ISSN Vol.03,Issue.02, June-2015, Pages:
|
|
|
- Martin Giles Walker
- 5 years ago
- Views:
Transcription
1 ISSN Vol.03,Issue.02, June-2015, Pages: Reliable Sensing for Crowd Management in Cloud-Centric Internet of Things MUDAVATH SOMLA NAIK 1, J. SWAMI NAIK 2 1 PG Scholar, Dept of CS, G. Pulla Reddy Engineering College(Autonomous), Kurnool, AP, India, somla3994@gmail.com. 2 Associate Professor, Dept of CSE, G. Pulla Reddy Engineering College(Autonomous), Kurnool, AP, India, swaminaikcse@gmail.com. Abstract: Modern technology is rapidly altering and enhancing all aspects of our lives. The communication sector has been improving continuously. The Cloud computing is a game changing phase of IT that promises several benefits but the challenges too need to be considered when planning for Cloud adoption. Cloud computing is aimed at providing IT as a service to the cloud users on-demand basis with greater flexibility, scalability, reliability and availability with utility computing model. Cloud computing model can enable provisioning of sensing services through mobile phones, namely Sensing-as a- Service (S 2 aas). In this paper, we study S 2 aas over socialnet working services for crowd management problem where malicious users report false sensor readings leading to severe disinformation at the crowd control platform. To this end, we propose Trustworthy Sensing for Crowd Management (TSCM)which is a reputation-based crowd management scheme over the cloud platform where sensing data is collected from smart phones based on an auction mechanism. Sensing-as-a-Service (S2aaS) is a cloud-inspired service model which enables access to the IoT. The Internet of Things (IoT) paradigm denotes the pervasive and ubiquitous interconnection of billions of embedded devices that can be uniquely identified, localized, and communicated. IoT architecture can be implemented as either Internet centric or object centric. The former aims at provisioning services within the Internet, where data are contributed by the objects whereas the latter aims at provisioning services via network of smart objects. Scalability and cost efficiency of IoT services can be achieved by the integration of cloud-computing into the IoT architecture, i.e., cloud-centric IoT. Keywords: Internet of Things (IoT), Cloud Computing, Crowd Management, Public Safety, Sensing-as-a- Service (S 2 aas), Trustworthy Sensing for Crowd Management (TSCM), Smart Phone Sensing, Social Networking. I. INTRODUCTION Internet of Things (IoT) is increasing the connectedness of things and people on a scale that was not imaginable before. The pace of adoption of IoT in market is increasing due to ubiquitous computing and increase in the connectedness of machines and people. But very few parameters exist to check and ensure the quality of IoT implemented devices and machines. The Internet of Things (IoT) represents a revolution happening now-a-days which results in increased intercommunication and autonomous machine-to-machine data transfer. But with great opportunity comes great responsibility. Along with its conveniences, the IoT unveils several security challenges: in data privacy, safety, governance and trust. Internet of Things (IoT) is technological wave in information technology after the Internet. The IoT connects every physical entity of the world with the internet for switching information and communicate with other entities. It is used to recognize, trace, follow, observe and supervise things. It extends and expands the communication between human and human, or human and machine, or machine and machine where machine can be any physical entity. IoT is achieved through RF identification (RFID) and sensor technology. The Internet of Things (IoT) paradigm stands for virtually interconnected objects that are identifiable and equipped with sensing, computing, and communication capabilities. Implementation of services and applications over the IoT architecture can take benefit of the cloud computing concept. Sensing-as-a-Service (S 2 aas) is a cloud-inspired service model which enables access to the IoT. In this paper, we present a framework where IoT can enhance public safety by crowd management via sensing services that are provided by smart phones equipped with various types of sensors. In order to ensure trustworthiness in the presented framework, we propose a reputation-based S 2 aas scheme, namely, Trustworthy Sensing for Crowd Management (TSCM) for front-end access to the IoT. TSCM collects sensing data based on a cloud model and an auction procedure which selects mobile devices for particular sensing tasks and determines the payments to the users of the mobile devices that provide data. This paper is organized as follows. In Section II, related work and motivation are presented. Section III presents the Cloud based IoT framework, Section IV presents the proposed framework, TSCM in detail. Numerical results are presented and discussed in Section V. Section VI concludes the paper and gives future directions IJIT. All rights reserved.
2 II. RELATED WORK AND MOTIVATION Cloud computing offers on demand access to a shared pool of resources such as software, infrastructure and platform with rapid elasticity based on the pay-as-you-go fashion. Furthermore, cloud computing model harmonizes well with the future Internet of services where several other resources such as CPU, storage and networks will be offered as a service [1]. Provisioning of sensing services through smart phones with in a cloud platform is called Sensing as a Service (S 2 aas). Three main requirements for any S 2 aascloud system as smart phone platform independence, energy efficiency and effective incentives for participatory sensing. In [5], the authors state the advantages of S2aaS as enabling collection, processing and sharing of big data in collaboration of large crowds as a cloud service via mobile devices which already have various built-in sensors. According to [4], introducing S2aaS to social networks would lead to a win-win situation for both systems. Today, social networks connect millions of users based on their interests, relations or features, and it is very likely to evolve to a social network connecting services and applications over the cloud. In [3], based on the requirements of the sensing objects, the authors propose deployment, development, and management of the IoT applications over the cloud, namely, the Cloud Things architecture. Applications that can be improved by the integration of IoT into cloud computing are many; such as pervasive healthcare, smart homes, smart cities, and future transportation systems. Furthermore, public safety in smart city management can be efficiently addressed by taking advantage of cloud and IoT integration. Ina cloud-centric IoT framework, sensors provide their sensed data to a storage cloud as a service, which then undergoes data analytics and data mining tools for information retrieval and knowledge discovery. Built-in sensors in mobile devices can leverage the performance of IoT applications in terms of energy and communication overhead savings. Therefore, Sensing-as-a- Service (S 2 aas) appears as a strong candidate for front-end access to the cloud-centric IoT, where mobile devices provide their sensed data based on the pay-as-you-go fashion. In this paper, we present a cloud-centric IoT-based crowd management scheme for public safety which utilizes S 2 aaswith the ultimate goal of trustworthy crowd sourcing. The proposed scheme is called Trustworthy Sensing for Crowd Management (TSCM) which has been briefly presented in with initial simulation results. As integration of S2aaSand social networks can introduce various benefits to both systems, we present the TSCM framework with the option of social network assistance. TSCM enables the public safety authority to collect sensing data in a particular region for crowd management. The term crowd refers to a large group of people who have gathered for an event. Public safety authority can use sensor data of the smart phones if effective incentives exist for the users in the event to provide their sensing data as a service. TSCM adopts the M Sensing auction-based user centric incentives that have been proposed in for a smart phonebased crowd sourcing scenario, and enhances them by introducing reputation-awareness and trustworthiness of the MUDAVATH SOMLA NAIK, J. SWAMI NAIK smart phone users. Maliciously altered sensing data aiming at disinformation at the public safety authority or inaccurate sensor readings reduce user reputation, whereas truthful and accurate sensor readings increase user trustworthiness.1 TSCM uses recent and past sensor readings of a user in order to compute his/her current trustworthiness dynamically. As TSCM runs an auction to select the users who will crowd source the required tasks, a user s bid and his/her marginal values introduced to the sensing set are redefined by the public safety authority by using the trustworthiness of the corresponding user. We show that when TSCM is adopted, the utility of the public safety authority is significantly improved by reputation-awareness, where as disinformation probability in a crowd sourced task is dramatically reduced when compared to the reputation un aware user-centric incentive approach. Furthermore, public safety authority can save 40% of the payments made to the malicious users in comparison to a reputation unaware auction. III. CLOUD BASED IOT FRAMEWORK The Cloud based IoT Framework removes fundamental constraints concerning place, time and human observations. Cloud centric IoT architecture has following layers in proposed framework, Object Management Cloud Computing Platform Information as a Service Smart Phone User Object Management: Objects have central role in SCM, objects are digital representation of information that communicated and processed via Internet. In SCM objects are information transferred between different partners from primary production to the market. These objects submits sensing task request to the cloud platform and receives sensing data of corresponding task. Cloud Computing Platform: Maintains a user database where objects, sensing tasks and associated events are stored. This middleware enables a seamless exchange of object information between different supply chain participants. Cloud centric IoT framework processes functionalities for service management and service composition. The data exchange and information integration is done by this platform. Information as a Service: This layer considered as data publisher layer in this cloud centric IoT framework for Supply Chain Management. The specific service for different supply chain user based on the object information made accessible by using web interface application. Smart Phone Users: Users at an area of interest are a subset of the crowd to be monitored and controlled by the authority. By installing the S 2 aas application on his/her smart phone, a user agrees to publish the sensing data, as well as his/her bids/payments in any sensing auction over the social media. Furthermore, installation of this application grants access to his/her published S 2 aas data to the TSCM platform. Two types of users are assumed: First type of users bid and publish truthfully whereas the second type of users maliciously end altered sensing data in order to lead to disinformation at the
3 Reliable Sensing for Crowd Management in Cloud-Centric Internet of Things crowd management authority. Furthermore, the second type of users participate the auction with lower bids and aim at winning the auction. IV. TRUSTWORTHY S 2 aas FOR CROWD MANAGEMENT (TSCM) Crowd denotes a group of people who have gathered for an event such as a sports game, a concert or a peaceful demonstration as shown in Fig.1. In all of these activities, the crowd control authorities are responsible for public safety, as well as the safety of the crowd, and they should take immediate action when needed. We propose a reputationaware and social network-based S2aaS framework for crowd management, namely Trustworthy Sensing for Crowd Management (TSCM). TSCM dynamically updates users reputation by using recent and historical data and it jointly considers users bids and their reputation while selecting the participants, as well as making payments to the participants. Fig.1. Illustration of TSCM within the S 2 aas cloud architecture. A. System Architecture The four layers of a cloud-centric IoT, correspond to four main components of TSCM as follows. Crowd Management Authority: Submits sensing task requests to the cloud platform and receives the sensing data of the corresponding tasks once the auction is completed in the cloud. Indeed, sensing task requests also include the value of each task so that the cloud platform can manage the auction by jointly considering the utility of the crowd management authority, as well as the users utility. Cloud Computing Platform: Maintains a user database, where users reputations, bids, payments, sensing tasks, and associated events are stored. Furthermore, the cloud platform interacts with social networking services in order to detect candidate users and collect sensing data. Huge amount of data will need to be stored and processed throughout an event; Hence TSCM over Hadoop Map Reduce framework can be a feasible solution for implementation. Social Networking Service: Is considered to be the sensor data publisher layer in the cloud-centric IoT for crowd management. Furthermore, social network services can cooperate with the cloud platform in retrieving the users who are present at a particular location to attend a particular event. Moreover, S2aaS data such as bids, payments, and sensing data are also published over social network, whereas the above applications enable fast detection of the smart phone users who may take part in the S2aaS auction. Smart Phone Users: Denote a subset of the crowd in a particular region, which is aimed to be monitored by the public safety authority. A user who agrees to publish his/her sensing data on the sensor data publisher layer (e.g., social network) of the IoT architecture, installs the S2aaS application on his/her smart phone. As mentioned in the motivation section, two types of users are considered in this scenario. The first type of users bid and publish their sensor data truthfully (i.e., non malicious users) whereas the second type of users bidlower than their costs in order to guarantee being selected, and publish altered sensing data in order to lead to dis-information at the public safety authority (i.e., malicious users). TSCM consists of the following steps. Step 1: Crowd management authority submits its S2aaSrequest to the cloud platform. Step 2: The cloud platform queries the users who have checked-in nearby corresponding location. Social networks respond with a list of candidate users who will join the auction. Step 3: The cloud platform updates the user database and sends the tasks to the users via corresponding social networks. Step 4: The users publish the sensing tasks in which they are interested on their social networks along with their corresponding bid values, and the social network relays the data to the cloud platform. It is worth while noting that the bid of a truthful user is equal to his/her sensing cost. Step 5: The cloud platform runs the auction. First, it queries the database to retrieve user reputations. Once the user reputations are retrieved, the cloud platform selects the winners of the auction, determines the payments and sends user-task matching information along with the payments to the users via corresponding social network services.
4 MUDAVATH SOMLA NAIK, J. SWAMI NAIK Step 6: Users publish their sensing data on their social TABLE I: Notation used in the Formulation networks, which is also visible to the cloud platform. Step 7: Upon receiving the sensing data, the cloud platform updates its user database with the newly calculated trustworthiness of the selected users. While calculating the trustworthiness of the users, the platform runs an outlier detection algorithm to detect possibly altered data so that trustworthiness of the users who have sent altered data is degraded. Step 8: The cloud platform sends the sensed data of the submitted tasks to the public safety authority. B. Auction Mechanism The auction mechanism in Steps 6 and 7 of TSCM adopts M Sensing auction in and enhances it by introducing reputation-awareness. The auction aims at selecting W winners out of P participants, and determining the payment to be made to each user i (ρi). Table 1 presents the notation used in the model. Among these terms, marginal value of user i for set W (ϑi(w)) is a key parameter of the algorithm, and it denotes the additional value added to the corresponding set by the sensing tasks of user i as shown in (1). Value of a set (ϑ(w)) denotes the total value of the tasks sensed by the users forming the corresponding set as shown in (2),where TW is the list of tasks sensed by the users in set W. Since TSCM introduces reputation-awareness to M Sensing auction, we also use the reputable marginal value (ϑi(w))of user i on set- W as formulated in (3). Reputable marginal value denotes the additional value introduced by user i to the reputable value of set W. Equation (4) formulates the reputable value of set-w which is calculated by summing the values of the tasks forming the sensing set while the value of a task is defined by its actual value scaled by the average trust worthiness of the users participating in the corresponding sensing task (4) We define the trustworthiness of a user during the period t as the ratio of the positive readings (p(t)) to the total readings. When the cloud platform detects a sensor reading as an outlier, the corresponding sensor reading is marked as a negative reading (n).equation (5) is used to calculate the overall trust worthiness of a user, where latest and previous trustworthiness contribute to the overall trustworthiness with β and α coefficients, respectively, where α + β = 1. Thus, the greater the α(β) is, the less the contribution of the latest (previous) reputation is, and vice versa. (1) (2) (3) The auction has two modes, namely, the aggressive and nonaggressive modes. We also define an adaptive mode, where TSCM dynamically switches between these two modes and adjusts α and β parameters. Payment Determination: In the payment determination phase, similar to the benchmark scheme in TSC Mensures that any user, user w, will not be paid less than his/her bid. Initially, each user is assumed to be paid zero. For each selected user, user w, the algorithm constructs a temporary set which is equal to the set of participants excluding user w. TSCM-Adaptive Mode: The adaptive mode of TSCM aims at dynamic adjustment of the impact of recent and past reputation of the user by varying α and β coefficients in trustworthiness calculation. Furthermore, in the winner selection phase (see Algorithm 1),the algorithm first selects the users whose trustworthiness values have not been degraded. This step is followed by selection of the users whose trustworthiness values have been degraded in the most recent task assignment period. To this end, TSC M adaptive mode redefines the reputable marginal value for all users as formulated in (7). Thus, if the trustworthiness of a user has not been degraded in the previous period, the reputable marginal value of the corresponding user for a given set W is set at the naive marginal value of the user for W. By naïve marginal value, we denote the calculation in (2). Otherwise, user s reputation is taken into account in order to calculate his/her reputable marginal value for W, which is defined in (4). (6) V. NUMERICAL RESULTS Performance metrics are defined as follows: Utility of the public safety authority is the difference between the total reputable value of the sensing tasks and the total payments made to the winners in the auction as formulated where τ denotes the τ th period in which the crowd management (5) authority requested a new set of tasks through the cloud platform. Average user utility is the difference between total
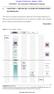
5 Reliable Sensing for Crowd Management in Cloud-Centric Internet of Things payments made to the winners and the total sensing cost of the winners. Fig. 2 illustrates the crowd management authority s utility under the reputation-aware framework, TSCM in comparison to reputation-unaware implementation of M Sense. As seen in the figure, reputation-awareness increases the utility of the platform by 12% under lightly arriving sensing task requests and by 85% under heavily arriving sensing task requests when the aggressive mode is on. The reason of this phenomenon is that the users with lower trustworthiness are less likely to be selected in the auction even though their original bids are lower than the other users. Furthermore, the improvement of the aggressive mode of TSCM over non-aggressive mode is at the order of 15%. This is an expected phenomenon since the aggressive mode determines the payments based on the reputable values of the task sets, which leads to cuts in the payments when users with lower reputation (not necessarily to be malicious) participate sensing. Fig.3. Average disinformation ratio. Besides, TSCM is robust to the intermittent disinformation (ID) strategy of the malicious users as the crowd management authority s utility is not significantly impacted when disinformation occurs intermittently rather than occurring continuously. In case of ID, the users improve their trustworthiness by publishing truthful information on their social network. Thus, even though a malicious user is selected, it will most likely publish its sensed data without any alteration. Fig. 4.Average utility of a participant. Fig.2.Utility of the crowd management authority. Fig3 illustrates the disinformation ratio (DIR) as formulated by Eq. 8 under TSCM and the benchmark scheme without reputation-awareness. The improvement under TSCM over the benchmark scheme in terms of DIR is at the order of 75%.Indeed, this is an expected phenomenon as trust worthiness based ranking of the users lower the chance of a malicious user to be selected in the auction. Besides, in case of ID, crowd management authority experiences higher DIR in comparison to the CD case. When a malicious user has the ID strategy, it aims at publishing truthful data until its trust worthiness exceeds the UP THRESHOLD. Once its trust worthiness is high enough to win the auction, it can resume publishing altered data. Therefore, DIR is higher in case of ID. Fig. 4 reports that the improvement in the utility of the public safety authority, savings in the payments to the malicious users, and improvement in DIR are at the expenses of reduction in user utility. However, when compared to the improvement ratio in other performance metrics (Figs. 1 3), the reduction in user utility is significantly low. Furthermore, when sensing task requests arrive more frequently, the degradation in user utility is as low as 2% under the non aggressive mode. Since every selected user is ensured to be paid at least his/her actual bid, slight degradation in user utility is acceptable. In Fig. 5(a), utility of the public safety authority is illustrated for TSCM-nonaggressive mode with ID. Under each load level, introducing reputation-awareness to crowd sourcing increases the platform utility as the ratio of malicious users increases. The enhancement in presence of significant amount of malicious users is more visible under heavy loads, where load denotes the sensing task request arrival rate. Fig. 5(b) illustrates the total payment to the malicious users. In compliance with the previous figure, as the amount of malicious users increases, the benefits of TSCM is more clear as reputation-awareness avoids rapid selection of malicious users in the auction.
6 Fig. 5(c) illustrates the disinformation probability under various malicious user ratios. As users with low reputation are less likely to be selected, disinformation probability can be degraded by reputation-awareness. On the other hand, since reputation-unaware sensing does not discriminate users in the auction with respect to their trustworthiness, as the amount of malicious users increase, it makes the public safety authority become more prone to disinformation. Fig 5: Performance under various malicious user ratios: (a) utility of the safety authority, (b) total payment to malicious users, and (c) DIR. MUDAVATH SOMLA NAIK, J. SWAMI NAIK V. CONCLUSION Today s smart phones offer advanced sensing and navigation capabilities which may promote cloud-inspired provisioning of sensing services, namely Sensing-as-a- Service (S 2 aas). We have proposed a reputation-based framework for a cloud centric IoT architecture with the aim of crowd management, namely, TSCM. In TSCM, the cloud platform confirms the presence of the participants who are willing to collaborate with the public safety authority by publishing their sensing data and bids over their social networks. According to TSCM, the cloud platform confirms the presence of the participants who are willing to collaborate with the crowd management authority by publishing their sensing data and bid over their social networks. Sensing tasks are assigned to the users based on an auction run over a cloud computing platform for TSCM which interacts with the crowd management authority, social networking service and the users. TSCM mainly aims at preventing disinformation caused by maliciously altered sensing data and improving the crowd management authority s utility. We have evaluated TSCM through simulations and shown that utility of the crowd management authority can be improved significantly while disinformation ratio can be degraded by 75%. Another important research finding is that the income of the malicious users who aim at disinformation at the crowd management authority can be degraded by 40%.Early warning systems can utilize S 2 aas to assist disaster management. Malicious groups may also use crowd sourcing to mislead the emergency forces by injecting specious information into crowd sourced data. TSCM can also be adapted to such scenarios to increase community resilience against a crisis. Furthermore, integration of other trust derivation models into TSCM can also enhance its efficiency. VI. REFERENCES [1] BurakKantarci and Hussein T. Mouftah, Trustworthy Sensing for Public Safetyin Cloud-Centric Internet of Things,IEEE Internet of Things Journal, Vol. 1, No. 4, August [2] BurakKantarciand Hussein T.Mouftah, Fellow, Reputation-based Sensing-as-a-Service for Crowd Management Over the Cloud, IEEE ICC Selected Areas in Communications Symposium [3] R. Moreno-Vozmediano, R.S. Montero, and I.M. Llorente, Key challengesin cloud computing: Enabling the future internet of services, IEEE Internet Computing, vol. 17, no. 4, pp , Jul./Aug [4] X. Sheng, X. Xiao, J. Tang, and G. Xue, Sensing as a service: A cloudcomputing system for mobile phone sensing, in IEEE Sensors, Oct.2012, pp [5] S. Distefano, G. Merlino, and A. Puliafito, Sensing and actuation as aservice: A new development for clouds, in 11th IEEE Intl. Symp. OnNetwork Computing and Applications (NCA), 2012, pp [6] X. Sheng, J. Tang, X. Xiao, and G. Xue, Sensing as a service:challenges, solutions and future directions, IEEE Sensors Journal, vol. 13/10, pp , Oct [7] B.B.P. Rao, P. Saluia, N. Sharma, A. Mittal, and S.V. Sharma, Cloudcomputing for Internet of Things and sensing based applications, insixth Intl. Conf. on Sensing Technology (ICST), Dec. 2012, pp
7 Reliable Sensing for Crowd Management in Cloud-Centric Internet of Things [8] W. Tan, M. B. Blake, I. Saleh, and S. Dustdar, Socialnetwork-sourcedbig data analytics, IEEE Internet Computing, vol. 17/5, pp , [9] C. Aggarwal, N. Ashish, and A. Sheth, The Internet of Things: Asurvey from the data-centric perspective, in Managing and MiningSensor Data, C. C. Aggarwal, Ed. New York, NY, USA: Springer, 2013,pp [10] J. Gubbi, R. Buyya, S. Marusic, and M. Palaniswami, Internet of Thing(IoT): A vision, architectural elements, and future directions, FutureGenerat. Comput.Syst., vol. 29, no. 7, pp , Author s Profile:. Mr. M SomlaNaikhas completed B.Tech in Computer Science and Engineering from Y.S.R Engg College of YVU, Proddatur, Kadapa (Dist), AP, in the year Presently he is pursuing him M. Tech from G. Pulla Reddy Engineering College (Autonomous), affiliated to JNTUA, A.P, India. Mr. J Swami Naik, Obtained his B.Tech degree from G. Pulla Reddy Engineering College, Kurnool. He obtained M.Tech from IIT, Guwahati. He is presently working as Associate Professor in the Department of Computer Science and Engineering at G. Pulla Reddy Engineering College (Autonomous), Kurnool, Andhra Pradesh, India.He has got 10 years of teaching experience. His main research interest includes Cloud Computing.
Game-Theoretic Recruitment of Sensing Service Providers for Trustworthy Cloud-Centric Internet-of-Things (IoT) Applications
 Game-Theoretic Recruitment of Sensing Service Providers for Trustworthy Cloud-Centric Internet-of-Things (IoT) Applications Maryam Pouryazdan, Claudio Fiandrino, Burak Kantarci ±, Dzmitry Kliazovich, Tolga
Game-Theoretic Recruitment of Sensing Service Providers for Trustworthy Cloud-Centric Internet-of-Things (IoT) Applications Maryam Pouryazdan, Claudio Fiandrino, Burak Kantarci ±, Dzmitry Kliazovich, Tolga
A Survey on Smart City using IoT (Internet of Things)
 A Survey on Smart City using IoT (Internet of Things) Akshay Kadam 1, Vineet Ovhal 2, Anita Paradhi 3, Kunal Dhage 4 U.G. Student, Department of Computer Engineering, SKNCOE, Pune, Maharashtra, India 1234
A Survey on Smart City using IoT (Internet of Things) Akshay Kadam 1, Vineet Ovhal 2, Anita Paradhi 3, Kunal Dhage 4 U.G. Student, Department of Computer Engineering, SKNCOE, Pune, Maharashtra, India 1234
The Internet: The New Industrial Revolution
 The Internet: The New Industrial Revolution China expects to combine its industrial and Internet advantages to pioneer a new industrial revolution, keep up with global trends, and fully realize its competitive
The Internet: The New Industrial Revolution China expects to combine its industrial and Internet advantages to pioneer a new industrial revolution, keep up with global trends, and fully realize its competitive
A Profile-based Trust Management Scheme for Ubiquitous Healthcare Environment
 A -based Management Scheme for Ubiquitous Healthcare Environment Georgia Athanasiou, Georgios Mantas, Member, IEEE, Maria-Anna Fengou, Dimitrios Lymberopoulos, Member, IEEE Abstract Ubiquitous Healthcare
A -based Management Scheme for Ubiquitous Healthcare Environment Georgia Athanasiou, Georgios Mantas, Member, IEEE, Maria-Anna Fengou, Dimitrios Lymberopoulos, Member, IEEE Abstract Ubiquitous Healthcare
MSc(CompSc) List of courses offered in
 Office of the MSc Programme in Computer Science Department of Computer Science The University of Hong Kong Pokfulam Road, Hong Kong. Tel: (+852) 3917 1828 Fax: (+852) 2547 4442 Email: msccs@cs.hku.hk (The
Office of the MSc Programme in Computer Science Department of Computer Science The University of Hong Kong Pokfulam Road, Hong Kong. Tel: (+852) 3917 1828 Fax: (+852) 2547 4442 Email: msccs@cs.hku.hk (The
Mobile Crowdsensing enabled IoT frameworks: harnessing the power and wisdom of the crowd
 Mobile Crowdsensing enabled IoT frameworks: harnessing the power and wisdom of the crowd Malamati Louta Konstantina Banti University of Western Macedonia OUTLINE Internet of Things Mobile Crowd Sensing
Mobile Crowdsensing enabled IoT frameworks: harnessing the power and wisdom of the crowd Malamati Louta Konstantina Banti University of Western Macedonia OUTLINE Internet of Things Mobile Crowd Sensing
Performance Analysis of Cognitive Radio based on Cooperative Spectrum Sensing
 Performance Analysis of Cognitive Radio based on Cooperative Spectrum Sensing Sai kiran pudi 1, T. Syama Sundara 2, Dr. Nimmagadda Padmaja 3 Department of Electronics and Communication Engineering, Sree
Performance Analysis of Cognitive Radio based on Cooperative Spectrum Sensing Sai kiran pudi 1, T. Syama Sundara 2, Dr. Nimmagadda Padmaja 3 Department of Electronics and Communication Engineering, Sree
[Kumar, 5(12): December2018] ISSN DOI /zenodo Impact Factor
![[Kumar, 5(12): December2018] ISSN DOI /zenodo Impact Factor [Kumar, 5(12): December2018] ISSN DOI /zenodo Impact Factor](/thumbs/92/108178704.jpg) GLOBAL JOURNAL OF ENGINEERING SCIENCE AND RESEARCHES IOT BASED TRACKING AND MONITORING SYSTEM FOR SCHOOL CHILDREN SAFETY D. Lokesh Sai Kumar *1, B. Vishnu Vardhan 2 & A. Yuva Krishna 3 *1,2&3 Asst. Professor,
GLOBAL JOURNAL OF ENGINEERING SCIENCE AND RESEARCHES IOT BASED TRACKING AND MONITORING SYSTEM FOR SCHOOL CHILDREN SAFETY D. Lokesh Sai Kumar *1, B. Vishnu Vardhan 2 & A. Yuva Krishna 3 *1,2&3 Asst. Professor,
I. INTRODUCTION II. LITERATURE SURVEY. International Journal of Advanced Networking & Applications (IJANA) ISSN:
 A Friend Recommendation System based on Similarity Metric and Social Graphs Rashmi. J, Dr. Asha. T Department of Computer Science Bangalore Institute of Technology, Bangalore, Karnataka, India rash003.j@gmail.com,
A Friend Recommendation System based on Similarity Metric and Social Graphs Rashmi. J, Dr. Asha. T Department of Computer Science Bangalore Institute of Technology, Bangalore, Karnataka, India rash003.j@gmail.com,
SPTF: Smart Photo-Tagging Framework on Smart Phones
 , pp.123-132 http://dx.doi.org/10.14257/ijmue.2014.9.9.14 SPTF: Smart Photo-Tagging Framework on Smart Phones Hao Xu 1 and Hong-Ning Dai 2* and Walter Hon-Wai Lau 2 1 School of Computer Science and Engineering,
, pp.123-132 http://dx.doi.org/10.14257/ijmue.2014.9.9.14 SPTF: Smart Photo-Tagging Framework on Smart Phones Hao Xu 1 and Hong-Ning Dai 2* and Walter Hon-Wai Lau 2 1 School of Computer Science and Engineering,
Knowledge-based Reconfiguration of Driving Styles for Intelligent Transport Systems
 Knowledge-based Reconfiguration of Driving Styles for Intelligent Transport Systems Lecturer, Informatics and Telematics department Harokopion University of Athens GREECE e-mail: gdimitra@hua.gr International
Knowledge-based Reconfiguration of Driving Styles for Intelligent Transport Systems Lecturer, Informatics and Telematics department Harokopion University of Athens GREECE e-mail: gdimitra@hua.gr International
Executive Summary Industry s Responsibility in Promoting Responsible Development and Use:
 Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
Executive Summary Artificial Intelligence (AI) is a suite of technologies capable of learning, reasoning, adapting, and performing tasks in ways inspired by the human mind. With access to data and the
GTU BOARD for MOBILE COMPUTING and WIRELESS TECHNOLOGIES. Mobile Computing, Networking and Applications (MNA).
 TO ALL FACULTY MEMBER: Research is an important part of the Learning System in any institution of Higher Learning. Since last year, the University has been working with the faculty to upgrade our Learning
TO ALL FACULTY MEMBER: Research is an important part of the Learning System in any institution of Higher Learning. Since last year, the University has been working with the faculty to upgrade our Learning
ISSN Vol.04,Issue.16, October-2016, Pages:
 WWW.IJITECH.ORG ISSN 2321-8665 Vol.04,Issue.16, October-2016, Pages:3000-3006 Active Control for Power Quality Improvement in Hybrid Power Systems VINUTHAS 1, DHANA DEEPIKA. B 2, S. RAJESH 3 1 PG Scholar,
WWW.IJITECH.ORG ISSN 2321-8665 Vol.04,Issue.16, October-2016, Pages:3000-3006 Active Control for Power Quality Improvement in Hybrid Power Systems VINUTHAS 1, DHANA DEEPIKA. B 2, S. RAJESH 3 1 PG Scholar,
Framework Programme 7
 Framework Programme 7 1 Joining the EU programmes as a Belarusian 1. Introduction to the Framework Programme 7 2. Focus on evaluation issues + exercise 3. Strategies for Belarusian organisations + exercise
Framework Programme 7 1 Joining the EU programmes as a Belarusian 1. Introduction to the Framework Programme 7 2. Focus on evaluation issues + exercise 3. Strategies for Belarusian organisations + exercise
Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes
 7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
7th Mediterranean Conference on Control & Automation Makedonia Palace, Thessaloniki, Greece June 4-6, 009 Distributed Collaborative Path Planning in Sensor Networks with Multiple Mobile Sensor Nodes Theofanis
Pervasive Services Engineering for SOAs
 Pervasive Services Engineering for SOAs Dhaminda Abeywickrama (supervised by Sita Ramakrishnan) Clayton School of Information Technology, Monash University, Australia dhaminda.abeywickrama@infotech.monash.edu.au
Pervasive Services Engineering for SOAs Dhaminda Abeywickrama (supervised by Sita Ramakrishnan) Clayton School of Information Technology, Monash University, Australia dhaminda.abeywickrama@infotech.monash.edu.au
Pan-Canadian Trust Framework Overview
 Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
Pan-Canadian Trust Framework Overview A collaborative approach to developing a Pan- Canadian Trust Framework Authors: DIACC Trust Framework Expert Committee August 2016 Abstract: The purpose of this document
LOCALIZATION AND ROUTING AGAINST JAMMERS IN WIRELESS NETWORKS
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 5, May 2015, pg.955
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 5, May 2015, pg.955
Perspectives of development of satellite constellations for EO and connectivity
 Perspectives of development of satellite constellations for EO and connectivity Gianluca Palermo Sapienza - Università di Roma Paolo Gaudenzi Sapienza - Università di Roma Introduction - Interest in LEO
Perspectives of development of satellite constellations for EO and connectivity Gianluca Palermo Sapienza - Università di Roma Paolo Gaudenzi Sapienza - Università di Roma Introduction - Interest in LEO
An Overview of SMARTCITY Model Using IOT
 An Overview of SMARTCITY Model Using IOT Princi Jain, Mr.Ashendra Kumar Saxena Student, Teerthanker Mahaveer University, CCSIT, Moradabad Assistant Professor, Teerthanker Mahaveer University, CCSIT, Moradabad
An Overview of SMARTCITY Model Using IOT Princi Jain, Mr.Ashendra Kumar Saxena Student, Teerthanker Mahaveer University, CCSIT, Moradabad Assistant Professor, Teerthanker Mahaveer University, CCSIT, Moradabad
Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration
 Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration Research Supervisor: Minoru Etoh (Professor, Open and Transdisciplinary Research Initiatives, Osaka University)
Development and Integration of Artificial Intelligence Technologies for Innovation Acceleration Research Supervisor: Minoru Etoh (Professor, Open and Transdisciplinary Research Initiatives, Osaka University)
Wi-Fi Fingerprinting through Active Learning using Smartphones
 Wi-Fi Fingerprinting through Active Learning using Smartphones Le T. Nguyen Carnegie Mellon University Moffet Field, CA, USA le.nguyen@sv.cmu.edu Joy Zhang Carnegie Mellon University Moffet Field, CA,
Wi-Fi Fingerprinting through Active Learning using Smartphones Le T. Nguyen Carnegie Mellon University Moffet Field, CA, USA le.nguyen@sv.cmu.edu Joy Zhang Carnegie Mellon University Moffet Field, CA,
Innovation Report: The Manufacturing World Will Change Dramatically in the Next 5 Years: Here s How. mic-tec.com
 Innovation Report: The Manufacturing World Will Change Dramatically in the Next 5 Years: Here s How mic-tec.com Innovation Study 02 The Manufacturing World - The Next 5 Years Contents Part I Part II Part
Innovation Report: The Manufacturing World Will Change Dramatically in the Next 5 Years: Here s How mic-tec.com Innovation Study 02 The Manufacturing World - The Next 5 Years Contents Part I Part II Part
Metrology in the Digital Transformation
 Metrology in the Digital Transformation This project proposal is about to establish a European metrology data infrastructure, a European Metrology Cloud to support the processes of conformity assessment
Metrology in the Digital Transformation This project proposal is about to establish a European metrology data infrastructure, a European Metrology Cloud to support the processes of conformity assessment
The Citizen View of Government Digital Transformation 2017 Findings
 WHITE PAPER The Citizen View of Government Digital Transformation 2017 Findings Delivering Transformation. Together. Shining a light on digital public services Digital technologies are fundamentally changing
WHITE PAPER The Citizen View of Government Digital Transformation 2017 Findings Delivering Transformation. Together. Shining a light on digital public services Digital technologies are fundamentally changing
The Role of the Internet of Things in the Development of Smart Cities- Peter Knight PhD.
 The Role of the Internet of Things in the Development of Smart Cities- Peter Knight PhD. Why me? Ecommerce Researcher/Course Developer for 7 years prior to coming to Parkside Completed my PhD in the greater
The Role of the Internet of Things in the Development of Smart Cities- Peter Knight PhD. Why me? Ecommerce Researcher/Course Developer for 7 years prior to coming to Parkside Completed my PhD in the greater
AGENTS AND AGREEMENT TECHNOLOGIES: THE NEXT GENERATION OF DISTRIBUTED SYSTEMS
 AGENTS AND AGREEMENT TECHNOLOGIES: THE NEXT GENERATION OF DISTRIBUTED SYSTEMS Vicent J. Botti Navarro Grupo de Tecnología Informática- Inteligencia Artificial Departamento de Sistemas Informáticos y Computación
AGENTS AND AGREEMENT TECHNOLOGIES: THE NEXT GENERATION OF DISTRIBUTED SYSTEMS Vicent J. Botti Navarro Grupo de Tecnología Informática- Inteligencia Artificial Departamento de Sistemas Informáticos y Computación
Copyright: Conference website: Date deposited:
 Coleman M, Ferguson A, Hanson G, Blythe PT. Deriving transport benefits from Big Data and the Internet of Things in Smart Cities. In: 12th Intelligent Transport Systems European Congress 2017. 2017, Strasbourg,
Coleman M, Ferguson A, Hanson G, Blythe PT. Deriving transport benefits from Big Data and the Internet of Things in Smart Cities. In: 12th Intelligent Transport Systems European Congress 2017. 2017, Strasbourg,
Assessment of Smart Machines and Manufacturing Competence Centre (SMACC) Scientific Advisory Board Site Visit April 2018.
 Assessment of Smart Machines and Manufacturing Competence Centre (SMACC) Scientific Advisory Board Site Visit 25-27 April 2018 Assessment Report 1. Scientific ambition, quality and impact Rating: 3.5 The
Assessment of Smart Machines and Manufacturing Competence Centre (SMACC) Scientific Advisory Board Site Visit 25-27 April 2018 Assessment Report 1. Scientific ambition, quality and impact Rating: 3.5 The
Our Corporate Strategy Digital
 Our Corporate Strategy Digital Proposed Content for Discussion 9 May 2016 CLASSIFIED IN CONFIDENCE INLAND REVENUE HIGHLY PROTECTED Draft v0.2a 1 Digital: Executive Summary What is our strategic digital
Our Corporate Strategy Digital Proposed Content for Discussion 9 May 2016 CLASSIFIED IN CONFIDENCE INLAND REVENUE HIGHLY PROTECTED Draft v0.2a 1 Digital: Executive Summary What is our strategic digital
Internet of Things Paradigms as Enablers of Ambient Assisted Living Systems
 International Journal of Automation, Control and Intelligent Systems Vol. 4, No. 4, 2018, pp. 27-32 http://www.aiscience.org/journal/ijacis ISSN: 2381-7526 (Print); ISSN: 2381-7534 (Online) Internet of
International Journal of Automation, Control and Intelligent Systems Vol. 4, No. 4, 2018, pp. 27-32 http://www.aiscience.org/journal/ijacis ISSN: 2381-7526 (Print); ISSN: 2381-7534 (Online) Internet of
Volume 5, Issue 3, March 2017 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) e-isjn: A4372-3114 Impact Factor: 6.047 Volume 5, Issue 3, March 2017 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey
ISSN: 2321-7782 (Online) e-isjn: A4372-3114 Impact Factor: 6.047 Volume 5, Issue 3, March 2017 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey
Durham Research Online
 Durham Research Online Deposited in DRO: 29 August 2017 Version of attached le: Accepted Version Peer-review status of attached le: Not peer-reviewed Citation for published item: Chiu, Wei-Yu and Sun,
Durham Research Online Deposited in DRO: 29 August 2017 Version of attached le: Accepted Version Peer-review status of attached le: Not peer-reviewed Citation for published item: Chiu, Wei-Yu and Sun,
International Journal of Research
 IOT based Smart Grid to remotely monitor and control Renewable Energy Sources 1. MOHAMED AFZAL, 2. MR. N. KARTHEEK 1PG Scholar, Department of ECE, SVS INSTITUTE OF TECHNOLOGY (Approved by AICTE, New Delhi
IOT based Smart Grid to remotely monitor and control Renewable Energy Sources 1. MOHAMED AFZAL, 2. MR. N. KARTHEEK 1PG Scholar, Department of ECE, SVS INSTITUTE OF TECHNOLOGY (Approved by AICTE, New Delhi
Retrieval of Large Scale Images and Camera Identification via Random Projections
 Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
Retrieval of Large Scale Images and Camera Identification via Random Projections Renuka S. Deshpande ME Student, Department of Computer Science Engineering, G H Raisoni Institute of Engineering and Management
AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS)
 AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS) 1.3 NA-14-0267-0019-1.3 Document Information Document Title: Document Version: 1.3 Current Date: 2016-05-18 Print Date: 2016-05-18 Document
AN0503 Using swarm bee LE for Collision Avoidance Systems (CAS) 1.3 NA-14-0267-0019-1.3 Document Information Document Title: Document Version: 1.3 Current Date: 2016-05-18 Print Date: 2016-05-18 Document
Our position. ICDPPC declaration on ethics and data protection in artificial intelligence
 ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
ICDPPC declaration on ethics and data protection in artificial intelligence AmCham EU speaks for American companies committed to Europe on trade, investment and competitiveness issues. It aims to ensure
Emerging Transportation Technology Strategic Plan for the St. Louis Region Project Summary June 28, 2017
 Emerging Transportation Technology Strategic Plan for the St. Louis Region Project Summary June 28, 2017 Prepared for: East West Gateway Council of Governments Background. Motivation Process to Create
Emerging Transportation Technology Strategic Plan for the St. Louis Region Project Summary June 28, 2017 Prepared for: East West Gateway Council of Governments Background. Motivation Process to Create
UCS-805 MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2011
 Location Management for Mobile Cellular Systems SLIDE #3 UCS-805 MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com
Location Management for Mobile Cellular Systems SLIDE #3 UCS-805 MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com
ISSN Vol.05,Issue.07, July-2017, Pages:
 WWW.IJITECH.ORG ISSN 2321-8665 Vol.05,Issue.07, July-2017, Pages:1240-1245 Fuzzy Logic Control of Single-Phase PV Cascaded H-Bridge Multilevel Grid Connected Inverter A. YAMINI 1, K. RAMA MOHAN REDDY 2,
WWW.IJITECH.ORG ISSN 2321-8665 Vol.05,Issue.07, July-2017, Pages:1240-1245 Fuzzy Logic Control of Single-Phase PV Cascaded H-Bridge Multilevel Grid Connected Inverter A. YAMINI 1, K. RAMA MOHAN REDDY 2,
Digital Transformation. A Game Changer. How Does the Digital Transformation Affect Informatics as a Scientific Discipline?
 Digital Transformation A Game Changer How Does the Digital Transformation Affect Informatics as a Scientific Discipline? Manfred Broy Technische Universität München Institut for Informatics ... the change
Digital Transformation A Game Changer How Does the Digital Transformation Affect Informatics as a Scientific Discipline? Manfred Broy Technische Universität München Institut for Informatics ... the change
Incentive Mechanisms for Device-to-Device Communications
 Incentive Mechanisms for Device-to-Device Communications Peng Li and Song Guo Abstract DD communication has recently been proposed as a promising technique to improve resource utilization of cellular networks
Incentive Mechanisms for Device-to-Device Communications Peng Li and Song Guo Abstract DD communication has recently been proposed as a promising technique to improve resource utilization of cellular networks
NEM Strategic Research and Innovation Agenda 2018 NEM General Assembly, 30 May 2017
 NEM Strategic Research and Innovation Agenda 2018 NEM General Assembly, 30 May 2017 pierreyves.danet@orange.com 1 SRIA 2018 development timeline and FP9 (Horizon Europe) Hub4NGI, Engineroom, SpeakNGI,
NEM Strategic Research and Innovation Agenda 2018 NEM General Assembly, 30 May 2017 pierreyves.danet@orange.com 1 SRIA 2018 development timeline and FP9 (Horizon Europe) Hub4NGI, Engineroom, SpeakNGI,
Privacy, Technology and Economics in the 5G Environment
 Privacy, Technology and Economics in the 5G Environment S A M A N T K H A J U R I A A S S I S T P R O F E S S O R, C M I K N U D E R I K S K O U B Y P R O F E S S O R, D I R E C T O R C M I S K O U B Y
Privacy, Technology and Economics in the 5G Environment S A M A N T K H A J U R I A A S S I S T P R O F E S S O R, C M I K N U D E R I K S K O U B Y P R O F E S S O R, D I R E C T O R C M I S K O U B Y
Introduction. digitalsupercluster.ca
 Introduction digitalsupercluster.ca Government of Canada s Innovation Supercluster Initiative Federal government investing $950MM into superclusters to drive growth, prosperity, jobs and global leadership.
Introduction digitalsupercluster.ca Government of Canada s Innovation Supercluster Initiative Federal government investing $950MM into superclusters to drive growth, prosperity, jobs and global leadership.
Сonceptual framework and toolbox for digital transformation of industry of the Eurasian Economic Union
 Сonceptual framework and toolbox for digital transformation of industry of the Eurasian Economic Union Dmitry Krupsky Head of Department of Economy of Innovation Activity, Ministry of Economy of the Republic
Сonceptual framework and toolbox for digital transformation of industry of the Eurasian Economic Union Dmitry Krupsky Head of Department of Economy of Innovation Activity, Ministry of Economy of the Republic
TECHNICAL AND OPERATIONAL NOTE ON CHANGE MANAGEMENT OF GAMBLING TECHNICAL SYSTEMS AND APPROVAL OF THE SUBSTANTIAL CHANGES TO CRITICAL COMPONENTS.
 TECHNICAL AND OPERATIONAL NOTE ON CHANGE MANAGEMENT OF GAMBLING TECHNICAL SYSTEMS AND APPROVAL OF THE SUBSTANTIAL CHANGES TO CRITICAL COMPONENTS. 1. Document objective This note presents a help guide for
TECHNICAL AND OPERATIONAL NOTE ON CHANGE MANAGEMENT OF GAMBLING TECHNICAL SYSTEMS AND APPROVAL OF THE SUBSTANTIAL CHANGES TO CRITICAL COMPONENTS. 1. Document objective This note presents a help guide for
PROGRAM CONCEPT NOTE Theme: Identity Ecosystems for Service Delivery
 PROGRAM CONCEPT NOTE Theme: Identity Ecosystems for Service Delivery Program Structure for the 2019 ANNUAL MEETING DAY 1 PS0 8:30-9:30 Opening Ceremony Opening Ceremony & Plenaries N0 9:30-10:30 OPENING
PROGRAM CONCEPT NOTE Theme: Identity Ecosystems for Service Delivery Program Structure for the 2019 ANNUAL MEETING DAY 1 PS0 8:30-9:30 Opening Ceremony Opening Ceremony & Plenaries N0 9:30-10:30 OPENING
PAPR Reduction in SLM Scheme using Exhaustive Search Method
 Available online www.ejaet.com European Journal of Advances in Engineering and Technology, 2017, 4(10): 739-743 Research Article ISSN: 2394-658X PAPR Reduction in SLM Scheme using Exhaustive Search Method
Available online www.ejaet.com European Journal of Advances in Engineering and Technology, 2017, 4(10): 739-743 Research Article ISSN: 2394-658X PAPR Reduction in SLM Scheme using Exhaustive Search Method
Implementation of Optimized Proportionate Adaptive Algorithm for Acoustic Echo Cancellation in Speech Signals
 International Journal of Electronics Engineering Research. ISSN 0975-6450 Volume 9, Number 6 (2017) pp. 823-830 Research India Publications http://www.ripublication.com Implementation of Optimized Proportionate
International Journal of Electronics Engineering Research. ISSN 0975-6450 Volume 9, Number 6 (2017) pp. 823-830 Research India Publications http://www.ripublication.com Implementation of Optimized Proportionate
ANALYSIS OF BER DEGRADATION FOR TRANSMITTED DOWNLINK DSCDMA SIGNALS
 David Solomon Raju Y et al, Int. J. Comp. Tech. Appl., Vol 2 (6), 2085-2090 ANALYSIS OF BER DEGRADATION FOR TRANSMITTED DOWNLINK DSCDMA SIGNALS Ashok Ch 1, Murali Mohan K V 2 David Solomon Raju Y 3 1*
David Solomon Raju Y et al, Int. J. Comp. Tech. Appl., Vol 2 (6), 2085-2090 ANALYSIS OF BER DEGRADATION FOR TRANSMITTED DOWNLINK DSCDMA SIGNALS Ashok Ch 1, Murali Mohan K V 2 David Solomon Raju Y 3 1*
MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012
 Location Management for Mobile Cellular Systems MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Cellular System
Location Management for Mobile Cellular Systems MOBILE COMPUTING NIT Agartala, Dept of CSE Jan-May,2012 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Cellular System
RBI Working Group report on FinTech: Key themes
 www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
www.pwc.in RBI Working Group report on FinTech: Key themes April 2018 Ten key themes: 1 2 3 4 5 6 7 8 9 10 Need for deeper understanding of Fintech and inherent risks Regulatory supervision, realignment
SMARTPHONE SENSOR BASED GESTURE RECOGNITION LIBRARY
 SMARTPHONE SENSOR BASED GESTURE RECOGNITION LIBRARY Sidhesh Badrinarayan 1, Saurabh Abhale 2 1,2 Department of Information Technology, Pune Institute of Computer Technology, Pune, India ABSTRACT: Gestures
SMARTPHONE SENSOR BASED GESTURE RECOGNITION LIBRARY Sidhesh Badrinarayan 1, Saurabh Abhale 2 1,2 Department of Information Technology, Pune Institute of Computer Technology, Pune, India ABSTRACT: Gestures
IEEE IoT Vertical and Topical Summit - Anchorage September 18th-20th, 2017 Anchorage, Alaska. Call for Participation and Proposals
 IEEE IoT Vertical and Topical Summit - Anchorage September 18th-20th, 2017 Anchorage, Alaska Call for Participation and Proposals With its dispersed population, cultural diversity, vast area, varied geography,
IEEE IoT Vertical and Topical Summit - Anchorage September 18th-20th, 2017 Anchorage, Alaska Call for Participation and Proposals With its dispersed population, cultural diversity, vast area, varied geography,
ICT : Internet of Things and Platforms for Connected Smart Objects
 LEIT ICT WP2014-15 ICT 30 2015: Internet of Things and Platforms for Connected Smart Objects Peter Friess (peter.friess@ec.europa.eu), Network Technologies Werner Steinhoegl (werner.steinhoegl@ec.europa.eu),
LEIT ICT WP2014-15 ICT 30 2015: Internet of Things and Platforms for Connected Smart Objects Peter Friess (peter.friess@ec.europa.eu), Network Technologies Werner Steinhoegl (werner.steinhoegl@ec.europa.eu),
Abstract. Keywords: virtual worlds; robots; robotics; standards; communication and interaction.
 On the Creation of Standards for Interaction Between Robots and Virtual Worlds By Alex Juarez, Christoph Bartneck and Lou Feijs Eindhoven University of Technology Abstract Research on virtual worlds and
On the Creation of Standards for Interaction Between Robots and Virtual Worlds By Alex Juarez, Christoph Bartneck and Lou Feijs Eindhoven University of Technology Abstract Research on virtual worlds and
2. CHAPTER 2: THE SOCIAL NATURE OF INFORMATION TECHNOLOGY
 2. CHAPTER 2: THE SOCIAL NATURE OF INFORMATION TECHNOLOGY The discovery of truth is prevented more effectively not by the false appearance of things present and which mislead into error, not directly by
2. CHAPTER 2: THE SOCIAL NATURE OF INFORMATION TECHNOLOGY The discovery of truth is prevented more effectively not by the false appearance of things present and which mislead into error, not directly by
CS 621 Mobile Computing
 Lecture 11 CS 621 Mobile Computing Location Management for Mobile Cellular Systems Zubin Bhuyan, Department of CSE, Tezpur University http://www.tezu.ernet.in/~zubin Several slides and images in this presentation
Lecture 11 CS 621 Mobile Computing Location Management for Mobile Cellular Systems Zubin Bhuyan, Department of CSE, Tezpur University http://www.tezu.ernet.in/~zubin Several slides and images in this presentation
Image Extraction using Image Mining Technique
 IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 9 (September. 2013), V2 PP 36-42 Image Extraction using Image Mining Technique Prof. Samir Kumar Bandyopadhyay,
The Study on the Architecture of Public knowledge Service Platform Based on Collaborative Innovation
 The Study on the Architecture of Public knowledge Service Platform Based on Chang ping Hu, Min Zhang, Fei Xiang Center for the Studies of Information Resources of Wuhan University, Wuhan,430072,China,
The Study on the Architecture of Public knowledge Service Platform Based on Chang ping Hu, Min Zhang, Fei Xiang Center for the Studies of Information Resources of Wuhan University, Wuhan,430072,China,
Foreword The Internet of Things Threats and Opportunities of Improved Visibility
 Foreword The Internet of Things Threats and Opportunities of Improved Visibility The Internet has changed our business and private lives in the past years and continues to do so. The Web 2.0, social networks
Foreword The Internet of Things Threats and Opportunities of Improved Visibility The Internet has changed our business and private lives in the past years and continues to do so. The Web 2.0, social networks
Distributed Power Control in Cellular and Wireless Networks - A Comparative Study
 Distributed Power Control in Cellular and Wireless Networks - A Comparative Study Vijay Raman, ECE, UIUC 1 Why power control? Interference in communication systems restrains system capacity In cellular
Distributed Power Control in Cellular and Wireless Networks - A Comparative Study Vijay Raman, ECE, UIUC 1 Why power control? Interference in communication systems restrains system capacity In cellular
PROGRESS IN BUSINESS MODEL TRANSFORMATION
 PROGRESS IN BUSINESS MODEL TRANSFORMATION PART 1 CREATING VALUE The Fujitsu Group, striving to create new value in the Internet of Things (IoT) era, is working to realign its business structure toward
PROGRESS IN BUSINESS MODEL TRANSFORMATION PART 1 CREATING VALUE The Fujitsu Group, striving to create new value in the Internet of Things (IoT) era, is working to realign its business structure toward
SMS Based Kids Tracking and Safety System by Using RFID and GSM
 SMS Based Kids Tracking and Safety System by Using RFID and GSM Nitin Shyam1 (nitinshyam109@gmail.com), Narendra Kumar2 (nkkumarnarendra27@ gmail.com), Maya Shashi3 (aj.kumar29stm@gmail.com), Devesh Kumar4
SMS Based Kids Tracking and Safety System by Using RFID and GSM Nitin Shyam1 (nitinshyam109@gmail.com), Narendra Kumar2 (nkkumarnarendra27@ gmail.com), Maya Shashi3 (aj.kumar29stm@gmail.com), Devesh Kumar4
ABSTRACT 1. INTRODUCTION
 THE APPLICATION OF SOFTWARE DEFINED RADIO IN A COOPERATIVE WIRELESS NETWORK Jesper M. Kristensen (Aalborg University, Center for Teleinfrastructure, Aalborg, Denmark; jmk@kom.aau.dk); Frank H.P. Fitzek
THE APPLICATION OF SOFTWARE DEFINED RADIO IN A COOPERATIVE WIRELESS NETWORK Jesper M. Kristensen (Aalborg University, Center for Teleinfrastructure, Aalborg, Denmark; jmk@kom.aau.dk); Frank H.P. Fitzek
Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain
 This fiche is part of the wider roadmap for cross-cutting KETs activities Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain Cross-cutting
This fiche is part of the wider roadmap for cross-cutting KETs activities Potential areas of industrial interest relevant for cross-cutting KETs in the Electronics and Communication Systems domain Cross-cutting
Extraction and Recognition of Text From Digital English Comic Image Using Median Filter
 Extraction and Recognition of Text From Digital English Comic Image Using Median Filter S.Ranjini 1 Research Scholar,Department of Information technology Bharathiar University Coimbatore,India ranjinisengottaiyan@gmail.com
Extraction and Recognition of Text From Digital English Comic Image Using Median Filter S.Ranjini 1 Research Scholar,Department of Information technology Bharathiar University Coimbatore,India ranjinisengottaiyan@gmail.com
Enabling ICT for. development
 Enabling ICT for development Interview with Dr M-H Carolyn Nguyen, who explains why governments need to start thinking seriously about how to leverage ICT for their development goals, and why an appropriate
Enabling ICT for development Interview with Dr M-H Carolyn Nguyen, who explains why governments need to start thinking seriously about how to leverage ICT for their development goals, and why an appropriate
Research and implementation of key technologies for smart park construction based on the internet of things and cloud computing 1
 Acta Technica 62 No. 3B/2017, 117 126 c 2017 Institute of Thermomechanics CAS, v.v.i. Research and implementation of key technologies for smart park construction based on the internet of things and cloud
Acta Technica 62 No. 3B/2017, 117 126 c 2017 Institute of Thermomechanics CAS, v.v.i. Research and implementation of key technologies for smart park construction based on the internet of things and cloud
Analysis of Hybrid Power Conditioner in Three-Phase Four-Wire Distribution Power Systems for Suppressing Harmonics and Neutral-Line Current
 Analysis of Hybrid Power Conditioner in Three-Phase Four-Wire Distribution Power Systems for Suppressing Harmonics and Neutral-Line Current B. Pedaiah 1, B. Parameshwar Reddy 2 M.Tech Student, Dept of
Analysis of Hybrid Power Conditioner in Three-Phase Four-Wire Distribution Power Systems for Suppressing Harmonics and Neutral-Line Current B. Pedaiah 1, B. Parameshwar Reddy 2 M.Tech Student, Dept of
The Key to the Internet-of-Things: Conquering Complexity One Step at a Time
 The Key to the Internet-of-Things: Conquering Complexity One Step at a Time at IEEE QRS2017 Prague, CZ June 19, 2017 Adam T. Drobot Wayne, PA 19087 Outline What is IoT? Where is IoT in its evolution? A
The Key to the Internet-of-Things: Conquering Complexity One Step at a Time at IEEE QRS2017 Prague, CZ June 19, 2017 Adam T. Drobot Wayne, PA 19087 Outline What is IoT? Where is IoT in its evolution? A
A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks
 A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks Eiman Alotaibi, Sumit Roy Dept. of Electrical Engineering U. Washington Box 352500 Seattle, WA 98195 eman76,roy@ee.washington.edu
A Location-Aware Routing Metric (ALARM) for Multi-Hop, Multi-Channel Wireless Mesh Networks Eiman Alotaibi, Sumit Roy Dept. of Electrical Engineering U. Washington Box 352500 Seattle, WA 98195 eman76,roy@ee.washington.edu
A CYBER PHYSICAL SYSTEMS APPROACH FOR ROBOTIC SYSTEMS DESIGN
 Proceedings of the Annual Symposium of the Institute of Solid Mechanics and Session of the Commission of Acoustics, SISOM 2015 Bucharest 21-22 May A CYBER PHYSICAL SYSTEMS APPROACH FOR ROBOTIC SYSTEMS
Proceedings of the Annual Symposium of the Institute of Solid Mechanics and Session of the Commission of Acoustics, SISOM 2015 Bucharest 21-22 May A CYBER PHYSICAL SYSTEMS APPROACH FOR ROBOTIC SYSTEMS
The robots are coming, but the humans aren't leaving
 The robots are coming, but the humans aren't leaving Fernando Aguirre de Oliveira Júnior Partner Services, Outsourcing & Automation Advisory May, 2017 Call it what you want, digital labor is no longer
The robots are coming, but the humans aren't leaving Fernando Aguirre de Oliveira Júnior Partner Services, Outsourcing & Automation Advisory May, 2017 Call it what you want, digital labor is no longer
ISSN Vol.04,Issue.06, June-2016, Pages:
 WWW.IJITECH.ORG ISSN 2321-8665 Vol.04,Issue.06, June-2016, Pages:1117-1121 Design and Development of IMC Tuned PID Controller for Disturbance Rejection of Pure Integrating Process G.MADHU KUMAR 1, V. SUMA
WWW.IJITECH.ORG ISSN 2321-8665 Vol.04,Issue.06, June-2016, Pages:1117-1121 Design and Development of IMC Tuned PID Controller for Disturbance Rejection of Pure Integrating Process G.MADHU KUMAR 1, V. SUMA
Eastern Bank Challenges the Status Quo in Bank Lending by Implementing the DocuSign esignature API to Digitize Processes
 Eastern Bank Challenges the Status Quo in Bank Lending by Implementing the DocuSign esignature API to Digitize Processes Implementing a digital transaction strategy was a huge win for Eastern Bank. It
Eastern Bank Challenges the Status Quo in Bank Lending by Implementing the DocuSign esignature API to Digitize Processes Implementing a digital transaction strategy was a huge win for Eastern Bank. It
Technologies that will make a difference for Canadian Law Enforcement
 The Future Of Public Safety In Smart Cities Technologies that will make a difference for Canadian Law Enforcement The car is several meters away, with only the passenger s side visible to the naked eye,
The Future Of Public Safety In Smart Cities Technologies that will make a difference for Canadian Law Enforcement The car is several meters away, with only the passenger s side visible to the naked eye,
Technology Trends for Government
 Technology Trends for Government Leaders @RajneshSingh rds@jugad.in Where we came from Module 4: ICT Trends for Government Leaders First edition: 2007/8 Revised: 2011 But ICT Trends are fast-evolving K
Technology Trends for Government Leaders @RajneshSingh rds@jugad.in Where we came from Module 4: ICT Trends for Government Leaders First edition: 2007/8 Revised: 2011 But ICT Trends are fast-evolving K
Nonlinear Companding Transform Algorithm for Suppression of PAPR in OFDM Systems
 Nonlinear Companding Transform Algorithm for Suppression of PAPR in OFDM Systems P. Guru Vamsikrishna Reddy 1, Dr. C. Subhas 2 1 Student, Department of ECE, Sree Vidyanikethan Engineering College, Andhra
Nonlinear Companding Transform Algorithm for Suppression of PAPR in OFDM Systems P. Guru Vamsikrishna Reddy 1, Dr. C. Subhas 2 1 Student, Department of ECE, Sree Vidyanikethan Engineering College, Andhra
INTEL INNOVATION GENERATION
 INTEL INNOVATION GENERATION Overview Intel was founded by inventors, and the company s continued existence depends on innovation. We recognize that the health of local economies including those where our
INTEL INNOVATION GENERATION Overview Intel was founded by inventors, and the company s continued existence depends on innovation. We recognize that the health of local economies including those where our
INTERNET OF THINGS (IoT) PRESENTED BY: Wafaa Rizin Ameer
 INTERNET OF THINGS (IoT) PRESENTED BY: Wafaa Rizin Ameer INTRODUCTION IoT: All about physical items talking to each other The term coined by Kevin Ashton in 1999 Composed by two words and concepts: Internet
INTERNET OF THINGS (IoT) PRESENTED BY: Wafaa Rizin Ameer INTRODUCTION IoT: All about physical items talking to each other The term coined by Kevin Ashton in 1999 Composed by two words and concepts: Internet
Advances and Perspectives in Health Information Standards
 Advances and Perspectives in Health Information Standards HL7 Brazil June 14, 2018 W. Ed Hammond. Ph.D., FACMI, FAIMBE, FIMIA, FHL7, FIAHSI Director, Duke Center for Health Informatics Director, Applied
Advances and Perspectives in Health Information Standards HL7 Brazil June 14, 2018 W. Ed Hammond. Ph.D., FACMI, FAIMBE, FIMIA, FHL7, FIAHSI Director, Duke Center for Health Informatics Director, Applied
RADIO SPECTRUM COMMITTEE
 Ref. Ares(2018)4780924-18/09/2018 EUROPEAN COMMISSION Communications Networks Content & Technology Directorate-General Electronic Communications Networks & Services Radio Spectrum Policy Brussels, 12 July
Ref. Ares(2018)4780924-18/09/2018 EUROPEAN COMMISSION Communications Networks Content & Technology Directorate-General Electronic Communications Networks & Services Radio Spectrum Policy Brussels, 12 July
A web-based early-warning service to monitor drinking-water treatment plant operations
 Snapshots of Doctoral Research at University College Cork 2010 A web-based early-warning service to monitor drinking-water treatment plant operations Franclin S. Foping Cork Constraint Computation Centre,
Snapshots of Doctoral Research at University College Cork 2010 A web-based early-warning service to monitor drinking-water treatment plant operations Franclin S. Foping Cork Constraint Computation Centre,
Horizon 2020 ICT Robotics Work Programme (draft - Publication: 20 October 2015)
 NCP TRAINING BRUSSELS 07 OCTOBER 2015 1 Horizon 2020 ICT Robotics Work Programme 2016 2017 (draft - Publication: 20 October 2015) Cécile Huet Deputy Head of Unit Robotics Directorate General for Communication
NCP TRAINING BRUSSELS 07 OCTOBER 2015 1 Horizon 2020 ICT Robotics Work Programme 2016 2017 (draft - Publication: 20 October 2015) Cécile Huet Deputy Head of Unit Robotics Directorate General for Communication
AUTOMATED WATER METER READING
 AUTOMATED WATER METER READING Padmini M S(Assistant Professor) 1, Sejal S Kulkarni 2, Shruthi K Bhat 3, Shruti S Uppin 4 Dept. of Computer Science and Engineering,National Institute Of Engineering,Mysore,
AUTOMATED WATER METER READING Padmini M S(Assistant Professor) 1, Sejal S Kulkarni 2, Shruthi K Bhat 3, Shruti S Uppin 4 Dept. of Computer Science and Engineering,National Institute Of Engineering,Mysore,
The Disappearing Computer. Information Document, IST Call for proposals, February 2000.
 The Disappearing Computer Information Document, IST Call for proposals, February 2000. Mission Statement To see how information technology can be diffused into everyday objects and settings, and to see
The Disappearing Computer Information Document, IST Call for proposals, February 2000. Mission Statement To see how information technology can be diffused into everyday objects and settings, and to see
Draft executive summaries to target groups on industrial energy efficiency and material substitution in carbonintensive
 Technology Executive Committee 29 August 2017 Fifteenth meeting Bonn, Germany, 12 15 September 2017 Draft executive summaries to target groups on industrial energy efficiency and material substitution
Technology Executive Committee 29 August 2017 Fifteenth meeting Bonn, Germany, 12 15 September 2017 Draft executive summaries to target groups on industrial energy efficiency and material substitution
ISSN Vol.03,Issue.07, August-2015, Pages:
 WWW.IJITECH.ORG ISSN 2321-8665 Vol.03,Issue.07, August-2015, Pages:1276-1281 Comparison of an Active and Hybrid Power Filter Devices THAKKALAPELLI JEEVITHA 1, A. SURESH KUMAR 2 1 PG Scholar, Dept of EEE,
WWW.IJITECH.ORG ISSN 2321-8665 Vol.03,Issue.07, August-2015, Pages:1276-1281 Comparison of an Active and Hybrid Power Filter Devices THAKKALAPELLI JEEVITHA 1, A. SURESH KUMAR 2 1 PG Scholar, Dept of EEE,
Industry 4.0: the new challenge for the Italian textile machinery industry
 Industry 4.0: the new challenge for the Italian textile machinery industry Executive Summary June 2017 by Contacts: Economics & Press Office Ph: +39 02 4693611 email: economics-press@acimit.it ACIMIT has
Industry 4.0: the new challenge for the Italian textile machinery industry Executive Summary June 2017 by Contacts: Economics & Press Office Ph: +39 02 4693611 email: economics-press@acimit.it ACIMIT has
An Introduction to IoT and its Impact on Society
 An Introduction to IoT and its Impact on Society CDAIT Thought Leadership Working Group Karen I. Matthews, PhD, MBA 1 Our Journey to Understanding the Internet of Things (IoT) and its Impact on Society
An Introduction to IoT and its Impact on Society CDAIT Thought Leadership Working Group Karen I. Matthews, PhD, MBA 1 Our Journey to Understanding the Internet of Things (IoT) and its Impact on Society
An Innovative Public Private Approach for a Technology Facilitation Mechanism (TFM)
 Summary An Innovative Public Private Approach for a Technology Facilitation Mechanism (TFM) July 31, 2012 In response to paragraph 265 276 of the Rio+20 Outcome Document, this paper outlines an innovative
Summary An Innovative Public Private Approach for a Technology Facilitation Mechanism (TFM) July 31, 2012 In response to paragraph 265 276 of the Rio+20 Outcome Document, this paper outlines an innovative
SMART CITY VNPT s APPROACH & EXPERIENCE. VNPT Group
 SMART CITY VNPT s APPROACH & EXPERIENCE VNPT Group Thanh Hoa, 5 th July 2018 1 SmartCity AGENDA 1 Technology context for Smart City 2 VNPT s Approach for Smart City 3 VNPT s Experience in Smart City Development
SMART CITY VNPT s APPROACH & EXPERIENCE VNPT Group Thanh Hoa, 5 th July 2018 1 SmartCity AGENDA 1 Technology context for Smart City 2 VNPT s Approach for Smart City 3 VNPT s Experience in Smart City Development
Comments of Shared Spectrum Company
 Before the DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Washington, D.C. 20230 In the Matter of ) ) Developing a Sustainable Spectrum ) Docket No. 181130999 8999 01
Before the DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Washington, D.C. 20230 In the Matter of ) ) Developing a Sustainable Spectrum ) Docket No. 181130999 8999 01
FP7 ICT Work Programme
 FP7 ICT Work Programme 2011-12 Focus on ICT Call 8 and PPP Calls Alessandro Barbagli European Commission Head of Sector - ICT Operations Roma 9 September 2011 Disclaimer: The aim of this presentation is
FP7 ICT Work Programme 2011-12 Focus on ICT Call 8 and PPP Calls Alessandro Barbagli European Commission Head of Sector - ICT Operations Roma 9 September 2011 Disclaimer: The aim of this presentation is
DIGITAL WITH PLYMOUTH UNIVERSITY DIGITAL STRATEGY
 DIGITAL DIGITAL Vision Our vision is to ensure our world-class teaching, learning and research continues to thrive in an increasingly digital world by rapidly adapting to digital trends and exploiting
DIGITAL DIGITAL Vision Our vision is to ensure our world-class teaching, learning and research continues to thrive in an increasingly digital world by rapidly adapting to digital trends and exploiting
Designing for an Internet of Humans
 Designing for an Internet of Humans The Route to Adoption of IoT Paul Grace pjg@it-innovation.soton.ac.uk 24 March 2017 IT Innovation Centre The IT Innovation Centre is an applied research centre advancing
Designing for an Internet of Humans The Route to Adoption of IoT Paul Grace pjg@it-innovation.soton.ac.uk 24 March 2017 IT Innovation Centre The IT Innovation Centre is an applied research centre advancing
APEC Internet and Digital Economy Roadmap
 2017/CSOM/006 Agenda Item: 3 APEC Internet and Digital Economy Roadmap Purpose: Consideration Submitted by: AHSGIE Concluding Senior Officials Meeting Da Nang, Viet Nam 6-7 November 2017 INTRODUCTION APEC
2017/CSOM/006 Agenda Item: 3 APEC Internet and Digital Economy Roadmap Purpose: Consideration Submitted by: AHSGIE Concluding Senior Officials Meeting Da Nang, Viet Nam 6-7 November 2017 INTRODUCTION APEC
