Face Presentation Attack Detection by Exploring Spectral Signatures
|
|
|
- Elizabeth Hill
- 6 years ago
- Views:
Transcription
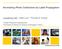
1 Face Presentation Attack Detection by Exploring Spectral Signatures R. Raghavendra, Kiran B. Raja, Sushma Venkatesh, Christoph Busch Norwegian Biometrics Laboratory, NTNU - Gjøvik, Norway {raghavendra.ramachandra; kiran.raja; sushma.venkatesh; Abstract Presentation attack on the face recognition systems is well studied in the biometrics community resulting in various techniques for detecting the attacks. A low-cost presentation attack (e.g. print attacks) on face recognition systems has been demonstrated for systems operating in visible, multispectral (visible and near infrared spectrum) and extended multispectral (more than two spectral bands spanning from visible to near infrared space, commonly in 5nm-nm). In this paper, we propose a novel method to detect the presentation attacks on the extended multispectral face recognition systems. The proposed method is based on characterising the reflectance properties of the captured image through the spectral signature. The spectral signature is further classified using the linear Support Vector Machine (SVM) to obtain the decision on presented sample as an artefact or bona-fide. Since the reflectance property of the human skin and the artefact material differ, the proposed method can efficiently detect the presentation attacks on the extended multispectral system. Extensive experiments are carried out on a publicly available extended multispectral face database (EMSPAD) comprised of 5 subjects with two different Presentation Attack Instruments (PAI) generated using two different printers. The comparison analysis is presented by comparing the performance of the proposed scheme with the contemporary schemes based on the image fusion and score level fusion for PAD. Based on the obtained results, the proposed method has indicated the best performance in detecting both known and unknown attacks.. INTRODUCTION Face recognition systems are widely used in many access control applications by considering the lower costs and nonintrusive imaging ability. However, the widespread deployment of the face recognition solutions have also resulted in newer ways of presentation attacks leveraging the vulnerability of sensors at capture level. The widespread availability of facial images of the targeted attacker can be used 425nm 475nm 525nm 57nm 625nm 68nm 93nm (a) (b) Figure : Example of extended multi-spectral face images from EMSPAD database (a) bona-fide (or real) samples (b) artefact samples generated using laser printer and recaptured using extended multispectral face images by any attacker to create a Presentation Attack Instrument (PAI) (or artefact) which can in-turn be used to gain access to the face recognition system posing as the legitimate user. The vulnerability of the face recognition system is well studied in the literature on different kinds of baseline face recognition systems as well as the commercial-of-theshelf (COTS) that have indicated the vulnerability towards low-cost PAI species such as printed artefact, electronic display artefact and 3D masks [4]. Extensive studies on face Presentation Attack Detection (PAD) (or anti-spoofing or countermeasures) have resulted in various software-based techniques [4]. These developed techniques have demonstrated a reliable accuracy in detecting the presentation attacks from known artefact species, especially in the visible spectrum. However, the generalising capability of the existing PAD techniques in identifying different kinds of artefact species is still a challenge. A possible approach based on the multispectral face capture is perceived as promising alternative by the biometric community. The conventional multi-spectral face capture device will capture the face images in two different spectral bands that include visible (VIS) and near infrared (NIR) spectrum. Since the artefact species are generated from the materials with non-skin texture (e.g. plastics, electronic screen, glossy papers, silicon, rubber, latex, etc.), the use of NIR spectrum can indicate the presence of such materials as the reflective properties differ from real skin texture. Along the lines of motivation, the applicability of mul- 7
2 tispectral face sensors for presentation attack detection has received an increasing interest in the biometric community. Early work [9] in this direction has explored the VIS and NIR spectrum to capture the face images and process them based on the color and texture features to detect the print attacks on the multispectral face recognition systems. The utility of the Short-Wave Infra-Red (SWIR) spectrum for face PAD was introduced in [8] that revealed the presence of the 3D face masks due to the reflective characteristics that are different to that of normal skin. It is interesting to note that, the 3D masks used in [8] can cover most part of the face region but parts of forehead that can be used to estimate the difference between skin and non-skin region. This may limit the applicability of the technique presented in [8] when full face mask is used without displaying any skin region. Further, the first publicly available multispectral face artefact database was presented in []. Experimental analysis indicated the vulnerability of the multispectral face sensor towards low-cost PAI such as the print attacks. The face PAD technique tailored to multispectral face images captured based on the L a MT i F descriptors was proposed in [6] that has indicated an improved performance in detecting the attacks on the publicly available multispectral face PAD database. The L a MT i F descriptors are used separately on VIS and NIR and decision is fused using the logical AND rule to identify the presentation attacks on multispectral face recognition sensor. Most recently, the vulnerability of the extended multispectral face sensor on print attacks was presented in [7]. Extensive experiments were further carried on extended multispectral face sensor where data was captured from seven individual spectral bands (such as 425nm, 475nm, 525nm, 57nm, 625nm, 68nm, and 93nn). Figure illustrates the example of extended multispectral face images corresponding to both bona-fide (or real or normal) and artefact images from the EMSPAD database [7]. Thus, based on the available state-of-the-art techniques it can be deduced that existing algorithms have focused on exploring either colour (from VIS) or texture (from VIS and NIR) features which are limited by generalisability towards unknown attacks. To the best of our knowledge, there exists no work that explores the intrinsic characteristics of the multispectral face sensor to detect the presentation attack. Thus, in this work, we propose a framework for the multispectral face presentation attack detection by exploring the intrinsic characteristics of the sensor by analysing the spectral signature from different spectral bands. To this extent, we explore the Extended Multispectral Presentation Attack Face Database (EMSPAD) [7] to demonstrate the significance of the proposed approach. The main contributions of this work are listed as: Presents a novel approach of detecting the presentation attacks reliably by exploring the spectral signature of the captured face images from extended multispectral bands. Extensive experiments are carried out on the EMSPAD database by comparing the proposed method with the conventional texture based approaches using Binarised Statistical Image Features (BSIF) extracted individually on each band and combining the decision at score level. Further, we also present the comparison of the proposed scheme with image fusion method in which wavelet-based image fusion is explored to combine the multispectral images to form the single composite image to detect the presentation attack. Extensive experiments are presented to investigate the robustness of the proposed PAD scheme for the unknown attacks. To this extent, we have devised additional experiments to train the PAD methods known type of PAI (or artefact) and test them against unknown type of PAI (or artefact). The rest of the paper is organised as follows: Section 2 describes the proposed scheme for face PAD, Section 3 presents the experimental results on the Extended Multispectral Presentation Attack Face Database (EMSPAD) and Section 4 draws the conclusion. 2. Proposed face PAD framework based on the spectral signatures Figure 2 shows the block diagram of the proposed multispectral face PAD framework by exploring the spectral signature. The proposed framework has three main functional units, namely: () Extended multispectral image capture and pre-processing unit (2) Spectral signature extraction unit (3) Classification unit to separate spectral signatures using Support Vector Machine (SVM). In the following section, we discuss each of these functional components in detail. 2.. Extended multispectral image capture and preprocessing unit The extended multispectral images employed in this work are collected using the commercial Multispectral Camera - SpectraCam TM [7]. The face image is captured in seven different spectral bands corresponding to wavelength of 425nm, 475nm, 525nm, 57nm, 625nm, 68nm, and 93nn. As these images are captured sequentially in Extended Multispectral face images Extract Spectral Signature Classifier: SVM Accept Reject Figure 2: Block diagram of the proposed face PAD approach 7
3 Artefact Bona fide (a) (b) (c) Figure 3: Illustration of the proposed face PAD approach (a) multispectral face image capture (b) illustration of the spectral signature on 4 different pixels (c) Average spectral signature obtained on multispectral images from (a) an automatic fashion, there is no need for image registration between the spectral images captured using this sensor. Thus, for each capture, we get seven multi-spectral images that we process sequentially to extract the face region and to perform the normalisation. The face region is extracted using the Haar-based cascade detector, and normalisation is carried out to correct the minor translation and rotation effects. Thus, the detected and normalised face region is re-sized to have 2 2 pixels. Figure 3 (a) shows the example of the processed multispectral face images that will be treated further in next step to compute the spectral signature. Let the face detected and normalized multispectral image bei s = {I s,i s2,...,i s7 } Spectral signature extraction unit In this work, we have utilised the spectral signature of the captured and processed extended multi-spectral image I s. It has to be noted that PAI (or artefacts) species are generated using different kinds of materials that have different spectral variability when compared to that of bona-fide face. Figure 3 illustrates the example of the spectral signatures extracted on both bona fide and artefact face samples captured using the extended multispectral sensor. Given thei th interest point (x i,y i ), the spectral signature corresponding to the multispectral image I s can be extracted as follows: S I =[I s (x i,y i ) I s2 (x i,y i )... I s7 (x i,y i )] () Figure 3 (b) shows the spectral signatures that are extracted from four different interest points (pixels) from the face region corresponding to bona-fide and artefact presentation. For illustration, we have considered the interest points from the fore-head, left cheek, right cheek and lip (refer Figure 3 (a)). It is interesting to note the difference in the spectral signature for both bona-fide and artefact presentation as illustrated in the Figure 3 (b). In this work, we estimate the spectral signature vector R I by averaging over all N pixels of the extended multispectral image I s as follows: R λk = N N X I s (x,y,λ k ) (2) Where, N is the number of rows and columns in the image, in our case it is 2 2, where k = {,2,...,7} indicates the number of spectral bands. Figure 3 (c) shows the average spectral signature R I computed on both bona fide and artefact presentation. As observed from the Figure 3 (c) there is clear distinction in profile of the spectral signature of bona-fide and artefact presentation that further justifies the applicability of the proposed method. Since, we have seven different spectral band (K =7), the dimension of ther λk = Classification: Support Vector Machines (SVM) In this work, we employed the linear Support Vector Machines (SVM) classifier to the make the final decision. The SVM classifier is trained using the spectral signatures R λk from both bona fide and artefact species from the training set of EMSPAD dataset. Given the spectral signature cor- x,y 72
4 (a) (b) (c) Figure 4: Example of the bona-fide and artefacts multispectral images from Extended Multispectral Presentation Attack Face Database (EMSPAD) (a) Bona fide capture (b) Laser print artefact capture (c) Inkjet print artefact capture responding to multispectral probe face image from testing set (or probe set), the decision is made by computing the comparison score magnitude to the pre-determined threshold. The experimental protocols and the threshold selection will be discussed in the following Section Experiments and Results Extensive experiments are carried out on the Extended Multispectral Presentation Attack Face Database (EMSPAD) [7]. EMSPAD database is comprised of 5 subjects captured in two different sessions in the laboratory environment using the commercial multispectral camera -SpectraCam TM [7]. For each subject, five images per session are obtained in seven different spectral bands with a wavelength of 425nm, 475nm, 525nm, 57nm, 625nm, 68nm, and 93nn. Thus, the bona fide database has 5 subjects 7 spectral bands 2 sessions 5 samples = 35 image samples. EMSPAD database has two kinds of artefacts that are generated using two different printers (a) InkJet printer (HP Photosmart 552) (b) LaserJet printer (RICOH ATICIO MP C452) using a high-quality paper. The artefacts are generated by capturing the high-quality photo using Canon EOS 55D DSLR camera in two sessions. There are ten high-quality photos captured that correspond to five images captured in each session. These captured high-quality photos are used to generate the artefacts by printing them using a laser and inkjet printer. Finally, these artefacts are presented to the multispectral camera to perform the attacks. Thus, the artefact species corresponding to inkjet printer has a total of 5 subjects 7 spectral bands samples = 35 samples, and laser jet also has 35 samples. Figure 4 shows the example of multispectral face images from bona fide and the artefact presentation from EMSPAD database. 3.. Performance evaluation protocol In this work, we follow the experimental protocol as described in [7] for the PAD evaluation to demonstrate the superiority of the proposed method under the same protocol. The database is divided in two independent partitions, namely: Partition-I with subjects and Partition-II with 4 subjects. The Partition-I is used as the development database to determine the threshold value for bona fide and artefact species for the final classification. The Partition-II is solely utilized for the testing and reporting the results. Among 4 subjects from partition-ii, we divide in two independent partitions with 2 subjects each to get Set-I and Set-II. The Set-I is used as the training set and Set-II is used as the testing set in all the experiments reported in this paper. The performance of the PAD algorithms is presented using the following metrics [2]: Attack Presentation Classification Error Rate (APCER %): The error in classifying the attack samples as bona-fide (or normal) samples. Bonafide Presentation Attack Classification Error Rate (BPCER %): The error in classifying the bona fide samples as artefact samples. In this work, we report the performance at 73
5 P PAD Scores Probe Sample Scores PAD Scores PAD Scores Figure 5: Distribution of the comparison scores obtained on the probe multispectral face samples and the PAI species correspond to the Laser print artefacts (Laser-Laser) Comparison Score Bona fide Scores Comparison Scores.5 Bona fide Scores Figure 6: Distribution of the comparison scores obtained on the probe multispectral face samples and the PAI species correspond to the Inkjet print artefacts (Inkjet-Inkjet) the operating point with APCER = 5% and % and also the Equal Error Rate (EER%) computed when APCER is equal to BPCER. The operating point or threshold is set corresponding to the value of APCER = 5% and % to report the performance of the proposed method along with the state-of-the-art PAD methods Results and discussion In this section, we present the quantitative results of the proposed multispectral PAD scheme together with the comparative performance of the contemporary systems based on the image fusion and comparison score fusion. As the conventional multispectral face recognition systems work by combining the images capturing with different spectral wavelength either at image level or the comparison score level [5], we also compare these two approaches with the proposed approach. The image fusion approach is based on combining the multispectral images using wavelet coefficients by taking the average of all pixels across different spectral bands [3]. Further, we have used the Binarised Statistical Image Features (BSIF) and Support Vector Machines (SVM) as the PAD scheme to detect the attacks on the multispectral face recognition system. The second comparison system is based on the comparison score (a.k.a, PAD score) level fusion such that, BSIF-SVM scheme is evaluated independently on each spectral band and the corresponding PAD scores are combined using the sum rule to make the final decision on either bona fide or attack presentation. In this work, we have selected BSIF-SVM by considering it s robustness and accuracy on the detecting the artefact species, especially from the print attack on the extended multispectral face database [7]. To effectively quantify the performance of the proposed scheme, we carried out two different experiments namely: Experiment : This experiment aims at evaluating the performance of the PAD techniques on the known attack. Thus, the PAD methods are trained and tested on the same artefact species. Thus, this experiment has two protocols such as: training and testing with Laser print artefact (Laser-Laser) and training and testing with Inkjet print artefact (Inkjet- Inkjet) independently. In this experiment, we employ images from 2 Subjects samples = 2 bona fide and artefact scores from the PAD module that corresponds to the testing set. Experiment 2: This experiment is designed to evaluate the performance of the PAD methods to unknown attacks. Thus, this experiment has two protocols in which the first protocol is based on training the PAD modules with Laser print artefact and testing with Inkjet print artefact (indicated as Laser-Inkjet) and the second protocol is based on training the PAD module with Inkjet print artefact and testing with Laser print artefacts (indicated as Inkjet-Laser). In this experiment, we have employed 2 subjects sam- 74
6 o nm l k j i h g : Š ˆ V T U S R Q O Ÿ Bona fide Scores / Arteface Scores 2 4!"#$% &'()*% &%+,%-.% N M <KL 2 ;<< 4 =>?@A BCDEFA BAGHAIJA Figure 7: Distribution of the comparison scores obtained on the probe multispectral face samples and the PAI species when training data corresponds to Inkjet print artefacts and testing data corresponds to Laser print artefacts (Inkjet-Laser) WXX 4 YZ[\] ^_`ab] ^]cd]ef] ƒ q 2 pqq 4 rstuv wxyz{v wv }v~v ž Œ œ 2 ŒŒ 4 Ž š Figure 8: Distribution of the comparison scores obtained on the probe multispectral face samples and the PAI species when training data corresponds to Laser print artefacts and testing data corresponds to Inkjet print artefacts (Laser-Inkjet) ples = 2 bona-fide scores that corresponds to the testing set and 2 subjects samples = 2 artefact species scores that corresponds to both training and testing set of the artefact species (independent on Laser and inkjet print artefact). Figure 5 illustrates the PAD score distribution of the proposed scheme and the scores obtained from image fusion and score level fusion obtained on the artefact species corresponding to the Laser print (Laser-Laser). It can be observed that, the proposed PAD scheme shows better separation of artefact and bona fide scores indicating better performance as compared to combining the information of spectral bands of both image and comparison score level fusion. Table indicates the quantitative performance of the proposed scheme on Laser-Laser protocol when compared to the performance of both image fusion and comparison score level fusion methods. The proposed scheme has indicated the best result with an EER of 3.5% (see Figure 9 (a)) and a BPCER of % at APCER = 5% and BPCER = % at APCER = %. Figure 6 illustrates the PAD score distribution of the proposed scheme and the contemporary schemes based on image fusion and comparison score level fusion on the inkjet print artefacts (Inkjet-Inkjet). It can also be observed that the proposed PAD scheme shows good separation between artefact and bona fide scores when compared with both image and comparison score level fusion. Table indicates the quantitative performance of the proposed scheme that indicates the best performance with EER of % (see Figure 9 (a)) and a BPCER of % at APCER = 5% and BPCER = % at APCER = %. Thus, based on the experimental results obtained on both Laser-Laser and Inkjet-Inkjet in which the PAD systems are trained and tested on the same artefacts, it can be noted that performance of the proposed method has indicated best results with the lowest error rates. Figure 7 illustrates the PAD score distribution of the proposed scheme and the contemporary schemes based on image fusion and comparison score level fusion when Inkjet print artefact is used to train the systems and Laser print artefact is used test the systems (Inkjet-Laser). In this experiment, 4 Inkjet print artefacts are used for training and 4 Laser print artefact is used for the testing. It can observed here that, the artefact score distribution is spread close to the bona fide score presentation that has resulted in the reduced performance of the proposed method. However, similar observation is also valid for the image fusion and comparison score level fusion schemes. In spite of this, the proposed scheme has indicated the best performance with the EER of 7.62 % (see Figure 9 (a)) and a BPCER of 3.75 % at APCER = 5% and BPCER = % at APCER =%. Figure 8 illustrates the PAD score distribution of the proposed scheme and the contemporary schemes based on image fusion and comparison score level fusion when Laser print artefact is used to train the systems and Inkjet print artefact is used test the systems (Laser-Inkjet). It is inter- 75
7 Table : Quantitative performance of the proposed method Method Training-Testing EER (%) APCER = 5% APCER = % Inkjet-Inkjet Score fusion Approach Laser-Laser Inkjet-Laser Laser-Inkjet Inkjet-Inkjet Image Fusion Approach Laser-Laser Inkjet-Laser Laser-Inkjet Inkjet-Inkjet... Proposed Approach Laser-Laser Inkjet-Laser Laser-Inkjet BPCER (%) 3 2 Inkjet-inkjet Laser-Laser Inkjet-Laser Laser-Inkjet BPCER (%) 8 Inkjet-Inkjet Laser-Laser Inkjet-Laser Laser-Inkjet BPCER(%) 2 ª Inkjet-Inkjet Laser-Laser Inkjet-Laser Laser-Inkjet APCER (%) 2 8 APCER (%) ª 2 APCER(%) Figure 9: EER performance of the proposed scheme and the state-of-the-art schemes on four different protocols corresponding to two different experiments on EMSPAD database esting to observe for the separation of bona fide and artefact samples with the proposed scheme when compared with the contemporary methods. The proposed method has demonstrated the best performance with the EER of 3. % (see Figure 9 (a)) and a BPCER of.5 % at APCER = 5% and BPCER = % at APCER = %. Based on the extensive experiments carried out on four different protocols, the best performance of the proposed scheme has been revealed on both known and unknown attacks. Since the proposed method is based on the spectral signature that are characterized based on the reflective properties of the captured image, it can reliably detect and differentiate the skin reflectance when compared to that of the artefact (or material used to generate the artefact). 4. Conclusion Presentation attack detection techniques are widely studied, especially, for the visible spectrum face recognition. However, the use of extended multispectral face sensor for face PAD detection is gaining momentum as they can be used to detect low cost attacks based on artefacts such as printed photo attack. This work has explored the intrinsic characteristics of the extended multispectral sensor by characterising the spectral signatures to quantify the captured images as bona fide or artefact. The spectral signature is a unique feature that can quantify the reflective properties of the captured images and the applicability of the spectral signatures can robustly detect the presentation attacks on extended face recognition sensors. Furthermore, as the spectral characteristics of the normal skin is very different than the materials used for the presentation attacks when imaged from extended spectral camera, the proposed scheme can also be used to detect the unknown attacks. Extensive experiments are carried out on the publicly available Extended Multispectral Presentation Attack Face Database (EMSPAD) comprising of 5 subjects with two different 76
8 Presentation Attack Instruments (PAI) generated using two different printers. Experiments are designed in four different protocols in which first two protocols are based on detecting the known attacks and thus, the proposed method is trained and tested on the same PAI (or artefact). The next two protocols are based on the evaluating the proposed method for the unknown attacks and thus, the proposed scheme is trained and tested using different PAIs. Based on the obtained results, the proposed method has illustrated an improved performance when compared with the contemporary methods based on the image fusion and the PAD score fusion using SUM rule. The proposed method has also indicated the best performance for known and unknown attacks with the performance of BPCER = % at APCER = %. The future work will focus on extracting the spectral signature from the prominent region of the face (e.g. cheeks, eye region) and establish a weighting strategy to characterise the spectral signature with higher degree of accuracy. Acknowledgment This work is carried out under the funding of the Research Council of Norway (Grant No. IKTPLUSS 2483/O7). References [] I. Chingovska, N. Erdogmus, A. Anjos, and S. Marcel. Face recognition systems under spoofing attacks. In Face Recognition Across the Imaging Spectrum, pages Springer, 26. [2] International Organization for Standardization. ISO/IEC WD Information Technology - Biometric presentation attack detection - Part 3: Testing and Reporting, 25. [3] H. Li, B. Manjunath, and S. K. Mitra. Multi-sensor image fusion using the wavelet transform. In Image Processing, 994. Proceedings. ICIP-94., IEEE International Conference, volume, pages 5 55, 994. [4] R. Raghavendra and C. Busch. Presentation attack detection methods for face recognition system - A comprehensive survey. ACM Computing Surveys, 5((8)): 45, 27. [5] R. Raghavendra, B. Dorizzi, A. Rao, and K. Hemantha. Particle swarm optimization based fusion of near infrared and visible images for improved face verification. Pattern Recognition, 44(2):4 4, 2. [6] R. Raghavendra, Kiran Raja, S. Marcel, and C. Busch. Face presentation attack detection across spectrum using timefrequency descriptors of maximal response in laplacian scalespace. In Sixth International Conference on Image Processing Theory, Tools and Applications (IPTA), pages 8. IEEE, 27. [7] R. Raghavendra, Kiran Raja, V. Sushma, C. Faouzi, and C. Busch. On the vulnerability of extended multispectral face recognition systems towards presentation attacks. In IEEE International Conference on Identity, Security and Behavior Analysis (ISBA), pages 8. IEEE, 27. [8] H. Steiner, A. Kolb, and N. Jung. Reliable face anti-spoofing using multispectral swir imaging. In 26 International Conference on Biometrics (ICB), pages 8, June 26. [9] D. Yi, Z. Lei, Z. Zhang, and S. Z. Li. Face anti-spoofing: Multi-spectral approach. In Handbook of Biometric Anti- Spoofing, pages Springer,
Presentation Attack Detection Algorithms for Finger Vein Biometrics: A Comprehensive Study
 215 11th International Conference on Signal-Image Technology & Internet-Based Systems Presentation Attack Detection Algorithms for Finger Vein Biometrics: A Comprehensive Study R. Raghavendra Christoph
215 11th International Conference on Signal-Image Technology & Internet-Based Systems Presentation Attack Detection Algorithms for Finger Vein Biometrics: A Comprehensive Study R. Raghavendra Christoph
Empirical Evaluation of Visible Spectrum Iris versus Periocular Recognition in Unconstrained Scenario on Smartphones
 Empirical Evaluation of Visible Spectrum Iris versus Periocular Recognition in Unconstrained Scenario on Smartphones Kiran B. Raja * R. Raghavendra * Christoph Busch * * Norwegian Biometric Laboratory,
Empirical Evaluation of Visible Spectrum Iris versus Periocular Recognition in Unconstrained Scenario on Smartphones Kiran B. Raja * R. Raghavendra * Christoph Busch * * Norwegian Biometric Laboratory,
Presentation Attack Detection Methods for Face Recognition Systems: A Comprehensive Survey
 Presentation Attack Detection Methods for Face Recognition Systems: A Comprehensive Survey RAGHAVENDRA RAMACHANDRA and CHRISTOPH BUSCH, Norwegian Biometric Laboratory, Norwegian University of Science and
Presentation Attack Detection Methods for Face Recognition Systems: A Comprehensive Survey RAGHAVENDRA RAMACHANDRA and CHRISTOPH BUSCH, Norwegian Biometric Laboratory, Norwegian University of Science and
A Novel Image Fusion Scheme For Robust Multiple Face Recognition With Light-field Camera
 A Novel Image Fusion Scheme For Robust Multiple Face Recognition With Light-field Camera R. Raghavendra Kiran B Raja Bian Yang Christoph Busch Norwegian Biometric Laboratory, Gjøvik University College,
A Novel Image Fusion Scheme For Robust Multiple Face Recognition With Light-field Camera R. Raghavendra Kiran B Raja Bian Yang Christoph Busch Norwegian Biometric Laboratory, Gjøvik University College,
International Journal of Scientific & Engineering Research, Volume 7, Issue 12, December ISSN IJSER
 International Journal of Scientific & Engineering Research, Volume 7, Issue 12, December-2016 192 A Novel Approach For Face Liveness Detection To Avoid Face Spoofing Attacks Meenakshi Research Scholar,
International Journal of Scientific & Engineering Research, Volume 7, Issue 12, December-2016 192 A Novel Approach For Face Liveness Detection To Avoid Face Spoofing Attacks Meenakshi Research Scholar,
A New Fake Iris Detection Method
 A New Fake Iris Detection Method Xiaofu He 1, Yue Lu 1, and Pengfei Shi 2 1 Department of Computer Science and Technology, East China Normal University, Shanghai 200241, China {xfhe,ylu}@cs.ecnu.edu.cn
A New Fake Iris Detection Method Xiaofu He 1, Yue Lu 1, and Pengfei Shi 2 1 Department of Computer Science and Technology, East China Normal University, Shanghai 200241, China {xfhe,ylu}@cs.ecnu.edu.cn
An Enhanced Biometric System for Personal Authentication
 IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p- ISSN: 2278-8735. Volume 6, Issue 3 (May. - Jun. 2013), PP 63-69 An Enhanced Biometric System for Personal Authentication
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p- ISSN: 2278-8735. Volume 6, Issue 3 (May. - Jun. 2013), PP 63-69 An Enhanced Biometric System for Personal Authentication
Near Infrared Face Image Quality Assessment System of Video Sequences
 2011 Sixth International Conference on Image and Graphics Near Infrared Face Image Quality Assessment System of Video Sequences Jianfeng Long College of Electrical and Information Engineering Hunan University
2011 Sixth International Conference on Image and Graphics Near Infrared Face Image Quality Assessment System of Video Sequences Jianfeng Long College of Electrical and Information Engineering Hunan University
3D Face Recognition System in Time Critical Security Applications
 Middle-East Journal of Scientific Research 25 (7): 1619-1623, 2017 ISSN 1990-9233 IDOSI Publications, 2017 DOI: 10.5829/idosi.mejsr.2017.1619.1623 3D Face Recognition System in Time Critical Security Applications
Middle-East Journal of Scientific Research 25 (7): 1619-1623, 2017 ISSN 1990-9233 IDOSI Publications, 2017 DOI: 10.5829/idosi.mejsr.2017.1619.1623 3D Face Recognition System in Time Critical Security Applications
SCIENCE & TECHNOLOGY
 Pertanika J. Sci. & Technol. 25 (S): 163-172 (2017) SCIENCE & TECHNOLOGY Journal homepage: http://www.pertanika.upm.edu.my/ Performance Comparison of Min-Max Normalisation on Frontal Face Detection Using
Pertanika J. Sci. & Technol. 25 (S): 163-172 (2017) SCIENCE & TECHNOLOGY Journal homepage: http://www.pertanika.upm.edu.my/ Performance Comparison of Min-Max Normalisation on Frontal Face Detection Using
Feature Extraction Techniques for Dorsal Hand Vein Pattern
 Feature Extraction Techniques for Dorsal Hand Vein Pattern Pooja Ramsoful, Maleika Heenaye-Mamode Khan Department of Computer Science and Engineering University of Mauritius Mauritius pooja.ramsoful@umail.uom.ac.mu,
Feature Extraction Techniques for Dorsal Hand Vein Pattern Pooja Ramsoful, Maleika Heenaye-Mamode Khan Department of Computer Science and Engineering University of Mauritius Mauritius pooja.ramsoful@umail.uom.ac.mu,
Feature Extraction Technique Based On Circular Strip for Palmprint Recognition
 Feature Extraction Technique Based On Circular Strip for Palmprint Recognition Dr.S.Valarmathy 1, R.Karthiprakash 2, C.Poonkuzhali 3 1, 2, 3 ECE Department, Bannari Amman Institute of Technology, Sathyamangalam
Feature Extraction Technique Based On Circular Strip for Palmprint Recognition Dr.S.Valarmathy 1, R.Karthiprakash 2, C.Poonkuzhali 3 1, 2, 3 ECE Department, Bannari Amman Institute of Technology, Sathyamangalam
A Novel Algorithm for Hand Vein Recognition Based on Wavelet Decomposition and Mean Absolute Deviation
 Sensors & Transducers, Vol. 6, Issue 2, December 203, pp. 53-58 Sensors & Transducers 203 by IFSA http://www.sensorsportal.com A Novel Algorithm for Hand Vein Recognition Based on Wavelet Decomposition
Sensors & Transducers, Vol. 6, Issue 2, December 203, pp. 53-58 Sensors & Transducers 203 by IFSA http://www.sensorsportal.com A Novel Algorithm for Hand Vein Recognition Based on Wavelet Decomposition
Iris Recognition-based Security System with Canny Filter
 Canny Filter Dr. Computer Engineering Department, University of Technology, Baghdad-Iraq E-mail: hjhh2007@yahoo.com Received: 8/9/2014 Accepted: 21/1/2015 Abstract Image identification plays a great role
Canny Filter Dr. Computer Engineering Department, University of Technology, Baghdad-Iraq E-mail: hjhh2007@yahoo.com Received: 8/9/2014 Accepted: 21/1/2015 Abstract Image identification plays a great role
Multimodal Face Recognition using Hybrid Correlation Filters
 Multimodal Face Recognition using Hybrid Correlation Filters Anamika Dubey, Abhishek Sharma Electrical Engineering Department, Indian Institute of Technology Roorkee, India {ana.iitr, abhisharayiya}@gmail.com
Multimodal Face Recognition using Hybrid Correlation Filters Anamika Dubey, Abhishek Sharma Electrical Engineering Department, Indian Institute of Technology Roorkee, India {ana.iitr, abhisharayiya}@gmail.com
IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION
 IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION Sevinc Bayram a, Husrev T. Sencar b, Nasir Memon b E-mail: sevincbayram@hotmail.com, taha@isis.poly.edu, memon@poly.edu a Dept.
IMPROVEMENTS ON SOURCE CAMERA-MODEL IDENTIFICATION BASED ON CFA INTERPOLATION Sevinc Bayram a, Husrev T. Sencar b, Nasir Memon b E-mail: sevincbayram@hotmail.com, taha@isis.poly.edu, memon@poly.edu a Dept.
ENHANCHED PALM PRINT IMAGES FOR PERSONAL ACCURATE IDENTIFICATION
 ENHANCHED PALM PRINT IMAGES FOR PERSONAL ACCURATE IDENTIFICATION Prof. Rahul Sathawane 1, Aishwarya Shende 2, Pooja Tete 3, Naina Chandravanshi 4, Nisha Surjuse 5 1 Prof. Rahul Sathawane, Information Technology,
ENHANCHED PALM PRINT IMAGES FOR PERSONAL ACCURATE IDENTIFICATION Prof. Rahul Sathawane 1, Aishwarya Shende 2, Pooja Tete 3, Naina Chandravanshi 4, Nisha Surjuse 5 1 Prof. Rahul Sathawane, Information Technology,
FACE RECOGNITION USING NEURAL NETWORKS
 Int. J. Elec&Electr.Eng&Telecoms. 2014 Vinoda Yaragatti and Bhaskar B, 2014 Research Paper ISSN 2319 2518 www.ijeetc.com Vol. 3, No. 3, July 2014 2014 IJEETC. All Rights Reserved FACE RECOGNITION USING
Int. J. Elec&Electr.Eng&Telecoms. 2014 Vinoda Yaragatti and Bhaskar B, 2014 Research Paper ISSN 2319 2518 www.ijeetc.com Vol. 3, No. 3, July 2014 2014 IJEETC. All Rights Reserved FACE RECOGNITION USING
Image Extraction using Image Mining Technique
 IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
Global and Local Quality Measures for NIR Iris Video
 Global and Local Quality Measures for NIR Iris Video Jinyu Zuo and Natalia A. Schmid Lane Department of Computer Science and Electrical Engineering West Virginia University, Morgantown, WV 26506 jzuo@mix.wvu.edu
Global and Local Quality Measures for NIR Iris Video Jinyu Zuo and Natalia A. Schmid Lane Department of Computer Science and Electrical Engineering West Virginia University, Morgantown, WV 26506 jzuo@mix.wvu.edu
3D Face Recognition in Biometrics
 3D Face Recognition in Biometrics CHAO LI, ARMANDO BARRETO Electrical & Computer Engineering Department Florida International University 10555 West Flagler ST. EAS 3970 33174 USA {cli007, barretoa}@fiu.edu
3D Face Recognition in Biometrics CHAO LI, ARMANDO BARRETO Electrical & Computer Engineering Department Florida International University 10555 West Flagler ST. EAS 3970 33174 USA {cli007, barretoa}@fiu.edu
License Plate Localisation based on Morphological Operations
 License Plate Localisation based on Morphological Operations Xiaojun Zhai, Faycal Benssali and Soodamani Ramalingam School of Engineering & Technology University of Hertfordshire, UH Hatfield, UK Abstract
License Plate Localisation based on Morphological Operations Xiaojun Zhai, Faycal Benssali and Soodamani Ramalingam School of Engineering & Technology University of Hertfordshire, UH Hatfield, UK Abstract
RECOGNITION OF RECAPTURED IMAGES USING PHYSICAL BASED FEATURES
 RECOGNITION OF RECAPTURED IMAGES USING PHYSICAL BASED FEATURES ABSTRACT S. A. A. H. Samaraweera 1 and B. Mayurathan 2 1 Department of Computer Science, University of Jaffna, Sri Lanka anuash119@gmail.com
RECOGNITION OF RECAPTURED IMAGES USING PHYSICAL BASED FEATURES ABSTRACT S. A. A. H. Samaraweera 1 and B. Mayurathan 2 1 Department of Computer Science, University of Jaffna, Sri Lanka anuash119@gmail.com
Contact lens detection in iris images
 page 1 Chapter 1 Contact lens detection in iris images Jukka Komulainen, Abdenour Hadid and Matti Pietikäinen Iris texture provides the means for extremely accurate uni-modal person identification. However,
page 1 Chapter 1 Contact lens detection in iris images Jukka Komulainen, Abdenour Hadid and Matti Pietikäinen Iris texture provides the means for extremely accurate uni-modal person identification. However,
Wavelet-based Image Splicing Forgery Detection
 Wavelet-based Image Splicing Forgery Detection 1 Tulsi Thakur M.Tech (CSE) Student, Department of Computer Technology, basiltulsi@gmail.com 2 Dr. Kavita Singh Head & Associate Professor, Department of
Wavelet-based Image Splicing Forgery Detection 1 Tulsi Thakur M.Tech (CSE) Student, Department of Computer Technology, basiltulsi@gmail.com 2 Dr. Kavita Singh Head & Associate Professor, Department of
Iris Recognition in Mobile Devices
 Chapter 12 Iris Recognition in Mobile Devices Alec Yenter and Abhishek Verma CONTENTS 12.1 Overview 300 12.1.1 History 300 12.1.2 Methods 300 12.1.3 Challenges 300 12.2 Mobile Device Experiment 301 12.2.1
Chapter 12 Iris Recognition in Mobile Devices Alec Yenter and Abhishek Verma CONTENTS 12.1 Overview 300 12.1.1 History 300 12.1.2 Methods 300 12.1.3 Challenges 300 12.2 Mobile Device Experiment 301 12.2.1
Biometric Recognition: How Do I Know Who You Are?
 Biometric Recognition: How Do I Know Who You Are? Anil K. Jain Department of Computer Science and Engineering, 3115 Engineering Building, Michigan State University, East Lansing, MI 48824, USA jain@cse.msu.edu
Biometric Recognition: How Do I Know Who You Are? Anil K. Jain Department of Computer Science and Engineering, 3115 Engineering Building, Michigan State University, East Lansing, MI 48824, USA jain@cse.msu.edu
COLOR LASER PRINTER IDENTIFICATION USING PHOTOGRAPHED HALFTONE IMAGES. Do-Guk Kim, Heung-Kyu Lee
 COLOR LASER PRINTER IDENTIFICATION USING PHOTOGRAPHED HALFTONE IMAGES Do-Guk Kim, Heung-Kyu Lee Graduate School of Information Security, KAIST Department of Computer Science, KAIST ABSTRACT Due to the
COLOR LASER PRINTER IDENTIFICATION USING PHOTOGRAPHED HALFTONE IMAGES Do-Guk Kim, Heung-Kyu Lee Graduate School of Information Security, KAIST Department of Computer Science, KAIST ABSTRACT Due to the
Roberto Togneri (Signal Processing and Recognition Lab)
 Signal Processing and Machine Learning for Power Quality Disturbance Detection and Classification Roberto Togneri (Signal Processing and Recognition Lab) Power Quality (PQ) disturbances are broadly classified
Signal Processing and Machine Learning for Power Quality Disturbance Detection and Classification Roberto Togneri (Signal Processing and Recognition Lab) Power Quality (PQ) disturbances are broadly classified
Predicting Eye Color from Near Infrared Iris Images
 Predicting Eye Color from Near Infrared Iris Images Denton Bobeldyk 1,2 Arun Ross 1 denny@bobeldyk.org rossarun@cse.msu.edu 1 Michigan State University, East Lansing, USA 2 Davenport University, Grand
Predicting Eye Color from Near Infrared Iris Images Denton Bobeldyk 1,2 Arun Ross 1 denny@bobeldyk.org rossarun@cse.msu.edu 1 Michigan State University, East Lansing, USA 2 Davenport University, Grand
Biometric: EEG brainwaves
 Biometric: EEG brainwaves Jeovane Honório Alves 1 1 Department of Computer Science Federal University of Parana Curitiba December 5, 2016 Jeovane Honório Alves (UFPR) Biometric: EEG brainwaves Curitiba
Biometric: EEG brainwaves Jeovane Honório Alves 1 1 Department of Computer Science Federal University of Parana Curitiba December 5, 2016 Jeovane Honório Alves (UFPR) Biometric: EEG brainwaves Curitiba
Fusing Iris Colour and Texture information for fast iris recognition on mobile devices
 Fusing Iris Colour and Texture information for fast iris recognition on mobile devices Chiara Galdi EURECOM Sophia Antipolis, France Email: chiara.galdi@eurecom.fr Jean-Luc Dugelay EURECOM Sophia Antipolis,
Fusing Iris Colour and Texture information for fast iris recognition on mobile devices Chiara Galdi EURECOM Sophia Antipolis, France Email: chiara.galdi@eurecom.fr Jean-Luc Dugelay EURECOM Sophia Antipolis,
Design and Testing of DWT based Image Fusion System using MATLAB Simulink
 Design and Testing of DWT based Image Fusion System using MATLAB Simulink Ms. Sulochana T 1, Mr. Dilip Chandra E 2, Dr. S S Manvi 3, Mr. Imran Rasheed 4 M.Tech Scholar (VLSI Design And Embedded System),
Design and Testing of DWT based Image Fusion System using MATLAB Simulink Ms. Sulochana T 1, Mr. Dilip Chandra E 2, Dr. S S Manvi 3, Mr. Imran Rasheed 4 M.Tech Scholar (VLSI Design And Embedded System),
Note on CASIA-IrisV3
 Note on CASIA-IrisV3 1. Introduction With fast development of iris image acquisition technology, iris recognition is expected to become a fundamental component of modern society, with wide application
Note on CASIA-IrisV3 1. Introduction With fast development of iris image acquisition technology, iris recognition is expected to become a fundamental component of modern society, with wide application
Adaptive Feature Analysis Based SAR Image Classification
 I J C T A, 10(9), 2017, pp. 973-977 International Science Press ISSN: 0974-5572 Adaptive Feature Analysis Based SAR Image Classification Debabrata Samanta*, Abul Hasnat** and Mousumi Paul*** ABSTRACT SAR
I J C T A, 10(9), 2017, pp. 973-977 International Science Press ISSN: 0974-5572 Adaptive Feature Analysis Based SAR Image Classification Debabrata Samanta*, Abul Hasnat** and Mousumi Paul*** ABSTRACT SAR
Student Attendance Monitoring System Via Face Detection and Recognition System
 IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 11 May 2016 ISSN (online): 2349-784X Student Attendance Monitoring System Via Face Detection and Recognition System Pinal
IJSTE - International Journal of Science Technology & Engineering Volume 2 Issue 11 May 2016 ISSN (online): 2349-784X Student Attendance Monitoring System Via Face Detection and Recognition System Pinal
EFFICIENT ATTENDANCE MANAGEMENT SYSTEM USING FACE DETECTION AND RECOGNITION
 EFFICIENT ATTENDANCE MANAGEMENT SYSTEM USING FACE DETECTION AND RECOGNITION 1 Arun.A.V, 2 Bhatath.S, 3 Chethan.N, 4 Manmohan.C.M, 5 Hamsaveni M 1,2,3,4,5 Department of Computer Science and Engineering,
EFFICIENT ATTENDANCE MANAGEMENT SYSTEM USING FACE DETECTION AND RECOGNITION 1 Arun.A.V, 2 Bhatath.S, 3 Chethan.N, 4 Manmohan.C.M, 5 Hamsaveni M 1,2,3,4,5 Department of Computer Science and Engineering,
Classification in Image processing: A Survey
 Classification in Image processing: A Survey Rashmi R V, Sheela Sridhar Department of computer science and Engineering, B.N.M.I.T, Bangalore-560070 Department of computer science and Engineering, B.N.M.I.T,
Classification in Image processing: A Survey Rashmi R V, Sheela Sridhar Department of computer science and Engineering, B.N.M.I.T, Bangalore-560070 Department of computer science and Engineering, B.N.M.I.T,
THE IMAGE REGISTRATION TECHNIQUE FOR HIGH RESOLUTION REMOTE SENSING IMAGE IN HILLY AREA
 THE IMAGE REGISTRATION TECHNIQUE FOR HIGH RESOLUTION REMOTE SENSING IMAGE IN HILLY AREA Gang Hong, Yun Zhang Department of Geodesy and Geomatics Engineering University of New Brunswick Fredericton, New
THE IMAGE REGISTRATION TECHNIQUE FOR HIGH RESOLUTION REMOTE SENSING IMAGE IN HILLY AREA Gang Hong, Yun Zhang Department of Geodesy and Geomatics Engineering University of New Brunswick Fredericton, New
VideometerLab 3 Multi-Spectral Imaging
 analytikltd VideometerLab 3 Multi-Spectral Imaging Rapid Non-destructive Analysis of Heritage Artefacts Adrian Waltho, Analytik Ltd (Cambridge, UK) adrian.waltho@analytik.co.uk www.analytik.co.uk/multispectral-imaging
analytikltd VideometerLab 3 Multi-Spectral Imaging Rapid Non-destructive Analysis of Heritage Artefacts Adrian Waltho, Analytik Ltd (Cambridge, UK) adrian.waltho@analytik.co.uk www.analytik.co.uk/multispectral-imaging
Processing and Enhancement of Palm Vein Image in Vein Pattern Recognition System
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 4, April 2015,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 4, April 2015,
Practical View on Face Presentation Attack Detection
 DAMER, DIMITROV: PRACTICAL FACE PRESENTATION ATTACK DETECTION 1 Practical View on Face Presentation Attack Detection Naser Damer naser.damer@igd.fraunhofer.de Kristiyan Dimitrov kristiyan.dimitrov@igd.fraunhofer.de
DAMER, DIMITROV: PRACTICAL FACE PRESENTATION ATTACK DETECTION 1 Practical View on Face Presentation Attack Detection Naser Damer naser.damer@igd.fraunhofer.de Kristiyan Dimitrov kristiyan.dimitrov@igd.fraunhofer.de
THE EFFECT OF PHYSICAL BASED FEATURES FOR RECOGNITION OF RECAPTURED IMAGES
 THE EFFECT OF PHYSICAL BASED FEATURES FOR RECOGNITION OF RECAPTURED IMAGES ABSTRACT S. A. A. H. Samaraweera and B. Mayurathan Department of Computer Science, University of Jaffna, Sri Lanka It is very
THE EFFECT OF PHYSICAL BASED FEATURES FOR RECOGNITION OF RECAPTURED IMAGES ABSTRACT S. A. A. H. Samaraweera and B. Mayurathan Department of Computer Science, University of Jaffna, Sri Lanka It is very
Content Based Image Retrieval Using Color Histogram
 Content Based Image Retrieval Using Color Histogram Nitin Jain Assistant Professor, Lokmanya Tilak College of Engineering, Navi Mumbai, India. Dr. S. S. Salankar Professor, G.H. Raisoni College of Engineering,
Content Based Image Retrieval Using Color Histogram Nitin Jain Assistant Professor, Lokmanya Tilak College of Engineering, Navi Mumbai, India. Dr. S. S. Salankar Professor, G.H. Raisoni College of Engineering,
Objective Evaluation of Edge Blur and Ringing Artefacts: Application to JPEG and JPEG 2000 Image Codecs
 Objective Evaluation of Edge Blur and Artefacts: Application to JPEG and JPEG 2 Image Codecs G. A. D. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences and Technology, Massey
Objective Evaluation of Edge Blur and Artefacts: Application to JPEG and JPEG 2 Image Codecs G. A. D. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences and Technology, Massey
BIOMETRIC IDENTIFICATION USING 3D FACE SCANS
 BIOMETRIC IDENTIFICATION USING 3D FACE SCANS Chao Li Armando Barreto Craig Chin Jing Zhai Electrical and Computer Engineering Department Florida International University Miami, Florida, 33174, USA ABSTRACT
BIOMETRIC IDENTIFICATION USING 3D FACE SCANS Chao Li Armando Barreto Craig Chin Jing Zhai Electrical and Computer Engineering Department Florida International University Miami, Florida, 33174, USA ABSTRACT
Color Constancy Using Standard Deviation of Color Channels
 2010 International Conference on Pattern Recognition Color Constancy Using Standard Deviation of Color Channels Anustup Choudhury and Gérard Medioni Department of Computer Science University of Southern
2010 International Conference on Pattern Recognition Color Constancy Using Standard Deviation of Color Channels Anustup Choudhury and Gérard Medioni Department of Computer Science University of Southern
Remote Sensing. The following figure is grey scale display of SPOT Panchromatic without stretching.
 Remote Sensing Objectives This unit will briefly explain display of remote sensing image, geometric correction, spatial enhancement, spectral enhancement and classification of remote sensing image. At
Remote Sensing Objectives This unit will briefly explain display of remote sensing image, geometric correction, spatial enhancement, spectral enhancement and classification of remote sensing image. At
EFFECTS OF SEVERE SIGNAL DEGRADATION ON EAR DETECTION. J. Wagner, A. Pflug, C. Rathgeb and C. Busch
 EFFECTS OF SEVERE SIGNAL DEGRADATION ON EAR DETECTION J. Wagner, A. Pflug, C. Rathgeb and C. Busch da/sec Biometrics and Internet Security Research Group Hochschule Darmstadt, Darmstadt, Germany {johannes.wagner,anika.pflug,christian.rathgeb,christoph.busch}@cased.de
EFFECTS OF SEVERE SIGNAL DEGRADATION ON EAR DETECTION J. Wagner, A. Pflug, C. Rathgeb and C. Busch da/sec Biometrics and Internet Security Research Group Hochschule Darmstadt, Darmstadt, Germany {johannes.wagner,anika.pflug,christian.rathgeb,christoph.busch}@cased.de
Performance study of Text-independent Speaker identification system using MFCC & IMFCC for Telephone and Microphone Speeches
 Performance study of Text-independent Speaker identification system using & I for Telephone and Microphone Speeches Ruchi Chaudhary, National Technical Research Organization Abstract: A state-of-the-art
Performance study of Text-independent Speaker identification system using & I for Telephone and Microphone Speeches Ruchi Chaudhary, National Technical Research Organization Abstract: A state-of-the-art
Biometrics 2/23/17. the last category for authentication methods is. this is the realm of biometrics
 CSC362, Information Security the last category for authentication methods is Something I am or do, which means some physical or behavioral characteristic that uniquely identifies the user and can be used
CSC362, Information Security the last category for authentication methods is Something I am or do, which means some physical or behavioral characteristic that uniquely identifies the user and can be used
Stamp detection in scanned documents
 Annales UMCS Informatica AI X, 1 (2010) 61-68 DOI: 10.2478/v10065-010-0036-6 Stamp detection in scanned documents Paweł Forczmański Chair of Multimedia Systems, West Pomeranian University of Technology,
Annales UMCS Informatica AI X, 1 (2010) 61-68 DOI: 10.2478/v10065-010-0036-6 Stamp detection in scanned documents Paweł Forczmański Chair of Multimedia Systems, West Pomeranian University of Technology,
CAN NO-REFERENCE IMAGE QUALITY METRICS ASSESS VISIBLE WAVELENGTH IRIS SAMPLE QUALITY?
 CAN NO-REFERENCE IMAGE QUALITY METRICS ASSESS VISIBLE WAVELENGTH IRIS SAMPLE QUALITY? Xinwei Liu 1,2,, Marius Pedersen 2, Christophe Charrier 1, and Patrick Bours 2 1 Normandie Univ, UNICAEN, ENSICAEN,
CAN NO-REFERENCE IMAGE QUALITY METRICS ASSESS VISIBLE WAVELENGTH IRIS SAMPLE QUALITY? Xinwei Liu 1,2,, Marius Pedersen 2, Christophe Charrier 1, and Patrick Bours 2 1 Normandie Univ, UNICAEN, ENSICAEN,
Université Laval Face Motion and Time-Lapse Video Database (UL-FMTV)
 14 th Quantitative InfraRed Thermography Conference Université Laval Face Motion and Time-Lapse Video Database (UL-FMTV) by Reza Shoja Ghiass*, Hakim Bendada*, Xavier Maldague* *Computer Vision and Systems
14 th Quantitative InfraRed Thermography Conference Université Laval Face Motion and Time-Lapse Video Database (UL-FMTV) by Reza Shoja Ghiass*, Hakim Bendada*, Xavier Maldague* *Computer Vision and Systems
Evaluation of Biometric Systems. Christophe Rosenberger
 Evaluation of Biometric Systems Christophe Rosenberger Outline GREYC research lab Evaluation: a love story Evaluation of biometric systems Quality of biometric templates Conclusions & perspectives 2 GREYC
Evaluation of Biometric Systems Christophe Rosenberger Outline GREYC research lab Evaluation: a love story Evaluation of biometric systems Quality of biometric templates Conclusions & perspectives 2 GREYC
Stochastic Screens Robust to Mis- Registration in Multi-Pass Printing
 Published as: G. Sharma, S. Wang, and Z. Fan, "Stochastic Screens robust to misregistration in multi-pass printing," Proc. SPIE: Color Imaging: Processing, Hard Copy, and Applications IX, vol. 5293, San
Published as: G. Sharma, S. Wang, and Z. Fan, "Stochastic Screens robust to misregistration in multi-pass printing," Proc. SPIE: Color Imaging: Processing, Hard Copy, and Applications IX, vol. 5293, San
Iris Recognition using Hamming Distance and Fragile Bit Distance
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 06, 2015 ISSN (online): 2321-0613 Iris Recognition using Hamming Distance and Fragile Bit Distance Mr. Vivek B. Mandlik
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 06, 2015 ISSN (online): 2321-0613 Iris Recognition using Hamming Distance and Fragile Bit Distance Mr. Vivek B. Mandlik
Sensors. CSE 666 Lecture Slides SUNY at Buffalo
 Sensors CSE 666 Lecture Slides SUNY at Buffalo Overview Optical Fingerprint Imaging Ultrasound Fingerprint Imaging Multispectral Fingerprint Imaging Palm Vein Sensors References Fingerprint Sensors Various
Sensors CSE 666 Lecture Slides SUNY at Buffalo Overview Optical Fingerprint Imaging Ultrasound Fingerprint Imaging Multispectral Fingerprint Imaging Palm Vein Sensors References Fingerprint Sensors Various
Datong Chen, Albrecht Schmidt, Hans-Werner Gellersen
 Datong Chen, Albrecht Schmidt, Hans-Werner Gellersen TecO (Telecooperation Office), University of Karlsruhe Vincenz-Prießnitz-Str.1, 76131 Karlruhe, Germany {charles, albrecht, hwg}@teco.uni-karlsruhe.de
Datong Chen, Albrecht Schmidt, Hans-Werner Gellersen TecO (Telecooperation Office), University of Karlsruhe Vincenz-Prießnitz-Str.1, 76131 Karlruhe, Germany {charles, albrecht, hwg}@teco.uni-karlsruhe.de
Outdoor Face Recognition Using Enhanced Near Infrared Imaging
 Outdoor Face Recognition Using Enhanced Near Infrared Imaging Dong Yi, Rong Liu, RuFeng Chu, Rui Wang, Dong Liu, and Stan Z. Li Center for Biometrics and Security Research & National Laboratory of Pattern
Outdoor Face Recognition Using Enhanced Near Infrared Imaging Dong Yi, Rong Liu, RuFeng Chu, Rui Wang, Dong Liu, and Stan Z. Li Center for Biometrics and Security Research & National Laboratory of Pattern
Spectral signatures of surface materials in pig buildings
 Spectral signatures of surface materials in pig buildings by Guoqiang Zhang and Jan S. Strøm Danish Institute of Agricultural Sciences, Research Centre Bygholm Department of Agricultural Engineering P.O.
Spectral signatures of surface materials in pig buildings by Guoqiang Zhang and Jan S. Strøm Danish Institute of Agricultural Sciences, Research Centre Bygholm Department of Agricultural Engineering P.O.
High-speed Micro-crack Detection of Solar Wafers with Variable Thickness
 High-speed Micro-crack Detection of Solar Wafers with Variable Thickness T. W. Teo, Z. Mahdavipour, M. Z. Abdullah School of Electrical and Electronic Engineering Engineering Campus Universiti Sains Malaysia
High-speed Micro-crack Detection of Solar Wafers with Variable Thickness T. W. Teo, Z. Mahdavipour, M. Z. Abdullah School of Electrical and Electronic Engineering Engineering Campus Universiti Sains Malaysia
CHAPTER-V SUMMARY AND CONCLUSIONS
 CHAPTER-V SUMMARY AND CONCLUSIONS SUMMARY AND CONCLUSIONS The present work has been devoted to the differentiation and characterization of inkjet printed documents. All the four primary inks used in printers
CHAPTER-V SUMMARY AND CONCLUSIONS SUMMARY AND CONCLUSIONS The present work has been devoted to the differentiation and characterization of inkjet printed documents. All the four primary inks used in printers
3 Department of Computer science and Application, Kurukshetra University, Kurukshetra, India
 Minimizing Sensor Interoperability Problem using Euclidean Distance Himani 1, Parikshit 2, Dr.Chander Kant 3 M.tech Scholar 1, Assistant Professor 2, 3 1,2 Doon Valley Institute of Engineering and Technology,
Minimizing Sensor Interoperability Problem using Euclidean Distance Himani 1, Parikshit 2, Dr.Chander Kant 3 M.tech Scholar 1, Assistant Professor 2, 3 1,2 Doon Valley Institute of Engineering and Technology,
Visible-light and Infrared Face Recognition
 Visible-light and Infrared Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 {xchen2, flynn, kwb}@nd.edu
Visible-light and Infrared Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 {xchen2, flynn, kwb}@nd.edu
Basic Hyperspectral Analysis Tutorial
 Basic Hyperspectral Analysis Tutorial This tutorial introduces you to visualization and interactive analysis tools for working with hyperspectral data. In this tutorial, you will: Analyze spectral profiles
Basic Hyperspectral Analysis Tutorial This tutorial introduces you to visualization and interactive analysis tools for working with hyperspectral data. In this tutorial, you will: Analyze spectral profiles
Title Goes Here Algorithms for Biometric Authentication
 Title Goes Here Algorithms for Biometric Authentication February 2003 Vijayakumar Bhagavatula 1 Outline Motivation Challenges Technology: Correlation filters Example results Summary 2 Motivation Recognizing
Title Goes Here Algorithms for Biometric Authentication February 2003 Vijayakumar Bhagavatula 1 Outline Motivation Challenges Technology: Correlation filters Example results Summary 2 Motivation Recognizing
Investigations on Multi-Sensor Image System and Its Surveillance Applications
 Investigations on Multi-Sensor Image System and Its Surveillance Applications Zheng Liu DISSERTATION.COM Boca Raton Investigations on Multi-Sensor Image System and Its Surveillance Applications Copyright
Investigations on Multi-Sensor Image System and Its Surveillance Applications Zheng Liu DISSERTATION.COM Boca Raton Investigations on Multi-Sensor Image System and Its Surveillance Applications Copyright
Master sky images for the WFC3 G102 and G141 grisms
 Master sky images for the WFC3 G102 and G141 grisms M. Kümmel, H. Kuntschner, J. R. Walsh, H. Bushouse January 4, 2011 ABSTRACT We have constructed master sky images for the WFC3 near-infrared G102 and
Master sky images for the WFC3 G102 and G141 grisms M. Kümmel, H. Kuntschner, J. R. Walsh, H. Bushouse January 4, 2011 ABSTRACT We have constructed master sky images for the WFC3 near-infrared G102 and
Database of Iris Printouts and its Application: Development of Liveness Detection Method for Iris Recognition
 Database of Iris Printouts and its Application: Development of Liveness Detection Method for Iris Recognition Adam Czajka, Institute of Control and Computation Engineering Warsaw University of Technology,
Database of Iris Printouts and its Application: Development of Liveness Detection Method for Iris Recognition Adam Czajka, Institute of Control and Computation Engineering Warsaw University of Technology,
Iris Recognition using Histogram Analysis
 Iris Recognition using Histogram Analysis Robert W. Ives, Anthony J. Guidry and Delores M. Etter Electrical Engineering Department, U.S. Naval Academy Annapolis, MD 21402-5025 Abstract- Iris recognition
Iris Recognition using Histogram Analysis Robert W. Ives, Anthony J. Guidry and Delores M. Etter Electrical Engineering Department, U.S. Naval Academy Annapolis, MD 21402-5025 Abstract- Iris recognition
A. Dalrin Ampritta 1 and Dr. S.S. Ramakrishnan 2 1,2 INTRODUCTION
 Improving the Thematic Accuracy of Land Use and Land Cover Classification by Image Fusion Using Remote Sensing and Image Processing for Adapting to Climate Change A. Dalrin Ampritta 1 and Dr. S.S. Ramakrishnan
Improving the Thematic Accuracy of Land Use and Land Cover Classification by Image Fusion Using Remote Sensing and Image Processing for Adapting to Climate Change A. Dalrin Ampritta 1 and Dr. S.S. Ramakrishnan
Sensory Fusion for Image
 , pp.34-38 http://dx.doi.org/10.14257/astl.2014.45.07 Sensory Fusion for Image Sungjun Park, Wansik Yun, and Gwanggil Jeon 1 Department of Embedded Systems Engineering, Incheon National University, 119
, pp.34-38 http://dx.doi.org/10.14257/astl.2014.45.07 Sensory Fusion for Image Sungjun Park, Wansik Yun, and Gwanggil Jeon 1 Department of Embedded Systems Engineering, Incheon National University, 119
LabVIEW based Intelligent Frontal & Non- Frontal Face Recognition System
 LabVIEW based Intelligent Frontal & Non- Frontal Face Recognition System Muralindran Mariappan, Manimehala Nadarajan, and Karthigayan Muthukaruppan Abstract Face identification and tracking has taken a
LabVIEW based Intelligent Frontal & Non- Frontal Face Recognition System Muralindran Mariappan, Manimehala Nadarajan, and Karthigayan Muthukaruppan Abstract Face identification and tracking has taken a
Evaluation of FLAASH atmospheric correction. Note. Note no SAMBA/10/12. Authors. Øystein Rudjord and Øivind Due Trier
 Evaluation of FLAASH atmospheric correction Note Note no Authors SAMBA/10/12 Øystein Rudjord and Øivind Due Trier Date 16 February 2012 Norsk Regnesentral Norsk Regnesentral (Norwegian Computing Center,
Evaluation of FLAASH atmospheric correction Note Note no Authors SAMBA/10/12 Øystein Rudjord and Øivind Due Trier Date 16 February 2012 Norsk Regnesentral Norsk Regnesentral (Norwegian Computing Center,
Real-Time Face Detection and Tracking for High Resolution Smart Camera System
 Digital Image Computing Techniques and Applications Real-Time Face Detection and Tracking for High Resolution Smart Camera System Y. M. Mustafah a,b, T. Shan a, A. W. Azman a,b, A. Bigdeli a, B. C. Lovell
Digital Image Computing Techniques and Applications Real-Time Face Detection and Tracking for High Resolution Smart Camera System Y. M. Mustafah a,b, T. Shan a, A. W. Azman a,b, A. Bigdeli a, B. C. Lovell
Face Detection System on Ada boost Algorithm Using Haar Classifiers
 Vol.2, Issue.6, Nov-Dec. 2012 pp-3996-4000 ISSN: 2249-6645 Face Detection System on Ada boost Algorithm Using Haar Classifiers M. Gopi Krishna, A. Srinivasulu, Prof (Dr.) T.K.Basak 1, 2 Department of Electronics
Vol.2, Issue.6, Nov-Dec. 2012 pp-3996-4000 ISSN: 2249-6645 Face Detection System on Ada boost Algorithm Using Haar Classifiers M. Gopi Krishna, A. Srinivasulu, Prof (Dr.) T.K.Basak 1, 2 Department of Electronics
IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION
 Chapter 23 IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION Sevinc Bayram, Husrev Sencar and Nasir Memon Abstract In an earlier work [4], we proposed a technique for identifying digital camera models
Chapter 23 IDENTIFYING DIGITAL CAMERAS USING CFA INTERPOLATION Sevinc Bayram, Husrev Sencar and Nasir Memon Abstract In an earlier work [4], we proposed a technique for identifying digital camera models
Recent research results in iris biometrics
 Recent research results in iris biometrics Karen Hollingsworth, Sarah Baker, Sarah Ring Kevin W. Bowyer, and Patrick J. Flynn Computer Science and Engineering Department, University of Notre Dame, Notre
Recent research results in iris biometrics Karen Hollingsworth, Sarah Baker, Sarah Ring Kevin W. Bowyer, and Patrick J. Flynn Computer Science and Engineering Department, University of Notre Dame, Notre
A Novel Approach for MRI Image De-noising and Resolution Enhancement
 A Novel Approach for MRI Image De-noising and Resolution Enhancement 1 Pravin P. Shetti, 2 Prof. A. P. Patil 1 PG Student, 2 Assistant Professor Department of Electronics Engineering, Dr. J. J. Magdum
A Novel Approach for MRI Image De-noising and Resolution Enhancement 1 Pravin P. Shetti, 2 Prof. A. P. Patil 1 PG Student, 2 Assistant Professor Department of Electronics Engineering, Dr. J. J. Magdum
ZKTECO COLLEGE- FUNDAMENTAL OF FINGER VEIN RECOGNITION
 ZKTECO COLLEGE- FUNDAMENTAL OF FINGER VEIN RECOGNITION What are Finger Veins? Veins are blood vessels which present throughout the body as tubes that carry blood back to the heart. As its name implies,
ZKTECO COLLEGE- FUNDAMENTAL OF FINGER VEIN RECOGNITION What are Finger Veins? Veins are blood vessels which present throughout the body as tubes that carry blood back to the heart. As its name implies,
Improved SIFT Matching for Image Pairs with a Scale Difference
 Improved SIFT Matching for Image Pairs with a Scale Difference Y. Bastanlar, A. Temizel and Y. Yardımcı Informatics Institute, Middle East Technical University, Ankara, 06531, Turkey Published in IET Electronics,
Improved SIFT Matching for Image Pairs with a Scale Difference Y. Bastanlar, A. Temizel and Y. Yardımcı Informatics Institute, Middle East Technical University, Ankara, 06531, Turkey Published in IET Electronics,
For a long time I limited myself to one color as a form of discipline. Pablo Picasso. Color Image Processing
 For a long time I limited myself to one color as a form of discipline. Pablo Picasso Color Image Processing 1 Preview Motive - Color is a powerful descriptor that often simplifies object identification
For a long time I limited myself to one color as a form of discipline. Pablo Picasso Color Image Processing 1 Preview Motive - Color is a powerful descriptor that often simplifies object identification
NON UNIFORM BACKGROUND REMOVAL FOR PARTICLE ANALYSIS BASED ON MORPHOLOGICAL STRUCTURING ELEMENT:
 IJCE January-June 2012, Volume 4, Number 1 pp. 59 67 NON UNIFORM BACKGROUND REMOVAL FOR PARTICLE ANALYSIS BASED ON MORPHOLOGICAL STRUCTURING ELEMENT: A COMPARATIVE STUDY Prabhdeep Singh1 & A. K. Garg2
IJCE January-June 2012, Volume 4, Number 1 pp. 59 67 NON UNIFORM BACKGROUND REMOVAL FOR PARTICLE ANALYSIS BASED ON MORPHOLOGICAL STRUCTURING ELEMENT: A COMPARATIVE STUDY Prabhdeep Singh1 & A. K. Garg2
CHAPTER-2. Application of Video Spectral Comparator for Examination of Printed Material
 CHAPTER-2 Application of Video Spectral Comparator for Examination of Printed Material 2.1 Introduction Historically the document examiner mainly examined handwritten and typed documents. With the evolution
CHAPTER-2 Application of Video Spectral Comparator for Examination of Printed Material 2.1 Introduction Historically the document examiner mainly examined handwritten and typed documents. With the evolution
IR and Visible Light Face Recognition
 IR and Visible Light Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 USA {xchen2, flynn, kwb}@nd.edu
IR and Visible Light Face Recognition Xin Chen Patrick J. Flynn Kevin W. Bowyer Department of Computer Science and Engineering University of Notre Dame Notre Dame, IN 46556 USA {xchen2, flynn, kwb}@nd.edu
Challenges and Potential Research Areas In Biometrics
 Challenges and Potential Research Areas In Biometrics Defence Research and Development Canada Qinghan Xiao and Karim Dahel Defence R&D Canada - Ottawa October 18, 2004 Recherche et développement pour la
Challenges and Potential Research Areas In Biometrics Defence Research and Development Canada Qinghan Xiao and Karim Dahel Defence R&D Canada - Ottawa October 18, 2004 Recherche et développement pour la
Impulse Noise Removal Based on Artificial Neural Network Classification with Weighted Median Filter
 Impulse Noise Removal Based on Artificial Neural Network Classification with Weighted Median Filter Deepalakshmi R 1, Sindhuja A 2 PG Scholar, Department of Computer Science, Stella Maris College, Chennai,
Impulse Noise Removal Based on Artificial Neural Network Classification with Weighted Median Filter Deepalakshmi R 1, Sindhuja A 2 PG Scholar, Department of Computer Science, Stella Maris College, Chennai,
Face Detection using 3-D Time-of-Flight and Colour Cameras
 Face Detection using 3-D Time-of-Flight and Colour Cameras Jan Fischer, Daniel Seitz, Alexander Verl Fraunhofer IPA, Nobelstr. 12, 70597 Stuttgart, Germany Abstract This paper presents a novel method to
Face Detection using 3-D Time-of-Flight and Colour Cameras Jan Fischer, Daniel Seitz, Alexander Verl Fraunhofer IPA, Nobelstr. 12, 70597 Stuttgart, Germany Abstract This paper presents a novel method to
Comparison of ridge- and intensity-based perspiration liveness detection methods in fingerprint scanners
 Comparison of ridge- and intensity-based perspiration liveness detection methods in fingerprint scanners Bozhao Tan and Stephanie Schuckers Department of Electrical and Computer Engineering, Clarkson University,
Comparison of ridge- and intensity-based perspiration liveness detection methods in fingerprint scanners Bozhao Tan and Stephanie Schuckers Department of Electrical and Computer Engineering, Clarkson University,
Multispectral Image Restoration of Historical Document Images
 Research Manuscript Title Multispectral Image Restoration of Historical Document Images R. Kiruthika, P.G. Scholar, ME. Communication systems, Department of ECE, Sri Venkateswara College of Engineering.
Research Manuscript Title Multispectral Image Restoration of Historical Document Images R. Kiruthika, P.G. Scholar, ME. Communication systems, Department of ECE, Sri Venkateswara College of Engineering.
Wheel Health Monitoring Using Onboard Sensors
 Wheel Health Monitoring Using Onboard Sensors Brad M. Hopkins, Ph.D. Project Engineer Condition Monitoring Amsted Rail Company, Inc. 1 Agenda 1. Motivation 2. Overview of Methodology 3. Application: Wheel
Wheel Health Monitoring Using Onboard Sensors Brad M. Hopkins, Ph.D. Project Engineer Condition Monitoring Amsted Rail Company, Inc. 1 Agenda 1. Motivation 2. Overview of Methodology 3. Application: Wheel
An Un-awarely Collected Real World Face Database: The ISL-Door Face Database
 An Un-awarely Collected Real World Face Database: The ISL-Door Face Database Hazım Kemal Ekenel, Rainer Stiefelhagen Interactive Systems Labs (ISL), Universität Karlsruhe (TH), Am Fasanengarten 5, 76131
An Un-awarely Collected Real World Face Database: The ISL-Door Face Database Hazım Kemal Ekenel, Rainer Stiefelhagen Interactive Systems Labs (ISL), Universität Karlsruhe (TH), Am Fasanengarten 5, 76131
Liangliang Cao *, Jiebo Luo +, Thomas S. Huang *
 Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
Annotating ti Photo Collections by Label Propagation Liangliang Cao *, Jiebo Luo +, Thomas S. Huang * + Kodak Research Laboratories *University of Illinois at Urbana-Champaign (UIUC) ACM Multimedia 2008
Automation of Fingerprint Recognition Using OCT Fingerprint Images
 Journal of Signal and Information Processing, 2012, 3, 117-121 http://dx.doi.org/10.4236/jsip.2012.31015 Published Online February 2012 (http://www.scirp.org/journal/jsip) 117 Automation of Fingerprint
Journal of Signal and Information Processing, 2012, 3, 117-121 http://dx.doi.org/10.4236/jsip.2012.31015 Published Online February 2012 (http://www.scirp.org/journal/jsip) 117 Automation of Fingerprint
Using Fragile Bit Coincidence to Improve Iris Recognition
 Using Fragile Bit Coincidence to Improve Iris Recognition Karen P. Hollingsworth, Kevin W. Bowyer, and Patrick J. Flynn Abstract The most common iris biometric algorithm represents the texture of an iris
Using Fragile Bit Coincidence to Improve Iris Recognition Karen P. Hollingsworth, Kevin W. Bowyer, and Patrick J. Flynn Abstract The most common iris biometric algorithm represents the texture of an iris
GE 113 REMOTE SENSING
 GE 113 REMOTE SENSING Topic 8. Image Classification and Accuracy Assessment Lecturer: Engr. Jojene R. Santillan jrsantillan@carsu.edu.ph Division of Geodetic Engineering College of Engineering and Information
GE 113 REMOTE SENSING Topic 8. Image Classification and Accuracy Assessment Lecturer: Engr. Jojene R. Santillan jrsantillan@carsu.edu.ph Division of Geodetic Engineering College of Engineering and Information
arxiv: v1 [cs.cv] 25 May 2015
![arxiv: v1 [cs.cv] 25 May 2015 arxiv: v1 [cs.cv] 25 May 2015](/thumbs/77/76488281.jpg) OAGM Workshop 2015 (arxiv:1505.01065) 1 VeinPLUS: A Transillumination and Reflection-based Hand Vein Database Alexander Gruschina Department of Computer Sciences, University of Salzburg, Austria arxiv:1505.06769v1
OAGM Workshop 2015 (arxiv:1505.01065) 1 VeinPLUS: A Transillumination and Reflection-based Hand Vein Database Alexander Gruschina Department of Computer Sciences, University of Salzburg, Austria arxiv:1505.06769v1
The Role of Biometrics in Virtual Communities. and Digital Governments
 The Role of Biometrics in Virtual Communities and Digital Governments Chang-Tsun Li Department of Computer Science University of Warwick Coventry CV4 7AL UK Tel: +44 24 7657 3794 Fax: +44 24 7657 3024
The Role of Biometrics in Virtual Communities and Digital Governments Chang-Tsun Li Department of Computer Science University of Warwick Coventry CV4 7AL UK Tel: +44 24 7657 3794 Fax: +44 24 7657 3024
Compressive Optical MONTAGE Photography
 Invited Paper Compressive Optical MONTAGE Photography David J. Brady a, Michael Feldman b, Nikos Pitsianis a, J. P. Guo a, Andrew Portnoy a, Michael Fiddy c a Fitzpatrick Center, Box 90291, Pratt School
Invited Paper Compressive Optical MONTAGE Photography David J. Brady a, Michael Feldman b, Nikos Pitsianis a, J. P. Guo a, Andrew Portnoy a, Michael Fiddy c a Fitzpatrick Center, Box 90291, Pratt School
