On the Robustness of Deep Neural Networks
|
|
|
- Arlene Harper
- 6 years ago
- Views:
Transcription
1 On the Robustness of Deep Neural Networks Manuel Günther, Andras Rozsa, and Terrance E. Boult Vision and Security Technology Lab, University of Colorado Colorado Springs May 27, Vulnerability of Deep Neural Networks Deep Neural Networks (DNNs) have become the quasi-standard in many machine learning tasks since they obtain state-of-the-art results and outperform more traditional machine learning models for problems in vision, image and speech processing, and many other tasks. One reason that DNNs have proven very useful is that they are one of the few algorithms that can make principled use of huge databases for training. However, despite their brilliant recognition capabilities, little is known about how DNNs achieve their accuracies, and even less is known about their robustness and their limitations. After Szegedy et al. [19] showed that deep networks have some intriguing properties, several researchers started actively exploring the limitations, and showed how easily the networks could be attacked or fooled demonstrating essential limits of the robustness of DNNs. This paper analyzes these two categories of attacks: adversarial images [19, 3], which are imperceptible perturbations to an input to turn it into another class, and fooling images [9], which look like none of the This research is based upon work funded in part by NSF IIS and in part by the Office of the Director of National Intelligence (ODNI), Intelligence Advanced Research Projects Activity (IARPA), via IARPA R&D Contract No The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of the ODNI, IARPA, or the U.S. Government. The U.S. Government is authorized to reproduce and distribute reprints for Governmental purposes notwithstanding any copyright annotation thereon. 1
2 Hammerhead Adversarial Scuba Diver Fooling Hammerhead Figure 1: Adversarial and Fooling Images. Examples show an original image classified as hammerhead, an associated adversarial image, and an associated fooling image. The adversarial image has added noise after which the network incorrectly classifies it as a scuba diver. The fooling image looks nothing like normal images, but the network classifies it as hammerhead shark with very high confidence. This paper discussed issues related to such adversarial and fooling images including how to improve robustness by mitigating their impact. classes, see Fig. 1. While a deep network will always have a most-likely class, one might hope that for an unknown input, all classes would have a low probability and that thresholding on uncertainty would reject unknown classes. Recent papers have shown how to produce fooling [9], rubbish [3] and adversarial images [19, 3, 8] that are visually far from the labeled class, but produce high-confidence scores for that label. Thresholding on uncertainty is not sufficient to determine what is unknown, illustrating that there are fundamental issues that need to be understood about the robustness of deep networks. Thus, fooling and adversarial images are directly an issue of network robustness; we briefly review these concepts and then summarize the contributions of this paper. 1.1 Fooling Images Nguyen et al. [9] used images containing random and non-random patterns, which are far from any class that the network has learned to predict. By applying small non-random perturbations to these images, the DNN will predict, whatever you want it to predict. Particularly, given a starting image, a DNN that was trained to predict classes, and the desired output class, a perturbation is computed using gradient ascent [9], which will increase the 2
3 Figure 2: Fooling Images. Fooling images for hand-written digits were generated on a LeNet pretrained on the MNIST image training set. Starting from the pattern in the center, fooling images for different labels and three different desired classification confidences (F50, F90 and F99) are produced. probability of the desired class. This procedure is iteratively executed until the classification probability reached the desired confidence level. Fig. 2 shows some examples of fooling images. Starting from a pattern in the center the image is evolved to increase the DNN s classification as one of the digits: 0, 1, 4 and 8. The images with 50 % confidence, which we call F50, do not look much alike the desired class. For labels 0 and 1, images that are classified with higher confidences start to resemble the desired digit at least for this starting image. For labels 4 and 8, the digit is not well pronounced even though they have moved relatively far from the starting image. Note that Nguyen et al. [9] present other fooling images for the MNIST dataset on their web page. 1.2 Adversarial Images Although fooling images show weaknesses of deep networks, a different type of threat was introduced by so-called adversarial examples. Similarly to fooling images, adversarial examples are based on perturbations added to images that change the classification. The difference is that for adversarial examples the starting image is a correctly classified and the perturbations are ideally imperceptible. Because they are imperceptible, some researchers claim that adversarial images pose a security threat, an issue we examine later. After Szegedy et al. [19] introduced the concept of adversarial images, several techniques were engineered to create those. The first method that could reliably and efficiently produce 3
4 Figure 3: Adversarial Images. Adversarial images for hand-written digits were generated on a LeNet pretrained on the MNIST image training set. The first row shows the originating images, the three rows below show the FGS, FGV and HC-1 adversarial images, while their classifications are given below. Though each adversarial image generation type can generate different classification results, images were selected such that they are classified identically (per column). adversarial examples was introduced by Goodfellow et al. [3]. Their Fast Gradient Sign (FGS) method used the gradient of loss with respect to the input image in order to create perturbations. Given a correctly classified input image x and its gradient x, the adversarial image is x FGS = x+w sign( x) where w is such that the classification of x FGS just switches to another class. Note that in some papers, a fixed w is used that may produce larger perturbations making them more portable and stable, but also more visible. Rozsa et al. [13] adapted FGS by dropping the sign, yielding the Fast Gradient Value (FGV) method: x FGV = x + w x. They also introduced the so-called Hot/Cold (HC) approach, generating adversarial perturbations by simultaneously increasing the probability of the target (hot) class while reducing the probability of the original (cold) class. Herein we consider targeting either the closest class, HC-1, or all other classes (HC). The tutorial code includes methods for generating all three types of adversarial images: FGS, FGV and HC-1. Some of the exemplary images shown in Fig. 3 look noisier and slightly different from their originals. Adversarial images, however, only post a security threat if they are visually indistinguishable from the originals and clearly show the original class, while DNNs are predicting another label. To quantify the quality of the adversarial image, 4
5 several metrics are used. Goodfellow et al. [3], for example, used the L 1, L 2 and L norms of the perturbation as a quality measure. However, none of these measures are close to human perception. For example, L only measures the maximum pixel perturbation, independent of if this perturbation was in the object, an edge or in the background. To overcome this inconsistency, Rozsa et al. [13] introduces the Perceptual Adversarial Similarity Score (PASS), which is based on human perception. PASS values close to 1 indicate imperceptible perturbations, while smaller PASS values suggest stronger modifications. While the above works and others intentionally generate adversarial images to defeat deep networks, recent work [12] shows that adversarial inputs frequently occur naturally many errors by networks are images that are a small perturbation from being correct. 1.3 Contributions Since we still do not know why fooling and adversarial images exist in the first place, an important question is if we can find ways to limit the success of adversarial images. In Sec. 2 we review three different approaches that were proposed in the literature. First, we test how adversarial training [3, 13] can reduce the success rate of adversarial image generation, and we discuss the limitations of such training. Second, experiments by Graese et al. [4] used simple image preprocessing techniques to remove adversarial properties. Third, we discuss the work on Open Set Deep Network (OSDN) introduced by Bendale and Boult [1], review their findings on ImageNet data and do a new testing with MNIST to evaluate if we can correct their labels or at least predict the presence of adversarial or fooling images. Returning to potential causes, an idea independently developed by the authors of [14] and our team is that adversarial images were the result of aliasing. In Sec. 3, we perform experiments that reject this hypothesis by showing that a network that cannot be affected by aliasing is still susceptible to adversarial image generation. Throughout this article, we review material from the literature, but to help the reader we use tutorial-like code and focus our evaluations on hand-written digit classification using the MNIST dataset, and LeNet, a not-so-deep neural network, which is well-investigated 5
6 in the literature, while being small enough to easily run experiments on a laptop. The MNIST dataset consists of images of hand-written digits, which are cropped to be in the center of pixel gray-scale images. Examples are displayed in the first row of Fig. 3. LeNet consists of two convolutional layers (conv1 and conv2) followed by two fully-connected layers (ip1 and ip2). The classification is performed using a softmax layer, which turns the ten outputs of layer ip2 into classification probabilities. This example is part of many deep network tutorials, and we expand on that with tutorial-like code for adversarial images, fooling images and Open Set Deep Networks. This code is based on the Caffe framework [5] and implemented using its Python interface. The code requires some small modifications to the original Caffe code refer to our installation instructions. Our code can be found at 2 Techniques to Manage Adversarial and Fooling Images Recently, researchers have stated that adversarial examples can seriously undermine the security of the system supported by the DCNN [11] because the incorrect classification could potentially lead to an incorrect action with consequences. For example, if the digits signifying an amount on a check were crafted to be adversarial, the amount of money transferred between accounts could be altered. Though a defense is presented [11], it was later shown [2] to be fundamentally flawed and, hence, provides no real defense. Other researchers have been exploring techniques, which provide some real defense, three of which we explore deeper in this section. 2.1 Does Adversarial Training Improve Robustness? One simple idea of generating more stable networks is by data augmentation. When a DNN is fooled by small modifications to the input, augmenting the training with these kinds of images should be able to reduce these properties. Indeed, Szegedy et al. [19] and Goodfellow et al. [3] showed that training a network explicitly or implicitly using adversarial 6
7 images improves the stability towards those adversarial images. However, they performed experiments only on a single type of adversarial images, i.e., FGS, and they used images that were not adversarial in that the perturbations were clearly visible. From their experiments, it is unclear if such an adversarial training will improve the stability for other adversarial image generation techniques such as FGV or HC. In our work [13], we explored training with a greater range of adversarial types, showing that increased diversity improved both network accuracy and robustness. That paper showed that going a bit farther than the minimum adversarial, say by 5%, improved accuracy more than just using minimally adversarial images, including showing that such training improved deep networks on ImageNet. However, Rozsa et al. [13] just mixed various adversarial image types together and did not study how training with one type impacted robustness with respect to others. Using the MNIST dataset, we do adversarial training experiments, but this time we evaluate several techniques to compute adversarial images for training, and test robustness across types. First, we train a basic LeNet model on the MNIST training set for 100k iterations. Afterward, we use that network to extract one adversarial image with FGS and for FGV, as well as nine adversarial images for each training set image with HC. For each of the adversarial image types, we fine-tuned the basic LeNet using only the adversarial images of that type. The fine-tuning for FGS and FGV used 20k iterations, while we chose 50k iterations for the HC adversarial images as we have more of those. The tutorial code includes the networks and the images. Finally, we evaluated the three fine-tuned LeNets plus our basic LeNet. We tried to extract adversarial images on the MNIST test set using the four networks it is not sufficient to test adversarial images generated on the basic network since fine-tuning modifies the network s weights such that many of original adversarial images are no longer adversarial. We computed, how often we could find an adversarial perturbation that would change the classification of the fine-tuned network, and computed the average PASS value of the successful cases. The results are presented in Tab. 1. We can first see that fine-tuning 7
8 FGS FGV HC Model Accuracy Rate PASS Rate PASS Rate PASS LeNet % % % % 0.73 LeNet+FGS % % % % 0.72 LeNet+FGV % % % % 0.71 LeNet+HC % % % % 0.71 Table 1: Training with Adversarial Images. We compare the original LeNet model with the models fine-tuned with FGS, FGV and HC adversarial images. The second column presents classification accuracy of the networks. The remaining columns provide success rate and average PASS value for adversarial images generated with FGS, FGV, and HC on the MNIST test set. with any type of adversarial images improves the (already very high) classification accuracy a little. This is not a surprise, as data augmentation is known to increase classification accuracies. More interestingly, for FGS and FGV the success rate of adversarial images does drop moderately, the highest drop, i.e., from 85 % to 60 % is seen when trained with FGV adversarial images. On the other hand, HC adversarial images could be generated in almost all cases, and adversarial training did not reduce this success rate. In all cases, the quality of adversarial images did not change substantially, indicated by an almost stable average PASS value per technique. Hence, we can conclude that adversarial training can slightly reduce the number of FGS and FGV adversarial images, but HC adversarial images can not be combated with adversarial training, even when training with them. 2.2 Fighting Adversarial Images with Image Preprocessing Most real world applications of deep learning use inputs from a camera or scanned images, where the input images will never be perfectly captured, but contain slight transformations, such as shifting or blurring, and perturbations, such as noise. Hence, images generally undergo preprocessing before being input to the neural network. It is reasonable to ask if a simple image preprocessing could be sufficient to mitigate the effect of adversarial images. Graese et al. [4] investigated how images would be transformed in a real application, i.e., when (adversarial) images are printed on paper and recaptured for further processing. 8
9 Technique None Noise Blur Shift Combined Crops FGS 0.00 % % % % % % FGV 0.00 % % % % % % HC % % % % % % Accuracy % % % % % % Table 2: Fighting Adversarial Images with Preprocessing. The success of correcting the classification of adversarial images with several image preprocessing techniques is shown. For comparison, images with no perturbation are reported, too. Adversarial images were created with three different techniques: FGS, FGV and HC-1. The last row presents the classification accuracy on the original images that were preprocessed. To mimic the image acquisition process, they performed several preprocessing techniques such as shifting or blurring the image slightly, adding random noise to the image before classification, or scaling and re-cropping the image. Graese et al. [4] also explored a preprocessing specific to text-like problems, i.e., binarization and found that it was the most effective technique for destroying the tested adversarial image types. However, binarization is rather problem specific and, hence, not included in this analysis. In our experiments, we use the same basic LeNet and the same adversarial images from the last section, where we apply three types of modifications. First, the image is shifted with one pixel in random direction (left, right, top, bottom) and the removed row or column is added to the other side of the image. Second, the image is blurred with a Gaussian blur kernel with one pixel standard deviation. Third, random normal-distributed noise with zero mean and a standard deviation of one gray level is added to each pixel in the image. Finally, a combination of all processing steps is applied (first shift, then blur, and finally noise). After processing, all pixels are converted to integral values in [0,255]. The results of these different preprocessing steps are presented in Tab. 2. To see if the preprocessing has any impact on the classification accuracy, we classified all test images that were preprocessed with the presented techniques. When shifting and blurring the image, the classification accuracy drops moderately, i.e., from % with the original unprocessed images to % using blurred images and % with shifted images. Interestingly, 9
10 adding small noise does not affect the classification accuracy at all. The highest drop in performance is obtained when combining all preprocessing techniques. Further, we tried to classify the adversarial images after shifting, blurring and adding noise. Tab. 2 reports the percentage of adversarial images that were classified correctly after applying preprocessing. Due to the very noisy nature of FGS adversarial images, adding noise did not help too much, only 28 % of those images were classified correctly. FGV and HC-1 adversarial images usually contain less visible perturbations and, hence, adding noise works considerably better. However, other preprocessing techniques such as blurring and shifting removed the adversarial properties of around two thirds of the adversarial images. Combining the techniques did not improve mitigation further. One technique that is often applied to improve classification accuracy is to take several crops of an image and average the results of these crops into the final classification. Previously, this preprocessing was not added to address adversarial robustness, but rather to improve network performance. However, we argue that these are related, as we show that using crops helps destroy adversarial properties. The performance improvement is likely because it impacts natural adversarials [12], where the networks misclassifies the center crop. While Graese et al. [4] rescaled the images before cropping, which is not common practice, we simply padded the images with one black pixel on each side, resulting in a pixel image. As common in literature, we take five crops of the image, i.e., top-left, top-right, bottom-left, bottom-right and the center crop, where the latter corresponds to the original image. In literature, images are often also mirrored, but for the digit classification this makes no sense. Hence, we run the five crops trough our network and compute the average of the ip2 features, and classify the image based on this average. The results are given in the last column of Tab. 2. As we can see, using this simple technique already 90 % of the adversarial images are no longer adversarial. Interestingly, this comes at the price of very slightly reduced accuracy, which is almost identical to the accuracy without preprocessing. As a result, we can see that very small perturbations to the input images can reveal their adversarial properties in about two thirds of the cases. We can assume that adding 10
11 larger shifts, a stronger blurring and more noise will further increase the number of adversarial images that will be corrected. However, these perturbations may slightly decrease classification accuracy, and stronger perturbations will decrease accuracy even more. Fortunately, as Graese et al. [4] demonstrated this decrease in accuracy can be prevented when the original network is trained or fine-tuned using the same perturbations as applied to the test set images. Graese et al. [4] suggest that normal image acquisition would destroy most adversarial images. In recent work, Kurakin et al. [6] showed that some adversarial images from ImageNet can printed and recaptured, persisting as adversarial images. However, their approach was rather artificial by printing the images in higher resolution than the original images were. Even for those images, the rate of destroying adversarial properties of highquality adversarials with invisible noise was around %. While this suggests that many adversarial images might survive, its important to recall that the original network accuracy has only approximately 80 % top-1 accuracy, even 20 % of the adversarials surviving is not inherently more of a risk than standard classification errors. We also note, the paper does not discuss multiple crops. Hence, it is not clear if Kurakin et al. [6] truly contracts Graese et al. [4], but it does suggest that more work is needed to address the potential security concern in real settings. For now, the security concern some researchers are raising may largely be an artifact of not applying normal image preprocessing combined with state of the art deep network techniques, and are certainly a lower risk than some authors suggest. 2.3 Open Set Deep Networks for Adversarial and Fooling Images. In the previous section, we showed how to detect and correct adversarial images. Fooling images, however, pose a different problem, as there is no notion of correcting the images, as they do not represent a class that is known by the classifier. Unfortunately, in general classifiers are closed set, and will classify any input image as one of the classes it was trained on. Rather, the classifier should be open set and able to reject the image as unknown. The first approach extending DNNs to open set recognition was presented by Bendale 11
12 and Boult [1]. To reject an image as unknown, the representation (activation vector) at a given layer of the DNN was averaged over all images of a class. They call this the Mean Activation Vector (MAV). They then compute an Weibull-based calibration which, together with the MAV, served as a coarse representation of the networks known about a class. When an input image is classified as a given class, the Open Set Deep Network (OSDN) also checks if the representation was close enough to the MAV, and if it was not, the input image can be rejected as unknown, or the various class probabilities can be recomputed using openmax. The OSDN [1] was a proof of concept using AlexNet on ImageNet, testing with some fooling, adversarial and open-set images, i.e., normal images from unknown classes. Their paper presented the first adversarial image detector and showed that blurring and processing with the OSDN could correct the classification, see Fig. 1. However, their primary focus was on open set including fooling images. They showed the network was fairly good at detecting fooling images. We replicate and expand on their experiments, adapting and running it on the MNIST dataset with a formal experiment on detection or correction rates of adversarial and fooling images. To implement OSDN on MNIST, the mean activation vectors of the first fully-connected layer (ip1) is computed from the correctly classified training images of each of the 10 classes, and the cosine distances of all training set activation vectors to their corresponding MAV s is computed. Weibull probability distributions are estimated on these distances, which allows us to estimate the probability of exclusion for any input image. For a test image, the activation vector is computed, compared to all MAV s, and probably of it being unknown is computed via the Weibull-model for each class. These exclusion probabilities are then merged with the original decision of the network via the openmax algorithm. The result is 11 probabilities, one for each class plus one for the input being unknown. Note that these results rely on some parameters of the OSDN, such as the tailsize and α, which need to be selected appropriately. For more details, please refer to [1]. Tab. 3 presents results using the OSDN to classify MNIST examples, with columns for closed set accuracy after openmax processing, estimated probably of the input to be 12
13 Data Accuracy Unknown Same Target Other Label Test Set % 0.63 % 1.30 % FGS Adversarial % 1.82 % 5.76 % 1.31 % FGV Adversarial % 0.30 % 0.00 % 0.40 % HC-1 Adversarial % 0.60 % 0.10 % 0.40 % Fooling 50 % % % % Fooling 90 % % % 3.75 % Fooling 99 % % % 1.42 % Table 3: Open Set Network. Images are rejected to be unknown by the open set deep network. The first row shows classification accuracy and rejection rate on the original test data. Below, rejection rates for adversarial images of different types are presented, including the number of adversarial images that are still classified as the targeted class. Note that adversarial images are created only for those test images that were correctly classified by the original LeNet. Finally, rejection rates and targeted class rates for fooling images of different strength are provided. unknown, frequency of the image staying in its target class, and the frequency in which it ended up in another incorrect class. The first row of the table shows that the classification accuracy on the original images dropped moderately, i.e., from % to %, but not dramatically. The next three rows present the results on the different types of adversarial images, which were created from the images that were classified correctly by the original network. For FGV and HC-1 adversarial images, almost all of these images are corrected, i.e., they are now classified as the original class. Below 1 % of the adversarial examples are rejected to be unknown, and almost no image was classified as the same (wrong) class as it was before and that it was aimed at in case of HC-1. FGS adversarial images seem to be a little bit harder to detect, but still 91 % of them are classified as the originating class by the OSDN, 2 % are classified to be unknown and 6 % survived at the same class. The remaining images changed the class label to another class, which is neither the adversarial nor the originating class. To test the ability of the OSDN to reject fooling images, we created such images using an adapted version of the source code provided by [9], which is provided in our source 13
14 Figure 4: Fooling Images from Random Initialization. Fooling images are created for each of the 10 digits for three values of classification probabilities: 50 %, 90 % and 99 %. For each of three random starting images, all fooling images are presented. Images with green border are classified unknown, red border images are accepted as the target class, and yellow border images are accepted for another class. For missing images, the generation of the fooling image did not succeed. code. Starting from random images, we created 100 fooling images for each digit, in several classification probabilities, i.e., F50, F90, and F99. Examples are shown in Fig. 4. For F50 and F90, most of the images do not represent the targeted class very well, while for F99 fooling images, several of the images seem to represent instances of the targeted classes (with a little bit of imagination). The response of the OSDN on fooling images is in the last three rows of Tab. 3. For the F50 and F90 fooling images, OSDN was able to reject around 70 % of the images as unknown. For F50, 12 % of the images were assigned a different label, and only 19 % still obtained the targeted label. Looking at the examples in Fig. 4, we can see that most of the 14
15 images that have contents that could be interpreted as the according digit are classified by the network to contain that digit, indicated by a red border. Few of the images, those with yellow border, are accepted by the network, but with a different label as the one used to produce the fooling image. Images with a green border are detected by the OSDN to be unknown, which is what we want to happen. Here, we report results for a tailsize of 200 and alpha of 2, which provides a reasonable trade-off between accuracy on the raw images and correction or rejection rate for adversarial and fooling images, but we note that a wide range of performance can be achieved depending on the desired accuracy or robustness. While running the OSDN experiments, we found that the tailsize influences the classification accuracy in the clean test set and the classification accuracy (i.e., the correction) of adversarial images. Larger tailsizes will results in better accuracy on the clean test set, and smaller tailsizes increase the adversarial image correction. When using a tailsize of 1000, for example, the classification accuracy on the test images drops to 93 %, but it removes all FGS, FGV and HC-1 adversarials from reaching the target, and rejects 41 % of the F99 fooling images as unknown, and 88 % of the F50 and F90 fooling images. A tailsize of 20, on the other hand, keeps the classification accuracy of clean samples as high as 99 %, but leaves 51 % of the FGS and 11 % of the FGV and HC-1 adversarial images to be classified as the targeted class, as well as 83 % of the F90 fooling images and 97 % of the F99 fooling images. A more detailed analysis of the parameters is left as exercise for the readers, e.g., using the provided code. One difference between our experiments and the work of Bendale and Boult [1] is, which layer of the network was used. While we used a deeper layer (ip1) in the network, Bendale and Boult performed experiments with the last network layer (FC8 on AlexNet). However, in unreported results, other layers (FC7 of AlexNet) performed similarly. We also tested OSDN on LeNet by computing the MAV from layer ip2. While it did very well on adversarial images, it was not as accurate on fooling images. The much lower dimensionality of ip2 is likely why using that layer provides much weaker performance for MNIST fooling images. Bendale and Boult [1] worked with features of 1000 classes; it is interesting to see that the 15
16 OSDN model transitioned quite well on MNIST when using ip1. 3 Can Adversarial Images be explained by Aliasing? So far, we showed techniques to help manage adversarial images. However, we still do not know, why adversarial images exist. Adversarial perturbations tend to add high frequency information to the image, leading to a misclassification. Furthermore, DNNs perform some kind of spatial resolution reduction. Looking at this from a signal processing point of view, it seems obvious that aliasing could impact networks and that aliased information might lead to misclassification. As the Niquist-Shannon sampling theorem [10, 15] shows, instead of being ignored, high-frequency information above the sampling rate folds over into lowfrequency information. While not presented here, examining the FFT of MNIST network data at various layers shows significant high-frequency information within each layer of the network. Hence, the (imperceptible) high-frequency information that is introduced by adversarial images could naturally be turned into low-frequency information, i.e., it would be aliased. Could this be the root cause of adversarial images? To investigate if the aliasing effect causes adversarial images to be so successful, we ran experiments using LeNet. In LeNet, the two convolutional layers (conv1 and conv2) are each followed by a max-pooling layer, which performs sampling by taking taking the maximum of a 2 2 pixel region. To make it impossible for the network to be affected by aliasing, before each of the pooling layers we added another convolutional layer with fixed (non-learnable) weights. These convolution layers perform a Gaussian blurring of the output of the previous (original) convolution layer, with a Gaussian standard deviation σ set to 1.25, so that basically no high-frequency information survived. We trained both the LeNet with these additional blurring layers for anti-aliasing, and the original LeNet on the MNIST training set for 50k iterations using the same training strategy. Interestingly, classification accuracies between the original network (99.17 %) and the blurred network (98.84 %) differ only slightly. Then, we tried to generate FGV adver- 16
17 Adversarial Label Source Label (a) Original LeNet 100% 80% 60% 40% 20% 0% Adversarial Label Source Label (b) Anti-Aliased LeNet 100% 80% 60% 40% 20% 0% Number of Images Original Blurred Perceptual Adversarial Similarity Score (PASS) (c) PASS distribution Figure 5: Adversarial Labels of LeNet with and without Aliasing. FGV adversarial image labels were generated with (a) the original LeNet and (b) the LeNet trained with blurring to reduce aliasing. Colors in the confusion matrices indicate the relative number of labels, while exact numbers are given in the cells. (c) contains a histogram of PASS values for both networks. sarials of the MNIST test images with both networks. If aliasing causes adversarial images, we would expect to see dramatic reduction in the number of adversarial images that we could generate, or in the PASS quality of them. Surprisingly, the number of adversarial images that we could generate using the anti-aliased network (9483) is even higher than using the original network (8811). Also, as shown in Fig. 5, the distribution of PASS values is very similar, and even the distribution of adversarial labels, i.e., the labels that the adversarial images obtained, is very comparable. Note that, in unpublished work, we have found similar results on more difficult datasets with deeper network structures. This conclusively shows that aliasing is not the cause of adversarial images, and puzzling anti-aliasing may actually increase susceptibility to adversarial generation. While our experiments relatively convincingly show that aliasing is not the cause of adversarial images, since networks repeatedly downsample without filtering, the experiments raise their own interesting questions about the robustness of deep networks why does aliasing not seem to impact deep network performance? 17
18 4 What the Results Tell us As we have shown in our experiments, adversarial and fooling images do not present such a big threat as people might think. Even simple image preprocessing techniques such as blurring, shifting or adding noise removes a good portion of the adversarial images. As Graese et al. [4] showed, these small perturbations will automatically occur in a normal image acquisition process, i.e., when an adversary uses a printed adversarial image to attack. Furthermore, a technique that is applied to most of the classification networks to improve classification accuracy, namely extracting different crops of the image, was able to eradicate 90 % of the adversarial images. In our example, we used only five different crops, which were only one pixel apart from each other. Other network architectures use many more, e.g., [17, 18, 16] use 144 different crops of the image. Extrapolating from our experiments, it is very unlikely that any adversarial image that was generated using only the center crop would survive averaging 144 crops. However, in the future people might be able to generate adversarial images that are based on several crops of the image, so a simple cropping might not help against those images. Another technique that we have used is the Open Set Deep Network (OSDN) [1], which inherently is designed to reject images that are of classes that the network did not train on. Although Bendale and Boult [1] claimed that the OSDN could easily detect adversarial and fooling images, they did not perform a statistical analysis. Here, we showed that the OSDN corrects most of the adversarial images, i.e., they are classified as the original class, and are, hence, not adversarial anymore. Also, many of the fooling images at least the ones which would be difficult to classify by humans are detected as unknown. We have to note that we only used difficult adversarial images, with a minimal perturbation for which the adversarial class is predicted with only a slightly higher probability than the original class. Hence, the OSDN was able to correct these weights easily. When creating adversarial images with larger perturbations it would increase the probability of the adversarial class, e.g., a minimum probability of 50 %, many of these images might not be detected or corrected by 18
19 the OSDN. However, the quality of the adversarial images will also get worse, e.g., in terms of PASS values, and it will be more visible that these images are modified. Its is also likely that detectors can be trained for such adversarial images [7] and it would be easy to extend the OSDN to include such a detector. Also, we have performed experiments only for three different types of adversarial image generation techniques; other techniques might generate much better adversarial images that are harder to detect or correct by the OSDN. In this tutorial, we have run experiments only on a small-scale dataset and a small-scale network. The main purpose of this tutorial is to provide an easy entrance into A) generating adversarial and fooling images, B) implementing easy image processing algorithms to fight adversarial images, and C) using the open set deep network addition to normal classification networks to correct adversarial and detect fooling images. For this purpose, we provide the source code to rerun our experiments, so that researchers have a starting point to develop similar ideas or test them on more difficult databases. With this, we hope to foster more research in the direction of open set classification and improving the robustness of deep networks. References [1] A. Bendale and T. E. Boult. Toward open set deep networks. In The IEEE Conf. on Computer Vision and Pattern Recognition (CVPR), pages , , 12, 15, 18 [2] N. Carlini and D. Wagner. Defensive distillation is not robust to adversarial examples. arxiv preprint arxiv: , [3] I. J. Goodfellow, J. Shlens, and C. Szegedy. Explaining and harnessing adversarial examples. In Int. Conf. on Learning Representation (ICLR), , 2, 4, 5, 6 [4] A. Graese, A. Rozsa, and T. E. Boult. Assessing threat of adversarial examples on deep neural networks. In IEEE Int. Conf. on Mach. Learn. and App. (ICMLA), , 8, 9, 10, 11, 18 [5] Y. Jia, E. Shelhamer, J. Donahue, S. Karayev, J. Long, R. Girshick, S. Guadarrama, and T. Darrell. Caffe: Convolutional architecture for fast feature embedding. In Int. Conf. on Multimedia. ACM,
20 [6] A. Kurakin, I. Goodfellow, and S. Bengio. Adversarial examples in the physical world. In Workshop at Int. Conf. Learning Representatin, [7] J. H. Metzen, T. Genewein, V. Fischer, and B. Bischoff. On Detecting Adversarial Perturbations. In ICLR 2017, [8] S.-M. Moosavi-Dezfooli, A. Fawzi, and P. Frossard. Deepfool: a simple and accurate method to fool deep neural networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages , [9] A. Nguyen, J. Yosinski, and J. Clune. Deep neural networks are easily fooled: High confidence predictions for unrecognizable images. In IEEE Computer Vision and Pattern Recognition (CVPR), , 2, 3, 13 [10] H. Nyquist. Certain topics in telegraph transmission theory. In American Institute of Electrical Engineers Transactions, volume 47, pages , April [11] N. Papernot, P. McDaniel, X. Wu, S. Jha, and A. Swami. Distillation as a defense to adversarial perturbations against deep neural networks. In IEEE Sym. Security and Privacy, [12] A. Rozsa, M. Günther, E. M. Rudd, and T. E. Boult. Are facial attributes adversarially robust? In Int. Conf. on Pattern Recognition (ICPR), , 10 [13] A. Rozsa, E. M. Rudd, and T. E. Boult. Adversarial diversity and hard positive generation. In IEEE Conf. on Computer Vision and Pattern Recognition (CVPR) Workshops, , 5, 7 [14] S. Sabour, Y. Cao, F. Faghri, and D. J. Fleet. Adversarial manipulation of deep representations. Int. Conf. Learning Representations (ICLR) 2016, [15] C. Shannon. Communication in the presence of noise. Proc. of the IRE, 37(1):10 21, [16] C. Szegedy, S. Ioffe, V. Vanhoucke, and A. Alemi. Inception-v4, inception-resnet and the impact of residual connections on learning. In Int. Conf. on Learning Representation (ICLR) Workshop, [17] C. Szegedy, W. Liu, Y. Jia, P. Sermanet, S. Reed, D. Anguelov, D. Erhan, V. Vanhoucke, and A. Rabinovich. Going deeper with convolutions. In IEEE Conf. on Computer Vision and Pattern Recognition (CVPR), [18] C. Szegedy, V. Vanhoucke, S. Ioffe, J. Shlens, and Z. Wojna. Rethinking the inception architecture for computer vision. In IEEE Conf. on Computer Vision and Pattern Recognition (CVPR), pages ,
21 [19] C. Szegedy, W. Zaremba, I. Sutskever, J. Bruna, D. Erhan, I. Goodfellow, and R. Fergus. Intriguing properties of neural networks. In Int. Conf. on Learning Representations. Computational and Biological Learning Society, , 2, 3, 6 21
arxiv: v1 [cs.cv] 12 Jul 2017
![arxiv: v1 [cs.cv] 12 Jul 2017 arxiv: v1 [cs.cv] 12 Jul 2017](/thumbs/79/79524156.jpg) NO Need to Worry about Adversarial Examples in Object Detection in Autonomous Vehicles Jiajun Lu, Hussein Sibai, Evan Fabry, David Forsyth University of Illinois at Urbana Champaign {jlu23, sibai2, efabry2,
NO Need to Worry about Adversarial Examples in Object Detection in Autonomous Vehicles Jiajun Lu, Hussein Sibai, Evan Fabry, David Forsyth University of Illinois at Urbana Champaign {jlu23, sibai2, efabry2,
Adversarial examples in Deep Neural Networks. Luiz Gustavo Hafemann Le Thanh Nguyen-Meidine
 Adversarial examples in Deep Neural Networks Luiz Gustavo Hafemann Le Thanh Nguyen-Meidine Agenda Introduction Attacks and Defenses NIPS 2017 adversarial attacks competition Demo Discussion 2 Introduction
Adversarial examples in Deep Neural Networks Luiz Gustavo Hafemann Le Thanh Nguyen-Meidine Agenda Introduction Attacks and Defenses NIPS 2017 adversarial attacks competition Demo Discussion 2 Introduction
CROSS-LAYER FEATURES IN CONVOLUTIONAL NEURAL NETWORKS FOR GENERIC CLASSIFICATION TASKS. Kuan-Chuan Peng and Tsuhan Chen
 CROSS-LAYER FEATURES IN CONVOLUTIONAL NEURAL NETWORKS FOR GENERIC CLASSIFICATION TASKS Kuan-Chuan Peng and Tsuhan Chen Cornell University School of Electrical and Computer Engineering Ithaca, NY 14850
CROSS-LAYER FEATURES IN CONVOLUTIONAL NEURAL NETWORKS FOR GENERIC CLASSIFICATION TASKS Kuan-Chuan Peng and Tsuhan Chen Cornell University School of Electrical and Computer Engineering Ithaca, NY 14850
Tiny ImageNet Challenge Investigating the Scaling of Inception Layers for Reduced Scale Classification Problems
 Tiny ImageNet Challenge Investigating the Scaling of Inception Layers for Reduced Scale Classification Problems Emeric Stéphane Boigné eboigne@stanford.edu Jan Felix Heyse heyse@stanford.edu Abstract Scaling
Tiny ImageNet Challenge Investigating the Scaling of Inception Layers for Reduced Scale Classification Problems Emeric Stéphane Boigné eboigne@stanford.edu Jan Felix Heyse heyse@stanford.edu Abstract Scaling
Learning Pixel-Distribution Prior with Wider Convolution for Image Denoising
 Learning Pixel-Distribution Prior with Wider Convolution for Image Denoising Peng Liu University of Florida pliu1@ufl.edu Ruogu Fang University of Florida ruogu.fang@bme.ufl.edu arxiv:177.9135v1 [cs.cv]
Learning Pixel-Distribution Prior with Wider Convolution for Image Denoising Peng Liu University of Florida pliu1@ufl.edu Ruogu Fang University of Florida ruogu.fang@bme.ufl.edu arxiv:177.9135v1 [cs.cv]
Biologically Inspired Computation
 Biologically Inspired Computation Deep Learning & Convolutional Neural Networks Joe Marino biologically inspired computation biological intelligence flexible capable of detecting/ executing/reasoning about
Biologically Inspired Computation Deep Learning & Convolutional Neural Networks Joe Marino biologically inspired computation biological intelligence flexible capable of detecting/ executing/reasoning about
Understanding Neural Networks : Part II
 TensorFlow Workshop 2018 Understanding Neural Networks Part II : Convolutional Layers and Collaborative Filters Nick Winovich Department of Mathematics Purdue University July 2018 Outline 1 Convolutional
TensorFlow Workshop 2018 Understanding Neural Networks Part II : Convolutional Layers and Collaborative Filters Nick Winovich Department of Mathematics Purdue University July 2018 Outline 1 Convolutional
Adversarial Attacks on Face Detectors using Neural Net based Constrained Optimization
 Adversarial Attacks on Face Detectors using Neural Net based Constrained Optimization Joey Bose University of Toronto joey.bose@mail.utoronto.ca September 26, 2018 Joey Bose (UofT) GeekPwn Las Vegas September
Adversarial Attacks on Face Detectors using Neural Net based Constrained Optimization Joey Bose University of Toronto joey.bose@mail.utoronto.ca September 26, 2018 Joey Bose (UofT) GeekPwn Las Vegas September
Deep Learning. Dr. Johan Hagelbäck.
 Deep Learning Dr. Johan Hagelbäck johan.hagelback@lnu.se http://aiguy.org Image Classification Image classification can be a difficult task Some of the challenges we have to face are: Viewpoint variation:
Deep Learning Dr. Johan Hagelbäck johan.hagelback@lnu.se http://aiguy.org Image Classification Image classification can be a difficult task Some of the challenges we have to face are: Viewpoint variation:
Colorful Image Colorizations Supplementary Material
 Colorful Image Colorizations Supplementary Material Richard Zhang, Phillip Isola, Alexei A. Efros {rich.zhang, isola, efros}@eecs.berkeley.edu University of California, Berkeley 1 Overview This document
Colorful Image Colorizations Supplementary Material Richard Zhang, Phillip Isola, Alexei A. Efros {rich.zhang, isola, efros}@eecs.berkeley.edu University of California, Berkeley 1 Overview This document
Adversarial Examples and Adversarial Training. Ian Goodfellow, OpenAI Research Scientist Presentation at Quora,
 Adversarial Examples and Adversarial Training Ian Goodfellow, OpenAI Research Scientist Presentation at Quora, 2016-08-04 In this presentation Intriguing Properties of Neural Networks Szegedy et al, 2013
Adversarial Examples and Adversarial Training Ian Goodfellow, OpenAI Research Scientist Presentation at Quora, 2016-08-04 In this presentation Intriguing Properties of Neural Networks Szegedy et al, 2013
Research on Hand Gesture Recognition Using Convolutional Neural Network
 Research on Hand Gesture Recognition Using Convolutional Neural Network Tian Zhaoyang a, Cheng Lee Lung b a Department of Electronic Engineering, City University of Hong Kong, Hong Kong, China E-mail address:
Research on Hand Gesture Recognition Using Convolutional Neural Network Tian Zhaoyang a, Cheng Lee Lung b a Department of Electronic Engineering, City University of Hong Kong, Hong Kong, China E-mail address:
Lecture 23 Deep Learning: Segmentation
 Lecture 23 Deep Learning: Segmentation COS 429: Computer Vision Thanks: most of these slides shamelessly adapted from Stanford CS231n: Convolutional Neural Networks for Visual Recognition Fei-Fei Li, Andrej
Lecture 23 Deep Learning: Segmentation COS 429: Computer Vision Thanks: most of these slides shamelessly adapted from Stanford CS231n: Convolutional Neural Networks for Visual Recognition Fei-Fei Li, Andrej
Camera Model Identification With The Use of Deep Convolutional Neural Networks
 Camera Model Identification With The Use of Deep Convolutional Neural Networks Amel TUAMA 2,3, Frédéric COMBY 2,3, and Marc CHAUMONT 1,2,3 (1) University of Nîmes, France (2) University Montpellier, France
Camera Model Identification With The Use of Deep Convolutional Neural Networks Amel TUAMA 2,3, Frédéric COMBY 2,3, and Marc CHAUMONT 1,2,3 (1) University of Nîmes, France (2) University Montpellier, France
Detection and Segmentation. Fei-Fei Li & Justin Johnson & Serena Yeung. Lecture 11 -
 Lecture 11: Detection and Segmentation Lecture 11-1 May 10, 2017 Administrative Midterms being graded Please don t discuss midterms until next week - some students not yet taken A2 being graded Project
Lecture 11: Detection and Segmentation Lecture 11-1 May 10, 2017 Administrative Midterms being graded Please don t discuss midterms until next week - some students not yet taken A2 being graded Project
Vehicle Color Recognition using Convolutional Neural Network
 Vehicle Color Recognition using Convolutional Neural Network Reza Fuad Rachmadi and I Ketut Eddy Purnama Multimedia and Network Engineering Department, Institut Teknologi Sepuluh Nopember, Keputih Sukolilo,
Vehicle Color Recognition using Convolutional Neural Network Reza Fuad Rachmadi and I Ketut Eddy Purnama Multimedia and Network Engineering Department, Institut Teknologi Sepuluh Nopember, Keputih Sukolilo,
To Post or Not To Post: Using CNNs to Classify Social Media Worthy Images
 To Post or Not To Post: Using CNNs to Classify Social Media Worthy Images Lauren Blake Stanford University lblake@stanford.edu Abstract This project considers the feasibility for CNN models to classify
To Post or Not To Post: Using CNNs to Classify Social Media Worthy Images Lauren Blake Stanford University lblake@stanford.edu Abstract This project considers the feasibility for CNN models to classify
GESTURE RECOGNITION FOR ROBOTIC CONTROL USING DEEP LEARNING
 2017 NDIA GROUND VEHICLE SYSTEMS ENGINEERING AND TECHNOLOGY SYMPOSIUM AUTONOMOUS GROUND SYSTEMS (AGS) TECHNICAL SESSION AUGUST 8-10, 2017 - NOVI, MICHIGAN GESTURE RECOGNITION FOR ROBOTIC CONTROL USING
2017 NDIA GROUND VEHICLE SYSTEMS ENGINEERING AND TECHNOLOGY SYMPOSIUM AUTONOMOUS GROUND SYSTEMS (AGS) TECHNICAL SESSION AUGUST 8-10, 2017 - NOVI, MICHIGAN GESTURE RECOGNITION FOR ROBOTIC CONTROL USING
Introduction to Machine Learning
 Introduction to Machine Learning Deep Learning Barnabás Póczos Credits Many of the pictures, results, and other materials are taken from: Ruslan Salakhutdinov Joshua Bengio Geoffrey Hinton Yann LeCun 2
Introduction to Machine Learning Deep Learning Barnabás Póczos Credits Many of the pictures, results, and other materials are taken from: Ruslan Salakhutdinov Joshua Bengio Geoffrey Hinton Yann LeCun 2
Adversarial Robustness for Aligned AI
 Adversarial Robustness for Aligned AI Ian Goodfellow, Staff Research NIPS 2017 Workshop on Aligned Artificial Intelligence Many thanks to Catherine Olsson for feedback on drafts The Alignment Problem (This
Adversarial Robustness for Aligned AI Ian Goodfellow, Staff Research NIPS 2017 Workshop on Aligned Artificial Intelligence Many thanks to Catherine Olsson for feedback on drafts The Alignment Problem (This
Continuous Gesture Recognition Fact Sheet
 Continuous Gesture Recognition Fact Sheet August 17, 2016 1 Team details Team name: ICT NHCI Team leader name: Xiujuan Chai Team leader address, phone number and email Address: No.6 Kexueyuan South Road
Continuous Gesture Recognition Fact Sheet August 17, 2016 1 Team details Team name: ICT NHCI Team leader name: Xiujuan Chai Team leader address, phone number and email Address: No.6 Kexueyuan South Road
Convolutional Neural Networks
 Convolutional Neural Networks Convolution, LeNet, AlexNet, VGGNet, GoogleNet, Resnet, DenseNet, CAM, Deconvolution Sept 17, 2018 Aaditya Prakash Convolution Convolution Demo Convolution Convolution in
Convolutional Neural Networks Convolution, LeNet, AlexNet, VGGNet, GoogleNet, Resnet, DenseNet, CAM, Deconvolution Sept 17, 2018 Aaditya Prakash Convolution Convolution Demo Convolution Convolution in
arxiv: v1 [cs.lg] 2 Jan 2018
![arxiv: v1 [cs.lg] 2 Jan 2018 arxiv: v1 [cs.lg] 2 Jan 2018](/thumbs/89/98840529.jpg) Deep Learning for Identifying Potential Conceptual Shifts for Co-creative Drawing arxiv:1801.00723v1 [cs.lg] 2 Jan 2018 Pegah Karimi pkarimi@uncc.edu Kazjon Grace The University of Sydney Sydney, NSW 2006
Deep Learning for Identifying Potential Conceptual Shifts for Co-creative Drawing arxiv:1801.00723v1 [cs.lg] 2 Jan 2018 Pegah Karimi pkarimi@uncc.edu Kazjon Grace The University of Sydney Sydney, NSW 2006
Adversarial Examples and Adversarial Training. Ian Goodfellow, OpenAI Research Scientist Presentation at HORSE 2016 London,
 Adversarial Examples and Adversarial Training Ian Goodfellow, OpenAI Research Scientist Presentation at HORSE 2016 London, 2016-09-19 In this presentation Intriguing Properties of Neural Networks Szegedy
Adversarial Examples and Adversarial Training Ian Goodfellow, OpenAI Research Scientist Presentation at HORSE 2016 London, 2016-09-19 In this presentation Intriguing Properties of Neural Networks Szegedy
arxiv: v1 [cs.ce] 9 Jan 2018
![arxiv: v1 [cs.ce] 9 Jan 2018 arxiv: v1 [cs.ce] 9 Jan 2018](/thumbs/77/76232406.jpg) Predict Forex Trend via Convolutional Neural Networks Yun-Cheng Tsai, 1 Jun-Hao Chen, 2 Jun-Jie Wang 3 arxiv:1801.03018v1 [cs.ce] 9 Jan 2018 1 Center for General Education 2,3 Department of Computer Science
Predict Forex Trend via Convolutional Neural Networks Yun-Cheng Tsai, 1 Jun-Hao Chen, 2 Jun-Jie Wang 3 arxiv:1801.03018v1 [cs.ce] 9 Jan 2018 1 Center for General Education 2,3 Department of Computer Science
DYNAMIC CONVOLUTIONAL NEURAL NETWORK FOR IMAGE SUPER- RESOLUTION
 Journal of Advanced College of Engineering and Management, Vol. 3, 2017 DYNAMIC CONVOLUTIONAL NEURAL NETWORK FOR IMAGE SUPER- RESOLUTION Anil Bhujel 1, Dibakar Raj Pant 2 1 Ministry of Information and
Journal of Advanced College of Engineering and Management, Vol. 3, 2017 DYNAMIC CONVOLUTIONAL NEURAL NETWORK FOR IMAGE SUPER- RESOLUTION Anil Bhujel 1, Dibakar Raj Pant 2 1 Ministry of Information and
Park Smart. D. Di Mauro 1, M. Moltisanti 2, G. Patanè 2, S. Battiato 1, G. M. Farinella 1. Abstract. 1. Introduction
 Park Smart D. Di Mauro 1, M. Moltisanti 2, G. Patanè 2, S. Battiato 1, G. M. Farinella 1 1 Department of Mathematics and Computer Science University of Catania {dimauro,battiato,gfarinella}@dmi.unict.it
Park Smart D. Di Mauro 1, M. Moltisanti 2, G. Patanè 2, S. Battiato 1, G. M. Farinella 1 1 Department of Mathematics and Computer Science University of Catania {dimauro,battiato,gfarinella}@dmi.unict.it
A Deep Learning Approach To Universal Image Manipulation Detection Using A New Convolutional Layer
 A Deep Learning Approach To Universal Image Manipulation Detection Using A New Convolutional Layer ABSTRACT Belhassen Bayar Drexel University Dept. of ECE Philadelphia, PA, USA bb632@drexel.edu When creating
A Deep Learning Approach To Universal Image Manipulation Detection Using A New Convolutional Layer ABSTRACT Belhassen Bayar Drexel University Dept. of ECE Philadelphia, PA, USA bb632@drexel.edu When creating
Impact of Automatic Feature Extraction in Deep Learning Architecture
 Impact of Automatic Feature Extraction in Deep Learning Architecture Fatma Shaheen, Brijesh Verma and Md Asafuddoula Centre for Intelligent Systems Central Queensland University, Brisbane, Australia {f.shaheen,
Impact of Automatic Feature Extraction in Deep Learning Architecture Fatma Shaheen, Brijesh Verma and Md Asafuddoula Centre for Intelligent Systems Central Queensland University, Brisbane, Australia {f.shaheen,
arxiv: v2 [cs.cv] 11 Oct 2016
![arxiv: v2 [cs.cv] 11 Oct 2016 arxiv: v2 [cs.cv] 11 Oct 2016](/thumbs/94/119169670.jpg) Xception: Deep Learning with Depthwise Separable Convolutions arxiv:1610.02357v2 [cs.cv] 11 Oct 2016 François Chollet Google, Inc. fchollet@google.com Monday 10 th October, 2016 Abstract We present an
Xception: Deep Learning with Depthwise Separable Convolutions arxiv:1610.02357v2 [cs.cv] 11 Oct 2016 François Chollet Google, Inc. fchollet@google.com Monday 10 th October, 2016 Abstract We present an
Defense Against the Dark Arts: Machine Learning Security and Privacy. Ian Goodfellow, Staff Research Scientist, Google Brain BayLearn 2017
 Defense Against the Dark Arts: Machine Learning Security and Privacy Ian Goodfellow, Staff Research Scientist, Google Brain BayLearn 2017 An overview of a field This presentation summarizes the work of
Defense Against the Dark Arts: Machine Learning Security and Privacy Ian Goodfellow, Staff Research Scientist, Google Brain BayLearn 2017 An overview of a field This presentation summarizes the work of
arxiv: v3 [cs.cv] 18 Dec 2018
![arxiv: v3 [cs.cv] 18 Dec 2018 arxiv: v3 [cs.cv] 18 Dec 2018](/thumbs/96/128789272.jpg) Video Colorization using CNNs and Keyframes extraction: An application in saving bandwidth Ankur Singh 1 Anurag Chanani 2 Harish Karnick 3 arxiv:1812.03858v3 [cs.cv] 18 Dec 2018 Abstract In this paper,
Video Colorization using CNNs and Keyframes extraction: An application in saving bandwidth Ankur Singh 1 Anurag Chanani 2 Harish Karnick 3 arxiv:1812.03858v3 [cs.cv] 18 Dec 2018 Abstract In this paper,
Convolutional Neural Network-based Steganalysis on Spatial Domain
 Convolutional Neural Network-based Steganalysis on Spatial Domain Dong-Hyun Kim, and Hae-Yeoun Lee Abstract Steganalysis has been studied to detect the existence of hidden messages by steganography. However,
Convolutional Neural Network-based Steganalysis on Spatial Domain Dong-Hyun Kim, and Hae-Yeoun Lee Abstract Steganalysis has been studied to detect the existence of hidden messages by steganography. However,
Xception: Deep Learning with Depthwise Separable Convolutions
 Xception: Deep Learning with Depthwise Separable Convolutions François Chollet Google, Inc. fchollet@google.com 1 A variant of the process is to independently look at width-wise correarxiv:1610.02357v3
Xception: Deep Learning with Depthwise Separable Convolutions François Chollet Google, Inc. fchollet@google.com 1 A variant of the process is to independently look at width-wise correarxiv:1610.02357v3
Comparison of Google Image Search and ResNet Image Classification Using Image Similarity Metrics
 University of Arkansas, Fayetteville ScholarWorks@UARK Computer Science and Computer Engineering Undergraduate Honors Theses Computer Science and Computer Engineering 5-2018 Comparison of Google Image
University of Arkansas, Fayetteville ScholarWorks@UARK Computer Science and Computer Engineering Undergraduate Honors Theses Computer Science and Computer Engineering 5-2018 Comparison of Google Image
Convolutional Neural Networks: Real Time Emotion Recognition
 Convolutional Neural Networks: Real Time Emotion Recognition Bruce Nguyen, William Truong, Harsha Yeddanapudy Motivation: Machine emotion recognition has long been a challenge and popular topic in the
Convolutional Neural Networks: Real Time Emotion Recognition Bruce Nguyen, William Truong, Harsha Yeddanapudy Motivation: Machine emotion recognition has long been a challenge and popular topic in the
ROAD RECOGNITION USING FULLY CONVOLUTIONAL NEURAL NETWORKS
 Bulletin of the Transilvania University of Braşov Vol. 10 (59) No. 2-2017 Series I: Engineering Sciences ROAD RECOGNITION USING FULLY CONVOLUTIONAL NEURAL NETWORKS E. HORVÁTH 1 C. POZNA 2 Á. BALLAGI 3
Bulletin of the Transilvania University of Braşov Vol. 10 (59) No. 2-2017 Series I: Engineering Sciences ROAD RECOGNITION USING FULLY CONVOLUTIONAL NEURAL NETWORKS E. HORVÁTH 1 C. POZNA 2 Á. BALLAGI 3
Image Manipulation Detection using Convolutional Neural Network
 Image Manipulation Detection using Convolutional Neural Network Dong-Hyun Kim 1 and Hae-Yeoun Lee 2,* 1 Graduate Student, 2 PhD, Professor 1,2 Department of Computer Software Engineering, Kumoh National
Image Manipulation Detection using Convolutional Neural Network Dong-Hyun Kim 1 and Hae-Yeoun Lee 2,* 1 Graduate Student, 2 PhD, Professor 1,2 Department of Computer Software Engineering, Kumoh National
Derek Allman a, Austin Reiter b, and Muyinatu Bell a,c
 Exploring the effects of transducer models when training convolutional neural networks to eliminate reflection artifacts in experimental photoacoustic images Derek Allman a, Austin Reiter b, and Muyinatu
Exploring the effects of transducer models when training convolutional neural networks to eliminate reflection artifacts in experimental photoacoustic images Derek Allman a, Austin Reiter b, and Muyinatu
An Introduction to Convolutional Neural Networks. Alessandro Giusti Dalle Molle Institute for Artificial Intelligence Lugano, Switzerland
 An Introduction to Convolutional Neural Networks Alessandro Giusti Dalle Molle Institute for Artificial Intelligence Lugano, Switzerland Sources & Resources - Andrej Karpathy, CS231n http://cs231n.github.io/convolutional-networks/
An Introduction to Convolutional Neural Networks Alessandro Giusti Dalle Molle Institute for Artificial Intelligence Lugano, Switzerland Sources & Resources - Andrej Karpathy, CS231n http://cs231n.github.io/convolutional-networks/
TRANSFORMING PHOTOS TO COMICS USING CONVOLUTIONAL NEURAL NETWORKS. Tsinghua University, China Cardiff University, UK
 TRANSFORMING PHOTOS TO COMICS USING CONVOUTIONA NEURA NETWORKS Yang Chen Yu-Kun ai Yong-Jin iu Tsinghua University, China Cardiff University, UK ABSTRACT In this paper, inspired by Gatys s recent work,
TRANSFORMING PHOTOS TO COMICS USING CONVOUTIONA NEURA NETWORKS Yang Chen Yu-Kun ai Yong-Jin iu Tsinghua University, China Cardiff University, UK ABSTRACT In this paper, inspired by Gatys s recent work,
Improved SIFT Matching for Image Pairs with a Scale Difference
 Improved SIFT Matching for Image Pairs with a Scale Difference Y. Bastanlar, A. Temizel and Y. Yardımcı Informatics Institute, Middle East Technical University, Ankara, 06531, Turkey Published in IET Electronics,
Improved SIFT Matching for Image Pairs with a Scale Difference Y. Bastanlar, A. Temizel and Y. Yardımcı Informatics Institute, Middle East Technical University, Ankara, 06531, Turkey Published in IET Electronics,
CS 7643: Deep Learning
 CS 7643: Deep Learning Topics: Toeplitz matrices and convolutions = matrix-mult Dilated/a-trous convolutions Backprop in conv layers Transposed convolutions Dhruv Batra Georgia Tech HW1 extension 09/22
CS 7643: Deep Learning Topics: Toeplitz matrices and convolutions = matrix-mult Dilated/a-trous convolutions Backprop in conv layers Transposed convolutions Dhruv Batra Georgia Tech HW1 extension 09/22
CHAPTER 8: EXTENDED TETRACHORD CLASSIFICATION
 CHAPTER 8: EXTENDED TETRACHORD CLASSIFICATION Chapter 7 introduced the notion of strange circles: using various circles of musical intervals as equivalence classes to which input pitch-classes are assigned.
CHAPTER 8: EXTENDED TETRACHORD CLASSIFICATION Chapter 7 introduced the notion of strange circles: using various circles of musical intervals as equivalence classes to which input pitch-classes are assigned.
Impeding Forgers at Photo Inception
 Impeding Forgers at Photo Inception Matthias Kirchner a, Peter Winkler b and Hany Farid c a International Computer Science Institute Berkeley, Berkeley, CA 97, USA b Department of Mathematics, Dartmouth
Impeding Forgers at Photo Inception Matthias Kirchner a, Peter Winkler b and Hany Farid c a International Computer Science Institute Berkeley, Berkeley, CA 97, USA b Department of Mathematics, Dartmouth
LANDMARK recognition is an important feature for
 1 NU-LiteNet: Mobile Landmark Recognition using Convolutional Neural Networks Chakkrit Termritthikun, Surachet Kanprachar, Paisarn Muneesawang arxiv:1810.01074v1 [cs.cv] 2 Oct 2018 Abstract The growth
1 NU-LiteNet: Mobile Landmark Recognition using Convolutional Neural Networks Chakkrit Termritthikun, Surachet Kanprachar, Paisarn Muneesawang arxiv:1810.01074v1 [cs.cv] 2 Oct 2018 Abstract The growth
Learning to Predict Indoor Illumination from a Single Image. Chih-Hui Ho
 Learning to Predict Indoor Illumination from a Single Image Chih-Hui Ho 1 Outline Introduction Method Overview LDR Panorama Light Source Detection Panorama Recentering Warp Learning From LDR Panoramas
Learning to Predict Indoor Illumination from a Single Image Chih-Hui Ho 1 Outline Introduction Method Overview LDR Panorama Light Source Detection Panorama Recentering Warp Learning From LDR Panoramas
Coursework 2. MLP Lecture 7 Convolutional Networks 1
 Coursework 2 MLP Lecture 7 Convolutional Networks 1 Coursework 2 - Overview and Objectives Overview: Use a selection of the techniques covered in the course so far to train accurate multi-layer networks
Coursework 2 MLP Lecture 7 Convolutional Networks 1 Coursework 2 - Overview and Objectives Overview: Use a selection of the techniques covered in the course so far to train accurate multi-layer networks
tsushi Sasaki Fig. Flow diagram of panel structure recognition by specifying peripheral regions of each component in rectangles, and 3 types of detect
 RECOGNITION OF NEL STRUCTURE IN COMIC IMGES USING FSTER R-CNN Hideaki Yanagisawa Hiroshi Watanabe Graduate School of Fundamental Science and Engineering, Waseda University BSTRCT For efficient e-comics
RECOGNITION OF NEL STRUCTURE IN COMIC IMGES USING FSTER R-CNN Hideaki Yanagisawa Hiroshi Watanabe Graduate School of Fundamental Science and Engineering, Waseda University BSTRCT For efficient e-comics
Analyzing features learned for Offline Signature Verification using Deep CNNs
 Accepted as a conference paper for ICPR 2016 Analyzing features learned for Offline Signature Verification using Deep CNNs Luiz G. Hafemann, Robert Sabourin Lab. d imagerie, de vision et d intelligence
Accepted as a conference paper for ICPR 2016 Analyzing features learned for Offline Signature Verification using Deep CNNs Luiz G. Hafemann, Robert Sabourin Lab. d imagerie, de vision et d intelligence
Convolutional Neural Network-Based Infrared Image Super Resolution Under Low Light Environment
 Convolutional Neural Network-Based Infrared Super Resolution Under Low Light Environment Tae Young Han, Yong Jun Kim, Byung Cheol Song Department of Electronic Engineering Inha University Incheon, Republic
Convolutional Neural Network-Based Infrared Super Resolution Under Low Light Environment Tae Young Han, Yong Jun Kim, Byung Cheol Song Department of Electronic Engineering Inha University Incheon, Republic
Multimedia Forensics
 Multimedia Forensics Using Mathematics and Machine Learning to Determine an Image's Source and Authenticity Matthew C. Stamm Multimedia & Information Security Lab (MISL) Department of Electrical and Computer
Multimedia Forensics Using Mathematics and Machine Learning to Determine an Image's Source and Authenticity Matthew C. Stamm Multimedia & Information Security Lab (MISL) Department of Electrical and Computer
Multi-task Learning of Dish Detection and Calorie Estimation
 Multi-task Learning of Dish Detection and Calorie Estimation Department of Informatics, The University of Electro-Communications, Tokyo 1-5-1 Chofugaoka, Chofu-shi, Tokyo 182-8585 JAPAN ABSTRACT In recent
Multi-task Learning of Dish Detection and Calorie Estimation Department of Informatics, The University of Electro-Communications, Tokyo 1-5-1 Chofugaoka, Chofu-shi, Tokyo 182-8585 JAPAN ABSTRACT In recent
Auto-tagging The Facebook
 Auto-tagging The Facebook Jonathan Michelson and Jorge Ortiz Stanford University 2006 E-mail: JonMich@Stanford.edu, jorge.ortiz@stanford.com Introduction For those not familiar, The Facebook is an extremely
Auto-tagging The Facebook Jonathan Michelson and Jorge Ortiz Stanford University 2006 E-mail: JonMich@Stanford.edu, jorge.ortiz@stanford.com Introduction For those not familiar, The Facebook is an extremely
Analysis of adversarial attacks against CNN-based image forgery detectors
 Analysis of adversarial attacks against CNN-based image forgery detectors Diego Gragnaniello, Francesco Marra, Giovanni Poggi, Luisa Verdoliva Department of Electrical Engineering and Information Technology
Analysis of adversarial attacks against CNN-based image forgery detectors Diego Gragnaniello, Francesco Marra, Giovanni Poggi, Luisa Verdoliva Department of Electrical Engineering and Information Technology
Classification Accuracies of Malaria Infected Cells Using Deep Convolutional Neural Networks Based on Decompressed Images
 Classification Accuracies of Malaria Infected Cells Using Deep Convolutional Neural Networks Based on Decompressed Images Yuhang Dong, Zhuocheng Jiang, Hongda Shen, W. David Pan Dept. of Electrical & Computer
Classification Accuracies of Malaria Infected Cells Using Deep Convolutional Neural Networks Based on Decompressed Images Yuhang Dong, Zhuocheng Jiang, Hongda Shen, W. David Pan Dept. of Electrical & Computer
Image Extraction using Image Mining Technique
 IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
Visualizing and Understanding. Fei-Fei Li & Justin Johnson & Serena Yeung. Lecture 12 -
 Lecture 12: Visualizing and Understanding Lecture 12-1 May 16, 2017 Administrative Milestones due tonight on Canvas, 11:59pm Midterm grades released on Gradescope this week A3 due next Friday, 5/26 HyperQuest
Lecture 12: Visualizing and Understanding Lecture 12-1 May 16, 2017 Administrative Milestones due tonight on Canvas, 11:59pm Midterm grades released on Gradescope this week A3 due next Friday, 5/26 HyperQuest
Deep Neural Network Architectures for Modulation Classification
 Deep Neural Network Architectures for Modulation Classification Xiaoyu Liu, Diyu Yang, and Aly El Gamal School of Electrical and Computer Engineering Purdue University Email: {liu1962, yang1467, elgamala}@purdue.edu
Deep Neural Network Architectures for Modulation Classification Xiaoyu Liu, Diyu Yang, and Aly El Gamal School of Electrical and Computer Engineering Purdue University Email: {liu1962, yang1467, elgamala}@purdue.edu
DeCAF: A Deep Convolutional Activation Feature for Generic Visual Recognition. ECE 289G: Paper Presentation #3 Philipp Gysel
 DeCAF: A Deep Convolutional Activation Feature for Generic Visual Recognition ECE 289G: Paper Presentation #3 Philipp Gysel Autonomous Car ECE 289G Paper Presentation, Philipp Gysel Slide 2 Source: maps.google.com
DeCAF: A Deep Convolutional Activation Feature for Generic Visual Recognition ECE 289G: Paper Presentation #3 Philipp Gysel Autonomous Car ECE 289G Paper Presentation, Philipp Gysel Slide 2 Source: maps.google.com
Proposed Method for Off-line Signature Recognition and Verification using Neural Network
 e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Proposed Method for Off-line Signature
e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Proposed Method for Off-line Signature
Distance Estimation and Localization of Sound Sources in Reverberant Conditions using Deep Neural Networks
 Distance Estimation and Localization of Sound Sources in Reverberant Conditions using Deep Neural Networks Mariam Yiwere 1 and Eun Joo Rhee 2 1 Department of Computer Engineering, Hanbat National University,
Distance Estimation and Localization of Sound Sources in Reverberant Conditions using Deep Neural Networks Mariam Yiwere 1 and Eun Joo Rhee 2 1 Department of Computer Engineering, Hanbat National University,
Learning Deep Networks from Noisy Labels with Dropout Regularization
 Learning Deep Networks from Noisy Labels with Dropout Regularization Ishan Jindal, Matthew Nokleby Electrical and Computer Engineering Wayne State University, MI, USA Email: {ishan.jindal, matthew.nokleby}@wayne.edu
Learning Deep Networks from Noisy Labels with Dropout Regularization Ishan Jindal, Matthew Nokleby Electrical and Computer Engineering Wayne State University, MI, USA Email: {ishan.jindal, matthew.nokleby}@wayne.edu
Pelee: A Real-Time Object Detection System on Mobile Devices
 Pelee: A Real-Time Object Detection System on Mobile Devices Robert J. Wang, Xiang Li, Shuang Ao & Charles X. Ling Department of Computer Science University of Western Ontario London, Ontario, Canada,
Pelee: A Real-Time Object Detection System on Mobile Devices Robert J. Wang, Xiang Li, Shuang Ao & Charles X. Ling Department of Computer Science University of Western Ontario London, Ontario, Canada,
AUGMENTED CONVOLUTIONAL FEATURE MAPS FOR ROBUST CNN-BASED CAMERA MODEL IDENTIFICATION. Belhassen Bayar and Matthew C. Stamm
 AUGMENTED CONVOLUTIONAL FEATURE MAPS FOR ROBUST CNN-BASED CAMERA MODEL IDENTIFICATION Belhassen Bayar and Matthew C. Stamm Department of Electrical and Computer Engineering, Drexel University, Philadelphia,
AUGMENTED CONVOLUTIONAL FEATURE MAPS FOR ROBUST CNN-BASED CAMERA MODEL IDENTIFICATION Belhassen Bayar and Matthew C. Stamm Department of Electrical and Computer Engineering, Drexel University, Philadelphia,
Lane Detection in Automotive
 Lane Detection in Automotive Contents Introduction... 2 Image Processing... 2 Reading an image... 3 RGB to Gray... 3 Mean and Gaussian filtering... 5 Defining our Region of Interest... 6 BirdsEyeView Transformation...
Lane Detection in Automotive Contents Introduction... 2 Image Processing... 2 Reading an image... 3 RGB to Gray... 3 Mean and Gaussian filtering... 5 Defining our Region of Interest... 6 BirdsEyeView Transformation...
A TWO-PART PREDICTIVE CODER FOR MULTITASK SIGNAL COMPRESSION. Scott Deeann Chen and Pierre Moulin
 A TWO-PART PREDICTIVE CODER FOR MULTITASK SIGNAL COMPRESSION Scott Deeann Chen and Pierre Moulin University of Illinois at Urbana-Champaign Department of Electrical and Computer Engineering 5 North Mathews
A TWO-PART PREDICTIVE CODER FOR MULTITASK SIGNAL COMPRESSION Scott Deeann Chen and Pierre Moulin University of Illinois at Urbana-Champaign Department of Electrical and Computer Engineering 5 North Mathews
Free-hand Sketch Recognition Classification
 Free-hand Sketch Recognition Classification Wayne Lu Stanford University waynelu@stanford.edu Elizabeth Tran Stanford University eliztran@stanford.edu Abstract People use sketches to express and record
Free-hand Sketch Recognition Classification Wayne Lu Stanford University waynelu@stanford.edu Elizabeth Tran Stanford University eliztran@stanford.edu Abstract People use sketches to express and record
FOOLING SMART MACHINES: SECURITY CHALLENGES FOR MACHINE LEARNING
 FOOLING SMART MACHINES: SECURITY CHALLENGES FOR MACHINE LEARNING JOPPE W. BOS OCTOBER 2018 INTERNET & MOBILE WORLD 2018 Bucharest PUBLIC Developing Solutions Close to Where Our Customers and Partners Operate
FOOLING SMART MACHINES: SECURITY CHALLENGES FOR MACHINE LEARNING JOPPE W. BOS OCTOBER 2018 INTERNET & MOBILE WORLD 2018 Bucharest PUBLIC Developing Solutions Close to Where Our Customers and Partners Operate
Author(s) Corr, Philip J.; Silvestre, Guenole C.; Bleakley, Christopher J. The Irish Pattern Recognition & Classification Society
 Provided by the author(s) and University College Dublin Library in accordance with publisher policies. Please cite the published version when available. Title Open Source Dataset and Deep Learning Models
Provided by the author(s) and University College Dublin Library in accordance with publisher policies. Please cite the published version when available. Title Open Source Dataset and Deep Learning Models
Multimodal Face Recognition using Hybrid Correlation Filters
 Multimodal Face Recognition using Hybrid Correlation Filters Anamika Dubey, Abhishek Sharma Electrical Engineering Department, Indian Institute of Technology Roorkee, India {ana.iitr, abhisharayiya}@gmail.com
Multimodal Face Recognition using Hybrid Correlation Filters Anamika Dubey, Abhishek Sharma Electrical Engineering Department, Indian Institute of Technology Roorkee, India {ana.iitr, abhisharayiya}@gmail.com
Semantic Segmentation in Red Relief Image Map by UX-Net
 Semantic Segmentation in Red Relief Image Map by UX-Net Tomoya Komiyama 1, Kazuhiro Hotta 1, Kazuo Oda 2, Satomi Kakuta 2 and Mikako Sano 2 1 Meijo University, Shiogamaguchi, 468-0073, Nagoya, Japan 2
Semantic Segmentation in Red Relief Image Map by UX-Net Tomoya Komiyama 1, Kazuhiro Hotta 1, Kazuo Oda 2, Satomi Kakuta 2 and Mikako Sano 2 1 Meijo University, Shiogamaguchi, 468-0073, Nagoya, Japan 2
Study Impact of Architectural Style and Partial View on Landmark Recognition
 Study Impact of Architectural Style and Partial View on Landmark Recognition Ying Chen smileyc@stanford.edu 1. Introduction Landmark recognition in image processing is one of the important object recognition
Study Impact of Architectural Style and Partial View on Landmark Recognition Ying Chen smileyc@stanford.edu 1. Introduction Landmark recognition in image processing is one of the important object recognition
Classification of Road Images for Lane Detection
 Classification of Road Images for Lane Detection Mingyu Kim minkyu89@stanford.edu Insun Jang insunj@stanford.edu Eunmo Yang eyang89@stanford.edu 1. Introduction In the research on autonomous car, it is
Classification of Road Images for Lane Detection Mingyu Kim minkyu89@stanford.edu Insun Jang insunj@stanford.edu Eunmo Yang eyang89@stanford.edu 1. Introduction In the research on autonomous car, it is
AUTOMATED MALARIA PARASITE DETECTION BASED ON IMAGE PROCESSING PROJECT REFERENCE NO.: 38S1511
 AUTOMATED MALARIA PARASITE DETECTION BASED ON IMAGE PROCESSING PROJECT REFERENCE NO.: 38S1511 COLLEGE : BANGALORE INSTITUTE OF TECHNOLOGY, BENGALURU BRANCH : COMPUTER SCIENCE AND ENGINEERING GUIDE : DR.
AUTOMATED MALARIA PARASITE DETECTION BASED ON IMAGE PROCESSING PROJECT REFERENCE NO.: 38S1511 COLLEGE : BANGALORE INSTITUTE OF TECHNOLOGY, BENGALURU BRANCH : COMPUTER SCIENCE AND ENGINEERING GUIDE : DR.
Enhancing Symmetry in GAN Generated Fashion Images
 Enhancing Symmetry in GAN Generated Fashion Images Vishnu Makkapati 1 and Arun Patro 2 1 Myntra Designs Pvt. Ltd., Bengaluru - 560068, India vishnu.makkapati@myntra.com 2 Department of Electrical Engineering,
Enhancing Symmetry in GAN Generated Fashion Images Vishnu Makkapati 1 and Arun Patro 2 1 Myntra Designs Pvt. Ltd., Bengaluru - 560068, India vishnu.makkapati@myntra.com 2 Department of Electrical Engineering,
Colour Profiling Using Multiple Colour Spaces
 Colour Profiling Using Multiple Colour Spaces Nicola Duffy and Gerard Lacey Computer Vision and Robotics Group, Trinity College, Dublin.Ireland duffynn@cs.tcd.ie Abstract This paper presents an original
Colour Profiling Using Multiple Colour Spaces Nicola Duffy and Gerard Lacey Computer Vision and Robotics Group, Trinity College, Dublin.Ireland duffynn@cs.tcd.ie Abstract This paper presents an original
Student Attendance Monitoring System Via Face Detection and Recognition System
 IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 11 May 2016 ISSN (online): 2349-784X Student Attendance Monitoring System Via Face Detection and Recognition System Pinal
IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 11 May 2016 ISSN (online): 2349-784X Student Attendance Monitoring System Via Face Detection and Recognition System Pinal
Frame-Based Classification of Operation Phases in Cataract Surgery Videos
 Frame-Based Classification of Operation Phases in Cataract Surgery Videos Manfred Jüergen Primus 1, Doris Putzgruber-Adamitsch 2 Mario Taschwer 1, Bernd Münzer 1, Yosuf El-Shabrawi 2, Laszlo Böszörmenyi
Frame-Based Classification of Operation Phases in Cataract Surgery Videos Manfred Jüergen Primus 1, Doris Putzgruber-Adamitsch 2 Mario Taschwer 1, Bernd Münzer 1, Yosuf El-Shabrawi 2, Laszlo Böszörmenyi
CS534 Introduction to Computer Vision. Linear Filters. Ahmed Elgammal Dept. of Computer Science Rutgers University
 CS534 Introduction to Computer Vision Linear Filters Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What are Filters Linear Filters Convolution operation Properties of Linear Filters
CS534 Introduction to Computer Vision Linear Filters Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What are Filters Linear Filters Convolution operation Properties of Linear Filters
Chess Recognition Using Computer Vision
 Chess Recognition Using Computer Vision May 30, 2017 Ramani Varun (U6004067, contribution 50%) Sukrit Gupta (U5900600, contribution 50%) College of Engineering & Computer Science he Australian National
Chess Recognition Using Computer Vision May 30, 2017 Ramani Varun (U6004067, contribution 50%) Sukrit Gupta (U5900600, contribution 50%) College of Engineering & Computer Science he Australian National
Comparing Computer-predicted Fixations to Human Gaze
 Comparing Computer-predicted Fixations to Human Gaze Yanxiang Wu School of Computing Clemson University yanxiaw@clemson.edu Andrew T Duchowski School of Computing Clemson University andrewd@cs.clemson.edu
Comparing Computer-predicted Fixations to Human Gaze Yanxiang Wu School of Computing Clemson University yanxiaw@clemson.edu Andrew T Duchowski School of Computing Clemson University andrewd@cs.clemson.edu
Wadehra Kartik, Kathpalia Mukul, Bahl Vasudha, International Journal of Advance Research, Ideas and Innovations in Technology
 ISSN: 2454-132X Impact factor: 4.295 (Volume 4, Issue 1) Available online at www.ijariit.com Hand Detection and Gesture Recognition in Real-Time Using Haar-Classification and Convolutional Neural Networks
ISSN: 2454-132X Impact factor: 4.295 (Volume 4, Issue 1) Available online at www.ijariit.com Hand Detection and Gesture Recognition in Real-Time Using Haar-Classification and Convolutional Neural Networks
Multispectral Pedestrian Detection using Deep Fusion Convolutional Neural Networks
 Multispectral Pedestrian Detection using Deep Fusion Convolutional Neural Networks Jo rg Wagner1,2, Volker Fischer1, Michael Herman1 and Sven Behnke2 1- Robert Bosch GmbH - 70442 Stuttgart - Germany 2-
Multispectral Pedestrian Detection using Deep Fusion Convolutional Neural Networks Jo rg Wagner1,2, Volker Fischer1, Michael Herman1 and Sven Behnke2 1- Robert Bosch GmbH - 70442 Stuttgart - Germany 2-
Laboratory 1: Uncertainty Analysis
 University of Alabama Department of Physics and Astronomy PH101 / LeClair May 26, 2014 Laboratory 1: Uncertainty Analysis Hypothesis: A statistical analysis including both mean and standard deviation can
University of Alabama Department of Physics and Astronomy PH101 / LeClair May 26, 2014 Laboratory 1: Uncertainty Analysis Hypothesis: A statistical analysis including both mean and standard deviation can
Consistent Comic Colorization with Pixel-wise Background Classification
 Consistent Comic Colorization with Pixel-wise Background Classification Sungmin Kang KAIST Jaegul Choo Korea University Jaehyuk Chang NAVER WEBTOON Corp. Abstract Comic colorization is a time-consuming
Consistent Comic Colorization with Pixel-wise Background Classification Sungmin Kang KAIST Jaegul Choo Korea University Jaehyuk Chang NAVER WEBTOON Corp. Abstract Comic colorization is a time-consuming
arxiv: v2 [cs.sd] 22 May 2017
![arxiv: v2 [cs.sd] 22 May 2017 arxiv: v2 [cs.sd] 22 May 2017](/thumbs/72/66381162.jpg) SAMPLE-LEVEL DEEP CONVOLUTIONAL NEURAL NETWORKS FOR MUSIC AUTO-TAGGING USING RAW WAVEFORMS Jongpil Lee Jiyoung Park Keunhyoung Luke Kim Juhan Nam Korea Advanced Institute of Science and Technology (KAIST)
SAMPLE-LEVEL DEEP CONVOLUTIONAL NEURAL NETWORKS FOR MUSIC AUTO-TAGGING USING RAW WAVEFORMS Jongpil Lee Jiyoung Park Keunhyoung Luke Kim Juhan Nam Korea Advanced Institute of Science and Technology (KAIST)
A Hybrid Deep Learning Architecture for Privacy-Preserving Mobile Analytics
 A Hybrid Deep Learning Architecture for Privacy-Preserving Mobile Analytics Ossia, SA; Shamsabadi, AS; Taheri, A; Rabiee, HR; Lane, N; Haddadi, H The Author(s) 2017 For additional information about this
A Hybrid Deep Learning Architecture for Privacy-Preserving Mobile Analytics Ossia, SA; Shamsabadi, AS; Taheri, A; Rabiee, HR; Lane, N; Haddadi, H The Author(s) 2017 For additional information about this
arxiv: v1 [cs.cv] 27 Nov 2016
![arxiv: v1 [cs.cv] 27 Nov 2016 arxiv: v1 [cs.cv] 27 Nov 2016](/thumbs/72/66770659.jpg) Real-Time Video Highlights for Yahoo Esports arxiv:1611.08780v1 [cs.cv] 27 Nov 2016 Yale Song Yahoo Research New York, USA yalesong@yahoo-inc.com Abstract Esports has gained global popularity in recent
Real-Time Video Highlights for Yahoo Esports arxiv:1611.08780v1 [cs.cv] 27 Nov 2016 Yale Song Yahoo Research New York, USA yalesong@yahoo-inc.com Abstract Esports has gained global popularity in recent
A Spatial Mean and Median Filter For Noise Removal in Digital Images
 A Spatial Mean and Median Filter For Noise Removal in Digital Images N.Rajesh Kumar 1, J.Uday Kumar 2 Associate Professor, Dept. of ECE, Jaya Prakash Narayan College of Engineering, Mahabubnagar, Telangana,
A Spatial Mean and Median Filter For Noise Removal in Digital Images N.Rajesh Kumar 1, J.Uday Kumar 2 Associate Professor, Dept. of ECE, Jaya Prakash Narayan College of Engineering, Mahabubnagar, Telangana,
The Basic Kak Neural Network with Complex Inputs
 The Basic Kak Neural Network with Complex Inputs Pritam Rajagopal The Kak family of neural networks [3-6,2] is able to learn patterns quickly, and this speed of learning can be a decisive advantage over
The Basic Kak Neural Network with Complex Inputs Pritam Rajagopal The Kak family of neural networks [3-6,2] is able to learn patterns quickly, and this speed of learning can be a decisive advantage over
Liangliang Cao *, Jiebo Luo +, Thomas S. Huang *
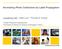 Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
A Neural Algorithm of Artistic Style (2015)
 A Neural Algorithm of Artistic Style (2015) Leon A. Gatys, Alexander S. Ecker, Matthias Bethge Nancy Iskander (niskander@dgp.toronto.edu) Overview of Method Content: Global structure. Style: Colours; local
A Neural Algorithm of Artistic Style (2015) Leon A. Gatys, Alexander S. Ecker, Matthias Bethge Nancy Iskander (niskander@dgp.toronto.edu) Overview of Method Content: Global structure. Style: Colours; local
Objective Evaluation of Edge Blur and Ringing Artefacts: Application to JPEG and JPEG 2000 Image Codecs
 Objective Evaluation of Edge Blur and Artefacts: Application to JPEG and JPEG 2 Image Codecs G. A. D. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences and Technology, Massey
Objective Evaluation of Edge Blur and Artefacts: Application to JPEG and JPEG 2 Image Codecs G. A. D. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences and Technology, Massey
Visible-light and Infrared Face Recognition
 Visible-light and Infrared Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 {xchen2, flynn, kwb}@nd.edu
Visible-light and Infrared Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 {xchen2, flynn, kwb}@nd.edu
A Numerical Approach to Understanding Oscillator Neural Networks
 A Numerical Approach to Understanding Oscillator Neural Networks Natalie Klein Mentored by Jon Wilkins Networks of coupled oscillators are a form of dynamical network originally inspired by various biological
A Numerical Approach to Understanding Oscillator Neural Networks Natalie Klein Mentored by Jon Wilkins Networks of coupled oscillators are a form of dynamical network originally inspired by various biological
Human or Robot? Robert Recatto A University of California, San Diego 9500 Gilman Dr. La Jolla CA,
 Human or Robot? INTRODUCTION: With advancements in technology happening every day and Artificial Intelligence becoming more integrated into everyday society the line between human intelligence and computer
Human or Robot? INTRODUCTION: With advancements in technology happening every day and Artificial Intelligence becoming more integrated into everyday society the line between human intelligence and computer
Retrieval of Large Scale Images and Camera Identification via Random Projections
 Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
Semantic Segmentation on Resource Constrained Devices
 Semantic Segmentation on Resource Constrained Devices Sachin Mehta University of Washington, Seattle In collaboration with Mohammad Rastegari, Anat Caspi, Linda Shapiro, and Hannaneh Hajishirzi Project
Semantic Segmentation on Resource Constrained Devices Sachin Mehta University of Washington, Seattle In collaboration with Mohammad Rastegari, Anat Caspi, Linda Shapiro, and Hannaneh Hajishirzi Project
EE-559 Deep learning 7.2. Networks for image classification
 EE-559 Deep learning 7.2. Networks for image classification François Fleuret https://fleuret.org/ee559/ Fri Nov 16 22:58:34 UTC 2018 ÉCOLE POLYTECHNIQUE FÉDÉRALE DE LAUSANNE Image classification, standard
EE-559 Deep learning 7.2. Networks for image classification François Fleuret https://fleuret.org/ee559/ Fri Nov 16 22:58:34 UTC 2018 ÉCOLE POLYTECHNIQUE FÉDÉRALE DE LAUSANNE Image classification, standard
