-Scene Video Based on Inconsistency in Noise Level Functions IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 5,
Introduction to Video Forgery Detection: Part I Detecting Forgery From Static-Scene Video Based on Inconsistency in Noise Level Functions IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 5,
Image Forgery Detection Using Svm Classifier
 Image Forgery Detection Using Svm Classifier Anita Sahani 1, K.Srilatha 2 M.E. Student [Embedded System], Dept. Of E.C.E., Sathyabama University, Chennai, India 1 Assistant Professor, Dept. Of E.C.E, Sathyabama
Image Forgery Detection Using Svm Classifier Anita Sahani 1, K.Srilatha 2 M.E. Student [Embedded System], Dept. Of E.C.E., Sathyabama University, Chennai, India 1 Assistant Professor, Dept. Of E.C.E, Sathyabama
Multimedia Forensics
 Multimedia Forensics Using Mathematics and Machine Learning to Determine an Image's Source and Authenticity Matthew C. Stamm Multimedia & Information Security Lab (MISL) Department of Electrical and Computer
Multimedia Forensics Using Mathematics and Machine Learning to Determine an Image's Source and Authenticity Matthew C. Stamm Multimedia & Information Security Lab (MISL) Department of Electrical and Computer
IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION
 Chapter 23 IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION Sevinc Bayram, Husrev Sencar and Nasir Memon Abstract In an earlier work [4], we proposed a technique for identifying digital camera models
Chapter 23 IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION Sevinc Bayram, Husrev Sencar and Nasir Memon Abstract In an earlier work [4], we proposed a technique for identifying digital camera models
Exposing Digital Forgeries from JPEG Ghosts
 1 Exposing Digital Forgeries from JPEG Ghosts Hany Farid, Member, IEEE Abstract When creating a digital forgery, it is often necessary to combine several images, for example, when compositing one person
1 Exposing Digital Forgeries from JPEG Ghosts Hany Farid, Member, IEEE Abstract When creating a digital forgery, it is often necessary to combine several images, for example, when compositing one person
IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 01, 2016 ISSN (online):
 IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 01, 2016 ISSN (online): 2321-0613 High-Quality Jpeg Compression using LDN Comparison and Quantization Noise Analysis S.Sasikumar
IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 01, 2016 ISSN (online): 2321-0613 High-Quality Jpeg Compression using LDN Comparison and Quantization Noise Analysis S.Sasikumar
Literature Survey on Image Manipulation Detection
 Literature Survey on Image Manipulation Detection Rani Mariya Joseph 1, Chithra A.S. 2 1M.Tech Student, Computer Science and Engineering, LMCST, Kerala, India 2 Asso. Professor, Computer Science And Engineering,
Literature Survey on Image Manipulation Detection Rani Mariya Joseph 1, Chithra A.S. 2 1M.Tech Student, Computer Science and Engineering, LMCST, Kerala, India 2 Asso. Professor, Computer Science And Engineering,
A Novel Approach of Compressing Images and Assessment on Quality with Scaling Factor
 A Novel Approach of Compressing Images and Assessment on Quality with Scaling Factor Umesh 1,Mr. Suraj Rana 2 1 M.Tech Student, 2 Associate Professor (ECE) Department of Electronic and Communication Engineering
A Novel Approach of Compressing Images and Assessment on Quality with Scaling Factor Umesh 1,Mr. Suraj Rana 2 1 M.Tech Student, 2 Associate Professor (ECE) Department of Electronic and Communication Engineering
Image Extraction using Image Mining Technique
 IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
Detection and Localization of Image and Document Forgery: Survey and Benchmarking
 Detection and Localization of Image and Document Forgery: Survey and Benchmarking Anurag Ghosh Dongmian Zou Maneesh Singh Verisk Analytics {anurag.ghosh, dongmian.zou, maneesh.singh}@verisk.com Abstract
Detection and Localization of Image and Document Forgery: Survey and Benchmarking Anurag Ghosh Dongmian Zou Maneesh Singh Verisk Analytics {anurag.ghosh, dongmian.zou, maneesh.singh}@verisk.com Abstract
Forensic Framework. Attributing and Authenticating Evidence. Forensic Framework. Attribution. Forensic source identification
 Attributing and Authenticating Evidence Forensic Framework Collection Identify and collect digital evidence selective acquisition? cloud storage? Generate data subset for examination? Examination of evidence
Attributing and Authenticating Evidence Forensic Framework Collection Identify and collect digital evidence selective acquisition? cloud storage? Generate data subset for examination? Examination of evidence
Digital Watermarking Using Homogeneity in Image
 Digital Watermarking Using Homogeneity in Image S. K. Mitra, M. K. Kundu, C. A. Murthy, B. B. Bhattacharya and T. Acharya Dhirubhai Ambani Institute of Information and Communication Technology Gandhinagar
Digital Watermarking Using Homogeneity in Image S. K. Mitra, M. K. Kundu, C. A. Murthy, B. B. Bhattacharya and T. Acharya Dhirubhai Ambani Institute of Information and Communication Technology Gandhinagar
OBJECTIVE OF THE BOOK ORGANIZATION OF THE BOOK
 xv Preface Advancement in technology leads to wide spread use of mounting cameras to capture video imagery. Such surveillance cameras are predominant in commercial institutions through recording the cameras
xv Preface Advancement in technology leads to wide spread use of mounting cameras to capture video imagery. Such surveillance cameras are predominant in commercial institutions through recording the cameras
Image Tampering Localization via Estimating the Non-Aligned Double JPEG compression
 Image Tampering Localization via Estimating the Non-Aligned Double JPEG compression Lanying Wu a, Xiangwei Kong* a, Bo Wang a, Shize Shang a a School of Information and Communication Engineering, Dalian
Image Tampering Localization via Estimating the Non-Aligned Double JPEG compression Lanying Wu a, Xiangwei Kong* a, Bo Wang a, Shize Shang a a School of Information and Communication Engineering, Dalian
An Automatic JPEG Ghost Detection Approach for Digital Image Forensics
 An Automatic JPEG Ghost Detection Approach for Digital Image Forensics Sepideh Azarian-Pour Sharif University of Technology Tehran, 4588-89694, Iran Email: sepideazarian@gmailcom Massoud Babaie-Zadeh Sharif
An Automatic JPEG Ghost Detection Approach for Digital Image Forensics Sepideh Azarian-Pour Sharif University of Technology Tehran, 4588-89694, Iran Email: sepideazarian@gmailcom Massoud Babaie-Zadeh Sharif
Sapna Sameriaˡ, Vaibhav Saran², A.K.Gupta³
 A REVIEW OF TRENDS IN DIGITAL IMAGE PROCESSING FOR FORENSIC CONSIDERATION Sapna Sameriaˡ, Vaibhav Saran², A.K.Gupta³ Department of Forensic Science Sam Higginbottom Institute of agriculture Technology
A REVIEW OF TRENDS IN DIGITAL IMAGE PROCESSING FOR FORENSIC CONSIDERATION Sapna Sameriaˡ, Vaibhav Saran², A.K.Gupta³ Department of Forensic Science Sam Higginbottom Institute of agriculture Technology
License Plate Localisation based on Morphological Operations
 License Plate Localisation based on Morphological Operations Xiaojun Zhai, Faycal Benssali and Soodamani Ramalingam School of Engineering & Technology University of Hertfordshire, UH Hatfield, UK Abstract
License Plate Localisation based on Morphological Operations Xiaojun Zhai, Faycal Benssali and Soodamani Ramalingam School of Engineering & Technology University of Hertfordshire, UH Hatfield, UK Abstract
AN OPTIMIZED APPROACH FOR FAKE CURRENCY DETECTION USING DISCRETE WAVELET TRANSFORM
 AN OPTIMIZED APPROACH FOR FAKE CURRENCY DETECTION USING DISCRETE WAVELET TRANSFORM T.Manikyala Rao 1, Dr. Ch. Srinivasa Rao 2 Research Scholar, Department of Electronics and Communication Engineering,
AN OPTIMIZED APPROACH FOR FAKE CURRENCY DETECTION USING DISCRETE WAVELET TRANSFORM T.Manikyala Rao 1, Dr. Ch. Srinivasa Rao 2 Research Scholar, Department of Electronics and Communication Engineering,
Photo Editing Workflow
 Photo Editing Workflow WHY EDITING Modern digital photography is a complex process, which starts with the Photographer s Eye, that is, their observational ability, it continues with photo session preparations,
Photo Editing Workflow WHY EDITING Modern digital photography is a complex process, which starts with the Photographer s Eye, that is, their observational ability, it continues with photo session preparations,
Watermarking patient data in encrypted medical images
 Sādhanā Vol. 37, Part 6, December 2012, pp. 723 729. c Indian Academy of Sciences Watermarking patient data in encrypted medical images 1. Introduction A LAVANYA and V NATARAJAN Department of Instrumentation
Sādhanā Vol. 37, Part 6, December 2012, pp. 723 729. c Indian Academy of Sciences Watermarking patient data in encrypted medical images 1. Introduction A LAVANYA and V NATARAJAN Department of Instrumentation
Splicing Forgery Exposure in Digital Image by Detecting Noise Discrepancies
 International Journal of Computer and Communication Engineering, Vol. 4, No., January 25 Splicing Forgery Exposure in Digital Image by Detecting Noise Discrepancies Bo Liu and Chi-Man Pun Noise patterns
International Journal of Computer and Communication Engineering, Vol. 4, No., January 25 Splicing Forgery Exposure in Digital Image by Detecting Noise Discrepancies Bo Liu and Chi-Man Pun Noise patterns
Laser Printer Source Forensics for Arbitrary Chinese Characters
 Laser Printer Source Forensics for Arbitrary Chinese Characters Xiangwei Kong, Xin gang You,, Bo Wang, Shize Shang and Linjie Shen Information Security Research Center, Dalian University of Technology,
Laser Printer Source Forensics for Arbitrary Chinese Characters Xiangwei Kong, Xin gang You,, Bo Wang, Shize Shang and Linjie Shen Information Security Research Center, Dalian University of Technology,
Understanding Image Formats And When to Use Them
 Understanding Image Formats And When to Use Them Are you familiar with the extensions after your images? There are so many image formats that it s so easy to get confused! File extensions like.jpeg,.bmp,.gif,
Understanding Image Formats And When to Use Them Are you familiar with the extensions after your images? There are so many image formats that it s so easy to get confused! File extensions like.jpeg,.bmp,.gif,
Liangliang Cao *, Jiebo Luo +, Thomas S. Huang *
 Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
Detection of Adaptive Histogram Equalization Robust Against JPEG Compression
 Detection of Adaptive Histogram Equalization Robust Against JPEG Compression Mauro Barni, Ehsan Nowroozi, Benedetta Tondi Department of Information Engineering and Mathematics, University of Siena Via
Detection of Adaptive Histogram Equalization Robust Against JPEG Compression Mauro Barni, Ehsan Nowroozi, Benedetta Tondi Department of Information Engineering and Mathematics, University of Siena Via
Higher-Order, Adversary-Aware, Double JPEG-Detection via Selected Training on Attacked Samples
 Higher-Order, Adversary-Aware, Double JPEG-Detection via Selected Training on ed Samples Mauro Barni, Ehsan Nowroozi, Benedetta Tondi Department of Information Engineering and Mathematics, University of
Higher-Order, Adversary-Aware, Double JPEG-Detection via Selected Training on ed Samples Mauro Barni, Ehsan Nowroozi, Benedetta Tondi Department of Information Engineering and Mathematics, University of
Image Manipulation Detection using Convolutional Neural Network
 Image Manipulation Detection using Convolutional Neural Network Dong-Hyun Kim 1 and Hae-Yeoun Lee 2,* 1 Graduate Student, 2 PhD, Professor 1,2 Department of Computer Software Engineering, Kumoh National
Image Manipulation Detection using Convolutional Neural Network Dong-Hyun Kim 1 and Hae-Yeoun Lee 2,* 1 Graduate Student, 2 PhD, Professor 1,2 Department of Computer Software Engineering, Kumoh National
Specific structure or arrangement of data code stored as a computer file.
 FILE FORMAT Specific structure or arrangement of data code stored as a computer file. A file format tells the computer how to display, print, process, and save the data. It is dictated by the application
FILE FORMAT Specific structure or arrangement of data code stored as a computer file. A file format tells the computer how to display, print, process, and save the data. It is dictated by the application
Subjective evaluation of image color damage based on JPEG compression
 2014 Fourth International Conference on Communication Systems and Network Technologies Subjective evaluation of image color damage based on JPEG compression Xiaoqiang He Information Engineering School
2014 Fourth International Conference on Communication Systems and Network Technologies Subjective evaluation of image color damage based on JPEG compression Xiaoqiang He Information Engineering School
Dr. Kusam Sharma *1, Prof. Pawanesh Abrol 2, Prof. Devanand 3 ABSTRACT I. INTRODUCTION
 International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 6 ISSN : 2456-3307 Feature Based Analysis of Copy-Paste Image Tampering
International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 6 ISSN : 2456-3307 Feature Based Analysis of Copy-Paste Image Tampering
Automatic source camera identification using the intrinsic lens radial distortion
 Automatic source camera identification using the intrinsic lens radial distortion Kai San Choi, Edmund Y. Lam, and Kenneth K. Y. Wong Department of Electrical and Electronic Engineering, University of
Automatic source camera identification using the intrinsic lens radial distortion Kai San Choi, Edmund Y. Lam, and Kenneth K. Y. Wong Department of Electrical and Electronic Engineering, University of
Setting Up Your Camera Overview
 Setting Up Your Camera Overview Lecture #1B LOUDEN 1 Digital Shooting: Setting up your Camera & Taking Photographs Watch this Video: Getting to Know Some Controls on Your Camera (DSLR CAMERAS): http://www.youtube.com/watch?v=1wu63fbg27o&feature=rel
Setting Up Your Camera Overview Lecture #1B LOUDEN 1 Digital Shooting: Setting up your Camera & Taking Photographs Watch this Video: Getting to Know Some Controls on Your Camera (DSLR CAMERAS): http://www.youtube.com/watch?v=1wu63fbg27o&feature=rel
Image Processing by Bilateral Filtering Method
 ABHIYANTRIKI An International Journal of Engineering & Technology (A Peer Reviewed & Indexed Journal) Vol. 3, No. 4 (April, 2016) http://www.aijet.in/ eissn: 2394-627X Image Processing by Bilateral Image
ABHIYANTRIKI An International Journal of Engineering & Technology (A Peer Reviewed & Indexed Journal) Vol. 3, No. 4 (April, 2016) http://www.aijet.in/ eissn: 2394-627X Image Processing by Bilateral Image
Certification Commission Get Certified! Photojournalism. Starr Sackstein San Francisco 2013
 Get Certified! Certification Commission www.jea.org Photojournalism Starr Sackstein San Francisco 2013 JEA Standards 1A. 10 Value of photojournalism to tell stories in compelling ways CJE test format:
Get Certified! Certification Commission www.jea.org Photojournalism Starr Sackstein San Francisco 2013 JEA Standards 1A. 10 Value of photojournalism to tell stories in compelling ways CJE test format:
Fingerprint Quality Analysis: a PC-aided approach
 Fingerprint Quality Analysis: a PC-aided approach 97th International Association for Identification Ed. Conf. Phoenix, 23rd July 2012 A. Mattei, Ph.D, * F. Cervelli, Ph.D,* FZampaMSc F. Zampa, M.Sc, *
Fingerprint Quality Analysis: a PC-aided approach 97th International Association for Identification Ed. Conf. Phoenix, 23rd July 2012 A. Mattei, Ph.D, * F. Cervelli, Ph.D,* FZampaMSc F. Zampa, M.Sc, *
Note on CASIA-IrisV3
 Note on CASIA-IrisV3 1. Introduction With fast development of iris image acquisition technology, iris recognition is expected to become a fundamental component of modern society, with wide application
Note on CASIA-IrisV3 1. Introduction With fast development of iris image acquisition technology, iris recognition is expected to become a fundamental component of modern society, with wide application
Lossless Image Watermarking for HDR Images Using Tone Mapping
 IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.5, May 2013 113 Lossless Image Watermarking for HDR Images Using Tone Mapping A.Nagurammal 1, T.Meyyappan 2 1 M. Phil Scholar
IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.5, May 2013 113 Lossless Image Watermarking for HDR Images Using Tone Mapping A.Nagurammal 1, T.Meyyappan 2 1 M. Phil Scholar
A Study of Slanted-Edge MTF Stability and Repeatability
 A Study of Slanted-Edge MTF Stability and Repeatability Jackson K.M. Roland Imatest LLC, 2995 Wilderness Place Suite 103, Boulder, CO, USA ABSTRACT The slanted-edge method of measuring the spatial frequency
A Study of Slanted-Edge MTF Stability and Repeatability Jackson K.M. Roland Imatest LLC, 2995 Wilderness Place Suite 103, Boulder, CO, USA ABSTRACT The slanted-edge method of measuring the spatial frequency
Reversible data hiding based on histogram modification using S-type and Hilbert curve scanning
 Advances in Engineering Research (AER), volume 116 International Conference on Communication and Electronic Information Engineering (CEIE 016) Reversible data hiding based on histogram modification using
Advances in Engineering Research (AER), volume 116 International Conference on Communication and Electronic Information Engineering (CEIE 016) Reversible data hiding based on histogram modification using
THE popularization of imaging components equipped in
 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 3, MARCH 2015 Revealing the Trace of High-Quality JPEG Compression Through Quantization Noise Analysis Bin Li, Member, IEEE, Tian-Tsong
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 3, MARCH 2015 Revealing the Trace of High-Quality JPEG Compression Through Quantization Noise Analysis Bin Li, Member, IEEE, Tian-Tsong
Passive Image Forensic Method to detect Copy Move Forgery in Digital Images
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. XII (Mar-Apr. 2014), PP 96-104 Passive Image Forensic Method to detect Copy Move Forgery in
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. XII (Mar-Apr. 2014), PP 96-104 Passive Image Forensic Method to detect Copy Move Forgery in
Photoshop and Lightroom for Photographers
 Photoshop and Lightroom for Photographers Topic 7 Making Subtle changes in Photoshop Learning Outcomes In this lesson, we will take a photograph in Photoshop and do some quick touches to ensure that we
Photoshop and Lightroom for Photographers Topic 7 Making Subtle changes in Photoshop Learning Outcomes In this lesson, we will take a photograph in Photoshop and do some quick touches to ensure that we
Journal of mathematics and computer science 11 (2014),
 Journal of mathematics and computer science 11 (2014), 137-146 Application of Unsharp Mask in Augmenting the Quality of Extracted Watermark in Spatial Domain Watermarking Saeed Amirgholipour 1 *,Ahmad
Journal of mathematics and computer science 11 (2014), 137-146 Application of Unsharp Mask in Augmenting the Quality of Extracted Watermark in Spatial Domain Watermarking Saeed Amirgholipour 1 *,Ahmad
Source Camera Model Identification Using Features from contaminated Sensor Noise
 Source Camera Model Identification Using Features from contaminated Sensor Noise Amel TUAMA 2,3, Frederic COMBY 2,3, Marc CHAUMONT 1,2,3 1 NÎMES UNIVERSITY, F-30021 Nîmes Cedex 1, France 2 MONTPELLIER
Source Camera Model Identification Using Features from contaminated Sensor Noise Amel TUAMA 2,3, Frederic COMBY 2,3, Marc CHAUMONT 1,2,3 1 NÎMES UNIVERSITY, F-30021 Nîmes Cedex 1, France 2 MONTPELLIER
Efficient Estimation of CFA Pattern Configuration in Digital Camera Images
 Faculty of Computer Science Institute of Systems Architecture, Privacy and Data Security esearch roup Efficient Estimation of CFA Pattern Configuration in Digital Camera Images Electronic Imaging 2010
Faculty of Computer Science Institute of Systems Architecture, Privacy and Data Security esearch roup Efficient Estimation of CFA Pattern Configuration in Digital Camera Images Electronic Imaging 2010
An Integrated Image Steganography System. with Improved Image Quality
 Applied Mathematical Sciences, Vol. 7, 2013, no. 71, 3545-3553 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2013.34236 An Integrated Image Steganography System with Improved Image Quality
Applied Mathematical Sciences, Vol. 7, 2013, no. 71, 3545-3553 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2013.34236 An Integrated Image Steganography System with Improved Image Quality
Stamp detection in scanned documents
 Annales UMCS Informatica AI X, 1 (2010) 61-68 DOI: 10.2478/v10065-010-0036-6 Stamp detection in scanned documents Paweł Forczmański Chair of Multimedia Systems, West Pomeranian University of Technology,
Annales UMCS Informatica AI X, 1 (2010) 61-68 DOI: 10.2478/v10065-010-0036-6 Stamp detection in scanned documents Paweł Forczmański Chair of Multimedia Systems, West Pomeranian University of Technology,
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ We offer free update service for one year Exam : 9A0-125 Title : Adobe Photoshop Lightroom 2 ACE Exam Vendors : Adobe Version : DEMO Get Latest &
PASS4TEST IT Certification Guaranteed, The Easy Way! \ We offer free update service for one year Exam : 9A0-125 Title : Adobe Photoshop Lightroom 2 ACE Exam Vendors : Adobe Version : DEMO Get Latest &
IMAGE SPLICING FORGERY DETECTION AND LOCALIZATION USING FREQUENCY-BASED FEATURES
 Chiew K.T., et al. (Eds.): PGRES 2017, Kuala Lumpur: Eastin Hotel, FCSIT, 2017: pp 35-42 IMAGE SPLICING FORGERY DETECTION AND LOCALIZATION USING FREQUENCY-BASED FEATURES Thamarai Subramaniam and Hamid
Chiew K.T., et al. (Eds.): PGRES 2017, Kuala Lumpur: Eastin Hotel, FCSIT, 2017: pp 35-42 IMAGE SPLICING FORGERY DETECTION AND LOCALIZATION USING FREQUENCY-BASED FEATURES Thamarai Subramaniam and Hamid
PHOTOTUTOR.com.au Share the Knowledge
 THE DIGITAL WORKFLOW BY MICHAEL SMYTH This tutorial is designed to outline the necessary steps from digital capture, image editing and creating a final print. FIRSTLY, BE AWARE OF WHAT CAN AND CAN T BE
THE DIGITAL WORKFLOW BY MICHAEL SMYTH This tutorial is designed to outline the necessary steps from digital capture, image editing and creating a final print. FIRSTLY, BE AWARE OF WHAT CAN AND CAN T BE
Camera Image Processing Pipeline: Part II
 Lecture 14: Camera Image Processing Pipeline: Part II Visual Computing Systems Today Finish image processing pipeline Auto-focus / auto-exposure Camera processing elements Smart phone processing elements
Lecture 14: Camera Image Processing Pipeline: Part II Visual Computing Systems Today Finish image processing pipeline Auto-focus / auto-exposure Camera processing elements Smart phone processing elements
Exposing Image Forgery with Blind Noise Estimation
 Exposing Image Forgery with Blind Noise Estimation Xunyu Pan Computer Science Department University at Albany, SUNY Albany, NY 12222, USA xypan@cs.albany.edu Xing Zhang Computer Science Department University
Exposing Image Forgery with Blind Noise Estimation Xunyu Pan Computer Science Department University at Albany, SUNY Albany, NY 12222, USA xypan@cs.albany.edu Xing Zhang Computer Science Department University
STEGANALYSIS OF IMAGES CREATED IN WAVELET DOMAIN USING QUANTIZATION MODULATION
 STEGANALYSIS OF IMAGES CREATED IN WAVELET DOMAIN USING QUANTIZATION MODULATION SHAOHUI LIU, HONGXUN YAO, XIAOPENG FAN,WEN GAO Vilab, Computer College, Harbin Institute of Technology, Harbin, China, 150001
STEGANALYSIS OF IMAGES CREATED IN WAVELET DOMAIN USING QUANTIZATION MODULATION SHAOHUI LIU, HONGXUN YAO, XIAOPENG FAN,WEN GAO Vilab, Computer College, Harbin Institute of Technology, Harbin, China, 150001
SECTION I - CHAPTER 2 DIGITAL IMAGING PROCESSING CONCEPTS
 RADT 3463 - COMPUTERIZED IMAGING Section I: Chapter 2 RADT 3463 Computerized Imaging 1 SECTION I - CHAPTER 2 DIGITAL IMAGING PROCESSING CONCEPTS RADT 3463 COMPUTERIZED IMAGING Section I: Chapter 2 RADT
RADT 3463 - COMPUTERIZED IMAGING Section I: Chapter 2 RADT 3463 Computerized Imaging 1 SECTION I - CHAPTER 2 DIGITAL IMAGING PROCESSING CONCEPTS RADT 3463 COMPUTERIZED IMAGING Section I: Chapter 2 RADT
Capturing Realistic HDR Images. Dave Curtin Nassau County Camera Club February 24 th, 2016
 Capturing Realistic HDR Images Dave Curtin Nassau County Camera Club February 24 th, 2016 Capturing Realistic HDR Images Topics: What is HDR? In Camera. Post-Processing. Sample Workflow. Q & A. Capturing
Capturing Realistic HDR Images Dave Curtin Nassau County Camera Club February 24 th, 2016 Capturing Realistic HDR Images Topics: What is HDR? In Camera. Post-Processing. Sample Workflow. Q & A. Capturing
Information Forensics: An Overview of the First Decade
 Received March 8, 2013, accepted April 6, 2013, published May 10, 2013. Digital Object Identifier 10.1109/ACCESS.2013.2260814 Information Forensics: An Overview of the First Decade MATTHEW C. STAMM (MEMBER,
Received March 8, 2013, accepted April 6, 2013, published May 10, 2013. Digital Object Identifier 10.1109/ACCESS.2013.2260814 Information Forensics: An Overview of the First Decade MATTHEW C. STAMM (MEMBER,
A Comparison Study of Image Descriptors on Low- Resolution Face Image Verification
 A Comparison Study of Image Descriptors on Low- Resolution Face Image Verification Gittipat Jetsiktat, Sasipa Panthuwadeethorn and Suphakant Phimoltares Advanced Virtual and Intelligent Computing (AVIC)
A Comparison Study of Image Descriptors on Low- Resolution Face Image Verification Gittipat Jetsiktat, Sasipa Panthuwadeethorn and Suphakant Phimoltares Advanced Virtual and Intelligent Computing (AVIC)
Exposing Photo Manipulation with Geometric Inconsistencies
 Exposing Photo Manipulation with Geometric Inconsistencies James F. O Brien U.C. Berkeley Collaborators Hany Farid Eric Kee Valentina Conotter Stephen Bailey 1 image-forensics-pg14.key - October 9, 2014
Exposing Photo Manipulation with Geometric Inconsistencies James F. O Brien U.C. Berkeley Collaborators Hany Farid Eric Kee Valentina Conotter Stephen Bailey 1 image-forensics-pg14.key - October 9, 2014
Authentication of grayscale document images using shamir secret sharing scheme.
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. VII (Mar-Apr. 2014), PP 75-79 Authentication of grayscale document images using shamir secret
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. VII (Mar-Apr. 2014), PP 75-79 Authentication of grayscale document images using shamir secret
This version has been archived. Find the current version at on the Current Documents page. Scientific Working Groups on.
 Scientific Working Groups on Digital Evidence and Imaging Technology SWGDE/SWGIT Guidelines & Recommendations for Training in Digital & Multimedia Evidence Disclaimer: As a condition to the use of this
Scientific Working Groups on Digital Evidence and Imaging Technology SWGDE/SWGIT Guidelines & Recommendations for Training in Digital & Multimedia Evidence Disclaimer: As a condition to the use of this
Different-quality Re-demosaicing in Digital Image Forensics
 Different-quality Re-demosaicing in Digital Image Forensics 1 Bo Wang, 2 Xiangwei Kong, 3 Lanying Wu *1,2,3 School of Information and Communication Engineering, Dalian University of Technology E-mail:
Different-quality Re-demosaicing in Digital Image Forensics 1 Bo Wang, 2 Xiangwei Kong, 3 Lanying Wu *1,2,3 School of Information and Communication Engineering, Dalian University of Technology E-mail:
Two Improved Forensic Methods of Detecting Contrast Enhancement in Digital Images
 Two Improved Forensic Methods of Detecting Contrast Enhancement in Digital Images Xufeng Lin, Xingjie Wei and Chang-Tsun Li Department of Computer Science, University of Warwick, Coventry, CV4 7AL, UK
Two Improved Forensic Methods of Detecting Contrast Enhancement in Digital Images Xufeng Lin, Xingjie Wei and Chang-Tsun Li Department of Computer Science, University of Warwick, Coventry, CV4 7AL, UK
Empirical Study on Quantitative Measurement Methods for Big Image Data
 Thesis no: MSCS-2016-18 Empirical Study on Quantitative Measurement Methods for Big Image Data An Experiment using five quantitative methods Ramya Sravanam Faculty of Computing Blekinge Institute of Technology
Thesis no: MSCS-2016-18 Empirical Study on Quantitative Measurement Methods for Big Image Data An Experiment using five quantitative methods Ramya Sravanam Faculty of Computing Blekinge Institute of Technology
Digital Audio Watermarking With Discrete Wavelet Transform Using Fibonacci Numbers
 Digital Audio Watermarking With Discrete Wavelet Transform Using Fibonacci Numbers P. Mohan Kumar 1, Dr. M. Sailaja 2 M. Tech scholar, Dept. of E.C.E, Jawaharlal Nehru Technological University Kakinada,
Digital Audio Watermarking With Discrete Wavelet Transform Using Fibonacci Numbers P. Mohan Kumar 1, Dr. M. Sailaja 2 M. Tech scholar, Dept. of E.C.E, Jawaharlal Nehru Technological University Kakinada,
The Effect of Exposure on MaxRGB Color Constancy
 The Effect of Exposure on MaxRGB Color Constancy Brian Funt and Lilong Shi School of Computing Science Simon Fraser University Burnaby, British Columbia Canada Abstract The performance of the MaxRGB illumination-estimation
The Effect of Exposure on MaxRGB Color Constancy Brian Funt and Lilong Shi School of Computing Science Simon Fraser University Burnaby, British Columbia Canada Abstract The performance of the MaxRGB illumination-estimation
ENF ANALYSIS ON RECAPTURED AUDIO RECORDINGS
 ENF ANALYSIS ON RECAPTURED AUDIO RECORDINGS Hui Su, Ravi Garg, Adi Hajj-Ahmad, and Min Wu {hsu, ravig, adiha, minwu}@umd.edu University of Maryland, College Park ABSTRACT Electric Network (ENF) based forensic
ENF ANALYSIS ON RECAPTURED AUDIO RECORDINGS Hui Su, Ravi Garg, Adi Hajj-Ahmad, and Min Wu {hsu, ravig, adiha, minwu}@umd.edu University of Maryland, College Park ABSTRACT Electric Network (ENF) based forensic
Image De-Noising Using a Fast Non-Local Averaging Algorithm
 Image De-Noising Using a Fast Non-Local Averaging Algorithm RADU CIPRIAN BILCU 1, MARKKU VEHVILAINEN 2 1,2 Multimedia Technologies Laboratory, Nokia Research Center Visiokatu 1, FIN-33720, Tampere FINLAND
Image De-Noising Using a Fast Non-Local Averaging Algorithm RADU CIPRIAN BILCU 1, MARKKU VEHVILAINEN 2 1,2 Multimedia Technologies Laboratory, Nokia Research Center Visiokatu 1, FIN-33720, Tampere FINLAND
Aperture. The lens opening that allows more, or less light onto the sensor formed by a diaphragm inside the actual lens.
 PHOTOGRAPHY TERMS: AE - Auto Exposure. When the camera is set to this mode, it will automatically set all the required modes for the light conditions. I.e. Shutter speed, aperture and white balance. The
PHOTOGRAPHY TERMS: AE - Auto Exposure. When the camera is set to this mode, it will automatically set all the required modes for the light conditions. I.e. Shutter speed, aperture and white balance. The
International Journal of Advanced Research in Computer Science and Software Engineering
 Volume 3, Issue 4, April 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Novel Approach
Volume 3, Issue 4, April 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Novel Approach
Implementation of a Visible Watermarking in a Secure Still Digital Camera Using VLSI Design
 2009 nternational Symposium on Computing, Communication, and Control (SCCC 2009) Proc.of CST vol.1 (2011) (2011) ACST Press, Singapore mplementation of a Visible Watermarking in a Secure Still Digital
2009 nternational Symposium on Computing, Communication, and Control (SCCC 2009) Proc.of CST vol.1 (2011) (2011) ACST Press, Singapore mplementation of a Visible Watermarking in a Secure Still Digital
Countering Anti-Forensics of Lateral Chromatic Aberration
 IH&MMSec 7, June -, 7, Philadelphia, PA, USA Countering Anti-Forensics of Lateral Chromatic Aberration Owen Mayer Drexel University Department of Electrical and Computer Engineering Philadelphia, PA, USA
IH&MMSec 7, June -, 7, Philadelphia, PA, USA Countering Anti-Forensics of Lateral Chromatic Aberration Owen Mayer Drexel University Department of Electrical and Computer Engineering Philadelphia, PA, USA
Hiding Image in Image by Five Modulus Method for Image Steganography
 Hiding Image in Image by Five Modulus Method for Image Steganography Firas A. Jassim Abstract This paper is to create a practical steganographic implementation to hide color image (stego) inside another
Hiding Image in Image by Five Modulus Method for Image Steganography Firas A. Jassim Abstract This paper is to create a practical steganographic implementation to hide color image (stego) inside another
Copyright by Bettina and Uwe Steinmueller (Revision ) Publisher: Steinmueller Photo, California USA
 Page 1 Copyright 2002-2012 by Bettina and Uwe Steinmueller (Revision 2012-1) Publisher: Steinmueller Photo, California USA All rights reserved. No part of this publication may be reproduced, stored in
Page 1 Copyright 2002-2012 by Bettina and Uwe Steinmueller (Revision 2012-1) Publisher: Steinmueller Photo, California USA All rights reserved. No part of this publication may be reproduced, stored in
Virtual Restoration of old photographic prints. Prof. Filippo Stanco
 Virtual Restoration of old photographic prints Prof. Filippo Stanco Many photographic prints of commercial / historical value are being converted into digital form. This allows: Easy ubiquitous fruition:
Virtual Restoration of old photographic prints Prof. Filippo Stanco Many photographic prints of commercial / historical value are being converted into digital form. This allows: Easy ubiquitous fruition:
Digital Image Processing Introduction
 Digital Processing Introduction Dr. Hatem Elaydi Electrical Engineering Department Islamic University of Gaza Fall 2015 Sep. 7, 2015 Digital Processing manipulation data might experience none-ideal acquisition,
Digital Processing Introduction Dr. Hatem Elaydi Electrical Engineering Department Islamic University of Gaza Fall 2015 Sep. 7, 2015 Digital Processing manipulation data might experience none-ideal acquisition,
Automation of JPEG Ghost Detection using Graph Based Segmentation
 International Journal Of Computational Engineering Research (ijceronline.com) Vol. Issue. 2 Automation of JPEG Ghost Detection using Graph Based Segmentation Archana V Mire, Dr S B Dhok 2, Dr P D Porey,
International Journal Of Computational Engineering Research (ijceronline.com) Vol. Issue. 2 Automation of JPEG Ghost Detection using Graph Based Segmentation Archana V Mire, Dr S B Dhok 2, Dr P D Porey,
Wi-Fi Fingerprinting through Active Learning using Smartphones
 Wi-Fi Fingerprinting through Active Learning using Smartphones Le T. Nguyen Carnegie Mellon University Moffet Field, CA, USA le.nguyen@sv.cmu.edu Joy Zhang Carnegie Mellon University Moffet Field, CA,
Wi-Fi Fingerprinting through Active Learning using Smartphones Le T. Nguyen Carnegie Mellon University Moffet Field, CA, USA le.nguyen@sv.cmu.edu Joy Zhang Carnegie Mellon University Moffet Field, CA,
Digital Image Sharing and Removing the Transmission Risk Problem by Using the Diverse Image Media
 1 1 Digital Image Sharing and Removing the Transmission Risk Problem by Using the Diverse Image Media 1 Shradha S. Rathod, 2 Dr. D. V. Jadhav, 1 PG Student, 2 Principal, 1,2 TSSM s Bhivrabai Sawant College
1 1 Digital Image Sharing and Removing the Transmission Risk Problem by Using the Diverse Image Media 1 Shradha S. Rathod, 2 Dr. D. V. Jadhav, 1 PG Student, 2 Principal, 1,2 TSSM s Bhivrabai Sawant College
Autocomplete Sketch Tool
 Autocomplete Sketch Tool Sam Seifert, Georgia Institute of Technology Advanced Computer Vision Spring 2016 I. ABSTRACT This work details an application that can be used for sketch auto-completion. Sketch
Autocomplete Sketch Tool Sam Seifert, Georgia Institute of Technology Advanced Computer Vision Spring 2016 I. ABSTRACT This work details an application that can be used for sketch auto-completion. Sketch
How Many Pixels Do We Need to See Things?
 How Many Pixels Do We Need to See Things? Yang Cai Human-Computer Interaction Institute, School of Computer Science, Carnegie Mellon University, 5000 Forbes Avenue, Pittsburgh, PA 15213, USA ycai@cmu.edu
How Many Pixels Do We Need to See Things? Yang Cai Human-Computer Interaction Institute, School of Computer Science, Carnegie Mellon University, 5000 Forbes Avenue, Pittsburgh, PA 15213, USA ycai@cmu.edu
